- Machine Learning
- Data Science
- Data Security
- Console Gaming
- Gaming Guides
- Sustainability
- AR & VR

Cybersecurity
Understanding the different types of computer viruses.
July 13, 2020 • Zachary Amos
Staying informed about the threats facing your computer is the first step in defending against them. If you know what to watch out for, you can more easily avoid risks. A good place to start is with knowing the many types of computer virus that are out there.
All viruses are malicious bits of code that spread from user to user, harming their host computers. Different types of computer viruses go about this in a variety of ways, though. Knowing some common signs of these viruses will help you stay protected.
Virus vs. Malware
You may hear people use the words “virus” and “malware” interchangeably, but that’s not entirely correct. Think of it like rectangles and squares. All squares are rectangles, but not all rectangles are squares, and it’s the same with viruses and malware.
There are more than one billion pieces of malware on the internet right now, but not all of these are viruses. Some are aggressive forms of hacks and breaches, while others are subtler subcategories of malware. For instance, it’s also important to note that “ransomware” is a branch under malware. There can be different types of ransomware, and it can infect computers and cause irreversible damage, just the same as a virus would.
Viruses are a considerable portion of malware in general, so it’s critical to get a feel for what you could encounter one day. Here are the types of computer virus you may encounter.
1. Ransomware
First, let’s take a look at ransomware. This nasty piece of malware does as its name suggests — it will hold some of your files or data hostage and ask for ransom money. Ransomware works its way through your drives and will capture various extensions, like .PPT, .XLS and .DOC files.
Once it gets a hold of your files, it encrypts them so they’re inaccessible and will state that you need to pay a ransom in order to get the key that gives you access to your files again. Some experts say to avoid paying the ransom, but it’s tricky in the moment because the request could double in value.
Sometimes the key is in the encryption, but still, it’s a draining process that you’ll want to avoid. Keep an eye out for suspicious files that claim to be software updates.
2. Boot Secure Virus
Your computer’s master boot record is a special type of boot sector at the start of a drive, like certain disks or removable drives. Here is where your computer will locate the operating system and ensure that it will boot with the device’s storage and memory.
A virus that infects the master boot record is unfortunately one of the most dangerous you could be dealing with. Like many of the viruses on this list, it’s hard to remove and can encrypt the boot sector, which can damage the code.
Boot secure viruses originally came about with floppy disks, but have adapted over time through USB drives or emails. Money and NYB are common examples of this kind of virus.
3. Resident Viruses
Resident viruses hide in your computer’s RAM. Since they reside in the memory, they can infect any file that you run. As a result, resident viruses spread especially fast and cause as much damage as they can if not detected and removed early. However, there’s a slow version of resident viruses, too. These infect files at a much slower rate and are then harder to detect or notice.
Many types of computer virus need users to execute certain processes to work, but not resident viruses. Instead, whenever you run a program or open a file, it activates the virus. This all makes it particularly challenging to find and remove resident viruses.
4. Direct Action Viruses
Direct action viruses are another type of computer virus that puts your content at risk. These are similar to resident viruses, in the sense that their prime targets are files. Unlike resident viruses, though, direct action viruses go after file type, most often .exe and .com files. They attach themselves to a file and once you open it, they activate and spread.
Direct action viruses can restrict your access, but don’t delete anything or hinder your computer’s performance. They typically don’t hide in your computer’s memory either. You should be able to find them without much trouble once you encounter inaccessible files.
5. Overwrite Viruses
Viruses don’t have to be complicated to be effective. Overwrite viruses are a prime example of this concept, overwriting the content in a file, as their name implies, and residing in said file. This behavior means you must delete the infected file to get rid of the virus or else it will spread.
Since they destroy content, this type of computer virus is especially harmful and aggravating. You could end up losing content you were working on or have been saving for years. One of the most significant malware pandemics in history , the ILOVEYOU outbreak, involved overwriting.
6. Browser Hijackers
A less severe but more common type of computer virus is browser hijackers. Like overwrite viruses, these do what their name suggests they do. They take over your browser to redirect you to different websites.
Browser hijackers fall under the category of malware. These could happen somewhat commonly today, replacing a home page, search engine or even an error page with another site.
The websites browser hijackers open are often just irritating advertisements but could also be more malicious. You usually don’t have to worry about them much, though. Nowadays, most browsers include built-in protection against browser hijackers.
7. Multipartite Viruses
Multipartite viruses are one of the most threatening types of computer virus. Unlike most other viruses, multipartite viruses can infect your computer in a variety of ways. The method depends on your operating system and what kind of files you have, but multipartite viruses will usually have several openings. They can target both files and your computer’s boot sector simultaneously.
Since multipartite viruses can infect so many different applications, they can spread much faster than some other viruses. Upon replication, this virus also changes their binary pattern — antivirus software may not detect it due to it appearing as something else entirely after it switches.
Typically, you’ll need an advanced antivirus software or expert help since this form of computer virus is so adaptive and evasive.
Staying Safe from these Types of Computer Virus
It would be near impossible to list every specific type of computer virus out in the digital realm. These seven examples of computer viruses are some of the most common, though, and demonstrate a variety of virus behaviors. Understanding how they can infect your computer can help you know what you need to protect.
Antivirus software can take care of many of these viruses. Even with this layer of protection, though, you should be careful to avoid downloading any files that may be infected.
Now knowing the dangers of all the different types of computer viruses, you can navigate the internet with ease, staying safe and virus-free at all times.
Recent Stories
How to spot misinformation on social media and protect yourself, what is an ios rapid security response, 23 spotify podcasts guaranteed to eradicate boredom, follow us on, get the latest tech stories and news in seconds.
Sign up for our newsletter below to receive updates about technology trends

35 Weird Science Facts Worth Knowing in 2024

What Are the Main Components of Robots?

Playing Chess by Yourself in 2024: How It Benefits Your Brain

The Negative Impact of Technology on the Environment

5 Augmented Reality Apps for Interior Design

Is TikTok Getting Banned in the US? Everything We Know

How Much Are Bits Worth on Twitch?

Does 5G Cause Radiation? Current Popular 5G Facts and Myths

What Is the Metaverse and Why Is Everyone Talking About It?

Are Discord Messages Encrypted? How Safe is Discord?
Similar content.

How to Get People to Care About Phishing Statistics
Don’t trust [email protected] unless you like malware.

Take These IT Security Measures at Home to Prevent Cyberattacks

5 Reasons Why Cybersecurity Matters in Modern Times

- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

9 types of computer virus and how they do their dirty work
From macro viruses and boot sector viruses to droppers and packers, here’s a look at 9 common virus types, what they do, and the function they perform for attackers..

The human mind loves to categorize things, and malware is no exception. We here at CSO have done our part: our malware explainer breaks down malware based on how it spreads (self-propagating worms , viruses piggybacking on other code, or sneakily disguised Trojans ) as well as by what it does to infected machines ( rootkits , adware , ransomware , cryptojacking , and malvertising , oh my).
You can find a lot of this type of technical taxonomy, and there’s certainly utility to it. In particular, it can be helpful to differentiate different types of malware infection vectors rather than lumping everything together as a “virus,” despite popular usage of the term. But we can also put too much emphasis on these sorts of divisions.
“A lot of the terminology used to describe malware in the 90s and early 00s is still technically accurate, but maybe less relevant than it once was,” says Jacob Ansari, Security Advocate and Emerging Cyber Trends Analyst for Schellman, a global independent security and privacy compliance assessor. “While malware of the prior decades got installed on the target system and then ran by itself without human intervention, most modern attack campaigns are operated by groups of people, what we commonly call threat actors. Attackers still attempt to evade detection and persist despite defenses, and make use of a variety of programming or scripting languages to produce their hostile code.”
So we asked Ansari and other security pros about how they break down the types of malware they deal with. In general, we found that there are two different perspectives on malware taxonomy: you can think of how viruses do their dirty work (i.e., what they do to you), or about where they fit into an ecosystem (i.e., what they do for an attacker).
9 common types of computer virus
- Macro viruses
- Polymorphic viruses
- Resident viruses
- Boot sector viruses
- Multipartite viruses
- Beacon/payload
- Command and control
Virus types defined by what they do to you If you want a great perspective on the different types of malware, you could do worse than talk to someone who writes it for a living. That’s Dahvid Schloss’s job: he’s the managing lead for offensive security at cybersecurity professional services firm Echelon Risk + Cyber, where he works on malware meant to emulate real threat actors to execute command-and-control platforms on his company’s adversarial emulation and red team engagements. He broke down the different types of viruses he works with by their function.
Macro viruses. “This category is probably the most common malware technique in the world,” says Schloss. “Roughly 92% of external attacks begin with phishing , and macros are the core of the problem. A macro is an automated execution of keystrokes or mouse actions that a program can do without user interaction—typically, we’re talking about Microsoft Word/Excel macros, which can automate repetitive tasks on the worksheet or document.”
Macros are an extremely common malware type. “The delivery method is believable, especially when it looks work related,” says Schloss. “Also, the coding language (Visual Basic, in Microsoft’s case) is quite simplistic. Thus, macro viruses reduce the amount of technology skill required to write them.”
Lauren Pearce, incident response lead at cloud security company Redacted, agreed. “We continue to see significant damage from unsophisticated malware,” she says. “The simple Office document macro reigns supreme as an initial infection vector.”
Polymorphic viruses. “While the macro virus is the easiest to code, this type [the polymorphic virus ] would be the most complex due to the virus being exactly what its name says: polymorphic,” says Schloss. “Each time the code runs, it executes slightly differently, and typically every time it moves to a new machine, its code will be slightly different.”
You should treat all your children (or your enemies) equally, but Schloss admits that “this category of viruses is my favorite, as it’s intricate and is extremely hard to investigate and detect.”
Resident viruses. This is a particularly pernicious category: a disembodied virus that doesn’t exist as part of a file. “The virus itself is actually executing within the RAM of the host,” says Schloss. “The virus code is not stored within the executable that called it; instead it’s usually stored on a web-accessible site or storage container. The executable that calls the resident code is usually written as non-malicious by intent to avoid detection by an antivirus application.”
The term resident virus implies the existence of a non-resident virus, of course. Schloss defines this as “a virus that is contained within the executable that is calling it. These viruses most commonly spread by abusing enterprise services.”
Boot sector viruses. “This category I like to call the ‘nation state cocktail,'” Schloss explains. “These types of viruses are meant to provide the threat actor with unrestricted and deep persistence. They will infect all the way down to the computer’s master boot record (MBR), meaning that even if you reimage your machine, the virus will persist and will be able to execute within the memory of the host upon boot. These types of viruses are rare to see outside of nation-state threat actors, and almost always rely on a zero-day exploit to be able to reach the level of the MBR or are spread through physical media such as infected USB or hard drives.”
Multipartite viruses. While some malware developers may specialize, others take an “all of the above” approach, attacking everywhere all at once. “These types of viruses are usually the hardest to contain and deal with,” says Schloss. “They will infect multiple parts of a system, including memory, files, executables, and even the boot sector. We see more and more viruses of this variety, and these types of viruses will spread in whatever way they can, usually implementing multiple techniques to maximize spread.”
Types of malware defined by what they do for the attacker
Another way of thinking about different malware you’ll encounter is how they fit into the larger picture of an overall attack. Remember what Schellman’s Ansari said above: modern malware is deployed by teams, and the viruses themselves can be thought of as a team as well. “Many malware campaigns consist of an array of components, sometimes each developed separately or even sourced from other threat actors,” Ansari says. He breaks down some of the different players:
Droppers. “This piece of malware is intended to drop other malware onto the infected system,” Ansari said. “Victims may get infected with a dropper from a hostile link, attachment, download, or the like—and it typically does not persist after dropping the next stage of malware.”
“Macro malware falls into the category of a dropper,” adds Redacted’s Pearce. “It’s malware made for the sole purpose of downloading and executing additional malware.”
Beacon/payload . These malware types are the next stage in the attack. “Often installed by a dropper, a beacon or payload is the malware that signals back to the threat actor its newly installed means of access,” says Ansari. “From here, an attacker can access the victim systems through the means established by the beacon and access the system, the data it contains, or other systems on the network.”
Packers. These components package other components, using cryptographic techniques as a means of evading detection. “Some sophisticated malware campaigns use a series of packers, nested like a stacking doll,” says Ansari. “Each contains another packed item, until the final payload is able to execute.”
Command and control. Every team needs a leader, and that’s the role command and control plays for these collaborative malware components. “These systems, sometimes called C&C, CNC, or C2 , operate outside of the victim’s environment and allow the threat actor to communicate with the other components of the malware campaign installed on the target system,” says Ansari. “When law enforcement targets a threat actor, they often seize the command and control systems as part of their efforts to stop the threat.”
Classifying computer viruses
In the end, whatever taxonomy we use shouldn’t be overly rigid, but should instead make it easier to communicate important information about cyberthreats. And that means tailoring your language for your audience, says Ori Arbel, CTO of CYREBRO, a security services provider.
“If I’m writing for CISOs, they would think about it from a risk perspective,” he says, “while the general public would better understand commonly used names in the news. These virus categorizations are presented from the point of view of what will be most easily understood—but doing it that way doesn’t necessarily communicate the best actions for security professionals to take. If I’m writing for a group of threat intelligence pros, I would use terms related to geolocation and the attacker’s motivation rather than what the virus actually does.”
We’ll end with one last way to categorize viruses, one that really only makes sense from the perspective of the virus hunters themselves: viruses that are worthy adversaries, and those that are not. “As a reverse engineer, I take pleasure from the puzzle of reversing,” says Redacted’s Pearce. “Macros present a significant threat to a network, but they are not particularly fun to reverse. I enjoy reversing samples that use anti-analysis techniques to actively fight against being reversed. Malware may use anti-debugging techniques that detect and respond to a debugger via methods such as check summing or timing attacks. Use of anti-analysis techniques indicate a skilled malware author and serve to increase the amount of time in between detection of a sample and extraction of useful indicators to counter it.”
Just because your adversaries are criminals doesn’t mean you can’t respect them for putting pride into their work.
Related content
Sap users are at high risk as hackers exploit application vulnerabilities, understanding cisa's proposed cyber incident reporting rules, where in the world is your ai identify and secure ai across a hybrid environment, more open-source project takeover attempts found after xz utils attack, from our editors straight to your inbox.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
Defense in depth explained: layering tools and processes for better security, what is an sbom software bill of materials explained, 11 infamous malware attacks: the first and the worst, most popular authors.

Show me more
Sensitive us government data exposed after space-eyes data breach.

10 tips to keep IP safe

US supreme court ruling suggests change in cybersecurity disclosure process

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

CSO Executive Sessions: Former convicted hacker Hieu Minh Ngo on blindspots in data protection

LockBit feud with law enforcement feels like a TV drama

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
What are Computer Viruses?
Learn about the types of computer viruses, examples, and tips to prevent them.
- Get A Threat Assessment
- Read the Outbreak Alerts Report

Computer Virus Definition
Chances are you’ve heard how important it is to keep viruses out, but what is a computer virus exactly? A computer virus is a type of malicious software, or malware, that spreads between computers and causes damage to data and software.
Computer viruses aim to disrupt systems, cause major operational issues, and result in data loss and leakage. A key thing to know about computer viruses is that they are designed to spread across programs and systems. Computer viruses typically attach to an executable host file, which results in their viral codes executing when a file is opened. The code then spreads from the document or software it is attached to via networks, drives, file-sharing programs, or infected email attachments.
Common Signs of Computer Viruses
1. speed of system.
A computer system running slower than usual is one of the most common signs that the device has a virus. This includes the system itself running slowly, as well as applications and internet speed suffering. If a computer does not have powerful applications or programs installed and is running slowly, then it may be a sign it is infected with a virus.
2. Pop-up windows
Unwanted pop-up windows appearing on a computer or in a web browser are a telltale sign of a computer virus. Unwanted pop-ups are a sign of malware, viruses, or spyware affecting a device.
3. Programs self-executing
If computer programs unexpectedly close by themselves, then it is highly likely that the software has been infected with some form of virus or malware. Another indicator of a virus is when applications fail to load when selected from the Start menu or their desktop icon. Every time that happens, your next step should be to perform a virus scan and remove any files on programs that might not be safe to use.
4. Accounts being logged out
Some viruses are designed to affect specific applications, which will either cause them to crash or force the user to automatically log out of the service.
5. Crashing of the device
System crashes and the computer itself unexpectedly closing down are common indicators of a virus. Computer viruses cause computers to act in a variety of strange ways, which may include opening files by themselves, displaying unusual error messages, or clicking keys at random.
6. Mass emails being sent from your email account
Computer viruses are commonly spread via email. Hackers can use other people's email accounts to spread malware and carry out wider cyberattacks. Therefore, if an email account has sent emails in the outbox that a user did not send, then this could be a sign of a computer virus.
7. Changes to your homepage
Any unexpected changes to a computer—such as your system’s homepage being amended or any browser settings being updated—are signs that a computer virus may be present on the device.
Get a Cybersecurity Threat Assessment
Know your vulnerabilities - get the facts about your security risk and at no cost.
How Do Computer Viruses Attack and Spread?
In the early days of computers, viruses were spread between devices using floppy disks. Nowadays, viruses can still be spread via hard disks and Universal Serial Bus (USB) devices, but they are more likely to be passed between devices through the internet.
Computer viruses can be spread via email, with some even capable of hijacking email software to spread themselves. Others may attach to legitimate software, within software packs, or infect code, and other viruses can be downloaded from compromised application stores and infected code repositories. A key feature of any computer virus is it requires a victim to execute its code or payload, which means the host application should be running.
Types of Computer Viruses
1. resident virus.
Viruses propagate themselves by infecting applications on a host computer. A resident virus achieves this by infecting applications as they are opened by a user. A non-resident virus is capable of infecting executable files when programs are not running.
2. Multipartite virus
A multipartite virus uses multiple methods to infect and spread across computers. It will typically remain in the computer’s memory to infect the hard disk, then spread through and infect more drives by altering the content of applications. This results in performance lag and application memory running low.
Multipartite viruses can be avoided by not opening attachments from untrusted sources and by installing trusted antivirus software. It can also be prevented by cleaning the boot sector and the computer’s entire disk.
3. Direct action
A direct action virus accesses a computer’s main memory and infects all programs, files, and folders located in the autoexec.bat path, before deleting itself. This virus typically alters the performance of a system but is capable of destroying all data on the computer’s hard disk and any USB device attached to it. Direct action viruses can be avoided through the use of antivirus scanners. They are easy to detect, as is restoring infected files.
4. Browser hijacker
A browser hijacker manually changes the settings of web browsers, such as replacing the homepage, editing the new tab page, and changing the default search engine. Technically, it is not a virus because it cannot infect files but can be hugely damaging to computer users, who often will not be able to restore their homepage or search engine. It can also contain adware that causes unwanted pop-ups and advertisements.
Browser hijackers typically attach to free software and malicious applications from unverified websites or app stores, so only use trusted software and reliable antivirus software.
5. Overwrite virus
Overwrite viruses are extremely dangerous. They can delete data and replace it with their own file content or code. Once files get infected, they cannot be replaced, and the virus can affect Windows, DOS, Linux, and Apple systems. The only way this virus can be removed is by deleting all of the files it has infected, which could be devastating. The best way to protect against the overwrite virus is to use a trusted antivirus solution and keep it updated.
6. Web scripting virus
A web scripting virus attacks web browser security, enabling a hacker to inject web-pages with malicious code, or client-side scripting. This allows cyber criminals to attack major websites, such as social networking sites, email providers, and any site that enables user input or reviews. Attackers can use the virus to send spam, commit fraudulent activity, and damage server files.
Protecting against web scripting is reliant on deploying real-time web browser protection software, using cookie security, disabling scripts, and using malicious software removal tools.
7. File infector
A file infector is one of the most common computer viruses. It overwrites files when they are opened and can quickly spread across systems and networks. It largely affects files with .exe or .com extensions. The best way to avoid file infector viruses is to only download official software and deploy an antivirus solution.
8. Network Virus
Network viruses are extremely dangerous because they can completely cripple entire computer networks. They are often difficult to discover, as the virus could be hidden within any computer on an infected network. These viruses can easily replicate and spread by using the internet to transfer to devices connected to the network. Trusted, robust antivirus solutions and advanced firewalls are crucial to protecting against network viruses.
9. Boot Sector Virus
A boot sector virus targets a computer’s master boot record (MBR). The virus injects its code into a hard disk’s partition table, then moves into the main memory when a computer restarts. The presence of the virus is signified by boot-up problems, poor system performance, and the hard disk becoming unable to locate. Most modern computers come with boot sector safeguards that restrict the potential of this type of virus.
Steps to protecting against a boot sector virus include ensuring disks are write-protected and not starting up a computer with untrusted external drives connected.
Exampes of Computer Viruses
Is trojan a virus.
A Trojan horse is a type of program that pretends to be something it is not to get onto a device and infect it with malware. Therefore, a Trojan horse virus is a virus disguised to look like something it is not. For example, viruses can be hidden within unofficial games, applications, file-sharing sites, and bootlegged movies.
Is a worm a virus?
A computer worm is not a virus. Worms do not need a host system and can spread between systems and networks without user action, whereas a virus requires users to execute its code.
Is ransomware a virus?
Ransomware is when attackers lock victims out of their system or files and demand a ransom to unlock access. Viruses can be used to carry out ransomware attacks.
Is rootkit a virus?
A rootkit is not a virus. Rootkits are software packages that give attackers access to systems. They cannot self-replicate or spread across systems.
Is a software bug a virus?
"Bug" is a common word used to describe problems with computers, but a software bug is not a virus. A bug is a flaw or mistake in software code, which hackers can exploit to launch a cyberattack or spread malware .
How To Prevent Your Computer From Viruses
1. use a trusted antivirus product.
Trusted computer antivirus products are crucial to stop malware attacks and prevent computers from being infected with viruses. These antivirus concepts will protect devices from being infected through regular scans and identifying and blocking malware.
2. Avoid clicking pop-up advertisements
Unwanted pop-up advertisements are more than likely to be linked to computer viruses and malware. Never click on pop-up advertisements because this can lead to inadvertently downloading viruses onto a computer.
3. Scan your email attachments
A popular way to protect your device from computer viruses is to avoid suspicious email attachments, which are commonly used to spread malware. Computer antivirus solutions can be used to scan email attachments for potential viruses.
4. Scan the files that you download using file-sharing programs
File-sharing programs, particularly unofficial sites, are also popular resources for attackers to spread computer viruses. Avoid downloading applications, games, or software from unofficial sites, and always scan files that have been downloaded from any file-sharing program.
Cybersecurity Resources
- Cybersecurity
- Types of Cyber Attacks
- IT vs OT Cybersecurity
- AI Cybersecurity
- Cyber Threat Intelligence
- Cybersecurity Management
- Network Security
- Data Security
- Email Security
- Endpoint Security
- Web Security
- Enterprise Security
- Cybersecurity Mesh
Quick Links
- Fortinet Products
- Fortinet Demos
- Analyst Reports
Stop inbound email threats and drive security awareness.
Authenticate email and identify risky suppliers.
Protect identities in hybrid enterprises from account takeover.
Defend data and manage insider threat.
Leverage proactive expertise, operational continuity and deeper insights from our skilled experts.

Human-centric cybersecurity packages from Proofpoint. Complete protection against today's risks—tailored to your organization's unique needs. Maximize security. Optimize value.
Protect your people from email and cloud threats with an intelligent and holistic approach.
Help your employees identify, resist and report attacks before the damage is done.
Prevent data loss via negligent, compromised and malicious insiders by correlating content, behavior and threats.
Manage risk and data retention needs with a modern compliance and archiving solution.
Keep your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk.
Learn about this growing threat and stop attacks by securing today’s top ransomware vector: email.
Implement the very best security and compliance solution for your Microsoft 365 collaboration suite.
Secure access to corporate resources and ensure business continuity for your remote workers.
Protect your email deliverability with DMARC.
Today’s cyber attacks target people. Learn about our unique people-centric approach to protection.
Become a channel partner. Deliver Proofpoint solutions to your customers and grow your business.
Learn about Proofpoint Extraction Partners.
Learn about our global consulting and services partners that deliver fully managed and integrated solutions.
Learn about our relationships with industry-leading firms to help protect your people, data and brand.
Learn about the technology and alliance partners in our Social Media Protection Partner program.
Small Business Solutions for channel partners and MSPs.
Find the information you're looking for in our library of videos, data sheets, white papers and more.
Keep up with the latest news and happenings in the ever‑evolving cybersecurity landscape.
Learn about the human side of cybersecurity. Episodes feature insights from experts and executives.
Get the latest cybersecurity insights in your hands – featuring valuable knowledge from our own industry experts.
Learn about the latest security threats and how to protect your people, data, and brand.
Connect with us at events to learn how to protect your people and data from ever‑evolving threats.
Read how Proofpoint customers around the globe solve their most pressing cybersecurity challenges.
Browse our webinar library to learn about the latest threats, trends and issues in cybersecurity.
Get free research and resources to help you protect against threats, build a security culture, and stop ransomware in its tracks.
Proofpoint is a leading cybersecurity company that protects organizations' greatest assets and biggest risks: their people.
Stand out and make a difference at one of the world's leading cybersecurity companies.
Read the latest press releases, news stories and media highlights about Proofpoint.
Learn about how we handle data and make commitments to privacy and other regulations.
Learn about our people-centric principles and how we implement them to positively impact our global community.
Access the full range of Proofpoint support services.
What Is a Computer Virus?
Table of contents, types of computer viruses, what causes computer viruses, how do computer viruses work, how do viruses spread, what is a computer worm, what does a computer virus do, computer viruses vs. malware, signs of computer virus, examples of computer virus, how to remove a computer virus, how to prevent computer viruses, computer virus definition.
A computer virus is an ill-natured software application or authored code that can attach itself to other programs, self-replicate, and spread itself onto other devices. When executed, a virus modifies other computer programs by inserting its code into them. If the virus’s replication is successful, the affected device is considered “infected” with a computer virus.
The malicious activity carried out by the virus’s code can damage the local file system, steal data, interrupt services, download additional malware, or any other actions the malware author coded into the program. Many viruses pretend to be legitimate programs to trick users into executing them on their devices, delivering the computer virus payload.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:.
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
Every computer virus has a payload that performs an action. The threat actor can code any malicious activity into the virus payload, including simple, innocuous pranks that don’t do any harm. While a few viruses have harmless payloads, most of them cause damage to the system and its data. There are nine main virus types, some of which could be packaged with other malware to increase the chance of infection and damage. The nine major categories for viruses on computers are:
Boot Sector Virus
Your computer drive has a sector solely responsible for pointing to the operating system so that it can boot into the interface. A boot sector virus damages or controls the boot sector on the drive, rendering the machine unusable. Attackers usually use malicious USB devices to spread this computer virus. The virus is activated when users plug in the USB device and boot their machine.
Web Scripting Virus
Most browsers have defenses against malicious web scripts, but older, unsupported browsers have vulnerabilities allowing attackers to run code on the local device.
Browser Hijacker
A computer virus that can change the settings on your browser will hijack browser favorites, the home page URL, and your search preferences and redirect you to a malicious site. The site could be a phishing site or an adware page used to steal data or make money for the attacker.
Resident Virus
A virus that can access computer memory and sit dormant until a payload is delivered is considered a resident virus. This malware may stay dormant until a specific date or time or when a user performs an action.
Direct Action Virus
When a user executes a seemingly harmless file attached to malicious code, direct-action viruses deliver a payload immediately. These computer viruses can also remain dormant until a specific action is taken or a timeframe passes.
Polymorphic Virus
Malware authors can use polymorphic code to change the program’s footprint to avoid detection. Therefore, it’s more difficult for an antivirus to detect and remove them.
File Infector Virus
To persist on a system, a threat actor uses file infector viruses to inject malicious code into critical files that run the operating system or important programs. The computer virus is activated when the system boots or the program runs.
Multipartite Virus
These malicious programs spread across a network or other systems by copying themselves or injecting code into critical computer resources.
Macro Virus
Microsoft Office files can run macros that can be used to download additional malware or run malicious code. Macro viruses deliver a payload when the file is opened and the macro runs.
Computer viruses are standard programs; instead of offering useful resources, these programs can damage your device. Computer viruses are typically crafted by hackers with various intentions, like stealing sensitive data to causing chaos in systems. Some hackers create these malicious programs for fun or as a challenge, while others have more sinister motives like financial gain or cyber warfare.
Hackers may exploit weak points in an operating system or app to acquire unapproved access and power over a user’s machine to achieve their goals.
- Ego-driven: Some virus authors seek fame within the hacker community by creating destructive or widespread viruses that garner media attention.
- Cybercrime: Hackers often use computer viruses as tools for ransomware attacks, identity theft, and other forms of online fraud.
- Sabotage: In some cases, disgruntled employees create computer viruses to intentionally damage their employer’s infrastructure.
- Cyber espionage: State-sponsored hackers may develop advanced persistent threats (APTs) using custom-made malware designed for long-term infiltration into targeted networks.
For a threat actor to execute a virus on your machine, you must initiate execution. Sometimes, an attacker can execute malicious code through your browser or remotely from another network computer. Modern browsers have defenses against local machine code execution, but third-party software installed on the browser could have vulnerabilities that allow viruses to run locally.
The delivery of a computer virus can happen in several ways. One common method is via a phishing email . Another technique is hosting malware on a server that promises to provide a legitimate program. It can be delivered using macros or by injecting malicious code into legitimate software files.
At their core, computer viruses are discreet programs that hitch a ride on other files or applications. In most cases, their primary objective is to replicate and spread like wildfire.
Computer viruses function as malicious software programs designed to infect other programs by modifying them in some way. In doing so, a virus will attach itself to an unsuspecting file or application in order to spread.
The Infection Process
A virus can attach itself to any legitimate program or document that supports macros to execute its code, such as an email attachment or a file download from a website. Once the file is opened or downloaded, the virus springs into action and starts executing.
Hiding in Plain Sight
Computer viruses can be quite crafty to remain hidden from both users and antivirus software alike. Viruses employ stealth techniques such as polymorphism, which changes their appearance, or encryption methods.
The Damage Done
Once activated, a virus may wreak havoc on your computer system. It can steal sensitive data, corrupt files, slow down performance, and even crash your entire system. It can spread from system to system after a user takes action that either intentionally or accidentally facilitates it.
It’s important to note that viruses are just one type of malware, and many other types of malicious software can harm your computer or steal your personal information.
Proofpoint Threat Response
No defense can stop every attack
Computer viruses spread through various channels, and being aware of these channels is essential to protect yourself and your organization from infection.
Email Attachments
One method of virus transmission is through email attachments. Hackers often disguise their malicious code as seemingly harmless files, such as documents or images unsuspecting users open without a second thought. For example, Ursnif banking Trojan campaigns are known to spread via email attachments posing as invoices or financial statements.
Internet Downloads
Viruses can also hide in software installers, media files, or even browser extensions that you download from the web. It’s important to be cautious when downloading files from unknown sources or sketchy websites. A notorious case was the Download.com scandal, where popular applications were bundled with adware and other unwanted programs by default.
File Sharing Networks
File sharing networks like torrent sites and peer-to-peer platforms can easily transmit viruses. Innocent-looking movie torrents or cracked software may carry hidden payloads designed to compromise your device upon installation. For example, The Pirate Bay used a browser-based cryptocurrency miner, so when someone visited the website, their computer was used to mine cryptocurrency without their knowledge or consent.
Removable Media
Viruses can attach to removable media, such as USB drives and CDs/DVDs, infecting any computer they’re plugged into. The infamous Stuxnet worm is a prime example of a virus that spreads through removable media.
To protect yourself and your organization from computer viruses, always exercise caution and employ robust cybersecurity measures like up-to-date antivirus software and regular system scans. Remember, knowledge is power, especially when preventing viruses and cyber-attacks.
A computer worm is a type of malware designed to replicate itself to spread to other computers. Unlike computer viruses, worms do not require a host program to spread and self-replicate. Instead, they often use a computer network to spread themselves, relying on security failures on the target computer to access it.
Once a worm infects a computer, it uses that device as a host to scan and infect other computers. When these new worm-infested computers are compromised, the worm continues to scan and infect other computers using these computers as hosts. Worms operate by consuming heavy memory and bandwidth loads, resulting in overloaded servers, systems, and networks.
The way a computer virus acts depends on how it’s coded. It could be something as simple as a prank that doesn’t cause any damage, or it could be sophisticated, leading to criminal activity and fraud. Many viruses only affect a local device, but others spread across a network environment to find other vulnerable hosts.
A computer virus that infects a host device continues delivering a payload until it’s removed. Most antivirus vendors offer small removal programs that eliminate the virus. Polymorphic viruses make removal difficult because they change their footprint consistently. The payload could be stealing data, destroying data, or interrupting services on the network or the local device.
While overlapping in intention and meaning, malware and viruses are two distinct terms that are often used interchangeably.
Malware is a general term for any type of malicious software, while a virus is a specific type of malware that self-replicates by inserting its code into other programs. While viruses are a type of malware, not all malware is a virus.
Malware can take many forms, including viruses, worms, trojans, spyware , adware, and ransomware, and it can be distributed through infected websites, flash drives, emails, and other means. A virus requires a host program to run and attaches itself to legitimate files and programs. It causes a host of malicious effects, such as deleting or encrypting files, modifying applications, or disabling system functions.
Malware authors write code that is undetectable until the payload is delivered. However, like any software program, bugs could present issues while the virus runs. Signs that you have a computer virus include:
- Popup windows, including ads (adware) or links to malicious websites.
- Your web browser home page changes, and you did not change it.
- Outbound emails to your contact list or people on your contact list alert you to strange messages sent by your account.
- The computer crashes often, runs out of memory with few active programs or displays the blue screen of death in Windows.
- Slow computer performance even when running few programs or the computer was recently booted.
- Unknown programs start when the computer boots or when you open specific programs.
- Passwords change without your knowledge or your interaction on the account.
- Frequent error messages arise with basic functions like opening or using programs.
The web contains millions of computer viruses, but only a few have gained popularity and infect record numbers of machines. Some examples of widespread computer viruses include:
- Morris Worm – One of the earliest and most pervasive computer virus examples, this self-replicating computer program spread through the early Internet in 1988, slowing down or crashing many machines.
- Nimda – This particular type of worm targeted web servers and computers running Microsoft Windows operating systems, spreading through multiple infection vectors in 2001.
- ILOVEYOU – A highly destructive worm that spread via email, disguised as a love confession and caused widespread damage in 2000 by overwriting files.
- SQL Slammer – A fast-spreading computer worm that exploited a vulnerability in Microsoft SQL Server, causing network congestion and disrupting Internet services in 2003.
- Stuxnet – A sophisticated worm designed to target and sabotage industrial control systems, particularly Iran’s nuclear program, by exploiting zero-day vulnerabilities in 2010.
- CryptoLocker – This ransomware Trojan, which infected hundreds of thousands of computers in 2013, encrypted victims’ files and demanded a ransom for their decryption.
- Conficker – Emerging in 2008, this worm exploited vulnerabilities in Windows operating systems, creating a massive botnet and causing widespread infection.
- Tinba – First discovered in 2012, this banking Trojan primarily targeted financial institutions, aiming to steal login credentials and banking information.
- Welchia – A worm that aimed to remove the Blaster worm from infected systems and patch the exploited vulnerability but caused unintended network congestion in 2003.
- Shlayer – A macOS-specific Trojan that primarily spreads through fake software updates and downloads, delivering adware and potentially unwanted programs since 2018.
Removing a computer virus can be a challenging task, but there are several steps you can take to get rid of it. Common steps to remove a computer virus include:
- Download and install antivirus software: Assuming you don’t already have antivirus software installed, download and install a real-time and on-demand solution, if possible. A real-time malware scanner scans for viruses in the background while you use the computer. You must start the on-demand scanner whenever you want to scan your device.
- Disconnect from the internet: Some computer viruses use the internet connection to spread, so it’s best to disconnect from the internet when removing a virus from your PC to prevent further damage.
- Delete any temporary files: Depending on the type of virus, deleting temporary files can also delete the virus, as some viruses are designed to initiate when your computer boots up.
- Reboot your computer into safe mode: To help mitigate damages to your computer while you remove a virus, reboot your device in ‘Safe Mode.’ This will inhibit the virus from running and allow you to remove it more effectively.
- Run a virus scan: Run a full scan using your antivirus software, opting for the most thorough or complete scanning option available. If possible, cover all your hard drive letters during the scan.
- Delete or quarantine the virus: Once the virus is detected, your antivirus software will give you the option to delete or quarantine the virus. Quarantining the virus will isolate it from the rest of your computer to prevent it from causing further damage.
- Reboot your computer: Assuming you’ve effectively removed the virus, your computer can be rebooted. Simply turn on the device as you would do so normally without initiating the “Safe Mode” option.
- Update your browser and operating system: To complete the virus removal process, update your operating system and web browser to the latest version possible. Browser and OS Updates often contain fixes for particular vulnerabilities and exploits.
Given the general nature of this process, the outcome may vary from virus to virus and device to device. If you are unsure if you’ve effectively removed a virus from your computer, contact an IT or computer professional for assistance.
Computer viruses can damage your PC, send sensitive data to attackers, and cause downtime until the system is repaired. You can avoid becoming the next computer virus victim by following a few best practices:
- Install antivirus software: Antivirus should run on any device connected to the network. It’s your first defense against viruses. Antivirus software stops malware executables from running on your local device.
- Don’t open executable email attachments: Many malware attacks including ransomware start with a malicious email attachment . Executable attachments should never be opened, and users should avoid running macros programmed into files such as Microsoft Word or Excel.
- Keep your operating system updated: Developers for all major operating systems release patches to remediate common bugs and security vulnerabilities. Always keep your operating system updated and stop using end-of-life versions (e.g., Windows 7 or Windows XP).
- Avoid questionable websites: Older browsers are vulnerable to exploits used when just browsing a website. You should always keep your browser updated with the latest patches and avoid these sites to prevent drive-by downloads or redirecting you to sites that host malware.
- Don’t use pirated software: Free pirated software might be tempting, but it’s often packaged with malware. Download vendor software only from the official source and avoid using software pirated and shared software.
- Use strong passwords: Make sure your passwords are highly secure and difficult to guess. Avoid using the same password across multiple accounts and change them regularly to mitigate vulnerabilities and prevent hackers from stealing them.
- Remain vigilant: Always be cautious when downloading files or software from the internet or opening suspicious email attachments. Turn off file sharing and never share access to your computer with someone you don’t know. Also, avoid keeping sensitive or private information stored on your computer
Related Resources
The definitive email cybersecurity strategy guide, ransomware and phishing attacks: why anti-virus software can't save you, proofpoint email isolation, 68% of tested antivirus apps put android users at risk.
Subscribe to the Proofpoint Blog
Ready to Give Proofpoint a Try?
Start with a free Proofpoint trial.
- Security Tips
- Social Media
- Privacy Tips
- Performance Tips
What Is a Computer Virus?
One of the oldest types of computer threats, viruses are nasty bits of malware that hijack your computer’s resources to replicate, spread, and cause all sorts of chaos. Keep reading to learn how viruses work and how you can protect your computer from viruses with common-sense tips and a dedicated cybersecurity tool.
Get it for Mac , PC , Android
Get it for Android , iOS , Mac
Get it for iOS , Android , PC
Get it for PC , Mac , iOS
Computer viruses are just like that. If you’re unlucky enough to catch one (but don’t beat yourself too much if you do, because they are incredibly common), expect havoc to be wrecked on your hard disk — slower PC performance , damaged or destroyed files, and everything in between.

A computer virus definition, Wikipedia-style
Looking for an essay-friendly definition? Here it goes:
A computer virus is a program or piece of code designed to damage your computer by corrupting system files, wasting resources, destroying data or otherwise being a nuisance.
Viruses are unique from other forms of malware in that they are self-replicating — capable of copying themselves across files or other computers without a user's consent.
Basically, they are really contagious.
Virus, malware, Trojan... what's the difference?
Not every piece of software that attacks your PC is a virus. Computer viruses are just one kind of malware (mal-icious soft- ware ). Here are some of the other, most common kinds:
Trojans : like the ancient wooden horse full of attackers it takes its name from, this malware pretends to be harmless legitimate software, or comes embedded in it, in order to trick the user and open up the gates for other malware to infect a PC.
Spyware : with examples such as keyloggers , this kind of malware is designed to spy on users, save their passwords, credit card details, other personal data and online behavior patterns, and send them off to whoever programmed it.
Worms : this malware type targets entire networks of devices, hopping from PC to PC.
Ransomware : this malware variety hijacks files (and sometimes an entire hard drive), encrypts them, and demands money from its victim in exchange for a decryption key (which may or may not work, but it probably won’t).
Adware : this exceedingly irritating kind of malware floods victims with unwanted ads, and opens up vulnerable security spots for other malware to wiggle its way in.
To recap, viruses are just one of several kinds of malware out there. Strictly speaking, Trojans, ransomware , etc, are not computer viruses, though many people use the shorthand “virus” to refer to malware in a general sense. Altough some devices like phones and iPads are not likely to get a virus , they are not immune to other threats.
Why do people make viruses, and what do they do?
Unlike the bio variety, computer viruses don’t just “happen”. They are manufactured, often with great care, intentionally targeting computers, systems and networks.
But what are these viruses used for?
Well, “fun”. Trolling by software, computer code graffiti… The earliest computer viruses were essentially programmers playing around, like the (maybe, probably) first one, known as the Creeper virus back in 1971, which displayed the message “I’m the creeper, catch me if you can!”.
Not quite Sylvia Plath

Or the Stoned virus , which randomly displayed the words “Your computer is stoned. Legalize marihuana!” on your screen (and stayed in stoner character throughout by doing absolutely nothing else).
Or a personal favorite: the virus that pretends to be a message from a well-known software company, offering you a free cup holder if you download and install it, at which point it opens your PC’s CD tray (remember CD trays?).
Sadly, not all viruses are so cuddly. Take it from Batman’s butler: some people just want to watch the world burn — and computer viruses are a very effective way to spread chaos far and wide.
Like the ILOVEYOU virus , which destroyed the files of more than 50 million internet users worldwide, rendered PCs unbootable, copied people’s passwords and sent them to its creators, and caused up to US$9 billion in damages in the year 2000.
Even that amount pales in comparison to the US$37 billion in damages caused by the Sobig.F virus , which stopped computer traffic in Washington DC and grounded Air Canada for a while.
And then there’s the Mydoom virus , which caused such cyber bloating that it’s believed to have slowed worldwide internet traffic by 10% the day of its release.
Yes, there is a tiny, tiny subset of “good” computer viruses — such as the Cruncher virus, which compresses every file that it infects and theoretically tries to help by saving precious hard disk space.
For example, there’s a virus out there labelled Linux. Wifatch which appears to do nothing other than keeping other viruses out of your router . Linux.Wifatch is itself a virus — it infects a device without its user’s consent and coordinates its actions through a peer-to-peer network — but instead of hurting you, it acts as a sort of security guard.
(But still, there are far better ways to secure your router — and even the creators of Linux.Wifatch tell you not to trust it).
Other “well-intentioned” viruses want to act like a vaccine in that they force people, corporations and governments to strengthen their safety measures and therefore become able to repel genuine threats.
Some virus creators argue they make the world safer by pointing out security gaps and flaws that can be exploited by other viruses with truly malicious intentions.
“What could possibly go wrong?”, asked the first ten minutes of every pandemic disaster movie ever made. The truth is that viruses quickly overwhelm the defenses they’re supposed to put to the test — take the Code Red virus , which in true disaster film fashion attacked the White House (OK the White House’s web server but still OMG) and caused 2.6 billion dollars in damage worldwide.
Some vaccine.
How do computer viruses spread?
Here are some common ways in which you can get infected with a computer virus:
Email viruses
Email is one of the favorite means of transportation for computer viruses everywhere. You can get computer viruses through email by:
Opening an attachment . Often named as something harmless (such as “ Your flight itinerary ”), an executable program file (.com, .exe, .zip, .dll, .pif, .vbs, .js, .scr) or macro file type (.doc, .dot, .xls, .xlt, xlsm, .xsltm…).
Opening an email with an infected body. In these days of rich graphics and colors and bells and whistles, some viruses are being transported in the HTML body of the email itself. Many email services disable HTML by default until you confirm you trust the sender.
Instant messaging viruses
Instant messaging (IM) is another means for viruses to spread. Skype, Facebook Messenger, Windows Live Messenger and other IM services are inadvertently used to spread viruses to your contacts with infected links sent through chat messages.
These instant messaging and social media viruses spread wide and fast because it’s far easier to get people to click on a link when it’s delivered in a message coming from someone they trust, as opposed to a an email from a stranger.
File sharing viruses
Peer-to-peer file sharing services like Dropbox, SharePoint or ShareFile can be used to propagate viruses too. These services sync files and folders to any computer linked to a specific account, so when someone (inadvertently or otherwise) uploads a virus-infected file to a file-sharing account, that virus gets downloaded to everyone else with access to that shared folder.
Some file sharing services, such as Google Drive , scan uploaded files for viruses (although it only scans files smaller than 25MB, giving virus spreaders an easy out — they just have to make sure their virus-infected files are larger than that).
But most other services do not scan for viruses at all, so it’s your responsibility to make sure that you’re protected against any potential threats contained in the file they’re downloading.
Software download viruses
Fake antivirus infections are one of the most common types of virus-loaded software downloads. Scammers and cyber criminals use aggressive pop-ups and ads to scare users into believing that a non-existent virus has been detected in their PC, and compels them to download their “antivirus” software in order to clear the threat.
Instead of ridding the computer of viruses, this fake antivirus proceeds to infect the PC with malware, often with devastating consequences for the victim’s files, hard drive, and personal information.
Unpatched vulnerable software
Last but not least, one of the most common (yet most often overlooked) means for viruses to spread is unpatched software.
Unpatched software refers to software and apps which have not been updated with the latest security updates from the developer, in order to plug up security holes in the software itself.
Unpatched software is a major cybersecurity headache for businesses and organizations, but with criminals exploiting vulnerabilities in outdated versions of such popular programs as Adobe Reader, Java, Microsoft Windows or Microsoft Office , us civilians are very much at risk of infection too.
Types of computer virus
Here’s a list of different types of computer viruses currently out there:
Boot Sector Virus
The boot sector is the part of your PC’s hard drive that loads your computer’s operating system — such as Microsoft Windows. A boot sector virus infects the master boot record (MBR), so the virus loads onto the computer memory during startup.
Boot sector viruses used to be propagated mainly via pluggable devices, like USB keys, floppy disks and CD-ROMS. As technology moves on, boot sector viruses have become much rarer, and these days they mostly live on as email attachments.
Examples of boot sector viruses:
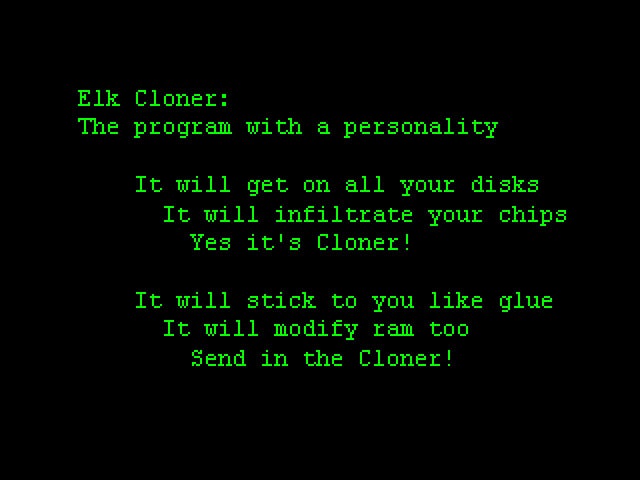
Elk Cloner: this early 1980s virus was attached to a game. At the 50th time the game was started, the virus displayed a poem on-screen.
Stoned: the initial variety displayed on-screen messages in favor of the legalization of marihuana. Its signature (though not the virus itself) crept up into the bitcoin blockchain in 2014.
Parity Boot: another “vintage” virus, this one was the most prevalent virus in Germany up to 1996.
Brain: considered to be the first computer virus for MS-DOS, it was created by the Pakistani Alvi brothers as an attempt to protect their medical software from copyright infringement — an attempt that quickly got out of hand, much to their chagrin.
Michelangelo: every year on March 6 (the birthday of artist Michelangelo), this virus would come alive and overwrite the first 100 sectors of a hard drive with nulls, making it impossible for everyday users to retrieve their files.
Direct Action Virus
These viruses are designed to “pass through” your computer: they get in, generally spread around files of a specific type (COM or EXE files, generally), and when they are done, they delete themselves. They are the most common type of virus out there and the easiest to create — which also makes them the simplest to get rid of.
Examples of direct action viruses:
Win64.Rugrat: also known as the Rugrat virus, this early example of direct action virus could would infect all 64-bit executables it could find in the directory and subdirectories in which it was launched.
Vienna virus: the Vienna virus has the distinction of being the first virus to be destroyed by an antivirus. It searches for .com files and destroys some of them while attempting to infect them.
Resident Virus
Unlike the direct action viruses we mentioned before, memory resident viruses actually set up camp in your computer’s primary memory (RAM). This is bad news, because they can keep working even after you’ve rid yourself of the original infector. Some act fast, some do their damage slowly — and are therefore harder to detect.
Examples of memory resident viruses:
Jerusalem virus (a.k.a. Friday 13th virus): after finding its way into your RAM and hiding inside it, this virus would delete programs from your computer on Friday 13, or increase the size of infected programs until they were too big to run.
Onehalf virus: sometimes known as the Freelove virus, or the Slovak Bomber, this virus slowly encrypts its way through your hard disk. Once it’s done with half (and on the 4th, 8th, 10th, 14th, 18th, 20th, 24th, 28th and 30th day of any month), it displays the message “Dis is one half. Press any key to continue…”
Magistr virus: this very destructive virus emails itself to your contact list, deletes every other file, wrecks your CMOS and BIOS — and leaves you insulting messages to boot.
Multipartite Virus
These ultra-versatile viruses double their spreading power by targeting both your files and your boot space. That way, even after you’ve succeeded in removing all the infected files in your computer, the virus still lingers hidden in the boot sector, ready to strike again — and if you clean the boot sector, the virus will re-infect it by jumping from one of the infected files.
Examples of multipartite viruses:
Junkie virus: this multipartite virus was transmitted in a file called HV-PSPTC.ZIP., supposedly a Pacific Strike computer game. Which it wasn’t.
Tequila virus: this one avoids files which contain the letters “v” and “sc” in their name, and likes to display the message “BEER and TEQUILA forever!”

- Shhhh, don't argue with the virus
Invader virus: this one starts off nicely by playing a Mozart tune, but the moment you hit CTRL+ALT+DEL to reboot, it overwrites the first line of your hard disk with a copy of the virus.
Polymorphic Virus
The mutants of the computer virus world, these viruses shape-shift in order to avoid detection, while holding onto their basic threat capabilities. After infecting your files, these viruses replicate themselves in a slightly different way — which makes them very difficult to fully detect and remove.
Examples of polymorphic viruses:
Satanbug virus: despite its let’s face it quite badass name, this polymorphic virus doesn’t intentionally damage your files — but with its up to nine levels of encryption, virus scanners have a hard time removing it from your PC.
VirLock virus: part ransomware, part polymorphic virus, the Win32/VirLock virus encrypts your files and asks you for ransom — but it also changes shape every time it spreads.
Macro Virus
Macro viruses are written in macro language, with the intention of embedding them within software that allows macro mini-programs such as Microsoft Word. That means your PC can be infected by Word Document viruses.
Examples of macro viruses:
Melissa: distributed through email attachments, once this virus infects your PC it makes its way to your Microsoft Outlook mail client and mails itself to the first 50 contacts in your address book, potentially slowing down or even completely disabling servers in a chain reaction of suck.
How do I protect myself against viruses?
By now we have established you definitely don’t want any of these viruses anywhere near your files, your hard drive or your network. Now, let’s look at how you can avoid computer viruses in the first place.
Use antivirus protection
You have to, have to, have to have some form of antivirus software installed in your PC and your smartphone.
An antivirus is your first line of defense against viruses and a whole bunch of other malware that you seriously don’t want to have to deal with. If you think viruses are bad (and they are), there’s stuff out there that’s even worse.
No excuses. Don’t want to fork out money? There are a few exceptionally good free antivirus software choices out there (ahem). Worried the software will slow down your PC? Ours is so light, you won’t even notice it’s there.
If you’re looking for something extra, premium antivirus programs can offer all kinds of added security features - like our Ransomware Protection shield, which stops anyone from hijacking your files and extorting money from you. For instance, we help you find your phone if you lose it, which is pretty neat.
But hey, you don’t have to get our antivirus (even though it’s free and awesome). Just get some antivirus.*
*although (AND THIS IS THE LAST THING WE’LL SAY ABOUT THIS WE PROMISE) you really shouldn’t get just any free antivirus you find laying around out there, because some of them are actually malware carriers in disguise, and some others are just really blah. So for your own good, always go with an antivirus from a cyber security company whose reputation is at least as good as ours.
Use that pretty head of yours
Apart from letting your antivirus detect and remove viruses, you’ll be doing yourself a huge favor by using proper cyber hygiene in the first place and following some basic internet safety tips:
Don’t just click on any link your friends send you on social media — especially if the message is just a link with no context, or if the words in the message don’t quite sound like them. People’s Facebook accounts get hacked and used to spread out viruses and malware. When in doubt, message your friend directly and ask if they really meant to send you that link. Often, the answer will be “What!? No!”
Don’t open any email attachment unless you 100% know what it is. Cyber criminals often rely on your natural curiosity to spread viruses - they tell you you’ve won something, but you haven’t entered any contests; or they send you a “flight itinerary”, but you aren’t planning on going anywhere. So you open the attachment to see what it’s all about, and bam, you’re infected. So, don’t.
Don’t fall for “Your PC is infected!” hysteric messages and pop-ups that aren’t coming directly from your antivirus. There is a very good chance they’re trying to lure you into downloading a fake antivirus and take your money, infect you computer with malware, or both. When our antivirus catches something, we let you know with a satisfying little message, and that’s it. We don’t ask you to download anything else, or pay any money.
Don’t enable macros in Microsoft Office . A few years ago we would have recommend you to disable macros, but Microsoft already does that by default. Which means cyber criminals try to trick you into enabling them with all sorts of dark mind tricks and fake warnings when you receive an infected email. Don’t fall for them.
But seriously. Antivirus. Now.
How do I remove a virus from my computer?
Stopping a virus from getting into your PC is a lot easier than deleting a virus that’s already in your computer, but if you suspect your PC is already infected with a virus, do not fret. We’ve got you covered.
Is your computer infected?
If your computer has become very slow all of a sudden for no particular reason; if you’re being flooded with pop-up messages out of the blue; if programs and apps start by themselves, and you can hear the hum-hum of your hard drive constantly working in the background…
… it may be.
Here’s how you delete a virus
We have a step-by-step guide that tells you how to get rid of computer viruses the safe and easy way. Give it a read. Or, if your phone has been acting oddly lately, check out our detailed guide to learn how to tell if your phone has a virus or other form of nasty malware — and how to get rid of it.
Get Free Virus Protection
Install free AVG AntiVirus for Android to block viruses and prevent threats. Enjoy 24/7 malware protection.
Get Free Threat Protection
Install free AVG Mobile Security for iOS to prevent security threats. Enjoy 24/7 protection for your iPhone or iPad.
Download AVG AntiVirus FREE for PC to block viruses and prevent threats. Enjoy 24/7 malware protection.
Download AVG AntiVirus FREE for Mac to block viruses and prevent threats. Enjoy 24/7 malware protection.
More helpful tips...
The latest security articles.
- What Is Spyware?
- What Is Adware and How to Get Rid of It?
- What Is a Smurf Attack and How to Prevent It
- What’s the Difference Between Malware and Viruses
- What Is Malware? The Ultimate Guide to Malware
- Microsoft Defender vs. Full-Scale Antivirus
- What Is Scareware? Telltale Signs & How to Remove It
- What Is a Logic Bomb Virus and How to Prevent It
- How to Detect and Remove Spyware from Your iPhone
- How to Remove Spyware from a Mac
- How to Remove Spyware From Android
- What Is Malvertising and How to Prevent It
- How to Scan and Remove Malware From Your Router
- What is a Trojan Horse? Is it Malware or Virus?
- How to Check if an Android App Is Safe to Install
- The Ultimate Guide to Mac Security
- Santa: The Greatest Malware of all Time
- Safest and Most Dangerous US States for PCs and Laptops
- Analysis of Banking Trojan Vawtrak
- iPhone Calendar Virus: What Is It and How Do You Get Rid of It?
- How to Get Rid of a Virus & Other Malware on Your Computer
- How to Find and Clean Viruses on Android Phones or iPhones
- Fake Virus Warnings: How to Spot and Avoid Them
- Can iPads Get Viruses? What You Need to Know
- What Is a Macro Virus and How Do I Remove it?
- The Best Free Antivirus Software for 2024
- Can Macs Get Viruses?
- Worm vs. Virus: What's the Difference?
- What Is a Miner Virus and How Can You Remove It?
- A Brief History of Computer Viruses
- Cobalt Strike Ransomware: What Is It and How to Remove It
- The Ultimate Guide to Ransomware
- The Complete Guide to Mac Ransomware and How to Prevent it
- WannaCry Ransomware: What You Need to Know
- What All Android Users Need to Know About Ransomware
- 2017 Petya Ransomware Outbreak — Your Quick Safety Guide
- The Cost of Ransomware
- EternalBlue Exploit: What Is It and Is It Still a Threat?
- How to Tell If Your Phone Is Tapped: 10 Warning Signs
- What Is a Sniffer and How Can You Prevent Sniffing?
- Reporting Identity Theft — What to Do If Your Identity Is Stolen
- Sextortion and Blackmail — What You Need to Know
- Keyloggers: What They Are, Where They Come From, and How to Remove Them
- What Is SQL Injection?
- What Is a Browser Hijacker and How to Remove One
- Zero-Day Attacks: What You Need to Know
- What Is an Exploit in Computer Security?
- How Secure Is My Phone?
- Identity Theft: What It Is & How It Works
- Everything You Need to Know About Rootkits and How to Protect Yourself
- What Is Pharming and How to Protect Against Attacks
- The NSA is Begging You to Update Windows — Here’s Why
- Your Large-Scale Cyberattack Survival Guide
- Man-in-the-Middle Attacks: What They Are and How to Prevent Them
- The Ultimate Guide to Denial of Service (DoS) Attacks
- What is a Botnet and How Can You Protect Your Computer?
- Megabugs! A Quick 'n Easy Guide to Meltdown and Spectre
- 7 Essential iPhone Security Tips
- What is DNS Hijacking?
- Analyzing an Android WebView Exploit
- Threat Report Reveals Pre-teen Children Developing Malicious Code
- How to Block Spam Calls on Your iPhone, Android, or Landline
- What Is a Honeypot? Cybersecurity Traps Explained
- What to Do If You Lose Your Phone With Google Authenticator on It
- How To Open, Create, and Convert RAR Files
- What Is a Security Breach and How to Protect Against It
- What Is Venmo? Is It Safe and How Does It Work?
- What Is Rooting on Android?
- Email Spam Guide: How to Stop Getting Spam and Other Junk Email
- Is PayPal Safe and Secure? 10 Tips for Buyers and Sellers
- What Is a CVV Number and How to Keep It Safe
- What Is Blockchain & How Does It Work?
- What to Do If Your Phone Is Lost or Stolen
- Google Dorks: What Are They and How Are Google Hacks Used?
- What Is a Jailbroken iPhone?
- What Is UPnP (Universal Plug and Play) and Is It Safe?
- How to Delete iPhone Calendar Spam
- How to Browse Safely on Public Wi-Fi
- Best Security Apps for Android Phones
- How to Choose a Secure Cryptocurrency Wallet
- What Is the Best Cryptocurrency Exchange?
- How Safe Is Bitcoin, Really?
- The Best iPhone Security Apps
- 5 Ways to Enhance Your Cybersecurity
- The Ultimate Guide to Keeping Your Email Secure
- What Is a Digital Identity and How Can You Protect Yours?
- 5 Tips to Make Working From Home Work for You
- How to Avoid Coronavirus Malware & Misinformation
- The Dirty Truth About USBs
- 5 Common Security & Privacy Misconceptions Busted
- 20:20 Vision — 5 Threats to Watch Out for This
- 5 Feel-Good Charities for the Digital Age
- Cybersecurity Basics
- 5 Cybersecurity To-Dos Before You Travel
- Malware Is Still Spying on You Even When Your Mobile Is Off
- Why Is My Ping so High? Helpful Tips for Reducing Lag
- What Is Wi-Fi 6 and Do You Need to Upgrade?
- What Is Streaming and How Does It Work?
- What Is a Router and How Does It Work?
- What Is a Cloud Access Security Broker?
- What Is WPA2 (Wireless Protected Access 2)?
- What Is APKPure and Is It Safe to Use on Android?
- What Is the Dark Web and How to Get on It?
- WEP, WPA, or WPA2 — Which Wi-Fi Security Protocol Is Best?
- Fake Website Check: How to Check If a Website Is Safe or Trying to Scam You
- What Is Fake News and How Can You Spot It?
- Is 2020 the Year We Save the Internet?
- Don’t Get Robbed – 7 Tips for Safer Online Shopping
- 5 Fun Ways to Pointlessly Gamble Your Data
- What Kids Do Online May Surprise You. Internet Safety Tips for You and Your Child
- Who is Tracking You Online?
- Avoid These Mistakes When Using Free Wi-Fi
- What's an Ad Blocker (and Should You Get One)?
- Email Security Checklist – 9+1 Tips for Staying Safe
- Avoid USPS Text Scams: Beware of Fake Tracking Numbers and Messages
- 6 Ways to Identify a Fake Text Message
- Pretexting: Definition, Examples, and How to Prevent It
- Common Venmo Scams: How to Avoid Them and Stay Protected
- How To Stop and Report Spam Texts on iPhone or Android
- How to Recognize and Report an Internet Scammer
- What Is Spoofing and How to Protect Against It
- What Is Caller ID Spoofing and How to Stop It
- How to Identify a Tech Support Scammer
- What Is Social Engineering and Are You at Risk?
- Deepfake Videos: Is There Anything You Can Do to Protect Yourself?
- ATM and Card Fraud: Protect Your Money at Home or Abroad
- How to Make Travel Plans, the Secure Way
- Check Out These Real-Life Airline Scams
- Why Is The FBI Asking You To Restart Your Router? (hint: hackers)
- Scammers Trying to Steal Netflix Passwords, and More
- What Is a Vishing Attack?
- What Is Spear Phishing and How to Avoid It
- What is Smishing and How to Avoid it
- What Is Catfishing & How to Spot Warning Signs
- What is Phishing? The Ultimate Guide to Phishing Emails and Scams
- Is Alexa Always Listening To Us?
- Drones: How Do They Work and Are They Safe?
- Is Your TV Watching You?
- Five Types of Risky Smart Devices to Avoid
- Which Is the Most Secure Android Smart Lock?
- The Birds, Bees, and Bots: Why Parents Are Having The Talk Sooner
- 5 Feel-Good Technology Stories From 2020
- AVG Still Supports Windows 7
- AVG Survey Finds that Parents Don’t Know Enough About Their Children’s Online Habits — Do You?
- AVG Evolved: The Future of Antivirus
- AVG Reveals Invisibility Glasses at Pepcom Barcelona
- Endpoint Security: A Guide for Businesses
- Cybersecurity for Small Businesses: Top Tips and Why It Matters
- What Is a Network Security Key and How Do I Find It?
- Best Small Business Antivirus Solutions for 2024
- Security Suite: What Is It and How Can It Protect Your Business?
iPhone Calendar Virus: What Is It and How Do You Get Rid of It? iPhone Calendar Virus: What Is It and How Do You Get Rid of It?

How to Get Rid of a Virus & Other Malware on Your Computer How to Get Rid of a Virus & Other Malware on Your Computer

How to Find and Clean Viruses on Android Phones or iPhones How to Find and Clean Viruses on Android Phones or iPhones
You Might Also Like...

Fake Virus Warnings: How to Spot and Avoid Them Fake Virus Warnings: How to Spot and Avoid Them
Protect your Android against threats with AVG AntiVirus
Protect your iPhone against threats with AVG Mobile Security
- Media Center
Home Products
- Free Antivirus Download
- Internet Security
- Android Antivirus
- Free Mac Antivirus
- Virus Scanning & Malware Removal
- Installation Files
- Beta Downloads
- Driver Updater
Customer Area
- Register Your License
- Anti-Theft Login
- Home Product Support
- Security & Performance Tips
- Online Research
Partners & Business
- Business Antivirus Software
- Partner Support
- Business Support
Privacy | Report vulnerability | Contact security | License agreements | Modern Slavery Statement | Cookies | Accessibility Statement | Do not sell my info | | All third party trademarks are the property of their respective owners.
We use cookies and similar technologies to recognize your repeat visits and preferences, to measure the effectiveness of campaigns, and improve our websites. For settings and more information about cookies, view our Cookie Policy . By clicking “I accept” on this banner or using our site, you consent to the use of cookies.

14 Different Types of Computer Viruses [As Of 2024]
A computer virus is a harmful program intentionally designed to access a computer without the owner’s permission, often with the goal of stealing or destroying data.
Viruses often infect systems because of programming errors, weaknesses in operating systems, and lax security practices. According to AV-Test, an independent organization that analyzes and rates antivirus and security suite software, about 560,000 new malware pieces are detected every day.
Computer viruses come in various types, classified by their origin, how they spread, where they store themselves, the files they affect, and their destructive capabilities. Each type brings a unique set of characteristics and threats.
Let’s dig deeper to see how different types of viruses actually work.
In 2017, the WannaCry ransomware affected over 200,000 computers across 150 countries by exploiting a vulnerability in Windows systems. This cybercrime is estimated to have caused $4 billion in losses worldwide.
Table of Contents
1. Boot Sector Virus
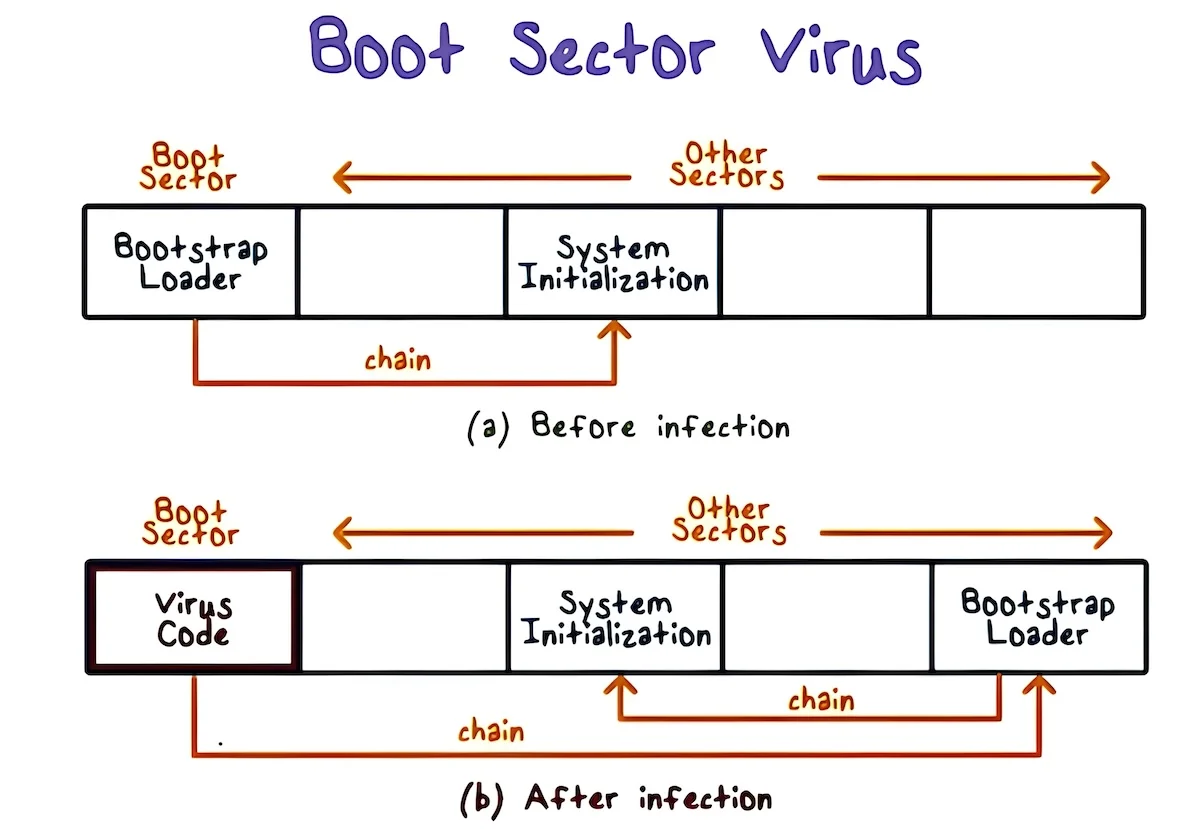
A Boot Sector virus targets a storage device’s master boot record (MBR). Any media, whether it is bootable or not, can trigger this virus. The virus injects its code into the hard disk’s partition table and enters the computer’s main memory upon restarting.
The common issues that may arise after getting infected include booting problems, unstable system performance, and inability to locate hard disks.
Since the boot sector virus can encrypt the boot sector, it may be difficult to remove. In most cases, users are not even aware they have been infected with a virus until they scan the system with an antivirus program.
However, this type of virus has become rare since the decline in floppy disks. Modern operating systems come with an inbuilt boot sector safeguard, which makes it difficult to find the MBR.
2. Direct Action Virus
Direct Action Virus quickly gets into the main memory, infects all programs/files/folders defined in the Autoexec.bat path, and then deletes itself. It can also destroy the data present in a hard drive disk or USB attached to the computer.
They usually spread when the file in which they are contained is executed. As long as you don’t run or open the file, it shouldn’t spread to other parts of your device or your network.
Even though these viruses are often located in the root directory of the hard disk, they can change their location with each execution. While they usually don’t delete system files, they can significantly impact the overall performance of the system.
3. Overwrite Virus
Overwrite viruses are very dangerous. They have affected a wide range of operating systems, including Windows, DOS, Macintosh, and Linux. They simply delete the data (partially or completely) and replace the original code with their own.
They replace file content without changing its size. And once the file is infected, it cannot be restored and you will end up losing all data.
Furthermore, this type of virus can not only make applications un-operational but also encrypt and steal your data on execution.
While they are very effective, attackers do not use overwrite viruses anymore. They tend to focus on tempting users with genuine Trojan horses and distributing malicious code via email.
4. Web Scripting Virus

A web scripting virus breaches web browser security, allowing attackers to inject client-side scripting into the web page. It propagates quite faster than other conventional viruses.
When it breaches the web browser security, it injects malicious code to alter some settings and take over the browser. Typically, it spreads with the help of infected ads that pop up on web pages.
Web scripting viruses mostly target social networking sites. Some are powerful enough to send spam emails and initiate dangerous attacks such as DDoS attacks to make the server unresponsive or ridiculously slow.
They can be further categorized into two groups:
- Persistent web scripting virus : can impersonate a user and cause a lot of damage.
- Non-persistent web scripting virus : attacks the user without getting noticed. It operates in the background and remains forever hidden from the user.
5. Directory Virus
Directory Virus (also known as Cluster virus) infects the file by changing the DOS directory information. It changes DOS in such a way that it points to the virus code rather than pointing to the original program.
More specifically, this virus injects malicious code into a cluster and marks it as allocated in the FAT. It then saves the first cluster and uses it to target other clusters that are associated with the file it wants to infect next.
When you run a program, DOS loads and executes the virus code before running the actual program code. In other words, you unknowingly run the virus program, and the original program is relocated by the virus. This makes it challenging to locate the original file once it’s infected.
6. Polymorphic Virus
Well, that’s the Workbench install on that one completed buggered-up. I’m like a human-computer virus. A polymorphic human-computer virus. I’d like to see Norton AV stop me. I spread from Amiga to Amiga, destroying Workbench installs as I bloody go. #ShootMe pic.twitter.com/VWUsrdwh8O — 3DO, PS1 & Atari Will (@ste_mega) February 25, 2021
Polymorphic viruses encode themselves using different encryption keys each time they infect a program or create a copy of themselves. Because of different encryption keys, it becomes very difficult for the antivirus software to find them.
This type of virus depends on mutation engines to change its decryption routines every time it infects a device. It uses complex mutation engines that generate billions of decryption routines, which makes it even more difficult to detect.
In other words, it is a self-encrypted virus that is designed to avoid detection by scanners.
The first known polymorphic virus (named “1260”) was created by Mark Washburn in 1990. It infects .com files in the current or PATH directories upon execution.
7. Memory Resident Virus
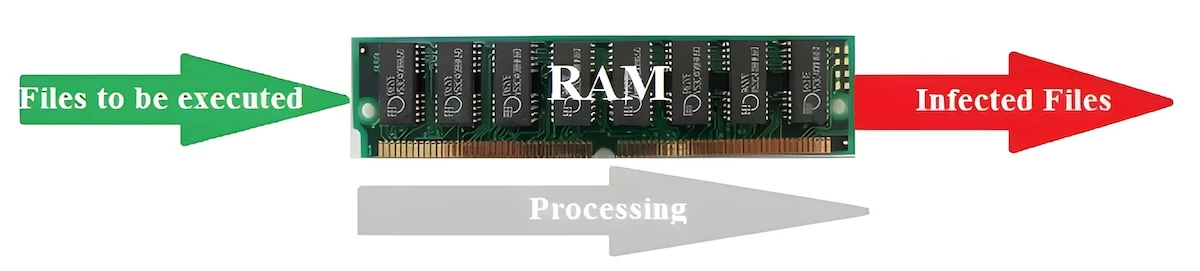
Memory resident virus lives in primary memory (RAM) and gets activated when you switch on the computer. It affects all files currently running on the desktop.
Since the virus loads its replication module into the main memory, it can infect files without being executed. It automatically gets activated whenever the operating system loads or performs specific functions.
There are two types of memory-resident viruses:
- Fast infectors are specifically built to corrupt as many files it can as quickly as possible. They are very easy to notice because of their adverse effects.
- Slow infectors gradually degrade the performance of the computer. They spread more widely because they can go undetected for much longer.
If you are lucky, your antivirus software may have an extension or plugin that can be downloaded on a USB flash drive and run to remove the virus from memory. Otherwise, you may have to reformat the machine and restore whatever you can from the available backup.
8. Macro Virus

These viruses are written in the same macro language used for popular software programs such as Microsoft Excel and Word. They insert malicious code in the macros that are associated with spreadsheets, documents, and other data files, causing the infected program to run as soon as the document is opened.
Macro viruses are designed to corrupt data, insert words or pictures, move text, send files, format hard drives, or deliver even more destructive kinds of malware. They are transmitted through phishing emails. And they mostly target MS Excel, Word, and PowerPoint files.
Since this type of virus centers on applications (not on operating systems), it can infect any computer running any operating system, even those running Linux and macOS.
9. Companion Virus
Companion viruses were more popular during the MS-DOS era. Unlike conventional viruses, they do not modify the existing file. Instead, they create a copy of a file with a different extension (such as .com), which runs in parallel with the actual program.
For example, if there is a file named abc.exe, this virus will create another hidden file named abc.com. And when the system calls a file ‘abc’, the .com (higher priority extension) runs before the .exe extension. It can perform malicious steps such as deleting the original files.
In most cases, companion viruses require human intervention to further infect a machine. After the arrival of Windows XP, which doesn’t use the MS-DOS interface much anymore, there were fewer ways for such viruses to propagate themselves.
However, the virus still works on recent versions of Windows operating systems if a user opens a file unintentionally, especially when the ‘show file extension’ option is deactivated.
10. Multipartite Virus
The Multipartite virus infects and spreads in multiple ways depending on the operating system. It usually stays in memory and infects the hard disk.
Unlike other viruses that either affect the boot sector or program files, the multipartite virus attacks both the boot sector and executable files simultaneously, causing more damage.
Once it gets into the system, it infects all drives by altering applications’ content. You will soon start noticing performance lag and low virtual memory available for user applications.
The first reported multipartite virus was “Ghostball.” It was detected in 1989 when the Internet was still in its early phase. At that time, it wasn’t able to reach many users.
However, things have changed a lot since then. With more than 4.66 billion active internet users worldwide, multipartite viruses pose a serious threat to businesses and consumers.
11. FAT Virus
FAT stands for file allocation table , a section of storage disk used to store information, such as the location of all files, total storage capacity, available space, used space, etc.
A FAT virus alters the index and makes it impossible for the computer to allocate the file. It is powerful enough to force you to format the whole disk.
In other words, the virus doesn’t modify host files. Instead, it forces the operating system to execute malicious code altering particular fields in the FAT file system. This prevents your computer from accessing specific sections on the hard drive where important files are located.
As the virus spreads its infection, several files or even entire directories can be overwritten and permanently lost.
Other Malware That Are Not Viruses But Are Equally Dangerous
12. trojan horse.
Trojan Horse (or Trojan) is a non-replicating type of malware that looks legitimate. Users are typically tricked into loading and executing it on their system. It can destroy/modify all the files, modify the registry, or crash the computer. In fact, it can give hackers remote access to your PC.
Generally, trojans are usually spread through different forms of social engineering. For example, users are tricked into clicking on fake advertisements or opening email attachments disguised to appear genuine.
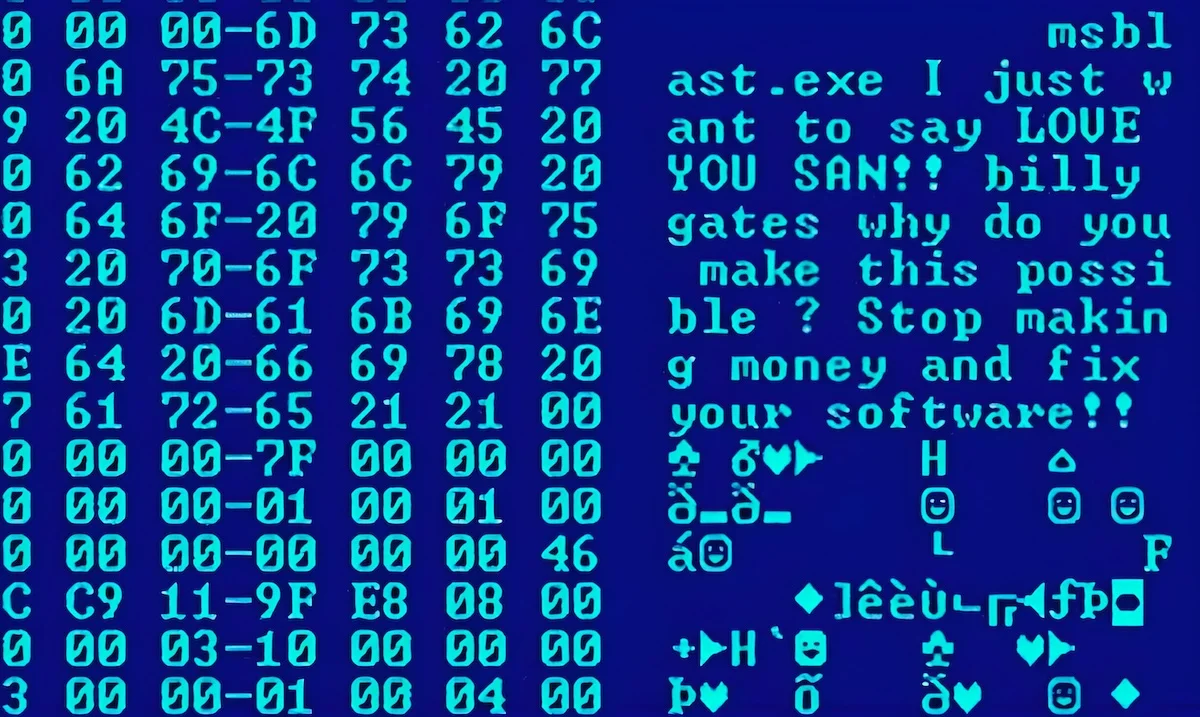
A worm is a standalone malware program that replicates itself in order to spread to other computers. It relies on networks (mostly emails) and security holes to travel from one system to another. Unlike viruses, it overloads the network by replicating or sending too much data (overusing bandwidth), forcing the hosts to shut down the server.
A worm is capable of replicating itself without any human interaction. It doesn’t even need to attach an application to cause damage.
Most worms are designed to modify content, delete files, deplete system resources, or inject additional malicious code onto a computer. They can also steal data and install a backdoor, making it easy for attackers to gain control over a machine and its system settings.
14. Logic Bombs
Logic bombs are not a virus but inherently malicious like worms and viruses. It is a piece of code intentionally inserted (hidden) into a software program. The code is executed when certain criteria are met.
For example, a cracker can insert a Keylogger code inside any web browser extension. The code gets activated every time you visit a login page. It then captures all your keystrokes to steal your username and password.
Logic bombs can be inserted into existing software or into other forms of malware, such as worms, viruses, or Trojan horses. They then lie dormant until the trigger occurs, and can go undetected for years.
Frequently Asked Questions
When was the very first computer virus created.
The first-ever computer virus (named Creeper) was written by Bob Thomas at BBN Technologies in 1971. Creeper was an experimental self-replicating program that had no malicious intent. It only displayed a simple message: “ I’m creeper. Catch me if you can! ”
Who created the first PC virus?
In 1986, Amjad Farooq Alvi and Basit Farooq Alvi wrote a boot sector virus named ‘Brain’ to deter unauthorized copying of the software they had created. ‘Brain’ is considered to be the first computer virus for the IBM PC and compatibles.
Amjad Farooq and Basit Farooq made world’s first computer virus named “Brain Boot Sector Virus” in 1986. It was made for MS-DOS operating systems. The virus used to infect the boot sector of storage media formatted with the DOS File Allocation Table (FAT) file system. pic.twitter.com/MnOaJoDEDJ — Rafay (@xgboostin) January 26, 2021
The first virus to specifically target Microsoft Windows was WinVir. It was discovered in 1992. The virus didn’t contain any Windows API calls. Instead, it relied on the DOS API .
What is the most expensive cyberattack of all time?
The most destructive malware to date is MyDoom. First sighted in January 2004, it became the fastest-spreading email worm ever. It created network openings that allowed attackers to access infected machines.
In 2004, nearly one-fourth of all emails had been infected by MyDoom. The virus caused over 38 billion in estimated damages.
Emerging cybersecurity trends that can help combat computer viruses
In recent years, we have witnessed several emerging trends and technologies in cybersecurity aimed at combating computer viruses. For example,
- Artificial Intelligence and Machine Learning models are being used to detect previously unseen threats
- Behavioral analytics can detect abnormal patterns that may go unnoticed by traditional signature-based methods
- Endpoint Detection and Response (EDR) solutions provide visibility into activities on individual devices, enabling faster response to potential threats
- Blockchain technology provides a decentralized and tamper-resistant way to store and verify security-related data
- Deception technology adds an extra layer of defense by deploying decoy assets and false data to mislead attackers
Cyber Security Market Size
According to Fortune Bussiness Insights, the global cyber security market size will exceed $424.97 billion by 2030, growing at a CAGR of 13.8%.
This growth is driven by several key factors, including the increasing sophistication of attacks, the widespread adoption of digital technologies, and regulatory compliance requirements for robust cybersecurity solutions.
Read More
Single Point Of Failure | A Simple Overview
15 Worst Computer Viruses of all time | Explained
Varun Kumar
I am a professional technology and business research analyst with more than a decade of experience in the field. My main areas of expertise include software technologies, business strategies, competitive analysis, and staying up-to-date with market trends.
I hold a Master's degree in computer science from GGSIPU University. If you'd like to learn more about my latest projects and insights, please don't hesitate to reach out to me via email at [email protected] .
Related articles

Self-Driving Vehicles Find It Hard To Detect Dark-Skinned Pedestrians
Programmed DNA Nanorobots Can Reduce Tumor
Leave a reply cancel reply.
Hi Varun, Thanks for sharing the valuable information. Get huge information about different types virus from this post.
Glad, you find this helpful 🙂
Thanks for sharing knowledge to us…. Love from Nepal
Thanks a lot was so much more than I expected, it really helped me.
- Preferences

Different Types Of Computer Viruses - PowerPoint PPT Presentation

Different Types Of Computer Viruses
Computer virus is a harmful software program written intentionally to enter a computer without the user's permission or knowledge. there are different types of viruses which can be classified according to their origin, techniques, types of files they infect, where they hide, the kind of damage they cause, the type of operating system, or platform they attack. – powerpoint ppt presentation.
- A computer virus is a self replicating program that cause harm to your computer . A computer virus might delete or change your data. Computer Doctor BG help you to fix your computer problems at affordable rate. http//computerdoctor-bg.com/
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.


What are computer viruses and its types?
Jul 07, 2014
90 likes | 1.15k Views
What are computer viruses and its types? . Computer Viruses are malicious software programs that damage computer program entering into the computer without the permission of the users, and also run against the wishes of the users. . Viruses, worms, Trojans.
Share Presentation
- white hat hackers
- computer virus
- mail attachments
- mail attachment
- malicious world

Presentation Transcript
- Viruses, worms, Trojans Viruses, worms, Trojans, spyware, and bots are all part of a class of software called malware(malicious software) . It is code or software that is specifically designed to damage, disrupt, steal, or in general inflict some other “bad” or illegitimate action on data, hosts, or networks. Damage from malware varies from causing minor irritation (such as browser popup ads), to stealing confidential information or money, destroying data, and compromising and/or entirely disabling systems and networks.
- Two Important Classes of Malware:VIRUSES and WORMS These types of programs are able to self-replicate and can spread copies of themselves, which might even be modified copies VIRUSES: A computer virus is a type of malware that propagates by inserting a copy of itself into and becoming part of another program. It spreads from one computer to another, leaving infections as it travels. Almost all viruses are attached to an executable file, which means the virus may exist on a system but will not be active or able to spread until a user runs or opens the malicious host file or program Viruses spread when the software or document they are attached to is transferred from one computer to another using the network, a disk, file sharing, or infected e-mail attachments.
- Contd… WORMS:Computer worms are similar to viruses in that they replicate functional copies of themselves and can cause the same type of damage. In contrast to viruses, which require the spreading of an infected host file, worms are standalone software and do not require a host program or human help to propagate. TROJANS:A Trojan is another type of malware named after the wooden horse the Greeks used to infiltrate Troy. It is a harmful piece of software that looks legitimate. Users are typically tricked into loading and executing it on their systems. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate. Trojans must spread through user interaction such as opening an e-mail attachment or downloading and running a file from the Internet.
- What to do in this malicious world of viruses? Keep your computer’s OS up to date. You should have Updated Antivirus Software Installed (e.gKespersky, Quick Heal etc). You may also want to consider installing a firewall.
- FIREWALLS A firewall is a system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
- Computing Ethics and Cyber Crime Computer ethics is a set of moral principles that regulate the use of computers. Some of the computing ethics are to not use a computer to harm other people or to steal. It also intends to help in the prevention of cyber crime. Cyber crime is criminal activity done using computers and the internet. It is considered to be one of the fastest growing areas in crime Identity Theft. Stealing money from online bank accounts. Creating and distributing viruses. Internet use by terrorists(National/International security.
- What are crackers and hackers? A cracker (also known as a black hat hacker) is an individual with extensive computer knowledge whose purpose is to breach or bypass internet security or gain access to software without paying royalties. The general view is that, while hackers build things, crackers break things. Cracker is the name given to hackers who break into computers for criminal gain; whereas, hackers can also be internet security experts hired to find vulnerabilities in systems. These hackers are also known as white hat hackers.
- Thanks … Have A Nice Day…
- More by User

Computer viruses as a paradigm for infectious diseases
Computer viruses as a paradigm for infectious diseases T. Wassenaar and M.J. Blaser* Molecular Microbiology and Genomics Consultants Zotzenheim, Germany *School of Medicine, New York University NY Introduction Viral diseases will be compared to computer viruses.
651 views • 27 slides

GCSE ICT. Viruses, Security & Hacking. GCSE ICT - Viruses. Introduction to Viruses – what is a virus? Computer virus definition - Malicious code of computer programming How do they work Designed to install, propagate & cause damage Work on the memory of a system
409 views • 12 slides

Chapter 20: Viruses and Bacteria
Chapter 20: Viruses and Bacteria. pp. 454-461, 470-471. Overview…. What is a virus? The anatomy of a virus. Types of viruses. Diseases caused by viruses. Vaccinations. What is a Virus?. Living or Non-living? Viruses were once thought to be a type of bacteria . Tobacco Mosaic Virus
414 views • 16 slides

Computer Viruses Theory and Experiments
Computer Viruses Theory and Experiments. By Dr. Frederick B. Cohen Presented by Jose Andre Morales. Background. Originally written in 1984 Published in Computers and Security, Vol. 6, pp. 22-35 Appeared in DOD/NBS 7 th Conference on Computer Security
473 views • 19 slides

VIRUSES. Computer Technology Day 21. Computer Virus. Set of program instructions that attaches itself to a file, reproduces itself, and/or spreads to other files It can Corrupt files Destroy data Display irritating messages Corrupt computer systems. Spreading Viruses.
320 views • 16 slides

COMPUTER VIRUSES
COMPUTER VIRUSES. Christopher Motl February 21, 2008. Computers & Viruses. History of Computer Viruses. How Viruses Work. Virus DetectionRemovalAnalysis. Alternative Detection Method. Computer Immune System. Miscellaneous Other Topics. OVERVIEW. COMPUTERS AND VIRUSES.
505 views • 34 slides

Computer Viruses
5. 4. 3. 2. 1. Computer Viruses. Kyle Rojewski Computers 1. Slow computer performance Programs start unexpectedly Random computer freezes and restarts Frequent error messages Files have been deleted or changed Slow startup Frequent computer crashes Unseen files have been added
443 views • 10 slides

Worms. Viruses vs. Worms. Viruses don’t break into your computer – they are invited by you They cannot spread unless you run infected application or click on infected attachment Early viruses spread onto different applications on your computer
1.08k views • 82 slides

Outcomes . Why are computer networks vulnerable? Methods used by hacker to gain unauthorised access Viruses Different type of viruses How do viruses infect computers Methods used by anti-virus software Symptoms of virus infection Steps to take to protect your computer from viruses.
667 views • 47 slides

The Nature of Viruses
The Nature of Viruses. Chapter 27. Structure of Viruses. Types of Viruses. DNA RNA Retroviruses. Main Shapes. Helical Icosahedral. Sizes of Viruses. How Viruses Replicate. 1. Attach to and Enter Host Cell 2. Take over Protein synthesis machinery inside of cell- Lysogenic Cycle
1.47k views • 15 slides

Computer Viruses. Your computer gets terribly sick! . Definitions. Virus A small piece of software that attaches itself to a program on the computer. It can cause serious damage to your computer. Worm
530 views • 6 slides

Viruses . A virus is a small infectious agent that can replicate only inside the living cells of organisms. Most viruses are too small to be seen directly with a microscope . Viruses infect all types of organisms, from animals and plants to bacteria and Achaea .
282 views • 9 slides

Computer Viruses. Introduction. Computer virus have become today’s headline news With the increasing use of the Internet, it has become easier for virus to spread Virus show us loopholes in software Most virus are targeted at the MS Windows OS. Definition.
453 views • 28 slides
Computer Security. Viruses. You will need your mouse in this presentation. What is a Virus??? A Virus is something on your computer that will slow your computer down.
265 views • 13 slides

Bacteria and Viruses
Bacteria and Viruses. Viruses. VIRUSES ARE NOT ALIVE!!! Viruses are made up of genetic material surrounded by a protein coat ( capsid ). I. Viruses. - Viruses are non-living particles. - They have a nucleic acid core and a protein containing capsid. Viruses.
401 views • 13 slides

Viruses. -Segments of RNA or DNA contained In a protein coat. Viruses are not living!!!. 1) Viruses are not made of cells 2) Viruses do not grow 3) Viruses can’t reproduce on their own. 2 Main Shapes of Viruses. 1) Helical Virus - Rodlike
734 views • 35 slides

Computer viruses
Computer viruses. What is a computer virus?. A computer virus is a small software program that spreads from one computer to another computer and that interferes with computer operation.
800 views • 37 slides
Why is your computer sick? …And how you can cure it
Why is your computer sick? …And how you can cure it. CLICK HERE TO FIND OUT. MOST COMMON THINGS THAT WOULD MAKE YOUR COMPUTER SICK. VIRUSES. TROJANS. SPYWARE. Click on any of the categories above to find out. WHAT ARE COMPUTER VIRUSES?. Human-made software programs
605 views • 53 slides

Computer Worms & Viruses
Computer Worms & Viruses. ERICA SANTIAGO ASHLEY GUY DAVID HOLLAND ASHLEY WHITE JESSICA PUETTNER. Viruses. By: Erica Santiago. What is a Virus?.
686 views • 44 slides

Computer Viruses. What You Need to Know to Protect Yourself. Types of Viruses. File infectors Attach themselves to programs. Boot-sector infectors Attach to the “boot sector” of a disk. Macro viruses Attach to documents and spreadsheets. Other Malicious Programs. Trojan Horses
407 views • 13 slides

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Various types of computer virus
Our Various Types Of Computer Virus are explicit and effective. They combine clarity and concise expression.

These PPT Slides are compatible with Google Slides
Compatible With Google Slides

- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
Want Changes to This PPT Slide? Check out our Presentation Design Services
Get Presentation Slides in WideScreen
Get This In WideScreen
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
- Add a user to your subscription for free
You must be logged in to download this presentation.
Do you want to remove this product from your favourites?
PowerPoint presentation slides
Presenting this set of slides with name Various Types Of Computer Virus. The topics discussed in these slides are Boot Sector Virus, Multipartite Virus, File Infector Virus, Macro Virus, Resident Virus, Web Scripting Virus, Browser Hijacker, Direct Action Virus. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

People who downloaded this PowerPoint presentation also viewed the following :
- Diagrams , Business , Planning , Strategy , Management , Business Slides , Flat Designs , Technology and Communication , Software Development
- Multipartite Virus ,
- Macro Virus ,
- Resident Virus ,
- Web Scripting Virus ,
- Browser Hijacker
Various types of computer virus with all 2 slides:
Give your audience a fulfilling experience. They will find our Various Types Of Computer Virus elevating.

Ratings and Reviews

- Government Exam Articles
Computer Virus and its Types
A computer virus is a kind of malicious computer program, which when executed, replicates itself and inserts its own code. When the replication is done, this code infects the other files and program present on your system.
These computer viruses are present in various types and each of them can infect a device in a different manner.
In this article, we shall discuss in detail what is a computer virus and what are its different types. Also, we will read on to know what is an Anti-virus and how it can nullify a virus in our computer devices, along with some sample questions from the competitive exam point of view.
To know more about the Fundamentals of Computer , visit the linked article.
Apart from being aware of what a computer virus is, this topic is even important for candidates preparing for Government exams. Major competitive exams in the country comprise Computer Knowledge as an integral part of the syllabus and questions based on virus and anti-virus can also be expected in these exams.
Thus, to excel in the upcoming Govt exams, aspirants must go through this article in detail and carefully study the different types of viruses.
What is a Computer Virus?
A computer virus is a program which can harm our device and files and infect them for no further use. When a virus program is executed, it replicates itself by modifying other computer programs and instead enters its own coding. This code infects a file or program and if it spreads massively, it may ultimately result in crashing of the device.
Across the world, Computer viruses are a great issue of concern as they can cause billions of dollars’ worth harm to the economy each year.

Since the computer virus only hits the programming of the device, it is not visible. But there are certain indications which can help you analyse that a device is virus-hit. Given below are such signs which may help you identify computer viruses:
- Speed of the System – In case a virus is completely executed into your device, the time taken to open applications may become longer and the entire system processing may start working slowly
- Pop-up Windows – One may start getting too many pop up windows on their screen which may be virus affected and harm the device even more
- Self Execution of Programs – Files or applications may start opening in the background of the system by themselves and you may not even know about them
- Log out from Accounts – In case of a virus attack, the probability of accounts getting hacked increase and password protected sites may also get hacked and you might get logged out from all of them
- Crashing of the Device – In most cases, if the virus spreads in maximum files and programs, there are chances that the entire device may crash and stop working
The first thing which you might notice in case of virus attack is the speed with which your system shall process. And then gradually other changes can also be observed.
Types of Computer Virus
Discussed below are the different types of computer viruses:
- Boot Sector Virus – It is a type of virus that infects the boot sector of floppy disks or the Master Boot Record (MBR) of hard disks. The Boot sector comprises all the files which are required to start the Operating system of the computer. The virus either overwrites the existing program or copies itself to another part of the disk.
- Direct Action Virus – When a virus attaches itself directly to a .exe or .com file and enters the device while its execution is called a Direct Action Virus. If it gets installed in the memory, it keeps itself hidden. It is also known as Non-Resident Virus.
- Resident Virus – A virus which saves itself in the memory of the computer and then infects other files and programs when its originating program is no longer working. This virus can easily infect other files because it is hidden in the memory and is hard to be removed from the system.
- Multipartite Virus – A virus which can attack both, the boot sector and the executable files of an already infected computer is called a multipartite virus. If a multipartite virus attacks your system, you are at risk of cyber threat.
- Overwrite Virus – One of the most harmful viruses, the overwrite virus can completely remove the existing program and replace it with the malicious code by overwriting it. Gradually it can completely replace the host’s programming code with the harmful code.
- Polymorphic Virus – Spread through spam and infected websites, the polymorphic virus are file infectors which are complex and are tough to detect. They create a modified or morphed version of the existing program and infect the system and retain the original code.
- File Infector Virus – As the name suggests, it first infects a single file and then later spreads itself to other executable files and programs. The main source of this virus are games and word processors.
- Spacefiller Virus – It is a rare type of virus which fills in the empty spaces of a file with viruses. It is known as cavity virus. It will neither affect the size of the file nor can be detected easily.
- Macro Virus – A virus written in the same macro language as used in the software program and infects the computer if a word processor file is opened. Mainly the source of such viruses is via emails.
Government exam aspirants can check the links given below for the detailed section-wise syllabus for the other subjects apart from Computer Awareness:
How To Protect Your Computer from Virus?
The most suitable way of making your computer virus-free is by installing an Anti-virus software. Such software help in removing the viruses from the device and can be installed in a computer via two means:
- Online download
- Buying an Anti-virus software and installing it
Further below, we bring to you details as to what anti-virus is and what are its different types along with a few examples.
Moving further, candidates can also refer to the following links to learn more about Computer Knowledge and prepare themselves accordingly:
- Difference Between RAM and ROM
- Difference Between MS Excel and MS Word
- Difference Between IPV4 and IPV 6
- Difference Between Firewall and Antivirus
- Difference Between WWW and Internet
- Difference Between Notepad and WordPad
- Difference Between Virus and Malware
What is an Anti-Virus?
An anti-virus is a software which comprises programs or set of programs which can detect and remove all the harmful and malicious software from your device. This anti-virus software is designed in a manner that they can search through the files in a computer and determine the files which are heavy or mildly infected by a virus.
Given below is a list of few of the major antivirus software which is most commonly used:
- Norton Antivirus
- F-Secure Antivirus
- Kaspersky Antivirus
- AVAST Antivirus
- Comodo Antivirus
- McAfee Antivirus
These are few of the many anti-virus software widely used to remove viruses from a device.
Sample Questions on Computer Virus and Anti-Virus
As discussed above, Computer Awareness is a common topic for major Government exams and questions based on Computer Virus and Antivirus may also be asked in the exam.
Thus, given below are a few sample computer virus questions and answers for the assistance of aspirants.
Q 1. Which of the following is not a type of computer virus?
- Polymorphic virus
- Space filler virus
- Multipartite virus
- Boot sector virus
Answer: (4) Trojan
Q 2. Which of these was the first computer virus?
- Crypto Locker
- Morris Worm
Answer: (1) Creeper
Solution: Creeper was the first-ever computer virus and was an experimental self-replicating virus released in the year 1971.
Q 3. Which of the following is not a source of the virus entering your system?
- All of the above
- None of the above
Answer: (5) All of the above
Q 4. The other name for Non-Resident virus is _________
- Direct Action Virus
- Boot Sector Virus
- Multipartite Virus
- Overwrite Virus
- Polymorphic Virus
Answer: (1) Direct Action Virus
Q 5. Which of the following viruses is also known as “Cavity Virus”?
- Space Filler Virus
Answer: (2) Space Filler Virus
For more questions to ace the upcoming competitive exams, aspirants can visit the articles given below:
- Free Online Government Exam Quiz
- Free Online Mock Test Series with Solutions
- Previous Year Govt Exam Question Papers PDF with Solutions
Also, to get the best Preparation Strategy for Competitive exams , candidates can visit the linked article.
Get the latest exam information and study material at BYJU’S and keep yourself updated.
Frequently Asked Questions on Computer Virus and its Types
Q 1. what is the definition of a computer virus, q 2. what are the main computer viruses.
Ans. The main types of computer virus are as follows:
- Resident Virus
- File Infector Virus
Q 3. What is the Creeper Virus?
Q 4. what are the examples of a computer virus.
Ans. Given below are a few examples of a computer virus:
- CryptoLocker
Q 5. How to secure a computer system from a virus attack?

Leave a Comment Cancel reply
Your Mobile number and Email id will not be published. Required fields are marked *
Request OTP on Voice Call
Post My Comment
Connect with us for Free Preparation
Get access to free crash courses & video lectures for all government exams..
- Share Share
Register with BYJU'S & Download Free PDFs
Register with byju's & watch live videos.

IMAGES
VIDEO
COMMENTS
11. Top 5 Sources of Computer Virus Attack The most potent and vulnerable threat of computer users is virus attacks. Virus attacks hampers important work involved with data and documents. It is imperative for every computer user to be aware about the software and programs that can help to protect the personal computers from attacks.
Computer virus definition. A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself. Like other types of malware, a ...
Like many of the viruses on this list, it's hard to remove and can encrypt the boot sector, which can damage the code. Boot secure viruses originally came about with floppy disks, but have adapted over time through USB drives or emails. Money and NYB are common examples of this kind of virus. 3. Resident Viruses.
A virus which hides its presence from the computer user and anti-virus programs, usually by trapping interrupt services. Transmission Control Protocol/Internet Protocol. The collective name for the standard internet protocols. computer program with (undesirable) effects that are not described in its specification.
Resident viruses. Boot sector viruses. Multipartite viruses. Droppers. Beacon/payload. Packers. Command and control. Virus types defined by what they do to you. If you want a great perspective on ...
A computer virus is a type of malicious software, or malware, that spreads between computers and causes damage to data and software. Computer viruses aim to disrupt systems, cause major operational issues, and result in data loss and leakage. A key thing to know about computer viruses is that they are designed to spread across programs and systems.
A computer virus is an ill-natured software application or authored code that can attach itself to other programs, self-replicate, and spread itself onto other devices. When executed, a virus modifies other computer programs by inserting its code into them. If the virus's replication is successful, the affected device is considered ...
Here's a list of different types of computer viruses currently out there: Boot Sector Virus. The boot sector is the part of your PC's hard drive that loads your computer's operating system — such as Microsoft Windows. A boot sector virus infects the master boot record (MBR), so the virus loads onto the computer memory during startup. ...
Hex dump of the Brain virus, generally regarded as the first computer virus for the IBM Personal Computer (IBM PC) and compatibles. A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus ...
The computer virus definition is a code that has the potential to copy itself and corrupt a system. It is designed to spread from one computer to another and can cause damage. The virus enters a ...
11. FAT Virus. FAT stands for file allocation table, a section of storage disk used to store information, such as the location of all files, total storage capacity, available space, used space, etc. A FAT virus alters the index and makes it impossible for the computer to allocate the file.
GENERAL INFORMATION ABOUT COMPUTER VIRUS Different Malware Types. Malware is a general name for all programs that are harmful; viruses, trojan, worms and all other similar programs. Viruses A computer virus is a program, a block of executable code, which attach itself to, overwrite or otherwise replace another program in order to reproduce ...
Computer virus is a harmful software program written intentionally to enter a computer without the user's permission or knowledge. There are different types of viruses which can be classified according to their origin, techniques, types of files they infect, where they hide, the kind of damage they cause, the type of operating system, or platform they attack.
Computer Viruses are malicious software programs that damage computer program entering into the computer without the permission of the users, and also run against the wishes of the users. Viruses, worms, Trojans Viruses, worms, Trojans, spyware, and bots are all part of a class of software called malware (malicious software) .
Features of these PowerPoint presentation slides: Presenting this set of slides with name Various Types Of Computer Virus. The topics discussed in these slides are Boot Sector Virus, Multipartite Virus, File Infector Virus, Macro Virus, Resident Virus, Web Scripting Virus, Browser Hijacker, Direct Action Virus.
A computer virus is a malicious software program which has the ability to make copies of itself. The computer virus infects the files and programs present on the computer system without the knowledge or permission of the user. It spreads from one computer to another, leaving infections as it travels. Almost all viruses are attached to an ...
Resident Virus - A virus which saves itself in the memory of the computer and then infects other files and programs when its originating program is no longer working. This virus can easily infect other files because it is hidden in the memory and is hard to be removed from the system. Multipartite Virus - A virus which can attack both, the ...