Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Survey Paper
- Open access
- Published: 09 December 2019
Internet of Things is a revolutionary approach for future technology enhancement: a review
- Sachin Kumar ORCID: orcid.org/0000-0003-3949-0302 1 ,
- Prayag Tiwari 2 &
- Mikhail Zymbler 1
Journal of Big Data volume 6 , Article number: 111 ( 2019 ) Cite this article
244k Accesses
472 Citations
43 Altmetric
Metrics details
Internet of Things (IoT) is a new paradigm that has changed the traditional way of living into a high tech life style. Smart city, smart homes, pollution control, energy saving, smart transportation, smart industries are such transformations due to IoT. A lot of crucial research studies and investigations have been done in order to enhance the technology through IoT. However, there are still a lot of challenges and issues that need to be addressed to achieve the full potential of IoT. These challenges and issues must be considered from various aspects of IoT such as applications, challenges, enabling technologies, social and environmental impacts etc. The main goal of this review article is to provide a detailed discussion from both technological and social perspective. The article discusses different challenges and key issues of IoT, architecture and important application domains. Also, the article bring into light the existing literature and illustrated their contribution in different aspects of IoT. Moreover, the importance of big data and its analysis with respect to IoT has been discussed. This article would help the readers and researcher to understand the IoT and its applicability to the real world.
Introduction
The Internet of Things (IoT) is an emerging paradigm that enables the communication between electronic devices and sensors through the internet in order to facilitate our lives. IoT use smart devices and internet to provide innovative solutions to various challenges and issues related to various business, governmental and public/private industries across the world [ 1 ]. IoT is progressively becoming an important aspect of our life that can be sensed everywhere around us. In whole, IoT is an innovation that puts together extensive variety of smart systems, frameworks and intelligent devices and sensors (Fig. 1 ). Moreover, it takes advantage of quantum and nanotechnology in terms of storage, sensing and processing speed which were not conceivable beforehand [ 2 ]. Extensive research studies have been done and available in terms of scientific articles, press reports both on internet and in the form of printed materials to illustrate the potential effectiveness and applicability of IoT transformations. It could be utilized as a preparatory work before making novel innovative business plans while considering the security, assurance and interoperability.
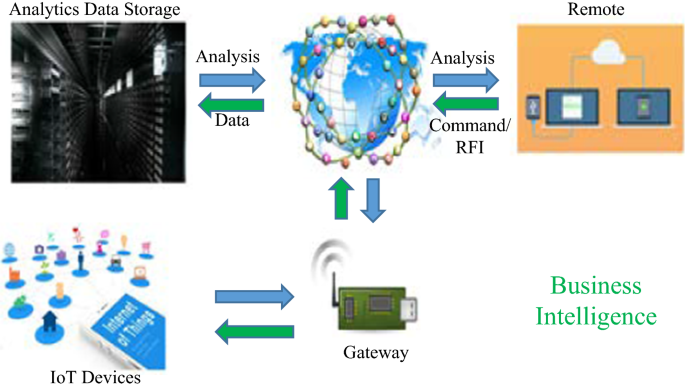
General architecture of IoT
A great transformation can be observed in our daily routine life along with the increasing involvement of IoT devices and technology. One such development of IoT is the concept of Smart Home Systems (SHS) and appliances that consist of internet based devices, automation system for homes and reliable energy management system [ 3 ]. Besides, another important achievement of IoT is Smart Health Sensing system (SHSS). SHSS incorporates small intelligent equipment and devices to support the health of the human being. These devices can be used both indoors and outdoors to check and monitor the different health issues and fitness level or the amount of calories burned in the fitness center etc. Also, it is being used to monitor the critical health conditions in the hospitals and trauma centers as well. Hence, it has changed the entire scenario of the medical domain by facilitating it with high technology and smart devices [ 4 , 5 ]. Moreover, IoT developers and researchers are actively involved to uplift the life style of the disabled and senior age group people. IoT has shown a drastic performance in this area and has provided a new direction for the normal life of such people. As these devices and equipment are very cost effective in terms of development cost and easily available within a normal price range, hence most of the people are availing them [ 6 ]. Thanks to IoT, as they can live a normal life. Another important aspect of our life is transportation. IoT has brought up some new advancements to make it more efficient, comfortable and reliable. Intelligent sensors, drone devices are now controlling the traffic at different signalized intersections across major cities. In addition, vehicles are being launched in markets with pre-installed sensing devices that are able to sense the upcoming heavy traffic congestions on the map and may suggest you another route with low traffic congestion [ 7 ]. Therefore IoT has a lot to serve in various aspects of life and technology. We may conclude that IoT has a lot of scope both in terms of technology enhancement and facilitate the humankind.
IoT has also shown its importance and potential in the economic and industrial growth of a developing region. Also, in trade and stock exchange market, it is being considered as a revolutionary step. However, security of data and information is an important concern and highly desirable, which is a major challenging issue to deal with [ 5 ]. Internet being a largest source of security threats and cyber-attacks has opened the various doors for hackers and thus made the data and information insecure. However, IoT is committed to provide the best possible solutions to deal with security issues of data and information. Hence, the most important concern of IoT in trade and economy is security. Therefore, the development of a secure path for collaboration between social networks and privacy concerns is a hot topic in IoT and IoT developers are working hard for this.
The remaining part of the article is organized as follows: “ Literature survey ” section will provide state of art on important studies that addressed various challenges and issues in IoT. “ IoT architecture and technologies ” section discussed the IoT functional blocks, architecture in detail. In “ Major key issues and challenges of IoT ” section, important key issues and challenges of IoT is discussed. “ Major IoT applications ” section provides emerging application domains of IoT. In “ Importance of big data analytics in IoT ” section, the role and importance of big data and its analysis is discussed. Finally, the article concluded in “ Conclusions ” section.
Literature survey
IoT has a multidisciplinary vision to provide its benefit to several domains such as environmental, industrial, public/private, medical, transportation etc. Different researchers have explained the IoT differently with respect to specific interests and aspects. The potential and power of IoT can be seen in several application domains. Figure 2 illustrates few of the application domains of IoTs potentials.
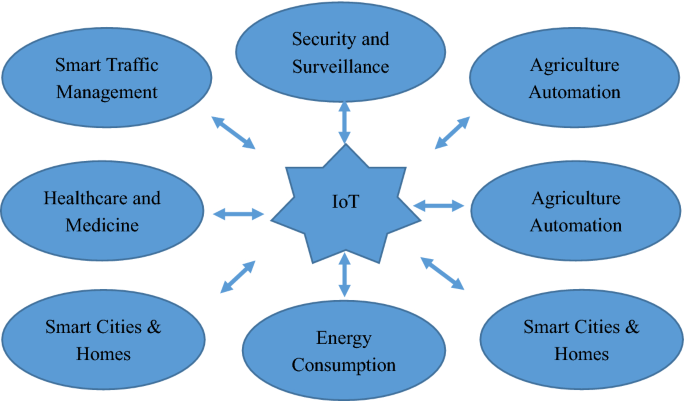
Some of the potential application domains of IoT
Various important IoT projects have taken charge over the market in last few years. Some of the important IoT projects that have captured most of the market are shown in Fig. 3 . In Fig. 3 , a global distribution of these IoT projects is shown among American, European and Asia/Pacific region. It can be seen that American continent are contributing more in the health care and smart supply chain projects whereas contribution of European continent is more in the smart city projects [ 8 ].
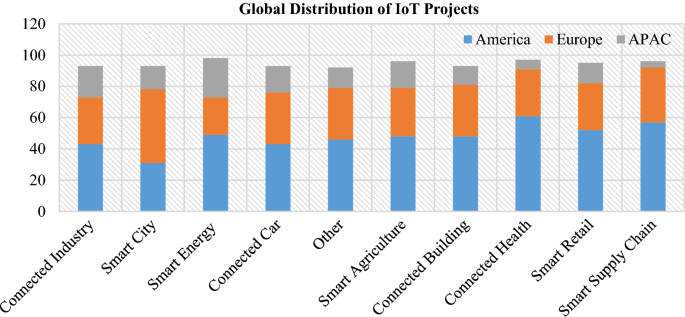
Global distribution of IoT projects among America (USA, South America and Canada), Europe and APAC (Asia and Pacific region) [ 8 ]
Figure 4 , illustrates the global market share of IoT projects worldwide [ 8 ]. It is evident that industry, smart city, smart energy and smart vehicle based IoT projects have a big market share in comparison to others.
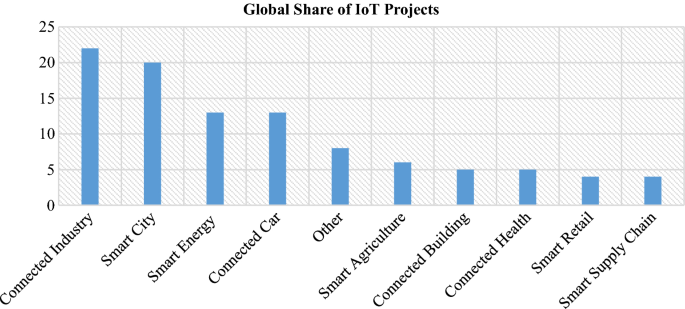
Global share of IoT projects across the world [ 8 ]
Smart city is one of the trendy application areas of IoT that incorporates smart homes as well. Smart home consists of IoT enabled home appliances, air-conditioning/heating system, television, audio/video streaming devices, and security systems which are communicating with each other in order to provide best comfort, security and reduced energy consumption. All this communication takes place through IoT based central control unit using Internet. The concept of smart city gained popularity in the last decade and attracted a lot of research activities [ 9 ]. The smart home business economy is about to cross the 100 billion dollars by 2022 [ 10 ]. Smart home does not only provide the in-house comfort but also benefits the house owner in cost cutting in several aspects i.e. low energy consumption will results in comparatively lower electricity bill. Besides smart homes, another category that comes within smart city is smart vehicles. Modern cars are equipped with intelligent devices and sensors that control most of the components from the headlights of the car to the engine [ 11 ]. The IoT is committed towards developing a new smart car systems that incorporates wireless communication between car-to-car and car-to-driver to ensure predictive maintenance with comfortable and safe driving experience [ 12 ].
Khajenasiri et al. [ 10 ] performed a survey on the IoT solutions for smart energy control to benefit the smart city applications. They stated that at present IoT has been deployed in very few application areas to serve the technology and people. The scope of IoT is very wide and in near future IoT is able to capture almost all application areas. They mentioned that energy saving is one of the important part of the society and IoT can assist in developing a smart energy control system that will save both energy and money. They described an IoT architecture with respect to smart city concept. The authors also discussed that one of the challenging task in achieving this is the immaturity of IoT hardware and software. They suggested that these issues must be resolved to ensure a reliable, efficient and user friendly IoT system.
Alavi et al. [ 13 ] addressed the urbanization issue in the cities. The movement of people from rural to urban atmosphere resulting in growing population of the cities. Therefore, there is a need to provide smart solutions for mobility, energy, healthcare and infrastructure. Smart city is one of the important application areas for IoT developers. It explores several issues such as traffic management, air quality management, public safety solutions, smart parking, smart lightning and smart waste collection (Fig. 5 ). They mentioned that IoT is working hard to tackle these challenging issues. The need for improved smart city infrastructure with growing urbanization has opened the doors for entrepreneurs in the field of smart city technologies. The authors concluded that IoT enabled technology is very important for the development of sustainable smart cities.
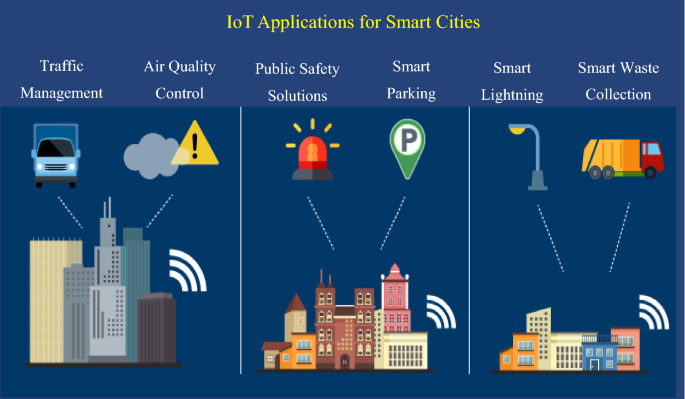
Potential IoT application areas for smart cities
Another important issue of IoT that requires attention and a lot of research is security and privacy. Weber [ 14 ] focused on these issues and suggested that a private organization availing IoT must incorporate data authentication, access control, resilience to attacks and client privacy into their business activities that would be an additional advantage. Weber suggested that in order to define global security and privacy issues, IoT developers must take into account the geographical limitations of the different countries. A generic framework needs to be designed to fit the global needs in terms of privacy and security. It is highly recommended to investigate and recognize the issues and challenges in privacy and security before developing the full fledge working IoT framework.
Later, Heer et al. [ 15 ] came up with a security issue in IP based IoT system. They mentioned that internet is backbone for the communication among devices that takes place in an IoT system. Therefore, security issues in IP based IoT systems are an important concern. In addition, security architecture should be designed considering the life cycle and capabilities of any object in the IoT system. It also includes the involvement of the trusted third party and the security protocols. The security architecture with scalability potential to serve the small-scale to large-scale things in IoT is highly desirable. The study pointed out that IoT gave rise to a new way of communication among several things across the network therefore traditional end to end internet protocol are not able to provide required support to this communication. Therefore, new protocols must be designed considering the translations at the gateways to ensure end-to-end security. Moreover, all the layers responsible for communication has their own security issues and requirements. Therefore, satisfying the requirements for one particular layers will leave the system into a vulnerable state and security should be ensured for all the layers.
Authentication and access control is another issue in IoT that needs promising solutions to strengthen the security. Liu et al. [ 16 ] brought up a solution to handle authentication and access control. Authentication is very important to verify the communicating parties to prevent the loss of confidential information. Liu et al. [ 16 ] provided an authentication scheme based on Elliptic Curve Cryptosystem and verified it on different security threats i.e. eavesdropping, man-in-the-middle attack, key control and replay attack. They claimed that there proposed schemes are able to provide better authentication and access control in IoT based communication. Later, Kothmayr et al. [ 17 ] proposed a two-way authentication scheme based of datagram transport layer security (DTLS) for IoT. The attackers over the internet are always active to steal the secured information. The proposed approach are able to provide message security, integrity, authenticity and confidentiality, memory overhead and end-to-end latency in the IoT based communication network.
Li et al. [ 18 ] proposed a dynamic approach for data centric IoT applications with respect to cloud platforms. The need of an appropriate device, software configuration and infrastructure requires efficient solutions to support massive amount of IoT applications that are running on cloud platforms. IoT developers and researchers are actively engaged in developing solutions considering both massive platforms and heterogeneous nature of IoT objects and devices. Olivier et al. [ 19 ] explained the concept of software defined networking (SDN) based architecture that performs well even if a well-defined architecture is not available. They proposed that SDN based security architecture is more flexible and efficient for IoT.
Luk et al. [ 20 ] stated that the main task of a secure sensor network (SSN) is to provide data privacy, protection from replay attacks and authentication. They discussed two popular SSN services namely TinySec [ 21 ] and ZigBee [ 22 ]. They mentioned that although both the SSN services are efficient and reliable, however, ZigBee is comparatively provides higher security but consumes high energy whereas TinySec consumes low energy but not as highly secured as ZigBee. They proposed another architecture MiniSec to support high security and low energy consumption and demonstrated its performance for the Telos platform. Yan et al. [ 23 ] stated that trust management is an important issue in IoT. Trust management helps people to understand and trust IoT services and applications without worrying about uncertainty issues and risks [ 24 ]. They investigated different issues in trust management and discussed its importance with respect to IoT developers and users.
Noura et al. [ 25 ] stated the importance of interoperability in IoT as it allows integration of devices, services from different heterogeneous platforms to provide the efficient and reliable service. Several other studies focused on the importance of interoperability and discussed several challenges that interoperability issue is facing in IoT [ 26 , 27 , 28 ]. Kim et al. [ 29 ] addressed the issue of climate change and proposed an IoT based ecological monitoring system. They mentioned that existing approaches are time consuming and required a lot of human intervention. Also, a routine visit is required to collect the information from the sensors installed at the site under investigation. Also, some information remained missing which leads to not highly accurate analysis. Therefore, IoT based framework is able to solve this problem and can provide high accuracy in analysis and prediction. Later, Wang et al. [ 30 ] shows their concern for domestic waste water treatment. They discussed several deficiencies in the process of waste water treatment and dynamic monitoring system and suggested effective solutions based on IoT. They stated that IoT can be very effective in the waste water treatment and process monitoring.
Agriculture is one of the important domain around the world. Agriculture depends on several factors i.e. geographical, ecological etc. Qiu et al. [ 31 ] stated that technology that is being used for ecosystem control is immature with low intelligence level. They mentioned that it could be a good application area for IoT developers and researchers.
Qiu et al. [ 31 ] proposed an intelligent monitoring platform framework for facility agriculture ecosystem based on IoT that consists of four layer mechanism to manage the agriculture ecosystem. Each layer is responsible for specific task and together the framework is able to achieve a better ecosystem with reduced human intervention.
Another important concern around the world is climate change due to global warming. Fang et al. [ 32 ] introduced an integrated information system (IIS) that integrates IoT, geo-informatics, cloud computing, global positioning system (GPS), geographical information system (GIS) and e-science in order to provide an effective environmental monitoring and control system. They mentioned that the proposed IIS provides improved data collection, analysis and decision making for climate control. Air pollution is another important concern worldwide. Various tools and techniques are available to air quality measures and control. Cheng et al. [ 33 ] proposed AirCloud which is a cloud based air quality and monitoring system. They deployed AirCloud and evaluated its performance using 5 months data for the continuous duration of 2 months.
Temglit et al. [ 34 ] considered Quality of Service (QoS) as an important challenge and a complex task in evaluation and selection of IoT devices, protocols and services. QoS is very important criteria to attract and gain trust of users towards IoT services and devices. They came up with an interesting distributed QoS selection approach. This approach was based on distributed constraint optimization problem and multi-agent paradigm. Further, the approach was evaluated based on several experiments under realistic distributed environments. Another important aspect of IoT is its applicability to the environmental and agriculture standards. Talavera et al. [ 35 ] focused in this direction and presented the fundamental efforts of IoT for agro-industrial and environmental aspects in a survey study. They mentioned that the efforts of IoT in these areas are noticeable. IoT is strengthening the current technology and benefiting the farmers and society. Jara et al. [ 36 ] discussed the importance of IoT based monitoring of patients health. They suggested that IoT devices and sensors with the help of internet can assist health monitoring of patients. They also proposed a framework and protocol to achieve their objective. Table 1 provides a summary of the important studies and the direction of research with a comparison of studies on certain evaluation parameters.
IoT architecture and technologies
The IoT architecture consists of five important layers that defines all the functionalities of IoT systems. These layers are perception layer, network layer, middleware layer, application layer, business layer. At the bottom of IoT architecture, perception layer exists that consists of physical devices i.e. sensors, RFID chips, barcodes etc. and other physical objects connected in IoT network. These devices collects information in order to deliver it to the network layer. Network layer works as a transmission medium to deliver the information from perception layer to the information processing system. This transmission of information may use any wired/wireless medium along with 3G/4G, Wi-Fi, Bluetooth etc. Next level layer is known as middleware layer. The main task of this layer is to process the information received from the network layer and make decisions based on the results achieved from ubiquitous computing. Next, this processed information is used by application layer for global device management. On the top of the architecture, there is a business layer which control the overall IoT system, its applications and services. The business layer visualizes the information and statistics received from the application layer and further used this knowledge to plan future targets and strategies. Furthermore, the IoT architectures can be modified according to the need and application domain [ 19 , 20 , 37 ]. Besides layered framework, IoT system consists of several functional blocks that supports various IoT activities such as sensing mechanism, authentication and identification, control and management [ 38 ]. Figure 6 illustrates such functional blocks of IoT architecture.
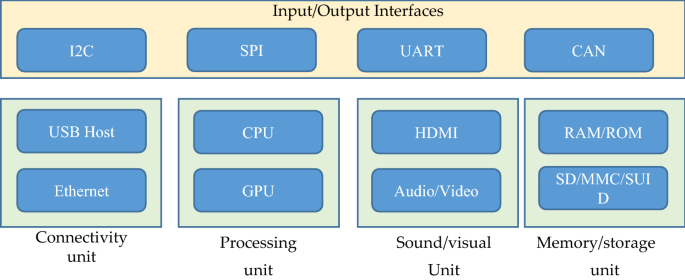
A generic function module of IoT system
There are several important functional blocks responsible for I/O operations, connectivity issues, processing, audio/video monitoring and storage management. All these functional block together incorporates an efficient IoT system which are important for optimum performance. Although, there are several reference architectures proposed with the technical specifications, but these are still far from the standard architecture that is suitable for global IoT [ 39 ]. Therefore, a suitable architecture is still needsvk to be designed that could satisfy the global IoT needs. The generic working structure of IoT system is shown in Fig. 7 . Figure 7 shows a dependency of IoT on particular application parameters. IoT gateways have an important role in IoT communication as it allows connectivity between IoT servers and IoT devices related to several applications [ 40 ].
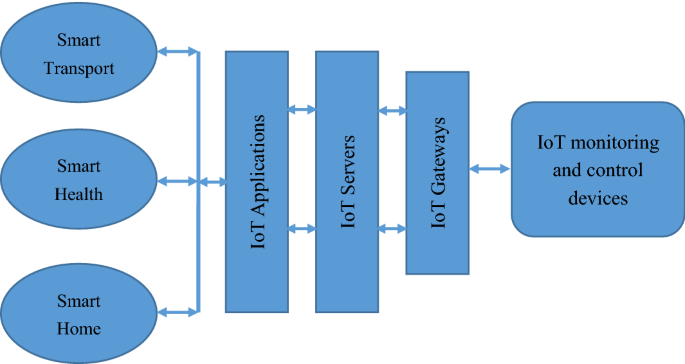
Working structure of IoT
Scalability, modularity, interoperability and openness are the key design issues for an efficient IoT architecture in a heterogenous environment. The IoT architecture must be designed with an objective to fulfil the requirements of cross domain interactions, multi-system integration with the potential of simple and scalable management functionalities, big data analytics and storage, and user friendly applications. Also, the architecture should be able to scaleup the functionality and add some intelligence and automation among the IoT devices in the system.
Moreover, increasing amount of massive data being generated through the communication between IoT sensors and devices is a new challenge. Therefore, an efficient architecture is required to deal with massive amount of streaming data in IoT system. Two popular IoT system architectures are cloud and fog/edge computing that supports with the handling, monitoring and analysis of huge amount of data in IoT systems. Therefore, a modern IoT architecture can be defined as a 4 stage architecture as shown in Fig. 8 .
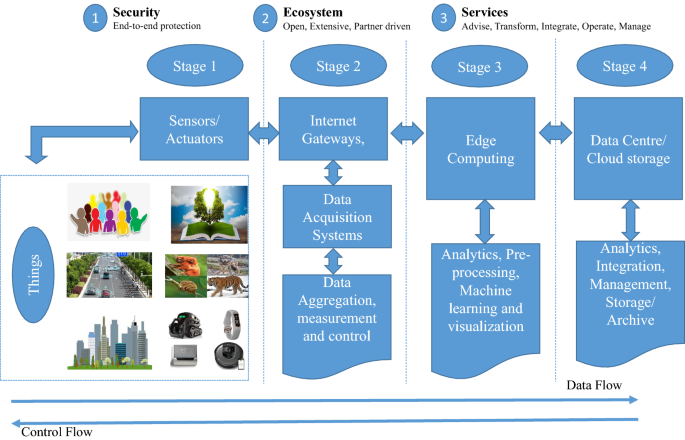
Four stage IoT architecture to deal with massive data
In stage 1 of the architecture, sensors and actuators plays an important role. Real world is comprised of environment, humans, animals, electronic gadgets, smart vehicles, and buildings etc. Sensors detect the signals and data flow from these real world entities and transforms into data which could further be used for analysis. Moreover, actuators is able to intervene the reality i.e. to control the temperature of the room, to slow down the vehicle speed, to turn off the music and light etc. Therefore, stage 1 assist in collecting data from real world which could be useful for further analysis. Stage 2 is responsible to collaborate with sensors and actuators along with gateways and data acquisition systems. In this stage, massive amount of data generated in stage 1 is aggregated and optimized in a structured way suitable for processing. Once the massive amount of data is aggregated and structured then it is ready to be passed to stage 3 which is edge computing. Edge computing can be defined as an open architecture in distributed fashion which allows use of IoT technologies and massive computing power from different locations worldwide. It is very powerful approach for streaming data processing and thus suitable for IoT systems. In stage 3, edge computing technologies deals with massive amount of data and provides various functionalities such as visualization, integration of data from other sources, analysis using machine learning methods etc. The last stage comprises of several important activities such as in depth processing and analysis, sending feedback to improve the precision and accuracy of the entire system. Everything at this stage will be performed on cloud server or data centre. Big data framework such as Hadoop and Spark may be utilized to handle this large streaming data and machine learning approaches can be used to develop better prediction models which could help in a more accurate and reliable IoT system to meet the demand of present time.
Major key issues and challenges of IoT
The involvement of IoT based systems in all aspects of human lives and various technologies involved in data transfer between embedded devices made it complex and gave rise to several issues and challenges. These issues are also a challenge for the IoT developers in the advanced smart tech society. As technology is growing, challenges and need for advanced IoT system is also growing. Therefore, IoT developers need to think of new issues arising and should provide solutions for them.
Security and privacy issues
One of the most important and challenging issues in the IoT is the security and privacy due to several threats, cyber attacks, risks and vulnerabilities [ 41 ]. The issues that give rise to device level privacy are insufficient authorization and authentication, insecure software, firmware, web interface and poor transport layer encryption [ 42 ]. Security and privacy issues are very important parameters to develop confidence in IoT Systems with respect to various aspects [ 43 ]. Security mechanisms must be embedded at every layer of IoT architecture to prevent security threats and attacks [ 23 ]. Several protocols are developed and efficiently deployed on every layer of communication channel to ensure the security and privacy in IoT based systems [ 44 , 45 ]. Secure Socket Layer (SSL) and Datagram Transport Layer Security (DTLS) are one of the cryptographic protocols that are implemented between transport and application layer to provide security solutions in various IoT systems [ 44 ]. However, some IoT applications require different methods to ensure the security in communication between IoT devices. Besides this, if communication takes place using wireless technologies within the IoT system, it becomes more vulnerable to security risks. Therefore, certain methods should be deployed to detect malicious actions and for self healing or recovery. Privacy on the other hand is another important concern which allows users to feel secure and comfortable while using IoT solutions. Therefore, it is required to maintain the authorization and authentication over a secure network to establish the communication between trusted parties [ 46 ]. Another issue is the different privacy policies for different objects communicating within the IoT system. Therefore, each object should be able to verify the privacy policies of other objects in IoT system before transmitting the data.
Interoperability/standard issues
Interoperability is the feasibility to exchange the information among different IoT devices and systems. This exchange of information does not rely on the deployed software and hardware. The interoperability issue arises due to the heterogeneous nature of different technology and solutions used for IoT development. The four interoperability levels are technical, semantic, syntactic and organizational [ 47 ]. Various functionalities are being provided by IoT systems to improve the interoperability that ensures communication between different objects in a heterogeneous environment. Additionally, it is possible to merge different IoT platforms based on their functionalities to provide various solutions for IoT users [ 48 ]. Considering interoperability an important issue, researchers approved several solutions that are also know as interoperability handling approaches [ 49 ]. These solutions could be adapaters/gateways based, virtual networks/overlay based, service oriented architecture based etc. Although interoperability handling approaches ease some pressure on IoT systems but there are still certain challenges remain with interoperability that could be a scope for future studies [ 25 ].
Ethics, law and regulatory rights
Another issue for IoT developers is the ethics, law and regulatory rights. There are certain rules and regulations to maintain the standard, moral values and to prevent the people from violating them. Ethics and law are very similar term with the only difference is that ethics are standards that people believes and laws are certain restrictions decided by the government. However, both ethics and laws are designed to maintain the standard, quality and prevent people from illegal use. With the development of IoT, several real life problems are solved but it has also given rise to critical ethical and legal challenges [ 50 ]. Data security, privacy protection, trust and safety, data usability are some of those challenges. It has also been observed that majority of IoT users are supporting government norms and regulations with respect to data protection, privacy and safety due to the lack of trust in IoT devices. Therefore, this issue must be taken into consideration to maintain and improve the trust among people for the use of IoT devices and systems.
Scalability, availability and reliability
A system is scalable if it is possible to add new services, equipments and devices without degrading its performance. The main issue with IoT is to support a large number of devices with different memory, processing, storage power and bandwidth [ 28 ]. Another important issue that must be taken into consideration is the availability. Scalability and availability both should be deployed together in the layered framework of IoT. A great example of scalability is cloud based IoT systems which provide sufficient support to scale the IoT network by adding up new devices, storage and processing power as required.
However, this global distributed IoT network gives rise to a new research paradigm to develop a smooth IoT framework that satisfy global needs [ 51 ]. Another key challenge is the availability of resources to the authentic objects regardless of their location and time of the requirement. In a distributed fashion, several small IoT networks are timely attached to the global IoT platforms to utilize their resources and services. Therefore, availability is an important concern [ 52 ]. Due to the use of different data transmission channels i.e. satellite communication, some services and availability of resources may be interrupted. Therefore, an independent and reliable data transmission channel is required for uninterrupted availability of resources and services.
Quality of Service (QoS)
Quality of Service (QoS) is another important factor for IoT. QoS can be defined as a measure to evaluate the quality, efficiency and performance of IoT devices, systems and architecture [ 34 ]. The important and required QoS metrics for IoT applications are reliability, cost, energy consumption, security, availability and service time [ 53 ]. A smarter IoT ecosystem must fulfill the requirements of QoS standards. Also, to ensure the reliability of any IoT service and device, its QoS metrics must be defined first. Further, users may also be able to specifiy their needs and requirements accordingly. Several approaches can be deployed for QoS assessment, however as mentioned by White et al. [ 54 ] there is a trade-off between quality factors and approaches. Therefore, good quality models must be deployed to overcome this trade-off. There are certain good quality models available in literature such as ISO/IEC25010 [ 55 ] and OASIS-WSQM [ 56 ] which can be used to evaluate the approaches used for QoS assessment. These models provides a wide range of quality factors that is quite sufficient for QoS assessment for IoT services. Table 2 summarizes the different studies with respect to IoT key challenges and issues discussed above.
Major IoT applications
Emerging economy, environmental and health-care.
IoT is completely devoted to provide emerging public and financial benefits and development to the society and people. This includes a wide range of public facilities i.e. economic development, water quality maintenance, well-being, industrialization etc. Overall, IoT is working hard to accomplish the social, health and economic goals of United Nations advancement step. Environmental sustainability is another important concern. IoT developers must be concerned about environmental impact of the IoT systems and devices to overcome the negative impact [ 48 ]. Energy consumption by IoT devices is one of the challenges related to environmental impact. Energy consumption is increasing at a high rate due to internet enabled services and edge cutting devices. This area needs research for the development of high quality materials in order to create new IoT devices with lower energy consumption rate. Also, green technologies can be adopted to create efficient energy efficient devices for future use. It is not only environmental friendly but also advantageous for human health. Researchers and engineers are engaged in developing highly efficient IoT devices to monitor several health issues such as diabetes, obesity or depression [ 57 ]. Several issues related to environment, energy and healthcare are considered by several studies.
Smart city, transport and vehicles
IoT is transforming the traditional civil structure of the society into high tech structure with the concept of smart city, smart home and smart vehicles and transport. Rapid improvements are being done with the help of supporting technologies such as machine learning, natural language processing to understand the need and use of technology at home [ 58 ]. Various technologies such as cloud server technology, wireless sensor networks that must be used with IoT servers to provide an efficient smart city. Another important issue is to think about environmental aspect of smart city. Therefore, energy efficient technologies and Green technologies should also be considered for the design and planning of smart city infrastructure. Further, smart devices which are being incorporated into newly launched vehicles are able to detect traffic congestions on the road and thus can suggest an optimum alternate route to the driver. This can help to lower down the congestion in the city. Furthermore, smart devices with optimum cost should be designed to be incorporated in all range vehicles to monitor the activity of engine. IoT is also very effective in maintaining the vehicle’s health. Self driving cars have the potential to communicate with other self driving vehicles by the means of intelligent sensors. This would make the traffic flow smoother than human-driven cars who used to drive in a stop and go manner. This procedure will take time to be implemented all over the world. Till the time, IoT devices can help by sensing traffic congestion ahead and can take appropriate actions. Therefore, a transport manufacturing company should incorporate IoT devices into their manufactured vehicles to provide its advantage to the society.
Agriculture and industry automation
The world’s growing population is estimated to reach approximate 10 billion by 2050. Agriculture plays an important role in our lives. In order to feed such a massive population, we need to advance the current agriculture approaches. Therefore, there is a need to combine agriculture with technology so that the production can be improved in an efficient way. Greenhouse technology is one of the possible approaches in this direction. It provides a way to control the environmental parameters in order to improve the production. However, manual control of this technology is less effective, need manual efforts and cost, and results in energy loss and less production. With the advancement of IoT, smart devices and sensors makes it easier to control the climate inside the chamber and monitor the process which results in energy saving and improved production (Fig. 9 ). Automatization of industries is another advantage of IoT. IoT has been providing game changing solutions for factory digitalization, inventory management, quality control, logistics and supply chain optimization and management.
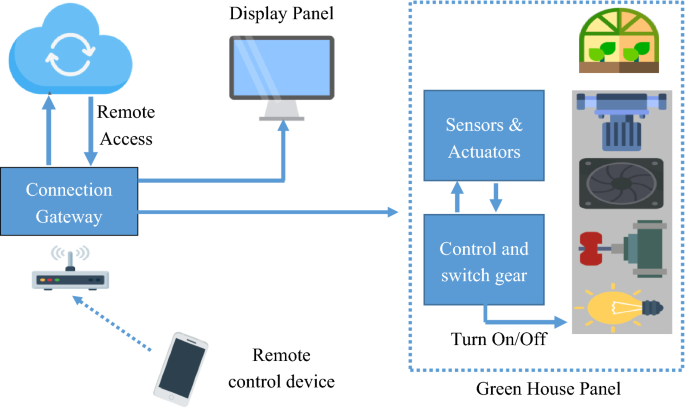
A working structure of IoT system in agriculture production
Importance of big data analytics in IoT
An IoT system comprises of a huge number of devices and sensors that communicates with each other. With the extensive growth and expansion of IoT network, the number of these sensors and devices are increasing rapidly. These devices communicate with each other and transfer a massive amount of data over internet. This data is very huge and streaming every second and thus qualified to be called as big data. Continuous expansion of IoT based networks gives rise to complex issue such as management and collection of data, storage and processing and analytics. IoT big data framework for smart buildings is very useful to deal with several issues of smart buildings such as managing oxygen level, to measure the smoke/hazardous gases and luminosity [ 59 ]. Such framework is capable to collect the data from the sensors installed in the buildings and performs data analytics for decision making. Moreover, industrial production can be improved using an IoT based cyber physical system that is equipped with an information analysis and knowledge acquisition techniques [ 60 ]. Traffic congestion is an important issue with smart cities. The real time traffic information can be collected through IoT devices and sensors installed in traffic signals and this information can be analyzed in an IoT based traffic management system [ 61 ]. In healthcare analysis, the IoT sensors used with patients generate a lot of information about the health condition of patients every second. This large amount of information needs to be integrated at one database and must be processed in real time to take quick decision with high accuracy and big data technology is the best solution for this job [ 62 ]. IoT along with big data analytics can also help to transform the traditional approaches used in manufacturing industries into the modern one [ 63 ]. The sensing devices generates information which can be analyzed using big data approaches and may help in various decision making tasks. Furthermore, use of cloud computing and analytics can benefit the energy development and conservation with reduced cost and customer satisfaction [ 64 ]. IoT devices generate a huge amount of streaming data which needs to be stored effectively and needs further analysis for decision making in real time. Deep learning is very effective to deal with such a large information and can provide results with high accuracy [ 65 ]. Therefore, IoT, Big data analytics and Deep learning together is very important to develop a high tech society.
Conclusions
Recent advancements in IoT have drawn attention of researchers and developers worldwide. IoT developers and researchers are working together to extend the technology on large scale and to benefit the society to the highest possible level. However, improvements are possible only if we consider the various issues and shortcomings in the present technical approaches. In this survey article, we presented several issues and challenges that IoT developer must take into account to develop an improved model. Also, important application areas of IoT is also discussed where IoT developers and researchers are engaged. As IoT is not only providing services but also generates a huge amount of data. Hence, the importance of big data analytics is also discussed which can provide accurate decisions that could be utilized to develop an improved IoT system.
Availability of data and materials
Not applicable.
Abbreviations
Internet of Things
Quality of Service
Web of Things
Cloud of Things
Smart Home System
Smart Health Sensing System
Sfar AR, Zied C, Challal Y. A systematic and cognitive vision for IoT security: a case study of military live simulation and security challenges. In: Proc. 2017 international conference on smart, monitored and controlled cities (SM2C), Sfax, Tunisia, 17–19 Feb. 2017. https://doi.org/10.1109/sm2c.2017.8071828 .
Gatsis K, Pappas GJ. Wireless control for the IoT: power spectrum and security challenges. In: Proc. 2017 IEEE/ACM second international conference on internet-of-things design and implementation (IoTDI), Pittsburg, PA, USA, 18–21 April 2017. INSPEC Accession Number: 16964293.
Zhou J, Cap Z, Dong X, Vasilakos AV. Security and privacy for cloud-based IoT: challenges. IEEE Commun Mag. 2017;55(1):26–33. https://doi.org/10.1109/MCOM.2017.1600363CM .
Article Google Scholar
Sfar AR, Natalizio E, Challal Y, Chtourou Z. A roadmap for security challenges in the internet of things. Digit Commun Netw. 2018;4(1):118–37.
Minoli D, Sohraby K, Kouns J. IoT security (IoTSec) considerations, requirements, and architectures. In: Proc. 14th IEEE annual consumer communications & networking conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017. https://doi.org/10.1109/ccnc.2017.7983271 .
Gaona-Garcia P, Montenegro-Marin CE, Prieto JD, Nieto YV. Analysis of security mechanisms based on clusters IoT environments. Int J Interact Multimed Artif Intell. 2017;4(3):55–60.
Behrendt F. Cycling the smart and sustainable city: analyzing EC policy documents on internet of things, mobility and transport, and smart cities. Sustainability. 2019;11(3):763.
IoT application areas. https://iot-analytics.com/top-10-iot-project-application-areas-q3-2016/ . Accessed 05 Apr 2019.
Zanella A, Bui N, Castellani A, Vangelista L, Zorgi M. Internet of things for smart cities. IEEE IoT-J. 2014;1(1):22–32.
Google Scholar
Khajenasiri I, Estebsari A, Verhelst M, Gielen G. A review on internet of things for intelligent energy control in buildings for smart city applications. Energy Procedia. 2017;111:770–9.
Internet of Things. http://www.ti.com/technologies/internet-of-things/overview.html . Accessed 01 Apr 2019.
Liu T, Yuan R, Chang H. Research on the internet of things in the automotive industry. In: ICMeCG 2012 international conference on management of e-commerce and e-Government, Beijing, China. 20–21 Oct 2012. p. 230–3.
Alavi AH, Jiao P, Buttlar WG, Lajnef N. Internet of things-enabled smart cities: state-of-the-art and future trends. Measurement. 2018;129:589–606.
Weber RH. Internet of things-new security and privacy challenges. Comput Law Secur Rev. 2010;26(1):23–30.
Article MathSciNet Google Scholar
Heer T, Garcia-Morchon O, Hummen R, Keoh SL, Kumar SS, Wehrle K. Security challenges in the IP based internet of things. Wirel Pers Commun. 2011;61(3):527–42.
Liu J, Xiao Y, Philip-Chen CL. Authentication and access control in the internet of things. In: 32nd international conference on distributed computing systems workshops, Macau, China. IEEE xplore; 2012. https://doi.org/10.1109/icdcsw.2012.23 .
Kothmayr T, Schmitt C, Hu W, Brunig M, Carle G. DTLS based security and two-way authentication for the internet of things. Ad Hoc Netw. 2013;11:2710–23.
Li Y, et al. IoT-CANE: a unified knowledge management system for data centric internet of things application systems. J Parallel Distrib Comput. 2019;131:161–72.
Olivier F, Carlos G, Florent N. New security architecture for IoT network. In: International workshop on big data and data mining challenges on IoT and pervasive systems (BigD2M 2015), procedia computer science, vol. 52; 2015. p. 1028–33.
Luk M, Mezzour G, Perrig A, Gligor V. MiniSec: a secure sensor netowrk communication architecture. In: Proc: 6th international symposium on information processing in sensor networks, Cambridge, MA, USA, 25–27 April 2007.
Karlof C, Sastry N, Wagner D. TinySec: a link layer security architecture for wireless sensor networks. In: Proceedings of the second ACM conference on embedded networked sensor systems (SenSys 2004), November 2004.
ZigBee Alliance. Zigbee specification. Technical Report Document 053474r06, Version 1.0, ZigBee Alliance, June 2005.
Yan Z, Zhang P, Vasilakos AV. A survey on trust management for internet of things. J Netw Comput Appl. 2014;42:120–34.
Bao F, Chen I-R, Guo J. Scalable, adaptive and survivable trust management for community of interest based internet of things systems. In: Proc. IEEE 11th international symposium on autonomous decentralized systems (ISADS); 2013. p. 1–7.
Noura M, Atiquazzaman M, Gaedke M. Interoperability in internet of things: taxonomies and open challenges. Mob Netw Appl. 2019;24(3):796–809.
Al-Fuqaha A, Guizani M, Mohammadi M, Aledhari M, Ayyash M. Internet of things: a survey, on enabling technologies, protocols, and applications. IEEE Commun Surv Tutor. 2015;17(June):2347–76.
Palattella MR, Dohler M, Grieco A, Rizzo G, Torsner J, Engel T, Ladid L. Internet of things in the 5G era: enablers, architecture and business models. IEEE J Sel Areas Commun. 2016;34(3):510–27.
Pereira C, Aguiar A. Towards efficient mobile M2M communications: survey and open challenges. Sensors. 2014;14(10):19582–608.
Kim NS, Lee K, Ryu JH. Study on IoT based wild vegetation community ecological monitoring system. In: Proc. 2015 7th international conference on ubiquitous and future networks, Sapporo, Japan, 7–10 July 2015. IEEE.
Wang JY, Cao Y, Yu GP, Yuan M. Research on applications of IoT in domestic waste treatment and disposal. In: Proc. 11th World congress on intelligent control and automation, Shenyang, China, 2014. IEEE.
Qiu T, Xiao H, Zhou P. Framework and case studies of intelligent monitoring platform in facility agriculture ecosystem. In: Proc. 2013 second international conference on agro-geoinformatics (agro-geoinformatics), Fairfax, VA, USA, 12–16 Aug 2013. IEEE.
Fang S, et al. An integrated system for regional environmental monitoring and management based on internet of things. IEEE Trans Ind Inf. 2014;10(2):1596–605.
Cheng Y, et al. AirCloud: a cloud based air-quality monitoring system for everyone. In: Proceedings of the 12th ACM conference on embedded network sensor systems, ACM, Memphis, Tennessee, 03–06 Nov 2014. p. 251–65.
Temglit N, Chibani A, Djouani K, Nacer MA. A distributed agent-based approach for optimal QoS selection in web of object choreography. IEEE Syst J. 2018;12(2):1655–66.
Talavera JM, et al. Review of IoT applications in agro-industrial and environmental fields. Comput Electron Agric. 2017;142(7):283–97.
Jara AJ, Zamora-Izquierdo MA, Skarmeta AF. Interconnection framework for mHealth and remote monitoring based in the internet of things. IEEE J Sel Areas Commun. 2013;31(9):47–65.
Gubbi J, Buyya R, Marusic S, Palaniswami M. Internet of things (IoT): a vision, architectural elements, and future directions. Future Gener Comput Syst. 2013;29(7):1645–60.
Sebastian S, Ray PP. Development of IoT invasive architecture for complying with health of home. In: Proc: I3CS, Shillong; 2015. p. 79–83.
Nicolescu R, Huth M, Radanliev P, Roure DD. Mapping the values of IoT. J Inf Technol. 2018;33(4):345–60.
Hu P, Ning H, Qiu T, Xu Y, Luo X, Sangaiah AK. A unified face identification and resolutions scheme using cloud computing in internet of things. Future Gener Comput Syst. 2018;81:582–92.
Babovic ZB, Protic V, Milutinovic V. Web performance evaluation for internet of things applications. IEEE Access. 2016;4:6974–92.
Internet of Things research study: Hewlett Packard Enterprise Report. 2015. http://www8.hp.com/us/en/hp-news/press-release.html?id=1909050#.WPoNH6KxWUk .
Xu LD, He W, Li S. Internet of things in industries: a survey. IEEE Trans Ind Inf. 2014;10(4):2233–43.
Dierks T, Allen C. The TLS protocol version 1.0, IETF RFC, 2246; 1999. https://www.ietf.org/rfc/rfc2246.txt .
Pei M, Cook N, Yoo M, Atyeo A, Tschofenig H. The open trust protocol (OTrP). IETF 2016. https://tools.ietf.org/html/draft-pei-opentrustprotocol-00 .
Roman R, Najera P, Lopez J. Securing the internet of things. Computer. 2011;44(9):51–8.
Van-der-Veer H, Wiles A. Achieving technical, interoperability-the ETSI approach, ETSI White Paper No. 3. 2008. http://www.etsi.org/images/files/ETSIWhitePapers/IOP%20whitepaper%20Edition%203%20final.pdf .
Colacovic A, Hadzialic M. Internet of things (IoT): a review of enabling technologies, challenges and open research issues. Comput Netw. 2018;144:17–39.
Noura M, Atiquazzaman M, Gaedke M. Interoperability in internet of things infrastructure: classification, challenges and future work. In: Third international conference, IoTaaS 2017, Taichung, Taiwan. 20–22 September 2017.
Tzafestad SG. Ethics and law in the internet of things world. Smart Cities. 2018;1(1):98–120.
Mosko M, Solis I, Uzun E, Wood C. CCNx 1.0 protocol architecture. A Xerox company, computing science laboratory PARC; 2017.
Wu Y, Li J, Stankovic J, Whitehouse K, Son S, Kapitanova K. Run time assurance of application-level requirements in wireless sensor networks. In: Proc. 9th ACM/IEEE international conference on information processing in sensor networks, Stockholm, Sweden, 21–16 April 2010. p. 197–208.
Huo L, Wang Z. Service composition instantiation based on cross-modified artificial Bee Colony algorithm. Chin Commun. 2016;13(10):233–44.
White G, Nallur V, Clarke S. Quality of service approaches in IoT: a systematic mapping. J Syst Softw. 2017;132:186–203.
ISO/IEC 25010—Systems and software engineering—systems and software quality requirements and evaluation (SQuaRE)—system and software quality models, Technical Report; 2010.
Oasis. Web services quality factors version 1.0. 2012. http://docs.oasis-open.org/wsqm/wsqf/v1.0/WS-Quality-Factors.pdf .
Fafoutis X, et al. A residential maintenance-free long-term activity monitoring system for healthcare applications. EURASIP J Wireless Commun Netw. 2016. https://doi.org/10.1186/s13638-016-0534-3 .
Park E, Pobil AP, Kwon SJ. The role of internet of things (IoT) in smart cities: technology roadmap-oriented approaches. Sustainability. 2018;10:1388.
Bashir MR, Gill AQ. Towards an IoT big data analytics framework: smart buildings system. In: IEEE 18th international conference on high performance computing and communications; IEEE 14th international conference on smart city; IEEE 2nd international conference on data science and systems; 2016. p. 1325–32.
Lee C, Yeung C, Cheng M. Research on IoT based cyber physical system for industrial big data analytics. In: 2015 IEEE international conference on industrial engineering and engineering management (IEEM). New York: IEEE; 2015. p. 1855–9.
Rizwan P, Suresh K, Babu MR. Real-time smart traffic management system for smart cities by using internet of things and big data. In: International conference on emerging techno-logical trends (ICETT). New York: IEEE; 2016. p. 1–7.
Vuppalapati C, Ilapakurti A, Kedari S. The role of big data in creating sense EHR, an integrated approach to create next generation mobile sensor and wear-able data driven electronic health record (EHR). In: 2016 IEEE second international conference on big data computing service and applications (BigDataService). New York: IEEE; 2016. p. 293–6.
Mourtzis D, Vlachou E, Milas N. Industrial big data as a result of IoT adoption in manufacturing. Procedia CIRP. 2016;55:290–5.
Ramakrishnan R, Gaur L. Smart electricity distribution in residential areas: Internet of things (IoT) based advanced metering infrastructure and cloud analytics. In: International Conference on internet of things and applications (IOTA). New York: IEEE; 2016. p. 46–51.
Mohammadi M, Al-Fuqaha A, Sorour S, Guizani M. Deep learning for IoT big data and streaming analytics: a survey. IEEE Commun Surv Tutor. 2018;20(4):2923–60.
Clausen T, Herberg U, Philipp M. A critical evaluation of the IPv6 routing protocol for low power and lossy networks (RPL). In: 2011 IEEE 7th international conference on wireless and mobile computing, networking and communications (WiMob), Wuhan, China, 10–12 Oct 2011.
Li H, Wang H, Yin W, Li Y, Qian Y, Hu F. Development of remote monitoring system for henhouse based on IoT technology. Future Internet. 2015;7(3):329–41.
Zhang L. An IoT system for environmental monitoring and protecting with heterogeneous communication networks. In: Proc. 2011 6th international ICST conference on communications and networking in China (CHINACOM), Harbin, China, 17–19 Aug 2011. IEEE.
Montori F, Bedogni L, Bononi L. A collaborative internet of things architecture for smart cities and environmental monitoring. IEEE Internet Things J. 2018;5(2):592–605.
Distefano S, Longo F, Scarpa M. QoS assessment of mobile crowd sensing services. J Grid Comput. 2015;13(4):629–50.
Stankovic JA. Research directions for the internet of things. IEEE Internet Things J. 2014;1(1):3–9.
Al-Fuqaha A, Khreishah A, Guizani M, Rayes A, Mohammadi M. Toward better horizontal integration among IoT services. IEEE Commun Mag. 2015;53(9):72–9.
Chen IR, Guo J, Bao F. Trust management for SOA-based IoT and its application to service composition. IEEE Trans Serv Comput. 2016;9(3):482–95.
Sarkar C, et al. DIAT: a scalable distributed architecture for IoT. IEEE Internet Things J. 2014;2(3):230–9.
Chen S, Xu H, Liu D, Hu B, Wang H. A vision of IoT: applications, challenges, and opportunities with China perspective. IEEE Internet Things J. 2014;1(4):349–59.
Kang K, Pang J, Xu LD, Ma L, Wang C. An interactive trust model for application market of the internet of things. IEEE Trans Ind Inf. 2014;10(2):1516–26.
Gupta A, Jha RK. A survey of 5G network: architecture and emerging technologies. IEEE Access. 2015;3:1206–32.
Vlacheas P, et al. Enabling smart cities through a cognitive management framework for the internet of things. IEEE Commun Mag. 2013;51(6):102–11.
Bizanis N, Kuipers FA. SDN and virtualization solutions for the internet of things: a survey. IEEE Access. 2016;4:5591–606.
Zeng X, et al. IOTSim: a simulator for analyzing IoT applications. J Syst Architect. 2017;72:93–107.
Fantacci R, Pecorella T, Viti R, Carlini C. A network architecture solutions for efficient IOT WSN backhauling: challenges and opportunities. IEEE Wirel Commun. 2014;21(4):113–9.
Kim M, Ahn H, Kim KP. Process-aware internet of things: a conceptual extension of the internet of things framework and architecture. KSII Trans Internet Inf Syst. 2016;10(8):4008–22.
Hsieh H-C, Chang K-D, Wang L-F, Chen J-L, Chao H-C. ScriptIoT: a script framework for and internet of things applications. IEEE Internet Things J. 2015;3(4):628–36.
Kiljander J, et al. Semantic interoperability architecture for pervasive computing and internet of things. IEEE Access. 2014;2:856–73.
Ye J, Chen B, Liu Q, Fang Y. A precision agriculture management system based on internet of things and WebGIS. In: Proc. 2013 21st international conference on geoinformatics, Kaifeng, China, 20–22 June 2013. IEEE.
Jara AJ, Martinez-Julia P, Skarmeta A. Light-weight multicast DNS and DNS-SD (ImDNS-SD): IPv6-based resource and service discovery for web of things. In: Proc. sixth international conference on innovative mobile and internet services in ubiquitous computing, Palermo, Italy, 4–6 July 2012.
Diaz M, Martin C, Rubio B. State-of-the-art, challenges, and open issues in the integration of internet of things and cloud computing. J Netw Comput Appl. 2016;67:99–117.
Lo A, Law YW, Jacobsson M. A cellular-centric service architecture for machine to machine (M2M) communications. IEEE Wirel Commun. 2013;20(5):143–51.
Kecskemeti G, Casale G, Jha DN, Lyon J, Ranjan R. Modeling and simulation challenges in internet of things. IEEE Cloud Comput. 2017;4(1):62–9.
Cuomo S, Somma VD, Sica F. An application of the one-factor HullWhite model in an IoT financial scenario. Sustain Cities Soc. 2018;38:18–20.
Liu J, et al. A cooperative evolution for QoS-driven IOT service composition. Autom J Control Meas Electron Comput Commun. 2013;54(4):438–47.
Huo Y, et al. Multi-objective service composition model based on cost-effective optimization. Appl Intell. 2017;48(3):651–69.
Han SN, Crespi N. Semantic service provisioning for smart objects: integrating IoT applications into the web. Future Gener Comput Syst. 2017;76:180–97.
Alodib M. QoS-aware approach to monitor violations of SLAs in the IoT. J Innov Digit Ecosyst. 2016;3(2):197–207.
Rizzardi A, Sicari S, Miorandi D, Coen-Porisini A. AUPS: an open source authenticated publish/subscribe system for internet of things. Inf Syst. 2016;62:29–41.
Fenye B, Ing-Ray C, Jia G. Scalable, adaptive and survivable trust management for community of interest based internet of things systems. In: Proc. IEEE eleventh international symposium on autonomous decentralized systems (ISADS), Mexico City, Mexico, 6–8 March 2013.
Tehrani MN, Uysal M, Yanikomeroglu H. Device to device communication in 5G cellular networks: challenges, solutions, and future directions. IEEE Commun Mag. 2014;52(5):86–92.
Zhu C, Leung VCM, Shu L, Ngai ECH. Green internet of things for smart world. IEEE Access. 2015;3:2151–62.
Adame T, Bel A, Bellalta B, Barcelo J, Oliver M. IEEE 802.11AH: the WiFi approach for M2M communications. IEEE Wirel Commun. 2014;21(6):144–52.
Shaikh FK, Zeadally S, Exposito E. Enabling technologies for green internet of things. IEEE Syst J. 2015;99:1–12.
Palattella MR, et al. Standardized protocol stack for the internet of (important) things. IEEE Commun Surv Tutor. 2012;15(3):1389–406.
Vatari S, Bakshi A, Thakur T. Green house by using IoT and cloud computing. In: Proc. 2016 IEEE international conference on recent trends in electronic, information & communication technology (RTEICT), Bangalore, India, 20–21 May 2016.
Chiang M, Zhang T. Fog and IoT: an overview of research opportunities. IEEE Internet Things J. 2016;3(6):854–64.
Elkhodr M, Shahrestani S, Cheung H. A smart home application based on the internet of things management platform. In: Proc. 2015 IEEE international conference on data science and data intensive systems, Sydney, Australia, 11–13 Dec 2015.
Talari S, et al. A review of smart cities based on the internet of things concept. Energies. 2017;10(4):421–43.
Burange AW, Misalkar HD. Review of internet of things in development of smart cities with data management & privacy. In: Proc. 2015 international conference on advances in computer engineering and applications, Ghaziabad, India, 19–20 March 2015.
Zia T, Liu P, Han W. Application-specific digital forensics investigative model in internet of things (IoT). In: Proc. 12th international conference on availability, reliability and security, Reggio Calabria, Italy; 2017.
Lingling H, Haifeng L, Xu X, Jian L. An intelligent vehicle monitoring system based on internet of things. In: Proc. 7th international conference on computational intelligence and security, Hainan, China, 3–4 Dec 2011. IEEE.
Duttagupta S, Kumar M, Ranjan R, Nambiar M. Performance prediction of IoT application: an experimental analysis. In: Proc. 6th international conference on the internet of things, Stuttgart, Germany, 07–09 Nov 2016. p. 43–51.
Chen S, Liu B, Chen X, Zhang Y, Huang G. Framework for adaptive computation offloading in IoT applications. In: Proc. 9th Asia-Pacific symposium on internetware, Shanghai, China, 23 Sep 2017. ACM.
Li Q, Dou R, Chen F, Nan G. A QoS-oriented web service composition approach based on multi-population genetic algorithm for internet of things. Int J Comput Intell Syst. 2014;7(Sup2):26–34.
Urbieta A, Gonzalez-Beltran A, Mokhtar SB, Hossain MA, Capra L. Adaptive and context-aware service composition for IoT-based smart cities. Future Gener Comput Syst. 2017;76:262–74.
Krishna GG, Krishna G, Bhalaji N. Analysis of routing protocol for low-power and lossy networks in IoT real time applications. Procedia Comput Sci. 2016;87:270–4.
Singh D, Tripathi G, Jara AJ. A survey of internet of things: future vision, architecture, challenge and services. In: Proc. IEEE world forum on internet of things, Seoul, South Korea; 2014. p. 287–92.
Jara AJ, Ladid L, Skarmeta A. The internet of everything through Ipv6: an analysis of challenges, solutions and opportunities. J Wirel Mob Netw Ubiquitous Comput Dependable Appl. 2013;4(3):97–118.
Madsen H, Burtschy B, Albeanu G, Popentiu-Vladicescu Fl. Reliability in the utility computing era: towards reliable Fog computing. In: Proc. 20th international conference on systems, signals, and image processing (IWSSIP); 2013. p. 43–6.
Soret B, Pedersen KI, Jorgensen NTK, Fernandez-Lopez V. Interference coordination for dense wireless networks. IEEE Commun Mag. 2015;53(1):102–9.
Andrews JG. Seven ways that HetNets are a cellular paradigm shift. IEEE Commun Mag. 2013;51(3):136–44.
Jaber M, Imran MA, Tafazolli R, Tukmanov A. 5G Backhaul challenges and emerging research directions: a survey. IEEE Access. 2016;4:1743–66.
Choi S, Koh S-J. Use of proxy mobile IPv6 for mobility management in CoAP-based internet of things networks. IEEE Commun Lett. 2016;20(11):2284–7.
Maier M, Chowdhury M, Rimal BP, Van DP. The tactile internet: vision, recent progress, and open challenges. IEEE Commun Mag. 2016;54(5):138–45.
Fernandes JL, Lopes IC, Rodrigues JJPC, Ullah S. Performance evaluations of RESTful web services and AMQP protocol. In: 5th international conference on ubiquitous and future networks (ICUFN), Da Nang, Vietnam, 2–5 July 2013.
Download references
Acknowledgements
This work was financially supported by the Ministry of Education and Science of Russian Federation (government order 2.7905.2017/8.9).
The research received no external funding.
Author information
Authors and affiliations.
Department of Computer Science, South Ural State University, Chelyabinsk, Russian Federation
Sachin Kumar & Mikhail Zymbler
Department of Information Engineering, University of Padova, Padua, Italy
Prayag Tiwari
You can also search for this author in PubMed Google Scholar
Contributions
SK and PT prepared the draft and Idea. SK wrote the manuscript. MZ prepared the tables, references and checked the English. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Sachin Kumar .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Kumar, S., Tiwari, P. & Zymbler, M. Internet of Things is a revolutionary approach for future technology enhancement: a review. J Big Data 6 , 111 (2019). https://doi.org/10.1186/s40537-019-0268-2
Download citation
Received : 24 July 2019
Accepted : 10 November 2019
Published : 09 December 2019
DOI : https://doi.org/10.1186/s40537-019-0268-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet of Things (IoT)
- IoT architecture
- IoT challenges
- IoT applications
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum
IEEE Internet of Things Journal

Call for Papers
Please prepare your manuscript according to the Guidelines for Authors.
Current and past issues are accessible in IEEE Xplore.
Special Issues
Tiny Machine Learning in Internet of Unmanned Aerial Vehicles Prognostics and Health Management using the Internet of Things Energy Internet: A Cyber-Physical-Social Perspective Data Management and Security in Resource-constrained Intelligent IoT Systems Current Research Trend and Open Challenge for Industrial Internet-of-Things Next Generation Multiple Access for Internet-of-Things Integrated Sensing and Communications (ISAC) for 6G IoE Edge Learning in B5G IoT Systems Integrated Sensing, Computing and Communication for Internet of Robotic Things Efficient, Effective, and Explicable Artificial Intelligence Inspired IoT over Non-Terrestrial Networks Augmented Intelligence of Things for Vehicle Road Cooperation Systems Low-Carbon Sustainable Computing Enabled Artificial Intelligence of Things
Review & Tutorial Papers
Purpose and scope.
The IEEE IoT Journal (IoT-J) , launched in 2014 (“ Genesis of the IoT-J “), publishes papers on the latest advances, as well as review articles, on the various aspects of IoT. Topics include IoT system architecture, IoT enabling technologies, IoT communication and networking protocols, IoT services and applications, and the social implications of IoT. Examples are IoT demands, impacts, and implications on sensors technologies, big data management, and future internet design for various IoT use cases, such as smart cities, smart environments, smart homes, etc. The fields of interest include:
- IoT architectures such as things-centric, data-centric, service-centric architecture, CPS and SCADA platforms, future Internet design for IoT, cloud-based IoT, and system security and manageability.
- IoT enabling technologies such as sensors, radio frequency identification, low power and energy harvesting, sensor networks, machine-type communication, resource-constrained networks, real-time systems, IoT data analytics, in situ processing, and embedded software.
- IoT services, applications, standards, and test-beds such as streaming data management and mining platforms, service middleware, open service platform, semantic service management, security and privacy-preserving protocols, design examples of smart services and applications, and IoT application support.
Editor-in-Chief
Nei Kato, Tohoku University, Japan (Email: [email protected] )
iot applications Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Service Provisioning for Multi-source IoT Applications in Mobile Edge Computing
We are embracing an era of Internet of Things (IoT). The latency brought by unstable wireless networks caused by limited resources of IoT devices seriously impacts the quality of services of users, particularly the service delay they experienced. Mobile Edge Computing (MEC) technology provides promising solutions to delay-sensitive IoT applications, where cloudlets (edge servers) are co-located with wireless access points in the proximity of IoT devices. The service response latency for IoT applications can be significantly shortened due to that their data processing can be performed in a local MEC network. Meanwhile, most IoT applications usually impose Service Function Chain (SFC) enforcement on their data transmission, where each data packet from its source gateway of an IoT device to the destination (a cloudlet) of the IoT application must pass through each Virtual Network Function (VNF) in the SFC in an MEC network. However, little attention has been paid on such a service provisioning of multi-source IoT applications in an MEC network with SFC enforcement. In this article, we study service provisioning in an MEC network for multi-source IoT applications with SFC requirements and aiming at minimizing the cost of such service provisioning, where each IoT application has multiple data streams from different sources to be uploaded to a location (cloudlet) in the MEC network for aggregation, processing, and storage purposes. To this end, we first formulate two novel optimization problems: the cost minimization problem of service provisioning for a single multi-source IoT application, and the service provisioning problem for a set of multi-source IoT applications, respectively, and show that both problems are NP-hard. Second, we propose a service provisioning framework in the MEC network for multi-source IoT applications that consists of uploading stream data from multiple sources of the IoT application to the MEC network, data stream aggregation and routing through the VNF instance placement and sharing, and workload balancing among cloudlets. Third, we devise an efficient algorithm for the cost minimization problem built upon the proposed service provisioning framework, and further extend the solution for the service provisioning problem of a set of multi-source IoT applications. We finally evaluate the performance of the proposed algorithms through experimental simulations. Simulation results demonstrate that the proposed algorithms are promising.
Design and Analysis of a RFID Reader Microstrip Array antenna for IoT Applications in Smart Cities
This paper presents the design of 2*1 and 4*1 RFID reader microstrip array antenna at 2.4GHz for the Internet of things (IoT) networks which are Zigbee, Bluetooth and WIFI. The proposed antenna is composed of identical circular shapes radiating patches printed in FR4 substrate. The dielectric constant εr and substrate thickness h are 4.4 and 1.6mm, respectively. The 2*1 and 4*1 array antennas present a gain improvement of 27.3% and 61.9%, respectively. The single,2*1 and 4*1 array antennas were performed with CADFEKO.
A Survey on Privacy Preservation in Fog-Enabled Internet of Things
Despite the rapid growth and advancement in the Internet of Things (IoT ), there are critical challenges that need to be addressed before the full adoption of the IoT. Data privacy is one of the hurdles towards the adoption of IoT as there might be potential misuse of users’ data and their identity in IoT applications. Several researchers have proposed different approaches to reduce privacy risks. However, most of the existing solutions still suffer from various drawbacks, such as huge bandwidth utilization and network latency, heavyweight cryptosystems, and policies that are applied on sensor devices and in the cloud. To address these issues, fog computing has been introduced for IoT network edges providing low latency, computation, and storage services. In this survey, we comprehensively review and classify privacy requirements for an in-depth understanding of privacy implications in IoT applications. Based on the classification, we highlight ongoing research efforts and limitations of the existing privacy-preservation techniques and map the existing IoT schemes with Fog-enabled IoT schemes to elaborate on the benefits and improvements that Fog-enabled IoT can bring to preserve data privacy in IoT applications. Lastly, we enumerate key research challenges and point out future research directions.
Design and Deployment of Expressive and Correct Web of Things Applications
Consumer Internet of Things (IoT) applications are largely built through end-user programming in the form of event-action rules. Although end-user tools help simplify the building of IoT applications to a large extent, there are still challenges in developing expressive applications in a simple yet correct fashion. In this context, we propose a formal development framework based on the Web of Things specification. An application is defined using a composition language that allows users to compose the basic event-action rules to express complex scenarios. It is transformed into a formal specification that serves as the input for formal analysis, where the application is checked for functional and quantitative properties at design time using model checking techniques. Once the application is validated, it can be deployed and the rules are executed following the composition language semantics. We have implemented these proposals in a tool built on top of the Mozilla WebThings platform. The steps from design to deployment were validated on real-world applications.
Design and Analysis of a RFID Reader Microstrip Array Antenna for IoT Applications in Smart Cities
Blockchain technology - based solutions for iot security.
Blockchain innovation has picked up expanding consideration from investigating and industry over the later a long time. It permits actualizing in its environment the smart-contracts innovation which is utilized to robotize and execute deals between clients. Blockchain is proposed nowadays as the unused specialized foundation for a few sorts of IT applications. Blockchain would aid avoid the duplication of information because it right now does with Bitcoin and other cryptocurrencies. Since of the numerous hundreds of thousands of servers putting away the Bitcoin record, it’s impossible to assault and alter. An aggressor would need to change the record of 51 percent of all the servers, at the precise same time. The budgetary fetched of such an assault would distantly exceed the potential picks up. The same cannot be said for our private data that lives on single servers possessed by Google and Amazon. In this paper, we outline major Blockchain technology that based as solutions for IOT security. We survey and categorize prevalent security issues with respect to IoT data privacy, in expansion to conventions utilized for organizing, communication, and administration. We diagram security necessities for IoT together with the existing scenarios for using blockchain in IoT applications.
Energy-Aware Security Adaptation for Low-Power IoT Applications
The constant evolution in communication infrastructures will enable new Internet of Things (IoT) applications, particularly in areas that, up to today, have been mostly enabled by closed or proprietary technologies. Such applications will be enabled by a myriad of wireless communication technologies designed for all types of IoT devices, among which are the Long-Range Wide-Area Network (LoRaWAN) or other Low-power and Wide-Area Networks (LPWAN) communication technologies. This applies to many critical environments, such as industrial control and healthcare, where wireless communications are yet to be broadly adopted. Two fundamental requirements to effectively support upcoming critical IoT applications are those of energy management and security. We may note that those are, in fact, contradictory goals. On the one hand, many IoT devices depend on the usage of batteries while, on the other hand, adequate security mechanisms need to be in place to protect devices and communications from threats against their stability and security. With thismotivation in mind, we propose a solution to address the management, in tandem, of security and energy in LoRaWAN IoT communication environments. We propose and evaluate an architecture in the context of which adaptation logic is used to manage security and energy dynamically, with the goal of guaranteeing appropriate security, while promoting the lifetime of constrained sensing devices. The proposed solution was implemented and experimentally evaluated and was observed to successfully manage security and energy. Security and energy are managed in line with the requirements of the application at hand, the characteristics of the constrained sensing devices employed and the detection, as well as the threat, of particular types of attacks.
Motivating Users to Manage Privacy Concerns in Cyber-Physical Settings—A Design Science Approach Considering Self-Determination Theory
Connectivity is key to the latest technologies propagating into everyday life. Cyber-Physical Systems (CPS) and Internet-of-Things (IoT) applications enable users, machines, and technologically enriched objects (‘Things’) to sense, communicate, and interact with their environment. Albeit making human beings’ lives more comfortable, these systems collect huge quantities of data that may affect human privacy and their digital sovereignty. Engaging in control over individuals by digital means, the data and the artefacts that process privacy-relevant data can be addressed by Self-Determination Theory (SDT) and its established instruments. In this paper, we discuss how the theory and its methodological knowledge can be considered for user-centric privacy management. We set the stage for studying motivational factors to improve user engagement in identifying privacy needs and preserving privacy when utilizing or aiming to adapt CPS or IoT applications according to their privacy needs. SDT considers user autonomy, self-perceived competence, and social relatedness relevant for human engagement. Embodying these factors into a Design Science-based CPS development framework could help to motivate users to articulate privacy needs and adopt cyber-physical technologies for personal task accomplishment.
Preventing MQTT Vulnerabilities Using IoT-Enabled Intrusion Detection System
The advancement in the domain of IoT accelerated the development of new communication technologies such as the Message Queuing Telemetry Transport (MQTT) protocol. Although MQTT servers/brokers are considered the main component of all MQTT-based IoT applications, their openness makes them vulnerable to potential cyber-attacks such as DoS, DDoS, or buffer overflow. As a result of this, an efficient intrusion detection system for MQTT-based applications is still a missing piece of the IoT security context. Unfortunately, existing IDSs do not provide IoT communication protocol support such as MQTT or CoAP to validate crafted or malformed packets for protecting the protocol implementation vulnerabilities of IoT devices. In this paper, we have designed and developed an MQTT parsing engine that can be integrated with network-based IDS as an initial layer for extensive checking against IoT protocol vulnerabilities and improper usage through a rigorous validation of packet fields during the packet-parsing stage. In addition, we evaluate the performance of the proposed solution across different reported vulnerabilities. The experimental results demonstrate the effectiveness of the proposed solution for detecting and preventing the exploitation of vulnerabilities on IoT protocols.
Proposed RPL routing protocol in the IoT applications
Export citation format, share document.
Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity
- Open access
- Published: 24 February 2021
- Volume 1 , article number 7 , ( 2021 )
Cite this article
You have full access to this open access article
- Murat Kuzlu 1 ,
- Corinne Fair 2 &
- Ozgur Guler 3
45k Accesses
87 Citations
21 Altmetric
Explore all metrics
In recent years, the use of the Internet of Things (IoT) has increased exponentially, and cybersecurity concerns have increased along with it. On the cutting edge of cybersecurity is Artificial Intelligence (AI), which is used for the development of complex algorithms to protect networks and systems, including IoT systems. However, cyber-attackers have figured out how to exploit AI and have even begun to use adversarial AI in order to carry out cybersecurity attacks. This review paper compiles information from several other surveys and research papers regarding IoT, AI, and attacks with and against AI and explores the relationship between these three topics with the purpose of comprehensively presenting and summarizing relevant literature in these fields.
Similar content being viewed by others

AI-Driven Cybersecurity: An Overview, Security Intelligence Modeling and Research Directions
Iqbal H. Sarker, Md Hasan Furhad & Raza Nowrozy

RETRACTED ARTICLE: A Review and State of Art of Internet of Things (IoT)
Asif Ali Laghari, Kaishan Wu, … Abdullah Ayub Khan

Cyber Security Threats and Vulnerabilities: A Systematic Mapping Study
Mamoona Humayun, Mahmood Niazi, … Sajjad Mahmood
Avoid common mistakes on your manuscript.
1 Introduction
Since around 2008, when the Internet of Things (IoT) was born [ 1 ], its growth has been booming, and now IoT is a part of daily life and has a place in many homes and businesses. IoT is hard to define as it has been evolving and changing since its conception, but it can be best understood as a network of digital and analog machines and computing devices provided with unique identifiers (UIDs) that have the ability to exchange data without human intervention [ 2 ]. In most cases, this manifests as a human interfacing with a central hub device or application, often a mobile app, that then goes on to send data and instructions to one or multiple fringe IoT devices [ 3 ]. The fringe devices are able to complete functions if required and send data back to the hub device or application, which the human can then view.
The IoT concept has given the world a higher level of accessibility, integrity, availability, scalability, confidentiality, and interoperability in terms of device connectivity [ 4 ]. However, IoTs are vulnerable to cyberattacks due to a combination of their multiple attack surfaces and their newness and thus lack of security standardizations and requirements [ 5 ]. There are a large variety of cyberattacks that attackers can leverage against IoTs, depending on what aspect of the system they are targeting and what they hope to gain from the attack. As such, there is a large volume of research into cybersecurity surrounding IoT. This includes Artificial Intelligence (AI) approaches to protecting IoT systems from attackers, usually in terms of detecting unusual behavior that may indicate an attack is occurring [ 6 ]. However, in the case of IoT, cyber-attackers always have the upper hand as they only need to find one vulnerability while cybersecurity experts must protect multiple targets. This has led to increased use of AI by cyber-attackers as well, in order to thwart the complicated algorithms that detect anomalous activity and pass by unnoticed [ 7 ]. AI has received much attention with the growth of IoT technologies. With this growth, AI technologies, such as decision trees, linear regression, machine learning, support vector machines, and neural networks, have been used in IoT cybersecurity applications to able to identify threats and potential attacks.
Authors in [ 8 ] provide a comprehensive review of the security risks related to IoT application and possible counteractions as well as compare IoT technologies in terms of integrity, anonymity, confidentiality, privacy, access control, authentication, authorization, resilience, and self-organization. The authors propose deep learning models using CICIDS2017 datasets for DDoS attack detection for the cybersecurity in IoT (Internet of Things), which provide high accuracy, i.e., 97.16% [ 9 ]. In [ 10 ], the authors evaluate the Artificial Neural Networks (ANN) in a gateway device to able to detect anomalies in the data sent from the edge devices. The results show that the proposed approach can improve the security of IoT systems. The authors in [ 11 ] propose an AI-based control approach for detection and estimation as well as compensation of cyber attacks in industrial IoT systems. In [ 12 ], The authors provide a robust pervasive detection for IoT Environments and develop a variety of adversarial attacks and defense mechanisms against them as well as validate their approach through datasets including MNIST, CIFAR-10, and SVHN. In [ 13 ], the authors analyze the recent evolution of AI decision-making in cyber physical systems and find that such evolution is virtually autonomous due to the increasing integration of IoT devices in cyber physical systems, and the value of AI decision-making due to its speed and efficiency in handling large loads of data is likely going to make this evolution inevitable. The authors of [ 14 ] discuss new approaches to risk analytics using AI and machine learning, particularly in IoT networks present in industry settings. Finally, [ 15 ] discusses methods of capturing and assessing cybersecurity risks to IoT devices for the purpose of standardizing such practices so that risk in IoT systems may be more efficiently identified and protected against.
This review paper covers a variety of topics regarding cybersecurity, the Internet of Things (IoT), Artificial Intelligence (AI), and how they all relate to each other in three survey-style sections and provides a comprehensive review of cyberattacks against IoT devices as well as provides recommended AI-based methods of protecting against these attacks. The ultimate goal of this paper is to create a resource for others who are researching these prevalent topics by presenting summaries of and making connections between relevant works covering different aspects of these subjects.
2 Methods of attacking IoT devices
Due to the lax security in many IoT devices, cyberattackers have found many ways to attack IoT devices from many different attack surfaces. Attack surfaces can vary from the IoT device itself, both its hardware and software, the network on which the IoT device is connected to, and the application with which the device interfaces; these are the three most commonly used attack surfaces as together they make up the main parts of an IoT system. Figure 1 illustrates a basic breakdown of a common IoT system; most of the attacks discussed in this paper occur at the network gateway and/or cloud data server connections, as these connections are generally where IoT security is most lacking.
A high-level breakdown of typical IoT structure
2.1 Initial reconnaissance
Before IoT attackers even attempt cyberattacks on an IoT device, they will often study the device to identify vulnerabilities. This is often done by buying a copy of the IoT device they are targeting from the market. They then reverse engineer the device to create a test attack to see what outputs can be obtained and what avenues exist to attack the device. Examples of this include opening up the device and analyzing the internal hardware—such as the flash memory—in order to learn about the software, and tampering with the microcontroller to identify sensitive information or cause unintended behavior [ 16 ]. In order to counter reverse engineering, it is important for IoT devices to have hardware-based security. The application processor, which consists of sensors, actuators, power supply, and connectivity, should be placed in a tamper-resistant environment [ 16 ]. Device authentication can also be done with hardware-based security, such that the device can prove to the server it is connected to that it is not fake.
2.2 Physical attacks
An often low-tech type category of attacks includes physical attacks, in which the hardware of the target device is used to the benefit of the attacker in some way. There are several different types of physical attacks. These include attacks such as outage attacks, where the network that the devices are connected to are shut off to disrupt their functions; physical damage, where devices or their components are damaged to prevent proper functionality; malicious code injection, an example of which includes an attacker plugging a USB containing a virus into the target device; and object jamming, in which signal jammers are used to block or manipulate the signals put out by the devices [ 17 ]. Permanent denial of service (PDoS) attacks, which are discussed later in this paper, can be carried out as a physical attack; if an IoT device is connected to a high voltage power source, for example, its power system may become overloaded and would then require replacement [ 18 ].
2.3 Man-in-the-Middle
One of the most popular attacks on IoTs is Man-in-the-Middle (MITM) attack. With regards to computers in general, an MITM attack intercepts communication between two nodes and allows the attacker to take the role of a proxy. Attackers can perform MITM attacks between many different connections such as a computer and a router, two cell phones, and, most commonly, a server and a client. Figure 2 shows a basic example of an MITM attack between a client and a server. In regards to IoT, the attacker usually performs MITM attacks between an IoT device and the application with which it interfaces. IoT devices, in particular, tend to be more vulnerable to MITM attacks as they lack the standard implementations to fight the attacks. There are two common modes of MITM attacks: cloud polling and direct connection. In cloud polling, the smart home device is in constant communication with the cloud, usually to look for firmware updates. Attackers can redirect network traffic using Address Resolution Protocol (ARP) poisoning or by altering Domain Name System (DNS) settings or intercept HTTPS traffic by using self-signed certificates or tools such as (Secure Sockets Layer) SSL strip [ 19 ]. Many IoT devices do not verify the authenticity or the trust level of certificates, making the self-signed certificate method particularly effective. In the case of direct connections, devices communicate with a hub or application in the same network. By doing this, mobile apps can locate new devices by probing every IP address on the local network for a specific port. An attacker can do the same thing to discover devices on the network [ 19 ]. An example of an MITM IoT attack is that of a smart refrigerator that could display the user’s Google calendar. It seems like a harmless feature, but attackers found that the system did not validate SSL certificates, which allowed them to perform an MITM attack and steal the user’s Google credentials [ 19 ].

A simple representation of a Man-in-the-Middle attack
2.3.1 Bluetooth Man-in-the-Middle
A common form of MITM attack leveraged against IoT devices is via Bluetooth connection. Many IoT devices run Bluetooth Low Energy (BLE), which is designed with IoT devices in mind to be smaller, cheaper, and more power-efficient [ 20 ]. However, BLE is vulnerable to MITM attacks. BLE uses AES-CCM encryption; AES encryption is considered secure, but the way that the encryption keys are exchanged is often insecure. The level of security relies on the pairing method used to exchange temporary keys between the devices. BLE specifically uses three-phase pairing processes: first, the initiating device sends a pairing request, and the devices exchange pairing capabilities over an insecure channel; second, the devices exchange temporary keys and verify that they are using the same temporary key, which is then used to generate a short-term key (some newer devices use a long-term key exchanged using Elliptic Curve Diffie-Hellman public-key cryptography, which is significantly more secure than the standard BLE protocol); third, the created key is exchanged over a secure connection and can be used to encrypt data [ 20 ]. Figure 3 represents this three-phase pairing process.
A diagram illustrating the basic BLE pairing process
The temporary key is determined according to the pairing method, which is determined on the OS level of the device. There are three common pairing methods popular with IoT devices. One, called Just Works, always sets the temporary key to 0, which is obviously very insecure. However, it remains one of if not the most popular pairing methods used with BLE devices [ 20 ]. The second, Passkey, uses six-digit number combinations, which the user must manually enter into a device, which is fairly secure, though there are methods of bypassing this [ 20 ]. Finally, the Out-of-Band pairing method exchanges temporary keys using methods such as Near Field Communication. The security level of this method is determined by the security capabilities of the exchange method. If the exchange channel is protected from MITM attacks, the BLE connection can also be considered protected. Unfortunately, the Out-of-Band method is not yet common in IoT devices [ 20 ]. Another important feature of BLE devices is the Generic Attribute Profile (GATT), which is used to communicate between devices using a standardized data schema. The GATT describes devices’ roles, general behaviors, and other metadata. Any BLE-supported app within the range of an IoT device can read its GATT schema, which provides the app with necessary information [ 20 ]. In order for attackers to perform MITM attacks in BLE networks, the attacker must use two connected BLE devices himself: one device acting as the IoT device to connect to the target mobile app, and a fake mobile app to connect to the target IoT device. Some other tools for BLE MITM attacks exist, such as GATTacker, a Node.js package that scans and copies BLE signals and then runs a cloned version of the IoT device, and BtleJuice, which allows MITM attacks on Bluetooth Smart devices which have improved security over BLE [ 20 ].
2.3.2 False data injection attacks
Once an attacker has access to some or all of the devices on an IoT network via an MITM attack, one example of an attack they could carry out next is a False Data Injection (FDI) attack. FDI attacks are when an attacker alters measurements from IoT sensors by a small amount so as to avoid suspicion and then outputs the faulty data [ 21 ]. FDI attacks can be perpetrated in a number of ways, but in practice doing so via MITM attacks is the most practical. FDI attacks are often leveraged against sensors that send data to an algorithm that attempts to make predictions based on the data it has received or otherwise uses data to make conclusions. These algorithms, sometimes referred to as predictive maintenance systems, are commonly used in monitoring the state of a mechanical machine and predicting when it will need to be maintained or tuned [ 21 ]. These predictive maintenance algorithms and similar would also be a staple feature of smart cities, FDI attacks against which could be disastrous. An example of an FDI attack on a predictive maintenance system is sensors on an airplane engine that predict when the engine will need critical maintenance. When attackers are able to access even a small portion of the sensors, they are able to create a small amount of noise that goes undetected by faulty data detection mechanisms but is just enough to skew the algorithm’s predictions [ 21 ]. In testing, it would even be enough to delay critical maintenance to the system, potentially causing catastrophic failure while in use, which could cause a costly unplanned delay or loss of life.
2.4 Botnets
Another kind of common attack on IoT devices is recruiting many devices to create botnets and launch Distributed Denial of Service (DDoS) attacks. A denial of service (DoS) attack is characterized by an orchestrated effort to prevent legitimate use of a service; a DDoS attack uses attacks from multiple entities to achieve this goal. DDoS attacks aim to overwhelm the infrastructure of the target service and disrupt normal data flow. DDoS attacks generally go through a few phases: recruitment, in which the attacker scans for vulnerable machines to be used in the DDoS attack against the target; exploitation and infection, in which the vulnerable machines are exploited, and malicious code is injected; communication, in which the attacker assesses the infected machines, sees which are online and decides when to schedule attacks or upgrade the machines; and attack, in which the attacker commands the infected machines to send malicious packets to the target [ 22 ]. One of the most popular ways to gain infected machines and conduct DDoS attacks is through IoT devices due to their high availability and generally poor security and maintenance. Figure 4 shows a common command structure, in which the attacker’s master computer sends commands to one or more infected command and control centers, who each control a series of zombie devices that can then attack the target.
A graphical representation of a common botnet hierarchy
One of the most famous malware, the Mirai worm, has been used to perpetrate some of the largest DDoS attacks ever known and is designed to infect and control IoT devices such as DVRs, CCTV cameras, and home routers. The infected devices become part of a large-scale botnet and can perpetrate several types of DDoS attacks. Mirai was built to handle multiple different CPU architectures that are popular to use in IoT devices, such as x86, ARM, Sparc, PowerPC, Motorola, etc., in order to capture as many devices as possible [ 23 ]. In order to be covert, the virus is quite small and actually does not reside in the device’s hard disk. It stays in memory, which means that once the device is rebooted, the virus is lost. However, devices that have been infected once are susceptible to reinfection due to having already been discovered as being vulnerable, and reinfection can take as little as a few minutes [ 23 ]. Today, many well-known IoT-targeting botnet viruses are derived from Mirai’s source code, including Okiru, Satori, and Reaper [ 23 ].
2.5 Denial of service attacks
IoT devices may often carry out DoS attacks, but they themselves are susceptible to them as well. IoT devices are particularly susceptible to permanent denial of service (PDoS) attacks that render a device or system completely inoperable. This can be done by overloading the battery or power systems or, more popularly, firmware attacks. In a firmware attack, the attacker may use vulnerabilities to replace a device’s basic software (usually its operating system) with a corrupted or defective version of the software, rendering it useless [ 18 ]. This process, when done legitimately, is known as flashing, and its illegitimate counterpart is known as “phlashing”. When a device is phlashed, the owner of the device has no choice but to flash the device with a clean copy of the OS and any content that might’ve been put on the device. In a particularly powerful attack, the corrupted software could overwork the hardware of the device such that recovery is impossible without replacing parts of the device [ 18 ]. The attacks to the device’s power system, though less popular, are possibly even more devastating. One example of this type of attack is a USB device with malware loaded on it that, when plugged into a computer, overuses the device’s power to the point that the hardware of the device is rendered completely ruined and needs to be replaced [ 18 ].
One example of PDoS malware is known as BrickerBot. BrickerBot uses brute force dictionary attacks to gain access to IoT devices and, once logged in to the device, runs a series of commands that result in permanent damage to the device. These commands include misconfiguring the device’s storage and kernel parameters, hindering internet connection, sabotaging device performance, and wiping all files on the device [ 24 ]. This attack is devastating enough that it often requires reinstallation of hardware or complete replacement of the device. If the hardware survives the attack, the software certainly didn’t and would need reflashing, which would lose everything that might have been on it. Interestingly enough, BrickerBot was designed to target the same devices the Mirai botnet targets and would employ as bots, and uses the same or a similar dictionary to make its brute force attacks. As it turns out, BrickerBot was actually intended to render useless those devices that Mirai would have been able to recruit in an effort to fight back against the botnet [ 24 ].
Due to the structure of IoT systems, there are multiple attack surfaces, but the most popular way of attacking IoT systems is through their connections as these tend to be the weakest links. In the future, it is advisable that IoT developers ensure that their products have strong protections against such attacks, and the introduction of IoT security standards would prevent users from unknowingly purchasing products that are insecure. Alternatively, keeping the network that the IoT system resides on secure will help prevent many popular attacks, and keeping the system largely separated from other critical systems or having backup measures will help mitigate the damage done should an attack be carried out.
3 Artificial Intelligence in cybersecurity
In order to dynamically protect systems from cyber threats, many cybersecurity experts are turning to Artificial Intelligence (AI). AI is most commonly used for intrusion detection in cybersecurity by analyzing traffic patterns and looking for an activity that is characteristic of an attack.
3.1 Machine learning
There are two main kinds of machine learning: supervised and unsupervised learning. Supervised learning is when humans manually label training data as malicious or legitimate and then input that data into the algorithm to create a model that has “classes” of data that it compares the traffic it is analyzing. Unsupervised learning forgoes training data and manual labeling, and instead the algorithm groups together similar pieces of data into classes and then classifies them according to the data coherence within one class and the data modularity between classes [ 25 ]. One popular machine learning algorithm for cybersecurity is naïve Bayes, which seeks to classify data based on the Bayesian theorem wherein anomalous activities are all assumed to originate from independent events instead of one attack. Naïve Bayes is a supervised learning algorithm, and once it is trained and has generated its classes will analyze each activity to determine the probability that it is anomalous [ 25 ]. Machine learning algorithms can also be used to create the other models discussed in this section
3.2 Decision trees
A decision tree is a type of AI that creates a set of rules based on its training data samples. It uses iterative division to find a description (often simply “attack” or “normal”) that best categorizes the traffic it is analyzing. An example of this approach in cybersecurity is detecting DoS attacks by analyzing the flow rate, size, and duration of traffic. For example, if the flow rate is low, but the duration of the traffic is long, it is likely to be an attack and will, therefore, be classified as such [ 25 ]. Decision trees can also be used to detect command injection attacks in robotic vehicles by categorizing values from CPU consumption, network flow, and volume of data written [ 25 ] as shown in Fig. 5 . This technique is popular as it is intuitive in that what the AI does and doesn’t consider anomalous traffic is known to the developer. Additionally, once an effective series of rules is found, the AI can analyze traffic in real-time, providing an almost immediate alert if unusual activity is detected.
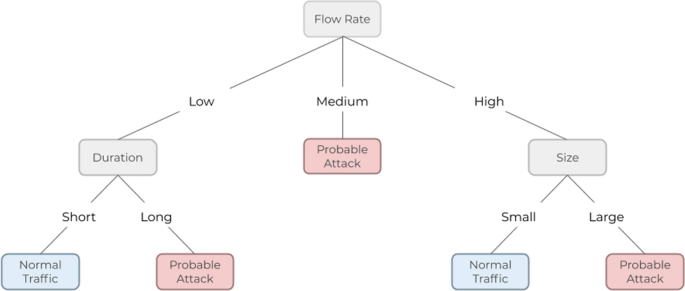
An example of a decision tree for classifying network traffic
Another approach to decision trees is the Rule-Learning technique, which searches for a set of attack characteristics in each iteration while maximizing some score that denotes the quality of the classification (i.e., the number of incorrectly classified data samples) [ 25 ]. The main difference between traditional decision trees and the rule-learning techniques is that traditional decision trees look for characteristics that will lead to a classification, whereas the rule-learning technique finds a complete set of rules that can describe a class. This can be an advantage as it can factor in human advice when generating rules, which creates an optimized set of rules [ 25 ].
3.3 K-nearest neighbors
The k-nearest neighbor (k-NN) technique learns from data samples to create classes by analyzing the Euclidean distance between a new piece of data and already classified pieces of data to decide what class the new piece should be put in, to put it simply [ 25 ]. For example, the new piece of data when k, the number of nearest neighbors, equals three (3) would be classified into class two (2), but when k equals nine (9), the new piece would be classified in class 1 as shown in Fig. 6 . The k-NN technique is attractive for intrusion detection systems as it can quickly learn from new traffic patterns to notice previously unseen, even zero-day attacks. Cybersecurity experts are also researching applications of k-NN for real-time detection of cyberattacks [ 25 ]. The technique has been employed to detect attacks such as false data injection attacks and performs well when data can be represented through a model that allows the measurement of their distance to other data, i.e., through a Gaussian distribution or a vector.

How k-NN technique can classify a data point differently given different k values
3.4 Support vector machines
Support vector machines (SVMs) are an extension of linear regression models that locates a plane that separates data into two classes [ 25 ]. This plane can be linear, non-linear, polynomial, Gaussian, sigmoid, etc., depending on the function used in the algorithm. SVMs can also separate data into more than two classes by using more than one plane. In cybersecurity, this technique is used to analyze Internet traffic patterns and separate them into their component classes such as HTTP, FTP, SMTP, and so on [ 25 ]. As SVM is a supervised machine learning technique, it is often used in applications where attacks can be simulated, such as using network traffic generated from penetration testing as training data.
3.5 Artificial neural networks
Artificial neural networks (ANNs) are a technique derived from the way that neurons interact with each other in the brain in order to pass and interpret information. In ANNs, a neuron is a mathematical equation that reads data and outputs a target value, which is then passed along to the next neuron based on its value. The ANN algorithm then iterates until the output value is acceptably close to the target value, which allows the neurons to learn and correct their weights by measuring the error between the expected value and the previous output value. Once this process is finished, the algorithm presents a mathematical equation that outputs a value that can be used to classify the data [ 25 ].
A large benefit of ANNs is that they are able to adjust their mathematical models when presented with new information, whereas other mathematical models may become obsolete as new types of traffic and attacks become common [ 25 ]. This also means that ANNs are adept at catching previously unseen and zero-day attacks as they take new information into heavier consideration than static mathematical models can. Because of this, ANNs make solid intrusion detection systems and have performed well with attacks such as DoS [ 25 ].
At present, using AI in cybersecurity is a small but rapidly growing field. It is also expensive and resource intensive, so using AI to protect a small system may not be feasible. However, businesses that have large networks may benefit from these solutions, especially if they are considering or have already introduced IoT devices into their network. AI cybersecurity would also be beneficial in the massive systems one would find in a smart city, and the AI would be able to give very quick response times that are important in systems like traffic management. In the future, AI cybersecurity could also be integrated into smaller systems such as self-driving cars or smart homes. Additionally, many AI cybersecurity measures detect or thwart attacks in progress rather than preventing attacks in the first place, meaning that other preventative security measured should also be in place.
4 AI to attack IoT
Not all AI is used for the purposes of cybersecurity; cybercriminals have begun using malicious AI to aid attacks, often to thwart the intrusion detection algorithms in the case of IoT, or attacking beneficial AI in such a way that the AI works against its own system.
4.1 Automation of vulnerability detection
Machine learning can be used to discover vulnerabilities in a system. While this can be useful for those trying to secure a system to intelligently search for vulnerabilities that need to be patched, attackers also use this technology to locate and exploit vulnerabilities in their target system. As technology soars in usage, especially technologies with low-security standards such as IoT devices, the number of vulnerabilities that attackers are able to exploit has soared as well, including zero-day vulnerabilities. In order to identify vulnerabilities quickly, attackers often use AI to discover vulnerabilities and exploit them much more quickly than developers can fix them. Developers are able to use these detection tools as well, but it should be noted that developers are at a disadvantage when it comes to securing a system or device; they must find and correct every single vulnerability that could potentially exist, while attackers need only find one, making automatic detection a valuable tool for attackers.
4.1.1 Fuzzing
Fuzzing, at its core, is a testing method that generates random inputs (i.e., numbers, chars, metadata, binary, and especially “known-to-be-dangerous” values such as zero, negative or very large numbers, SQL requests, special characters) that causes the target software to crash [ 26 ]. It can be divided into dumb fuzzing and smart fuzzing. Dumb fuzzing simply generates defects by randomly changing the input variables; this is very fast as changing the input variable is simple, but it is not very good at finding defects as code coverage is narrow [ 26 ]. Smart fuzzing, on the other hand, generates input values suitable for the target software based on the software’s format and error generation. This software analysis is a big advantage for smart fuzzing as it allows the fuzzing algorithm to know where errors can occur; however, developing an efficient smart fuzzing algorithm takes expert knowledge and tuning [ 26 ].
4.1.2 Symbolic execution
Symbolic execution is a technique similar to fuzzing that searches for vulnerabilities by setting input variables to a symbol instead of a real value [ 26 ]. This technique is often split into offline and online symbolic execution. Offline symbolic execution chooses only one path to explore at a time to create new input variables by resolving the path predicate [ 26 ]. This means that each time one wishes to explore a new path, the algorithm must be run from the beginning, which is a disadvantage due to the large amount of overhead due to code re-execution. Online symbolic execution replicates states and generates path predicates at every branch statement [ 26 ]. This method does not incur much overhead, but it does require a large amount of storage to store all the status information and simultaneous processing of all the states it creates, leading to significant resource consumption.
4.2 Input attacks
When an attacker alters the input of an AI system in such a way that causes the AI to malfunction or give an incorrect output, it is known as an input attack. Input attacks are carried out by adding an attack pattern to the input, which can be anything from putting tape on a physical stop sign to confuse self-driving cars to adding small amounts of noise to an image that is imperceptible to the human eye but will confuse an AI [ 27 ]. Notably, the actual algorithm and security of the AI does not need to be compromised in order to carry out an input attack—only the input that the attacker wants to compromise the output of must be altered. In the case of tape on a stop sign, the attacker may not need to use technology at all. However, more sophisticated attacks are completely hidden from the human eye, wherein the attacker may alter a tiny part of the image in a very precise manner that is designed to misdirect the algorithm. That being said, input attacks are often categorized based on where they rest on two axes: perceivability and format.
The perceivability of an input attack is the measure of how noticeable the attack is to the human eye, while the format is the measure of how digital versus physical the attack is [ 27 ]. On one end of the perceivability axis is perceivable attacks. Altering targets, such as by deforming, removing part of, or changing its colors, and adding to the target, such as affixing physical tape or adding digital marks, are types of perceivable attacks [ 27 ]. While perceivable attacks are perceivable by humans, humans may not notice slight changes like tape on a stop sign or consider them important. A human driver still sees a stop sign with tape or scratches as a stop sign, even though a self-driving car may not. This lends itself to the effectiveness of perceivable attacks, allowing them to, in many cases, hide in plain sight. Conversely, imperceivable attacks are invisible to the human eye. This can include things such as “digital dust,” which is a small amount of noise added to the entire image that is not visible to the human eye but significant enough to an AI to change its output or an imperceptible pattern on a 3D printed object that can be picked up by AI [ 27 ]. Imperceivable attacks can also be made through audio, such as playing audio at ranges outside of the human hearing range that would be picked up by a microphone [ 27 ]. Imperceivable attacks are generally more of a security risk, as there is almost no chance that a human would notice the attack before the AI algorithm outputs an incorrect response.
The format of an attack is usually either digital or physical, without many attacks that are a combination of both [ 27 ]. In many cases of physical attacks, the attack pattern must be more obvious rather than imperceivable as physical objects must be digitized to be processed and, in that process, may lose some finer detail [ 27 ]. Some attacks are still difficult to perceive even with the detail loss, however, as with the case of 3D printed objects with a pattern that blends into the structure of the object such that it is imperceptible to humans [ 27 ]. Opposite of physical attacks are digital attacks, which attack digital inputs such as images, videos, audio recordings, and files. As these inputs are already digitized, there is no process wherein detail is lost, and as such attackers can make very exact attacks, allowing them to be more imperceptible to the human eye than physical attacks [ 27 ]. Digital attacks are not necessarily imperceptible. However—photoshopping glasses with a strange pattern over a celebrity, for example, may cause the AI to identify the image as a different person, but still a person nonetheless. An example of input attacks specific to IoT smart cars and, more broadly, smart cities. As mentioned earlier, simply placing pieces of tape in a specific way on a stop sign is enough for an algorithm to not recognize the stop sign or even classify it as a green light—this is harmful for passengers in the car if the car does not heed the stop sign, and at a larger scale could alter traffic pattern detectors in smart cities. Additionally, noise-based input attacks could cause smart assistants to malfunction and carry out unintended commands.
4.3 Data poisoning/false data injection
Data poisoning attacks and input attacks are very similar, but while the goal of input attacks is simply to alter the output of the affected input, the goal of data poisoning is to alter inputs over a long enough period of time that the AI that analyzes data has shifted and is inherently flawed; because of this, data poisoning is usually carried out while the AI is still being trained before it is actually deployed [ 27 ]. In many cases, the AI learns to fail on specific inputs that the attacker chooses; for example, if a military uses AI to detect aircraft, the enemy military may poison the AI so that it does not recognize certain types of aircraft like drones [ 27 ]. Data poisoning can also be used on AIs that are constantly learning and analyzing data in order to make and adjust predictions, such as in predictive maintenance systems. There are three main methods attackers can use to poison an AI.
4.3.1 Dataset poisoning
Poisoning the dataset of an AI is perhaps the most direct method of data poisoning—as AI gain all of their knowledge from the training datasets they are provided, any flaws within those datasets will subsequently flaw the AI’s knowledge. A basic example of this is shown in Fig. 7 : a significant portion of the data is corrupted in the second dataset, leading the resultant machine learning model to be flawed. Dataset poisoning is done by including incorrect or mislabeled information in the target dataset [ 27 ]. As AI learn by recognizing patterns in datasets, poisoned datasets break patterns or may introduce new incorrect patterns, causing the AI to misidentify inputs or identify them incorrectly [ 27 ]. Many datasets are very large, so finding poisoned data within datasets can be difficult. Continuing the example of traffic patterns, an attacker could change dataset labels in such a way that the AI no longer recognizes stop signs or add data and labels that cause the AI to classify a red light as a green light.
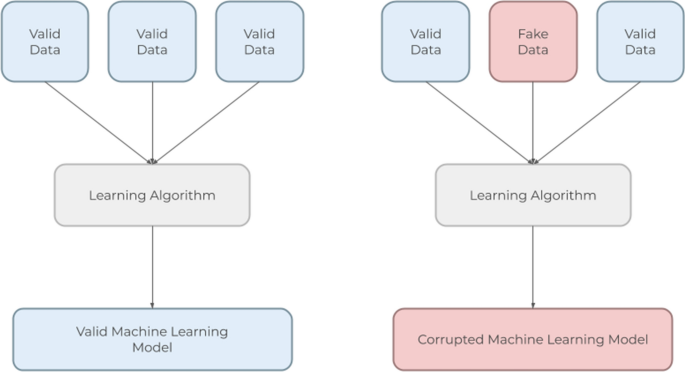
A visual representation of dataset poisoning
4.3.2 Algorithm poisoning
Algorithm poisoning attacks take advantage of weaknesses that may be in the learning algorithm of the AI. This method of attack is very prominent in federated learning, which is a method of training machine learning while protecting data privacy of an individual. Federated learning, rather than collecting potentially sensitive data from users and combining it into one dataset, trains small models directly on users’ devices and then combines these models to form the final model. The users’ data never leaves their devices, and so is more secure; however, if an attacker is one of the users that the algorithm is using the data of, they are free to manipulate their own data in order to poison the model [ 27 ]. The poisoned algorithm, when combined with the rest of the algorithms, has the potential to poison the final model. They could degrade the model or even install a backdoor in this manner.
One example of federated learning is Google’s Gboard, which used federated learning to learn about text patterns in order to train predictive keyboards [ 28 ]. Although Google has extensive data vetting measures, in a less careful approach, users could potentially type nonsensical messages to confuse the predictive text or, more sinisterly, inject code into the algorithm to give themselves a backdoor. Similarly, some cutting-edge IoT devices are beginning to employ federated learning in order to learn from each other. One example of this is using machine learning to predict air pressure changes as it flows through gradually clogging filters, allowing the IoT sensor to predict when the filter will need to be changed [ 29 ]. This learning process would take a long enough time to make the study infeasible with just a few filters, but with federated learning the process is able to be sped up significantly. However, users could easily manipulate the process with their own filters in order to poison the algorithm. Although this is a relatively innocent example of algorithm poisoning, as federated learning increases in IoT, so will the potentially harmful applications of federated learning.
4.3.3 Model poisoning
Finally, some attackers simply replace a legitimate model with an already poisoned model prepared ahead of time; all the attacker has to do is get into the system which stores the model and replace the file [ 27 ]. Alternatively, the equations and data within the trained model file could be altered. This method is potentially dangerous as even if a model trained model is double-checked and data is verified to be not poisoned, the attacker can still alter the model at various points in its distribution, such as while the model is still in company’s network awaiting placement on an IoT device or on an individual IoT device once it has been distributed [ 27 ].
Many of the attacks as described above can be mitigated or prevented by properly sanitizing inputs and checking for unusual data. However, some attacks are subtle and can bypass the notice of humans and even other AI, especially when the attacks are created by malevolent AI systems. These attacks and how to defend against effectively them are at the forefront of current research as the popularity of these attacks grow, but at present many attacks do not use AI for the same reason that many security systems do not: AI is resource intensive and a good algorithm requires high-level knowledge to build, making it inaccessible and infeasible to many attackers.
5 Summary of attacks and their defenses
The various attacks discussed in this paper are listed in Table 1 , and are paired with one or more ways of protecting an IoT system from the attack. While comprehensively protecting an IoT system can be a challenging task due to the number of attack surfaces present, many of the methods listed will defend against many types of attacks; for example, as many of the attacks listed are carried out by first conducting MITM attacks, protecting the network on which an IoT system resides will protect the system from many common attacks.
6 Conclusion
Due to the nature of IoT systems to have many attack surfaces, there exists a variety of attacks against these systems, and more are being discovered as IoT grows in popularity. It is necessary to protect systems against these attacks as effectively as possible. As the number and speed of attacks grow, experts are turning to AI as a means of protecting these systems intelligently and in real-time. Of course, attackers find ways to thwart these AI and may even use AI to attack systems. This paper explores popular techniques to attempt to disrupt or compromise IoT and explains at a surface level how these attacks are carried out. Where applicable, examples are also provided in order to clarify these explanations. Next, several AI algorithms are introduced, and their applications in cybersecurity are investigated. In many cases, these models are not yet common in commercial applications but rather are still undergoing research and development or are still difficult to implement and thus rare. Nonetheless, the models discussed are promising and may become common attack detection systems within just a couple of years. Methods of attacking AI and using AI to attack are also discussed, with the frame of IoT systems. The growth of IoT systems will see these types of attacks become more and more of a threat, especially as massive networks such as smart cities begin experimentation; both as massive networks are harder to protect with a multitude of attack surfaces, and as daily life and safety revolve around AI which needs to be more or less failure-proof. This is followed by a chart reiterating the threats covered in this paper, paired with common or recommended methods of protecting against each attack. Having covered all these topics, this paper aims to provide a useful tool with which researchers and cybersecurity professionals may study IoT in the context of cybersecurity and AI in order to secure IoT systems. Additionally, it also aims to emphasize the implications of up and coming technology and the impacts that each of these fields will have on the others. It is important to consider all the potential consequences of a technological development both before and after it is made public, as cyberattackers are constantly looking to use new technologies to their benefit, whether this means diverting the technology from its original purpose or using the technology as a tool to perpetuate other attacks. This paper discusses how IoT and AI have been taken advantage of for criminal purposes or have had weaknesses exploited as an example of this, which will help readers understand current risks and help cultivate an understanding such that these weaknesses are accounted for in the future in order to prevent cyberattacks.
Evans D. The Internet of Things: how the next evolution of the internet is changing everything. Cisco Internet Business Solutions Group: Cisco; 2011.
Google Scholar
Rouse M. What is IoT (Internet of Things) and how does it work? IoT Agenda, TechTarget. http://www.internetofthingsagenda.techtarget.com/definition/Internet-of-Things-IoT . Accessed 11 Feb 2020.
Linthicum D. App nirvana: when the internet of things meets the API economy. https://techbeacon.com/app-dev-testing/app-nirvana-when-internet-things-meets-api-economy . Accessed 15 Nov 2019.
Lu Y, Xu LD. Internet of Things (IoT) cybersecurity research: a review of current research topics. IEEE Internet Things J. 2019;6(2):2103–15.
Article Google Scholar
Vorakulpipat C, Rattanalerdnusorn E, Thaenkaew P, Hai HD. Recent challenges, trends, and concerns related to IoT security: aan evolutionary study. In: 2018 20th international conference on advanced communication technology (ICACT), Chuncheon-si Gangwon-do, Korea (South); 2018. p. 405–10.
Lakhani A. The role of artificial intelligence in IoT and OT security. https://www.csoonline.com/article/3317836/the-role-of-artificial-intelligence-in-iot-and-ot-security.html . Accessed 11 Feb 2020.
Pendse A. Transforming cybersecurity with AI and ML: view. https://ciso.economictimes.indiatimes.com/news/transforming-cybersecurity-with-ai-and-ml/67899197 . Accessed 12 Feb 2020.
Meneghello F, Calore M, Zucchetto D, Polese M, Zanella A. IoT: internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019;6(5):8182–201.
Roopak M, Yun Tian G, Chambers J. Models deep learning, for cyber security in IoT networks. In: IEEE 9th annual computing and communication workshop and conference (CCWC), Las Vegas, NV, USA. 2019;2019:0452–7.
Cañedo J, Skjellum A. Using machine learning to secure IoT systems. In: 2016 14th annual conference on privacy, security and trust (PST), Auckland; 2016. p. 219–22, https://doi.org/10.1109/PST.2016.7906930 .
Farivar F, Haghighi MS, Jolfaei A, Alazab M. Artificial intelligence for detection, estimation, and compensation of malicious attacks in nonlinear cyber-physical systems and industrial IoT. IEEE Trans Ind Inf. 2020;16(4):2716–25. https://doi.org/10.1109/TII.2019.2956474 .
Wang S, Qiao Z. Robust pervasive detection for adversarial samples of artificial intelligence in IoT environments. IEEE Access. 2019;7:88693–704. https://doi.org/10.1109/ACCESS.2019.2919695 .
Radanliev P, De Roure D, Van Kleek M, Santos O, Ani U. Artificial intelligence in cyber physical systems. AI & society. 2020; p. 1–14.
Radanliev P, De Roure D, Page K, Nurse JR, Mantilla Montalvo R, Santos O, Maddox LT, Burnap P. Cyber risk at the edge: current and future trends on cyber risk analytics and artificial intelligence in the industrial internet of things and industry 4.0 supply chains. Cybersecurity. 2020;3:1–21.
Radanliev P, De Roure DC, Nurse JR, Montalvo RM, Cannady S, Santos O, Burnap P, Maple C. Future developments in standardisation of cyber risk in the Internet of Things (IoT). SN Appl Sci. 2020;2(2):169.
Woo S. The right security for IoT: physical attacks and how to counter them. In: Minj VP, editor. Profit From IoT. http://www.iot.electronicsforu.com/headlines/the-right-security-for-iot-physical-attacks-and-how-to-counter-them/ . Accessed 13 June 2019.
Akram H, Dimitri K, Mohammed M. A comprehensive iot attacks survey based on a building-blocked reference mode. Int J Adv Comput Sci Appl. 2018. https://doi.org/10.14569/IJACSA.2018.090349 .
Herberger C. DDoS fire & forget: PDoS—a permanent denial of service. Radware Blog, Radware Ltd. http://www.blog.radware.com/security/2015/10/ddos-fire-forget-pdos-a-permanent-denial-of-service/ . Accessed 12 Sept 2016.
Cekerevac Z, Dvorak Z, Prigoda L, Čekerevac P. Internet of things and the man-in-the-middle attacks–security and economic risks. Mest J. 2017;5:15–25. https://doi.org/10.12709/mest.05.05.02.03 .
Melamed T. An active man-in-the-middle attack on bluetooth smart devices. WIT Press, International Journal of Safety and Security Engineering. http://www.witpress.com/elibrary/sse-volumes/8/2/2120 . Accessed 1 Feb 2018.
Mode G, Calyam P, Hoque K. False data injection attacks in Internet of Things and deep learning enabled predictive analytics; 2019.
De Donno M, Dragoni N, Giaretta A, Spognardi A. Analysis of DDoS-capable IoT malwares. In: 2017 federated conference on computer science and information systems (FedCSIS), Prague; 2017. p. 807–16. https://doi.org/10.15439/2017F288 .
Mirai Botnet DDoS Attack. Corero, Corero. http://www.corero.com/resource-hub/mirai-botnet-ddos-attack/ . Accessed 9 Dec 2019.
BrickerBot Malware emerges, permanently bricks iot devices. Trend Micro, Trend Micro Incorporated. http://www.trendmicro.com/vinfo/us/security/news/internet-of-things/brickerbot-malware-permanently-bricks-iot-devices . Accessed 19 Apr 2017.
Zeadally S, Adi E, Baig Z, Khan IA. Harnessing artificial intelligence capabilities to improve cybersecurity. IEEE Access. 2020;8:23817–37.
Jurn J, Kim T, Kim H. An automated vulnerability detection and remediation method for software security. Sustainability. 2018;10:1652. https://doi.org/10.3390/su10051652 .
Comiter M. Attacking artificial intelligence. Belfer Center for Science and International Affairs, Belfer Center for Science and International Affairs. http://www.belfercenter.org/sites/default/files/2019-08/AttackingAI/AttackingAI.pdf . Accessed 25 Aug 2019.
McMahan B, Daniel R. Federated learning: collaborative machine learning without centralized training data. Google AI Blog, Google. http://www.ai.googleblog.com/2017/04/federated-learning-collaborative.html . Accessed 6 Apr 2017.
Rojek M. Federated learning for IoT. Medium, becoming human: artificial intelligence magazine. http://www.becominghuman.ai/theres-a-better-way-of-doing-ai-in-The-iot-era-feabbbc1b589 . Accessed 16 Apr 2019.
Porter E. What is a botnet? And how to protect yourself in 2020. SafetyDetectives, Safety Detectives. http://www.safetydetectives.com/blog/what-is-a-botnet-and-how-to-protect-yourself-in/#review-2 . Accessed 28 Dec 2019.
Hendrickson J. What is the mirai botnet, and how can i protect my devices? How to geek, LifeSavvy media. http://www.howtogeek.com/408036/what-is-the-mirai-botnet-and-how-can-i-protect-my-devices/ . Accessed 22 Mar 2019.
Understanding denial of service attacks. Cybersecurity and infrastructure security agency CISA. http://www.us-cert.cisa.gov/ncas/tips/ST04-015 . Accessed 20 Nov 2019.
Moisejevs I. Poisoning attacks on machine learning. Towards data science, medium. http://www.towardsdatascience.com/poisoning-attacks-on-machine-learning-1ff247c254db . Accessed 15 July 2019.
Fang M et al. Local model poisoning attacks to Byzantine-Robust federated learning. In: Usenix security symposium. arXiv:1911.11815 . Accessed 6 Apr 2020.
Download references
Acknowledgements
This work was supported in part by the Commonwealth Cyber Initiative, an investment in the advancement of cyber R&D, innovation and workforce development in Virginia, USA. For more information about CCI, visit cyberinitiative.org.
Author information
Authors and affiliations.
Batten College of Engineering and Technology, Old Dominion University, Norfolk, VA, USA
Murat Kuzlu
Computer Science, Christopher Newport University, Newport News, VA, USA
Corinne Fair
eKare, Inc, Fairfax, VA, USA
Ozgur Guler
You can also search for this author in PubMed Google Scholar
Contributions
MK, and CF conceived and designed the work as well as contributed to the acquisition, analysis, and interpretation of data. All authors discussed the results and wrote the final manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Murat Kuzlu .
Ethics declarations
Competing interests.
The authors declare that they no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.

Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Kuzlu, M., Fair, C. & Guler, O. Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity. Discov Internet Things 1 , 7 (2021). https://doi.org/10.1007/s43926-020-00001-4
Download citation
Received : 29 September 2020
Accepted : 30 November 2020
Published : 24 February 2021
DOI : https://doi.org/10.1007/s43926-020-00001-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Artificial Intelligence
- Internet of Things (IoT)
- Cybersecurity
- Find a journal
- Publish with us
- Track your research
- Open access
- Published: 05 January 2022
A decade of research on patterns and architectures for IoT security
- Tanusan Rajmohan 1 ,
- Phu H. Nguyen ORCID: orcid.org/0000-0003-1773-8581 2 &
- Nicolas Ferry 3
Cybersecurity volume 5 , Article number: 2 ( 2022 ) Cite this article
10k Accesses
10 Citations
Metrics details
Security of the Internet of Things (IoT)-based Smart Systems involving sensors, actuators and distributed control loop is of paramount importance but very difficult to address. Security patterns consist of domain-independent time-proven security knowledge and expertise. How are they useful for developing secure IoT-based smart systems? Are there architectures that support IoT security? We aim to systematically review the research work published on patterns and architectures for IoT security (and privacy). Then, we want to provide an analysis on that research landscape to answer our research questions. We follow the well-known guidelines for conducting systematic literature reviews. From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed thirty-six (36) papers that have been peer-reviewed and published around patterns and architectures for IoT security and privacy in the last decade (January 2010–December 2020). Our analysis shows that there is a rise in the number of publications tending to patterns and architectures for IoT security in the last three years. We have not seen any approach of applying systematically architectures and patterns together that can address security (and privacy) concerns not only at the architectural level, but also at the network or IoT devices level. We also explored how the research contributions in the primary studies handle the different issues from the OWASP Internet of Things (IoT) top ten vulnerabilities list. Finally, we discuss the current gaps in this research area and how to fill in the gaps for promoting the utilization of patterns for IoT security and privacy by design.
Introduction
The Internet of Things (IoT) is becoming more popular as many “things” are getting more intelligent and connected, e.g., smartphones, smart cars, smart energy grids, smart cities. The IEEE Standards Association defines an IoT system as “a system of entities (including cyber-physical devices, information resources, and people) that exchange information and interact with the physical world by sensing, processing information, and actuating” (IEEE SA 2018 ). In 2019, the International Data Corporation (IDC) made a forecast that there will be 41.6 billion IoT devices in the field by 2025. Footnote 1 Most of the critical infrastructures pointed in the EU’s Directive on security of network and information systems Footnote 2 such as for energy, water, transport, and healthcare are or will be IoT-based. For instance, smart cities are integrating IoT sensors with analytic to streamline spending, improve infrastructural efficiency. Footnote 3 Internet-connected pacemakers have been implanted for millions to help control their abnormal heart rhythms. The IoT will thus play a key role in the digitalization of the society and IoT security issues will “affect not only bits and bytes”, but also “flesh and blood” (Schneier 2017 ). Without solid security in place, attacks and malfunctions in IoT-based critical infrastructures may outweigh any of its benefits (Roman et al. 2011 ). On the other hand, privacy is also very important in the IoT. Many “things” that people use in daily activities at work and at home are now connected to the Internet. This means that sensitive private data can be exposed via the Internet. Privacy challenges are just as important to tackle in comparison to security challenges in the IoT. The heterogeneous networking technologies and resource-constrained devices of the IoT that can only afford lightweight security and privacy solutions are proven to be weak links for IoT systems (Porambage et al. 2016 ). It is also possible that security and privacy are often overlooked by IoT solutions providers (Richa 2021 ), e.g., because of complexity, time-to-market pressure, or due to a lack of knowledge. A way to address this issue could be based on security patterns, which have proven to be very valuable for practitioners, especially non-security experts (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ).
In the software engineering discipline, patterns document well-known solutions that contain domain-independent knowledge and expertise in a reusable way. The solutions documented by patterns are known to be sound because they are tested over time (Schmidt and Buschmann 2003 ). Moreover, the pros and cons of a pattern are often explicitly documented. Therefore, sketching a solution based on a pattern can provide a good baseline for building the system. Using patterns and architecture alone is not enough but can provide an important support in the development methods for secure systems such as the ones surveyed in Nguyen et al. ( 2015 ). Security patterns consist of domain-independent, time-proven security knowledge, and expertise. Security patterns can contribute to the security and privacy of systems because they offer invaluable help in applying solid design solutions that, for example, secure the user authentication, information processing and storing, secure communication with other devices and with the server. Books and catalogs of security patterns, such as Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ), Nguyen et al. ( 2015 ) and Steel and Nagappan ( 2006 ) should be useful for users to unravel security challenges by utilizing time-proven security knowledge and expertise.
However, the IoT era introduces new security challenges that existing approaches and methods cannot address. Footnote 4 For example, the cross-domain cyber-to-physical (C2P) attack is the least understood one comparing to P2C, C2C, or P2P attack categories (Yampolskiy et al. 2013 ). IoT systems, especially mission-critical ones, having intrinsic complexity and heterogeneity, broader attack surfaces, often live under uncertainty, which exacerbates security issues (Ciccozzi et al. 2017 ). Indeed, nowadays IoT systems often span across the Cloud layer, the Fog/Edge layer, and the IoT field-devices layer consisting of many smart, connected devices. The explosion in connectivity created a larger attack surface area (Covington and Carskadden 2013 ). Besides, the IoT field-devices often operate under dynamic (physical) execution environments, involving dynamic actuation, but have limited data delivery and storage facilities. In other words, uncertainty is inherent in IoT systems. We are very much interested in examining the landscape of patterns and architectures being applied for the IoT domain, whose security (and privacy) challenges are huge. How have the existing security patterns been applied in tackling IoT security challenges? Are there any new security patterns that have been specifically introduced to address new security challenges in IoT?
To make sense of the research landscape of methodologies around patterns for security and privacy in IoT, we have conducted a systematic literature review (SLR) following the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Our SLR has three fundamental objectives. First, we need to find out the approaches around patterns and architectures for IoT security and privacy, called the primary studies of our SLR. Second, by analyzing the primary studies, we can perceive gaps in the state-of-the-art of patterns and architectures for IoT security and privacy. We are particularly interested in how advanced patterns and architectures are, and their approaches to address IoT security. Third, based on the results, we identify the gaps to support security and privacy in modern IoT systems and propose further research to fill the gaps. The main contributions of this work are our responses to the accompanying research questions (RQ)s.
RQ1 What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
RQ2 What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
RQ3 What are the “gaps” to make security patterns and architectures more applicable for IoT?
From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed 36 papers that have been published around patterns and architectures for IoT security in the last decade. Our analysis results show the trend of an increasing number of published papers in this research area in three recent years. We have performed our analysis based on a taxonomy that we built for this research area. Our analysis sheds some light on the state of the art around patterns and architectures for IoT security and the current limitations. Based on our analysis, we provides some suggestions for a way forward of this research topic. Specifically, the contributions in this paper include:
We have an exhaustive database search process. Moreover, we manually conducted snowballing (backward and forward as suggested in Wohlin 2014 ). We identified and included six new primary studies from this snowballing process. Therefore, our final set of primary studies reported in this paper is 36 (see “ Our systematic literature review approach ” section).
We have defined a clear taxonomy (see “ Taxonomy of the research area ” section) and provided in-depth analyses on the architectures and patterns from the primary studies (see “ Technical aspects of the primary studies (RQ2) ” section). For example, we summarize all the patterns from the primary studies and also discuss how the architectures from the primary studies cover the seven layers of the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ).
We have provided discussion on the existing gaps and limitations in “ Gaps and limitations (RQ3) ” section. For example, we discuss the gaps in the research contributions from the primary studies regarding how they handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ). Last but not least, we explicitly discuss the possible threats to validity of our study in “ Threats to validity ” section to give readers more insights in this work.
In the remainder of this paper: “ Background ” section gives some background definitions. In “ Our systematic literature review approach ” section, we present our SLR approach. To facilitate data extraction and comparison, “ Taxonomy of the research area ” section describes our classification schemes for the primary studies. We present the results of our SLR in “ Results ” section. Related work is discussed in “ Related work ” section. In “ Threats to validity ” section, we analyze possible threats to the validity of this work. Finally, we conclude the paper with summarizing the main findings in “ Conclusions ” section.
We give the definitions of SLR in the “ Systematic literature review ” section, (security) design patterns in the “ Design pattern ” section, and security architecture in the “ Security architecture ” section that were used to define the scope of this work.
Systematic literature review
A SLR is a study that “reviews all the primary studies relating to a specific research question”, and “uses a well-defined methodology to identify, analyze and interpret all available evidence related to that specific research question in a way that is unbiased and (to a degree) repeatable.” (Kitchenham et al. 2011 )
Design pattern
The primary understanding for a design pattern is that it is a reusable solution for a typical occurring issue in software design. A pattern is ordinarily abstract with the goal that it may be reused, and it is a proven solution for solving a software design problem. A design pattern is not a complete implementation that can be executed and utilized, but more a plan or template for how to take care of an issue that can serve in various circumstances/contexts (Gamma et al. 1994 ; Fernandez-Buglioni 2013 ).
According to Schumacher et al. ( 2013 ), “a security pattern describes a particular recurring security problem that arises in specific contexts, and presents a well-proven generic solution for it. The solution consists of a set of interacting roles that can be arranged into multiple concrete design structures, as well as a process to create one particular such structure.”
Note that there are key security patterns such as from Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ) and Steel and Nagappan ( 2006 ) that provide guidance at the architecture level. These patterns may also be called security architectures but yet they are design patterns and should be considered as patterns. In other words, we clearly call architectural patterns as patterns, not architectures. This definition means that we only consider an architecture as a pattern if it is explicitly described as a pattern. Any architecture for IoT security that is not a pattern is called “security architecture” in this paper.
Security architecture
The term sofware architecture typically refers to the structure of a software system, including software elements and the relationships between them. Within our SLR, we want to include architectures for IoT security or architectures that were specifically designed with IoT security concerns in mind. When architectures are not formalized as a pattern, we call them IoT security architectures, as opposed to architectural patterns. When a security architecture is generic enough to be used in different contexts, it is called an IoT security reference architecture. It is worth discussing the relationship between IoT security reference architectures and IoT security patterns: (1) IoT security patterns can be extracted from an IoT security reference architecture, and (2) an IoT security reference architecture can leverage and be composed of one or several patterns, including IoT security patterns. By analyzing not only security patterns but also security architectures, our study aims to cover security aspects encompassing not only only one layer of IoT systems but also multiple layers when architectures are key to address.
Our systematic literature review approach
We conducted our SLR using the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Three main phases of an SLR are: Planning the Review, Conducting the Review, Reporting the Review (see Fig. 1 ) (Kitchenham and Charters 2007 ).
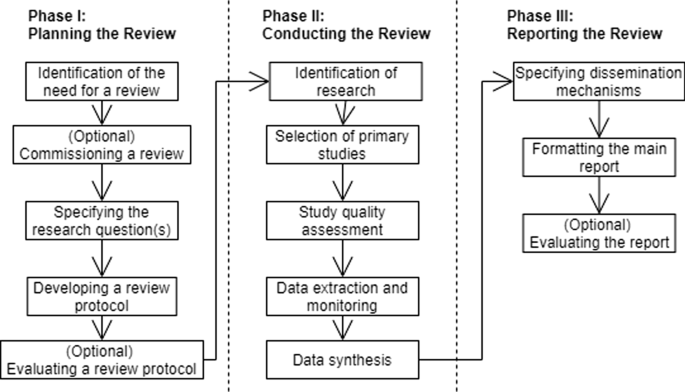
The process of planning, conducting, and reporting a SLR (Kitchenham and Charters 2007 )
We map the stages associated with planning our SLR with where we present them in this paper:
Identification of the need for a review: In the “ Introduction ” section, we have presented the motivation of our SLR.
Specifying the research question(s): the “ Research questions ” section.
Developing a review protocol: Our review protocol is developed according to the guidelines in Kitchenham and Charters ( 2007 ). The main parts of our review protocol are the research questions (“ Research questions ” section), the inclusion and exclusion criteria (“ Inclusion and exclusion criteria ” section), the search and selection strategy (“ Search and selection strategy ” section), and the taxonomy for data extraction and synthesis (“ Taxonomy of the research area ” section).
The stages associated with conducting our SLR:
Identification of research: Search and selection strategy (“ Search and selection strategy ” section).
Selection of primary studies: Search and selection strategy (“ Search and selection strategy ” section).
Study quality assessment: We only selected peer-reviewed papers with enough details as the primary studies of this SLR (“ Inclusion and exclusion criteria ” section).
Data extraction and monitoring: We extracted data based on the taxonomy defined in “ Taxonomy of the research area ” section.
Data synthesis: We synthesized the extracted data to answer our research questions in “ Results ” section.
The stages associated with reporting our SLR:
Specifying dissemination mechanisms: We specified the journal to publish the results of our SLR.
Formatting the main report: This paper.
With the particular context and motivation displayed in “ Introduction ” section, we introduce our RQs for this paper in “ Research questions ” section. In “ Inclusion and exclusion criteria ” section, we explain the criteria for choosing primary studies to explicitly portray the scope of our SLR and diminish possible bias in our selection procedure. “ Search and selection strategy ” section shows our search strategy to locate the primary studies for answering the RQs.
Research questions
This SLR aims to answer the three RQs presented in “ Introduction ” section. Each is extended with sub-questions.
RQ1 includes three sub-RQs. RQ1.1 In which year(s) are the primary studies published? Answering this question allows us to know when this research topic became fascinating as well as how recent the research on this topic is. It could give an indicator of how much attention security patterns and secure architectures for IoT get from the research community. RQ1.2 — What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Answering this question allows us to recognize the target domain for each paper. Note that security patterns are presented in publications across a few related research areas, e.g., IoT, Cloud, SE, Network. The type of paper can give a few hints on the maturity of the primary study. Journal papers should report more mature studies than conference papers. RQ1.3 — How is the distribution of publications in terms of papers affiliated with industry and the academic? We classify a paper as academic if all the associated authors are with a university or a research institute. Moreover, we group papers as industrial if all related authors are with an industrial organization, and characterize the papers as both if there is a coordinated effort of both academia and industry. Answering RQ1.3 will display the collaboration effort between industry and scholar communities. It also demonstrates the interest and needs of IoT security patterns in the industry.
RQ2 has three sub-RQs. RQ2.1 — What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? Answering RQ2.1 shows how the distribution of patterns and architectures are, as well as how the contribution is used or for what purpose. RQ2.2 — How well do the patterns and architectures cover security and privacy issues? Answering this RQ shows what security patterns and architectures focus on IoT systems’ specific security and privacy concerns. It also shows us what current security and privacy concerns are most covered today. RQ2.3 — What application domains have been addressed by the security patterns and architectures? This RQ can help us to see what application domains have got more attention in the application of security patterns and architectures.
RQ3 also has two sub-RQs. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? These RQs help to express and suggest the current issues and possible directions for future work.
Inclusion and exclusion criteria
Considering the RQs and the basis of our study introduced in “ Introduction ” section, we predefined the inclusion and exclusion criteria to decrease bias in our methodology of search and selection of primary studies. The primary studies must meet ALL the accompanying inclusion criteria (IC):
(IC1) Contain patterns or architectures (one or more) in some form relevant for IoT systems.
(IC2) Be specifically within the area of IoT, either in a generally applicable domain or in a specific application domain of IoT.
(IC3) Present security (or privacy) concerns explicitly in system design, architecture, or infrastructure.
(IC4) Have a minimum length of four pages in double-column format or six pages in single-column format.
Moreover, when a single approach is presented in more than one paper describing different parts of the approach (e.g., approach itself, empirical study, evaluation), we include all these papers, but still consider them as a single approach (study). When encountering more than one paper describing the same or similar approaches, which were published in different venues, we only include the most recent one that has the most complete description of the approach.
We excluded papers that are not written in English, non-peer-reviewed papers (e.g., “grey” literature, white papers in industry), and papers that are only accessible as extended abstracts, posters, or presentations (not full version). We also did not include multivocal surveys as primary studies because they are secondary studies. We do discuss the surveys on related topics as related work in “ Related work ” section. We also mainly focused our review for the publications in the duration 2010–2020 (see “ Search and selection strategy ” section).
Search and selection strategy
The search strategy utilized is a blend of various kinds, to thoroughly scan for IoT security pattern and architecture papers. The objective is to locate the most relevant papers and, along these lines, discover as many essential IoT security pattern and architecture papers as possible.
Database search
Using online inquiry components of popular publication databases is the most notable approach to scan for essential primary studies when directing supplemental studies (Kitchenham and Charters 2007 ). We used five of the popular publication databases IEEE Xplore, Footnote 5 ACM Digital Library, Footnote 6 ScienceDirect, Footnote 7 Web of Knowledge (ISI), Footnote 8 and Scopus Footnote 9 to search for potential primary studies. Scopus and ACM DL already index SpringerLink Footnote 10 (Tran et al. 2017 ). The five picked databases contain peer-reviewed articles, which give advanced search capacities. Following the guidelines from Kitchenham and Charters ( 2007 ), based on the research questions and keywords utilized in some related articles, we have defined our search keywords. The search query was adopted to fit each of the search engines of the five publication databases. Note that we did not include “misuse pattern” in the search query because misuse patterns (from the point of view of the attacker) are out of scope of this study.
( “Internet of Things” OR “IoT” OR “Cyber Physical Systems” OR “Web of Things” )
( “Security Pattern” OR “Design Pattern” OR “Security Design Pattern” OR “Privacy Pattern” OR “Security Architecture” OR “Secure Architecture” )
During our database search process, we did conduct many rounds of testing the search query on the search engines. On the one hand, this testing process helped us to improve our search query and customize it for better fit the search features. On the other hand, we also saw very few hits returned by the search engines for the duration 2000–2010. Therefore, we mainly focused our review for the publications in the duration 2010–2020.
For every candidate paper, we originally reviewed the paper’s title and abstract, trailed by skimming through the contents. On the off chance that an applicant paper shows up in more than one database, we show them in the other database results. When merging to the first set of primary studies, we consolidate the outcomes, so we get the right number of papers without copies. It is portrayed step by step in Fig. 2 .
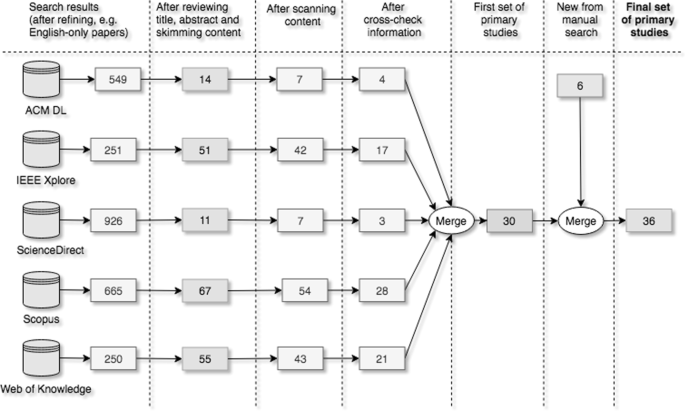
Overview of the search and selection steps
Manual search
It is unrealistic to guarantee the database search results can cover all IoT security patterns and architectures in our study. We have, therefore, attempted to supplement the database search by doing a manual search. We started by manually searching through published papers from previous journals and conferences. The conferences and journals we went through to find papers were: The International Conference on the Internet of Things, Footnote 11 Pattern Languages of Programs (PLoP), Footnote 12 EuroPLoP, Footnote 13 IEEE ICIOT, Footnote 14 ACM Transactions on Internet of Things (TIOT) Footnote 15 and IEEE Internet of Things Journal. Footnote 16 We also manually did snowballing (backward and forward) on all the primary studies found as suggested in Wohlin ( 2014 ). In the wake of looking through these journals and conferences as well as doing snowballing, we concluded that most of the relevant papers posted or found from our manual search were earlier discovered from the database search, or they did not satisfy our criteria. The papers from the manual search were checked against the automatic results, and vice versa. In the end, we had found six more primary studies from the manual search process.
Note that any candidate paper in doubt was kept for evaluation and cross-checked among the reviewers at each phase of our search and selection process. Our gathering conversations have finally yielded a set of 36 primary studies for data extraction and synthesis to answer the RQs Footnote 17 .
Taxonomy of the research area
In this section, we define a taxonomy for IoT security patterns and architectures. This taxonomy helps us to extract and synthesize data from the primary studies for answering the RQs. We applied a top-down strategy to process data from the literature around IoT, security patterns, IoT architectures, and design patterns to create a first version of the taxonomy. We also tried to validate and enrich the taxonomy by a bottom-up approach. The bottom-up approach is for extracting data from a test set of primary studies. This test set consists of the initial ten primary studies chosen. It helped us to characterize and determine the significant methods and terminology utilized in the primary studies.
Domain specificity
We characterize the domain specificity in the same manner as (Washizaki et al. 2020 ) with minor tweaks. It is essential to examine the applicability and reusability of each IoT security pattern.
General IoT security design patterns, and security architectures, which apply to any IoT system and software.
Specific IoT security design patterns, and security architectures that address specific problem domains (such as healthcare) and technical domains (such as the brain-computer interaction).
Categorization of security pattern research
We classify security patterns according to the main categories presented in Yskout et al. ( 2006 ). First, we distinguish security patterns based on how they affect the software application or the environment (e.g., infrastructure, middleware) in which the application will eventually be deployed.
Application architecture (AA): A pattern’s introduction can affect an extensive part of the application, e.g., by introducing new components in the application, or modifying existing components.
Application design (AD): A pattern’s introduction only has local implications. For example, a pattern can introduce some form of encapsulation of security data.
System (S)/Execution environment: A pattern’s introduction only affects the environment in which the application will be deployed.
We classify the (security, privacy) objectives of the patterns as presented below in “ Security and privacy concerns ” section. More importantly, we detail the patterns by their main properties from the software design pattern template by the Gang of Four (Gamma et al. 1994 ):
Intent: What (in what context) is the pattern used for? What is the purpose of the pattern?
Problem: What problem that the pattern can address. This may also include the different forces (and context) that lead to the problem.
Solution: A description of the solution provided by the pattern.
We also characterize patterns by purpose , method , and research implementation , which is similar to how Washizaki et al. ( 2018 ) did in their paper.
C1 purpose: This part includes the topics addressed by the research, software life-cycle, and the intended users.
C2 method: This part refers to the methodology and modeling methods to define the pattern’s structure and design.
C3 research implementation/validation: This part includes where, how and if the contributions were implemented and tested/validated, and in which context. It also includes analysis of a test case or scenario. Whether the results are automated and encapsulated in a tool, and whether case studies or experiments are conducted to evaluate the results relevant to the original research purpose.
IoT architecture
Many IoT architecture exist in the literature, all decomposed in a different number of layers. In our taxonomy, we leverage the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ). This architecture provides a fine-grained granularity over the different layers that typically compose an IoT system. It has recently been adopted in many large scale IoT systems, for instance, as indicated in Create-IoT ( 2018 ), all of the H2020 IoT large scale pilots at the exception of one, have adopted this architecture. It consists of the following seven layers:
L1 physical devices and controllers: Physical layer consisting of devices or “things” of the IoT. The “things”, sensors, and Edge Node devices are classified within this layer.
L2 connectivity: Connectivity spans from the “middle” of an Edge Node device up through transport to the Cloud. This layer maps data from the logical and physical technologies used, the communication between the physical layer and the computing layer, and above.
L3 edge computing: Layer that brings computation and data storage closer to the location it is needed. Protocol conversion, routing to higher-layer software functions, and even “fast path” logic for low latency decision making will be implemented at this layer.
L4 data accumulation: Intermediate storage of incoming storage and outgoing traffic queued for delivery to lower layers. Pure SQL is what the layer is implemented with, but it may require more advanced solutions, i.e., Hadoop & Hadoop File System, Mongo, Cassandra, Spark, or other NoSQL solutions.
L5 data abstraction: Data is made clear and understandable, centers around rendering data and its storage in manners that enable developing more straightforward, performance-enhanced applications. This layer speeds up high priority traffic or alarms, and sort incoming data from the data lake into the appropriate schema and streams for upstream processing. Likewise, application information bound for downstream layers is reformatted appropriately for device communication and queued for processing.
L6 application layer: At the application layer, information interpretation of multiple IoT sensors or measurements occur, and logic is executed. Monitoring, process optimization, alarm management, statistical analysis, control logic, logistics, consumer patterns, are just a few examples of IoT applications.
L7 collaboration and processes: Application processing to its users, and data processed at lower layers are integrated with business applications. This layer consists of human interaction with all the layers of the IoT system, and economic value is delivered.
Another simpler IoT architecture largely adopted in the literature consists of three layers: perception (L1), network (grouping L2 and L3), and application (grouping L4, L5, L6, L7, and L8). We map how the contributions of today fit in both the IoT World Forum Reference Model of the IoT architecture and the three-layer IoT architecture.
Security and privacy concerns
We analyze the primary studies according to the following security and privacy concerns: confidentiality, integrity, availability (CIA), accountability, and privacy (Ross et al. 2016 ; Kuhn et al. 2001 ; Yskout et al. 2006 ). These concerns are what we consider essential to IoT systems and devices. We also classify security mechanisms such as authentication and authorization when such information are available in the primary studies. We want to see what patterns and architectures uphold and protect against these security and privacy concerns. Their definitions are as follows.
Confidentiality: Ensures the property that information is not made available or disclosed to unauthorized individuals, entities, or processes.
Integrity: Maintains and ensures the accuracy and completeness of the data during its life-cycle.
Availability: The information/service is available when needed.
Authentication: The system/device can verify a claim of identity.
Authorization: The system can determine what resources the entities that have been identified and authenticated can access and what actions they can perform within/on the system.
Accountability: Enables the tracing of important (or all) actions performed on the system back to a particular user, usually by means of logging.
Privacy: The data collected is legally collected and stored, how data is shared, and follow regulatory restrictions from the GDPR (mostly EU), and HIPAA (Office for Civil Rights 2013 ), GLBA (Federal Trade Commission 1999 ) (mostly in the US).
This section presents the main results of our SLR and how our research questions are answered. Table 1 shows an overview of the primary studies that have been found in this review regarding patterns and architectures for IoT security and privacy. Based on the taxonomy in “ Taxonomy of the research area ” section, we have extracted and synthesized the primary studies’ data to answer the RQs. “ High-level statistics (RQ1) ” section shows high-level statistics that help us to answer RQ1. Then, we present low-level details of the primary studies in “ Technical aspects of the primary studies (RQ2) ” section that help us to answer RQ2. Based on our answers to RQ1 and RQ2, we discuss the gaps and limitations as our answer to RQ3.
High-level statistics (RQ1)
In this section, we provide our answers to the RQ1- What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
Answering RQ1.1 In which year(s) are the primary studies published? Fig. 3 shows a rise in the number of conference (C) and journal (J) publications related to IoT security patterns and architectures in the recent three years (2018: 7C, 2019: 5C, 4J and 2020 Footnote 18 : 5C, 5J). This spike shows that security patterns and architectures are gaining more focus over the years and that there is a demand for IoT security pattern and architecture research.
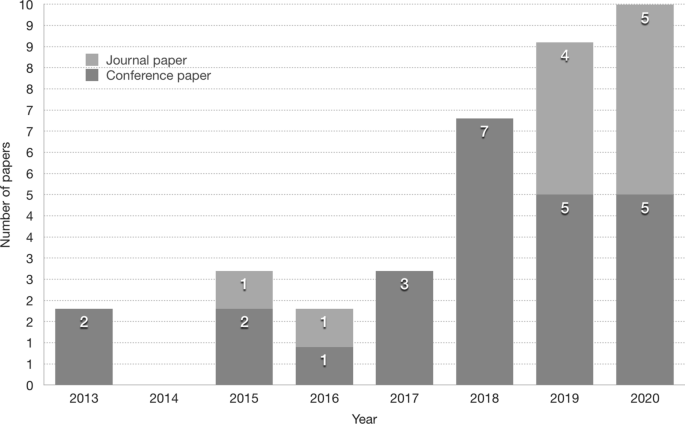
Publications per year, per venue type
Answering RQ1.2 What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Research on the IoT, with its heterogeneous nature, traverses through various important research areas, among which we perceived Software Engineering (SE), Cloud, Blockchain, Network, and recently specialized IoT research (Borgia et al. 2016 ). Figure 4 shows the research focus areas of the publication venues where the primary studies have been published. The main research areas that we found are between IoT: 36, Cloud: 4, Network: 7, Blockchain: 7. Note that publication venues often have several research areas in their calls for papers, e.g., IoT, network. Therefore a portion of the papers could be classified in several research areas at the same time (e.g., IoT, network). These numbers do reflect the different dimensions of IoT research, with IoT research domain getting progressively more visible. In other words, IoT-oriented conferences and journals are becoming more popular and have attracted research contributions on patterns and architectures for IoT security and privacy.
The number of primary studies that are published as conference papers are more than double the number of primary studies published in journals. From the number of publications found, we distinguished the distribution of conference papers ( \(\sim\) 69%) and journal papers ( \(\sim\) 31%). It is reasonable that conference papers tend to be published more often and quickly. But, we also see that the number of journal papers has increased since our last study (Rajmohan et al. 2020 ). We do, however, believe and encourage a continued increase of journal papers around this topic. Especially seeing that the growth of IoT is increasing rapidly and that journal papers contribute to more detailed and elaborated contributions.
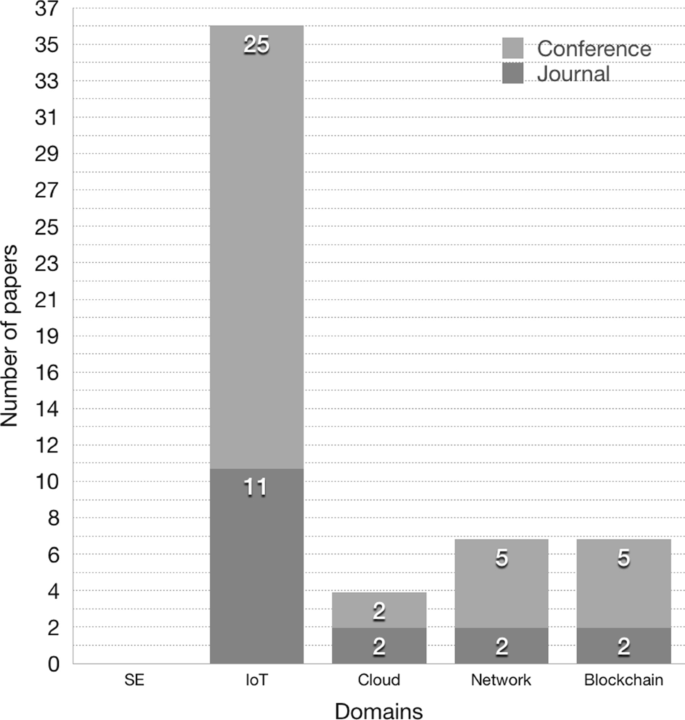
Research topics per publication venue
Answering RQ1.3 How is the distribution of publications in terms of papers affiliated with industry and the academic? Because IoT systems and devices are broadly utilized and growing in the industry and consumer market, we explored how the affiliations of the authors are dispersed from the primary studies. Would the affiliations of the authors have any implication on the publication of security patterns and architectures for IoT? From our analysis, we see that a significant amount of the authors who have published results on IoT security patterns or architectures are from academia ( \(\sim\) 75%). While there are no contributions exclusively from industry, authors working in industry do publish in joint efforts with co-authors from academia. In this work, we call the papers that have such joint efforts of academia-industry collaboration as “joint papers”. We discovered some papers of this type ( \(\sim\) 25%). The percentage of joint papers here is not high, but still remarkable compared to less than 10% of joint papers as primary studies reported in another review on security for cyber-physical systems (Nguyen et al. 2017 ).
Joint papers tend to have more usage examples and illustration contrasted with papers purely from academia. We saw in our study that 89% of the joint papers had graphical illustrations of their contribution in terms of architectural structure or pattern usage areas. The number of joint papers among academia and industry shows a promising collaboration level. We trust that this number continues to grow. The collaboration is win-win for the state of the art and practice, which can lead to the utilization of patterns and architectures proposed to improve products, production process, and internal processes that use IoT devices or systems further. We would be intrigued to see more implementations or examples of security patterns or architectures used by industry in the future.
Technical aspects of the primary studies (RQ2)
All the patterns and architectures in Table 1 have been examined according to our taxonomy (“ Taxonomy of the research area ” section), to give us meaningful information as well as pinpoint how the papers are relevant and where they contribute. The taxonomy was used to ensure that the primary studies have information relevant to this study. We can draw out some key examples, such as papers (Vijayakumaran et al. 2020 ; Vithya Vijayalakshmi and Arockiam 2020 ; Jerald et al. 2019 ; Pacheco et al. 2018 ), which are the ones who cover most security concerns (“ Security and privacy concerns ” section). We based on the (more fine-grained) data extracted from the primary studies to answer RQ2 : What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
Answering RQ2.1 What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? After finalizing the primary studies set, we found that the primary studies’ main contributions are either architectures ( \(\sim\) 81%) or patterns ( \(\sim\) 19%). These contributions are mostly solution proposals, where some have proper testing and validation ( \(\sim\) 57%) of their concept. Other papers have use case examples ( \(\sim\) 23%) in some form, and some papers even have implementations of their concept ( \(\sim\) 20%). As we presented in “ Security architecture ” section, papers describing frameworks are categorized as architectures (not patterns, if patterns are not explicitly mentioned). Therefore, we see a more significant contribution and more focus on architectures compared to patterns.
Claiming security solely based on a good architecture can be inadequate because it is typically not enough for end-to-end IoT security. We have seen other cases where architectures are not enough to solve the specific issues regarding e.g., user verification on the devices, firmware manipulation, and an attacker disconnects the devices upon will. Such issues are hard to handle only with security architecture solutions. The lack of security patterns is a result of its youth within the domain and security not being the main priority when developing IoT systems. Certain areas of an IoT system may need more attention than others regarding security, and architectures may not solve those issues. From our experience and information gathering, we have seen that the architecture solutions for IoT security have focused a lot on the whole system and all its layers (e.g., Cloud, Edge, IoT devices Juxtology 2018 ), more general system issues, and can target specific domains, but are very seldom enough to solve a specific problem. The architectures tend to focus on multiple layers (e.g., Cloud, Edge Juxtology 2018 ) and are harder to address a single layer issue or an issue in a small part of one of the architectural layers, where some specific security patterns may apply well.
As mentioned, a good architecture is only part of the solution and can be inadequate if we encounter specific security issues for a smaller area rather than the whole system, e.g., the breach on a casino’s thermostat in a fish tank to access customer data (Williams-Grut 2018 ). This breach shows the challenge to ensure end-to-end security for IoT systems, especially at their weakest links, e.g., a thermostat. Therefore, it would be exaggerating to tackle security only at the architectural level. A more straightforward solution would have been a security pattern for authentication of users or networks not to allow external communication to pass through IoT devices or verify the device when communication is sent. A more complete solution would be to employ suitable specific security patterns in a well-designed architecture. In other words, a high-level architecture supporting IoT security is only one side of the coin. The other side of the coin is to address specific IoT security challenges at any weak links such as IoT devices where some specific security patterns can help.
Table 2 shows which concerns regarding security and privacy for IoT are addressed by each of the 36 primary studies. When we compare the number of primary studies to the number of candidate papers we first found while doing the automatic search, there is a big difference. This means that security and IoT are popular keywords in many publications but “security patterns” for IoT is not. However, we still believe 36 is a reasonable amount, yet it ought to be higher with the goal that security patterns become increasingly frequent and accessible for industry and users who want to develop secure IoT systems.
Table 2 also shows us the distribution of the specificity of the various contributions. We see that most contributions fall under the “Generic” regarding application domains (“ Domain specificity ” section), which means that a substantial number of papers are adaptable for a widespread of IoT systems. These “Generic” solutions cover the core functionalities of an IoT system, which is why we labeled them “Generic” compared to the domain-specific solutions, which work within a specific domain for a specific purpose (e.g., smart cars, smart meters, and healthcare systems). As we can see, most of the contributions cover authentication, which is a crucial aspect of any system. One may link the amount of authentication coverage to the fact that several smart devices have been hacked due to a lack of authentication (Wright 2020 ). Even though authentication is the most focused concern in the primary studies, more efforts are needed for end-to-end security, including weak links in IoT systems. We would like to see more of such solutions and solutions for IoT pressing problems, e.g., communication, compatibility, integration, and scalability.
Answering RQ2.2 How well do the patterns and architectures cover security and privacy issues?
Table 2 shows a more detailed list of the concerns mentioned previously and what type of application domain the contributions have. We marked the concerns with an “x” if the concern was directly mentioned in the paper. The concern regarding privacy was only marked if it was explicitly mentioned, and not if they handle only the security concerns even they can contribute to privacy coverage.
Figure 5 displays the mapping of our security concerns based on the contribution. We weight how much each (security or privacy) concern was addressed in the primary studies compared to each other. We do so by simply calculating the percentage of how many times a concern was addressed compared to the total number of the times that all concerns were addressed. Note that as shown in Table 2 , most primary studies address more than one concern. As Fig. 5 shows, there is a widespread of focus between the security concerns (Confidentiality \(\sim\) 16%, Integrity \(\sim\) 19%, Availability \(\sim\) 8%, Authentication \(\sim\) 25%, and Authorization \(\sim\) 17%). Privacy ( \(\sim\) 15%) is relatively focused comparing to the security issues in terms of coverage within the primary studies. The low coverage for the availability concern could come from a lack of explicit explanation in the primary studies or availability was not considered in their solutions at all. In the first case, this is comprehensible as availability is a concern whose scope is broader than the only security domain. Indeed, preserving the availability of a system is tightly coupled to the ability of scaling it. Load scalability is the ability of a service to sustain variable workload while fulfilling quality of service (QoS) requirements, possibly by consuming a variable amount of underlying resources (Ferry et al. 2014 ). It is a core concern when engineering and designing complex system, and, as a result, many design patterns, including architectural patterns, have been defined in the literature from other fields (e.g., Big data, Cloud computing, large-scale systems, middleware).
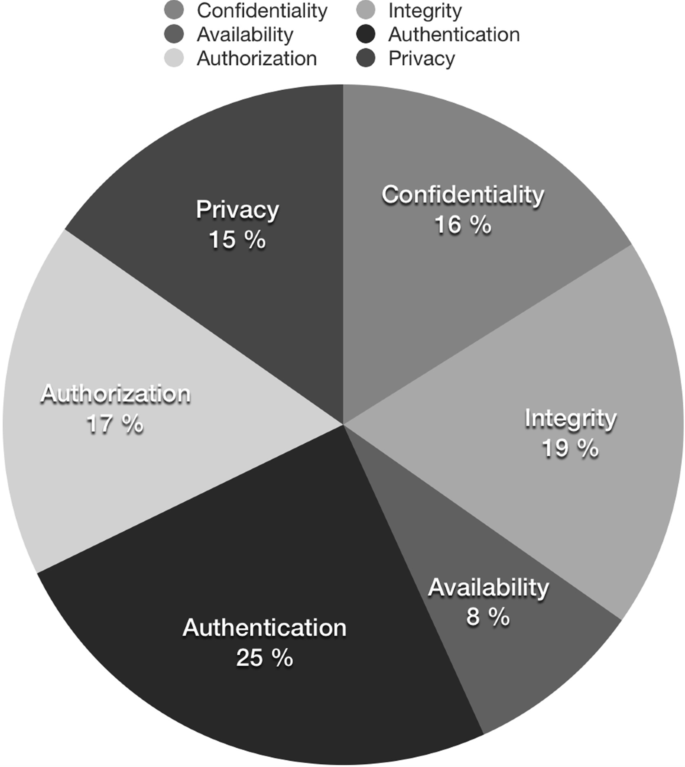
Security concerns based on the contribution
Table 2 can give a closer look on how many contributions of patterns and architectures focusing on the various concerns. For patterns, we see that only two papers out of seven security pattern papers cover the whole CIA (Confidentiality, Integrity, and Availability) triad, while security architecture papers have two out of 29 papers. Availability is the least covered concern in the primary studies. We are unsure if it is because the contributions focus mostly on authentication, but since many of these systems process or share information, we would argue that the basic CIA triad should be focused. Figure 6 illustrates the different security considerations and privacy, and shows which ones are more focused on in the papers found. Authentication is most focused by the primary studies. This point is understandable because authentication is often the foundation for building other security mechanisms such as for authorization, confidentiality, or privacy. But, the low focus on availability is something that should be drawn attention to because availability is crucial in many IoT systems, especially critical ones.
Another thing to notice is that privacy is considered in 18 out of the 36 papers. This number shows that privacy has gained nearly as much attention as security concerns in the primary studies. As mentioned previously, some papers and concerns may contribute indirectly to privacy, e.g., concerns such as authentication and authorization that verify and provide the correct access to users, which can be one way to preserve users’ privacy. But, we only count for privacy if a primary study does mention privacy explicitly.
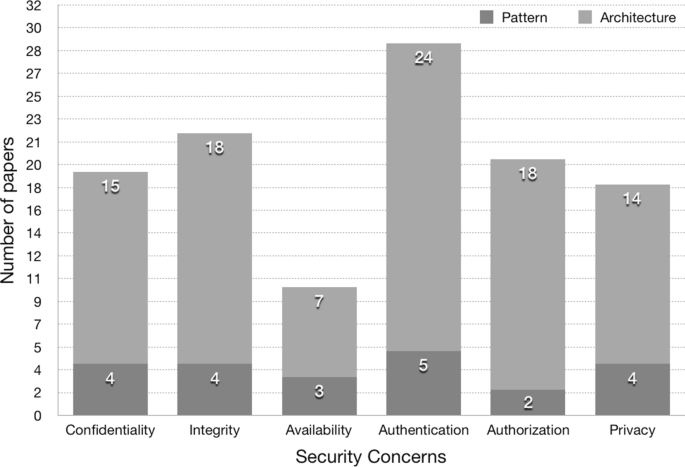
Architectures and patterns with focus on each security concern
Table 3 shows the IoT security and privacy patterns that are presented in the primary studies. It is worth to note that there is one primary study (Pape and Rannenberg 2019 ) dedicated to IoT privacy patterns. There are seven patterns for IoT privacy presented in Pape and Rannenberg ( 2019 ), which describe different possibilities of privacy violation and the corresponding solutions. We summarize these patterns according to the main elements of security pattern in Table 3 . There is another paper that even presents a misuse pattern (Syed et al. 2018 ). Paper Syed et al. ( 2018 ) shows a misuse pattern for Distributed Denial of Service (DDoS) in IoT. They specify appropriate countermeasures for mitigating it, contributing to a specific problem in many IoT systems. Paper Fysarakis et al. ( 2019 ) discusses a pattern-driven framework solution to encode dependencies between the security concerns mentioned in “ Security and privacy concerns ” section. More specifically, paper Fysarakis et al. ( 2019 ) presents orchestration models required for IoT and IIoT applications to guarantee quality properties including security, privacy. In the same direction but more on the trustfulness, paper Pahl et al. ( 2018 ) proposes an architecture pattern based on blockchain to ensure the identity of hardware devices and software applications, the origin and integrity of data and the contractual nature of orchestration. There is only one paper (Schuß et al. 2018 ) that proposes a pattern at the hardware layer for IoT security. Schuß et al. ( 2018 ) show a pattern to secure the device through hardware, by implementing exchangeable cryptographic co-processors. This paper provides security features that can be implemented to a general IoT system, but it requires changes or additions to the hardware. The hardware-based approach in Schuß et al. ( 2018 ) aims at allowing even constrained devices to utilize state-of-the-art cryptographic functions.
While the papers mentioned so far present IoT-specific patterns, the last two papers (Lee and Law 2017 ; Ur-Rehman and Zivic 2015 ) in Table 3 focus more on how generic security patterns can be applied for IoT. For example, both of them show how the well-known Secure Logger pattern can be used in IoT. Paper Lee and Law ( 2017 ) shows multiple patterns in which they describe and explain some usage areas, but they do not show results in these usage areas. It is more for cataloging purposes including other generic security patterns such as Secure Directory, Secure Adapter Pattern, Exception Manager Pattern, and Input Validation Pattern. Paper Ur-Rehman and Zivic ( 2015 ) presents the patterns that are adopted for smart metering systems. The Secure Remote Readout pattern is presented in details in Ur-Rehman and Zivic ( 2015 ). The other patterns are name checked only such as Secure Logger, Key Manager, Wakeup Service, and Transport Layer Security.
As mentioned in the previous section, patterns target more specific parts of an IoT system, which also makes it easier to implement a pattern for that section of the system. In most cases, architectures are harder to implement/adopt because they propose a solution for multiple parts or the whole system but often lack security details for specific parts. We discuss some representative examples of the papers we found that explicitly address, propose, or use security architectures such as Vithya Vijayalakshmi and Arockiam ( 2020 ), Witti and Konstantas ( 2018 ) and Pacheco et al. ( 2018 ). Paper Vithya Vijayalakshmi and Arockiam ( 2020 ) discusses an architecture that protects the data security at all the layers of data flow, the transmission of data is essential in this contribution. Paper Witti and Konstantas ( 2018 ) shows architectures in use-cases where they apply and discuss how they are used and the results. Paper Witti and Konstantas ( 2018 ) also explains how architecture can help securing a smart city while preserving citizens’ privacy in that city. A good example of security architecture can be found in paper Pacheco et al. ( 2018 ) by Pacheco et al. ( 2018 ), which proposes a security framework for a smart water system. That paper displays security issues at most of the IoT layers and proposes security algorithms for these issues to make developers consider security early rather than an ad-hoc or afterthought manner.
Answering RQ2.3 What application domains have been addressed by the security patterns and architectures? From Table 2 we see that nine primary studies have presented the application of IoT security patterns/architectures for some specific IoT application domains. The specific IoT application domains can help our analysis in the way they elaborate on the issues and how to mitigate them. Explicitly mentioning IoT application domain has the tendency to show that the patterns can be applied in the domain and can address the requirements in this IoT domain. Some patterns could be more important for some specific domains. For example, for smart city applications, patterns for scalability is important. For e-health, patterns for privacy are important. The primary studies that do explicitly present IoT application domains would address more clearly the IoT-specific requirements or challenges. The domain-specific solutions are created for the domains mentioned, but they may still be applicable in other domains. However, these domains usually take the initiative to incorporate IoT, which explains why these areas have specific solutions before others. We also saw that many of these domain-specific studies had graphical figures describing their contribution to show how they work or the different layers of their architectures.
We consider that domain-specific contributions may not necessarily have a more significant impact on IoT security, but it is better portrayed when having a real case scenario or issue. Both the generic and specific domain contributions cover approximately three security concerns per paper, so they both stand approximately equally strong in security concerns coverage. We believe these domain-specific contributions are getting more attention, but it may still not be a better solution than the general solutions that can apply to more systems or handle more generic issues. It is still good to see more security patterns and architectures in real cases to better grasp the contribution and the issues around these domains.
Table 2 can give us some ideas on any difference in terms of addressing security and privacy concerns between the papers by academic authors and the papers authored by both academia and industry. The joint papers on average cover \(\sim 3,2\) concerns per paper, while the “academic-only” papers on average cover \(\sim 3,3\) concerns per paper. We see that both types of paper cover at least over half of our security concerns on average. To better compare the difference between academic-only papers and joint papers in terms of addressing security and privacy concerns, we visualize the number of papers addressing each concern in Fig. 7 . The first glance at Fig. 7 may give us an impression that the papers from academia have a broader coverage than the joint. This impression makes sense because academic-only papers are nearly three times more than joint papers. However, the number of academic-only papers addressing privacy (15) is five times the number of joint papers addressing privacy (three). Would this comparison imply that privacy (compared to other concerns) has gained more focus in academic-only papers than in industry-oriented papers? On the other hand, the number of academic-only papers addressing availability (eight) is four times the number of joint papers addressing availability (two). Would this comparison imply that availability has also gained more focus in academic-only papers than industry-oriented papers? The data that we have so far is not significant to make any strong statement to answer these questions. As previously mentioned, we do, however, want to highlight joint papers as more practical for industry. If we compare the amounts of academic and joint papers, we see that the number of joint papers is still low. We hope the number of joint papers will grow in the years to come with the current trend.
Difference between academic-only and joint papers in terms of security and privacy concerns
In terms of validation, implementation and execution testing, five (Portal et al. 2020 ; Karaarslan et al. 2020 ; Koshy et al. 2020 ; Attia et al. 2019 ; Pacheco et al. 2016 ) out of the nine domain-specific contributions do testing to verify their contribution in some form, while the generic domain contributions have 16 out of 24 papers doing testing, or some form of validation or analysis of a case. These numbers can be found in Table 4 representing “ Categorization of security pattern research ” section and “ IoT architecture ” section and by “testing”, we are referring to item C3 (research implementation/validation). We also see from this table that there are limited number of papers that discuss their purpose with their contribution. Four papers from the domain-specific category and 12 from the general domain category specified their purpose (item C1 ). However for describing their work with figures and diagrams we found 30 contributions (10 specific, 20 general) where in average the domain-specific studies have a higher ratio of including figures (item C2 ).
Table 4 also shows where the primary studies operate in the different layers of the IoT architecture presented in “ IoT architecture ” section. If we look at the numbers from the three-layer IoT architecture point of view, all three layers perception, network, and application have been almost completely covered by the different primary studies. However, the seven-layer IoT World Forum Reference Model of the IoT architecture can offer a closer view. We can see that the studies that explicitly address specific IoT application domains again have a higher average (4,33 layers per contribution) when it comes to layer coverage while general papers display a lower number (2,96 layers per contribution). In total, we see the coverage of 3,3 layers per contribution, which seems a little low considering there are seven layers in the architecture from the World Forum Reference Model (Juxtology 2018 ). In particular, we found that most of the primary studies do not work in all the layers, but rather operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have lower coverage in terms of the number of primary studies addressing IoT security challenges in those layers: Edge Computing ( L3 ), and especially, Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ).
Gaps and limitations (RQ3)
This section gives our answers to the RQ3.1 and RQ3.2 that are supported by the findings presented above. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? Although there is a spike in the number of primary studies on IoT security patterns and architectures recently as presented in our answer for RQ1.1, our analyses show that IoT security patterns and architectures research is still in its beginning stages. This topic is yet to bloom, both in the industrial and academic universes. There are fundamental gaps and open issues to be handled.
The last decade was only the beginning of research efforts
One of the main limitations is that research on security patterns is still relatively “young” for IoT domain and premature, e.g., in terms of addressing all the different levels of IoT architecture reference model as presented in Table 4 , proper documentation and usage areas, as well as usage examples. Before conducting the review, we expected to see how existing security patterns being applied/adopted for IoT, and even more if new security patterns specific for IoT had emerged. But, based on the results of our review so far, we can say that the last decade has only marked the beginning of the research effort in this direction. The lack of evaluation in use cases or application in case studies as presented in our answer for RQ2.3 is one of the indicators of the premature work in most of the primary studies. Most of the contributions in the primary studies would only be ranked at the low levels (less than level five) in terms of the technology readiness levels (TRL). Footnote 19 We believe that (empirical) evaluations on the application of security patterns in IoT can make a substantial positive impact if more contributed to this research area. Empirical studies can provide more insights for any potential adopters of patterns to create more secure systems, or at least find a proven solution for a common problem.
Security patterns have proven to be very valuable for practitioners, especially non-security experts to adopt and build secure (IT) systems (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ). We would expect a similar impact of using security patterns in building secure IoT systems. Security patterns can help to mitigate the lack of knowledge from developers without security expertise, who are often under time-to-market pressure and as a result may contribute to more breaches and malicious usage, leading to more catastrophic incidents. Because, security patterns consist of domain-independent time-proven security knowledge, and expertise, they should be helpful, especially for addressing such limitations early in the development of IoT systems. We believe that security patterns can continue to be very valuable for practitioners, especially non-security experts, in building secure IoT systems. It would be even more so with a systematic understanding of different security patterns for addressing the heterogeneity of the IoT domain that our study could be a starting point for more comprehensive IoT domains. In other words, new research efforts could aim at building a catalog of security (and privacy) patterns more specifically and systematically for IoT.
The lack of addressing IoT-specific security and privacy challenges
Compatibility and complexity issues in IoT are other limitations that make security patterns and architectures less practical. An IoT system often makes use of multiple devices connected to a system(s) via a network(s). For example, one device could use a of protocols to communicate between nearby networks and other protocols to communicate with the service provider via IP. The heterogeneity of various communication protocols often used in IoT raises more security issues, which even get worse for complex IoT systems. So far, we have found patterns and architectures for mostly general issues and some specific issues that should work for their stated purposes. However, we have not encountered research that fulfills both types of issues that security patterns and architectures handle. In other words, we have not seen any approach that proposes a (systematic) top-down application of security patterns, first at the architectural level, then to more low-level details for addressing specific challenges in the heterogeneity of IoT, for example sometimes ad-hoc network, and weak links caused by tiny IoT devices.
From the results (see Table 2 ), we found that the quantity of security pattern approaches is less than the number of security architectures for IoT, and way too few compared to the initial numbers of the search results displayed in Fig. 2 . The quantity of existing papers that directly address security patterns for IoT is very low comparing to the explosion of the IoT as estimated by Gartner. Footnote 20 From the papers found, very few had characterized the patterns or architectures accordingly to the taxonomy categorization we constructed or characterized clearly in what layers of the IoT World Forum Reference Model Footnote 21 the contribution tackles (Fig. 8 ). We would, therefore, recommend that further research that should address thoroughly and systematically security pattern aspects for IoT systems.
Contributions distributed over the seven layers (Juxtology 2018 )
The status of addressing the top ten most common vulnerabilities within IoT
We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ) as shown in Table 5 . This extraction was done to highlight more of this topic’s gaps to see how the existing contributions handle the top ten most common vulnerabilities within IoT (OWASP 2018 ). As we see from the extraction, vulnerabilities such as Insecure Network Services (I2), Insecure Ecosystem Interfaces (I3), and Insecure Data Transfer and Storage (I7) are the most covered vulnerabilities by the contributions. This spread of coverage is fair in terms of what the contributions present. Most of the solutions found are either in the communication part of the system or when interacting with multiple devices/systems. Most of the contributions are also descriptions proposing high-level architectural solutions and not detailing actual (physical) IoT products or devices. The other types of vulnerabilities, such as Weak, Guessable, or Hardcoded Passwords (I1), Insecure Default Settings (I9), Lack of Physical Hardening (I10), and so forth were not visible in the contributions of the primary studies. I2, I3, and I7 are appropriate vulnerabilities that these contributions should mitigate, however Insufficient Privacy Protection (I6) and Lack of Device Management (I8) should be more highlighted due to its natural occurrence within security patterns and architectures.
The need for new security patterns specifically for IoT
Other directions we recommend is to keep up the research on existing patterns and architectures, but also find out new security patterns specifically for IoT. The dominance of academia-only and a few joint collaboration in IoT security pattern research (see our answer to RQ1.3) suggests that there should be even more collaboration between academia and industry. Especially since the IoT market is blossoming and making the industry more aware, there should be approaches that are more practical and closer to the needs in the industry. This research should be both of research nature but should also aim to create an interest for industry and business owners. This way, we can get more test cases, gain more knowledge, and spread awareness around IoT security patterns in general. However, the ultimate goal of promoting IoT security patterns is to make it easier to improve and implement security features early in the development of IoT systems.
Related work
There have been some recent surveys focusing on different aspects of IoT engineering, from the deployment support (Nguyen et al. 2019 ) to actuation conflict management (Lavirotte et al. 2020 ). In Nguyen et al. ( 2019 ), the authors present the state of the art of IoT deployment approaches in which most approaches do not properly support software deployment and orchestration at the tiny IoT device level. Besides, trustworthiness aspects including security were not addressed properly in the existing approaches for IoT systems deployment and orchestration. The new challenges in the IoT domain can also be seen in the physical layer of IoT actuators. The SMS in Lavirotte et al. ( 2020 ) brings attention to the risk of actuation effects to safety and trustworthiness, and analyzes approaches for actuation conflicts management. However, these two recent surveys do not focus on security patterns for IoT.
There exist some other surveys that have addressed IoT security and IoT patterns, but none has systematically, specifically investigated security pattern approaches for IoT. Oracevic et al. ( 2017 ) surveyed IoT security. They want to shed light on this topic and spread awareness, with examples of IoT security solutions. The authors provide different measures on different levels to secure the systems but do not go into details. They also do not offer any form of architectures or patterns to solve common recurring problems for IoT security. Nguyen et al. ( 2015 ) has also reviewed security patterns-based approaches for new systems design and development. However, the reviewed approaches are not specific for IoT systems, which the focus of this work.
Washizaki et al. ( 2020 ) present a collection of papers that either describe IoT architectures or design patterns, or both. They also classify the patterns that are being used in detail as well as in which paper. They present a security column and specify which papers from their study have patterns that cover security. We looked through these papers, but not all of the papers did meet our criteria described in “ Inclusion and exclusion criteria ” section. The papers from Washizaki et al. ( 2020 ) that we analyzed and included as primary studies are Pape and Rannenberg ( 2019 ), Pahl et al. ( 2018 ), Lee and Law ( 2017 )) and Ntuli and Abu-Mahfouz ( 2016 ).
Reinfurt et al. ( 2016 ) give details of IoT patterns by investigating a large number of production-ready IoT offerings to extract recurring proven solution principles into patterns. These patterns show and describe how to help other individuals to understand different aspects of IoT, and also make it easier.
Qanbari et al. ( 2016 ) elaborates on how to design, build, and engineer applications for IoT systems and have created patterns to do these steps in an IoT system. They do not highlight security as one of their focus points, which is our main concern for this paper.
In general, these studies’ results not only address the functional aspects of IoT patterns but also some quality aspects, such as security and development, that we even considered in our work. However, they were not systematically and explicitly conducted to analyze the patterns and architectures for IoT security similar to our work. Note that we have clearly defined the scope of our SLR, which only considered peer-reviewed publications, not white papers from the industry. Thus, our SLR reports state of the art in IoT security pattern research, not including the state of practice in the industry.
Threats to validity
We mainly found the primary studies of this work from the database search process. The search features provided by the five online publication databases are very different from each other. We had to adapt our search string to make use of the provided search features of the publication databases. We tried to use the keywords and built search strings that were not too strict to obtain as many relevant papers as possible. However, it would be impossible to have perfect search strings for the database search process.
There is a possibility that we missed some studies that should have been included in the final set of primary studies. We have tried to mitigate possible missing primary studies of the database search process by the manual search process. While doing snowballing, we saw again some primary studies that we already found from the database search process. Removing the duplicates, we managed to get six more new primary studies that have not been found from the database search process. There were some other relevant papers from snowballing, but they finally did not pass our selection criteria. These few studies may have fulfilled our criteria but may have failed to detail what they did or did not detail enough to include them according to our criteria confidently. We ended our search and selection process in the beginning of December 2020, which means that our review does not completely cover all the publications in 2020, but a major part of them.
The primary studies that passed our selection criteria could still have limitations that make their contributions unreliable or flawed. Because many of the contributions do not have test cases or examples, it can be hard to know if the patterns and architectures do what they are supposed to. It also creates uncertainty regarding how good the patterns preserve or contain the security in already existing systems. To mitigate this risk, we conducted cross-checks between at least two reviewers for some papers in doubt to remove any papers that do not have enough scientific contributions according to our selection criteria.
Conclusions
In this paper, we have presented our systematic review on patterns and architectures for IoT security. After systematically recognizing and reviewing 36 primary studies out of thousands of relevant papers in this domain, we have discovered that there is a slight rise in the number of publications addressing security patterns and architectures in the two recent years. However, our analysis has shown that security patterns are relatively “young” for the IoT domain and we have found more papers with main contributions categorized as architectures rather than patterns. This indicates that more efforts are needed in terms of formalization, proper documentation and adoption. We have not seen any approaches that combine architectural patterns or even IoT security reference architectures with other design patterns. Similarly, we have not seen architectural patterns or IoT security reference architectures referring to any design pattern they would be composed of. This includes patterns at the IoT “weak links”: the network and IoT devices levels. Most of the primary studies do not work in all the seven layers of the IoT World Forum Reference Model for IoT architecture. They mainly operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have little coverage in terms of patterns and architectures for addressing IoT security challenges: Edge Computing ( L3 ), Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ). We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list.
New IoT systems development should concentrate more on tending to security, which can be improved with progressively relevant security patterns to apply and reuse. In other words, we need to promote the utilization of patterns for IoT security (and privacy) by design. To make security patterns for IoT approaches more viable, we consider the research collaboration between academia and industry is key in this domain. Security patterns in literature can be researched and applied in developing secure IoT systems with industrial context. Vice versa, experiences gained from securing industrial IoT systems can help to improve existing security patterns for IoT, or even new ones can emerge.
Availability of data and materials
All the data of our work is available in Google Drive https://drive.google.com/drive/folders/19CbTTYauf4ijpcSSlN0yySZLz8QIgscJ?usp=sharing .
https://www.idc.com/ .
NIS Directive, https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive .
A. Dasgupta, The Continuum: Big Data, Cloud & Internet of Things, IBM Internet of Things blog, 2017.
Gartner, The Death of IoT Security as You Know It, Gartner, 2017.
https://ieeexplore.ieee.org .
https://dlnext.acm.org .
https://sciencedirect.com/ .
http://apps.webofknowledge.com .
https://scopus.com .
https://www.springer.com .
https://iot-conference.org/iot2020/ .
https://hillside.net/conferences .
https://www.europlop.net/ .
https://conferences.computer.org/iciot/2019/ .
https://dl.acm.org/journal/tiot .
https://ieee-iotj.org/ .
Our search and selection process for the primary studies concluded in December 2020
Our search and selection process covers the period until December 2020.
The use of TRLs in the Horizon 2020 Work Programmes ( https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/support/faq/2890 ).
Gartner, November 2018 ( https://www.gartner.com/en/newsroom/press-releases/2018-11-07-gartner-identifies-top-10-strategic-iot-technologies-and-trends ).
Juxtology - IoT: Architecture ( https://www.m2mology.com/iot-transformation/iot-world-forum/ ).
Abbreviations
- Internet of Things
Alphand O, Amoretti M, Claeys T, Dall’Asta S, Duda A, Ferrari G, Rousseau F, Tourancheau B, Veltri L, Zanichelli F (2018) IoTChain: a blockchain security architecture for the Internet of Things, vol. 2018-April, pp 1–6. https://doi.org/10.1109/WCNC.2018.8377385
Attia O, Khoufi I, Laouiti A, Adjih C (2019) An IoT-blockchain architecture based on hyperledger framework for healthcare monitoring application. In: 2019 10th IFIP international conference on new technologies, mobility and security (NTMS), pp 1–5. https://doi.org/10.1109/NTMS.2019.8763849
Borgia E, Gomes DG, Lagesse B, Lea RJ, Puccinelli D (2016) Special issue on “internet of things: research challenges and solutions”. Comput Commun 89:1–4
Ciccozzi F, Crnkovic I, Di Ruscio D, Malavolta I, Pelliccione P, Spalazzese R (2017) Model-driven engineering for mission-critical iot systems. IEEE Softw 34(1):46–53
Article Google Scholar
Covington MJ, Carskadden R (2013) Threat implications of the internet of things. In: 2013 5th international conference on cyber conflict (CYCON 2013), pp 1–12
Create-IoT (2018) Deliverable D6.02—Recommendations for commonalities and interoperability profiles of IoT platforms. https://european-iot-pilots.eu/wp-content/uploads/2018/11/D06_02_WP06_H2020_CREATE-IoT_Final.pdf . Accessed 30 Sept 2021
Dhieb N, Ghazzai H, Besbes H, Massoud Y (2020) Scalable and secure architecture for distributed iot systems. In: 2020 IEEE technology engineering management conference (TEMSCON), pp 1–6. https://doi.org/10.1109/TEMSCON47658.2020.9140108
Dougherty C, Sayre K, Seacord RC, Svoboda D, Togashi K (2009) Secure design patterns. Technical report, Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst
Durresi M, Subashi A, Durresi A, Barolli L, Uchida K (2019) Secure communication architecture for internet of things using smartphones and multi-access edge computing in environment monitoring. J Ambient Intell Humaniz Comput 10(4):1631–1640. https://doi.org/10.1007/s12652-018-0759-6
Federal Trade Commission (1999) How to comply with the privacy of consumer financial information rule of the Gramm-Leach-Bliley Act. https://www.ftc.gov/tips-advice/business-center/guidance/how-comply-privacy-consumer-financial-information-rule-gramm . Accessed 29 Sept 2020
Fernandez-Buglioni E (2013) Security patterns in practice: designing secure architectures using software patterns. Wiley, Hoboken
Google Scholar
Ferry N, Brataas G, Rossini A, Chauvel F, Solberg A (2014) Towards bridging the gap between scalability and elasticity. CLOSER 10:0004975307460751
Fysarakis K, Spanoudakis G, Petroulakis N, Soultatos O, Broring A, Marktscheffel T (2019) Architectural patterns for secure iot orchestrations. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766425
Gamma E, Helm R, Johnson R, Vlissides JM (1994) Design patterns: elements of reusable object-oriented software, 1st edn. Addison-Wesley Professional, Boston
MATH Google Scholar
Garcia-Morchon O, Keoh SL, Kumar S, Moreno-Sanchez P, Vidal-Meca F, Ziegeldorf JH (2013) Securing the ip-based internet of things with hip and dtls. In: Proceedings of the sixth ACM conference on security and privacy in wireless and mobile networks. WiSec ’13. Association for Computing Machinery, New York, NY, USA, pp 119–124. https://doi.org/10.1145/2462096.2462117
Goncalves F, Macedo J, Nicolau MJ, Santos A (2013) Security architecture for mobile e-health applications in medication control. In: 2013 21st international conference on software, telecommunications and computer networks—(SoftCOM 2013), pp 1–8. https://doi.org/10.1109/SoftCOM.2013.6671901
IEEE SA, S.A. (2018) IEEE draft standard for an architectural framework for the internet of things (IoT). IEEE P2413/D0.4.5, December 2018, pp 1–264
Jerald AV, Rabara SA, Arun Gnana Raj A (2019) Secured architecture for integrated iot enabled smart services. Int J Recent Technol Eng 8(3):7384–7393. https://doi.org/10.35940/ijrte.C6145.098319
Juxtology (2018) IoT: architecture. https://www.m2mology.com/iot-transformation/iot-world-forum/ . Accessed 27 July 2020
Karaarslan E, Karabacak E, Cetinkaya C (2020) Design and implementation of sdn-based secure architecture for iot-lab. In: Hemanth DJ, Kose U (eds) Artificial intelligence and applied mathematics in engineering problems. Springer, Cham, pp 877–885
Chapter Google Scholar
Karmakar KK, Varadharajan V, Nepal S, Tupakula U (2019) SDN enabled secure IoT architecture, pp 581–585. https://www.scopus.com/inward/record.uri?eid=2-s2.0-85066971444&partnerID=40&md5=c0f52e2ce49d38dad5d181190e28e795
Kitchenham BA, Charters S (2007) Guidelines for performing systematic literature reviews in software engineering. Technical Report EBSE 2007-001, Keele University and Durham University Joint Report . https://doi.org/10.1145/2372233.2372235
Kitchenham BA, Budgen D, Brereton OP (2011) Using mapping studies as the basis for further research—a participant-observer case study. Inf Softw Technol 53(6):638–651. https://doi.org/10.1016/j.infsof.2010.12.011 ( Special Section: Best papers from the APSEC )
Koo J, Oh SR, Lee SH, Kim YG (2020) Security architecture for cloud-based command and control system in iot environment. Appl Sci 10:1035. https://doi.org/10.3390/app10031035
Koshy P, Babu S, Manoj BS (2020) Sliding window blockchain architecture for internet of things. IEEE Internet Things J 7(4):3338–3348. https://doi.org/10.1109/JIOT.2020.2967119
Kuhn DR, Hu VC, Polk WT, Chang S-J (2001) NIST SP 800-32, introduction to public key technology and the federal PKI infrastructure. National Institute of Standards & Technology, p 54. https://doi.org/10.6028/NIST.SP.800-32
Lavirotte S, Rocher G, Tigli J, Gonnin T (2020) IoT-based systems actuation conflicts management towards DevOps: a systematic mapping study. In: Proceedings of the 5th international conference on internet of things, big data and security, vol 1. IoTBDS, pp 227–234. SciTePress. https://doi.org/10.5220/0009355102270234 . INSTICC
Lee W, Law P (2017) A case study in applying security design patterns for iot software system. In: 2017 international conference on applied system innovation (ICASI), pp 1162–1165. https://doi.org/10.1109/ICASI.2017.7988402
Lessa dos Santos G, Guimaraes VT, da Cunha Rodrigues G, Granville LZ, Tarouco LMR (2015) A dtls-based security architecture for the internet of things. In: 2015 IEEE symposium on computers and communication (ISCC), pp 809–815. https://doi.org/10.1109/ISCC.2015.7405613
Nguyen PH, Yskout K, Heyman T, Klein J, Scandariato R, Le Traon Y (2015) Sospa: a system of security design patterns for systematically engineering secure systems. In: 2015 ACM/IEEE 18th international conference on model driven engineering languages and systems (MODELS), pp 246–255. https://doi.org/10.1109/MODELS.2015.7338255
Nguyen PH, Kramer M, Klein J, Traon YL (2015) An extensive systematic review on the model-driven development of secure systems. Inf Softw Technol 68:62–81. https://doi.org/10.1016/j.infsof.2015.08.006
Nguyen PH, Ali S, Yue T (2017) Model-based security engineering for cyber-physical systems: a systematic mapping study. Inf Softw Technol 83:116–135. https://doi.org/10.1016/j.infsof.2016.11.004
Nguyen P, Ferry N, Erdogan G, Song H, Lavirotte S, Tigli J, Solberg A (2019) Advances in deployment and orchestration approaches for IoT—a systematic review. In: 2019 IEEE international congress on Internet of Things (ICIOT), pp 53–60. https://doi.org/10.1109/ICIOT.2019.00021
Ntuli N, Abu-Mahfouz A (2016) A simple security architecture for smart water management system. Procedia Comput Sci 83:1164–1169. https://doi.org/10.1016/j.procs.2016.04.239 . The 7th international conference on ambient systems, networks and technologies (ANT 2016)/The 6th international conference on sustainable energy information technology (SEIT-2016)/Affiliated workshops
Office for Civil Rights (2013) Summary of the HIPAA security rule. https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html . Accessed 29 Sept 2020
Oracevic A, Dilek S, Ozdemir S (2017) Security in internet of things: a survey. In: 2017 international symposium on networks, computers and communications (ISNCC), pp 1–6 . https://doi.org/10.1109/ISNCC.2017.8072001
OWASP (2018) Internet of Things (IoT) Top 10 2018. https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf . Accessed 30 Sept 2020
Pacheco J, Ibarra D, Vijay A, Hariri S (2018) IoT security framework for smart water system. In: 2017 IEEE/ACS 14th international conference on computer systems and applications (AICCSA), vol 2017-October, pp 1285–1292. https://doi.org/10.1109/AICCSA.2017.85
Pacheco J, Satam S, Hariri S, Grijalva C, Berkenbrock H (2016) IoT security development framework for building trustworthy smart car services, pp 237–242. https://doi.org/10.1109/ISI.2016.7745481
Pacheco J, Tunc C, Hariri S (2019) Security framework for IoT cloud services, vol 2018-November . https://doi.org/10.1109/AICCSA.2018.8612808
Pahl C, Ioini NE, Helmer S, Lee B (2018) An architecture pattern for trusted orchestration in iot edge clouds. In: 2018 third international conference on fog and mobile edge computing (FMEC), pp 63–70. https://doi.org/10.1109/FMEC.2018.8364046
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: Stern J (ed) Advances in cryptology—EUROCRYPT ’99. Springer, Berlin, Heidelberg, pp 223–238
Pape S, Rannenberg K (2019) Applying privacy patterns to the internet of things’ (iot) architecture. Mobile Netw Appl 24(3):925–933. https://doi.org/10.1007/s11036-018-1148-2
Park C (2020) Security architecture for secure multicast coap applications. IEEE Internet Things J 7(4):3441–3452. https://doi.org/10.1109/JIOT.2020.2970175
Perera C, Barhamgi M, Bandara AK, Ajmal M, Price B, Nuseibeh B (2020) Designing privacy-aware internet of things applications. Inf Sci 512:238–257. https://doi.org/10.1016/j.ins.2019.09.061
Petersen K, Vakkalanka S, Kuzniarz L (2015) Guidelines for conducting systematic mapping studies in software engineering: an update. Inf Softw Technol 64:1–18
Petroulakis NE, Lakka E, Sakic E, Kulkarni V, Fysarakis K, Somarakis I, Serra J, Sanabria-Russo L, Pau D, Falchetto M, Presenza D, Marktscheffel T, Ramantas K, Mekikis P, Ciechomski L, Waledzik K (2019) Semiotics architectural framework: End-to-end security, connectivity and interoperability for industrial iot. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766399
Porambage P, Ylianttila M, Schmitt C, Kumar P, Gurtov A, Vasilakos AV (2016) The quest for privacy in the internet of things. IEEE Cloud Comput 3(2):36–45
Portal G, de Matos E, Hessel F (2020) An edge decentralized security architecture for industrial iot applications. In: 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), pp 1–6. https://doi.org/10.1109/WF-IoT48130.2020.9221176
Qanbari S, Pezeshki S, Raisi R, Mahdizadeh S, Rahimzadeh R, Behinaein N, Mahmoudi F, Ayoubzadeh S, Fazlali P, Roshani K, Yaghini A, Amiri M, Farivarmoheb A, Zamani A, Dustdar S (2016) IoT design patterns: computational constructs to design, build and engineer edge applications. In: 2016 IEEE first international conference on Internet-of-Things design and implementation (IoTDI), pp 277–282. https://doi.org/10.1109/IoTDI.2015.18
Rajmohan T, Nguyen PH, Ferry N (2020) Research landscape of patterns and architectures for iot security: a systematic review. In: 2020 46th Euromicro conference on software engineering and advanced applications (SEAA), pp 463–470. https://doi.org/10.1109/SEAA51224.2020.00079
Reinfurt L, Breitenbücher U, Falkenthal M, Leymann F, Riegg A (2016) Internet of things patterns. In: Proceedings of the 21st European conference on pattern languages of programs. EuroPlop ’16. ACM, New York, NY, USA. https://doi.org/10.1145/3011784.3011789
Richa E (2021) Iot: security issues and challenges. In: Senjyu T, Mahalle PN, Perumal T, Joshi A (eds) Information and communication technology for intelligent systems. Springer, Singapore, pp 87–96
Robles Enciso A, Zarca A, Garcia Carrillo D, Hernandez-Ramos J, Bernal Bernabe J, Skarmeta A, Matheu Garcia SN (2020) Security architecture for defining and enforcing security profiles in dlt/sdn-based iot systems. Sensors 20:1882. https://doi.org/10.3390/s20071882
Roman R, Najera P, Lopez J (2011) Securing the internet of things. Computer 44(9):51–58
Ross R, McEvilley M, Oren J (2016) NIST SP 800-160, systems security engineering considerations for a multidisciplinary approach in the engineering of trustworthy secure systems. National Institute of Standards & Technology, p 243. https://doi.org/10.6028/NIST.SP.800-160v1
Schmidt DC, Buschmann F (2003) Patterns, frameworks, and middleware: their synergistic relationships. In: 25th international conference on software engineering, 2003. Proceedings, pp 694–704
Schneier B (2017) Iot security: what’s plan b? IEEE Secur Privacy 15(05):96. https://doi.org/10.1109/MSP.2017.3681066
Schumacher M, Fernandez-Buglioni E, Hybertson D, Buschmann F, Sommerlad P (2013) Security patterns: integrating security and systems engineering. Wiley, Hoboken
Schuß M, Iber J, Dobaj J, Kreiner C, Boano CA, Römer K (2018) Iot device security the hard(ware) way. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 20–1204. https://doi.org/10.1145/3282308.3282329
Steel C, Nagappan R (2006) Core security patterns: best practices and strategies for J2EE”, web services, and identity management. Pearson Education, London
Syed MH, Fernandez EB, Moreno J (2018) A misuse pattern for ddos in the iot. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 34–1345. https://doi.org/10.1145/3282308.3282343
Tiburski RT, Moratelli CR, Johann SF, Neves MV, Matos ED, Amaral LA, Hessel F (2019) Lightweight security architecture based on embedded virtualization and trust mechanisms for iot edge devices. IEEE Commun Mag 57(2):67–73. https://doi.org/10.1109/MCOM.2018.1701047
Tran NK, Sheng QZ, Babar MA, Yao L (2017) Searching the web of things: state of the art, challenges, and solutions. ACM Comput Surv (CSUR) 50(4):55
Ur-Rehman O, Zivic N (2015) Secure design patterns for security in smart metering systems. In: 2015 IEEE European modelling symposium (EMS), pp 278–283. https://doi.org/10.1109/EMS.2015.49
Vijayakumaran C, Senthil M, Manickavasagam B (2020) A reliable next generation cyber security architecture for industrial internet of things environment. Int J Electr Comput Eng: IJECE 10:387. https://doi.org/10.11591/ijece.v10i1.pp387-395
Vithya Vijayalakshmi A, Arockiam L (2020) A secured architecture for iot healthcare system. In: Pandian AP, Senjyu T, Islam SMS, Wang H (eds) Proceeding of the international conference on computer networks, big data and IoT (ICCBI-2018). Springer, Cham, pp 904–911
Vučinić M, Tourancheau B, Rousseau F, Duda A, Damon L, Guizzetti R (2015) Oscar: object security architecture for the internet of things. Ad Hoc Netw 32:3–16. https://doi.org/10.1016/j.adhoc.2014.12.005 ( Internet of Things security and privacy: design methods and optimization )
Washizaki H, Ogata S, Hazeyama A, Okubo T, Fernandez EB, Yoshioka N (2020) Landscape of architecture and design patterns for iot systems. In: IEEE Internet of Things Journal 2020 (early Access), p 1. https://doi.org/10.1109/JIOT.2020.3003528
Washizaki H, Xia T, Kamata N, Fukazawa Y, Kanuka H, Yamaoto D, Yoshino M, Okubo T, Ogata S, Kaiya H, Kato T, Hazeyama A, Tanaka T, Yoshioka N, Priyalakshmi G (2018) Taxonomy and literature survey of security pattern research. In: 2018 IEEE conference on application, information and network security (AINS), pp 87–92. https://doi.org/10.1109/AINS.2018.8631465
Williams-Grut O (2018) Hackers once stole a casino’s high-roller database through a thermometer in the lobby fish tank. https://www.businessinsider.com/hackers-stole-a-casinos-database-through-a-thermometer-in-the-lobby-fish-tank-2018-4?r=US&IR=T . Accessed 20 Aug 2020
Witti M, Konstantas D (2018) A secure and privacy-preserving internet of things framework for smart city. In: Proceedings of the 6th international conference on information technology: IoT and smart city. ICIT 2018. Association for Computing Machinery, New York, NY, USA, pp 145–150. https://doi.org/10.1145/3301551.3301607
Wohlin C (2014) Guidelines for snowballing in systematic literature studies and a replication in software engineering. In: Proceedings of the 18th international conference on evaluation and assessment in software engineering. ACM, p 38
Wright M (2020) Default passwords banned for smart devices as part of hacking crackdown. https://www.telegraph.co.uk/news/2020/01/27/default-passwords-banned-smart-devices-part-hacking-crackdown/ . Accessed 20 June 2020
Yampolskiy M, Horvath P, Koutsoukos XD, Xue Y, Sztipanovits J (2013) Taxonomy for description of cross-domain attacks on cps. In: Proceedings of the 2nd ACM international conference on high confidence networked systems. HiCoNS ’13. Association for Computing Machinery, New York, NY, USA, pp 135–142. https://doi.org/10.1145/2461446.2461465
Ye F, Qian Y (2017) A security architecture for networked Internet of Things devices, vol 2018-January, pp 1–6. https://doi.org/10.1109/GLOCOM.2017.8254021
Yskout K, Heyman T, Scandariato R, Joosen W (2006) A system of security patterns. CW Reports. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.142.4538
Zhang J, Jin H, Gong L, Cao J, Gu Z (2019) Overview of IoT security architecture, pp 338–345. https://doi.org/10.1109/DSC.2019.00058
Zhu X, Badr Y (2018) Fog computing security architecture for the internet of things using blockchain-based social networks. In: 2018 IEEE international conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), pp 1361–1366
Download references
Acknowledgements
The research leading to these results has partially received funding from the European Commission's H2020 Programme under the grant agreement numbers 958363 (Dat4.ZERO), and 958357 (InterQ).
Author information
Authors and affiliations.
Capgemini, Oslo, Norway
Tanusan Rajmohan
SINTEF, Oslo, Norway
Phu H. Nguyen
Université Côte d’Azur, I3S/INRIA Kairos, Sophia Antipolis, France
Nicolas Ferry
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to all the steps of conducting this work and writing this manuscript. All the authors read and approved the final manuscript.
Corresponding author
Correspondence to Phu H. Nguyen .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rajmohan, T., Nguyen, P.H. & Ferry, N. A decade of research on patterns and architectures for IoT security. Cybersecurity 5 , 2 (2022). https://doi.org/10.1186/s42400-021-00104-7
Download citation
Received : 30 April 2021
Accepted : 17 November 2021
Published : 05 January 2022
DOI : https://doi.org/10.1186/s42400-021-00104-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Architecture
Internet of Things - Open Access Research
Articles, call for papers, journals and more on iot.

Take a look at our open access journals covering the Internet of Things, browse selected freely available research and submit your IoT manuscript to our SpringerOpen journals.
Selected IoT Article Collections

Research and Challenges of Wireless Networks in Internet of Things
Published in EURASIP Journal on Wireless Communications and Networking

Recent Advances in Internet of Things Security and Privacy
Published in EURASIP Journal on Wireless Communications and Networking.
Internet of Things Article Highlights
Read more open access articles here
Featured Open Access Journals covering IoT




Find more open access journals here
Submit your IoT manuscript

Are you looking for a journal to submit your own Internet of Things research to? Read our tips on how to find the right journal here:
Register with us and stay up to date

As a registered user you can:
• Add article alerts from all SpringerOpen journals
• Easily manage your article alerts
• Receive regular news from your preferred subject areas
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Elsevier - PMC COVID-19 Collection

Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future
Sandro nižetić.
a LTEF-Laboratory for Thermodynamics and Energy Efficiency, Faculty of Electrical Engineering, Mechanical Engineering and Naval Architecture, University of Split, Rudjera Boskovica 32, 21000, Split, Croatia
Petar Šolić
b Department of Electronics, Faculty of Electrical Engineering, Mechanical Engineering and Naval Architecture, University of Split, Rudjera Boskovica 32, 21000, Split, Croatia
Diego López-de-Ipiña González-de-Artaza
c Faculty of Engineering, DeustoTech - Fundación Deusto, Universidad de Deusto, Despacho 545 Avda, Universidades 24, 48007, Bilbao, Spain
Luigi Patrono
d Department of Innovation Engineering, University of Salento, Ecotekne Campus - S.P. 6, Lecce, Monteroni, 73100, LECCE, LE, Italy
The rapid development and implementation of smart and IoT (Internet of Things) based technologies have allowed for various possibilities in technological advancements for different aspects of life. The main goal of IoT technologies is to simplify processes in different fields, to ensure a better efficiency of systems (technologies or specific processes) and finally to improve life quality. Sustainability has become a key issue for population where the dynamic development of IoT technologies is bringing different useful benefits, but this fast development must be carefully monitored and evaluated from an environmental point of view to limit the presence of harmful impacts and ensure the smart utilization of limited global resources. Significant research efforts are needed in the previous sense to carefully investigate the pros and cons of IoT technologies. This review editorial is partially directed on the research contributions presented at the 4th International Conference on Smart and Sustainable Technologies held in Split and Bol, Croatia, in 2019 (SpliTech 2019) as well as on recent findings from literature. The SpliTech2019 conference was a valuable event that successfully linked different engineering professions, industrial experts and finally researchers from academia. The focus of the conference was directed towards key conference tracks such as Smart City, Energy/Environment, e-Health and Engineering Modelling. The research presented and discussed at the SpliTech2019 conference helped to understand the complex and intertwined effects of IoT technologies on societies and their potential effects on sustainability in general. Various application areas of IoT technologies were discussed as well as the progress made. Four main topical areas were discussed in the herein editorial, i.e. latest advancements in the further fields: (i) IoT technologies in Sustainable Energy and Environment, (ii) IoT enabled Smart City, (iii) E-health – Ambient assisted living systems (iv) IoT technologies in Transportation and Low Carbon Products. The main outcomes of the review introductory article contributed to the better understanding of current technological progress in IoT application areas as well as the environmental implications linked with the increased application of IoT products.
Graphical abstract

1. Introduction
With rising technological developments in society, new possibilities have occurred and that could simplify our daily life and provide more efficient services or production processes. Digitalization has allowed ‘‘smart’’ ( Zheng et al., 2019 ) to become the epicentre of already ongoing technological developments. In fact, IoT technologies are nowadays assumed to be one of the key pillars of the fourth industrial revolution due to significant potential in innovations and useful benefits for the population. On the other side, each development utilizes limited resources leaving behind different environmental footprints, ( Li et al., 2020a ), especially different kinds of pollutants, ( Zeinalnezhad et al., 2020 ). Internet of things (IoT) based technologies bring a completely new perspective on the further progress of various fields, such as for instance in engineering, ( Zaidan and Zaidan, 2020 ), agriculture ( Farooq et al., 2020 ), or medicine ( Salagare and Prasad, 2020 ), and in other fields that have not been explored yet. Some potential application areas in IoT technologies are still unknown or insufficiently clear on how to approach them which is an evident indication that more intense research activity should be conducted in this challenging field towards new and important potential benefits for society. Therefore, the relevance and importance of IoT technologies in future terms are more than clear and should play an important role.
The rise of IoT technologies is currently intense and according to projections for the next 10 years, over 125 ·10 9 IoT devices are expected to be connected, ( Techradar, 2019 ). The expected investments in IoT technologies are also high with expectations being over 120 ·10 9 USD by 2021, with a compound annual growth rate of about 7.3%, ( Forbes, 2018 ). The general present market structure of IoT technologies is presented in Fig. 1 , where it is evident that the majority of the market is focused on smart cities and industrial IoT.

General market structure of IoT technologies ( Nižetić et al., 2019 ).
If recent projects in IoT technologies are being analysed than most of them are in the field of smart cities and industrial IoT. Other significant potentials are connected buildings, connected cars and energy segments ( Forbes, 2018 ), but lower than the first mentioned fields. It is also found that the most rising trend in the number of IoT projects currently is as expected in smart cities, connected health and smart supply chain segments, with an annual rise over 30% in the EU and USA. Industrial IoT, connected cars and agriculture segments has recorded a decrease in the number of realized projects, i.e. over 25% in the USA and EU, ( Forbes, 2018 ). From a perspective of high upcoming population pressure on cities and because a population of almost 11 ·10 9 is expected by the end of the century ( Pewresearch, 2019 ), the smart city concept could become a vital one to allow for a normal operation of highly populated cities.
In order to support the rapid technical development of IoT technologies, as well as novel potential applications areas, specific technical issues would need to be resolved, ( Techradar, 2019 ). One of the main issues is associated with the development of different tools for the monitoring of network operations ( Kakkavas et al., 2020 ), then issues with security tools and their management, ( Conti et al., 2020 ), issues with software bugs, demanding maintenance of IoT networks, and finally security issues related to IoT networks, ( Almusaylim et al., 2020 ). The important problem linked with the efficient implementation of IoT technologies is linked with the available speed and coverage of wireless networks (Wi-Fi), where expectations are high due to noticeable increases in Wi-Fi network coverage in the period of 2017–2022 as well as increases in Wi-Fi speed Fig. 2 . In a global sense, increases in Wi-Fi speed are expected for more than a factor of two, i.e. from about 24 Mbps to more than 54 Mbps. The most intense increase in Wi-Fi speed is expected in the Asian region, ( Zdnet, 2018 ).

Expected increase in global Wi-Fi speeds in period of 2017–2022 ( Zdnet, 2018 ),
The lowest Wi-Fi speed is noticeable in the Latin America and Middle East&Africa regions, which are an indication of potential problems for the efficient implementation of IoT products or novel more advanced upcoming technologies.
An increased implementation of IoT technologies would lead to a more intense utilization of fossil technologies to ensure the necessary energy supply for IoT production lines. The production of electronic equipment is causing potentially unbalanced waste of limited metals and resources in general, which could become a critical issue in the long run. Unfortunately, the recycling rate of electronic waste is low and currently in the amount of about 20% ( Thebalancesmb, 2020 ) which makes matters questionable regarding the available resource capacity to produce IoT products when taking into accounts the rising market demands. The production of electronic gadgets has led to the consumption of various chemicals, water and finally fossil fuels that have all left environmental impacts. As already tackled, different metals are also being used to produce electronics such as copper, silver, gold, palladium etc. One of the major issues is the led content in e-waste and its severe impact to the environment. Recycling in the previous sense is very important, where the present recycling rate of electronic equipment is certainly not sufficient and must be increased. Globally, the annual rise of the recycling rate ranges from about 4% to 5% ( Thebalancesmb, 2020 ). The legislation related to the e-waste is one of the main drawbacks since more than 50% of world population is still not well covered with proper legislation related to e-waste, ( Globalewaste, 2017 ), which is preventing the further development of e-waste facilities. The market value of raw materials from e-waste is estimated to be more than 50·10 9 Euros, ( Globalewaste, 2017 ). Certainly, more strategic and targeted actions are needed in the e-waste issue to secure a more balanced and sustainable development of IoT technologies. Overall, the annual generation of e-waste is more than 44·10 9 metric tonnes, which is equivalent to more than 6 kg per inhabitant annually, ( Globalewaste, 2017 ). A potential exists and must be better utilized to ensure a sufficient quantity of valuable raw resources.
It should be highlighted that there is no doubt in what IoT technologies would bring to the table, such as various useful benefits to society and an overall improvement in life quality. Each technology has specific issues and drawbacks that need to be detected and closely investigated on time, since IoT technologies have the potential to change our lives and habits. Several important facts need to be emphasized when addressing IoT technologies to be able to understand the long-term effects associated with the fast development of IoT:
- - IoT technologies have caused an increase in the utilization of limited resources or raw materials where some of them have become rare or are already rare (for instance, specific precious metals for electronics),
- - The prices of electronic devices have become more acceptable, which means an increase in production volume, finally more resources are being utilized. A rebound effect is possible in that sense,
- - The long term environmental impacts of IoT technologies are unknown. A noticeable amount of energy would be needed to support the production and operation of IoT devices,
- - An increase in electronic waste is expected due to the large estimated number of IoT based devices in the near future,
- - In some sectors, IoT technologies could have social impacts due to the reduced necessity for labour and limitation of direct social contacts, which is vital and an important aspect for each human being.
The main point of the above raised issues is not to indicate and create a negative attitude towards IoT technologies but to carefully analyze the overall aspects in order to secure a smart and sustainable development of IoT technologies, which are a valuable opportunity for humanity.
1.1. Necessity for smart technologies
The world is rapidly changing, i.e. developing in a technological sense and is being driven by the present economic system globally. Unfortunately, each technological development has got its price, which can be sensed through the intense utilization of limited fossil-based resources and the production of various impacts to the environment, ( Chen et al., 2020a ). The population is constantly growing with an annual rate of about 1.1% per year with the current population being over 7.7·10 9 ( Data.worldbank, 2020 ). As previously addressed, the population concentration is in cities and according to UN projections, about 68% of the population will be living in cities by 2050, ( UN, 2018 ). A significant infrastructure pressure is expected in cities due to boosted urbanization, thus novel technological solutions would be key to secure the normal operation of cities in the given complex and demanding circumstances. In the previous sense, the general application of IoT and smart technologies would have an important role and could help to bridge some major infrastructure related issues in cities. The necessity for IoT technologies is closely linked with ongoing technological advancements and digitalization where a variety of different electronic products need to be somehow connected in a useful manner. There is a necessity for more efficient services and flexible processes in general, which could be obtained with the proper implementation of IoT technologies. IoT technologies have allowed for a variety of efficient services and smart networking, applications or devices that can ensure useful synergic effects and produce benefits. The major advantage of IoT technologies is their connectivity aspect that has enormous potential, Fig. 3 .

General structure of IoT network and connectivity ( Zhang et al., 2018 ).
Various benefits are possible and would be gradually integrated in our lives thorough upcoming years in different application areas and will be briefly discussed in the upcoming section of the introductory review editorial.
1.2. Application areas
The application areas of IoT are various and based on current available technological solutions, the most represented application sectors are shown in Fig. 4 . The most important and most progressing application areas of IoT are related to the industry ( Osterrieder et al., 2020 ) and smart city concept ( Sivanageswara Rao et al., 2020 ), with respect to the number of realized projects.

Application areas of IoT technologies.
The transportation ( Porru et al., 2020 ), smart energy management in buildings ( Douglas et al., 2020 ) or management of power networks ( Martín-Lopo et al., 2020 ), as well as the agriculture sector ( Villa-Henriksen et al., 2020 ) are also promising, having significant potential.
The development of specific IoT application areas strongly depends from several key factors such as:
- - general available advancements in electronic components,
- - available software solutions and user friendly surrounding,
- - solutions related to sensor technologies and data acquisition,
- - quality of network, i.e. network connectivity and infrastructure,
- - sufficient energy supply for production and operation of IoT devices.
In the continuation of the review editorial, some key IoT application areas will be briefly addressed together with the main developments and current challenges.
1.2.1. IoT in industry
The application of IoT technologies in industrial applications would allow for an increase in efficiency regarding the production process and would ensure more efficient communication and networking between operators and machines, Fig. 5 . Finally, it would allow for more competitive companies on the market with more efficient quality control with a minimization in losses. A critical feature would be the development, design and integration of various useful sensors in the industrial applications ( Li et al., 2020b ), to form integral and effective management systems. More intense research efforts are needed towards an efficient application of IoT technologies in the industry and to better understand how IoT technologies could be implemented in specific industries where benefits would be possible. Progress is crucial in the sense of how to connect different industrial sensors, use and process the collected various data to enable enhanced industrial processes, i.e. ensue for instance smart IoT based Computer-Integrated Manufacturing, ( Chen et al., 2020b ).

General concept of IoT industrial application ( Aazam et al., 2018 ).
1.2.2. IoT in smart city concept
The role of IoT technologies in the smart city concept ( Janik et al., 2020 ) is crucial to bridge the already mentioned global infrastructural challenges in cities, which are linked with the current increase of population in cities. IoT technologies in smart cities would enable the utilization of different devices, which would increase the life quality in cities as well as the efficiency of different daily services such as transportation, security (surveillance), smart metering, smart energy systems, smart water management, etc. Different sensing devices would receive information, which would be processed towards efficient and useful solutions. The main benefit of IoT technologies in smart cities would be directed to the early detection of different problems or infrastructural faults (such as issues with traffic jams, energy supply, water shortage, security incidents, etc.). In smart cities, many sensors are installed and linked with many other devices over the internet which gives information to the users as for instance parking spaces, any malfunctions, electrical failure and many other issues. Developing these technologies would help in leading the cities towards smart grids, smart healthcare, smart warehouses, smart transportation, smart waste management, smart communities, etc. Different implementation challenges towards the smart city concept exists, Fig. 6 and should be solved for various applications, ( Fig. 7 ).

Different challenges in Smart City concept ( Bhagya et al., 2018 ).

Various smart home management systems ( Zhou et al., 2016 ).
The most present implementation challenges are linked with the efficient integration of different sensing technologies, development of a suitable network infrastructure, education of population, investigation of the sustainability aspect, such as carbon footprint, etc.
The application of IoT technologies in smart homes, ( Moniruzzaman et al., 2020 ), within the smart city concept allows for an increase in the life quality within residential facilities, bringing novel and attractive technological solutions. Both, energy and fund savings could be reached with more efficient time management, which is a valuable feature in our present economic system. Different control options are possible within the smart home concept and enable an efficient integration of renewable energy technologies in homes ( Stavrakas and Flamos, 2020 ), and their efficient balancing (efficient supply and demand).
1.2.3. IoT in agriculture
Efficient agriculture production is a necessity for our population to prevent the potential lack of food resources in future terms caused by different factors, ( Hussain et al., 2020 ). The first factor is constant population growth, as already emphasized, the second is linked with climate change issues ( Yang et al., 2020 ), which is causing a reduction in the yields of important crops, or some areas are even becoming unsuitable for efficient agriculture production. The food waste issue is one of the major problems ( Keng et al., 2020 ), since it has become a global problem, especially in developed economies. It is estimated that more than 28% of available agriculture areas is ‘‘reserved’’ for food waste and unfortunately more than 800·10 6 people are currently hungry, ( Fao.org, 2020 ). The implementation of IoT technologies in agriculture can certainly help to secure sufficient food demands and increase the efficiency of agricultural production processes in general. Various useful data about crops could be collected and used for yield monitoring and the detection of potential diseases in advance that can significantly reduce the yields of specific crops. The monitoring of soil and nutrients would rationalize agricultural production processes and lead to water savings that are precious in some specific geographical regions, which could be utilized through smart irrigation systems, ( Xin et al., 2020 ). A more precise seeding could also be ensured and fertility crop management in general, Fig. 8. There are some issues linked with the efficient application of IoT technologies in agriculture production. Different sensing and monitoring technologies should be developed and a better education of farmers should be provided (i.e. development of standard education modules for farmers). Due to a large quantity of collected data, farmers could be potentially overwhelmed, ( Ec.europa, 2017 ). Therefore, there is a necessity for the development of standard trainings (education modules) for farmers coupled with the development of more user-friendly software solutions.

IoT in agricultural production from farmer’s perspective.
The application of IoT technologies in the agricultural sector would lead to advancements that could drastically modify current production procedures in agriculture, ( Shafi et al., 2020 ) ( Fig. 8 ).
1.2.4. IoT in waste management
Waste management towards a circular economy concept ( Fan et al., 2019 ) is a vital current population problem, where there is certainly a role for IoT technologies that could help provide more efficient waste management in specific areas ( Voca and Ribic, 2020 ) and recycling of different limited resources, ( Qiu et al., 2020 ). Currently, various technological solutions are being developed to support the smart waste management concept, ( Das et al., 2019 ). Some of them are already available on the market for wide implementation, ( Iot.farsite, 2020 ). The developed solutions are mostly directed towards the smart monitoring of waste bins ( Dhana Shree et al., 2019 ), i.e. bin filling level detection, waste temperature and fire detection, bin vibration occurrence and bin tilt, presence of waste operators, waste humidity, bin GPS location etc. In general, smart waste management systems, can be effectively supported by IoT devices, Fig. 9 . IoT technologies could also be used for the smart coordination of waste trucks ( Idwan et al., 2020 ) and efficiency waste utility companies could be ensured in that manner, which would be followed by a reduction of harmful emissions (pollutants) created by garbage trucks, ( Kozina et al., 2020 ). From the perspective of smart technologies, the proper and IoT based waste management of electronic waste is very important ( Kang et al., 2020 ) to secure sufficient raw resources to produce electronic equipment as already highlighted. IoT technologies could also be used for the reduction of food waste through intelligent appliances and a developed management structure in that sense, ( Liegeard and Manning, 2020 ).

IoT in smart waste management system, ( Quamtra, 2020 ).
Innovative IoT based technological solutions are expected to be developed in upcoming years, especially from a smart city concept perspective and that could support smart waste management systems and a circular economy concept.
1.2.5. IoT in healthcare
One challenging implementation field of IoT technologies has been detected in the healthcare system in general, through the e-health concept, ( Farahani et al., 2020 ). An increase in the service quality of healthcare systems could be utilized through IoT support (mainly collection of patient health data) and finally with the improvement of patient safety and care since it could also lead to an increase in patient life expectancy. There is an enormous potential in smart medical devices for different purposes ( Papa et al., 2020 ) that can be utilized for the monitoring of various vital and valuable human functions such as heart rate, skin temperature, movement monitoring, etc. Remote health monitoring is also an interesting perspective that could be utilized with the proper support of IoT devices and products. The prediction of different symptoms and prevention of potentially life hazardous states and diseases could generally be enabled, ( Muthu et al., 2020 ). Assistance to the elderly could also be ensured by monitoring a patient’s general health condition and nutrition status ( Nivetha et al., 2020 ), that would be supported via IoT devices. Rehabilitation after a serious disease could also be efficiently supported with IoT technologies, especially in cases of home rehabilitation circumstances, ( Bisio et al., 2019 ). One of the main issues and challenges in this specific IoT application field would be to ensure proper cyber safety due to potential attacks that could occur within healthcare monitoring systems, ( John et al., 2019 ). Significant progress in upcoming years is expected in the field of software development for health care systems, i.e. especially in hospitals. Namely, different devices could be linked via advanced software solutions as for example MRIs or CT devices and connected with laboratory data to create a smart hospital information system. The previously mentioned approach would allow for the better treatment of patients, detection of medical priorities and support for medical staff in monitoring and therapy decisions. IoT systems could also be used in hospitals for the efficient maintenance of a large number of medical devices ( Shamayleh et al., 2020 ). Equipment costs could be reduced in hospital systems due to the early detection of severe equipment malfunctions that could affect the accuracy of specific readings from medical devices. The development of smart and based IoT solutions in healthcare systems could also be very useful in the case of severe global pandemic states (data collection and fast data diversity, resources of medical staff and resources, medical triage, etc.), such as is the recent corona virus situation that has severely threatened the global population, ( WHO, 2020 ). The healthcare sector is probably one of the most challenging areas for IoT, thus important progress is expected in the upcoming year with serious benefits for the population.
1.2.6. IoT in transportation
Transportation modes will be significantly changed in upcoming decades, ( Jonkeren et al., 2019 ), especially due to the expected rising implementation of electric cars on the market, ( Capuder et al., 2020 ). The upcoming ban of Diesel based vehicles due to environmental issues ( Li et al., 2020c ) and finally development of alternative transportation technologies, such as hydrogen based vehicles for example ( Ajanovic and Haas, 2019 ), would change the shape of future transportation systems. In general, there is a demand for more environmentally suitable transportation options that are already being gradually developed with an expected penetration on the market. A necessary development of transportation infrastructure is needed for specific vehicle technologies to ensure desirable vehicle autonomy. Nowadays, the IoT emerged in the ‘‘internet of vehicles’’ concept ( Shen et al., 2020 ), which just proves its potential in this important area. The most significant IoT application area is in the case of the smart car (vehicles) concept, ( Chugh et al., 2020 ). The smart car concept considers the utilization and optimization of different internal functions in the car that are supported by IoT technologies. The application of IoT would upgrade driver experience and increase in comfort and safety. Specific data are collected in the smart car and associated with the main operating parameters such as tyre pressure, fuelling, early detection of potential failures, regular maintenance indicators, etc. In general, improved service as well as added value for customers could be obtained with a targeted utilization of IoT technologies, which finally can improve competition in the automobile industry between vehicle manufacturers. The challenging aspect of IoT application is in the case of autonomous vehicles, ( Padmaja et al., 2019 ). Location, direction as well as a planned path of the autonomous vehicle could be efficiently supported with IoT in general as well as the monitoring of safety systems for autonomous vehicles, ( Bylykbashi et al., 2020 ). The most important issue with autonomous vehicles is the prevention and avoidance of crash vehicle accidents, which could be solved with a targeted utilization of IoT devices, ( Abdou et al., 2019 ). Smart parking is also currently one of the most developing IoT areas when considering the transportation sector in general terms. Different research efforts are provided in that sense with the main goal being to enable the latest status of available parking space, control and monitoring of different useful parking space information in real time, ( Luque-Vega et al., 2019 ). Again, the development of sensor technologies, i.e. smart parking sensors is very important to enable efficient and accurate service, ( Perković et al., 2020a ). The maintenance and failure prevention of different vehicles could also be supported by IoT ( Saki et al., 2020 ), which could improve security and the lifetime of vehicles. Taking all the previously addressed into account, IoT technologies could completely change the driving experience and generally improve the quality of transportation systems from various aspects.
1.2.7. IoT in smart grids and power management
Energy transition ( Biresselioglu et al., 2020 ) has become a necessity due to the potential shortcomings of fossil fuel resources in future terms and for the reduction of different pollution impacts that are associated with the utilization of various fossil-based technologies, ( Bielski et al., 2020 ). Since a more intense implementation of renewable energy technologies has already been occurring, the efficient and advanced power management of electric grids has become an important aspect. Efficient demand side management with accurate and flexible smart metering technologies are key factors to enable smart power management in smart grids, ( Mendes et al., 2020 ). The most important role of IoT technologies in smart grids is to save electricity ( Rishav et al., 2019 ), with efficient distribution of electricity, Fig. 10 . The collection of specific grid data through IoT devices, and later their analysis with the proper software, could help improve grid reliability and efficiency. The economic aspect of electricity could also be improved with IoT due to the already mentioned efficiency improvement as previously highlighted. Useful benefits could be ensured both for customers and service providers.

Concept of smart grids ( Tuballa and Lochinvar Abundo, 2016 ),
A demand side management in households is also an important application area of IoT, ( Rahimi et al., 2020 ). Homes are typically equipped with different appliances that are becoming more advanced, creating the possibility for an efficient operation with the regulation of IoT, ( Tawalbeh et al., 2019 ). The efficient and smart forecasting of electricity demands for households could also be effectively supported by IoT technologies, ( Nils et al., 2020 ). An expected higher penetration of renewables in households through hybrid energy systems as an example ( Gagliano et al., 2019 ), would also require a smart operation strategy that could be utilized by IoT through integrated smart nano-grids, ( Kalair et al., 2020 ). A growth of IoT products and technologies in smart power management is expected to enable accurate forecasting and different load strategies in the case of renewable generation, ( Pawar et al., 2020 ). The elaborated main issues and challenges above just reflect the importance of IoT devices in smart grids and power management.
1.3. Review methodology
By addressing all the above raised general challenges towards an efficient and suitable implementation of IoT technologies, it is evident that more intense research efforts are needed to lead to further advancements in this dynamic research topic, with a strong application potential. A synergy of different research efforts in the field, mainly focused on the targeted topical area is needed. The main contribution and novelty of this review editorial is in line with that. Further main topical areas are addressed in the herein review introductory editorial;
- - IoT technologies in sustainable energy and environmental issues,
- - IoT enabled Smart City
- - E-health – Ambient assisted living systems
- - IoT technologies in Transportation and Low Carbon Products
The main objective of the herein presented review editorial is to address and discuss the latest advancements in the above specified and key IoT application areas. This review editorial serves as an introduction to the Virtual Special Issue (VSI) of JCLEPRO devoted to the 4th International Conference on Smart and Sustainable Technologies (SplTtech 2019) held on 18–21 June 2019, in Bol (Island of Brač) and Split, at the University of Split, (Croatia). The herein presented introductory review editorial was directed to the selected and accepted publications from the international conference SpliTech2019 and published papers were divided into four main topical areas as already specified above. Overall 38 papers were initially selected and invited for potential inclusion in the VSI SpliTech 2019. After conducted peer-review process, based on the JCLP procedures, 29 of them were selected for inclusion in the VSI SpliTech 2019. Authors from following countries have contributed VSI SpliTech 2019: China, India, Australia, Canada, Italy, Croatia, Serbia, Greece, Poland, Czech Republic, Spain, Cyprus, Turkey, Norway, Iran, Germany, Brazil, Malaysia, Pakistan, Dubai and United Kingdom. Besides the selected VSI SpliTech2019 works published in the JCLEPRO, the other relevant and latest works from the existing literature in the field were also addressed using the Scopus database, ( Scopus, 2020 ). Based on the conducted review as well as selected contributions in this VSI the key issues were identified, discussed and highlighted in the conclusion section.
2. IoT technologies in sustainable energy and environment
The rapid development of information technologies caused in one sense the necessity for ‘‘energy digitalization’‘. The increasing application of renewable energy technologies and development of efficient policies will be key points in upcoming decades to be able to secure global energy transition goals, ( Tzankova, 2020 ). Referring to the previous, the development of alternative renewable energy sources would also be valuable, ( Nižetić, 2010 ). Different energy scenarios or options have been considered in recent years involving a high share of renewables via hybrid energy options ( Nizetic et al., 2014 ), or for instance the possible application of alternative energy sources such as hydrogen technologies in different implementation fields ( El-Emam et al., 2020 ), or vehicle applications ( Matulić et al., 2019 ). The focus of the research is to investigate the techno-economic viability of different energy concepts in order to secure a suitable mix of energy technologies that would support an efficient energy transition. An improvement in the energy efficiency of different renewable energy technologies is also important, especially in the case of photovoltaics ( Grubišić-Čabo et al., 2019 ) and wind generation technologies ( Marinić-Kragić et al., 2020 ), to secure large scale projects. The efficiency of specific production processes ( Giama et al., 2020 ), is also vital and certainly needs to be carefully investigated and analysed, to reduce energy intensity and provide a circular economy concept in specific application areas, ( Xu et al., 2020 ). The main research efforts should be directed towards the upgrade of energy saving technologies followed with the increasing utilization of renewable energy sources, ( Klemeš et al., 2019 ). Recent technological progress in the field of IoT technologies has enabled different opportunities for the possible application of IoT concepts in the energy sector and environmental protection to secure a sustainable development.
Energy and environment are two of the most important elements of Smart Cities and are very often closely interrelated concepts. The available challenges in energy management to use and generate energy in the most efficient manner possible, and the development of a sustainable energy structure can take advantage of Internet of Things (IoT) and Internet of Energy (IoE) technologies, Fig. 11 ( Mohammadian, 2019 ) or in the case of battery charging protocols ( Fachechi et al., 2015 ).

IoE architecture ( Mohammadian, 2019 ).
The climate change and global warming impose a paradigm shift in the exploitation of resources and in more efficient energy resource management: production, distribution and consumption, as an integral part of this vision. The energy transition must point to an infrastructure change at the center of which there are the so-called smart grids. With the advent of smart grids and new technologies, the energy industry is inexorably changing. The most interesting aspect is that smart grids ensure flexibility in demand and allow consumers to participate in the energy system, as prosumers. Smart grids exploit digital and innovative technologies to manage and monitor the transport of electricity from all sources of generation to promptly, quickly and effectively satisfy the demand of end users. Smart grids are raising reliability, system resilience and stability, and minimizing disruptions, costs and environmental impacts. Some of these new technologies such as Distributed Generation (DG) and microgrids provide energy locally, creating larger and more reliable networks and reducing the line overload. Energy storage complements the energy from renewable sources while microgrids help reduce any blackouts by providing energy locally. Unlike the existing power system of a unidirectional system, which distributes electricity generated from a power plant to the consumer, the microgrid is equipped with a local power supply and storage system centered on independent distributed power sources. It is an energy network that can connect with an existing power system as needed and the self-sufficiency of energy such as electricity and heat by using multiple distributed power sources independently. In addition to giving owners the ability to generate their own energy, microgrids also reduce the dependency on energy providers by helping reduce costs and avoid peak usage charges. The microgrid can produce revenue if it were to produce a surplus of power, which could be sold to the energy provider. Recent works in the energy related field are discussed in the upcoming section of the paper to highlight IoT implementation areas and clarify the benefits in specific engineering applications.
In microgrids, IoT technologies are introduced mainly to realize a smart system able to autonomously schedule loads and/or detect system faults and then improving the efficiency of the energy consumption. The work ( Nayanatara et al., 2018 ) proposes a renewable energy based microgrid management strategy to use renewable energy (solar energy from a photovoltaic panel and wind energy from a wind turbine) effectively reducing the energy usage from the power grid. IoT technologies are used to realizing a smart scheduling algorithm able to control schedulable loads as per the needs of the consumer. Authors demonstrate that the proposed energy management system installed in an institution enables low power consumption and reduced costs. In ( Sujeeth et al., 2018 ) an IoT-based automated system that constantly monitors the current and voltage flowing through various branches of a DC microgrid, detects and controls the fault clearance process during fault conditions that has been developed. The system is capable to alert the user during overcurrent faults, ground faults and short circuit faults. As the operation of a microgrid is automated, the need for human decision making is eliminated and the minimum reaction time to react to fault conditions is drastically reduced. The work ( Majee et al., 2018 ) is also focused on the issue of fault management within a microgrid exploiting the IoT. The concept of IoT is used to solve the issues of microgrid reconfiguration occurring due to faults, changing energy usage patterns and the inclusion and removal of distributed energy resources.
Smart grids can automatically monitor energy flows and adapt to changes in energy demand and supply in a flexible and real-time manner. These smart systems can benefit from technologies such as machine learning ( Chou et al., 2019 ) and artificial intelligence ( Bose, 2017 ) to perform predictive analyzes and better configure all the devices. To do this, however, smart grids require adequate and equally intelligent measuring instruments. Here, smart metering tools could be efficient solution, reaching the consumers and suppliers, providing them with information on consumption in real-time. With smart meters, consumers can adapt - in terms of time and volume - their energy consumption to different energy prices during the day, saving on their energy bills by consuming more energy in periods of lower prices. In this perspective, the possibilities generated by improved digitization and sensorization, utilizing to the Internet of Things solutions, has led many research works to focus on realizing innovative IoT-based hardware and software solutions. These solutions are capable of providing real-time information about the quality usage of appliances, data consumption, and energy flow information ( Morello et al., 2017 ). present an interesting study on the role of advanced smart metering systems in the electric grid of the future through the realization and the experimental validation of a smart meter, Fig. 12 . The cost effective three phase smart energy meter, IoT enabled, multi-protocol and modular, capable to collect, process, and transmit several electric energies related information, mainly focused on consumer-side, to any smart energy control system was proposed by ( Avancini et al., 2018 ), Fig. 13 .

Proposed smart power meter, ( Morello et al., 2017 ).

Photo of created IoT enabled smart energy meter ( Avancini et al., 2018 ).
Several solutions are also based on the use of the Arduino platform ( Arduino, 2020 ) and a few sensors for the realization of low-cost smart meters ( Patel et al., 2019 ) or for instance Arduino based solutions ( Saha et al., 2018 ). Although smart grids are fundamental elements when it comes to energy sustainability, it is reductive to identify the concept of smart energy only in them. In fact, smart buildings also play a crucial role. The energy efficiency of building structures using smart technologies provides an increasingly intelligent management of resources, avoiding waste, improving the life quality of people and making the buildings themselves more resilient in the face of current climate changes. Thanks to building automation and IoT not only individual buildings but also entire neighborhoods can be controlled remotely from an energy point of view and in terms of the security. For example, it is possible to carry out checks on air pollution remotely ( Becnel et al., 2019 ), monitor fire systems ( Cavalera et al., 2019 ) or, furthermore, immediately detect any intrusion by outsiders ( Dasari et al., 2019 ).
Smart buildings are able to monitor actual energy needs, optimizing consumption and therefore counting not only on green energy, but also on a high degree of energy efficiency. The virtuous process that passes from smart energy allows to count on Nearly (Net) Zero Energy Building (NZEB) ( Rushikesh Babu and Vyjayanthi, 2017 ) and on a wider energy sustainability.
The most common use of IoT for energy and environmental sustainability is in the home automation systems, which allow homeowners to live comfortably and manage energy consumption through connected devices. In this field, numerous applications have been implemented and, despite the common goal of creating an Energy Management System (EMS) for home, the techniques used to achieve it can be very different. For example ( Li et al., 2018 ), propose a self-learning home management system that exploits computational and machine learning technologies, Fig. 14 . The proposed system has been validated by collecting real-time power consumption data from a Singapore smart home. In ( Al-Ali et al., 2017 ), an EMS for smart home is realized exploiting off-the-shelf Business Intelligence (BI) and Big Data analytics software packages to better manage energy consumption and meet consumer demands. In this work, the proposed system has been validated realizing a case study based on the use of HVAC (Heating, Ventilation and Air Conditioning) Units. Smart energy solutions such as those analysed provide real-time visibility of consumption and billing data, helping consumers to save resources, while energy and service companies can better balance production to meet actual demands, reducing potential problems. As the main effect, the energy consumption of families is reduced, also decreasing our impact on climate change.

Self-learning home management system architecture ( Li et al., 2018 ).
In addition to buildings and homes, industrial facilities and enterprises also deal with the adoption of innovative energy efficiency solutions to optimize resource consumption and reduce costs, but they need to evaluate a high number of factors to adopt the best energy efficiency measures. The work ( Suciu et al., 2019 ) proposes an IoT and Cloud-based energy monitoring and simulation platform to help companies monitor energy production and consumption, forecast the energy production potential and simulate the economic efficiency for multiple investment scenarios.
The concept of sustainability is increasingly linked to that of circular economy, which is now considered the key to this new paradigm. Unlike the traditional linear economy, based on the so-called “take-make-dispose” scheme, which provides for a complete utilization of resources, the circular economy model promotes reparability, durability and recyclability. In practice, the circular economy aims to minimize waste through reuse, repair, refurbishment and recycling of existing materials and products, focusing attention on designs that last over time. In this system, the IoT is considered an essential element, as it offers new opportunities in various sectors, such as manufacturing, energy and public services, infrastructure, logistics, waste management, fishing and agriculture. Especially in the field of waste management, research has made great strides through the creation of innovative systems capable of concretizing the concept of digital economy. In the work ( De Fazio et al., 2019 ) the activities related to the research project called POIROT were discussed, which exploit innovative hardware and software technologies, aiming to realize a platform for the inertization and traceability of organic waste. In detail, the main project objective is to realize a targeted transformation, through technological processes, regarding the organic fraction of urban solid waste, into inert, odorless and sanitized material, identified and traced to be employed for building applications or as thermal acoustic insulator, Fig. 15 .

Architecture of proposed identification and traceability system, ( De Fazio et al., 2019 ).
Several works propose solutions to support waste management at a domestic level, simplifying the waste separation to avoid problems due to improper waste management including hazards for human health or environmental issues. For example ( Al-Masri et al., 2018 ), propose a server-less IoT architecture for smart waste management systems able to identify waste materials prior to the separation process. This allows reducing costs related to the waste separation process from hazardous materials such as paint or batteries ( Kumar et al., 2017 ). propose a hygienic electronic system of waste segregation. The proposed approach eases the segregation of wastes at source level and thereby reducing the human interaction and curbs the pollution caused by improper segregation and management of wastes at source level.
The role of IoT supported smart meters was considered in the work ( Mendes et al., 2020 ) to address different demand side management scenarios. The novel and adaptive compression mechanism was proposed in the same work to improve the communication infrastructure for the given case, i.e. complete controlling structure, Fig. 16 . The proposed mechanism can reduce the quantity of data sent to utility companies and can automatize energy consumption management.

Proposed general controlling structure ( Mendes et al., 2020 ).
The proposed and tested control solution showed to be efficient with respect to the considered application, since compression rates were satisfactory and the proposed concept showed potential for other applications. The demand side management of a hybrid rooftop photovoltaic system was discussed in ( Kalair et al., 2020 ) where the system was integrated in a smart Nano grid. The smart monitoring system was presented in detail for residential purposes, together with a developed experimental setup that contains specific electronic components, Fig. 17 . The developed controller can automatically detect any frequency and voltage changes and link them with specific loading patterns. The proposed solution demonstrated efficiency since the power supply reliability was up to 97%. The proposed home management system could lead to the reduction of carbon footprints in the case of residential facilities.

Experimental setup with pre-processing unit (a) and smart controller (b) ( Kalair et al., 2020 ).
A machine learning-based smart home energy system was investigated in ( Machorro-Cano et al., 2020 ), using big data with the support of IoT. The home automatization system was coupled with IoT devices that enabled energy savings for the given purpose. A machine learning algorithm was used to study user behaviour and was later linked with energy consumption, i.e., with the proposed approach, specific user patterns were revealed. The developed monitoring system, Fig. 18 allowed specific recommendations to lead towards an improvement of energy efficiency in households, which were somehow personalized for the specific household. The system was successfully validated via the provided case study where the main strength of the conducted research was the personalized approach for the specific household. A step further could be to network and balance other households in the specific building facility. The importance of the BIM (Building Information Modelling) systems was discussed and analysed in the review paper ( Pantelia et al., 2020 ). An overview of the recent works focused on the building smart operation was elaborated in detail with use of IoT technologies. In the same work the renovation projects were also tackled as well as interoperability problems caused by data sharing with respect to the BIM related applications.

Concept of proposed IoT supported smart home system ( Machorro-Cano et al., 2020 ).
An application of smart wearable sensors was reported in the study ( Pivac et al., 2019 ) that were used for the monitoring of thermal comfort data as well as for the modelling of occupant metabolic response in office buildings. The smart and IoT supported monitoring system allowed the collection of useful data from the wearable sensors. The readings helped for the better understanding of thermal comfort issues in office buildings from a personalized thermal comfort point of the view. The experimental readings were compared with a subjective response from the occupants, where a successful modelling of personal metabolic responses was enabled with an accuracy of over 90%. Industrial facilities could also be improved with the implementation of IoT technologies as already briefly addressed in the introduction section. Legislation support is important to ensure smart electricity utilization in the households, especially from the perspective of the smart city concept. Study ( Grycan, 2020 ) discussed legislative for electricity consumption for the case of the Polish residential sector. Lack of legislative was detected and mainly in the smart metering solutions that are slowing down development of the smart infrastructure. There is necessity for the new regulations to ensure adaptability to the novel desired goals towards smart cities. Development of the novel business models is important to ensure smart driven business in the energy sector. The case of the smart energy driven model was elaborated in ( Chasin et al., 2020 ) as well as implications and necessary changes in the energy sector. Eight smart business models were discussed with introduction of desired changes. Presented knowledge and development business scenarios could be useful guideline for energy utility companies. The possibility of IoT based smart solutions was discussed in the review paper ( Bagdadee et al., 2020 ), where the focus of the work was on IoT-based energy management systems in the industry. IoT based energy management systems were elaborated for industrial applications as well as for smart energy planning in industrial facilities. The energy management systems in factories were addressed from a perspective of energy demand and supply. The focus of IoT applications could also be used on a level of single or multiple devices or appliances. The scheduling and optimal power management of the transformers was analysed and discussed in ( Sarajčev et al., 2020 ). The Bayesian approach was applied to detect an optimal controlling strategy to ensure benefits for power utility companies. The proposed and demonstrated model can predict the transformer health index with an accuracy of about 90%. The solution could be applied on the fleet of the power transformers where with the application of IoT technologies, further savings could be ensured for the specific application. The efficiency of the lighting system could also be improved with IoT devices. The work ( Mukta et al., 2020 ) discussed and reviewed the possible application of IoT technologies for the energy efficiency improvement of highway lighting systems. The results of the conducted review revealed that the development of smart and IoT supported highway lighting systems lack a systematic approach, quality and comprehensiveness. Possible framework was proposed to bridge the mentioned gap and secure an efficient pathway for the improvement of energy efficiency in IoT based lighting smart and green highway systems. The necessity for the environmental suitability of the proposed smart lighting system was also raised in the same study and noted as an important factor that needs to be further investigated. Energy harvesting is also interesting topic and closely linked with the possible application of IoT technologies, especially since IoT devices require energy for their operation. An underwater piezoelectric energy harvesting system was discussed in ( Kim et al., 2020 ) for the case of autonomous IoT sensor production. The proposed solution was fully designed and provided in the form of a prototype and demonstrated an autonomous energy source that could be further linked with IoT devices. The harvesting of waste energy could also be considered with the implementation of IoT devices. The possibility for waste energy harvesting supported by IoT was addressed and discussed in ( Kausmally et al., 2020 ) for the case of an industrial chimney. The complete design procedure was reported, i.e. the conceptual approach for the waste heat recovery where the prototype was successfully developed and demonstrated. Energy storage systems are also interesting for the application of IoT technologies. A renewable energy storage system was analysed in ( Sathishkumar and Karthikeyan, 2020 ), where a power management strategy was supported by IoT. The optimal design of a hybrid energy system coupled with energy storage was discussed based on solar and wind renewable energy resources.
The IoT approach allows successful monitoring and managing of complex energy systems. The main advantage of IoT for the considered application is the energy efficiency improvement, better synchronization of different energy systems and improvement of the economic aspect. A significant development of IoT products would lead to a rapid increase of big data that are usually processed by data centres. The energy load of data centres is increased, so efficiency improvements are necessary in the case of data centres to minimize load power as well as utilization of other limited resources. The issue related to data centres, power demands and the possible application of IoT technologies in order to reduce the mentioned unwanted impacts was discussed in ( Kaur et al., 2020 ). The authors proposed a specific framework in the same work that is applicable for data centres and could lead to efficiency improvement of over 27% (proposed approach was based on empirical evaluations).
IoT technologies could also be successfully implemented in a circular economy concept as above already mentioned, especially in smart waste management systems and environment protection as already mentioned. The role of IoT technologies in e-waste was discussed in ( Kang et al., 2020 ) for the case of the Malaysian recycling sector. A novel smart waste collection box was designed together with a user friendly mobile application, Fig. 19 . The concept was successfully demonstrated. The developed solution could be further optimized and fitted for possible market implementation. A discussion of possible IoT framework, based on the developed IoT supported smart e-waste bin was elaborated for the Sunway city in Malaysia. The proposed approach could be a helpful guideline for other cities. The remaining issue with the proposed concept is its economic feasibility that should be further investigated via a detailed user survey, detecting user willingness for the acceptance of the proposed concept. The innovative IoT supported platform for the transformation of organic waste into inert and sterilized material was reported in ( Ferrari et al., 2020 ). The specific Arduino-electronic platform was developed to control process parameters and link them with user responses and traceability. Novel and low cost sensors were developed and successfully applied for the given purpose. The proposed prototype of the device was presented and was used for the mechanical treatment of waste. The developed IoT supported framework for the identification and traceability of products was presented in Fig. 20 .

Prototype of smart e-waste bin ( Kang et al., 2020 ).

Conceptual IoT supported framework for waste processing ( Ferrari et al., 2020 ).
The implementation of IoT technologies in a circular supply chain framework was elaborated in ( Garrido-Hidalgo et al., 2020 ) for the waste management of Li-ion battery packs from used electric vehicles. A novel and IoT supported supply chain framework was proposed, which is compatible with the information infrastructure. The approach could be further used for the recovery process of Li-ion batteries. Due to a planned increase in electric car fleets globally, intensive research was also directed for the potential usage of IoT technologies for the smart charging of electric vehicles. Real time IoT based forecasting applications were proposed in ( Savari et al., 2020 ) for a more efficient charging process of electric vehicles. The application allowed better scheduling management where the waiting time was minimized, which improved the overall charging economy as well as charging time.
Environmental protection and sustainable behaviour could also be improved with the targeted application of IoT technologies. In the study ( Irizar-Arrieta et al., 2020 ), long-term field investigation was presented with the main goal being to investigate how IoT technologies could help ensure the sustainable behaviour of users in office building facilities. The results of the conducted directed study could lead to the improvement of energy efficiency at workplaces with IoT utilization in different aspects. The impact of IoT technologies on a sustainable perspective and society was addressed in ( Mahmood et al., 2020 ). The study was focused on addressing the impacts of home systems on the environment and sustainability in general. A survey was conducted for specific users and the investigation showed that the impact of home automatization on sustainability and environment is significant. However, the environmental effects should be discussed in more detail and quantified to get realistic indicators that would later be used for sustainable planning.
Besides the obvious potential impact of IoT technologies to the environment, IoT products could on the other side be used for environmental protection. The design and concept of a systematic framework for the massive deployment of IoT-based PM (Particulate Matter) sensing devices was elaborated in ( Chen et al., 2020c ). The proposed framework was applied for the monitoring of air quality. Compressed spatiotemporal data were used and that allowed for the efficiency improvement of air quality monitoring systems, energy savings and improved data saving ratio. In order to improve the interoperability between different sensor networks, as well as data sources, a novel IoT data framework was proposed in ( Duy et al., 2019 ). The proposed analytical framework was used as a useful tool to improve the data management of environmental monitoring systems. The developed framework enabled a more efficient utilization of the gathered environmental data and improved knowledge extraction later. IoT platforms could also be used for environmental planning as it was demonstrated in the study ( Wu et al., 2019 ). In the conducted research, a building information model was integrated successfully with IoT and used for environmental planning for environmental protection reasons. Moreover, the system was used for environmental protection in a specific construction project (tunnel utility). Different impacts to the environment were monitored during the construction project such as dust falling control, temperature monitoring, visual monitoring etc. The overall findings directed that the proposed IoT supported system showed to be effective for the considered application. The application of an IoT based data logger was presented in ( Mishra et al., 2020 ), for the monitoring of equipment for environmental protection. The developed monitoring system ensured accurate and reliable work of the equipment used for the environmental protection. Potential equipment faults were detected in advance (prevention of serious failure), the equipment energy consumption was rationalized and scheduled maintenance was enabled. The accurate prediction of particulate matter (PM 2.5 ) concentrations is very important, especially in urban areas. Usually, there is a network of sensors used for the monitoring of PM 2.5 concentrations but they are not well connected and harmonized in some situations, which is vital. An IoT framework was used, together with a fusion technique, to improve the data utilization from the PM measuring stations in the work ( Lin et al., 2020 ). A novel multi-sensor space-time data fusion framework was proposed that ensured better accuracy, i.e. a more reliable model was ensured with a higher spatial-temporal resolution. Regarding the current progress of specific application areas in IoT devices for environmental protection, it can be conducted that the studies were mostly focused on air quality monitoring. Water-Energy-Carbon (WEC) nexus was analysed in detail for EU27 countries, in the recent work ( Wang et al., 2020 ) by implementation of the Environmental Input-Output model (EIO). Study was important since contributed to the better understanding of the environmental performance in EU27 and could serve as important basis for future considerations or planning for policymakers.
Based on the previously conducted overview of latest research findings related to the application of IoT technologies in sustainable energy and environment, the further main findings could be highlighted:
- - IoT technologies are intensively investigated from a perspective of smart monitoring in different devices or engineering components that are associated with energy applications. Better usage and networking of various collected data could lead to noticeable efficiency improvements, energy savings, improved safety, improved equipment maintenance and finally the general improved operation of devices in different engineering applications,
- - The economic aspect associated with the application of IoT technologies was not addressed in most studies, which is a significant drawback,
- - The environmental impacts associated with the implementation of IoT technologies for specific use were not addressed, which is serious and an important issue that should be carefully considered and investigated when discussing specific IoT concepts. Moreover, an integral techno-economic-environmental conceptual approach (TEE) should be applied when considering an IoT application for specific cases,
- - The main advantages (benefits) of IoT technologies enable a personalized approach in specific engineering applications such as smart homes (level of single user), which lead to different possibilities for both energy and fund savings,
- - There is significant potential in IoT technologies for environmental protection; however, rare studies have been conducted in that sense. More intense research efforts are needed in that direction to be able to utilize all the potential benefits of IoT technologies and improve the environmental suitability of IoT in one sense,
- - The waste management and circular economy concept could be well supported with IoT technologies, where the main issue is the development of integral and conceptual smart waste management frameworks that would efficiently support the circular economy concept in different economies.
3. IoT enabled smart city
To enable the IoT-based smart city concept, Fig. 21 , is described in the form of a tree that can be considered to further understand what the possible applications or functionalities the IoT-enabled Smart City can provide. The branches of the given tree are dedicated to applications, wherein the leaves of the given branch are dedicated to the functionalities that each application can have. As the more leaves a branch contains, the more functionalities it has. Fig. 16 represents the different functionalities of a smart parking system for instance. Further on, for example, smart homes can have many functionalities: smart metering (electricity, water consumption, gas monitoring), smart lock control, smart room temperature monitoring, smart kitchens and other appliances, etc. The root of the given tree (enabler and information source of these systems) is dedicated to the hardware whose system uses to accomplish any of the given possible functionalities. This section considers an overview of the most important hardware technologies, and software architectures that can enable and present functionalities for different applications in the smart city concept.

Generalized concept of IoT enabled Smart City Architecture ( Perković et al., 2020b ).
3.1. Hardware overview and state-of-the-art
To enable Smart Cities, an infrastructure that uses sensing hardware acting as an information source is of crucial importance. As this sensing hardware is located in remote areas, often without access to an electrical network, an almost zero-energy use is needed and therefore can prolong battery lifetime and possibly enable self-powering through ambient power sources, e.g. solar cells. This is crucial for improving the usability of the whole system as a battery replacement in these circumstances is difficult, expensive and a time-consuming activity. To understand power consumption issues, an overview of state-of-the-art technologies to build the hardware is provided.
A standard sensing node, presented in Fig. 22 is consisted of a sensor component that delivers the sensed information to a microcontroller unit (MCU) for its further processing. To reduce power needs, the node is usually equipped with a related power management unit, while there is a given power source. Once the MCU acquires the data from the sensor, it gives data to a radio unit that uses an antenna to transmit the data over a wireless channel. In the next sections, the components are described in depth by referencing the relevant literature, while the specific original work was done in current technology investigations that can enable these functionalities.

Block scheme of standard sensing node architecture in IoT enabled Smart City.
Sensors vary in terms of design and functionalities. A good overview of sensing technologies, and its power consumption is given in Fig. 23 . It can be noticed that each of them has its own power consumption pattern, where the more functionalities they have, the more consumption will appear. Using it in an optimal way is of the highest importance for reducing battery lifetime.

Most popular sensors and their power requirements in active and power-down (i.e. sleep mode, Perković et al., 2020b ).
3.2. Efficient IoT radio units
To achieve data transmission, a critical part is to deliver the data in an efficient manner. For this, the major idea and enabler is to provide data links between sensing nodes and receiving stations for transmitted data. To satisfy different applications and related functionalities, it is important that these radios can timely transmit the data over larger distances while consuming less energy. The major competitors in this area are Low-Power Wide Area Networks (LPWAN) with their technology competitors: LoRa, NB-IoT and Sigfox. According to Fig. 24 LPWAN can satisfy long ranges wherein the data rate is sacrificed, just suitable for sensorial application. In these cases, sensor devices send several data packets containing only the sensed information.

Overview of technologies that can satisfy different usage scenarios ( Mekki et al., 2019 ).
When considering LPWANs, the competitive technologies are also orthogonal in terms of different application points of view. A good overview of these technologies is given in Fig. 25 and Fig. 26 , also by providing the costs for each of them. In addition, Figs. 25 and and26 26 give the technological comparison between each of them, so the deployers can understand which technology better fits which need. These mostly refer to which kind of infrastructure is required to match needs, what distance can be covered, what the overall system latency is when considering the number of nodes, etc.

Overview of performances and deployment costs for different LPWAN technologies ( Mekki et al., 2019 ).

Pros and cons for each of LPWAN competitors ( Mekki et al., 2019 ).
3.3. Power management
The basic mechanism that allows for the long lifetime of battery-operated devices (up to a couple of years) is to keep the device in low-power state during inactive periods. IoT devices, especially battery-operated ones, spend only a small fraction of time within active state, in which MCU performs sensor readings, and communicates data over wireless channels using a radio peripheral, while during inactive periods, the MCU along with other components is kept in deep-sleep state. Such a period between two active states, i.e. active - sleep - active is referred to as a duty cycle. Intuitively, to increase the lifetime of an IoT device, it is necessary to minimize its consumption during inactive periods. Logically, within inactive periods, it is necessary to place all active components into sleep. Some components, such as sensors, and radio modules, already come with libraries that support low-power consumption in sleep state (around 1uA per component or less). Using built-in functions, the MCU triggers external components to enter sleep once the sensor reading and radio transmission is done. On the other hand, the MCU also has to be kept in deep-sleep during the sleep period. However, to trigger the MCU waking from deep-sleep, some form of interrupt has to be sent to it. This is usually accomplished with some form of low-power timer. Depending on the MCU that is used in the implementation of an IoT device, there are many ways to accomplish this.
An MCU such as ATmega328P, found on Arduino boards, comes with a built-in Watchdog timer (WDT), with consumption up to couple of Ua, ( ATmega328P, 2020 ). Some external timers, like TPL5010 come with Watchdog functionalities, however, with nA scale consumption ( TPL5010, 2020 ). Unfortunately, the maximum time WDT can hold the MCU in low-power mode is around 8 s ( Tutorial - Atmega328p, 2020 ). One way to increase sleep time using WDT would require a loop that periodically triggers the MCU waking up every 8 s, after which the MCU immediately enters deep-sleep. Within deep-sleep period, the consumption of MCU and WDT is only a few uA. To increase sleep time for ATmega328P, an external RTC clock could be employed, such as a cheap and precise RS3231 RTC clock, with ±2 ppm stability and 1uA of consumption (Datasheet - RTC3231, 2020 ). Other MCUs, such as STM32 or SAMD21, already come with built-in RTC clocks that can be used to trigger an alarm for waking up from deep sleep (Libraries - Arduino low-power, 2020 ), ( STM32, 2020 ). All these components (MCU, sensor, RTC clock, radio peripheral, voltage regulators, capacitors, etc.), although in low-power mode, combined may consume tens to even couple of hundred of uA while being placed in deep-sleep. Moreover, it may happen that some boards equipped with components that adopt low-power modes have a hardware problem that prevent them from achieving low deep-sleep currents, such as found in MKRWAN1300 (Arduino LoRa with SAMD21) and ( MKRWAN1300, 2020 ).
To reduce even more consumption regarding all components, it is suggested to use an external timer component that will completely cut-off power for predefined periods. The TPL5110 is a low power timer where an alarm clock is regulated with resistors, allowing for the duration of sleep mode to be up to 2 h ( TPL5110, 2020 ). Within the sleep period, the TPL5110 simply cuts-off power from other components leaving overall consumption to be equal to the consumption of the timer only. Since the TPL5110 is low power by nature, the overall consumption falls to only 50 nA. The drawback of such a solution is that the MCU is no longer in deep-sleep but is instead powered off, which means that possible variables that were held in volatile memory during deep-sleep will not be available to the MCU when it wakes up. For this reason, it is suggested to use EEPROM or flash memory to write the variables before cutting off power from the MCU. A Tega328P may use built-in EEPROM, while STM32 or SAMD21 can use flash memory or RTC backup RAM ( Flash storage, 2020 ). The RS3231 RTC clock has an EEPROM that can be used for saving variables. The main drawback of EEPROM and flash memory is the limited number of writes (around 10,000), hence some external EEPROM or flash memory may be used with a larger number of writings, or either an external specialized chip like ATECC508A ( ATECC508A, 2020 ) that supports secure storage (of key for example) (ATEC). It must be noted that when the MCU wakes from deep-sleep, the code runs from where it left off, which usually requires a couple of mS. On the other hand, powering the MCU with an external timer such as TPL5110 requires a fresh restart of code, which in some scenarios may indicate running the bootloader. For ATmega328P, by default it may take up to 2 s for the bootloader to start ( Tutorial - Low-power nodes, 2020 ). Hence, to reduce consumption, it is suggested to either completely wipe out the bootloader or flash faster bootloader ( Bootloader, 2020 ). It must be mentioned that battery capacity, along with its input voltage may vary during sensor lifetime or could be larger than the operating voltage of some components. A good quality voltage regulator that may deliver enough current to a sensor device while consuming itself small current is required. For example, MCP1700 ( MCP1700, 2020 ) is a family of CMOS low dropout (LDO) voltage regulators that can deliver up to 250 mA of current while consuming only 1.6 μA, with input operating ranging from 2.3V to 6.0V, making it ideal for battery operated devices.
3.4. Microcontrollers for IoT: scouting and comparison
The Microcontroller (MCU hereafter) is the core of any Internet of Things (IoT) device and embedded system. Indeed, its role is to coordinate, according to a specific pre-programmed logic, all the peripherals of the IoT node thus providing sensing, actuation, and connectivity in an as low power mode as possible. In other words, the MCU sets the “smart-ability” of a certain object in relation with its cost, computational capability, power consumption, memory, communication interfaces and other features to accurately select during the design phase. It is worth highlighting that a “perfect” microcontroller does not exist, but just the most suitable one for the specific application. For this reason, the role of the designer in selecting the microcontroller for a specific IoT application is never simple. Some “universal” microcontroller key features are useful to drive the designer towards the right choice according to the requirements of the considered IoT application.
The proposed analysis aims at comparing some microcontrollers as potentially useful for the IoT by considering the following objective parameters.
- • Register Memory Bits : This parameter refers to the number of internal register bits and buffer. The higher the number of MCU bits, the higher the number of operations that the MCU itself can sustain. This parameter sets different families of Microcontrollers.
- • Maximum Clock Frequency: is the maximum frequency on the internal/external clock of the microcontroller. It is useful because it sets the number of operations of an MCU in a single time unit.
- • RAM : RAM is the volatile memory of an MCU which is useful for performing quick operations, actions or data buffering. The absence of powering resets this kind of memory
- • Flash Type : It is the static memory of an MCU that retains data in the absence of power. The quality of this memory in terms of writing operation figures and writing/reading speed determines a consistent part of the microcontroller cost.
- • Number and Type of GPIOs : GPIO is the acronym of a general-purpose input/output interface. It is referred to as the presence of pins that can be configured to act as the analog or digital input/output of the MCU. The higher the number of MCU GPIOs, the higher the number of external devices (sensors, actuators, transceivers) that can be controlled.
- • Serial Bus : Presence of an SPI/I2C bus for communication
- • Integrated Wireless Connectivity Interfaces: This key feature is useful in the IoT to wirelessly connect the MCU by using Wi-Fi, Ethernet, or BLE interfaces.
- • Power Consumption: Power Consumption is the most important aspect of IoT-oriented Microcontrollers. This parameter should be optimized by controlling the Active time and Sleeping time of the MCU according to the specific application.
- • Development board/Launchpad: The availability of a development board is helpful during the design phase to test the targeted IoT solution before realizing a prototype. Providing this board is an added value for MCUs.
- • Arduino IDE Programming Interface: Multi-brand MCUs implement an Arduino-compatible convergence programming language useful to simplify the programming operations and modular implementation of IoT applications.
- • Cost: IoT applications are often cost-sensitive. In many cases, functionalities could not be implemented to maintain a low-cost IoT system design. Generally, both MCUs and the presence of specific sensors determine the cost of the whole solution.
In addition to the above-mentioned parameters, the computational capability of a microcontroller can be evaluated by considering the presence of an on-board Operating System. If supported, this feature helps in managing complex IoT embedded applications where several peripherals must be managed. In this regard, three different typologies of microcontrollers can be summarized:
- • No-Operating system: The operating system is not present. In this case the microcontroller can be programmed in a “canonical” manner, by developing a code for low-level operations (Assembler of C are the main programming languages). A software-level connection cannot be implemented, however, the cost-effectiveness of these kinds of microcontrollers as well as reduced power consumption, make this MCU typology quite diffused.
- • RTOS : namely “Real-Time Operating System”. An RTOS Operating system enables a multi-task approach by introducing priority levels among the tasks running under the operating system. Moreover, this Operating System guarantees the correct timing of single events.
- • Linux/UNIX : This feature allows high-level programming in a way similar to a canonical computer. Open source software can be run on the MCU thus enabling connectivity and port management. Real-time and low-power operations are never guaranteed so that this kind of MCU is often not compatible with IoT applications, except for hi-level management IoT node systems.
Underneath, selected multi-brand MCUs will be compared by using the above-mentioned metrics in order to have a quick perspective useful in selecting the right MCU for a specific IoT application. After a quick overview of the microcontrollers based on manufacturer descriptions, which is useful to understand the different categories, a table summarizing their main features will be provided. Being low-power, “No-Operating system” devices will be considered in this comparison, Fig. 27 .

Comparison of microcontroller devices.
3.4.1. Texas instruments G series MSP430G2x13 and MSP430G2x53
The MSP430G2x13 and MSP430G2x53 series are ultra-low-power microcontrollers with built-in 16-bit timers, up to 24 I/O capacitive-touch enabled pins, a versatile analog comparator, and built-in communication capability using a universal serial communication interface. In addition, the MSP430G2x53 family members have a 10-bit analog-to-digital (A/D) converter. This is an entry-level microcontroller useful for general purpose low-power and low-cost IoT applications. The availability of a development board for the MSP43G2553 MCU, called “Launchpad”, makes the design easy for simple IoT sensing nodes.
3.4.2. Texas instruments F series MSP430F552x
The MSP430F5529, MSP430F5527, MSP430F5525, and MSP430F5521 microcontrollers have an integrated USB and PHY supporting USB 2.0, four 16-bit timers, a high-performance 12-bit analog-to-digital converter (ADC), two USCIs, a hardware multiplier, DMA, an RTC module with alarm capabilities, and 63 I/O pins. The MSP430F5528, MSP430F5526, MSP430F5524, and MSP430F5522 microcontrollers include these peripherals but have 47 I/O pins. This MCU family is compatible with low-power hi-performance IoT applications where hi-speed communication, port availability, and USB connectivity is required. Also in this case, the availability of a “Launchpad”, for the MSP430F5529 MCU makes the design easy for rather advanced and low-cost IoT smart nodes.
3.4.3. Texas instruments FR series MSP430FR572x and MSP430FR59xx
The TI MSP430FR572x and MSP430FR59xx families of ultra-low-power microcontrollers consist of multiple devices that feature an embedded FRAM nonvolatile memory, ultra-low-power 16-bit MSP430™ CPU, and different peripherals targeted for various applications. The architecture, FRAM, and peripherals, combined with seven low-power modes, are optimized to achieve extended battery life in portable and wireless sensing applications. FRAM is a new nonvolatile memory that combines the speed, flexibility, and endurance of SRAM with the stability and reliability of flash, all at lower total power consumption. Peripherals include a 10-bit ADC, a 16-channel comparator with voltage reference generation and hysteresis capabilities, three enhanced serial channels capable of I2C, SPI, or UART protocols, an internal DMA, a hardware multiplier, an RTC, five 16-bit timers, and digital I/Os.
3.4.4. Microchip PIC18F family PIC18F26K22
The PIC18 microcontroller family provides PICmicro® devices in 18-to 80-pin packages, that are both socket and software upwardly compatible to the PIC16 family. The PIC18 family includes all the popular peripherals, such as MSSP, ESCI, CCP, flexible 8- and 16-bit timers, PSP, 10-bit ADC, WDT, POR and CAN 2.0B Active for a maximum flexible solution. Most PIC18 devices will provide a FLASH program memory in sizes from 8 to 128 Kbytes and data RAM from 256 to 4 Kbytes; operating from 2.0 to 5.5 V, at speeds of DC to 40 MHz. Optimized for high-level languages like ANSI C, the PIC18 family offers a highly flexible solution for complex embedded applications.
3.4.5. Microchip PIC24F family PIC24F16KA102
The PIC24F is a cost-effective, low-power family of microcontrollers (MCUs) based on eXtreme Low Power (XLP) technology and 16-bit architecture. The flash memory ranges from 16 KB to 1 MB. The PIC24F family is a suitable solution for many space-constrained, low-power, cost-sensitive industrial, IoT and consumer applications.
3.4.6. STMicroelectronics STM32L0 family – STM32L053x8
The STM32L053x6/8 devices provide high power efficiency for a wide range of IoT applications. It is achieved with a large choice of internal and external clock sources, an internal voltage adaptation and several low-power modes. The STM32L053x6/8 devices offer several analog features, one 12-bit ADC with hardware oversampling, one DAC, two ultra-low-power comparators, several timers, one low-power timer (LPTIM), three general-purpose 16-bit timers and one basic timer, one RTC and SysTick which can be used as time bases. The MCU is provided with SPI, I2C, UART and USB 2.0 busses. This kind of MCU is studied for Ultra Low Power IoT applications and is provided with an effective development Arduino-compatible modular kit, called NUCLEO, allowing for easy interconnection with connectivity (BLE, Wi-Fi, Lo-Ra, etc) modules for IoT.
Taking into the account the above elaborated recent works, application scenarios and the enabling technology overview, following can be emphasized:
- - all kinds of services that are used to enable smart cities highly depend on the deployed hardware sensing infrastructure. Less infrastructure implies limited functionalities for given application scenarios. On contrary, many different application scenarios can be considered but this increases implementation and maintenance costs,
- - many different sensing techniques were proposed, and research community is intensively working to provide more reliable and cost-effective sensing technologies that can be easily implemented in IoT sensing nodes,
- - to enable different functionalities of the given application scenarios it is important to have the technology which can deliver sensed data on a greater distance, while preserving the energy in order to improve battery lifetime. For their products, many vendors specify 2–10 years of lifetime for their products, and it can be concluded that the battery lifetime depends on how frequently data is sensed and sent to the receiving station. Two-years span can certainly be considered as not enough, ten years’ horizon could be enough as by then, new technologies may arise and substitute currently implemented technologies. In any case, providing new technologies from any point of view: radios, MCUs, sensing techniques that can preserve battery lifetime is of crucial interest for both current and future IoT deployment,
- - currently available radios can fulfil today’s needs in terms of delivering data from remote areas in smart cities/villages. The NB-IoT, LoRa and Sigfox are overlapping in part, but can be considered as orthogonal for specific use-cases. Smart usage of given radios can further improve battery lifetime. However, it is always of the high interest to consume even less energy and provide larger communication distances and it provides the space for further analysis and technology improvements.
4. E-health – ambient assisted living systems
In recent years, the exploitation of new assisted living technologies has become necessary due to a rapidly aging society. In fact, it is estimated that 50% of the population in Europe will be over 60 years old in 2040, while in the USA it is estimated that one in every six citizens will be over 65 years old in 2020 ( Corchado et al., 2008 ). In addition, in 75-year-olds, the risk of Mild Cognitive Impairment (MCI) and frailty increases and people over 85 years of age usually require continuous monitoring. This suggests that taking care of elderly people is a challenging and very important issue. People with limited mobility are increasingly looking for innovative services that can help their daily activities. Ambient Assisted Living (AAL) encompasses technological systems to support people in their daily routine to allow an independent and safe lifestyle as long as possible. AAL (or simply assisted living) solutions can provide a positive influence on health and quality of life, especially with the elderly. An AAL approach is the way to guarantee better life conditions for the aged and people with limited mobility, chronic diseases and in recovery status with the development of innovative technologies and services.
Modern assistive technologies constitute a wide range of technological solutions aimed at improving the well-being of the elderly, Fig. 28 . These technologies are used for personalized medicine, smart health, health tracking, telehealth, health-as-a-service (HaaS), smart drugs and multiple other applications ( Maskeliunas et al., 2019 ).

IoT technology applications for AAL domain, ( Maskeliunas et al., 2019 ).
AAL technologies can also provide more safety for the elderly, offering emergency response mechanisms ( Lin et al., 2013 ), fall detection solutions ( Kong et al., 2018 ), and video surveillance systems ( Meinel et al., 2014 ). Other AAL technologies were designed in order to provide support in daily life, by monitoring the activities of daily living (ADL) ( Reena and Parameswari, 2019 ), by generating reminders ( Uribe et al., 2011 ), as well as by allowing older adults to connect with their families and medical staff. The recent advancements in mobile and wearable sensors helped the vision of AAL to become a reality. All novel mobile devices are equipped with different sensors such as accelerometers, gyroscopes, a Global Positioning System (GPS) and so on, which can be used for detecting user mobility. In the same way, recent advances in electronic and microelectromechanical sensor (MEMS) technology promise a new era of sensor technology for health ( Vohnout et al., 2010 ). Researchers have already developed noninvasive sensors in the form of patches, small holter-type devices, wearable devices, and smart garments to monitor health signals. For example, blood glucose, blood pressure, and cardiac activity can be measured through wearable sensors using techniques such as infrared or optical sensing. User localization is another key concept in AAL systems because it allows tracking, monitoring, and providing fine-grained location-based services for the elderly. While GPS is the most widespread and reliable technology to deal with outdoor localization issues, in indoor scenarios it has a limited usage due to its limited accuracy due to the impact of obstacles on the received signals. The number of alternative indoor positioning systems have been proposed in the literature ( Mainetti et al., 2014 ) that can be exploited in order to support AAL systems. Among all technologies, Bluetooth (BT) technology represents a valid alternative for indoor localization ( Yapeng et al., 2013 ) or specifically in museums ( Alletto et al., 2015 ). It is able to guarantee a low cost since it is integrated in most of daily used devices such as tablets and smart phones. The spread of the emerging Bluetooth Low Energy (BLE) technology makes the BT also energy-efficient, which is a key requirement in many indoor applications. An interesting investigation regarding the state-of-the-art and adaptive AAL platforms for older adult assistance was provided in ( Duarte et al., 2018 ). The authors present an overview of AAL platforms, development patterns, and main challenges in this domain.
In recent years, a large number of solutions have been proposed in the literature in order to create smart environments and applications to support elderly people. The main purpose is to provide a level of independence at home and improve elderly quality of life. In ( Dobre et al., 2018 ), an architecture which constitutes the base for the development of an integrated Internet of Things (IoT) platform to deliver non-intrusive monitoring and support for older adults to augment professional healthcare giving is presented, Fig. 29 . The proposed architecture integrates proven open-data analytics technology with innovative user-driven IoT devices to assist caregivers and provide smart care for older adults at out-patients clinics and outdoors.

Proposed modular architecture, ( Dobre et al., 2018 ).
A solution for monitoring patients with specific diseases such as diabetes using mobile devices is discussed in ( Villarreal et al., 2014 ). The proposed system provides continuous monitoring and real time services, collecting the information from healthcare and monitoring devices located in the home environment which are connected to BT mobile devices. The sensor data are transmitted to a central database for medical server evaluation and monitoring via 3G and Wi-Fi networks. An ad hoc application, installed on a mobile phone, allows the remote control of a patient’s health status whilst the patient can receive any notifications from the health care professionals via the application running on her/his mobile phone, Fig. 30 .

Proposed system for continuous monitoring and real time services, ( Villarreal et al., 2014 ).
The work ( Villarrubia et al., 2014 ) proposes a monitoring and tracking system for people with medical problems whose system architecture is shown in Fig. 31 . The solution includes a system for performing biomedical measurements, locomotor activity monitoring through accelerometers and Wi-Fi networks. The interactive approach involves the user, through a smart TV. The locomotor activity of the elderly is deduced through the analysis of Received Signal Strength Indication (RSSI) measurements, i.e. through an algorithm, the received signal power from different access points located in the house is determined. Mobile accelerometers are used to analyze the movement of users and detect steps. Single board computers, such as Raspberry Pi, are used to collect data coming from the different sensors wirelessly connected to obtain real-time context-aware information such as gas, temperature, fire, etc. or to get information from biomedical sensors such as, oxygen meter, blood pressure, ECG, accelerometer, etc. The Raspberry Pi can be connected to a TV to transmit warnings or notifications coming from health care professionals.

Virtual organization of system, ( Villarrubia et al., 2014 ).
The work ( Mainetti et al., 2016 ) proposes an AAL system for elderly assistance applications able to provide both outdoor and indoor localization by using a single wearable device. A prototypal device has been developed exploiting GPS technology for outdoor localization and BLE technology for indoor localization. The proposed system is also able to collect all information coming from heterogeneous sensors and forward it towards a remote service that is able to trigger events (e.g., push notifications to families or caregivers and notifications to the same indoor environment that will change its status). In an enriched work ( Mainetti et al., 2017 ), presents an architecture that exploits IoT technologies to capture personal data for automatically recognizing changes in the behaviour of elderly people in an unobtrusive, low-cost and low-power manner, Fig. 32 . The system allows performing a behavioral analysis of elderly people to prevent the occurrence of MCI and frailty problems.

Overall logical architecture ( Mainetti et al., 2017 ).
Based on the recent analysed research works on the use of IoT technologies in the e-health and for the creation of AAL systems, it is possible to draw the following general observations:
- - an extensive research is aimed at creating AAL systems intended primarily for the elderly or for people with physical or mental diseases,
- - current challenges deal with the use of IoT technologies in order to capture the habits of the people monitored both in indoor and outdoor environments for behavioral analysis purposes. The behavioral analysis can be useful for monitoring people, scheduling interventions and providing notifications directly to the user,
- - increasing efforts are needed in order to unobtrusively capture habits by favoring the use of wearable devices.
5. IoT technologies in Transportation and Low Carbon Products
The issue of security and traceability of goods is increasingly important in the logistics sector, with repercussions in terms of supply chain management and goods transport. In this case, information technologies and in particular the IoT can offer valuable support, increasing the degree of visibility and control over the entire supply chain. Transportation is a good example of how IoT technologies can bring value. In fact, this sector needs systems that on the one hand allow for the planning, management and optimization of flows (both along the supply chain and within complex logistics hubs such as intermodal ones) and, on the other hand, allow for the traceability of goods (products or containers) in real time along the entire supply chain. A further requirement concerns the check of goods integrity. In this context, it is clear how IoT technologies can contribute to the remote monitoring of flows and assets, providing a series of information useful for their management and optimization. This is possible through identification (e.g., via RFID or barcode), location (e.g., via GPS), monitoring of parameters and status variables of the assets (e.g., via sensors) and their transmission (e.g., via Wi-Fi or GSM/GPRS network).
The advent of IoT technologies allows to organize, automate and control processes remotely and from any device connected to the Internet. By definition, an efficient supply chain is responsible for delivering the goods, from the manufacturer to the end user, at the agreed time and under the specified conditions. Through the use of IoT technologies, it is possible to track the entire process in real time, promoting speed and efficiency in automated processes, reducing time and personnel costs. IoT technologies such as sensors, embedded and mobile devices, and cloud storage systems allow for the connection of “things” (warehouses, vehicles or goods) to the Internet so that the manufacturer, the logistics service provider and even the end user can thoroughly know at any time the status of products, their location and estimated delivery time.
Logistics can benefit from the use of IoT technologies in all the following sectors:
- • efficient inventory and warehouse management
- • automation of internal business processes
- • fast and efficient delivery of products (e.g., route planning)
- • conservation and quality of transported goods (e.g., monitoring of cold chain)
- • location, monitoring and tracking of vehicle fleets
- • interactive communication between vehicles and manufacturers/distributors of goods
- • certification of both deliveries and transport phases
The basic principles of logistics always remain valid: transfer the right product, in the right quantity and condition, at the right time and right price, in the right place and to the right customer. As carrying out each of these tasks has become much more complicated in an increasingly globalized and interconnected world, the need for innovative solutions to achieve these objectives also increases. As mentioned above, the IoT is revolutionizing the logistics sector, offering many advantages and opportunities. Supply chain monitoring, vehicle tracking, inventory management, secure transport and process automation are the cornerstones of IoT applications as well as the main elements of interconnected logistics systems.
In the logistics sector, the IoT allows creating smart location management systems, which allow companies to easily monitor driver activities, vehicle location and delivery status, ( Brincat et al., 2019 ). This solution is indispensable in the planning of deliveries and the organization of timetables and reservations. It is possible to detect any changes in real time and this is precisely the reason behind the success of the IoT: the ability to improve the management of good movement and therefore streamline business processes. Inventory and warehouse management is another important element of the connected logistics ecosystem. The positioning of small sensors allows companies to easily track items in warehouses, monitor their status, position and create a smart control system. In fact, with the help of IoT technology, employees will be able to successfully prevent any loss, ensure the safe storage of goods and efficiently locate the product needed. Even the minimization of human error becomes possible thanks to the IoT. In this scenario ( Wang et al., 2015 ), proposes a layered architecture for the realization of an automation enterprise asset management system using IoT and RFID technologies, Fig. 33 .

Layered architecture of proposed automation enterprise asset management system ( Wang et al., 2015 ).
The sustainable and IoT supported business model was discussed in ( Gao and Li, 2020 ) for the case of the bike-sharing services. Novel framework was developed that links sustainable indicators as well as social aspects of the business concept. The case studies for dockless bike-sharing services were discussed and presented for China and UK. Practical findings extended knowledge needed for improvement of the sharing economy to achieve sustainably goals through IoT enabled support. The work ( Zhang et al., 2016 ) proposes an inventory management system for a warehousing company. The system adopts the concept of IoT using RFID technology to track the material and provide messages or warnings when incorrect behaviors are detected. In particular, it integrates RFID technology and a self-Adaptive distributed decision support model for inbound and outbound actives, inventory location suggestions and incident handling. In ( Guptha et al., 2018 ), the authors design an IoT architecture for order picking processes in a warehouse that allows the inventory real time tracking and visibility into the reduction of warehouse operation costs, improved safety and reduced theft. IoT and RFID technologies are again exploited in ( Valente et al., 2017 ) to improve productivity in the value chain of a steel mill. In this work, an existing RFID solution architecture based on the reference EPCGlobal/GS1 framework was modified in order to be extended to the IoT domain, Fig. 34 .

RFID/IoT solution architecture for steel mill (Valente et al., 2017).
The internet-connected devices collect large amounts of data which can be transmitted to a central system for further analysis. In this context, the integration between IoT and predictive analysis systems can help companies to create effective business development strategies, improve decision-making and manage risks. In the logistics sector, this integration finds application to plan routes and deliveries as well as identify various defects before something goes wrong. An integrated framework to track and monitor shipped packages, Fig. 29 was proposed in ( Proto et al., 2020 ). Framework relies on a network of IoT-enabled devices, called REDTags, allowing courier employees to easily collect the status of package at each delivery step. The framework provides back-end functionalities for smart data transmission, management, storage, and analytics. A machine-learning process is included to promptly analyze the features describing event-related data to predict the potential breaks of goods in the packages ( Fig. 35 ).

Framework architecture, ( Proto et al., 2020 ).
Ensuring product quality and integrity is an interesting challenge that in recent years has led to the creation of smart systems that integrate IoT solutions and block chain technology. The Blockchain technology associated with IoT sensors could allow the creation of a temporal “stamp” inside which a series of information is kept such as product delivery date, product characteristics and status, and origin of product. By positioning the sensors, for example, it is possible to monitor parameters such as product temperature and humidity, vehicle position and phases of the transport process and save this data in the block chain. Block chain infrastructure can also revolutionize company logistics in the field of document management (i.e., invoices, transport documents, etc.), traceability of goods (origin of products, monitoring of vehicle fleets, etc.), and play a substantial role in fighting counterfeiting. Imeri and Khadraoui (2018) showed a conceptual approach to the security and traceability of shared information in the process of dangerous goods transportation using block chain technology based on smart contracts. IoT and block chain technologies are exploited in ( Arumugam et al., 2018 ) where a smart logistics solution encapsulating smart contracts, logistics planner and condition monitoring of the assets in the supply chain management area is presented, Fig. 36 . Moreover, a prototype of the proposed solution is implemented.

High-level architecture of proposed solution, ( Arumugam et al., 2018 ).
The block chain-IoT-based food traceability system (BIFTS) to integrate the novel deployment of block chain, IoT technology, and fuzzy logic into a total traceability shelf life management system for the managing of perishable food, Fig. 37 was proposed in ( Tsang et al., 2019 ). Challenges in the adoption of the proposed framework in the food industry are analysed and future research planned to improve the proposed work.

Modular framework of BIFTS, ( Tsang et al., 2019 ).
Taking into account above discusses recent research findings further main findings could be highlighted:
- - The studies analysed previously show how the hardware and software technologies enabling the Internet of Things are leading to a digital transformation process that aims at an intelligent and advanced management of the entire logistics and transportation system.
- - The main scientific challenges in this field aim to use sensors in order to monitor the status of the goods transported, to ensure traceability and above all to safely and reliably collect telemetry data and offer them to Artificial Intelligence modules for advanced processing.
- - Furthermore, recently the interest has focused on the next generation of blockchain systems (the so-called blockchain 3.0) which aims to apply the benefits of the classic blockchain in typical scenarios of the Internet of Things, such as logistic and transportations.
6. Concluding remarks and future directions in the field
This review paper discussed and presented latest research findings that were included within the JCELPRO VSI SpliTech2019 and dedicated to the 4th International Conference on Smart and Sustainable Technologies (SpliTech 2019). The contributions as well as herein presented knowledge is summarized and discussed in upcoming sections.
The Intense digitalization in recent years has allowed for different technological possibilities that have already gradually been changing the main economic sectors and societies in general. Digitalization in different economic sectors enabled various possibilities for advancements and for a more efficient utilization of limited resources, systems or processes. The main driver for an efficient digitalization in various sectors is information technology, i.e., IoT supported smart technologies. In the previous sense, the energy sector is one of the key sectors where ‘‘energy digitalization’’ has already been rapidly developing in various energy related fields. Currently, one of the most progressing implementation areas of IoT technologies is related to the energy sector. The developing solutions are focused on smart homes, i.e. advanced automatization of home energy systems, development of smart and adaptive micro-grids, or advancements in efficient demand-side management of power systems. A circular economy concept has also been intensively worked on where various concepts have been investigated, which can support smart waste management and help bridge one of the main challenges in society. Recently, different concepts have been tested where IoT technologies could be used for environmental protection, primarily for the monitoring of air quality, which is a big potential in that sense.
Healthcare systems can also be significantly improved with the application of IoT devices, i.e. via the E-health concept. An improved quality of services and patient safety could be enabled with an advanced IoT supported monitoring system. The prediction of life threatening states could be efficiently detected with a better treatment of patients, such as timely therapy decisions and qualitative rehabilitation. In general, large healthcare systems could also benefit from IoT, both in efficiency and from a cost aspect, which is important for hospitals. The current pandemic state with COVID-19 allowed for the consideration of different IoT applications or devices that could help in efficiently monitoring and controlling the pandemic, which proves the added value of IoT products.
The transportation sector is currently in gradual transition where a mix of transportation vehicle technologies is expected in upcoming decades with the involvement of electric vehicles primarily along with hybrid or hydrogen based vehicles. The main advancements of IoT in transportation are the support of the smart car concept where different vehicle operating parameters can be monitored in an efficient manner. The main advantage is early detection of severe failures, then regular maintenance, improved fuelling and finally improvement of safety and driving experience in general. The most challenging IoT application area is in the case of autonomous vehicles, where safety is the main goal and in that sense, significant research advancements are expected to occur in the near future.
The smart city concept is the most progressing IoT application area since cities have been vastly populated, which causes severe infrastructural issues. The main benefit of IoT technologies in the smart city concept is to bridge severe infrastructural challenges in highly populated cities. The improvement of life quality in cities is also expected thanks to the efficiency improvement of various convectional services in cities. The early detection of various and common daily problems in cities could be efficiently solved with IoT as with transportation issues, energy and water shortage supplies, security issues, etc. The biggest challenge in the smart city concept is directed to the efficient networking and operation of different sensing technologies, which must be followed with the proper education of the population.
Each technology that is rapidly progressing has got specific potential drawbacks that need to be carefully analysed and addressed. Since IoT devices are measured in billions, and with large potential impacts on the population, specific challenges need to be addressed, which were detected based on the herein conducted review. The main goal is to secure a sustainable and balanced development of IoT technologies. Therefore, further issues are briefly discussed below and should be carefully considered during the further development of IoT technologies:
- - the rapid development of IoT technologies causes fast consumption of raw materials to produce different electronic devices where unfortunately some of raw materials are already rare or becoming,
- - electronic devices are becoming more economically acceptable where a potentially large population would be affected. High production volumes are expected which can finally cause a rebound effect and a more rapid unwanted utilization of already limited resources,
- - the sustainability aspect and long-term effects of IoT technologies are not clear and insufficiently investigated. A noticeable amount of energy would be needed to operate IoT devices and the electronic industry is leaving different unfavourable environmental footprints that also need to be carefully investigated,
- - electronic waste will become one of the major issues caused with the planned rise of IoT products. Recycling rates must be improved and better e-waste management should be secured,
- - IoT technologies can cause social impacts in specific industrial branches or businesses since working labour could be reduced and direct social contacts have also been reduced. In that sense, the application of IoT technologies should be carefully considered taking the raised issues into account,
- - significant advancements in both specific electronic components as well as user-friendly software solutions are required,
- - further development in sensing technologies and advanced data acquisition systems is also required,
- - the minimization of energy consumption in IoT devices is a crucial target, i.e. reduction of energy supply.
From the herein addressed recent research findings within the VSI SpliTech 2019, it is obvious that developments in various IoT application sectors are promising but further advancements are expected and that are mainly focused on maximizing the efficiency of specific IoT supported processes or technologies, minimizing resource utilization (raw materials and energy) and environmental footprints. IoT technologies are an opportunity for humanity and can bring important as well as useful benefits to the population. The authors contributions within the JCLEPRO VSI SpliTech2019 provided quality discussion and presentation of the latest advancements in the field, and most important, they contributed to the better understanding of IoT application areas, technological possibilities, but also potential drawbacks and issues that should be carefully monitored in future terms. The crucial and important aspects are linked with sustainability where the rapid developments in IoT technologies must be carefully monitored from a resource and environmental point of view to ensure balanced and sustainable development of IoT products. Herein presented knowledge and published works in the Journal of Cleaner Production are serving as important foundations for researchers dealing with this challenging and dynamic research field.
CRediT authorship contribution statement
Sandro Nižetić: Conceptualization, Methodology, Supervision. Petar Šolić: Conceptualization, Methodology, Supervision. Diego López-de-Ipiña González-de-Artaza: Supervision. Luigi Patrono: Conceptualization, Methodology, Supervision.
Declaration of competing interest
We wish to confirm that there are no known conflicts of interest associated with this publication in Journal of Cleaner Production ( Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future ) and there has been no significant financial support for this work that could have influenced its outcome.
We confirm that the manuscript has been read and approved by all named authors and that there are no other persons who satisfied the criteria for authorship but are not listed. We further confirm that the order of authors listed in the manuscript has been approved by all of us.
We confirm that we have given due consideration to the protection of intellectual property associated with this work and that there are no impediments to publication, including the timing of publication, with respect to intellectual property. In so doing we confirm that we have followed the regulations of our institutions concerning intellectual property.
We understand that the Corresponding Author is the sole contact for the Editorial process (including Editorial Manager and direct communications with the office). He is responsible for communicating with the other authors about progress, submissions of revisions and final approval of proofs. We confirm that we have provided a current, correct email address which is accessible by the Corresponding Author and which has been configured to accept email from ( [email protected] ).
Acknowledgments
This work has been supported in part by Croatian Science Foundation under the project “Internet of Things: Research and Applications”, UIP-2017-05-4206, Croatia.
Handling editor: Cecilia Maria Villas Bôas de Almeida
- Aazam M., Zeadally S., Harras K.A. Deploying fog computing in industrial internet of things and industry 4.0. IEEE Transactions on Industrial Informatics. 2018 PP (99):1-1. [ Google Scholar ]
- Abdou M., Mohammed R., Hosny Z., Essam M., Zaki M., Hassan M., Eid M., Mostafa H. 2019. Proceedings of the International Conference on Microelectronics, ICM, Volume 2019-December, December 2019; pp. 103–107. Article number 9021613. [ Google Scholar ]
- Ajanovic A., Haas R. Economic and environmental prospects for battery electric- and fuel cell vehicles: a review. Fuel Cell. 2019; 19 (5):515–529. [ Google Scholar ]
- Al-Ali A.R., Zualkernan I.A., Rashid M., Gupta R., Alikarar M. A smart home energy management system using IoT and big data analytics approach. IEEE Trans. Consum. Electron. 2017; 63 (4) [ Google Scholar ]
- Al-Masri E., Diabate I., Jain R., Lam M.H., Nathala S.R. 2018 IEEE International Conference on Industrial Internet (ICII) 2018. A serverless IoT architecture for smart waste management systems. [ Google Scholar ]
- Alletto S., Cucchiara R., Del Fiore G., Mainetti L., Mighali V., Patrono L., Serra G. An indoor location-aware system for an IoT-based smart museum. IEEE Internet of Things Journal. 2015; 3 (2):244–253. [ Google Scholar ]
- Almusaylim Z.A., Alhumam A., Jhanjhi N.Z. Proposing a secure RPL based internet of things routing protocol: a review. Ad Hoc Netw. 2020; 101 Article number 102096. [ Google Scholar ]
- Web source: Arduino.cc, (accessed, April 22, 2020).
- Web source: Arduino low-power, "Arduino Low Power”, Online: github.com/arduino-libraries/ArduinoLowPower, (accessed April 2020.).
- Arumugam S.S., Umashankar V., Narendra N.C., Badrinath R., Mujumdar A.P., Holler J., Hernandez A. 2018 8th International Conference on Logistics, Informatics and Service Sciences (LISS) 2018. IOT enabled smart logistics using smart contracts. [ CrossRef ] [ Google Scholar ]
- Web source: Datasheet - ATECC508A, “ATECC508A”, Online: microchip.com/wwwproducts/en/ATECC508A, (accessed April 21, 2020).
- Web source: Datasheet - ATmega328P, Online: microchip.com/downloads/en/DeviceDoc/Atmel-7810-Automotive-Microcontrollers-ATmega328P_Datasheet.pdf (accessed April 21, 2020).
- Avancini D.B., Martins S.G.B., Rabelo R.A.L., Solic P., Rodrigues J.J.P.C. 2018 3rd International Conference on Smart and Sustainable Technologies (SpliTech) 2018. A flexible IoT energy monitoring solution. [ Google Scholar ]
- Bagdadee A.H., Zhang L., Saddam Hossain Remus M. A brief review of the IoT-based energy management system in the smart industry. Advances in Intelligent Systems and Computing. 2020; 1056 :443–459. [ Google Scholar ]
- Becnel T., Tingey K., Whitaker J., Sayahi T., Lê K., Goffin P., Butterfield A. A distributed low-cost pollution monitoring platform. IEEE Internet of Things Journal. 2019; 6 (6) [ Google Scholar ]
- Bhagya N.S., Murad K., Kijun H. Towards sustainable smart cities: a review of trends, architectures, components, and open challenges in smart cities. Sustainable Cities and Society. 2018; 38 :697–713. [ Google Scholar ]
- Bielski A., Zielina M., Młyńska A. Analysis of heavy metals leaching from internal pipe cement coating into potable water. Journal of Cleaner Produciton. 2020; 265 :121425. [ Google Scholar ]
- Biresselioglu M.E., Demir M.H., Demirbag Kaplan M., Solak B. Individuals, collectives, and energy transition: analysing the motivators and barriers of European decarbonisation. Energy Research and Social Science. 2020; 66 Article number 101493. [ Google Scholar ]
- Bisio I., Garibotto C., Lavagetto F., Sciarrone A. 2019 IEEE Global Communications Conference, GLOBECOM 2019 - Proceedings. 2019. Towards IoT-based ehealth services: a smart prototype system for home rehabilitation. Article number 9013194. [ Google Scholar ]
- Web source: Bootloader, “Optiboot Bootloader for Arduino and Atmel AVR”. github.com/Optiboot/optiboot, (accessed April 21, 2020).
- Bose B.K. Artificial intelligence techniques in smart grid and renewable energy systems—some example applications. Proc. IEEE. 2017; 105 (11) [ Google Scholar ]
- Brincat A.A., Pacifici F., Martinaglia S., Mazzola F. 2019 IEEE 5th World Forum on Internet of Things (WF-IoT) 2019. The internet of things for intelligent transportation systems in real smart cities scenarios. [ CrossRef ] [ Google Scholar ]
- Bylykbashi K., Qafzezi E., Ikeda M., Matsuo K., Barolli L. Fuzzy-based Driver Monitoring System (FDMS): implementation of two intelligent FDMSs and a testbed for safe driving in VANETs. Future Generat. Comput. Syst. 2020; 105 :665–674. [ Google Scholar ]
- Capuder T., Miloš Sprčić D., Zoričić D., Pandžić H. Review of challenges and assessment of electric vehicles integration policy goals: integrated risk analysis approach. Int. J. Electr. Power Energy Syst. 2020; 119 Article number 105894. [ Google Scholar ]
- Cavalera G., Conte Rosito R., Lacasa V., Mongiello M., Nocera F., Patrono L., Sergi I. 2019 4th International Conference on Smart and Sustainable Technologies (SpliTech) 2019. An innovative smart system based on IoT technologies for fire and danger situations. [ Google Scholar ]
- Chasin F., Paukstadt U., Gollhardt T., Becker J. 2020. Smart Energy Driven Business Model Innovation: an Analysis of Existing Business Models and Implications for Business Model Change in the Energy Sector; p. 122083. (in press) [ CrossRef ] [ Google Scholar ]
- Chen N., Qin F., Zhai Y., Cao H., Zhang R., Cao F. Evaluation of coordinated development of forestry management efficiency and forest ecological security: a spatiotemporal empirical study based on China’s provinces. J. Clean. Prod. 2020; 260 Article number 121042. [ Google Scholar ]
- Chen Y.-Q., Zhou B., Zhang M., Chen C.-M. Using IoT technology for computer-integrated manufacturing systems in the semiconductor industry. Applied Soft Computing Journal. 2020; 89 Article number 106065. [ Google Scholar ]
- Chen H.-C., Putra K.T., Tseng S.-S., Chen C.-L., Lin J.C.-W. A spatiotemporal data compression approach with low transmission cost and high data fidelity for an air quality monitoring system. Future Generat. Comput. Syst. 2020; 108 :488–500. [ Google Scholar ]
- Chou J.S., Hsu S.C., Ngo N.T., Lin C.W., Tsui C.C. Hybrid machine learning system to forecast electricity consumption of smart grid-based air conditioners. IEEE Systems Journal. 2019; 13 (3) [ Google Scholar ]
- Chugh A., Jain C., Mishra V.P. IoT-based multifunctional smart toy car. Lecture Notes in Networks and Systems. 2020; 103 :455–461. [ Google Scholar ]
- Conti M., Kaliyar P., Rabbani M.M., Ranise S. Attestation-enabled secure and scalable routing protocol for IoT networks. Ad Hoc Netw. 2020; 98 Article number 102054. [ Google Scholar ]
- Corchado J.M., Bajo J., Abraham A. GerAmi: improving healthcare delivery in geriatric residences. IEEE Intell. Syst. 2008; 23 (2):19–25. [ Google Scholar ]
- Das S., Lee S.-H., Kumar P., Kim K.-H., Lee S.S., Bhattacharya S.S. Solid waste management: scope and the challenge of sustainability. J. Clean. Prod. 2019; 228 :658–678. [ Google Scholar ]
- Dasari S.V., Gvk S., Bapat J., Das D. 2019 IEEE 16th India Council International Conference (INDICON) 2019. IoT testbed for thermal profiling of a smart building. [ Google Scholar ]
- Web source: The World Bank. Data.worldbank.org/indicator/sp.pop.grow?name_desc=true, (accessed, March 26, 2020).
- De Fazio R., Esposito Corcione C., Greco A., Ferrari F., Striani R., Catarinucci L., Chietera F.P., Colella R., Patrono L., Mighali V., Sergi I., Visconti P., Venere E., Pucciarelli M., Caiazzo M., Pastore P., Ivtchenko O., Abruzzese L., Fornaro A. 2019 IEEE 8th International Workshop on Advances in Sensors and Interfaces (IWASI) 2019. Sensors-based treatment system of the organic waste with RFID identification and on-cloud traceability. [ Google Scholar ]
- Dhana Shree K., Janani B., Reenadevi R., Rajesh R. Garbage monitoring system using smart bins. International Journal of Scientific and Technology Research. 2019; 11 (8):1921–1925. [ Google Scholar ]
- Dobre C., Bajenaru L., Marinescu I.A., Tomescu M. 2019 22nd International Conference on Control Systems and Computer Science. CSCS; 2018. Improving the quality of life for older people: from smart sensors to distributed platforms. [ CrossRef ] [ Google Scholar ]
- Douglas L.S.M., Rabelo R.A.L., Veloso A.F.S., Rodrigues J.J.P.C., dos Reis Junior Jose V. An adaptive data compression mechanism for smart meters considering a demand side management scenario. J. Clean. Prod. 2020; 255 :120190. [ Google Scholar ]
- Duarte P.A.S., Barreto F.M., Aguilar P.A.C., Boudy J., Andrade R.M.C., Viana W. 2018 13th Annual Conference on System of Systems Engineering. SoSE; 2018. AAL platforms challenges in IoT era: a tertiary study. [ Google Scholar ]
- Duy T.K., Huu Hanh H., Tjoa A.M., Quirchmayr G. Proceedings - 2019 19th International Symposium on Communications and Information Technologies, ISCIT 2019. 2019. SemIDEA: towards a semantic IoT data analytic framework for facilitating environmental protection; pp. 481–486. Article number 8905178. [ Google Scholar ]
- Web source: European Commissions. Ec.europa.eu/growth/tools-databases/dem/monitor/sites/default/files/DTM_Agriculture%204.0%20IoT%20v1.pdf, (accessed, April 1, 2020).
- El-Emam Rami S., Ozcan H., Zamfirescu C. Updates on promising thermochemical cycles for clean hydrogen production using nuclear energy. J. Clean. Prod. 2020; 262 :121424. [ Google Scholar ]
- Fachechi A., Mainetti L., Palano L., Patrono L., Stefanizzi M.L., Vergallo R., Chu P., Gadh R. A new vehicle-to-grid system for battery charging exploiting IoT protocols. Proceedings of the IEEE International Conference on Industrial Technology. 2015:2154–2159. doi: 10.1109/ICIT.2015.7125414. 2015. art. no. 7125414. [ CrossRef ] [ Google Scholar ]
- Fan Y.V., Lee C.T., Lim J.S., Klemeš J.J., Le P.T.K. Cross-disciplinary approaches towards smart, resilient and sustainable circular economy. J. Clean. Prod. 2019; 232 :1482–1491. [ Google Scholar ]
- Web source: Food and agriculture organization of the United Nations fao.org/news/story/en/item/196402/icode/, (accessed, April 1, 2020).
- Farahani B., Barzegari M., Shams Aliee F., Shaik K.A. Towards collaborative intelligent IoT eHealth: from device to fog, and cloud. Microprocess. Microsyst. 2020 Article number 102938. [ Google Scholar ]
- Farooq M.S., Riaz S., Abid A., Umer T., Zikria Y.B. Role of iot technology in agriculture: A systematic literature review. 2020; 9 (2) Article number 319. [ Google Scholar ]
- Ferrari F., Striani R., Minosi S., De Fazio R., Visconti P., Patrono L., Catarinucci L., Corcione C.E., Greco A. An innovative IoT-oriented prototype platform for the management and valorisation of the organic fraction of municipal solid waste. J. Clean. Prod. 2020; 247 :119618. [ Google Scholar ]
- Web source: Flash storage, “FlashStorage library for Arduino”, Online: github.com/cmaglie/FlashStorage, (accessed April 20, 2020).
- Web source: Louis Columbus. Forbes.com/sites/louiscolumbus/2018/06/06/10-charts-that-will-challenge-your-perspective-of-iots-growth/#79c388e3ecce, (accessed, March 21, 2020).
- Gagliano A., Tina G.M., Aneli S., Nižetić S. Comparative assessments of the performances of PV/T and conventional solar plants. J. Clean. Prod. 2019; 219 :304–315. [ Google Scholar ]
- Gao P., Li J. Understanding sustainable business model: a framework and a case study of the bike-sharing industry. J. Clean. Prod. 2020; 267 :122229. [ Google Scholar ]
- Garrido-Hidalgo C., Ramirez F.J., Olivares T., Roda-Sanchez L. The adoption of Internet of Things in a Circular Supply Chain framework for the recovery of WEEE: the case of Lithium-ion electric vehicle battery packs. Waste Manag. 2020; 103 :32–44. [ PubMed ] [ Google Scholar ]
- Giama E., Papadopoulos A.M. Benchmarking carbon footprint and circularity in production processes: the case of stonewool and extruded polysterene. J. Clean. Prod. 2020; 257 :120559. [ Google Scholar ]
- Web source: Globalewaste. Globalewaste.org/wp-content/uploads/2018/10/Global-E-waste-Monitor-2017.pdf, (accessed, March 25, 2020).
- Grubišić-Čabo F., Nižetić S., Marinić Kragić I., Čoko D. Further progress in the research of fin-based passive cooling technique for the free-standing silicon photovoltaic panels. Int. J. Energy Res. 2019; 43 (8):3475–3495. [ Google Scholar ]
- Grycan W. Legislative support for improving sustainable and smart electricity consumption in polish residential sector. J. Clean. Prod. 2020; 266 :121995. [ Google Scholar ]
- Guptha C.K.N., Bhaskar M.G., Meghasree V. 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions (CSITSS) 2018. Design of IoT Architecture for order picking in a typical warehouse. [ CrossRef ] [ Google Scholar ]
- Hussain M., Butt A.R., Uzma F., Ahmed R., Irshad S., Rehman A., Yousaf B. A comprehensive review of climate change impacts, adaptation, and mitigation on environmental and natural calamities in Pakistan. Environ. Monit. Assess. 2020; 192 (1) Article number 48. [ PubMed ] [ Google Scholar ]
- Idwan S., Mahmood I., Zubairi J.A., Matar I. Optimal management of solid waste in smart cities using internet of things. Wireless Pers. Commun. 2020; 110 (1):485–501. [ Google Scholar ]
- Imeri A., Khadraoui D. 2018 9th IFIP International Conference on New Technologies, Mobility and Security. NTMS; 2018. The security and traceability of shared information in the process of transportation of dangerous goods. [ CrossRef ] [ Google Scholar ]
- Web source: NET Smart IoT Solutions.iot.farsite.com/iot-explained/netbin-fill-level-monitoring-for-a-smart-bin/?gclid=Cj0KCQjwmpb0BRCBARIsAG7y4zY3y-4cEOz4orGAHPjrDqKFRwVAZOQu6yNGEZlzcU16U2yLotXeQl4aAuqkEALw_wcB, (accessed, April 2, 2020).
- Irizar-Arrieta A., Casado-Mansilla D., Garaizar P., López-de-Ipiña D., Retegi A. User perspectives in the design of interactive everyday objects for sustainable behaviour. Int. J. Hum. Comput. Stud. 2020; 137 Article number 102393. [ Google Scholar ]
- Janik A., Ryszko A., Szafraniec M. Scientific landscape of smart and sustainable cities literature: a bibliometric analysis. Sustainability. 2020; 12 (3) Article number 779. [ Google Scholar ]
- John J., Varkey M.S., Selvi M. Security attacks in s-wbans on iot based healthcare applications. Int. J. Innovative Technol. Explor. Eng. 2019; 9 (1):2088–2097. [ Google Scholar ]
- Jonkeren O., Francke J., Visser J. A shift-share based tool for assessing the contribution of a modal shift to the decarbonisation of inland freight transport. European Transport Research Review. 2019; 11 (1) Article number 8. [ Google Scholar ]
- Kakkavas G., Gkatzioura D., Karyotis V., Papavassiliou S. A review of advanced algebraic approaches enabling network tomography for future network infrastructures. Future Internet. 2020; 12 (2) Article Number 20. [ Google Scholar ]
- Kalair Ali Raza, Naeem Abas, Qadeer Ul Hasan, Seyedmahmoudian Mehdi, Khan Nasrullah. Demand side management in hybrid rooftop photovoltaic integrated smart nano grid. J. Clean. Prod. 2020; 258 :120747. [ Google Scholar ]
- Kang K.D., Kang H., Ilankoon I.M.S.K., Chong C.Y. Electronic waste collection systems using Internet of Things (IoT): household electronic waste management in Malaysia. J. Clean. Prod. 2020; 252 Article number 119801. [ Google Scholar ]
- Kaur K., Garg S., Kaddoum G., Bou-Harb E., Choo K.-K.R. A big data-enabled consolidated framework for energy efficient software defined data centers in IoT setups. IEEE Transactions on Industrial Informatics. 2020; 16 (4):2687–2697. Article number 8825507. [ Google Scholar ]
- Kausmally M.A., Samson A.M., Cheng Y.S., Gobee S., Durairajah V. Harvesting waste energy from industrial chimney using thermoelectric generator and wind turbine with battery storage system integrated to IoT. International Journal of Advanced Science and Technology. 2020; 29 (3):2487–2499. [ Google Scholar ]
- Keng Z.X., Chong S., Ng C.G., Ridzuan N.I., Hanson S., Pan G.-T., Lau P.L., Supramaniam C.V., Singh A., Chin C.F., Lam H.L. Community-scale composting for food waste: a life-cycle assessment-supported case study. J. Clean. Prod. 2020; 261 Article number 121220. [ Google Scholar ]
- Kim S., Cho J.Y., Jeon D.H., Hwang W., Song Y., Jeong S.Y., Jeong S.W., Yoo H.H., Sung T.H. Propeller-based underwater piezoelectric energy harvesting system for an autonomous IoT sensor system. J. Kor. Phys. Soc. 2020; 76 (3):251–256. [ Google Scholar ]
- Klemeš J.J., Varbanov P.S., Ocłoń P., Chin H.H. Towards efficient and clean process integration: utilisation of renewable resources and energy-saving technologies. Energies. 2019; 12 (21) Article number 4092. [ Google Scholar ]
- Kong X., Meng Z., Meng L., Tomiyama H. 2018 International Conference on Advanced Mechatronic Systems. ICAMechS; 2018. A privacy protected fall detection IoT system for elderly persons using depth camera. [ CrossRef ] [ Google Scholar ]
- Kozina A., Radica G., Nižetić S. Analysis of methods towards reduction of harmful pollutants from Diesel engines. J. Clean. Prod. 2020; 262 :121105. [ Google Scholar ]
- Kumar B.R.S., Varalakshmi N., Lokeshwari S.S., Rohit K., Manjunath, Sahana D.N. 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques. ICEECCOT; 2017. Eco-friendly IOT based waste segregation and management. [ CrossRef ] [ Google Scholar ]
- Li W., Logenthiran T., Phan V.T., Woo W.L. Implemented IoT-based self-learning home management system (SHMS) for Singapore. IEEE Internet of Things Journal. 2018; 5 (3) [ Google Scholar ]
- Li J., Feng S., Luo T., Guan Z. What drives the adoption of sustainable production technology? Evidence from the large-scale farming sector in East China. J. Clean. Prod. 2020; 257 Article number 120611. [ Google Scholar ]
- Li Y., Gao M., Yang L., Zhang C., Zhang B., Zhao X. Design of and research on industrial measuring devices based on Internet of Things technology. Ad Hoc Netw. 2020; 102 Article number 102072. [ Google Scholar ]
- Li J., Han Y., Mao G., Wang P. Optimization of exhaust emissions from marine engine fueled with LNG/diesel using response surface methodology. Energy Sources, Part A Recovery, Util. Environ. Eff. 2020; 42 (12):1436–1448. [ Google Scholar ]
- Liegeard J., Manning L. Use of intelligent applications to reduce household food waste. Crit. Rev. Food Sci. Nutr. 2020; 60 (6):1048–1061. [ PubMed ] [ Google Scholar ]
- Lin Y., Lu X., Fang F., Fan J. First Int. Symp. On Future Information and Communication Technologies for Ubiquitous HealthCare. 2013. Personal health care monitoring and emergency response mechanisms; pp. 1–5. [ Google Scholar ]
- Lin Y.-C., Chi W.J., Lin Y.Q. The improvement of spatial-temporal resolution of PM2.5 estimation based on micro-air quality sensors by using data fusion technique. Environ. Int. 2020; 134 Article number 105305. [ PubMed ] [ Google Scholar ]
- Luque-Vega L.F., Michel-Torres D.A., Lopez-Neri E., Carlos-Mancilla M.A., González-Jiménez L.E. Iot smart parking system based on the visual-aided smart vehicle presence sensor: SPIN-V. Sensors. 2019; 20 (5) Article number 1476. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Machorro-Cano I., Alor-Hernández G., Paredes-Valverde M.A., Rodríguez-Mazahua L., Sánchez-Cervantes J.L., Olmedo-Aguirre J.O. HEMS-IoT: a big data and machine learning-based smart home system for energy saving. Energies. 2020; 13 (5) Article number 1097. [ Google Scholar ]
- Mahmood Y., Kama N., Azmi A., Ya’acob S. An IoT based home automation integrated approach: impact on society in sustainable development perspective. Int. J. Adv. Comput. Sci. Appl. 2020; 11 (1):240–250. [ Google Scholar ]
- Mainetti L., Patrono L., Sergi I. 22nd International Conference on Software, Telecommunications and Computer Networks. SoftCOM; 2014. A survey on indoor positioning systems; pp. 111–120. 2014, art. no. 7039067. [ Google Scholar ]
- Mainetti L., Patrono L., Secco A., Sergi I. 2016 International Multidisciplinary Conference on Computer and Energy Science. SpliTech; 2016. An IoT-aware AAL system for elderly people. [ CrossRef ] [ Google Scholar ]
- Mainetti L., Patrono L., Secco A., Sergi I. An IoT-aware AAL system to capture behavioral changes of elderly people. Journal of Communications Software and Systems. 2017; 13 (2):68–76. [ Google Scholar ]
- Majee A., Bhatia M., Gnana Swathika O.V. 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA) 2018. IoT based microgrid automation for optimizing energy usage and controllability. [ Google Scholar ]
- Marinić-Kragić I., Vučina D., Milas Z. Computational analysis of Savonius wind turbine modifications including novel scooplet-based design attained via smart numerical optimization. J. Clean. Prod. 2020; 262 :121310. [ Google Scholar ]
- Martín-Lopo M.M., Boal J., Sánchez-Miralles Á. A literature review of IoT energy platforms aimed at end users. Comput. Network. 2020; 171 Article number 107101. [ Google Scholar ]
- Maskeliunas R., Damaševičius R., Segal S. A review of internet of things technologies for ambient assisted. Living environments. Future Internet. 2019; 11 :259. doi: 10.3390/fi11120259. [ CrossRef ] [ Google Scholar ]
- Matulić N., Radica G., Barbir F., Nižetić S. Commercial vehicle auxiliary loads powered by PEM fuel cell. Int. J. Hydrogen Energy. 2019; 44 (20):10082–10090. Issue 20. [ Google Scholar ]
- Web source: MCP1700, “MCP1700”, Online: microchip.com/products/en/MCP1700 (accessed, April 21, 2020).
- Meinel L., Findeisen M., Heß M., Apitzsch A., ì Hirtz G. Automated real-time surveillance for ambient assisted living using an omnidirectional camera. IEEE Int. Conf. Consum. Electron. 2014:396–399. doi: 10.1109/ICCE.2014.6776056. [ CrossRef ] [ Google Scholar ]
- Mekki K., Bajic E., Chaxel F., Meyer F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT express. 2019; 5 (1):1–7. [ Google Scholar ]
- Mendes, Douglas L.S., Rabelo Ricardo A.L., Veloso Artur F.S., Rodrigues Joel J.P.C., dos Reis Junior Jose V. An adaptive data compression mechanism for smart meters considering a demand side management scenario. J. Clean. Prod. 2020; 255 :120190. [ Google Scholar ]
- Mishra V.P., Jain C., Chugh A. IoT-based data logger for environmental monitoring. Lecture Notes in Networks and Systems. 2020; 103 :463–471. [ Google Scholar ]
- Web source: MKRWAN1300, “MKRWAN1300 High sleep current”, Online: github.com/arduino-libraries/MKRWAN/issues/30, (accessed April 22, 2020).
- Mohammadian H.D. 2019 IEEE Global Engineering Education Conference (EDUCON) 2019. IoE – a solution for energy management challenges. [ Google Scholar ]
- Moniruzzaman M., Khezr S., Yassine A., Benlamri R. Blockchain for smart homes: review of current trends and research challenges. Comput. Electr. Eng. 2020; 83 Article number 106585. [ Google Scholar ]
- Morello R., De Capua C., Fulco G., Mukhopadhyay S.C. A smart power meter to monitor energy flow in smart grids: the role of advanced sensing and IoT in the electric grid of the future. IEEE Sensor. J. 2017; 17 (23):7828–7837. [ Google Scholar ]
- Mukta M.Y., Rahman M.A., Asyhari A.T., Alam Bhuiyan M.Z. IoT for energy efficient green highway lighting systems: challenges and issues. J. Netw. Comput. Appl. 2020; 158 Article number 102575. [ Google Scholar ]
- Muthu B.A., Sivaparthipan C.B., Manogaran G., Sundarasekar R., Kadry S., Shanthini A., Dasel A. IOT based wearable sensor for diseases prediction and symptom analysis in healthcare sector. Peer-to-Peer Networking and Applications. 2020 doi: 10.1007/s12083-019-00823-2. [ CrossRef ] [ Google Scholar ]
- Nayanatara C., Divya S., Mahalakshmi E.K. 2018 International Conference on Computation of Power, Energy, Information and Communication (ICCPEIC) 2018. Micro-grid management strategy with the integration of renewable energy using IoT. [ Google Scholar ]
- Nils Jakob Johannesen, Kolhe Mohan, Goodwin Morten. Relative evaluation of regression tools for urban area electrical energy demand forecasting. J. Clean. Prod. 2020; 218 :555–564. [ Google Scholar ]
- Nivetha R., Preethi S., Priyadharshini P., Shunmugapriya B., Paramasivan B., Naskath J. Smart health monitoring system using iot for assisted living of senior and challenged people. International Journal of Scientific and Technology Research. 2020; 9 (2):4285–4288. [ Google Scholar ]
- Nižetić S. An atmospheric gravitational vortex as a flow object: improvement of the three-layer model. Geofizika. 2010; 27 (1):1–20. [ Google Scholar ]
- Nizetic S., Coko D., Marasovic I. Experimental study on a hybrid energy system with small- and medium-scale applications for mild climates. Energy. 2014; 75 :379–389. [ Google Scholar ]
- Nižetić S., Djilali N., Papadopoulos A., Rodrigues J.J.P.C. Smart technologies for promotion of energy efficiency, utilization of sustainable resources and waste management. J. Clean. Prod. 2019; 231 :565–591. [ Google Scholar ]
- Osterrieder P., Budde L., Friedli T. The smart factory as a key construct of industry 4.0: a systematic literature review. Int. J. Prod. Econ. 2020; 221 Article number 107476. [ Google Scholar ]
- Padmaja B., Narasimha Rao P.V., Madhu Bala M., Rao Patro E.K. Proceedings of the International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), I-SMAC 2018, 26 February 2019. 2019. pp. 18–21. Article number 8653736. [ Google Scholar ]
- Pantelia C., Kylilia A., Paris A., Fokaides P. Building information modelling applications in smart buildings: from design to commissioning and beyond A critical review. J. Clean. Prod. 2020; 265 :121766. [ Google Scholar ]
- Papa A., Mital M., Pisano P., Del Giudice M. E-health and wellbeing monitoring using smart healthcare devices: an empirical investigation. Technol. Forecast. Soc. Change. 2020; 153 Article number 119226. [ Google Scholar ]
- Patel H.K., Mody T., Goyal A. 2019 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU) 2019. Arduino based smart energy meter using GSM. [ Google Scholar ]
- Pawar P., TarunKumar M., Vittal K.,P. An IoT based Intelligent Smart Energy Management System with accurate forecasting and load strategy for renewable generation. Measurement: Journal of the International Measurement Confederation. 2020; 152 Article number 107187. [ Google Scholar ]
- Perković T., Šolić P., Zargariasl H., Čoko D., Rodrigues J.J.P.C. Smart parking sensors: state of the art and performance evaluation. J. Clean. Prod. 2020; 262 :121181. Volume 262. [ Google Scholar ]
- Perković T., Damjanović S., Šolić P., Patrono L., Rodrigues J.J. Fourth International Congress on Information and Communication Technology. Springer; Singapore: 2020. Meeting challenges in IoT: sensing, energy efficiency, and the implementation; pp. 419–430. [ Google Scholar ]
- Web source: Pew Research Centre. Pewresearch.org/fact-tank/2019/06/17/worlds-population-is-projected-to-nearly-stop-growing-by-the-end-of-the-century/, (accessed, March 21, 2020).
- Pivac N., Nižetić S., Zanki V., Papadopoulos A.M. Application of wearable sensory devices in predicting occupant’s thermal comfort in office buildings during the cooling season. IOP Conf. Ser. Earth Environ. Sci. 2019; 410 (1) Article number 012092. [ Google Scholar ]
- Porru S., Misso F.E., Pani F.E., Repetto C. Smart mobility and public transport: opportunities and challenges in rural and urban areas. J. Traffic Transport. Eng. 2020; 7 (1):88–97. [ Google Scholar ]
- Proto S., Di Corso E., Apiletti D., Cagliero L., Cerquitelli T., Malnati G., Mazzucchi D. REDTag: a predictive maintenance framework for parcel delivery services. IEEE Access. 2020; 8 :14953–14964. doi: 10.1109/ACCESS.2020.2966568. [ CrossRef ] [ Google Scholar ]
- Qiu B., Duan F.b, He G. Value adding industrial solid wastes: impact of industrial solid wastes upon copper removal performance of synthesized low cost adsorbents. Energy Sources, Part A Recovery, Util. Environ. Eff. 2020; 42 (7):835–848. [ Google Scholar ]
- Web source: Quamtra.quamtra.com/en/technology/, (accessed, April 2, 2020).
- Rahimi M., Songhorabadi M., Kashani M.H. Fog-based smart homes: a systematic review. J. Netw. Comput. Appl. 2020; 153 Article number 102531. [ Google Scholar ]
- Reena J.K., Parameswari R. 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing. COMITCon; 2019. A smart health care monitor system in IoT based human activities of daily living: a review. [ CrossRef ] [ Google Scholar ]
- Rishav M., Maity R., Ghosh D., Ganesh V.N., Siva kumar Internet of thing based smart power grid for smart city. Int. J. Recent Technol. Eng. 2019; 8 (1):450–453. Special Issue 4. [ Google Scholar ]
- Web source: RTC3231,”Extremely Accurate I2C-Integrated RTC/TCXO/Crystal”, Online: https://datasheets.maximintegrated.com/en/ds/DS3231.pdf (accessed April 2020).
- Rushikesh Babu K., Vyjayanthi C. 2017 IEEE Region 10 Symposium (TENSYMP) 2017. Implementation of net zero energy building (NZEB) prototype with renewable energy integration. [ Google Scholar ]
- Saha S., Mondal S., Saha A., Purkait P. 2018 IEEE Applied Signal Processing Conference (ASPCON) 2018. Design and implementation of IoT based smart energy meter. [ Google Scholar ]
- Saki M., Abolhasan M., Lipman J.E. A novel approach for big data classification and transportation in rail networks. IEEE Trans. Intell. Transport. Syst. 2020; 21 (3):1239–1249. Article number 8701707. [ Google Scholar ]
- Salagare S., Prasad R. An overview of internet of dental things: new frontier in advanced dentistry. Wireless Pers. Commun. 2020; 110 (3):1345–1371. [ Google Scholar ]
- Sarajčev P., Jakus D., Vasilj J. Optimal scheduling of power transformers preventive maintenance with Bayesian statistical learning and influence diagrams. J. Clean. Prod. 2020; 258 :120850. [ Google Scholar ]
- Sathishkumar D., Karthikeyan C. Adaptive power management strategy-based optimization and estimation of a renewable energy storage system in stand-alone microgrid with machine learning and data monitoring. Int. J. Wavelets, Multiresolut. Inf. Process. 2020; 18 (1) Article number 1941023. [ Google Scholar ]
- Savari G.F., Krishnasamy V., Sathik J., Ali Z.M., Abdel Aleem S.H.E. Internet of Things based real-time electric vehicle load forecasting and charging station recommendation. ISA (Instrum. Soc. Am.) Trans. 2020; 97 :431–447. [ PubMed ] [ Google Scholar ]
- Web source: Elsevier. scopus.com, (accessed, March 1, 2020).
- Shafi U., Mumtaz R., García-Nieto J., Hassan S.A., Zaidi S.A.R., Iqbal N. Precision agriculture techniques and practices: from considerations to applications. Sensors. 2020; 17 (1) Article number 3796. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Shamayleh A., Awad M., Farhat J. IoT based predictive maintenance management of medical equipment. J. Med. Syst. 2020; 44 (4) Article number 72. [ PubMed ] [ Google Scholar ]
- Shen X., Fantacci R., Chen S. Internet of vehicles. Proc. IEEE. 2020; 108 (2):242–245. Article number 8967259. [ Google Scholar ]
- Sivanageswara Rao G., Raviteja K., Phanindra G., Vignesh D. Analysis of internet of things concept for the application of smart cities. International Journal of Advanced Science and Technology. 2020; 29 (3):3691–3704. 2020. [ Google Scholar ]
- Stavrakas V., Flamos A. A modular high-resolution demand-side management model to quantify benefits of demand-flexibility in the residential sector. Energy Convers. Manag. 2020; 205 Article number 112339. [ Google Scholar ]
- Web source: STM32, “STM32LowPower”, Online: github.com/stm32duino/STM32LowPower (accessed April 22, 2020).
- Suciu G., Necula L., Iosu R., Usurelu T., Ceaparu M. IoT and Cloud-Based Energy Monitoring and Simulation Platform 11th International Symposium on Advanced Topics in Electrical Engineering (ATEE) 2019. [ Google Scholar ]
- Sujeeth S., Gnana Swathika O.V. 2018. 2nd International Conference on Inventive Systems and Control (ICISC) 2018. IoT based automated protection and control of DC microgrids. [ Google Scholar ]
- Tawalbeh N., Abusamaha H.M., Al-Salaymeh A. Proceedings of 2019 IEEE PES Innovative Smart Grid Technologies Europe, ISGT-Europe 2019, September 2019. 2019. Domestic appliances scheduling using BPSO and IoT. Article number 8905695. [ Google Scholar ]
- Web source: Techradarpro.techradar.com/news/rise-of-the-internet-of-things-iot, (accessed, March 20, 2020).
- Web source: Rick Leblanc. Thebalancesmb.com/e-waste-recycling-facts-and-figures-2878189, (accessed, March 25, 2020).
- Web source: TPL5010, Online: ti.com/lit/ds/symlink/tpl5010.pdf, (accessed, April 20, 2020).
- Web source: TPL5110,”Adafruit TPL5110 Power Timer Breakout,” Online:learn.adafruit.com/adafruit-tpl5110-power-timer-breakout/, (accessed, April 22, 2020).
- Tsang Yung Po, Choy King Lun, Wu Chun Ho, Ho George To Sum, Lam Hoi Yan. Blockchain-driven IoT for food traceability with an integrated consensus mechanism. IEEE Access. 2019; 7 :129000–129017. doi: 10.1109/ACCESS.2019.2940227. [ CrossRef ] [ Google Scholar ]
- Tuballa M.L., Lochinvar Abundo M. A review of the development of Smart Grid technologies. Renew. Sustain. Energy Rev. 2016; 59 :710–725. [ Google Scholar ]
- Web source: Tutorial - Atmega328p, “How to run Atmega328p for a year on coin cell battery,” Online:home-automation-community.com/arduino-low-power-how-to-run-atmega328p-for-a-year-on-coin-cell-battery/, (accessed, April 21, 2020).
- Web source: Tutorial - Low-power nodes, “Very Low Power Nodes”, Online: loratracker.uk/very-low-power-nodes/, (accessed, April 22, 2020).
- Tzankova Z. Public policy spillovers from private energy governance: new opportunities for the political acceleration of renewable energy transition. Energy Research and Social Science. 2020; 67 Article number 101504. [ Google Scholar ]
- Web source: United Nations. Un.org/development/desa/en/news/population/2018-revision-of-world-urbanization-prospects.html, (accessed, March 26, 2020).
- Uribe J.A., Duitama J.F., Gómez N.G. Personalized message emission in a mobile application for supporting therapeutic adherence. 13th Int. Conf. on e-Health Networking Applications and Services (Healthcom) 2011:15–20. [ Google Scholar ]
- Valente F.J., Neto A.C. IEEE International Conference on RFID Technology & Application (RFID-TA); Warsaw: 2017. Intelligent steel inventory tracking with IoT / RFID; pp. 158–163. [ CrossRef ] [ Google Scholar ]
- Villa-Henriksen A., Edwards G.T.C.b, Pesonen L.A., Green O., Sørensen C.A.G. Internet of Things in arable farming: implementation, applications, challenges and potential. Biosyst. Eng. 2020; 191 :60–84. [ Google Scholar ]
- Villarreal V., Fontecha J., Hervás R., Bravo J. Mobile and ubiquitous architecture for the medical control of chronic diseases through the use of intelligent devices: using the architecture for patients with diabetes. Future Generat. Comput. Syst. 2014; 34 :161–175. [ Google Scholar ]
- Villarrubia G., Bajo J., de Paz J.F., Corchado J.M. Monitoring and detection platform to prevent anomalous situations in home care. Sensors. 2014; 14 (6):9900–9921. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Voca N., Ribic B. Biofuel production and utilization through smart and sustainable biowaste management. J. Clean. Prod. 2020; 259 :120742. [ Google Scholar ]
- Vohnout S., Engelman M., Enikov E. Miniature MEMS-based data recorder for prognostics and health management (PHM) IEEE AUTOTESTCON. 2010:1–8. doi: 10.1109/AUTEST.2010.5613608. [ CrossRef ] [ Google Scholar ]
- Wang M., Tan J., Li Y. 2015 IEEE International Conference on Communication Software and Networks (ICCSN) 2015. Design and implementation of enterprise asset management system based on IOT technology. [ CrossRef ] [ Google Scholar ]
- Wang X.C., Klemeš J.J., Long X., Zhang P., Sabev-Varbanov P., Fan W., Dong X., Wang Y. Measuring the environmental performance of the EU27 from the Water-Energy-Carbon nexus perspective. J. Clean. Prod. 2020; 265 Article number 121832. [ Google Scholar ]
- Web source: World Health Organization. Who.int/health-topics/coronavirus#tab=tab_1, (accessed, April 2, 2020).
- Wu C.-M., Liu H.-L., Huang L.-M., Lin J.-F., Hsu M.-W. Proceedings of the 2018 IEEE International Conference on Advanced Manufacturing, ICAM 2018. 2019. Integrating BIM and IoT technology in environmental planning and protection of urban utility tunnel construction; pp. 198–201. Article number 8615004. [ Google Scholar ]
- Xin Y., Tao F. Developing climate-smart agricultural systems in the North China Plain. Agric. Ecosyst. Environ. 2020; 291 Article number 106791. [ Google Scholar ]
- Xu Z., Fan W., Dong X., Wang X.-C., Liu Y., Xu H., Klemeš J.J. Analysis of the functional orientation of agricultural systems from the perspective of resource circulation. J. Clean. Prod. 2020; 258 Article number 120642. [ Google Scholar ]
- Yang M., Wang G., Ahmed K.F., Adugna B., Eggen M., Atsbeha E., You L., Koo J., Anagnostou E. vol. 723. 2020. (The Role of Climate in the Trend and Variability of Ethiopia’s Cereal Crop Yields). Article number 137893. [ PubMed ] [ Google Scholar ]
- Yapeng W., Xu Y., Yutian Z., Yue L., Cuthbert L. Bluetooth positioning using RSSI and triangulation methods. IEEE Consumer Communications and Networking Conference (CCNC) 2013:837–842. [ Google Scholar ]
- Zaidan A.A., Zaidan B.B. A review on intelligent process for smart home applications based on IoT: coherent taxonomy, motivation, open challenges, and recommendations. Artif. Intell. Rev. 2020; 53 (1):141–165. [ Google Scholar ]
- Web source: Natalie Gagliordi. Zdnet.com/article/iot-to-drive-growth-in-connected-devices-through-2022-cisco/, (accessed, March 24, 2020).
- Zeinalnezhad M., Gholamzadeh A., Feybi C., Goni A., Klemeš J.J. Air pollution prediction using semi-experimental regression model and adaptive neuro-fuzzy inference system. J. Clean. Prod. 2020; 261 :121218. [ Google Scholar ]
- Zhang L., Alharbe N., Atkins A.S. 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) 2016. An IoT application for inventory management with a self-adaptive decision model. [ CrossRef ] [ Google Scholar ]
- Zhang D., Chan C.C., You Zhou G. Enabling Industrial Internet of Things (IIoT) towards an emerging smart energy system. Global Energy Interconnection. 2018; 1 (1):39–47. [ Google Scholar ]
- Zheng C., Yuan J., Zhu L., Zhang Y., Shao Q. From digital to sustainable: a scientometric review of smart city literature between 1990 and 2019. J. Clean. Prod. 2019; 258 Article number 120689. [ Google Scholar ]
- Zhou B., Li W., Wing Chan K., Cao Y., Kuang Y., Liu X., Wang X. Smart home energy management systems: concept, configurations, and scheduling strategies. Renew. Sustain. Energy Rev. 2016; 61 :30–40. [ Google Scholar ]

IMAGES
VIDEO
COMMENTS
The Internet of Things (IoT)-centric concepts like augmented reality, high-resolution video streaming, self-driven cars, smart environment, e-health care, etc. have a ubiquitous presence now. These applications require higher data-rates, large bandwidth, increased capacity, low latency and high throughput. In light of these emerging concepts, IoT has revolutionized the world by providing ...
Recently, IoT has emerged. as a new technology that is used to express a modern. wireless te lecommunication network, and it can be define d. as an intelligent and interoperability node ...
The rise of IoT technologies is currently intense and according to projections for the next 10 years, over 125 ·10 9 IoT devices are expected to be connected, (Techradar, 2019).The expected investments in IoT technologies are also high with expectations being over 120 ·10 9 USD by 2021, with a compound annual growth rate of about 7.3%, (Forbes, 2018).
Calls for papers. This special issue on Advances in Internet of Fuzzy Things (IoFT) in the Elsevier Internet of Things Journal is a place for highly original ideas about how fuzzy logic combined with IoT is going to shape IoT of the future. Hence, it focuses on …. Guest editors: David Ramiro Troitiño; Tanel Kerikmäe.
Internet of Things (IoT) is a new paradigm that has changed the traditional way of living into a high tech life style. Smart city, smart homes, pollution control, energy saving, smart transportation, smart industries are such transformations due to IoT. A lot of crucial research studies and investigations have been done in order to enhance the technology through IoT.
Agrawal et al. presented a paper in a wider context of IoT, mainly enabling the factors for integration in various technologies. Furthermore, key technologies involved in the implementation of IoT and its major application domain have been discussed. ... Since research on IoT is an area of interest for both academia and the industrial sector ...
Purpose and Scope. The IEEE IoT Journal (IoT-J), launched in 2014 (" Genesis of the IoT-J "), publishes papers on the latest advances, as well as review articles, on the various aspects of IoT. Topics include IoT system architecture, IoT enabling technologies, IoT communication and networking protocols, IoT services and applications, and ...
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... (IoT) network, research on low ...
The aim of this paper is to categorize analytically and statistically, and analyze the current research techniques on IoT applications approaches published from 2011 to 2018. A technical taxonomy is presented for the IoT applications approaches according to the content of current studies that are selected with SLR process in this study ...
Research in this field shows that with AIoT, IoT devices are enabled to learn from data and make swift decisions when an abnormal behavior is detected in the network in real-time. 95 Chakrabarty and Engels 68 proposed a framework for the IoT enabled smart city using AI to mitigate a range of present and future cyber threats. The massive ...
5,823 views. 5 articles. An innovative journal which captures state-of-the-art research in architectures, technologies, and applications of the Internet of Things, opening the door to new interactions between things and hu...
Microstrip Array Antenna. This paper presents the design of 2*1 and 4*1 RFID reader microstrip array antenna at 2.4GHz for the Internet of things (IoT) networks which are Zigbee, Bluetooth and WIFI. The proposed antenna is composed of identical circular shapes radiating patches printed in FR4 substrate.
1.3 Paper organization. This paper is further organized as shown in Figure 3. ... Optimized solutions and algorithms development is a vast field of research in context of IoT operations and big data handling. Application and system software development for programming, data processing, security and privacy assurance is another important area ...
This review paper compiles information from several other surveys and research papers regarding IoT, AI, and attacks with and against AI and explores the relationship between these three topics with the purpose of comprehensively presenting and summarizing relevant literature in these fields. In recent years, the use of the Internet of Things ...
The main research areas that we found are between IoT: 36, Cloud: 4, Network: 7, Blockchain: 7. Note that publication venues often have several research areas in their calls for papers, e.g., IoT, network. Therefore a portion of the papers could be classified in several research areas at the same time (e.g., IoT, network).
Although a great deal has been written on concepts related to the IoT, there is a critical shortage of papers on IoT research-based studies and IoT literature reviews. Theory as related to IoT adoption and implementation appears to be non-existent. In Table 1 we show the IoT concept matrix and paper classification of the relevant papers reviewed.
The aim of this viewpoint paper is to provide an overview of the current IoT technology in health care, outline how IoT devices are improving health service delivery, and outline how IoT technology can affect and disrupt global health care in the next decade. ... Specific future research on IoT technology needs to address how IoT devices can be ...
The Internet of Things (IoT) is an interconnected network of objects which range from simple sensors to smartphones and tablets ... The fifth generation (5G) of cellular networks will bring 10 Gb/s user speeds, 1000-fold increase in system capacity, and 100 times higher connection density. In response to these requirements, the 5G networks will ...
This paper presents a comprehensive review of RPL, the challenges faced by the protocol and proposed improvements to the routing protocol. ... To secure the IoT devices, many research works have ...
This review paper discussed and presented latest research findings that were included within the JCELPRO VSI SpliTech2019 and dedicated to the 4th International Conference on Smart and Sustainable Technologies (SpliTech 2019). The contributions as well as herein presented knowledge is summarized and discussed in upcoming sections.