Cybersecurity Guide

From scholar to expert: Cybersecurity PhD options
In this guide
- Industry demand
- 2024 rankings
- Preparation
- Considerations
- School listings
The cybersecurity landscape is not just growing—it’s evolving at a breakneck pace. And what better way to stay ahead of the curve than by pursuing a PhD in cybersecurity?
This advanced degree is no longer confined to the realm of computer science. Today, it branches into diverse fields like law, policy, management, and strategy, reflecting the multifaceted nature of modern cyber threats.
Ad cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site. Featured Cybersecurity Training
If you’re looking to become a thought leader in this dynamic industry, a PhD in cybersecurity offers an unparalleled opportunity to deepen your expertise and broaden your horizons.
This guide is designed to give prospective cybersecurity PhD students a general overview of available cybersecurity PhD programs. It will also outline some of the factors to consider when trying to find the right PhD program fit, such as course requirements and tuition costs.
Industry demand for PhDs in cybersecurity
Like other cutting-edge technology fields, until recently, cybersecurity PhD programs were often training grounds for niche positions and specialized research, often for government agencies (like the CIA, NSA, and FBI), or closely adjacent research organizations or institutions.
Today, however, as the cybersecurity field grows to become more pervasive and consumer-oriented, there are opportunities for cybersecurity PhDs to work at public-facing companies like startups and name-brand financial, software, infrastructure, and digital service firms.
One trend that is emerging in the cybersecurity field is that cybersecurity experts need to be well-versed in a variety of growing threats. If recent headlines about cybersecurity breaches are any indication, there are a number of new attack vectors and opportunities for cybercrime and related issues. Historically, committing cybercrime took resources and a level of sophistication that required specialized training or skill.
But now, because of the pervasiveness of the internet, committing cybercrime is becoming more commonplace. So training in a cybersecurity PhD program allows students to become an experts in one part of a growing and multi-layered field.
In fact, this trend of needing well-trained, but adaptable cybersecurity professionals is reflected by the move by cybersecurity graduate schools to offer specialized master’s degrees , and many companies and professional organizations offer certifications in cybersecurity that focus on particular issues related to cybersecurity technology, cybersecurity law , digital forensics , policy, or related topics.
That said, traditional research-oriented cybersecurity positions continue to be in demand in academia and elsewhere — a trend that will likely continue.
One interesting facet of the cybersecurity field is trying to predict what future cybersecurity threats might look like and then develop tools and systems to protect against those threats.
As new technologies and services are developed and as more of the global population begins using Internet services for everything from healthcare to banking — new ways of protecting those services will be required. Often, it’s up to academic researchers to think ahead and examine various threats and opportunities to insulate against those threats.
Another key trend coming out of academic circles is that cybersecurity students are becoming increasingly multidisciplinary.
As cybersecurity hacks impact more parts of people’s everyday lives, so too do the academic programs that are designed to prepare the next generation of cybersecurity professionals. This emerging trend creates an enormous amount of opportunity for students who have a variety of interests and who are looking to create a non-traditional career path.
The best cybersecurity PhD programs for 2024
Capella university, georgia institute of technology, northeastern university, marymount university, school of technology and innovation, nova southeastern university, college of computing & engineering, purdue university, stevens institute of technology, worcester polytechnic institute, university of illinois at urbana-champaign, mississippi state university, new york institute of technology.
These rankings were compiled from data accessed in November 2023 from the Integrated Post-Secondary Education Data System (IPEDS) and College Navigator (both services National Center for Education Statistics). Tuition data was pulled from individual university websites and is current as of November 2023.
What is required to get a PhD in cybersecurity?
Good news first: Obtaining a PhD in a field related to cybersecurity will likely create tremendous employment opportunities and lead to interesting and dynamic career options.
Bad news: Getting a PhD requires a lot of investment of time and energy, and comes with a big opportunity cost (meaning you have to invest four to five years, or longer, or pursue other opportunities to obtain a doctoral degree.
Here’s a quick breakdown of what is required to get a PhD in cybersecurity. Of course, specific degree requirements will vary by program. One growing trend in the field is that students can now obtain degrees in a variety of formats, including traditional on-campus programs, online degree programs , and hybrid graduate degree programs that combine both on-campus learning with online learning.
Related resources
- Online PhD in cybersecurity – A guide to finding the right program
- Cybersecurity degree programs
- Podcast episodes and expert interviews
Preparing for a cybersecurity doctorate program
Cybersecurity is a relatively new formalized technology field, nonetheless, there are several ways that students or prospective PhD candidates can get involved or explore the field before and during a graduate school program. A few examples of ways to start networking and finding opportunities include:
Join cybersecurity organizations with professional networks
Specialized professional organizations are a good place to find the latest in career advice and guidance. Often they publish newsletters or other kinds of information that provide insights into the emerging trends and issues facing cybersecurity professionals. A couple of examples include:
The Center for Internet Security (CIS) is a non-profit dedicated to training cybersecurity professionals and fostering a sense of collaboration. The organization also publishes information and analysis of the latest cybersecurity threats and issues facing the professional community.
The SANS Institute runs several different kinds of courses for students (including certification programs) as well as ongoing professional cybersecurity education and training for people working in the field. The organization has several options including webinars, online training, and live in-person seminars. Additionally, SANS also publishes newsletters and maintains forums for cybersecurity professionals to interact and share information.
Leverage your social network
Places like LinkedIn and Twitter are good places to start to find news and information about what is happening in the field, who the main leaders and influencers are, and what kinds of jobs and opportunities are available.
Starting a professional network early is also a great opportunity. Often professionals and members of the industry are willing to provide guidance and help to students who are genuinely interested in the field and looking for career opportunities.
Cybersecurity competitions
Cybersecurity competitions are a great way to get hands-on experience working on real cybersecurity problems and issues. As a PhD student or prospective student, cybersecurity competitions that are sponsored by industry groups are a great way to meet other cybersecurity professionals while getting working on projects that will help flesh out a resume or become talking points in later job interviews.
The US Cyber Challenge , for example, is a series of competitions and hackathon-style events hosted by the Department of Homeland Security Science and Technology Directorate and the Center for Internet Security to prepare the next generation of cybersecurity professionals.
Internships
Internships also continue to be a tried and true way to gain professional experience. Internships in technical fields like cybersecurity can also pay well. Like the industry itself, cybersecurity internships are available across a wide range of industries and can range from academic research-oriented to more corporate kinds of work.
Things to consider when choosing a cybersecurity PhD program
There are many considerations to evaluate when considering any kind of graduate degree, but proper planning is essential to be able to obtain a doctoral degree. It’s also important to note that these are just guidelines and that each graduate program will have specific requirements, so be sure to double-check.
What you will need before applying to a cybersecurity PhD program:
- All undergraduate and graduate transcripts
- A statement of intent, which is like a cover letter outlining interest
- Letters of reference
- Application fee
- Online application
- A resume or CV outlining professional and academic accomplishments
What does a cybersecurity PhD program cost?
Obtaining a PhD is a massive investment, both in terms of time and money. Cybersecurity PhD students are weighing the cost of becoming an expert in the field with the payoff of having interesting and potentially lucrative career opportunities on the other side.
Degree requirements are usually satisfied in 60-75 hours, so the cost of a doctoral degree can be well into the six-figure range. Here’s a more specific breakdown:
Tuition rates
The Cybersecurity Guide research team looked at 26 programs that offer a cybersecurity-related PhD degree. Here’s a breakdown of tuition rates (all figures are based on out-of-state tuition).
$17,580 is the most affordable PhD program option and it is available at the Georgia Institute of Technology.
$86,833 is the average cost of a cybersecurity PhD and is based on tuition rates from all 26 schools.
$197,820 is the most expensive cybersecurity PhD program and is available at Indiana University Bloomington.
The good news is that by the time students get to the PhD level there are a lot of funding options — including some graduate programs that are completely funded by the university or academic departments themselves.
Additionally, funding in the form of research grants and other kinds of scholarships is available for students interested in pursuing cybersecurity studies.
One example is the CyberCorps: Scholarships for Service program. Administered by the National Science Foundation, PhD students studying cybersecurity are eligible for a $34,000 a year scholarship, along with a professional stipend of $6,000 to attend conferences in exchange for agreeing to work for a government agency in the cybersecurity space after the PhD program.
Frequently asked questions about cybersecurity PhD programs
Most traditional and online cybersecurity graduate programs require a minimum number of credits that need to be completed to obtain a degree. On average, it takes 71 credits to graduate with a PhD in cybersecurity — far longer (almost double) than traditional master’s degree programs. In addition to coursework, most PhD students also have research and teaching responsibilities that can be simultaneously demanding and great career preparation.
At the core of a cybersecurity doctoral program is a data science doctoral program, you’ll be expected to learn many skills and also how to apply them across domains and disciplines. Core curriculums will vary from program to program, but almost all will have a core foundation of statistics.
All PhD candidates will have to take a series of exams that act as checkpoints during the lengthy PhD process. The actual exam process and timing can vary depending on the university and the program, but the basic idea is that cybersecurity PhD candidates generally have to sit for a qualifying exam, which comes earlier in the program (usually the winter or spring of the second year of study), a preliminary exam, which a candidate takes to show they are ready to start the dissertation or research portion of the PhD program, and a final exam where PhD students present and defend their research and complete their degree requirements.
A cybersecurity PhD dissertation is the capstone of a doctoral program. The dissertation is the name of a formal paper that presents the findings of original research that the PhD candidate conducted during the program under the guidance of faculty advisors. Some example cybersecurity research topics that could potentially be turned into dissertation ideas include: * Policies and best practices around passwords * Ways to defend against the rise of bots * Policies around encryption and privacy * Corporate responsibility for employee security * Internet advertising targeting and privacy * The new frontier of social engineering attacks * Operation security (OpSec) strategy and policy * Network infrastructure and defense * Cybersecurity law and policy * The vulnerabilities of biometrics * The role of ethical hacking * Cybersecurity forensics and enforcement
A complete listing of cybersecurity PhD programs
The following is a list of cybersecurity PhD programs. The listing is intended to work as a high-level index that provides enough basic information to make quick side-by-side comparisons easy.
You should find basic data about what each school requires (such as a GRE score or prior academic work) as well as the number of credits required, estimated costs, and a link to the program.
Arizona State University
- Aim: Equip students with in-depth expertise in cybersecurity.
- Study Modules: Delve into advanced computer science subjects and specific cybersecurity courses.
- Research Component: Students undertake groundbreaking research in the cybersecurity domain.
Carnegie Mellon University
- CNBC Collaboration: A joint effort between Carnegie Mellon and the University of Pittsburgh to train students in understanding the brain's role in cognition.
- Training Program: Students take four main neuroscience courses and participate in seminars and ethics training.
- Course Integration: Whether students have a B.S. or M.S. degree, they can combine the CNBC and ECE Ph.D. courses without extra workload.
Colorado School of Mines
- Research Focus: Cybersecurity: Studying online security and privacy.
- Cost and Financial Aid: Provides details on program costs and available financial support.
- Current Mines Community: Offers specific information for those already affiliated with Mines.
Indiana University Bloomington
- Focus Areas: Options include Animal Informatics, Bioinformatics, Computer Design, and more.
- Information Sessions: The university holds events to guide potential students about admissions and study options.
- Minor Requirement: All Ph.D. students must complete a minor, which can be from within the Luddy School of Informatics or from another approved school at IU Bloomington.
Iowa State University
- Details: The program is open to both domestic and international students.
- Time to Complete: Ph.D.: About 5.2 years
- Goals: Students should gain deep knowledge, follow ethics, share their findings, and do advanced research if they're writing a thesis.
- Learning Goals: Master core areas of Computer Science, achieve in-depth knowledge in a chosen subfield, obtain expertise to perform original research, and demonstrate the ability to communicate technical concepts and research results.
- Duration: Median time to earn the doctorate is 5.8 years.
- Application Information: The program is open to both domestic and international students.
- Program's Aim: The Ph.D. program is tailored to produce scholars proficient in leading research initiatives, undertaking rigorous industrial research, or imparting high-level computer science education.
- Entry Routes: The program welcomes both students holding a B.S. degree for direct admission and those with an M.S. degree.
- Dissertation's Role: It stands as the pivotal component of the Ph.D. journey. Collaboration between the student, their dissertation director, and the guiding committee is essential.
Naval Postgraduate School
- Program Essence: The Computer Science Ph.D. is a top-tier academic program in the U.S.
- Admission Criteria: Open to military officers from the U.S. and abroad, U.S. governmental employees, and staff of foreign governments.
- Curriculum: Designed to deepen knowledge in computing, with a focus on the needs of the U.S. Department of Defense.
- Emphasis on Research: The college showcases its strength in research through sections dedicated to Research Areas, affiliated Institutes & Centers, ongoing Research Projects, and specialized Labs & Groups.
- Holistic Student Growth: The college promotes a comprehensive student experience, spotlighting Clubs & Organizations, campus Facilities, and tech Systems.
- Guidance for Future Students: Provides tailored insights for students considering joining at various academic levels, from Undergraduate to PhD.
- Broad Learning: The program covers many areas, from software and policy to psychology and ethics, reflecting the wide scope of cybersecurity.
- Course Design: Students learn foundational security topics first and then dive into specialized areas, like cyber forensics.
- Successful Alumni: Past students now work in places like NASA, Amazon, and Google.
- Feature: Students can apply to up to three different campuses and/or majors using a single application and fee payment.
- Preparing for a Globalized World: Courses such as Global Supply Chain Management equip students for international careers.
- Tech-Forward Curriculum: Purdue's commitment to advanced technology is evident.
Rochester Institute of Technology
- Cyberinfrastructure Focus: The program dives deep into how hardware, data, and networks work together to create secure and efficient digital tools.
- Broad Applications: The program uses computing to solve problems in fields like science, arts, and business.
- Success Rate: All RIT graduates from this program have found relevant roles, especially in the Internet and Software sectors.
Sam Houston State University
- Program's Objective: The course aims to nurture students to be technically adept and also to take on leadership roles in the digital and cyber forensic domain across various industries.
- Assessments: Students undergo comprehensive tests to evaluate their understanding.
- Research Paper (Dissertation): Once students reach the doctoral candidacy phase, they must produce and defend a significant research paper or dissertation.
- Funding: All Ph.D. students get financial help, so they can start their research right away.
- Teachers: The program has top experts, including those who've made big discoveries in computer science.
- Research Areas: Students can study the latest topics like AI, computer vision, and online security.
The University of Tennessee
- Study Areas: Options include Cybersecurity, Data Analytics, Computer Vision, and more.
- Tests: You'll have to pass a few exams, including one when you start, one before your final project, and then present your final project.
- Courses: Some specific courses are needed, and your main professor will help decide which ones.
- Big Exam: Before moving forward, you'll take a detailed exam about your research topic.
- Final Step: You'll present and defend your research project to experts.
- Overview: This program is for those with a degree in Computer Science or similar fields. It has special focus areas like Cybersecurity and Machine Learning.
University of Arizona
- Study Plan: Students start with learning research basics and then dive into modern tech topics.
- Support for Students: All PhD students get funding that covers their studies, a stipend, and health insurance. Money for travel to conferences is also available.
- After Graduation: Alumni work at top universities and big companies like Google and Microsoft.
University of California-Davis
- About the Program: Students engage in deep research, ending with a dissertation.
- Jobs After Graduation: Roles in companies or academic positions.
- Vibrant Community: Beyond academics, students join a supportive community, enriching their Ph.D. experience.
University of Colorado - Colorado Springs
- Recognition: UCCS is recognized by the National Security Agency (NSA) and the Department of Homeland Security for excellence in Information Assurance Education.
- Course Approval: The NSA has approved UCCS's courses as meeting national security training standards.
- Overview: This program focuses on vital areas like cyber security, physical security, and homeland security.
University of Idaho
- Partnership with NSA and DHS: The university is part of a program to boost cyber defense education.
- Recognition: The University of Idaho is among the institutions recognized as Centers of Academic Excellence in Cyber Defense.
- Objective: To minimize vulnerabilities in the national information infrastructure.
- Overview: This program is meticulously crafted to deliver premier legal education to its students.
- Courses: Encompasses a balanced mix of traditional legal doctrines, theoretical viewpoints, and hands-on practical experiences.
- Aim: The primary objective is to equip students with top-notch legal education.
University of Missouri-Columbia
- Seminars: PhD students should attend 20 seminars. If they were previously Master's students, their past attendance counts.
- Timeline Requirements: Comprehensive Exam must be completed within five years of starting the program.
- Dissertation and Publication: At least one journal paper must be submitted, accepted, or published.
University of North Carolina at Charlotte
- Faculty: The faculty members are renowned for their impactful research contributions on a global scale.
- Curriculum: The curriculum is versatile, catering to individuals aiming for academia as well as those targeting roles in the corporate, commerce, or public sectors.
- Program: A blend of theoretical and hands-on research is emphasized, offering a well-rounded educational experience.
Virginia Tech
- Seminars and Ethics: Students attend special seminars and complete training on scholarly ethics and diversity.
- Guidance: Each student gets a faculty advisor. A group of faculty members, called a committee, also guides them.
- Major Exams: Students go through four main stages: a qualifying process, a preliminary proposal, a research presentation, and a final defense.
- Strong Research: WPI's PhD program is recognized for its excellent research contributions.
- Practical Focus: The program teaches students to tackle real tech challenges.
- Modern Labs: Students use the latest labs like the Human-Robot Interaction Lab.
Dakota State University
- Program Goal: Train students to handle and prevent cyber threats.
- Awards: The university has received top cybersecurity awards.
- What You'll Learn: Research skills, cyber defense techniques, and ethical decision-making.
New Jersey City University, College of Professional Studies
- About: Focuses on best practices in areas like national security, cyber defense, and crisis communication.
- Recognitions: The program has been honored by the National Security Agency since 2009 and was recognized for excellence in intelligence studies.
- Jobs: Graduates are prepared for top roles in sectors like government and education.
- Program Content: The course dives deep into modern cybersecurity topics, from new tech and artificial intelligence to specialized research areas.
- Location Benefits: The university is near many cybersecurity companies and government agencies, giving students unique opportunities.
- For Working People: It's crafted for professionals, allowing them to experience various cybersecurity roles, from tech firms to government.
- Completion Time: Students have up to ten years from starting to finish their dissertation.
- Program: Trains students for roles in academia, government, and business.
- Multidisciplinary Approach: The program combines both technical and managerial aspects of cybersecurity, offering a comprehensive understanding of the field.
The University of Rhode Island
- Research Focus: The Ph.D. program is centered around a big research project in Computer Science.
- Qualifying Exams: Students take exams on core topics, but some might get exemptions if they're already skilled in certain areas.
- Equal Opportunity: The University of Rhode Island is committed to the principles of affirmative action and is an equal opportunity employer.
University of North Texas
- Team Effort: The program is a collaboration between various UNT departments for a well-rounded view of cybersecurity.
- Goals: The course aims to develop critical thinkers who are passionate about the role of information in our lives and can work across different fields.
- Skills Gained: Students will learn about research, teaching methods, decision-making, leadership, and analyzing data.
New York University Tandon School of Engineering
- Scholarships: Many students get scholarships that pay for tuition and give a monthly allowance.
- Research Interest: Research areas include cybersecurity, computer games, web search, graphics, and more.
- Experience: Students can also research in NYU's campuses in Shanghai or Abu Dhabi.
- One Degree for All: Every student gets the same Ph.D., regardless of their specific area of study.
- Research Focus: The program emphasizes deep research and prepares students for advanced roles.
- Major Project: Students work on a big research project, adding new knowledge to the computing world.
- Program: Prepares students for leadership roles in different sectors.
- Opportunities: Qualified students might get opportunities as Research or Teaching Assistants.
- Overview: Focuses on advanced research and modern technologies.
Augusta University
- Goal: The program prepares students for research roles and to make new discoveries in tech.
- Benefits: A Ph.D. opens up leadership opportunities in tech sectors.
- Overview: It focuses on new discoveries in areas like security, artificial intelligence, and virtual reality.
University of Texas at San Antonio
- Financial Support: Full-time students can get funding, which covers tuition and offers roles like teaching assistants.
- Job Prospects: UTSA trains students for jobs that are in high demand, using data from official sources.
- Overview: The program focuses on in-depth research and teaching.
University of Central Florida
- Mix of Subjects: Students can take courses from different areas, giving them a broad view of security topics.
- Many Job Options: Graduates can work in government, big companies, or teach in universities.
- Hands-on Learning: The program offers research, study projects, and internships for real-world experience.

- Academics Admissions Programs Departments Calendars & Timetables Office of Career Services Centre for Continued Education Office of Academic Affairs
- Research Office of SRC Institute Innovation Council
- Relations Press Releases Newsletter MoUs and Collaborations JICA Friendship Program Public Relations Alumni and Corporate Relations International Relations
- About About IITH How to Reach Campus Navigation Sustainability Rankings & Reports Administration
- People Faculty Staff Students Directory
- Donate to IITH
1. Regular PhD
Admissions portal is here.
IITH offers regular PhD programs in the following departments
- Artificial Intelligence
- Biomedical Engineering
- Biotechnology
- Center for Interdisciplinary Programs
- Chemical Engineering
- Civil Engineering
- Climate Change
- Computer Science and Engineering
- Electrical Engineering
- Engineering Science
- Entrepreneurship and Management
- Greenko School of Sustainability
- Heritage Science and Technology
- Liberal Arts
- Materials Science and Metallurgical Engineering
- Mathematics and Computing
- Mechanical and Aerospace Engineering
Basic Eligibility is a Masters degree. If you think you are an exceptionally good candidate, you can apply for a direct PhD after BTech/B.E. with a valid GATE score. IITH typically admits students to the PhD program twice in a year, in the month of Nov and in the month of April. IITH does not make newspaper advertisements regarding admission and the aspirants are requested to follow our website for admission notification. The applications received are screened by the individual departments and the successful applicants will be called for a written test and interview. The financial assistance for the Ph.D. program under MoE (Ministry of Education) and all other funding categories except PMRF and External category across all departments is 5 years.
All the departments at IITH offer PhD program. The eligibility criteria for PhD admission in the engineering departments is a Masters degree. If you think you are an exceptionally good candidate, you can apply for a direct PhD after B.Tech./B.E. with valid GATE score. IITH typically admits students to the PhD program twice a year. IITH do not make newspaper advertisements regarding admission and the aspirants are requested to follow our website for admission notification. Typically the notification comes out in the month of Nov and in the month of April. The applications received are screened by the individual departments and the successful applicants will be called for a written test and interview. The financial assistance for the PhD program under MoE (Ministry of Education) category across all departments is 5 years.
2. Interdisciplinary PhD Program
Seat acceptance fee and refund policy.
See this document for details

For more information, visit https://home.iitd.ac.in/pg-admissions.php
The last date for submission of online application for PG and PhD Programmes for admission for 1st semester 2024-25 extended up to 08 April 2024 (4 p.m.) for national and international candidates.
M.Tech Shortlisting Criteria and Other Information for May 2024 : click here
Latest News
10 power assets, Mumbai, Tamil Nadu ports came under RedEcho cyberattack
Read more..
Microsoft hack: 3,000 UK email servers remain unsecured
Cyber Attacks: India second-most attacked country in Asia Pacific region, says IBM Security
How A Dated Cyber-Attack Brought A Stock Exchange To Its Knees
Sopra Steria hit by new version of Ryuk ransomware
ComputerScience.org is an advertising-supported site. Featured or trusted partner programs and all school search, finder, or match results are for schools that compensate us. This compensation does not influence our school rankings, resource guides, or other editorially-independent information published on this site.
Are you ready to discover your college program?
A doctoral degree in cybersecurity is the highest academic credential in the discipline. Students can earn a Ph.D., which focuses on theory and prepares future educators, or a D.Sc., which focuses on applications of theory for emerging marketplace leaders.
Though almost 50 years old, cybersecurity recently emerged as a major field of employment, adding numerous profitable jobs over a short time window. The Bureau of Labor Statistics (BLS) projects 16,300 information security specialist jobs will open annually between 2020 and 2030. These positions command a median annual salary of $103,590 as of 2020.
Cybersecurity attracts math-oriented creative thinkers. These professionals help protect vulnerable citizens from some of today's most dangerous threats.
Top Doctoral Programs
Explore programs of your interests with the high-quality standards and flexibility you need to take your career to the next level.
Why Get a Cybersecurity Doctoral Degree?
Cybersecurity began in 1971 when a computer scientist named Bob Thomas created the first computer worm and called it "Creeper." Ray Tomlinson, the inventor of email, developed a program he called "Reaper" — the original antivirus program — to delete Creeper.
Modern cybersecurity experts face more complicated challenges. These professionals develop security strategies, create firewalls, simulate cyberattacks, and manage security teams. Information security specialists work across almost all industries, including government, healthcare, finance, and retail.
Cybersecurity experts have to think like black-hat hackers to combat the growing threat of data breaches. This means curious, analytical people who can work efficiently under pressure may find cybersecurity a rewarding field.
Earning a degree in cybersecurity can open entry-level jobs in this lucrative, fast-growing profession. A coding bootcamp can provide another quick and affordable pathway to a fresh career in cybersecurity.
A degree may require more time and money upfront than a bootcamp, but it may also offer more breadth and insight into the discipline for future cybersecurity specialists. A doctorate especially can lead to exciting research opportunities and the chance to shape the sector's future.
Job Security
High salaries, meaningful career, top five cybersecurity doctoral degrees 2022.
There's never been a better time for a career in cybersecurity. Information security analysts enjoy buoyant job prospects and pay well above the national average. A doctorate in cybersecurity provides advanced training for leadership and academic positions. This ranking takes a look at five of the nation's best cybersecurity schools.
- Collapse All
Capitol Technology University
Located in Laurel, Maryland, Capitol Technology University specializes in STEM programs. The institution is one of only two colleges authorized to provide cybersecurity training to NSA security engineers. The school's location gives graduates access to a high concentration of defense contractors and high-tech companies.
D.Sc. in Cybersecurity
Students can earn a D.Sc. in cybersecurity from a nationally recognized cyber defense college. The doctorate requires 54-66 credits that students complete online with low residency requirements. Enrollees explore information assurance research literature and engage in formal research.�
A course focuses on the research design process. Elective courses cover topics such as software assurance assessment and information assurance implementation. Enrollees culminate the cybersecurity doctorate with a dissertation. Capitol Tech operates a training center where students can practice cyber defense techniques and secure internships.�
All students pay the same tuition regardless of residency status. Capitol Tech is a Veterans Administration-approved institution and offers tuition discounts for active duty military personnel.
Applying to Capitol Tech
Admission requires a master's degree in a related field and at least five years of related work experience.
Program at a Glance
- Accreditation : Institutional: Middle States Commission on Higher Education (MSCHE)
- Tuition : $933/credit
- Program Length : N/A
- Delivery Format : 100% online with residency requirements
- Percentage Awarded Loans: 53%
Carnegie Mellon University
Carnegie Mellon University is a renowned research college located in Pittsburgh. The school enrolls about 16,000 students. CMU manages a renowned robotics engineering center and conducts classified research at the software engineering institute.
Ph.D. in Information Systems and Management
Students in the Ph.D. in information systems management study various technical and organizational facets of information systems. They engage in innovative research that addresses challenges in areas such as design and management. Participants study in classrooms with a small cohort of 6-8 peers.�
The cybersecurity Ph.D. requires coursework in social and policy sciences. Students complete quantitative methods coursework in statistics, machine learning, and econometrics. Learners engage in research in an area such as the economics of digitization or information security and privacy.�
Participants use a concentration area component to combine research and courses that support their research agenda. Doctoral students culminate the cybersecurity degree with a dissertation.
Applying to CMU
Admission requires a bachelor's degree in a related field and all school transcripts. Applicants must also submit GRE or GMAT scores and an essay describing a potential research project.
- Tuition : N/A
- Program Length : Unknown
- Delivery Format : On campus
- Percentage Awarded Loans: 38%
Dakota State University
Founded in 1881, Dakota State University is a small college located in South Dakota. The public college administers programs through four colleges. DSU holds several accolades for cybersecurity education from the National Security Agency and Department of Homeland Security.
Ph.D. in Cyber Defense
Students can earn DSU's Ph.D. in cyber defense without sacrificing their careers. Enrollees complete this 72-credit cybersecurity degree mostly online. The curriculum blends technical skill development, research, and managerial competency. Students attend three on-site research seminars held at the Madison campus.
A required core covers subjects such as data privacy, incident response, and computer forensics. All students complete a research core in preparation for the dissertation. Enrollees can use elective credit to further develop their managerial or technical skills. They can also pursue an optional internship.
Online learners receive access to resources, researchers, and peers through the Madison cyber labs. Full-time students with a master's degree can complete the cybersecurity degree in three years.�
Applying to DSU
Applicants must have a bachelor's or master's degree in cyber, computer science, or a technology-oriented field, a minimum undergraduate 3.0 GPA, and GRE scores.
- Accreditation : Institutional: Higher Learning Commission (HLC)
- Tuition : $470/credit in-state; $580/credit out-of-state
- Program Length : 3-7 years
- Delivery Format : Hybrid
- Percentage Awarded Loans: 43%
Marymount University
Marymount University is a private Catholic college located in Virginia. The region boasts robust employment opportunities and a hub for cybersecurity. Graduates can seek employment at various governmental agezancies in the Washington, D.C., metro area focused on cybersecurity initiatives.
The D.Sc. in cybersecurity enrolls learners with a bachelor's or master's degree. Students complete 36-72 credits depending on their education level. Degree-seekers can choose an online, hybrid, or on-campus format.�
The D.Sc. in cybersecurity builds on students' prior computer networking education or experience. Those without this knowledge may need to complete a prerequisite course to level up their knowledge. The cybersecurity curriculum covers areas such as computer security, managing cybersecurity risk, and digital forensics and incident response.�
All students engage in applied research in cybersecurity and develop a dissertation they must defend. Marymount is designated a center for excellence in cyber defense education by the National Security Administration and Department of Homeland Security.�
Applying to Marymount
Admission to the D.Sc. in cybersecurity requires a bachelor's or master's degree, school transcripts, and writing samples. Applicants must have also passed a college-level statistics course.
- Accreditation : Institutional: Southern Association of Colleges and Schools Commission on Colleges
- Tuition : $1,140/credit
- Delivery Format : 100% online, on campus, or hybrid
- Percentage Awarded Loans: 48%
Nova Southeastern University
A private institution in Fort Lauderdale, Florida, Nova Southeastern University serves about 24,000 students. Seventeen NSU Sharks teams compete in Division II of the National Collegiate Athletic Association.
Ph.D. in Cybersecurity Management
Designed for working professionals, Nova Southeastern University's Ph.D. in cybersecurity management program is part of the National Security Agency-recognized Center for Information Protection, Education, and Research.�
The computing and engineering college offers the hybrid degree, which combines online and in-person classes. Students attend once-a-term, four-day sessions on campus and complete research, assignments, and online activities between sessions.�
The 67-credit curriculum requires classes like information security risk management, human-computer interaction, and information protection. Students complete at least two doctoral research classes and a doctoral research dissertation. NSU's College of Computing and Engineering offers six fellowships for Ph.D. candidates pursuing a cybersecurity management or computer science degree.
Applying to NSU
Admission requirements include a relevant master's degree from a regionally accredited institution and a minimum 3.25 GPA. Applicants must submit transcripts, a resume or CV, an essay, and three letters of recommendation.
- Accreditation : Southern Association of Colleges and Schools Commission on Colleges (SACSCOC)
- Tuition : $1,282/credit
- Program Length : 67 credits
- Percentage Awarded Loans: 49%
St. Thomas University
A private Catholic school, St. Thomas University was founded in 1961 in Miami Gardens, Florida. The school offers a robust program catalog, including 11 doctoral programs.
Executive Doctorate of Business Administration in Information Security
St. Thomas University's Gus Machado College of Business offers a practice-focused executive doctorate of business administration in information security (EDBA-IS). The program adopts the engaged scholarship model. Students learn to apply current research to information security problems.�
Designed for executives with 7-10 years of cybersecurity management or consulting experience, the EDBA-IS is a three-year, part-time program. Students can transfer up to 12 graduate credits to the first-of-its-kind degree.�
The curriculum includes classes in research design in business administration and information privacy. The program does not require a comprehensive exam. The limited residency EDBA-IS program features nine weekend meetings each year.
Applying to STU
The no-GRE/GMAT program requires applicants to submit a completed online application and transcripts. The application is free.�
- Tuition : $1,025/credit
- Program Length : 3 years
- Delivery Format : On campus (limited residency)
- Percentage Awarded Loans: 19%
What To Expect From A Doctoral Degree in Cybersecurity
Cybersecurity doctorates offer two programs — the Ph.D. (doctor of philosophy degree) or the D.Sc. (doctor of science degree). The Ph.D. focuses on research and theory while the D.Sc. emphasizes application and action.
Students who earn a Ph.D. generally want to add to the body of research or teach at the postsecondary level. The D.Sc. prepares cybersecurity professionals to lead security teams in complex technological environments. Some schools offer a doctorate of information assurance, which is a professional degree similar to the D.Sc.
The Ph.D. requires an average load of 60 credits beyond the undergraduate degree and takes 3-7 years to complete. The D.Sc. demands a similar level of work but may operate in a cohort model, concluding in as few as three years.
Both doctoral programs offer research opportunities in subject areas such as artificial intelligence, cloud computing, and public policy. Like other doctorates, a cybersecurity degree concludes with a dissertation or a doctoral project.
The cost of a doctoral degree in cybersecurity depends on many factors. In-state public schools generally charge less than private or out-of-state institutions, and prestigious schools may cost more than their peers. On-campus cybersecurity Ph.D. programs sometimes offer assistantships that cover most or all of the cost of a doctorate.
Admission Requirements
Some doctorates in cybersecurity welcome applicants with only a bachelor's degree in a related field. Others require a master's degree for admission. An applicant's highest degree should always come from an accredited institution.
Cybersecurity doctoral programs often demand a minimum 3.0-3.5 undergraduate GPA. Some schools require GRE scores, but others admit applicants on the strength of their academic and professional backgrounds alone.
In addition to an undergraduate or graduate degree, prospective students need to submit an application, an essay, a resume, and letters of recommendation. Applicants usually pay an application fee ranging from $50 to $100.
Degree Options
Prospective students can consider several options when looking at a doctoral degree in cybersecurity. For instance, online programs offer flexibility and study-life balance, but an on-campus doctorate in cybersecurity provides face-to-face time with professors and peers.
A degree's curricular focus varies by program. Ph.D.s in cybersecurity emphasize designing and completing a research project with a goal of producing researchers and teachers. D.Sc. degrees elevate technical leadership with a goal of producing technical specialists and organizational leaders.
Even within cybersecurity Ph.D. programs, different universities have carved out their own areas of expertise. Subdiscipline specialties may include cybersecurity policy, emerging threats, or enterprise risk management.
Popular Cybersecurity Courses
Courses vary by school. A standard curriculum includes core courses in information security, information governance, and risk management. Students may also take concentration courses in areas like digital forensics or blockchain. A doctoral degree in cybersecurity concludes with a research sequence leading to a dissertation or capstone project.
Information Technology in a Global Economy
Emerging threats and countermeasures, human-computer interaction, how much will a doctoral degree in cybersecurity cost.
Several factors help determine the cost of getting a doctoral degree in cybersecurity. Things like state residency, degree format, available funding, and school prestige can all affect tuition prices.
According to the National Center for Education Statistics , in the 2019-20 academic year, the average public institution tuition was $12,410, while private institutions charged $26,597. Nonprofit, private colleges and universities charged an average of $28,430 while for-profits charged $14,289.
Students may incur other costs during their studies. Whether living on campus or studying from home, degree-seekers still need to budget for housing expenses, food, transportation, healthcare, insurance, and other expenses. Some institutions also charge technology fees or graduation fees.
Learners may not have to shoulder all the burden of a doctorate in cybersecurity alone. Applicants should explore financial aid options, including employer reimbursements, scholarships, fellowships, grants, and graduate assistantships. Many schools also offer tuition reductions for military personnel or teachers. Learn more at the link below.
Careers for Doctoral Graduates
Graduates with a bachelor's or master's degree can gain entry-level careers in computer science professions. Securing a position in corporate computer science research or as a professor at a university, however, often requires a graduate degree.
According to the BLS , computer information researchers earn a median annual salary of $126,830. The BLS also projects this field will grow 22% between 2020 and 2030.
Computer Science Professor
Computer science professors teach courses at the college/university level. Part-time professors or those who serve at small or community colleges often spend most of their time teaching. Tenured professors at research institutions may also engage in research, serve on academic committees, direct graduate student research, or make presentations at conferences and symposia.
Required Education: Doctorate
Job Outlook (2020-30): +12%
Median Annual Salary: $80,560
Computer Information Researcher
Computer information researchers solve complex problems in the computer science field. These professionals follow the scientific method: forming a hypothesis, designing an experiment, and recording their findings. They may study existing technology to improve its efficiency, or develop new tools and methods for computer programmers.
Required Education: Master's degree
Job Outlook (2020-30): +22%
Median Annual Salary: $126,830
IT Architect
IT architects organize and manage a company's technological components. They focus on business technology or security architecture. IT architects also help corporations, public agencies, or nonprofit organizations maintain compliance with computer security regulations. While IT architects do not have to hold a graduate degree, additional education may lead to management jobs in the field.
Required Education: Bachelor's degree
Job Outlook (2020-30): +5%
Median Annual Salary: $116,780
Data Scientist
Data scientists use data to solve problems. These professionals create mathematical models that corporate decision-makers can use to address real-world situations. Data science requires knowledge of analytics, computer languages, and machine learning. A Ph.D. in computer science often explores these concepts in depth.
Job Outlook (2020-30): N/A
Average Annual Salary: $97,000
Software Developer
Software developers design and build computer programs. They may write a new piece of software from scratch, or they might modify an existing piece of technology. A software developer's daily activities depend on their focus, and professionals who hold advanced education may qualify for software leadership roles.
Median Annual Salary: $110,140
Choosing the Right Cybersecurity Doctoral Program
Of all cybersecurity programs, a doctorate requires the most commitment to the discipline. Prospective students should review several factors before pursuing a doctorate. The most important of these factors is accreditation.
Regionally accredited schools offer credibility, marketplace utility, transfer options, and financial aid opportunities that may not extend to unaccredited institutions. One program accreditor, ABET, accredits bachelor's degrees in cybersecurity, but their accreditation does not cover doctorates.
Other decision-making factors include:
- Faculty Interest: At the doctoral level, students should consider whether an institution's faculty interests align with their own research pursuits.
- Ph.D. vs. D.Sc.: These two programs each create pathways to distinct outcomes. Prospective researchers and teachers should look at cybersecurity Ph.D. programs, while aspiring corporate leaders may want to consider D.Sc. options.
- Location: On-campus programs in other states may require learners to relocate and pay higher tuition. Some online programs may also require in-person meetings that involve periodic travel.
- Alumni Network: At top universities, a robust alumni network can help boost graduates' professional contacts.
Other Educational Paths
Educational options other than a doctorate can also lead to meaningful, lucrative careers in cybersecurity. Nevertheless, more education often equals more income.
For example, research at the Center on Education and the Workforce at Georgetown University revealed that workers with a doctorate earn a median salary of $4 million over their lifetime, compared to median lifetime earnings of $2.8 million for workers with only a bachelor's degree.
Individual experiences may not reflect these trends, however. The cost savings of a bootcamp or the benefits of a master's degree could prove sufficient for some students' goals.
Explore other cybersecurity education paths

Cybersecurity Certificates

Associate Degrees in Cybersecurity

Online Bachelor's Degrees in Cybersecurity

Bachelor's Degrees in Cybersecurity

Master's Degrees in Cybersecurity

Online Master's Degrees in Cybersecurity

Find the Right Bootcamp For You
Faq's about doctoral degrees in cybersecurity, is a ph.d. in cybersecurity worth it.
A Ph.D. in cybersecurity can prepare learners for lucrative and meaningful careers as leaders in a dynamic field. The degree can also equip students for roles in research, teaching, or public policy leadership.
What is the difference between a D.Sc. and a Ph.D.?
The D.Sc. prepares seasoned cybersecurity professionals to lead teams that address complex problems. The Ph.D. prepares aspiring academics who plan to conduct research or teach at a college or university.
How long does it take to get a D.Sc. degree?
Earning a D.Sc. can take 3-7 years depending on whether a student has earned a master's degree prior to enrollment. Some D.Sc. programs operate on a strict cohort model, wherein learners may graduate more quickly.
Which is better, a Ph.D. in cybersecurity or a D.Sc. degree?
These two doctoral degrees in cybersecurity help learners achieve different goals. The Ph.D. works better for learners planning careers in research or postsecondary teaching. The D.Sc. may prove more effective for students who aspire to lead cybersecurity teams.
Recommended Reading
Take the next step toward your future.
Discover programs you’re interested in and take charge of your education.
- cityline.com
- +1234 567 892
Computer Science and Engineering IIT Kanpur
Bt-mt dual degree, mtech and ms in cyber security.
' This list will change as per the availability of new faculty offering new courses related to the curriculum. '
Core Faculty
Manindra Agrawal
Sandeep K. Shukla
Debadatta Mishra
Nitin Saxena
Priyanka Bagade
Urbi Chatterjee
The department of Computer Science and Engineering at IIT Kanpur has been offering a good number of courses in Cyber Security related subjects for the last 4 years. Multiple faculty members in the department are engaged in research projects related to cyber security. Therefore, the department feels that it has a critical mass in terms of faculty strength to create new degree programs specializing in cyber security.
Simultaneously, the NASSCOM projects that the country needs cyber security professionals in large numbers – approximately 1 million currently. These professionals also need to have varying degrees of expertise, in order to fulfill their job obligations. The possible roles in cyber security jobs are cyber vulnerability assessment and penetration testing (VAPT) engineers, security operations center (SoC) analysts, security strategists, developers of cyber security tools and technologies, cyber security policy developers, researchers, and chief information security officers (CISO)s etc.
Additionally, a number of Army and Navy officials have personally visited IIT Kanpur, and requested that specialized Masters programs in Cyber Security be offered to defense personnel who upon completion of their degrees here – could join various positions at the defense CERT (Computer Emergency Response Team), the WESEE (Weapons and Electronics Engineering Center, Indian Navy), the Defense Intelligence Agency (DIA) , Defense Cyber Agency (DCyA) etc., where cyber security professionals are urgently required.
Due to the confluence of these three facts, the department of CSE is proposing three new master’s programs specializing in Cyber Security. The MTech program in Cyber Security is meant to cater to the students who are likely to take up jobs as VAPT engineers, security center analysis, CERT engineers, cyber security tool developers etc. The MS by research program is designed to train cyber security researchers, technology developers, cyber security strategists, and top-level Cyber Security policy designers. Also, an option for BT-MT dual degree students is proposed to specialize in Cyber Security. This proposal describes the three proposed programs.
Motivation and Goals of the Program
According to the Data Security Council of India’s latest annual Cyber Security India Market report, the cyber security market in India will grow from USD 1.97 billion in 2019 to USD 3.05 billion by 2022. NASSCOM – an industry body for the information technology (IT) industry projected recently that India will need approximately 1 million cyber security professionals in order to protect its cyber space from cyber-attacks. These jobs span diverse sectors including the software product industry, software-based services industry, as well as the government agencies such as NCIIPC (National Critical Information Infrastructure Protection Center), CERT-IN (Computer Emergency Response Team of India), Sector specific CERTs (such as CERT POWER, CERT FINANCE etc.), NIC, Defense CERT, and Defense labs such as WESEE, Defense Intelligence Agency etc.
At the same time, Army and Navy officers have repeatedly requested that IIT Kanpur offer new opportunities for their officers who are deputed to complete their M. Tech at IIT Kanpur. A frequent request has been a degree in Cyber Security in order to train for cyber security related jobs in the Defense. It is worth noting here that the government has recently announced setting up of Defense Cyber Agency (DCyA) for cyber warfare and this agency will require a significant number of well-trained officers.
Our faculty members have been approached by companies such as Intel, AMD, Fortanix, NetApps, NXP Semiconductors, Texas Instruments etc., requesting student interns and future employees who could work in the areas of micro-architecture security, hardware security, secure machine learning etc.
Combined with these three factors is the fact that in the recent years, the Computer Science and Engineering (CSE) department has been offering a large variety of cyber security related courses, and several faculty members are engaged in cyber security related research projects. A fairly good number of Masters’ thesis projects have been completed in cyber security related topics.
Keeping these factors in mind, the CSE department has decided to propose three Masters programs with specialization in Cyber Security. The first proposal is to provide an opportunity for BT-MT dual degree students to specialize in cyber security by fulfilling the same course requirements as the proposed MTech program with this specialization. The second proposal is to create an MTech degree with specialization in Cyber Security, and the third proposal is to create an MS by research program with specialization in Cyber Security.
Nature of Employment for students graduating with Cyber Security Specialization
As mentioned earlier, in the recent past, we have received a number of requests from government and non-government entities for creating specialization program in Cyber Security as there is a severe lack of trained man power in this field. In order for everyone to understand the various job roles available, and to distinguish between the job roles expected to be taken up by graduates of BT-MT dual degree students, MTech students and MS students, here we provide a list of common job types for Cyber Security professionals in India.
Like many fields of engineering, the government and industry need both cyber security generalists who have very broad understanding of various aspects of cyber security and how they interact with each other, as well as domain specialists who focus on a single domain – such as Network Security, Web Security, Vulnerability Assessment, Penetration Testing, Hardware Security etc. While the first type of role would require breadth and some depth, the second type requires domain specific depth, and hands-on experience in researching the specific domain.
Domain Specialist Jobs
- Information Security Analyst
- Cryptographer
- Security Administrator
- Penetration Tester
- Sector specific Security Operations Center Analyst
- Security Operations Center Head
- Cyber Security Product Engineers
- Cyber Security Application Engineers
Generalist Jobs
- Chief Information Security Officer
- Security Architect
- Lead Software Security Engineer
- Cyber Security Product Architect
- Cyber Security Service Architect
- Cyber Security Researcher
- Cyber Security Policy Designer
- Cyber security Strategists
The above list is not exhaustive, but aims to provide aa broad overview of the diverse roles and responsibilities for cyber security professionals. The roles in blue are roles that require training and hands-on experience in domain-specific cyber security technology, and employees with these roles will be doing more hands-on engineering, product development, application engineering of products etc. The roles in bold and green font are roles that would require more breadth and some hands-on experience. Therefore, it is expected that the generalist jobs will be more suitable for students graduating with BT-MT or MTech in Cyber Security while the other jobs will be more appropriate for students graduating with an MS by research in cyber security with a very in-depth thesis component in a specific topic.
Our proposed curriculum is reflective of what courses we currently have on offer, and we believe that in the future, our curriculum will have a broader choice of courses and courses in Cyber Security Ethics, Laws, and Regulations may be introduced.
Curriculum Structure
Table 1 list of cyber security courses currently offered.
The courses CS 628A and CS 641A will be designated as core courses for all proposed Masters programs.
Table 2 summarizes the credit requirements for the various programs.
Each student must complete the two core courses from the Group A courses. They also must complete 27 credits (i.e.3 courses of 9 credit hours each) out of the list of courses in Group B and at least 9 credits (i.e. 1 course of 9 credits) from the list of courses in Group C. However, in total, a student must complete a total of 63 credits (7 courses – each of 9 credits) for completing his/her degree requirements. Therefore, they must complete a minimum of 54 credits (6 courses of 9 credits each) from Group A, B and C, another 9 credits can be taken from either group B or Group C, or any other CSE department course with the explicit permission of the DPGC.
The list of courses currently available are listed in the Table 1. It will be extended in the future. The student must also complete thesis work worth 81 thesis credits (9 units). All requirements for MTech program of CSE vis-a- vis thesis work applies. In summary, the total number of credits required for MTech is 144 credits (63 credits in courses, and 81 credits in M. Tech thesis work).
BT-MT Dual Degree
For students in the BT-MT dual degree, minimum 81 credits of thesis work, and 54 credits in course work (with 18 credits of core courses, minimum 27 credits from Group B courses, and minimum 9 credits from Group C courses) must be completed. Another 9 credit PG level course must be taken either from the Group B or Group C or any other course offered by the CSE department with explicit permission of the DUGC.
For MS by Research
Each student must complete 18 credits of core courses and 18 credits of courses from Group B (i.e. 2 courses each of 9 credit hours). The list of courses in Table 1 will be extended in the future. The student must complete thesis credit of 108 credits (12 units). All requirements for MS program in CSE vis-à-vis thesis work will apply.
Initial Intake Plan
The goal is to start with a small size. For the BT-MT program, we propose to accept up to 10 students for the cyber security specialization. For the MTech program -- we plan to initially accept up to 15 students through GATE and 10 students from Defense and Government sectors based on selection by the Defense/Government agencies. For the MS program, 10 students through GATE, and 5 students from Defense, Government, and Industry sector. There will be no GATE requirement for candidates from Defense/Government/Industry sectors. The reservations as per rules will apply.
Table 3 Initial Intake Plan
Admissions criteria.
The admissions for the various programs will be as per the PG manual .
- Post Doctoral Fellows
- Current Timetable
- PhD Comprehensive
- Academic Integrity
- Mid-Sem Exam Schedule
- End-Sem Exam Schedule
- Dual Degree
- BT-MT, MTech, MS in Cyber Security
- Minor Programs
- e-masters (Enrollment Link)
- Under Graduate
- Post Graduate
- Counselling
- Lab Facilities
- Room Booking
- Newsletters
- Publications
- CDIS Center
© CSE, IIT Kanpur. All rights reserved.
- Go to IITD Website
- M. Tech. in Cyber Security
SIT hosts the interdisciplinary M. Tech. program in Cyber Security , for which the first batch of students was admitted in 2021. Partner academic units in this program include Departments of Computer Science and Engineering, Electrical Engineering, Mathematics, and Management Studies. The CoE-CSIA co-ordinates the Cyber Security initiatives in the institute.
Amar Nath and Shashi Khosla School of Information Technology, IIT Delhi
+(91) (11) 2659-6056.
- A
- T
- Aerospace Engineering
- Biological Sciences & Bioengineering
- Chemical Engineering
- Civil Engineering
- Computer Science & Engineering
- Electrical Engineering
- Management Sciences
- Materials Science & Engineering
- Mechanical Engineering
- Sustainable Energy Engineering
- Humanities & Social Sciences
- Economic Sciences
- Cognitive Science
- Earth Sciences
- Mathematics & Statistics
- Space, Planetary & Astronomical Sciences & Engineering
- Department of Management Sciences
- Materials Science Programme
- Nuclear Engineering & Technology
- Photonics Science and Engineering Programme
- Gangwal School of Medical Sciences and Technology
- Kotak School of Sustainability
- Advanced Centre for Material Science(ACMS)
- Advanced Centre for Electronic Systems(ACES)
- Advanced Imaging Centre
- Centre for Enviromental Science & Engineering
- Centre for Mechatronics
- Centre for Lasers and Photonics
- Computer Aided Design Laboratory
- Centre for Nanosciences
- Prabhu Goel Research Centre for Computer and Internet Security
- Samtel Centre for Display Technologies
- SIDBI Innovation and Incubation Centre
- Center for Mathematical Sciences
- Syndicate Bank Entrepreneurship Research and Training Centre (SBERTC)
- Centre for Continuing Education (CCE)
- Electronic and ICT Academy(E&ICT Academy)
- Centre for Energy Regulation (CER)
- Center for Ganga River Basin Management and Studies
- Energy Analytics Lab (EAL)
- Rice-IITK Collaborative Center
- Mehta Family Centre for Engineering in Medicine
- IIT Kanpur-La Trobe University Research Academy
- Chandrakanta Kesavan Center
- Just Transition Research Centre (JTRC)
- MedTech IIT Kanpur
- Centre for Railway Research (CRR)
- Computer Centre
- P. K. Kelkar Library
- Facility for Ecological & Analytical Testing
- Office Automation
- Scientific Glassware Fabrication & Special Water Facility (SGF&SWF)
- Imagineering Laboratory
- Central Cryogenic Facility
- Liquid Helium Facility
- SQUID Facility
- Virtual Instrument Cell
- National Center for Geodesy (NCG)
- National Centre for Flexible Electronics
- National Information Center of Earthquake Engineering
- National Wind Tunnel Facility
- KIT IIT Kanpur
- Quality Improvement Program (QIP)
- IP & Technology Transfer Cell
- Directorate
- Convocation
- Transcripts
- Current Registration/Add-Drop
- Pre-registraion
- Lecture Hall Booking
- Dues Clearance System
- Information Brochure
- Rolling Advertisement
- Current Opening
- Awards and Honors
- Faculty Forum
- Faculty Benefits
- Artist and Scholar In Residence
- Dean, Digital Infrastructure & Automation
- Office Orders
- Alumni in News
- Awards and Honours
- Academic Initiatives
- Students Initiatives
- Batch Initiatives
- Student Assistance
- Alumni Assistance
- DORD Online
- Research Centers
- Newsletters
- R&D Forms
- Project Vacancies
- Call for Proposal
- SURGE Programme
- Student Gymkhana
- Students Awards
- Training & Placements
- Counselling Service
- Physical Education Section
- Form DOIP: 101
- Office Order related to Project Employee
- Partnership
- News and Updates
- Students' Placement Office
- Why recruit at IITK?
- Procedures and Policy
- Contact Placement Coordinator
- Job Announcement Form
- Internship Offer Format
- Campus Recruitment Brochure
- Campus Recruitment Guide
- Departmental Brochures
- Institute Club & Community Center
- Gliding Club
- Swimming Pool
- Staff Gymkhana
- Visitors' Hostel
- Women's Association
- Lecture Hall Complex (L.H.C) Booking
- Emergency Services
- Central Stores
- Estate Office
- Finance & Accounts
- Health Centre
- Institute Works Department
- New Office Automation (Pingala)
- Media Technology Centre
- Image Archives
- NOIDA Outreach Center
- Internal Audit Section
- Public Information
- Institute Holidays
- Restricted Holidays
- Birds in IIT Kanpur
- Vehicle Pass Form
- Kislaya Nursery School
- Campus School
- Opportunity School
- Kendriya Vidyalaya
- Communication Skills
- Time Management Skills
- Interpersonal Skills
- Teamwork Skills
- Work Delegation Skills
- Work Ethics
- Debates & Discussions
- Guidelines for Communicating in Writing
- Self-Help Website for COVID
- Suggest a Quick Link
- Plan Your Visit
- Health Center
- P K Kelkar Library
- Campus Maps
- Directories
- OFFICE AUTOMATION
- Staff Bus Service
- IITK History
- Institute Archives
- Seminar & Thesis Defense Announcements
- Old Website
- Academic Calendar
- Faculty & Staff Campus Life
- Faculty Vacancies
- Teaching Blog
- Dean R & D
- R&D Newsletter
- R&D Profile
- SIDBI Innovation and Incubation Center
- Technopark@IITK
- Institute Lecture Series
- C.N.R Rao Lecture Series
- Intranet Users
- Apply for No Dues
- No Dues Admin
- New Dues Clearance System
- Students Gymkhana
- Computer Center
- Exam Schedule
- Student Campus Life
- COGJET-2020
- Alumni Impact
- Alumni Magazine
- Alumni Association
- Staff Overview
- Staff Vacancies
- Press Releases
- Media Coverage
- Extra Quick Link 1
- Extra Quick Link 2

- Institute Overview
- Featured Research
- Education at IITK
- Old News @ IIT Kanpur
- Avant Grade
- Board of Governors
- Key Administrators
- Organization Tree
- Registrar Office
- Finance Office
- Annual Report
- International Relations
- 360 Degree Campus View
- Campus Directory
- Campus Wiki
- Weather Information
- Announcements
- Latest News
- Women's Cell
- Research Overview
- Sustainable Tech. Research
- Socially Relevant Research
- Sponsored Programmes
- Dr. Tapan K. Sengupta
- Dr. Amey Karkare
- Dr. Bharat Lohani
- Major Research Areas
- R & D History
- Publications
- Interesting Videos
- SandHI Initiative
- INVENT Social Incubation Program
- IITK Faculty
- Research Highlights
- Awards & Honours
- Dr. Amitabha Bandyopadhyay
- Dr. Niraj Sinha
- Dr. Nandini Gupta
- Find An Expert
- Design & Scientific Officers
- Featured Facility
- Teaching blog
- News & Announcements
- IITK Research Scholars
- Education at IITK
- Information for Future Students
- International Students
- Parents & Families
- Financial Aid
- Ph.D / M.Tech / M.Des Admission 2014-15
- MBA Admission 2016-17
- Outreach Cell
- Student Placement Office
- Tuition Fees
- Scholarships and Awards
- Hobby Clubs
- Entrepreneurship with IITK
- IITK Courses
- Foreign Language Prog.
- Academics at IITK
- Internship at IITK
- Consulting Overview
- Dr. Anoop Singh
- Dr. S. Bhattacharjee
- Dr. Koumudi Patil
- Access Labs & Facilities
- License technology
- Sponsor Research
- Find an Expert
- NERD Magazine
- Projects & Case Studies
- Innovation at IITK
- Innovation Highlights
- Eligibility
- Success Stories
- Funding Options
- Incubated Companies
- Patents & IPR
- Incubation Resources
- Infrastructure Initiatives
- Awards & Achievements
- Notable Alumni
- Office of DoRA
- IITK Foundation
- Entrepreneurship
- Government Services
- Human Resource and General Administration Section
- Staff Members
- Staff Achievements
- Campus Maps
- Staff Training
- Research Management
- Culture at IITK
- Cultural Events at IITK
- Sports at IITK
- Sports Facilities
- Weightlifting
- Eating Places
- Recreational Facilities
- Rock Climbing
- Cultural Societies
- Tae Kwon Do
- Skip to content
- Jump to main navigation and login
Nav view search

MTech, MS by Research, and BT-MT Dual Degree programs to be available from August 2021 and admissions to commence during the April-May 2021 cycle
Kanpur, December 15, 2020 : In today’s digital world, vulnerability of the digital borders is the most critical and vital security threat a country can face. Given the fact that this attack on our digital infrastructure can originate from any individual, organisation or rogue nations that could bring the nation to its knees without a single drop of blood shed with little or no advance warning. The nature and ubiquity of this threat makes self-reliance in cybersecurity and trained cybersecurity professionals or digital soldiers highest priority for any nation’s defence systems. To address this need and to meet the shortfall in trained and skilled cybersecurity personnel in the country, the Indian Institute of Technology, Kanpur (IIT-K) is first to introduce three new master’s programs in Cybersecurity in addition to a dedicated centre for cybersecurity. These programs are designed to address this need by ensuring the training of dedicated and highly skilled manpower furthering and accelerating the nations march towards a Digital India.

The Department of Computer Science and Engineering (CSE), IIT-K would offer the three courses, M Tech, MS by Research, and BT-MT Dual Degree in Cybersecurity from August 2021. The programs would start with a limited number of seats with plans to gradually scale up in size and scope. The initiative for launching the three courses in Cybersecurity was taken by Prof. Manindra Agrawal and Prof. Sandeep K. Shukla from the Department of Computer Science and Engineering. Admissions for the courses will commence during the April-May 2021 cycle.
The MTech program in Cyber Security will equip students with skills necessary to be successful in roles such as VAPT (Vulnerability Assessment and Penetration Testing) engineers, Security center analysts, CERT (Computer Emergency Response Team) engineers, Cybersecurity tool developers and other roles that involve protecting systems against the threat of attacks by malicious actors. The MS by Research program is designed to train Cybersecurity researchers, Technology developers, Cybersecurity strategists, and top-level Cybersecurity policy designers. An option for BT-MT dual degree students is proposed that will enable them to specialize in Cybersecurity.
Prof. Abhay Krandikar , Director IIT Kanpur, said, “In the world of Digital Nomads (especially after Covid19) and Gig Economy, there has been a significant shift to the cloud as almost everyone who is involved in a productive activity has had to go online and use digital devices. This shift means there are millions of new netizens and organizations that are potentially vulnerable to sophisticated cybercrime. We have timed these Masters programs to ensure that we start producing cyber warriors of the future who can defend not only national boundaries but also make a mark internationally.
Our vision resonates with Hon’ble Prime Minister Narendra Modi’s vision - “I dream of a Digital India where cybersecurity becomes an integral part of our national security.” And we are happy that we are able to do our bit in this direction”.
Dr Radhakrishnan K Koppillil , Chairman BoG, IIT Kanpur added, “I was very happy to help to approve these Masters programs and believe that we at IIT Kanpur could not have timed it any better. The need for cyber warriors and cyber defenders is now felt more keenly . IIT Kanpur has always led the innovation in education from the front and this is just another example of the same”.
The initial intake to the MTech program in Cyber Security will be limited to 15 students through GATE/industry sponsorship and 10 students from Defence and other strategic government bodies to address the need in beefing up the cybersecurity and cyber-defence workforce in the government. The MS by Research in Cybersecurity program will accept 10 students through GATE and industry sponsorship and 5 students from Defence and other Government agencies. The BT-MT dual program is only open to the IIT-Kanpur Computer Science and Engineering BTech students who want to opt for a BTech-MTech dual degree by completing additional credits to earn a master’s degree. These numbers include the necessary percentage of reserved seats from various reserved categories as per the extant laws.
Prof. Manindra Agarwal , Department of CSE, IIT Kanpur said “The last years have seen our department offering quite a few courses in Cybersecurity related subjects. Several faculty members in the department are also engaged in research projects related to cybersecurity. Our faculty members have also been approached by various multinational companies, requesting students as interns and future employees who could work in the areas of micro-architecture security, hardware security, secure machine learning and related areas. The present situation is that education and training institutions have found it difficult to keep pace with the growing need for skilled cybersecurity talent. NASSCOM has indicated that rise in cyberattacks along with data protection and privacy laws will lead to a US$35 billion revenue opportunity and job opportunities for millions of Indian professionals by the year 2025. With the department achieving a critical mass in terms of faculty strength to create new degree programs specializing in cybersecurity, we decided that this was the appropriate time to introduce new programs in Cybersecurity.”
IIT Kanpur’s C3i Center funded by the SERB (Science and Engineering Research Board) is India’s first cyber security research and education centre in the field of cybersecurity of critical infrastructure. Further, the C3i Hub (The Technology Innovation Hub funded by DST’s National Mission on Cyber Physical systems) established at IIT Kanpur adds additional strength to the research, education, start up ecosystem, and industrial collaboration in the field of cyber security unparalleled in India at the time. The students of these new degree programs will get the opportunity to train at these state-of-the-art facilities.
Prof. Sandeep K Shukla , Department of CSE, IIT Kanpur, added, “By 2022, the global cybersecurity workforce shortage has been projected to reach upwards of 1.8 million unfilled positions. In India, an estimate by the Data Security Council of India indicates a requirement of about 1 million cybersecurity professionals. A study indicated that last year, there was a 117% increase in incidents of cyberattacks on Indian enterprises as compared to the previous year. With a corresponding increase in demand from companies looking to hire cybersecurity professionals, the gap in the availability of skilled cybersecurity professionals has widened and these courses are a beginning, albeit small, in meeting the demand and filling this gap.”
The courses will also meet the demand from the Defence sector for a specialized Masters program in Cybersecurity for defence personnel. Upon completion of the course, these trained personnel could take up responsibilities at various defence establishments such as CERT (Computer Emergency Response Team), WESEE (Weapons and Electronics Engineering Centre, Indian Navy), Defence Intelligence Agency (DIA), Defence Cyber Agency (DCyA) and others where there is an urgent requirement for trained cybersecurity professionals and become the cyber-soldiers guarding our country’s cyber-borders!

- Pyro-Metallurgy Lab
- Process Research Lab
- Powder Metallurgy Lab
- Phase Stability Lab
- Particulate Materials Lab
- Metal Working Lab
- Materials Separation Lab
- Lab for Biomaterials
- V M Krushnarao Kotteda
- Ishita Sengupta
- Srinivas Dharavath
- MoU between Dynamatics and institute
- Media Invite Institute Foundation Day
- Accessibility
- Content Submission
- In Memoriam
- Hindi Website
Copyright © 2020
Executive-Friendly Program | High Impact Format
Are you ready to enhance your cybersecurity expertise? Selection Test Starts March 30th.
Elevate your Cyber Defense Game
E-masters in cyber security.
Build capabilities to combat an evolving threat landscape. Join the next generation of Cyber Security professionals with IIT Kanpur online masters degree program. Study with industry experts, develop hands-on skills and stay ahead in the field.
- No GATE Score required
- IIT Kanpur Alumni Status

Applications closing in

Key Highlights of IIT Kanpur Masters in Cybersecurity
- Selection Based on academic and professional background and test, interview where necessary. No GATE required.
- High Impact Format Weekend-only Live interactive sessions coupled with self-paced learning.
- Executive Friendly Schedule Learn while you earn, with the flexibility to complete the program between 1 - 3 years.
- Career Advancement and Networking Support for placement and facilitation of incubation at IIT Kanpur's Incubation Centre.
- IIT Kanpur Alumni Status Become an IIT Kanpur alumni with access to all the alumni privileges.
- Credits Transfer Waiver of upto 60 credits for higher education (MTech/PhD) at IIT Kanpur.
Admission Process
- Application Register with Mobile Number Submit Details Remit Application Fee Upload Documents --> Round 2 applications closing on 20th April --> Application Deadline - 12th May -->
- Selection Selection Test Starts March 30th Application Review Selection Test * Interview Selection Announcement June 2023 -->
Class Start - July 2024
* Selection test differs for every programme
e-Masters Degree in Cyber Security Overview
Elevate Your Career in Cybersecurity with IIT Kanpur e-Masters Degree Program.
With a growing number of cyber attacks on information systems, critical infrastructures, and personal devices, there is a high demand for proficient cyber security professionals. Our comprehensive IIT Kanpur Masters program in Cybersecurity offers online education, equipping you with the latest tools, technologies, and concepts in the field. By earning a Masters degree in Cybersecurity from IIT Kanpur, you can take your career to the next level and be ready to tackle the ever-evolving landscape of cybersecurity.
Explore our e-Masters program in Cybersecurity and join the ranks of top cyber security professionals in India and worldwide. Enroll now and enhance your mastery of the subject with our well-researched curriculum and hands-on experience through projects and case studies.
Graduation Ceremony at IIT Kanpur Campus

- Get eMasters Degree from IIT Kanpur
- Build world-class Cyber Security expertise
- Learn from the leading research faculty
- Receive mentorship and career support from the IIT Kanpur placement cell
- Incubation support for promising startup initiatives
- Become a part of IIT Kanpur's alumni network

Why do participants choose the eMasters degree?
- "I have been managing the technical aspect of Digital & Core banking functions of a banking company (Africa region) over the last decade. Presently, I am working on architecture plans for the secure adoption of On-Prem Cloud solutions & I believe eMasters would augment my skills in this domain." Jaiesh, Lead, Technical Delivery (Digital & Core Banking) for a leading British Bank (Africa region) with 12 years of experience
- "My aspiration to enroll in this program and advance in my IT career is motivated by the fact that I have a strong interest in cyber security. This presents an unmissable opportunity to deepen my knowledge and advance in the chosen discipline and pursue a career in it in the long run." Anudeep, IT Professional working with a leading IT Consulting Company with 8 years of experience
Hear from our Program Alumni

Learn from the experts working at the forefront of well-researched curriculum research and technology in Cyber Security.

e-Masters in Cyber Security Curriculum
A well-researched real-world curriculum by IIT Kanpur subject matter experts that fosters hands-on learning and helps you master the desired capabilities by combining deep formal rigour and an intense practical approach.
eMasters in Financial Technology & Management will be offered as a 60-credit program delivered over 12 modules of 5 credits each. The modules are categorized into Compulsory (C) and Projects (P) and participants need to study the compulsory courses and undertake projects, following the 10 C+2 P structure.
- Introduction to Cryptography
- Operating System Principles
- Computer Networking I
- Introduction to Application Security, Mobile Security, and Critical Infrastructure Security
- Computer Networking II
- Introduction to Linear Algebra
- Introduction to Web Security, Network Security and Defenses
- Machine Learning for Cyber Security
- Introduction to Hardware Security
- Embedded and Cyber Physical Systems, and IoT Security
- Advanced Topics in Cryptography
- Advanced Critical Infrastructure Security
- Introduction to Blockchain Technology
Detailed Curriculum
Immersive Learning Format

- Online LIVE and self-paced sessions are delivered through AI-powered iPearl.ai
- Live interaction as per the faculty availability
- Apply learnings through projects while working in teams and establish a peer network
- Final module-level exams will be conducted online
- Opportunity to meet experts and experience the IITK campus during campus visits
Eligibility
- Bachelor's degree (4 years program) or a Master's degree in appropriate discipline with at least 55% marks or 5.5/10 CPI + 2 years of work experience (an applicant need not be employed to be eligible).
- Minimum of 2 years of work experience (You need not be currently employed to be eligible).
- Candidates with relevant experience and coding knowledge will be preferred.
Cyber Security Masters: Fees

Fee structure for candidates opting to complete the program in 1 year .
*For every additional quarter, fees of Rs 15,000 will be applicable.
For Example
Candidates opting to complete the program in 5 quarters need to pay an additional fee of ₹15,000
Candidates opting to complete the program in 11 quarters need to pay an additional fee of ₹1,05,000
All other fees remain the same.
Fees paid are non-refundable (after a certain time period) and non-transferable.

- Partial Fee waiver available. For more details Click Here
About IIT Kanpur
Established in 1959 by the Government of India, Indian Institute of Technology Kanpur (IIT Kanpur) is a globally acclaimed university for world-class education and research in science, engineering, management and humanities. We aim to provide leadership in technological innovation for the growth of India.
- Ranked 1st in Innovation, 4th in Engineering and 5th in Overall Category by NIRF 2023
- Built on world-class academic research culture
- Offers various undergraduate, post-graduate, integrated, and research programs in the field of engineering, science, management, and design

State-of-the-Art Digital Learning Platform
The eMasters Program by IIT Kanpur will be delivered on iPearl.ai , a State-of-the-Art digital learning platform, powered by TalentSprint. iPearl.ai , highly rated for its user experience, is a direct-to-device platform that works seamlessly on any internet-connected device and provides a single-sign on experience for all your learning needs including recorded videos, reading material, live interactive sessions, assignments, quizzes, discussion forums, virtual lounges and more.
Frequently Asked Questions
What is the curriculum for the program, core modules.
- Introduction to Cryptography The module covers the basics of finite field Arithmetic, private and public-key cryptography, existing cryptosystems and their security, Cryptanalysis of existing systems and more.
- Operating System Principles The module covers the computer organization interface, the concept of a process, threads, scheduling, process synchronization, deadlocks, memory management, and more.
- Computer Networking I The module covers the introduction, history, and development of computer networks, networks topologies, various aspects of layering and protocols, physical layer, MAC layer, data link layer, and more.
- Introduction to Application Security, Mobile Security, and Critical Infrastructure Security The module covers various aspects of Security in Mobile Platforms, Application Security, and Issues in Critical Infrastructure and SCADA Security.
- Computer Networking II The module covers the network layer, transport layer, design issues in protocols at different layers, network programming, socket programming, and application layer.
- Introduction to Linear Algebra The module covers vector spaces, examples, Rn, Cn; subspaces, linear independence, dependence and dimension, linear transformations, matrices, matrix algebra, determinants, properties of matrices and determinants, systems of linear equations, and more.
- Machine Learning for Cyber Security The module covers an introduction to data classification, Supervised vs. Unsupervised Learning, Linear Regression, Multivariate Regression., Logistic Regression, Hypothesis Testing, Maximum Likelihood Estimation, Bayesian Classification, Model Selection, Regularization, Generalization, Cross Validation and more.
- Introduction to Web Security, Network Security and Defenses The module covers Security Issues in TCP/IP, Wireless Security, Network Defense tools, DNSSec, NSec3, Distributed Firewalls, Intrusion Detection tools, Threat Models, Denial of Service Attacks, DOS-proof network architecture, Security architecture of World Wide Web, Security Architecture of Web Servers, and Web Clients and more.
- Advanced Topics in Cryptography The module covers zero-knowledge protocols, one-way functions, advanced protocols for different applications, network, and system-level security issues, post-quantum Cryptography, and more.
- Computational Number Theory for Cryptographers The module covers Elementary Operations, Polynomials, Integer Lattices, Elliptic Curves, and more.
- Embedded and Cyber Physical Systems, and IOT Security The module covers the modeling, implementation, and verification issues related to developing a cyber-physical system. In addition, through the discussion of implementing an embedded control system, the module will cover the basic design principles of an embedded system.
- Introduction to Hardware Security The module provides an in-depth understanding of Internet of Things (IoT) ecosystem and security vulnerabilities, attacks on cyber-physical systems, reverse engineering, side-channel attacks, intellectual property (IP) piracy, Hardware Trojan, electronic counterfeiting, Physical Unclonable Function (PUF) and more.
- Introduction to Malware Analysis The module covers malware classification, types, and platform-specific issues with malware, Intrusion into IT and operational network (OT) and their signs, manual malware infection analysis, signature-based malware detection and classification – pros and cons, and need for machine learning-based techniques, and more.
- Game Theory The module covers non-cooperative game theory, complete information sequential move games, complete information simultaneous move games, incomplete information games, cooperative Game Theory, and more.
- Advanced Critical Infrastructure Security The module covers Stuxnet worm and its aftereffects in the Critical Infrastructure security, Game Theory and other analytical modeling of the security problems of critical infrastructures, security of the Networked Infrastructure, event monitoring, Event Correlation, and Situational Awareness, vulnerability Database and its importance and more.
- Honeypots and Deception Technologies for Advanced Protection The module covers Cyber Threat Intelligence Collection Techniques, OSINT, Deception Technology for Monitoring Cyber Threat, Client-Side Deception Techniques, Service side Deception techniques, IT honeypots, OT honeypot, ICS Honeypots and more.
- Introduction to Blockchain Technology The module covers Basic Cryptographic primitives used in Blockchain – Secure, Collision-resistant hash functions, digital signature, public-key cryptosystems, zero-knowledge proof systems, basic Distributed System concepts, Blockchain 2.0, Blockchain 3.0, E-Governance and other contract enforcement mechanisms, and more.
How the modules will be sequenced in the program?
What is the tentative time-table for the live interactive sessions.

- Payment Gateway
- Recruiters/Careers

Indian Institute of Technology Delhi
An institution of eminence, भारतीय प्रौद्योगिकी संस्थान दिल्ली, hauz khas, new delhi-110016, india, publish date: october 28, 2021, online certificate programme on "cybersecurity: foundations and pragmatics".
Share this on

To Know More : Click Here

2nd online CEP programme on "Executive Programme in Product Innovation and Design Thinking for Business Growth".

Department of Management Studies, IIT Delhi launches 2 Year Executive MBA Program.

IIT Delhi Takes Multiple Initiatives for the Empowerment of Students with Disabilities

IIT Delhi launched a Workshop on PCB Fabrication.

AFMS and IIT Delhi Sign MoU for Collaborative Research and Training

UQ-IITD Academy of Research Seminar Series, scheduled on Friday 26 April 2024

5th online CEP programme "Executive Programme in Operations Management and Analytics"

2nd Online CEP Programme "Executive Programme In Brand Management"

SUMMER RESEARCH FELLOWSHIP PROGRAMME 2024 FOR M.TECH. /M.E. STUDENTS AT INDIAN INSTITUTE OF TECHNOLOGY DELHI

QS World University Rankings by Subject 2024: IIT Delhi Ranked Among the Top 100 World Institutions in 08 Specific Subject Areas; Features Among Top 50 in Engineering and Technology

online CEP programme titled "Executive Programme in Robotics"

International Women's Day: Talk titled "Rise to Shine: Embracing Challenges for Success” Organised

03rd online CEP programme titled "Machine Learning and Deep Learning"

Antara Senior Care Signs MoU with IIT Delhi to Design Innovative Mobility-aid Solutions for Seniors

UQ-IITD Research Academy Seminar Series- Ms.Sushmita Ghosh

IPHE Outreach Event

Israel Aerospace Industries and IIT Delhi Sign CSR Agreement to Collaborate on Applied Research

IITD Prelim Quiz

IIT Delhi’s Department of Humanities and Social Sciences to Offer a New Academic Program ‘M.A. in Culture, Society, Thought’
02nd online CEP programme titled "Fundamentals of EVs and Charging Infrastructure"

06th online CEP programme titled "Advanced Programme in Electric Vehicle (EV) Technology"

9th online CEP programme titled "Project Management"
A Twist in the Saga of Fractals

IITD Poster Competition

Completion of Sequencing of 10000 Genomes of Indian Population: IIT Delhi Scientists Make Significant Contribution

Bill Gates Inspires IIT Delhi Students, Encourages Them to Apply Their Skills to Global Challenges

03rd online CEP programme titled "Executive Management Programme in Advanced Strategic Management"

07th online CEP programme titled "Design Thinking and Innovation"

LC3-TRC Africa Project Mentored by IIT Delhi Researchers Inaugurated at Kenya’s Meru University of Science and Technology

Undergraduate Summer Research Fellowship 2024 at IIT Delhi

R Systems International Ltd. and IIT Delhi Partner to Set Up a Centre of Excellence on Applied AI for Sustainable Systems

Transformative Leadership in STEMM (TLS) Workshop for Ph.D. Scholars from SC/ST Community Held at IIT Delhi

Prime Minister, Shri Narendra Modi, Inaugurates Two Academic Complexes at IIT Delhi

UQ-IITD Research Academy publicity for July 2024 admissions

UQ-IITD Research Academy Seminar Series- Ms.Bernadette Huber

online CEP programme titled "AI/ML for Industry Bootcamp"

Faculty Research Awards

IIT Delhi Launches a New Academic Program ‘M.Sc. in Biological Sciences’; Admissions Through JAM

In Pictures: IIT Delhi Celebrates 75th Republic Day

GRIP: IIT Delhi Students Visit Uttarakhand Villages; Will Develop Tech Solutions to Address Issues Faced by Local Population

IIT Delhi Foundation Day Institute Lecture

UQ-IITD Research Academy Seminar Series - Prof. Tanusree Chakraborty

National Service Scheme (NSS) of IIT Delhi Launches an In-house-developed Mobile App, Making Volunteering Much More Accessible

Bharat Electronics Ltd., FITT-IIT Delhi Sign MoU

Call for Applications: Transformative Leadership in STEMM (TLS) Workshop for Advanced PhD Scholars from SC/ST community.

28th Inter IIT Staff Sports Meet: IIT Delhi Wins General Championship (Men's)

IIT Delhi Newsletter - December 2023 Issue

online CEP programme titled "Executive Programme for Tech Product Management"
Season of Alumni Reunions at IIT Delhi Begins

Request for Proposal: Empanelment of Service providers for the Online CEP Programmes at IIT Delhi

online CEP programme titled "Executive Certificate Programme in Digital Marketing"

Placement Season 2023-24: IIT Delhi Students Receive Around 1050 Job Offers in Phase 1

online CEP programme titled "Chief Technology Officer Programme"

UQ-IITD Academy of Research Seminar Series - Ms.Neha Singh

2nd online CEP programme titled "Executive Programme in Healthcare Entrepreneurship and Management"

Consultative Brainstorming Meeting: ‘DST's Roadmap Towards India’s Net Zero Targets Through Carbon Capture, Utilization, and Storage’

Shortlisting Criteria for PhD admissions at CRDT

Kaspersky, IIT Delhi Partner to Foster Local Cybersecurity Talent Development in India

04th online CEP programme titled "Certification in Quantum Computing and Machine Learning"

IIT Delhi Faculty Combines Technology with Art Forms to Offer a Holistic Educational Experience to Materials Engineering Students

Placement Season Begins at IIT Delhi- Students Receive 480 Job Offers By the End of December 1

Over 30 High School Girls Successfully Complete Second STEM Mentorship Program Launched by IIT Delhi

BioTEX-2023 : Organized by the CBME, Indian Institute of Technology (IIT) Delhi at New Delhi from 27th November-1st December 2023

Shortlisting Criteria and List of candidates shortlisted for interview for the MSR Program in the Department of Materials Science and Engineering for the session 2023-24, II Semester

Short-listing criteria for admission to Ph.D. in Materials Science and Engineering for the year 2023-2024 (2nd Semester)

IIT DELHI ANNOUNCES M. TECH. IN ENERGY TRANSITION AND SUSTAINABILITY FOR THE ABU DHABI CAMPUS: Last date extended to November 30, 2023

Masters in Energy Transition and Sustainability at IIT Delhi Abu Dhabi Campus

3rd online CEP programme titled "Advanced Certification in Data Science and Decision Science"

UQ-IITD Academy of Research Seminar Series - Ms. Simran Agarwal

online CEP programme titled "Hands-on Training on "Semiconductor Device Technology: Fabrication and Characterization"

QS Asia University Rankings 2024

In pictures: 16th Open House for School Students at IIT Delhi

IIT Delhi Showcases Cutting-Edge Research to School Students at the Open House 2023

IIT Delhi Faculty Prof. Shilpi Sharma and Prof. Anurag Singh Rathore Win Tata Transformation Prize; Recognized for their Cutting-Edge Solutions to Food Security and Healthcare

Artificial Intelligence and Machine Learning for Industry

Hon'ble Vice-President of India, Shri Jagdeep Dhankhar, Visits IIT Delhi and Interacts with Students

In pictures: Hon'ble Vice-President of India, Shri Jagdeep Dhankhar, Visits IIT Delhi and Interacts with Students

UQ-IITD Academy of Research Seminar Series - Dr. Zyta Ziora

Tehri Hydro Development Corporation India Limited (THDCIL) and IIT Delhi Ink MoU for Transformative Research and Development Initiatives

DAKSH Centre of Excellence for Law and Technology at IIT Delhi Launches a Book Titled ‘Technology and Analytics for Law and Justice’

Invitation of Applications for the post of Director. IIT Bombay

8th online CEP programme titled "Project Management"

37th Inter-IIT Aquatics Meet: IIT Delhi Wins Aquatics Men's Championship for First Time

online CEP programme titled "Executive Programme in Human Resource Management"

online CEP programme titled "Advanced Certification Programme in Persuasive UX Strategy"

IIT Delhi and HORIBA India Jointly Hold Tech Symposium on ‘Solutions for Semiconductor Industry’

In pictures: Birth Anniversary of Mahatma Gandhi and Shri Lal Bahadur Shastri Celebrated at IIT Delhi

Vice President of the Dominican Republic Visits IIT Delhi; MoU Signed

UQ-IITD Academy of Research - Special seminar on Fire safety engineering

SWACHHTA PAKHWADA

First of Its Kind ‘Medical Cobotics Centre (MCC)’ Inaugurated in New Delhi; to Foster Innovation in Healthcare

IIT Delhi Faculty Elected as INSA Fellows and Associate Fellows 2023

Amrit Kaal Vimarsh on Viksit Bharat@2047: Dr. R. Chidambaram Delivers Lecture

UQ-IITD Academy of Research Seminar Series - Ms. Deepti Mishra

IIT Delhi Newsletter - August 2023 Issue

online CEP programme titled "Certificate Programme in Project Management: Theory & Practice"

IIT Delhi’s Prof. Dipti Ranjan Sahoo Wins Shanti Swarup Bhatnagar Prize for Science and Technology 2022

IIT Delhi and EXL Enter into MoU to Work Towards Empowering Women Entrepreneurs Through Digital and Financial Literacy

UQIDAR information session scheduled on 12th and 13th of September

Join a world-leading joint PhD program with a generous scholarship

6th online CEP programme titled "Design Thinking & Innovation"

2nd online CEP programme titled "Executive Management Programme in Advanced Strategic Management"

5th online CEP programme titled "Advanced Programme in Electric Vehicle (EV) Technology"

First Batch of UQIDAR Students Receive Joint PhD Degree at 54th IIT Delhi Convocation Ceremony

UQ-IITD Academy of Research Seminar Series - Dr. Abdullah Mohammed Bareen

In pictures: IIT Delhi Celebrates Independence Day; Employees Awarded for Exemplary Contribution to Institute

IIT Delhi's School of Public Policy Successfully Places its Inaugural Masters in Public Policy Batch

Workshop on MedTech and Healthcare Ecosystem for Upcoming IIT Delhi - Jhajjar Campus Organised

2357 Graduating IIT Delhi Students Receive Degrees and Diplomas at the 54th Annual Convocation Ceremony
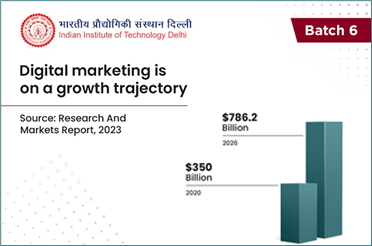
online CEP programme titled "Certificate Programme in Digital Marketing (Batch 6)"

online CEP programme titled "Certificate Programme in Project Management (Batch 7)"

2nd online CEP programme titled "Professional Certificate Programme in FinTech"

IIT Delhi to Hold its 54th Convocation on August 12; Eminent Virologist Dr. Gagandeep Kang to be the Chief Guest

Executive Vice President and Finance Minister of Venezuela Visits IIT Delhi
_1691059736.jpg)
3rd online CEP programme titled "Certification in Quantum Computing and Machine Learning"

online CEP programme titled "Fundamentals of EVs and Charging Infrastructure"

IIT Delhi Recognised as “GATI Achiever” for Promoting Women in STEM

IIT Delhi Takes Multiple Initiatives Towards Implementing NEP 2020

IIT Delhi Alumni Awards 2023

Advertisement inviting for the post of Director IIT Jodhpur

UQ-IITD Academy of Research Seminar Series - Dr. Vallari R. Chourasia

MoU for IIT Delhi-Abu Dhabi Campus Signed

IIT Delhi Student Plays in 2023 ICF Dragon Boat World Cup; Team Wins Bronze

IIT Delhi Successfully Organizes Open House for JEE (Advanced) 2023 Qualified Female and PwD Candidates

US Ambassador to India Praises IIT Delhi Ph.D. Scholar for Her Research

In pictures: International Yoga Day Celebrated at IIT Delhi

IIT Delhi Research Scholar Anchal Sharma Makes Research Presentation Before Indian PM and US First Lady at NSF

IIT Delhi is organising an Open House for JEE (Advanced) 2023 qualified Female and Pwd Candidates on June 24, 2023 (Saturday)

2nd online CEP programme titled "Machine Learning and Deep Learning"

online CEP programme titled "Applied Data Science using Machine Learning & Artificial Intelligence"

UQ-IITD Academy of research seminar series

IIT Delhi Organises Workshop on Mental Wellness and Stress Management

NIRF India Rankings 2023- IIT Delhi Among Top Three Educational Institutions in India

5th online CEP programme titled "Design Thinking and Innovation"

UAE’s Economy Minister Visits IIT Delhi; Delivers Talk

IIT Delhi Celebrates World Telecommunication Day; India’s G20 Sherpa, Mr. Amitabh Kant, Delivers Annual Bharti Lecture

Result of selected students for PG SRPF 2023

Haryana School Students Get a Glimpse of World-Class Research Facilities at IIT Delhi

on-campus CEP programme titled "Business Analytics for Young Managers"

"Pension Adalat" for IIT Pensioners on 17.05.2023

Declaration of result of SRFP- 2023

IIT Delhi Establishes "Bhandari-Sankhla Chair" in the Area of Clean Energy

2nd online CEP programme titled "Executive Programme in Advanced Project Management"

Result of MBA and MBA (Telecom) Programme 2023-2025

IIT Delhi Newsletter - April 2023 Issue

Apply for Sumant Sinha Sustainability Leadership Award 2023

5th batch of PGDEx- VLFM (Visionary Leaders for Manufacturing)

RESULT OF SUMMER RESEARCH FELLOWSHIP PROGRAMME -2023 WILL BE DECLARED BY THE SECOND WEEK OF MAY, 2023

MechAnalyzer Software to Help Engineering Students Learn Concepts of Mechanisms; FITT-IIT Delhi and SVR InfoTech Sign MoU for Sale and Tech Support

Venus Chair Established at IIT Delhi to Support Teaching and Research & Development in the Area of Fibrous Air Filters

CRF, IIT Delhi organises DST- STUTI Workshop in Collaboration with NIT Warangal
Advt. No.- Mission Mode (DR)(4)/2023 is hereby extended upto 12.05.2023 till 05:00 PM

6th online CEP programme titled "Data Science and Machine Learning"

Deadline of Submission of Online Applications for SRFP - 2023 extended upto 19.04.2023 till 11:59 PM

SUMMER RESEARCH FELLOWSHIP PROGRAMME 2023 FOR M.TECH. /M.E. STUDENTS AT IIT DELHI

2nd online CEP programme titled "Advanced Certification in Data Science and Decision Science (Batch 2) "

IIT Delhi’s Two-Day Annual Career Fest ‘Pravritti 2023- Expanding Horizons’ to Begin on April

2nd online CEP programme titled "Executive Programme for Advanced Product Management (Batch 2)"

2nd online CEP programme titled "Design Thinking for User Experience"

"SIRe Symposium 2023" dated 12th April, 2023

4th online CEP programme titled "Advanced Programme in Electric Vehicle (EV) Technology"

online CEP programme titled "Certificate Programme in Sales & Marketing"

IIT Delhi, HORIBA India Sign MoU to Support Students with Disabilities

online CEP programme titled "Executive Programme in Operations Management And Analytics"

online CEP programme titled "Executive Programme in Product Innovation & Design Thinking for Business Growth"

IIT Delhi Launches an Inter-Disciplinary M. Tech. Programme in Robotics

QS World University Rankings by Subject 2023: IIT Delhi Among the Top 50 Institutions in the World in Engineering & Technology with 48th Rank

6th online CEP programme titled "Project Management"

MoS for Education Dr. Subhas Sarkar Inaugurates Unnat Bharat Abhiyan's "UNNATI Mahotsav and Expo" at IIT Delhi
Advt. No.- Mission Mode (DR)(2)/2023 is hereby extended upto 27.03.2023

In pictures- Hon'ble Australian PM Mr. Anthony Albanese's Visit to IIT Delhi on March 10, 2023

Australian Prime Minister Witnesses State-of-the-Art Technologies Developed by IIT Delhi.

Hon’ble Australian Prime Minister Mr. Anthony Albanese Visits IIT Delhi; Addresses Students

IIT Delhi’s Three-day Annual Science, Technology and Management Festival “Tryst 2023” Kicks Off
Advt. No.- Mission Mode (DR)(1)/2023 is hereby extended upto 17.03.2023

IIT Delhi Alumnus Alok Aggarwal Endows Chair for Research in ESG (Environmental, Social, and Governance) Area

IIT Delhi to Develop Smart Monitoring System to Ensure Safety of Persons Working at Height

Unnat Bharat Abhiyan Organises Special Orientation Workshop

ReNew CoE organised event on 1st March 2023 , 5 - 6:30 pm

IIT Delhi Scientists Design Time Capsule for the Department of Posts

UQIDAR information session webinar scheduled on 24th February

Advertisement inviting applications for the post of Director, IIT Goa

IIT Delhi Inaugurates Second Batch of STEM Mentorship Programme for High School Girls

online CEP programme titled " Certificate Programme in Design Thinking and Innovation"

CSM Technologies Sign MoU with IIT Delhi to Establish Annual Scholarship

IIT Delhi Newsletter - January 2023 Issue

65th Foundation Day of IIT Delhi Celebrated; Faculty Research Awards 2022 Presented on Foundation Day

online CEP Programme "Executive Programme in Healthcare Entrepreneurship and Management"

Online CEP Programme "Digital Marketing"
Mobility for All: Continental with IIT Delhi Develop A Solution for Visually Impaired To Access Public Buses

Indian & Foreign Languages Learning Programme

Annual Summer Faculty Research Fellow Programme (SFRF-2023)

27th Inter-IIT Staff Sports Meet: IIT Delhi Wins Overall Championship and General Championship (Men)

Advertisement inviting applications for the post of Director, IIT Guwahati

Energy Systems, Security and Net Zero Emissions

IIT Delhi Placement Drive 2022-23: Students Receive Record Number of Job Offers Up to December 15

IIT Delhi and University of Helsinki, Finland, Sign MoU for Academic Cooperation; Aims to Contribute to Solving Air Quality and Climate Change Challenges in India

IIT Delhi Showcases Over 80 Technologies Developed by its Researchers at 4th Industry Day

IIT Delhi to Organise 4th Edition of Industry Day on December 10, 2022

Placement Season at IIT Delhi for Academic year 2022-23 Commences

CRDT, IIT Delhi Organises International Symposium on Circular Economy Solutions for Plastics and Microplastics jointly with University of Eastern Finland (UEF)

IIT Delhi Newsletter - November 2022 Issue

National Credit Framework (NCrF) Awareness Workshop(North Zone)

Four Startups led by IIT Delhi Students Win a Grant of Rs 50 lakh Each Under Endowment Nurture Fund Initiative

Advertisement inviting applications for the post of Director, IIT IIT Kanpur and IIT (ISM) Dhanbad

IIT Delhi Holds 53rd Annual Convocation Ceremony; 2100 Graduating Students Awarded Degrees and Diplomas

IIT Delhi to Hold its 53rd Annual Convocation Ceremony on November 05, 2022


"Advanced Programme in Electric Vehicle (EV) Technology".

Online CEP Certificate Programme "Project Management"

Rural Technology Action Group (RuTAG) at IIT Delhi Transfers Two Technologies to Four African Nations

Department of Telecommunications R&D Centre C-DOT and IIT Delhi Sign MoU for Cooperation in Various Emerging Areas of Telecom

Quantum Computing & Machine Learning

Certificate Programme in FinTech

Workshop on Addressing Air Quality Challenges in Delhi-NCT Held at IIT Delhi; Team Sweden, IIT Delhi Identify Possible Areas of Joint Intervention

"Seminar on "Polymers in Ionic Liquids" by Prof. Arun Yethiraj

In Media- IIT Delhi Diamond Jubilee Celebrations Closing Ceremony

Supreme Court Judge Hon’ble Justice D.Y. Chandrachud to Deliver Inaugural Talk for the Office of Diversity and Inclusion at IIT Delhi

Hon’ble Union Education Minister, Shri Dharmendra Pradhan Addresses IIT Delhi Diamond Jubilee Celebrations Closing Ceremony

IIT Delhi Diamond Jubilee Celebrations Closing Ceremony- Director Prof. Rangan Banerjee's Speech

IIT Delhi Diamond Jubilee Celebrations Closing Ceremony- Hon'ble President of India, Smt. Droupadi Murmu's Speech

Hon’ble President of India, Smt. Droupadi Murmu Graces IIT Delhi Diamond Jubilee Celebrations Closing Ceremony

IIT Delhi Newsletter - August 2022 Issue

FSAE Italy 2022- IIT Delhi’s Automobile Club AXLR8R Formula Racing Secures First Position in Cost and Manufacturing Event

Office of Career Services, IIT Delhi Unveils its Official Logo

Union Minister Shri Piyush Goyal Inaugurates Public Systems Lab at IIT Delhi Established in Partnership with UNWFP

IIT Delhi’s Technology Innovation Hub IHFC Gets 12 Projects Under DST-NSF Joint Research and Development Program

Over Three Thousand DSEU Students Visit IIT Delhi for Experiential Learning

Har Ghar Tiranga

Sumant Sinha Sustainability Leadership Award 2022

Certificate Programme in Machine Learning and Deep Learning
_1659327288.jpg)
IIT Delhi Organises Academic Outreach Day for Students and Faculty of Haryana Govt. Technical Universities and Colleges

Certificate Programme in Digital Marketing

Executive Programme in Startup Bootcamp

NIRF India Rankings 2022- IIT Delhi Achieves 2nd Rank in Engineering; Jumps to 4th in Management; Features Among Top 3 Research Institutes

IIT Delhi in Association with Prasar Bharati to Host DD-Robocon 2022

IIT Delhi Alumni Parul and Alok Mittal Join League of IIT Delhi Endowment Fund Founders

Census Data Workstation Inaugurated at IIT Delhi

India’s Best Colleges 2022: IIT Delhi #1 Engineering Institute

mPRAGATI, a One Stop MedTech Technology Development Facility at IIT Delhi Under ICMR-Medical Device and Diagnostics Mission Secretariat, Unveiled

Empanelment of retired officers as an Inquiry Officers for conducting Departmental Inquiry - reg.

First Batch Successfully Completes IIT Delhi’s STEM Mentorship Program for High Schoolgirls

School students showcase promising prototypes they built at Change.Makers summer boot camp organised by IIT Delhi

IITs in Delhi, Bombay and Kanpur Offer Internship and Sponsored M. Tech. Programmes to Students from Ladakh

IHFC, TIH of IIT Delhi, Celebrates its 2nd Anniversary; Announces Call for Proposal in Areas of Autonomous Vehicles, Nano Robotics, Block Chain for Applications in Robotics

Samsung Launches ‘Solve for Tomorrow’, an Innovation Contest for India’s Youth to Crack Real-World Problems; FITT at IIT Delhi to be the Knowledge Partner

QS World University Rankings 2023- IIT Delhi Achieves an Improved Overall Rank of 174 Globally

IIT Delhi Student Wins Coveted TCS CodeVita Season 10
IIT Delhi Study Reveals Mechanisms Driving SARS-CoV-2 Evolution in Humans

DEPARTMENT OF HUMANITIES AND SOCIAL SCIENCES, IIT DELHI --- Indian & Foreign Languages Learning Programme

Result- UG - Summer Research Fellowship Programme - 2022 ( IN CONTINUATION TO THE LIST OF STUDENTS PUBLISHED on 13th May, 2022 )

CEP programme titled "Executive Programme for Advance Product Management"

Technology Innovation Hub of IIT Delhi (IHFC) Signs MoU with the Council for the Indian School Certificate Examinations (CISCE)

CEP programme titled "Advance Programme in E-Vehicle Technology"

Result - UG Summer Research Fellowship programme (SRFP 2022)

3rd online CEP programme on "Design Thinking and Innovation"

Monumental National Flag Hoisted at IIT Delhi

ITC Inks Pact with IIT Delhi to Carry Out Collaborative Research in STEM Areas

IIT Delhi to Organise Do-It-Yourself (DIY) Summer Boot Camp for School Students

4th online CEP programme on "Project Management"
_1651059243.png)
4th online CEP programme on "Data Science and Machine Learning"

Empanelment of Advocates/Law Firms with IIT Delhi for Legal matters.

Did Climate Change Cause Ancient Civilizations to Collapse? 08thIIT Delhi SciTech Spins Lecture to Explain

Executive Management Programme in Strategic Management

IIT Delhi to Organize Career Fest ‘Pravritti 2022- Reshaping Chances to Choices'

First Online CEP programme on "Quantum Computing & Machine Learning"

PG Admission including Ph.D. - Last date for submission of online application and application fee has been extended to April 17, 2022 (4 pm). No further extension will be made.

SIRe Symposium 2022 on 13th, April, 2022 onwards 10:00 am (Hybrid Mode)

Executive Programme in Advanced Project Management

Operations Management & Analytics

Finance for Non-Finance Executives

Tryst 2022: IIT Delhi’s Annual Science and Technology Festival from April 15

QS World University Rankings by Subject 2022 - Five IIT Delhi Academic Programmes in Top 100

IIT Delhi, Delhi Jal Board Sign MoU to Address Water Security Issues Faced by NCT of Delhi

Executive Programme in Supply Chain Management & Analytics (EPSCMA)

World Class Indoor Sports Complex Built with Alumnus Saurabh Mittal's Support Inaugurated at IIT Delhi

2nd online CEP Certificate programme titled Executive Management Programme in Entrepreneurship Development (EMPED)

Fabiosys Innovations, an IIT Delhi Startup, Develops Technology to Manufacture Extremely Affordable and Highly Effective Antiviral Fabric

What makes a virus deadly? IIT Delhi SciTech Spins Lecture for High Schoolers to Explain

Prof. Dilip T. Shahani, Honorary Professor, IIT Delhi Honoured with Padma Shri
COVID-related Research & Development Work by Centrally Funded Technical Institutes (CFTIs), Ministry of Education, Government of India - February 2022

Advanced Certification in Data Science and Decision Science

Undergraduate Summer Research Fellowship Programme 2022 at IIT Delhi

IHFC, Technology Innovation Hub of IIT Delhi, Collaborates with US’ National Science Foundation for Research in Cobotics, AI

FITT, IIT Delhi Signs Agreement with SVR InfoTech for RoboAnalyzer Software

Webinar on "What's next in computing: when classical and quantum computing meet" by Dr. Mukesh V. Khare, Vice President, Semiconductor & Cloud, IBM Research, USA on March 04 (Friday) 2022, 8:30 AM IST

HORIBA India, IIT Delhi Join Hands to Establish Research Center at the Institute’s Chemistry Department

Troop Comforts Ltd Signs MoU with IIT Delhi to Develop Smart Protective Clothing for Indian Security Forces
Prof. Rangan Banerjee Takes Charge as New Director of IIT Delhi

SciTech Spins Lecture: School Students to Learn About Role of Imaging in Advancing Science and Technology
IIT Delhi Launches an Interactive Website of IIT-PAL to Help High School Students Prepare for Competitive Exams

IIT Delhi Researchers Develop High Efficiency, Shadow-less, Portable Solar PV Towers for Power Generation

Summer Faculty Research Fellow Programme 2022 (SFRF-2022) (During June- July 2022)

Alumnus Dr. Amit Sinha Gifts Rs. 10 Crore Endowment to IIT Delhi

IIT Delhi Climate Action Plan

IIT Delhi Celebrates 64th Foundation Day

Gender Advancement for Transforming Institutions (GATI)

5th SciTech Spins Lecture: School Students to Explore World of Elementary Particles

IIT Delhi Celebrates 73rd Republic Day

IIT Delhi Professor Dr. Dilip T Shahani to be conferred with Padma Shri Award 2022

Faculty Research Awards 2021

PMRF Symposium

IIT Delhi Alumnus Pledges Rs. 11 Cr to IIT Delhi Endowment Fund

3rd online Certificate Programme on "Digital Marketing"

2nd online Certificate Programme in "Advanced Programme in E-Vehicle Technology"

IIT Delhi Alumnus Pledges Rs. 10 Crores to Institute’s Endowment Fund

IIT Delhi Launches STEM Mentorship Program for Schoolgirls

IIT Delhi Sets up “Pillay Chair Professor” for Research in Machine Learning, VLSI Design and Sensors

IIT Delhi Students Receive Record Number of Job Offers Up to December 15 of Placement Drive 2021

SciTech Spins 4th Lecture: School Students to Learn About Mysteries of Universe from IIT Delhi Scientists

Indian Air Force Signs MoU with IIT Delhi To Accelerate Indigenisation Efforts

IIT Delhi’s State of the Art Research & Innovation Park Wins Prestigious Façade Project of the Year Award 2021

Brain Storming Conclave on Atmanirbhar North East through S&T Interventions at Cotton University, Guwahati, Assam December 21–22, 2021

IntelliSmart & IIT Delhi collaborate to develop next generation Smart Grid technology solutions & capabilities

3rd Certificate Programme in "FINANCE FOR NON FINANCE EXECUTIVES"

IIT Delhi Celebrates International Day for Persons with Disabilities

A Vibrant Start to Placement Season at IIT Delhi

IIT Delhi Collaborates with National Law University Delhi for Ushering in Tech-empowered Justice System

IIT Delhi and Business Sweden - The Swedish Trade and Invest Council Sign MoU for Clean Air and Green Energy Collaborations

Placement Season to Commence Virtually at IIT Delhi from December 01, 2021

ITC, IIT Delhi Discuss Opportunities for Collaboration

Neilom Prize 2020-21: Recent Graduates of IIT Delhi Awarded for their Work in the Field of Assistive Technology
‘Why did the Titanic Sink?’ 3rd SciTech Spins Lecture by IIT Delhi to Explain This and Many More Questions to School Students

Technology Innovation Hubs of IIT Delhi and IIIT Delhi Sign MoU to set up India’s First Medical Cobotics Centre

At 52nd Convocation of IIT Delhi Over 2000 Students Awarded Degrees

IIT Delhi to Hold its 52nd Convocation on November 13th, 2021

Alumnus Mr Anant Yardi to Contribute USD 10 Million to IIT Delhi

State-of-the-art Laboratories Inaugurated at IIT Delhi’s Centre Focusing on Electric Vehicle Technologies

IIT Delhi Wins Clarivate India Research Excellence- Citation Awards 2021

IIT Delhi, AIIMS New Delhi Jointly Establish Centre for Advanced Research and Excellence in Disability & Assistive Technology (CARE-DAT), a Centre of Excellence

IIT Delhi Establishes Prof N K Jha Chair for Research in Chemistry

IIT Delhi’s School of Artificial Intelligence to Start ‘M.Tech in Machine Intelligence & Data Science (MINDS)’

Applications are invited for appointment to the post of Director, Indian Institute of Technology (llT) Bhubaneswar

Advertisement inviting applications for the post of Director, IIT Palakkad, IIT Tirupati, IIT Dharwad, IIT Bhilai, IIT Goa and IIT Jammu

IIT Delhi to Teach School Students ‘How Powerful Computers Can Help in Providing Insights into Real-Life Phenomena’

IIT Delhi Announces Scholarships and Seed Funding Programs to Mark 2nd Anniversary of its Alumni Endowment Fund

IIT Delhi Launches New UG Programme ‘B. Tech. in Energy Engineering’; JEE (Advanced) Qualified Students Eligible

Alumnus Mohit Aron Gifts USD 1 Million to IIT Delhi’s Computer Science and Engineering Department

IIT Delhi Establishes SMITA Research Lab Centre of Excellence in Smart Textiles

Industrial Design, Innovation & Entrepreneurship

B.Tech. Students of NIT Sikkim to be Eligible for Direct Admission to IIT Delhi’s PhD Programmes

JK Paper Signs MoU with IIT Delhi to Set Up JK Paper Centre of Excellence in Paper and Packaging

3rd online Certificate Programme in "Data Science & Machine Learning"

2nd online Certificate Programme in "Design Thinking and Innovation"

Advance Certificate Programme in "Operation Management & Analytics"

Certificate Programme in Project Management

Certificate Programme in "Human Resource Management"

IIT Delhi’s Over Rs 500 Cr State-of-the Art ‘Central Research Facility’ Now Open for Researchers from Across Country

IIT Delhi Establishes Centre of Excellence (CoE) on Quantum Technologies

Optics and Photonics Centre of IIT Delhi launches an outreach initiative named "Optics Learning Centre"

IIT Delhi Establishes Alumnus Endowed “Shri. G.K. Chandiramani Chair for Cyber Security”

Advanced Electrical Characterization Facility Inaugurated at IIT Delhi

IIT Delhi to Start Bachelor of Design (B.Des.) Programme from Academic Session 2022-23

Sumant Sinha Sustainability Leadership Award-2021

IIT Delhi Launches Sci-Tech Spins - A Series of Weekend Seminars & Laboratory Demos for High School Students

Rapid Antigen Testing Facility for COVID-19 Inaugurated at IIT Delhi
DAKSH Centre of Excellence (CoE) for Law & Technology, IIT Delhi Releases Report on Six High Court Websites
IIT Delhi Launches Fundraising Campaign Going Further, by Giving Back

"ComIN21 Asian Voices in Pandemic" conference organized by the Department of Design, IIT Delhi in December 2021

ARIIA Rankings

Seminar on Benefits and Challenges in the Next Decade of Semiconductor Innovation by Dr. Randhir Thakur, Senior Vice President, Intel, USA on 19.08.2021 at 10:00 am

Unnat Bharat Abhiyan Announces Results of Regional Level Poster and Video Competition for COVID-19 Awareness

75th Independence Day celebration

Vipula and Mahesh Chaturvedi Foundation Signs MoU to Attract Outstanding Talent to IIT Delhi

An Institute Lecture on "Ways to a Carbon-free world" by Mr. Sumant Sinha, Chairman and Managing Director, ReNew Power

Certificate Programme in "Business Analytics and Optimisation"

National Health Authority and Indian Institute of Technology Delhi join hands to scale high-potential healthcare innovations

Attention 2020 Entry UG students: Final list of UG students (2020 Entry) for Change of Programme at the end of 1st Year

IIT Delhi Establishes Chairs to Support Research in Microelectronics & VLSI Design and Geotechnical & Geo-Environmental Engineering

Online Teaching for Semester I 2021-22

Energy Systems And Carbon Neutral Economy

Healthcare at Scale: Inspiration from Traditional AYUSH Medicine Systems of India

Entrepreneurship Innovation and Design for Catalysing Rural Economy
IFFCO Signs MoU with IIT Delhi for Innovative & Collaborative Projects to Bring Labs to Farms

IIT Delhi Alumni Endow Indu Shrivastava & Serla Singh Chair Professor in Artificial Intelligence

Prime Minister's event on completion of 1 year of NEP 2020 on 29th July 2021

IIT Delhi Moves Towards Implementation of National Education Policy 2020

Covid-19: What the pandemic has taught us and the way forward lecture by Prof./Dr. Randeep Guleria, Director, All India Institute of Medical Science (AIIMS), Delhi

National Workshop on Solid Waste Management July 30-31, 2021

IIT Delhi Establishes Manish Singhal Chair to Promote Teaching and Research in the Area of Smart Textiles

Height of Resilience : IIT- Delhi alumnus fights of COVID-19, scales Everest

IIT Delhi and IIIT-D come together for research in areas of mutual interest

Supreme Court Judge Mr. Justice S. Ravindra Bhat inaugurates UJF Lab Facility on AI for Judiciary at IIT Delhi
IIT Delhi Establishes Jaswinder and Tarvinder Chadha Chair in Data Analytics

IIT Delhi Launches Grassroots Innovation Programme (GRIP) for Students

Innovation Hub for Cobotics at IIT Delhi Completes One Year Successfully

IIT Delhi Launches New PG Programme Master of Public Policy

IIT Delhi Establishes Professors Narendra and Chandra Singhi Chair Endowed by Alumnus

IIT Delhi to Establish Transportation Research and Injury Prevention Centre

QS World University Rankings 2022: IIT Delhi Ranking Goes Up

IIT Delhi Launches a New PG Programme M. Tech. in Electric Mobility

PAID COVID VACCINATION CAMP - COVISHIELD - 8TH JUNE, 2021 (Tuesday), L.H.C., IIT CAMPUS - EMPLOYEES (FACULTY & STAFF)
IIT Delhi to Establish Department of Energy Science and Engineering: New UG Programme B.Tech. in Energy Engineering To Be Offered from This Year
Covid-19: IIT Delhi collaborates with Delhi Government to improve oxygen infrastructure and supply chain management in Delhi
IIT Delhi, NLU Delhi Explore Partnership Opportunities in Technology and Law Field

IIT Delhi to Create New Centre to Synergize and Boost R&D Activities in Optics and Photonics Field

Short-listing criteria for admission to Ph.D. in Materials Science and Engineering for the year 2021-2022 (I Semester) and List of Shortlisted candidates for PhD Interview
Short-listing criteria for admission to MS(R) in Materials Science and Engineering for 2021-22 (I Semester) & List of Shortlisted candidates for MS (R) Interview

Online teaching for Semester II, 2020-21

Result of Summer Research Fellowship Programme

REPORTING AND MONITORING OF COVID POSITIVE CASES

Invitation of Applications for the post of Director - Indian Institute of Technology, Madras
ISRO to Support Eight Joint Research Projects
Online SRFP 2021 For M.TECH. /M.E. Students

Notice Regarding Selection Procedure to be undertaken of various posts

Summer Research Fellowship Programme 2021
IIT Delhi Develops Handheld Device for Early and Rapid Diagnosis of Dengue

IIT Delhi Reduces its Carbon Footprint by More than 50%

IIT Delhi alumnus endows "Ramchandran Jaikumar Chair for Decision Sciences"

IIT Delhi to Establish State-of-the-Art Atmospheric Observatory on its Campus in Sonipat
Type the keyword(s) you are looking for, like... undergraduate programs latest research.

Post Graduation Certification in Cyber Security
Amplify growth in the ever-growing digital age that sparks the volume of attacks and nature of cyber threats. Now eradicate these prominent cyber heists with India's leading IITs, IIT Palakkad- Post Graduation Certification in Cyber Security . This new age cyber security programme is opportune; ever-increasing cyber threats to businesses and government bodies. Professionals must know their way around cybersecurity measures and develop a plan to defend their businesses, online organisations, and personal devices. The Post Graduation Certification in Cyber Security gives exposure to hands-on practices in malware analysis by using sandboxes for static and dynamic analysis. Learn in-depth to analyse network traffic, network, and system logs using security information and events monitoring systems. The holistic pedagogy includes technical and policy aspects of cyber security, insight on cryptography, malware analysis, network traffic analysis, emerging threat analysis and much more.
- Program name: Post Graduation Certification in Cyber Security
- Service Provider: Jaro Education
- Programme Chair: Dr. Satyajit Das
- Guest Industry Expert: Dr.Vishal Saraswat
- Programme Faculty: Dr. Srimanta Bhattacharya
- Brochure: Download
- Contact: [email protected]

Indian Institute of Technology Palakkad Kanjikkode | Palakkad Kerala | Pin: 678623
Copyright ©2023 Indian Institute of Technology Palakkad. All Rights Reserved.
Executive Post Graduate Certification in Cyber Security and Ethical Hacking
2,074 Ratings
This Executive Post Graduate Certification in Ethical Hacking is designed to provide professionals with the skills and techniques they need to kick starting their careers in the field of ethical hacking. Also, get a chance to win big with our course! The top 2 performers from each batch may get a fellowship worth Rs. 80,000, plus the opportunity to showcase their startup ideas and secure incubation support of up to Rs. 50 Lakhs for their startup from iHUB DivyaSampark, IIT Roorkee. Undergraduate students Read More.. are eligible for the Fellowships.
In collaboration with
Learning Format
Online Bootcamp
Live Classes
Executive PG
Certification
Campus Immersion
IIT Roorkee
Hiring Partners

About Program
This Executive Post Graduate Certification Program in Ethical Hacking by iHUB DivyaSampark, IIT Roorkee, offers 10 modules and a career-accelerating capstone project to elevate your professional journey. This course will help you gain expertise in Networks, SOC, Application Security, Risk Analysis, and Mitigation via live classes by Industry Expert and master classes by IIT faculty.
Key Highlights
About ihub divyasampark, iit roorkee.
iHUB DivyaSampark aims to enable an innovative ecosystem in new age technologies like AI, ML, Drones, Robots, and data analytics (often called CPS technologies) and become the source for the next generation of digital technologies, products, and services by promoting, enhancing core competencies, Read More.. capacity building, and manpower training to provide solutions for national strategic sectors and becoming a key contributor to Digital India. iHUB DivyaSampark a section 8 company (Non-Government Organization) is a Technology Innovation Hub, at IIT Roorkee and was set up under the National Mission on Interdisciplinary Cyber Physical systems (NM-ICPS), initiated by the Department of Science and Technology (DST) to build innovative solutions, train manpower, and encourage entrepreneurship for the world’s current challenges like affordable health care, Industry 4.0 and sustainable smart cities.
Key Achievements of IIT Roorkee:
- Ranked 7th ‘Overall’ and 6th in ‘Engineering’ in India as declared by NIRF 2022
- Ranked 175th in the world for ‘Engineering and Technology’ by QS World University Rankings 2023
- Ranked as the 369th best institute in the world by QS World University Rankings 2023
- Ranked as the 114th best institute in Asia by QS World University Rankings 2023
Upon the completion of this program, you will receive:
- Executive Post Graduate Certification in Ethical Hacking from iHUB DivyaSampark, IIT Roorkee.

About the EC-Council
This American organization offers education, training, and services on ethical hacking. The certification by the EC-Council validates the various ethical hacking skills that the learners will be trained in through the program.
Benefits for students from EC-Council
- Certified Ethical Hacker certificate from EC Council
- 24 Hacking Challenges from EC Council
- Student kit containing e-books, exam voucher

Who can apply for this program?
- Anyone who has a bachelor’s degree
- Anyone who is in the final year of their bachelor’s degree program
- IT professionals
- Anyone who wants to pursue Ethical Hacking

What roles can an ethical hacker play?
Chief information security officer (ciso).
The CISO is responsible for overseeing the organization’s overall cybersecurity strategy and ensuring the implementation of effective security measures. They develop policies, manage risk, and lead incident response efforts.
Security Analyst
Security analysts monitor and analyze systems, networks, and applications for potential security threats. They investigate security incidents, perform risk assessments, and implement security controls to protect company assets.
Security Engineer
Security engineers design and implement security solutions, including firewalls, encryption systems, and intrusion detection systems. They conduct vulnerability assessments, develop secure architectures, and respond to security incidents.
Network Administrator
Network administrators manage and maintain the organization’s computer networks. They configure network devices, monitor network performance, and implement security measures to protect against unauthorized access.
Security Architect
Security architects design and develop security frameworks, policies, and procedures for the organization. They collaborate with stakeholders to define security requirements and ensure that systems are designed with security in mind.
Security Operations Center (SOC) Analyst
SOC analysts monitor the organization’s systems and networks for security events, triage incidents, and escalate as needed. They analyze security logs, investigate potential threats, and provide real-time responses to security incidents.
Skills to Master
Ethical Hacking
Cryptography
Cyber Security
Application Security
Risk Analysis and Mitigation
Tools to Master

Meet Your Mentors

Manish Anand
Manish Anand is an IIT Kanpur alumnus with an MBA in Technology and innovation management from Korea Advanced Institute of Science and Technology (KAIST), Seoul. He currently heads iHUB, a Technology Innovation Hub hosted at IIT Roorkee.

Dr. Sudeb Das Gupta
Dr. Sudeb Dasgupta is currently working as a Professor at IIT Roorkee. He has completed his PhD from Banaras Hindu University in Electronics Engineering and has more than 20 years of teaching experience.

Dr. Balasubramanian R
Dr. Balasubramanian R, is currently working as Professor at IIT Roorkee. He has completed his PhD from IIT Madras in Mathematics and Computer Science and has more than 20 years of teaching experience.

Dr. Sushanta Karmakar
Dr Sushanta Karmakar is currently working as an Associate Professor at IIT Guwahati. He has completed his Ph.D. from IIT Kharagpur in the Computer Science and Engineering department. He has over 15 years of experience in teaching.

Rupesh Nasre
Rupesh Nasre is currently working as an Associate Professor in the CSE Department at IIT Madras. He holds a Ph.D. from IISc Bangalore and a Post-Doctoral Fellowship from the University of Texas at Austin.

Yogendra Deoskar
Yogendra Deoskar, who has 23 years of experience in the field of cyber security, is currently working at Accenture as the associate director of cyber security. He is skilled in solutions architecture and has served eminent companies like Infosys and Ernst & Young.

Dhruva Raj Pudel
Certified in CISSP and CCSP by (ISC)², and Cyber Security Risk Management by Harvard University, Dhruva carries 14+ yrs of experience with a focus on SIEM solutions and Host Based instruction detection systems, etc., and has worked with top MNCs like Wipro and IBM.

Gaurav Ranade
Gaurav Ranade is the CTO at RAH Infotech Pvt Ltd. He has over 25 years of experience in techno-commercial, solution designing, and managing big accounts for cyber security. His successful profile demonstrates self-motivation, entrepreneurial drive, and creativity.

Illyas Kooliyankal
Illyas is a Member of BCI (MBCI). He is the executor of many successful Information and Cyber Security Transformation Programs for banks and other institutions. He has 20+ years of core experience in Information Security and 25+ years altogether.
Module 1 – Preparatory Session Linux Foundation
1.1 Introduction to Linux OS fundamentals 1.2 Linux Basics – file handling, data extraction, etc. 1.3 Hands-on-Sessions and assignments for practice purpose
Module 2 – Fundamentals of Networking
2.1 Networking basics- Switches, routers, and wireless access points
Module 3 – Working with Kali Linux 2021.1
3.1 Introduction to Kali Linux 3.2 Services in Kali (HTTP, SSH) 3.3 Command-line utilities (Wget, curl, grep, awk, and many more) 3.4 Key concepts and basics of scripting (Piping, Redirection and Bash Scripting) 3.5 Tools and utilities in Kali Linux ( Netcat, Socat, Powercat, Powershell, etc.)
Module 4 – Certified Ethical Hacking by EC Council
4.1 Introduction to Ethical Hacking 4.2 Footprinting and Reconnaissance 4.3 Scanning Networks 4.4 Enumeration 4.5 Vulnerability Analysis 4.6 System Hacking 4.7 Malware Threats 4.8 Sniffing 4.9 Social Engineering 4.10 Denial-of-Service 4.11 Session Hijacking 4.12 Evading IDS, Firewalls, and Honeypots 4.13 Hacking Web Servers 4.14 Hacking Web Applications 4.15 SQL Injection 4.16 Hacking Wireless Networks 4.17 Hacking Mobile Platforms 4.18 IoT and OT Hacking 4.19 Cloud Computing 4.20 Cryptography 4.21 Working with Kali Linux 2021.1
Job Readiness
- Job Search Strategy
- Resume Building
- LinkedIn Profile Creation
- Interview Preparation Sessions by Industry Experts
- Mock Interviews
- Placement opportunities with 400+ hiring partners upon clearing the Placement Readiness Test.
Module 5 – Introduction to Cyber Security & Information Security
5.1 What is Cyber Security 5.2 Overview 5.3 Need and Importance 5.4 Different verticals
Module 6 – Certified Information System Security Professional (CISSP)
6.1 Domain One – Security and Risk Management
- Regulatory and legal issues
- Availability, Confidentiality, and concepts like integrity
- Principles of security governance
- Compliance and professional ethics
- Requirements of business continuity
- Policies of personnel security
- Security education, awareness, and training
- Security policies, standards, procedures, and guidelines
6.2 Domain Two – Asset Security
- Privacy protection
- Asset and information classification
- Data security controls and appropriate retention
- Requirements handling
6.3 Domain Three – Security Architecture and Engineering
- Security evaluation models
- Fundamental concepts of security models
- Security designs, architectures, and solution elements vulnerabilities
- Information systems security capabilities
- Using secure design principles for engineering processes
- Vulnerabilities of web-based and mobile systems
- Vulnerabilities of cyber-physical systems and embedded devices
- Secure principles of facility and site design
- Physical security
6.4 Domain Four – Communication and Network Security
- Architectural design of a secure network
- Channels for secure communication
- Components of a secure network
- Network attacks
6.5 Domain Five – Identity and Access Management (IAM)
- Logical/physical access to assets management
- Authentication and identification management
- Integrating identity as a third-party service
- Mechanism of authorization
- Provisioning life cycle’s identity and access
6.6 Domain Six – Security Assessment and Testing
- Test outputs (e.g., manual and automated)
- Security process data (e.g., operational and management controls)
- Vulnerabilities of security architectures
- Testing of security control
- Test and assessment strategies
6.7 Domain Seven – Security Operations
- Monitoring and logging activities
- Investigation requirements and support
- Incident management
- Resource provision
- Concepts of foundational security operations
- Recovery strategies
- Techniques of resource protection
- Measures of prevention
- Vulnerability and patch management
- Processes of change management
- Exercises and planning of business continuity
- Personnel safety concerns
- Plans and processes for disaster recovery
6.8 Domain Eight – Software Development Security
- Security controls for the development environment
- Software development life cycle security
- Impact of acquired software security
- Effectiveness of software security
Module 7 – Security Operations Centre (SOC)
7.1 SecOps: Protecting, Managing, responding and Monitoring 7.2 Cyber Security threat intelligence salary 7.3 Security data management – Event Logging 7.4 Improved Identification of Incidents using Threat Intelligence 7.5 Incident Response
Module 8 – Cloud Security
8.1 Overview of Azure Security 8.2 Active Directory (AD) of Azure for Workloads 8.3 Network Security for the Protection of the Platform 8.4 Host Security for the Protection of the Platform 8.5 Security and Containers 8.6 Role-based Access Control (RBAC) and Security Operations 8.7 Data Services Security 8.8 Security of Storage
Module 9 – Capstone Project
This module will teach you how to safeguard a web application against being hacked, along with key considerations when making an app secure. Your capstone project will give you exposure to both sides, giving an understanding of both working environments.
Module 10 – Python
- Learn the basics of the python programming language
- Use various IDEs for python development like Jupyter, Pycharm, etc.
Python Basics
- Learn variables, Data Types, decorators, functions, Loops, file handling, Conditional Statements, lambda functions, and exception handling ,etc.
- Object Oriented Programming
- Introduction to OOPs concepts like objects, classes, encapsulation, abstraction, inheritance, polymorphism, etc.
- Hands-on Sessions And Assignments for Practice
Learn all these concepts along with real time hands on sessions and practice assignments.
Program Highlights
All the projects included in this program are aligned with the industry demands and standards. These industry-oriented projects will test your level of knowledge in the Ethical Hacking domain and also help you get exposure to real-life scenarios.
Practice 20+ Essential Tools
Designed by Industry Experts
Get Real-world Experience
- Intermediate
Removing and Retrieving Files
This project will allow you to recover your deleted files and determine the location of the deleted files in the system or database. As part of this project, you will also create a report of all available data recovery tools.
SQL Injection
In this SQL Injection Cyber Security attack, you will be making a report on the SQL vulnerability and submitting it. This can be an interesting project for candidates having good knowledge of Python.
Password Strength
This project equips the candidate with the right skills and knowledge to create password analysis software. Going a step further, it is also possible to suggest a strong password to the user that is not vulnerable to attacks.
Break A Caesar Cipher
Using the logic behind the cipher, you will develop a small web app that can decrypt the Caesar cipher. This project is easy and will boost your confidence to take up advanced-level projects in cyber security.
Packet Sniffing
In this project, you will analyze network traffic to monitor all outgoing and incoming data packets. You will build a network analyzer and submit a report.
Hacking an Offline Device
In completing this project, you will need to gather information on the number of ways an intruder can illegally gain access to an offline device. You will submit a report that includes methods for securing devices such as cell phones, laptops, etc.
Credit Card Fraud Detection
In this project, you will work on a system that analyses user transactions and behavior. Based on this analysis, your system will identify parameters for unusual behavior in the system, such as incorrect passwords.
Using basic programming skills, you can develop your keylogger and capture keystrokes on a system. This project also allows you to learn to manually search a keylogger by digging into the system to end the keylogging process
Preventing Phishing Attacks on Voting Systems Using Visual Cryptography
In addition to visual cryptography, you will also learn how to integrate fingerprint techniques into the voting system to uniquely identify each voter.
Bypass Client-Side Controls and Attack Authentication
In this project, you will learn to bypass some of the client-side controls placed in the web application to limit user inputs. You will also learn to disrupt authentication functions in the attacking authentication sessions.
Intrusion Detection System with Self-programming Functionality
The objective of this project is to learn how to detect any intrusion on the system and to create a fake program to create a fake system. To prevent and secure the original application and track the attack pattern, you will create fake countermeasures.

Manas Sonkusare

Harnek singh

Success Stories

Shivaraj Thevendran
Intellipaat has the best experienced mentors. I am absolutely satisfied and glad that I learnt new technologies through real life scenarios that will also assist me in cracking interviews.

Syed Zakiruddin
The training went smoothly from day one. The learning content, trainers, hands-on assignments and quizzes all are perfect. Recording facility is excellent for revising. Also, a prompt support team.

Nanda Kishore
Intellipaat has some of the best trainers and a wonderful curriculum in the market. Amazing support team. I received assistance starting from the registration to the successful course completion.

Intellipaat is crystal clear and confident in what they are delivering. The trainers are experts with experience and this helped me get industry-level knowledge to shape my career.

The best thing that I liked about Intellipaat was the support provided by the career and mentoring team. Now coming to the sessions, they are great and power packed with a lot of information.

Koundinya Sanagala
Happy to have associated with Intellipaat through this amazing course. The learning experience was great through assignments, strong delivery, and a dedicated 24*7 support team.

I would highly recommend Intellipaat. If you wish to upgrade yourself, Intellipaat is the best place to go. Apart from the quality training, I also received exceptional support from them.
Hear From Our Hiring Partners

Lead Recruiter at Accenture, India
The candidates from Intellipaat were very good. They are better than experienced people from the same domain. The learners had hands-on experience. The product managers were very happy with the job-ready recruits.

HR at Genex Corporate Services, India
Even freshers from Intellipaat are technically strong and have hands-on experience. During the interview, they were able to answer everything that was asked. Certification plays a crucial role to move forward any resume.
Career Services By Intellipaat

- Job Assistance
- Interview Preparation
- Profile Building

Career Oriented Sessions
Over 10+ live interactive sessions with an industry expert to gain knowledge and experience on how to build skills that are expected by hiring managers. These will be guided sessions and that will help you stay on track with your up skilling objective.

Resume & LinkedIn Profile Building
Get assistance in creating a world-class resume & LinkedIn Profile from our career services team and learn how to grab the attention of the hiring manager at profile shortlisting stage

Mock Interview Preparation
Students will go through a number of mock interviews conducted by technical experts who will then offer tips and constructive feedback for reference and improvement.

1 on 1 Career Mentoring Sessions
Attend one-on-one sessions with career mentors on how to develop the required skills and attitude to secure a dream job based on a learners’ educational background, past experience, and future career aspirations.

3 Guaranteed Interviews
Guaranteed 3 job interviews upon movement to the placement pool after clearing the Placement Readiness Test ( PRT). Get interviewed by our 400+ hiring partners.

Exclusive access to Intellipaat Job portal
Exclusive access to our dedicated job portal and apply for jobs. More than 400 hiring partners’ including top start-ups and product companies hiring our learners. Mentored support on job search and relevant jobs for your career growth.
Our Alumni Works At
Peer Learning
Via Intellipaat PeerChat , you can interact with your peers across all classes and batches and even our alumni. Collaborate on projects, share job referrals & interview experiences, compete with the best, make new friends – the possibilities are endless and our community has something for everyone!
Class Notifications
Career services, major announcements, collaborative learning, admission details.
The application process consists of three simple steps. An offer of admission will be made to selected candidates based on the feedback from the interview panel. The selected candidates will be notified over email and phone, and they can block their seats through the payment of the admission fee.

Submit Application
Tell us a bit about yourself and why you want to join this program

Application Review
An admission panel will shortlist candidates based on their application

Selected candidates will be notified within 1–2 weeks
Program Fee
Total Admission Fee
Upcoming Application Deadline 27th Apr 2024
Admissions are closed once the requisite number of participants enroll for the upcoming cohort. Apply early to secure your seat.
Program Cohorts
Next Cohorts
Frequently Asked Questions
Why should i enroll in this executive post graduate certification in ethical hacking by ihub divyasampark, iit roorkee.
The program provides a holistic education in ethical hacking. The advanced certification offered by iHUB DivyaSampark, IIT Roorkee is aligned with industry requirements and will enable you to interview with leading MNCs.
Will iHUB DivyaSampark, IIT Roorkee be helping with the Career Services?
Intellipaat provides career services that include guaranteed interviews for all learners enrolled in this course. iHUB DivyaSampark, IIT Roorkee is not responsible for career services.
What are the growth opportunities after doing this Executive Post Graduate Certification in Ethical Hacking?
- The global demand for cybersecurity professionals will grow by 350,000 jobs in 2023. – Cybersecurity Ventures
- The average annual salary of a security analyst in India is ₹606,066 per annum. – Glassdoor
- The average annual salary of a security analyst in the U.S. is $104,210. – U.S. News
- The compound annual growth rate (CAGR) for ethical hacking jobs is expected to be 38% from 2022 to 2028.
Who are the course instructors for this online certification course?
You will be taught by the best practitioners in the industry and the course has been developed in consultation with IIT faculty.
What if I miss a live class?
If you miss a live class, you will receive the recording of the class within the next 12 hours. If you need assistance, you’ll also have access to our 24/7 support team to help you with any questions you may have.
How much time do I have to commit to successfully complete this program?
To complete this program, it is recommended that you spend approximately 6-8 hours per week studying.
Will iHUB DivyaSampark, IIT Roorkee be helping with the placements?
The career service is provided by Intellipaat, where you are guaranteed three interviews upon successful completion of the course. iHUB DivyaSampark, IIT Roorkee issues a certificate upon completion of the course.
Are there any scholarships available for this program?
Yes. You may contact course advisors to learn more about scholarship opportunities.
Is this program conducted online or offline?
This advanced certification program is conducted online for 11 months and is accompanied by several live sessions with instructors.
What is the process of getting into the placement pool?
To be included in the placement pool, the learner must complete the course and submit all projects and assignments. He/she must then pass the PRT (Placement Readiness Test) to be accepted into the placement pool and gain access to our job portal and career mentoring sessions.
What is included in this course?
- Unbiased career counseling
- Counselling based on your skills and preferences
- No repeat calls, only as needed
- Rigorous curriculum developed by industry experts
- Complete this program while you work
Who is eligible to receive the fellowship of Rs. 80,000?
From each batch, 2 candidates may get a fellowship of up to Rs. 80,000. Candidates will have to meet certain performance criteria to get selected. The selection of candidates who receive the fellowship will be at the discretion of the iHUB DivyaSampark, IIT Roorkee team. All the students will be informed about the performance criteria during the tenure of the program.
Who is eligible to receive funding and incubation support from iHUB DivyaSampark, IIT Roorkee?
All candidates who apply for this course will be eligible to receive an equity based seed funding and incubation support for their startup from iHUB DivyaSampark, IIT Roorkee. Candidates who enroll will get the chance to pitch their ideas to the iHUB DivyaSampark team. Ideas that get shortlisted may receive funding up to Rs. 50 Lakh and incubation support for their startup.
What exams will I be able to clear if I complete this advanced certification training?
This Executive Post Graduate Certification in Ethical Hacking will help you pass the Certified Ethical Hacker Certification for CEH v12, Certified Information System Security Professional Certification & Microsoft Certified: Azure Security Engineer Associate (Exam AZ 500).
What is the refund policy for this program?
Please note that the course fees is non-refundable and we will be at every step with you for your upskilling and professional growth needs.
Do you have the batch deferral policy for this program?
Due to any reason you want to defer the batch or restart the classes in a new batch then you need to send the batch defer request on [email protected] and only 1 time batch defer request is allowed without any additional cost.
Learners can request for batch deferral to any of the cohorts starting in the next 3-6 months from the start date of the initial batch in which the student was originally enrolled for. Batch deferral requests are accepted only once but you should not have completed more than 20% of the program. If you want to defer the batch 2nd time then you need to pay batch defer fees which is equal to 10% of the total course fees paid for the program + Taxes.
- Non-biased career guidance
- Counselling based on your skills and preference
- No repetitive calls, only as per convenience
- Rigorous curriculum designed by industry experts
- Best Cyber Security Course For Career Transition
Get Our App Now!
ANALYTICS COURSES
- Data Science Course
- Artificial Intelligence Course
- Data Analytics Course
- Machine Learning Course
- Python Data Science Course
- Business Analytics Course
- Python Course
CLOUD COURSES
- Azure Course
- DevOps Course
- Cyber Security Course
- AWS Solutions Architect
- Salesforce Course
- Selenium Course
- AWS DevOps Course
- Cloud Computing Courses
TRENDING COURSES
- Ethical Hacking Course
- Power BI Course
- Informatica Course
- Digital Marketing Course
- Business Analyst Course
- Investment Banking Course
- Azure DevOps Course
- Azure Data Engineer Course
Popular Courses
- Electric Vehicle Course
- UI UX Design Course
- Tableau Course
- Full Stack Developer Course
- Data Engineering Course
- Supply Chain Management Course
- General Management Course
Browse By Domains
Big Data Analytics Courses Business Intelligence Courses Salesforce Courses Cloud Computing Courses Digital Marketing Courses Programming Courses Database Courses Project Management Courses Web Development Courses Automation Courses
Popular Tutorials
Data Science Tutorials Machine Learning Tutorials Cyber Security Tutorials Salesforce Tutorials AWS Tutorials Azure Tutorials SQL Tutorials Selenium Tutorials Ethical Hacking Tutorials Artificial Intelligence Tutorials
Popular Resources
Data Science Machine Learning AWS Digital Marketing Cyber Security Artificial Intelligence DevOps Python UI UX Design Ethical Hacking
Degree program
Online M Tech in AI & ML Masters degree in Data Science MBA Big Data Management Masters degree in Artificial Intelligence Global MBA MBA in International Marketing Masters in Computer Science MBA in Finance and Accounting Masters in Engineering Management Msc in Data Science
© Copyright 2011 - 2024 Intellipaat Software Solutions Pvt. Ltd.
- Refund Policy
- Privacy Policy
- Terms of Use
- Interview Questions
- City Sitemap
- Become an Instructor
Address: 6th Floor, Primeco Towers, Arekere Gate Junction, Bannerghatta Main Road, Bengaluru, Karnataka 560076, India.
Disclaimer: The certification names are the trademarks of their respective owners.
Your cart is currently empty.
Return to shop
- Accreditation
- Press Media
- Arts & Science
- Agriculture Sciences
- Business / Management
- Biotechnology
- Engineering
- Mass Communication
- Health Sciences
- Nanoscience
- Social Work
- Interdisciplinary Studies
- Introduction to Hinduism
- Essence of Hinduism
- Mahabharata Upanayanam
- B.COM – Bachelor of Commerce
- M.COM – Master of Commerce
- MCA (Specialization: Artificial Intelligence)
- BBA – Bachelor of Business Administration
- MBA – Master of Business Administration
- MCA (Specialization: Cybersecurity)
- BCA – Bachelor of Computer Application
- MCA – Master of Computer Application
- Publications
- International
- B.Tech. in Artificial Intelligence (AI) and Data Science (Medical Engineering) - Undergraduate
- Ph. D. in Physics -
From the news
- Chancellor Amma Addresses the Parliament of World’s Religions
- Amrita Students Qualify for the European Mars Rover Challenge
- Total colorings-a survey
- Sombor Index of Edge Corona Product of Some Classes of Graphs

Ph. D. in Cyber Security Systems and Networks Attention Please ! Amrita Vishwa Vidyapeetham has not appointed any Agent or Third-Party Client for securing admission in any programme. Students are hereby requested to contact only the toll-free number on our website for any admission related queries. - Issued in public interest by Directorate of Admissions and Academic Outreach
- Program Overview
Fee Structure
Program overview, about program.
The Ph. D. in Cyber Security Systems and Networks is a Doctoral program provided by Amritha vishwa vidyapeetham.The call for applications will generally be posted twice a year on the website . However, Amrita Vishwa Vidyapeetham will accept applications throughout the year. Each Applicant should submit, in addition to his or her degree certificates,grade/ mark sheets and other documents mentioned in the application, a Statement of Purpose (describing his or her research interests) together with the completed application, and mention up to three areas of interest in the order of preference for PhD programme.
The Ph. D. in Cyber Security Systems and Networks is a Doctoral program provided by Amritha vishwa vidyapeetham.The call for applications will generally be posted twice a year on the website. However, Amrita Vishwa Vidyapeetham will accept applications throughout the year. Each Applicant should submit, in addition to his or her degree certificates,grade/ mark sheets and other documents mentioned in the application, a Statement of Purpose (describing his or her research interests) together with the completed application, and mention up to three areas of interest in the order of preference for PhD programme.

Attention Please!
Amrita Vishwa Vidyapeetham has not appointed any Agent or Third-Party Client for securing admission in any programme. Students are hereby requested to contact only the toll-free number on our website for any admission related queries.
– Issued In Public Interest By Directorate Of Admissions And Academic Outreach
Admission
Doctoral programs at Amrita Vishwa Vidyapeetham are designed to develop outstanding educational researchers with a wide range of research skills as well as in-depth knowledge and practical understanding and expertise in their chosen field of educational research.

ELIGIBILITY
The applicant should possess either (1), (2) or (3):
- M.E./ M.Tech./ M.S., or equivalent Degree
- B.E./ B.Tech./ B.S. (4-year Bachelor of Science), or equivalent Degree with a minimum of one year academic experience
- M.Sc./ M.C.A., or an equivalent Degree
Applicants should show evidence of strong academic record. Excellent test scores on standardised graduate aptitude tests such as GATE or GRE, and publications in recognised conferences and journals are examples of such evidence.
Important Note
2024 phase 1 admissions open, program overviews.
The call for applications will generally be posted twice a year on the website. However, Amrita Vishwa Vidyapeetham will accept applications throughout the year. Each Applicant should submit, in addition to his or her degree certificates,grade/ mark sheets and other documents mentioned in the application, a Statement of Purpose (describing his or her research interests) together with the completed application, and mention up to three areas of interest in the order of preference for PhD programme.
The Chairman, PGP will screen the applications and call the selected applicants for an entrance test followed by an interview. The Selection Committee constituted by the Chairman-PGP will examine the applicants’ background and aptitude for research. Based upon the entrance test and interview performance and prior academic record, the Committee shall give its recommendation to the Chairman-PGP who will finalise the admission and notify the selected applicants the date of joining. All prospective thesis advisors may be involved in the selection process and their consent obtained before being appointed as the Thesis Advisor for any applicant.
Whenever required, the Committee may request additional evidence, such as letters of recommendation, copies of claimed publications, etc.
There are two possible categories of admission for any applicant:
- Full-time doctoral students
Such students are entirely focused on carrying out their course work, research, and other requirements of the Ph.D. Program at Amrita Vishwa Vidyapeetham. Students admitted under this category may be employed as project staff on a research project; however, the research project must have the student’s thesis advisor as either a PI or a Co-PI, and the subject areas of the research project and the student’s proposed doctoral research should overlap.
- Part-time doctoral students
Such students are either full-time employees (e.g., faculty or project staff not covered under (a)) of Amrita Vishwa Vidyapeetham, or employees of other organisations (such as other colleges, Universities, R&D Centers, etc.). They are permitted to proceed at a slower pace in their Ph.D. Program at Amrita Vishwa Vidyapeetham.
Fees mentioned beside are current. The University reserves the right to alter fees at any time without notice.
The top reasons to choose Amrita for your career

Amrita Center for Cybersecurity Systems and Networks Amrita Vishwa Vidyapeetham Amritapuri Campus Amritapuri, Clappana P. O. Kollam – 690525 Kerala, India
+91 (0) 476 2801280 [email protected]
- Skip to Content
- Catalog Home
- Give to Illinois Tech
- Directories
- Courses A-Z
- Faculty A-Z
- Armour College of Engineering /
- Electrical and Computer Engineering /
- Master of Cyber Security Engineering
Rapid growth in the reliance of critical and personal information on cyber infrastructure has made us more vulnerable to cyber threats and cyberattacks. This master's program will educate students with techniques, tools, analysis, policies, and methodologies to solve complex cyber security problems of relevance to the engineering field.
There is a strong demand for security professionals in industries with the increase in cyber threats to their systems. This program will prepare students with extensive knowledge in cyber security, cyber-physical systems, cloud computing security, network engineering and cyber security for smart grid power systems, security vision systems, coding theory, and wireless secure communications.
Admission to the Master of Cyber Security Engineering program normally requires a bachelor of science degree in electrical or computer engineering from an institution accredited by the Accreditation Board of Engineering and Technology (ABET). Deficiency courses will be required for students who have not taken prerequisite or equivalent courses of the following: ECE 242 and MATH 374 . A student may demonstrate proficiency by successfully completing the courses or by demonstrating satisfactory performance in one or more special examinations administered by the department.
- Undergraduate
- University Overview
- Graduate Admission
- Financial Information
- Graduate Education
- Biomedical Engineering
- Chemical and Biological Engineering
- Civil, Architectural, and Environmental Engineering
- Master of Biomedical Imaging and Signals
- Master of Computational Engineering, Optimization, Machine Vision, and Decision Making Track
- Master of Computer Engineering in Internet of Things
- Master of Electrical and Computer Engineering
- Master of Electricity Markets
- Master of Network Engineering
- Master of Power Engineering
- Master of Telecommunications and Software Engineering
- Master of VLSI and Microelectronics
- Master of Engineering in Advanced Manufacturing, Automation and Control Systems Track
- Master of Engineering in Artificial Intelligence for Computer Vision and Control
- Master of Engineering in Energy Systems, Energy Transmission and Markets Track
- Master of Engineering in Wireless Communications and Computer Networks
- Master of Science in Computer Engineering
- Master of Science in Computer Engineering and Electrical Engineering
- Master of Science in Electrical Engineering
- Doctor of Philosophy in Computer Engineering
- Doctor of Philosophy in Electrical Engineering
- Master of Electrical and Computer Engineering with E3 Specialization
- Master of Science in Electrical Engineering with E3 Specialization
- Doctor of Philosophy in Electrical Engineering with E3 Specialization
- Certificate in Advanced Electronics
- Certificate in Applied Electromagnetics
- Certificate in Communication Systems
- Certificate in Computer Engineering
- Certificate in Control Systems
- Certificate in Electricity Markets
- Certificate in Power Electronics
- Certificate in Power Engineering
- Certificate in Signal Processing
- Certificate in Wireless Communications Engineering
- Industrial Technology and Management
- Mechanical, Materials, and Aerospace Engineering
- Chicago-Kent College of Law
- College of Architecture
- College of Computing
- Institute of Design
- Lewis College of Science and Letters
- Stuart School of Business
- Interdisciplinary Education
- Courses A-Z
- Academic Policies and Procedures
- General Policies
- Campus Overview

Print Options
Print this page.
The PDF will include all information unique to this page.
10 colleges and universities shaping the future of cybersecurity education
Institutions featured on this list often provide undergraduate and graduate degrees, courses, as well as certificate programs tailored to meet the growing demand for cybersecurity professionals in various industries.

Some notable colleges and universities renowned for their cybersecurity programs and courses include:
Carnegie Mellon University (USA)
Information Networking Institute (INI)
The Information Networking Institute (INI) at Carnegie Mellon University (CMU) educates and develops engineers through technical, interdisciplinary master’s degree programs in information networking, security and mobile and IoT engineering that incorporate business and policy perspectives.
Program : Master of Science in Information Security (MSIS)
Georgia Institute of Technology (USA)
Institute for Information Security & Privacy (IISP)
The Georgia Institute of Technology’s Institute for Information Security & Privacy (IISP) is a research institution dedicated to advancing cybersecurity and privacy technologies. Established within Georgia Tech, the IISP serves as a focal point for interdisciplinary research, education, and collaboration in the field of information security and privacy.
Program : Master of Science in Cybersecurity
Massachusetts Institute of Technology (USA)
MIT Department of Electrical Engineering and Computer Science
A joint venture between the Schwarzman College of Computing and the School of Engineering, EECS is grounded in three overlapping sub-units: electrical engineering (EE), computer science (CS), and artificial intelligence and decision-making (AI+D).
- Computer Science and Engineering
- Artificial Intelligence and Decision Making
Stanford University (USA)
Cyber Policy Center and Computer Science Department
The Cyber Policy Center brings together researchers across the Stanford campus to solve the biggest issues in cybersecurity, governance and the future of work.
- Global Digital Policy Incubator
- The Program on Platform Regulation
- Geopolitics, Technology, and Governance
SANS Technology Institute (USA)
An independent subsidiary of SANS, the SANS Technology Institute offers graduate programs (master’s degree and graduate certificates) that develop technically-adept leaders and undergraduate programs (bachelor’s degree and undergraduate certificate) for people who want to enter the cybersecurity field.
Program : Cybersecurity Master’s Degree
University of California, Berkeley (USA)
School of Information
The School of Information is a graduate research and education community committed to expanding access to information and to improving its usability, reliability, and credibility while preserving security and privacy. This requires the insights of scholars from diverse fields — information and computer science, design, social sciences, management, law, and policy.
Program : Master of Information and Cybersecurity (MICS)
University of Cambridge (UK)
Department of Computer Science and Technology
The Department of Computer Science and Technology (formerly known as the Computer Laboratory) is the academic department within the University of Cambridge that encompasses computer science, along with many aspects of technology, engineering and mathematics.
- Cybersecurity
- Software and Security Engineering
University of Oxford (UK)
Global Cyber Security Capacity Centre (GCSCC)
The Global Cyber Security Capacity Centre (GCSCC) is an international centre for research on efficient and effective cybersecurity capacity-building, promoting an increase in the scale, pace, quality and impact of cybersecurity capacity-building initiatives across the world.
Course : MSc in Software and Systems Security
Technische Universität Darmstadt (Germany)
Department of Computer Science
The scientists of the Department of Computer Science combine their diverse research activities in three main research areas:
- Artificial Intelligence
- Complex Networked Systems
- Cybersecurity & Privacy
Program : Master’s degree program IT Security
Tel Aviv University (Israel)
Research is a cornerstone of Tel Aviv University’s mission, with its scholars making discoveries in fields ranging from biotechnology and cybersecurity to archaeology and social sciences.
- Cyber Security Program
- Cyber Politics & Government

Fill out the form to get your copy of this whitepaper and find out what it takes to join a growing industry:
- I have read and agree to the Privacy Policy and would like to be updated on ISC2 certifications, educational resources, and offers.
- Carnegie Mellon University
- cybersecurity
- skill development
- University of Cambridge
Featured news
- What AI can tell organizations about their M&A risk
- Breaking down the numbers: Cybersecurity funding activity recap
- Applying DevSecOps principles to machine learning workloads
- eBook: Why CISSP?
- Whitepaper: Why Microsoft’s password protection is not enough
- Guide: Application security posture management deep dive
- Most people still rely on memory or pen and paper for password management
- Overcoming GenAI challenges in healthcare cybersecurity
Ph.D. candidate presents at Women in CyberSecurity 2024 Conference
Naureen Hoque , a Ph.D. candidate in the Computing and Information Sciences program under the supervision of Assistant Professor Hanif Rahbari , presented her poster “Exposing New Denial of Service Vulnerability in Connection Establishment of Wi-Fi Systems” at the Women in CyberSecurity 2024 Conference, April 11-13 in Nashville, Tenn. Her submission was recognized with a student scholarship.
Recommended News
April 26, 2024

Color Chat: Disney’s Image and Color Engineer Molly Hill
postPerspective talks to Molly Hill '18 (motion picture science), '18 (film and animation), about her experience working as a senior image and color engineer at The Walt Disney Studios.

Showcasing creativity and innovation at Imagine RIT
13WHAM/Fox Rochester previews Imagine RIT in eight segments.

Imagine RIT festival returns to Rochester this weekend
Spectrum News showcases exhibits appearing at Imagine RIT.

‘I’m hoping this makes a difference in little kids:’ Imagine RIT is this Saturday
WROC-TV highlights exhibits that will be on display at Imagine RIT.
Computer Science and Engineering
Search form.
- Future Students
- Current Students
- Accreditation
- Financial Assistance
- GradTrack Program
- Capstone Program
- Marketable Skills
- Study Abroad
- Internships
- UNT at Frisco
- Grad Orientation
- Financial Assistantship
- Pathways Program
- CSE Seminars
- Graduate Course Scheduling
- Retired Faculty
- TAs/Graders
- Peer Mentor /UG Grader
- Stay Connected
- PhD Graduates
- Update Your Info
- Order Transcript
- About the Department
- Our History
- Advisory Council
- Faculty History
- Student Organizations
- Give to CSE
- Centralized Environment for Linux Labs (CELL Machines)
- Faculty Resources
PhD candidates and faculty selected as winning team for the 2024 Siemens Tech Sustainabilitiy through Cybersecurity Challenge

On March 14, 2024, research from our Network Security Lab received the winning team award for the 2024 Siemen’s Tech Sustainability through Cybersecurity Challenge . PhD candidates, Amal Alshehri and Burak Tufekci, as well as Assistant Professor, Dr. Cihan Tunc , were one of the finalist research groups (out of 22 projects) and their project “OTZET: Operational Technology Zero Trust Engine for Trustworthiness” has been selected as the winning project during Siemens’ international competition.
The group’s project underwent 4 stages of review consisting of a 4-month timeframe. The first stage, Ideation, occurred during the month of December 2023, saw a large pool of research ideas submitted by universities and companies around the world. Then, the selected projects ideas were implemented under Siemens’ guidance. And the final review was made in March 2024 for the selected finalists, which allowed our team to present and win the competition under the sustainability through cybersecurity track during the final Hackathon & Live Pitches stage last month. The audience consisted of respected professionals in cybersecurity, as well as those in academia, with potential of future collaboration or sponsorship.
Here’s what Siemens outlines as their goals for their Cybersecurity challenge in Sustainability: At Siemens, we consider cybersecurity as one of the company’s sustainability goals. We live in an ever-evolving environment filled with digital threats and risks. Only through robust cybersecurity can we effectively address those risks. This includes safeguarding information and intellectual property by preventing digital attacks from materializing in the real world, or by supporting businesses and production sites to operate without disruptions.

The OTZET project continues on as the Network Security Lab crew are moving forward with more paper submissions and more advances in their work. Dr. Cihan Tunc states, “We’re looking to build this research for further progression. [Amal Alshehri] is doing this for her final research.”
The Department of Computer Science and Engineering extends a huge congratulations to Amal Alshehri, Burak Tufekci, and Dr. Cihan Tunc on a job well done!
For more information on the Network Security Lab and the Smart CyberSpace group, check out their website links here:
Home | Network Security Lab (NSL) (unt.edu )
Welcome to Smart CyberSpace (SCS) at UNT | Smart Cyber Space (SCS)
For more information on Siemens, click here to access their website: Sustainability through cybersecurity | Siemens Innovation Ecosystem

Title: Chairman of the Joint Chiefs of Staff Discusses International Conflict, Defense and Leadership on the Hilltop
On Thursday April 25, 2024 Georgetown students gathered in the Healey Family Student Center Social Room to hear from General Charles Q. Brown, Jr., Chairman of the Joint Chiefs of Staff about the role of the U.S. military in U.S. politics and the world. As the most senior-ranking military officer in the U.S. and military advisor to the President , General Brown shared his experiences as a military leader and students had the opportunity to ask questions.
Vilda Westh Blanc (SFS‘27), a student who was on Dan Lamothe’s Student Strategy Team this semester, introduced the event. She welcomed Brown to the stage as well as current GU Politics Fellow Dan Lamothe to moderate the conversation.
Lamothe started the conversation by asking Brown about the current state of U.S. military operations and the threats to national security. “What makes this time uniquely dangerous, uniquely challenging?” Lamothe asked.
Brown emphasized the complex dynamics of this moment for U.S. national security, noting the significance of threats from North Korea, China, Russia and Iran. He explained that before coming to his current position he championed the phrase “Accelerate change or lose.”
“Personally and professionally, I do not play for second place. And I am very focused on ensuring we have all the capabilities to ensure our national security,” Brown said.
Outlining his priorities for the U.S. military, Brown highlighted the importance of training skilled service members, embracing the modernization of capabilities, and creating a foundation of trust with communities and elected officials.
On the importance of maintaining trust with American people, Brown said “Having that trust is hugely important to ensure that we do the things the nation calls us to do as military members.”
Next, Lamothe asked Brown how the Israel-Hamas conflict shapes the priorities of the U.S. military.
On the tension between current crises and future threats, Brown said “You’ve got to balance risk over time.”
“You never want to take short-term satisfaction at the expense of your long-term goals,” Brown said.
Continuing to discuss the conflict in the Middle East, Lamothe asked Brown about what it takes to deal with such a volatile situation and what strategies the military is utilizing to keep the conflict contained.
“From the very beginning, we looked at how do we deter a future conflict and at the same time protect our armed forces and support Israel to defend itself,” Brown said. “In addition to that is making sure we were providing humanitarian assistance and minimizing collateral damage.”
“This has been a theme throughout: how do we deter a broader conflict,” Brown said. Brown further emphasized the military’s preparedness, the efforts of the U.S. National Security Council, and the role of other foreign nations.
Lamothe then asked about what initial concerns Brown had regarding Iran’s attack on Israel on April 13th.
“First thing I’ll tell you is that I didn’t have a lot of concern because I have complete confidence in our force and they were well-prepared,” Brown said. He emphasized the work of the U.S. military in the week leading up to the April 13th attack and explained the communication and collaboration between the Pentagon and White House that happened the day of.
Turning to the topic of Ukraine, Lamothe noted that despite the recent aid package approved by the U.S. Congress, many think that “Ukraine will continue to be outgunned this year. What do you see as the likely outcome this summer?”
“When Ukraine is supplied, they have been able to be effective,” Brown said, stressing the importance of continuing to provide support.
“Even broader than this: what happens in one corner of the world does not stay in one corner of the world,” Brown added. “Unchecked aggression provides opportunity for future aggression.”
Next, Lamothe asked about building trust in the U.S. military. “We’re in a time where there is dwindling support for the U.S. military in a lot of polls. There are concerns about American democracy at large. What does it take to build new faith in the American military?” Lamothe asked.
“Trust is the foundation of our profession. And part of that, my focus, is not only maintaining the trust we have but to continue to build upon it.” Brown added, “I think the most important thing I can do is lead by example.”
Brown also emphasized the importance of being non-partisan as a military member. “Our oath is to the Constitution of the United States, to an ideal— not to a leader, not to an office,” Brown said.
Students then had the opportunity to ask Brown questions.
Captain Trevor Barton, Omar Bradley Fellow and McCourt Student studying national security issues asked: “What is your assessment, as the Chairman of the Joint Chiefs, of the current health of the defense industrial base related to our production capability, and what can policymakers do to increase the resiliency of the defense industrial base?”
“There’s key things, from a policymaker standpoint, that I think are very important. Consistency is probably top of the notch,” Brown said. “What I mean by that is that there’s consistency in our demand signal from the Department of Defense in what we need. And then consistency in resourcing. When you have that consistency, that helps predictability for the defense industrial base.”
MJ Ninal (C’24), a cadet in the Air Force ROTC , asked Brown about his advice for young lieutenants in this unique time of international threats and political polarization.
“Whatever job you’re going into, get really good at it. That’s probably the most important thing you can do. I’d also say ask a lot of questions. There are no dumb questions,” Brown said. “And when you ask tough questions of your leaders, it challenges us.”
One student asked Brown about the challenges of advising political leaders and what his advice was for fostering mutual understanding of perspectives and positions.
“When providing advice, you need to understand your boss, and your boss’s boss, and their intent and what their focused on,” Brown said. He emphasized that the perfect military solution does not always line up with what is going on geopolitically, economically and diplomatically, but understanding the bigger picture is key to effective conversations and problem-solving.
Lewis Williams III (S’28), a student studying applied intelligence at Georgetown’s School of Continuing Studies asked Brown, “What are some of your role models or individuals that have inspired you, whether civilian or military?”
Brown talked about the influence of his father, who was in the Army and encouraged Brown to apply. “This is all his idea,” Brown said.
“I think the other thing that has been an inspiration to me has been the Tuskegee Airmen,” Brown said, referring to the first African American military aviators in the U.S. “Just in general, what they were able to do leading up to World War II and during World War II.”
Brown recounted his experience getting to talk to some of the Tuskegee Airmen and hear their stories. He remembered Brigadier General Charles McGee and reflected on the honor it was to meet him.
Brown also answered student questions about cybersecurity, use of innovative technologies in Ukraine, climate change as a national security threat, and promoting cooperation between branches of the U.S. military.
Luke Hughes (SFS‘27) asked Brown what his message would be to incoming Georgetown students who are considering joining the ROTC.
On reasons to join, “I would say two things: One, the opportunity to serve your nation but the opportunity to gain some valuable experience,” Brown noted.
Brown emphasized the opportunities for growing as a leader, building meaningful relationships, and giving back to your community through involvement in the military.
“We need you, whether you serve in uniform or you serve in some other part of government, that’s what makes our democracy so strong,” Brown said.
GU Politics extends its gratitude to the Walsh School of Foreign Service , the SFS Security Studies Program , the Georgetown University Military and Veterans Resource Center and the National Defense Policy Initiative for co-sponsoring this event.
This article was written by Jane Wright , a first-year graduate student in the McCourt School of Public Policy.
Watch the full recording below.

The Hoya: Panelists Discuss Ranked-Choice Voting and Polarization With GU Politics
Panelists argued ranked-choice voting produces more democratic elections and decreases polarization and apathy in a Georgetown University Institute of Politics and Public Service (GU Politics) event April 17.

Maxwell Frost Discusses Advocacy, Activism and Running for Office at Georgetown
On Wednesday, April 10, 2024 students gathered in the ICC Auditorium to hear from U.S. Representative Maxwell Frost (D-FL) about his experience as an organizer and elected official,…

Boris Johnson Talks Democracy Around World at Gaston Hall
On Thursday April, 11 Georgetown students filled Gaston Hall to hear former Prime Minister of the United Kingdom Boris Johnson have a conversation about global politics and democracy…

Graduate Commencement Speaker Makes Memories at Tennis Captain, Cybersecurity Champion

When Mya Milagros Fuentes first came to Drexel as an undergraduate student in 2017, she didn't have a clear idea of what she wanted to do after graduation. Her interest in advocacy drove her to pursue a bachelor's degree in Business Administration with a focus on legal studies as well as a minor in Women and Gender Studies. Fuentes was considering a career as an attorney - that was, until she was introduced to the world of cybersecurity.
"There wasn't one set moment that led me to the field," Fuentes explained. A course on data, privacy, and law, along with co-op positions at GSK in identity & access management and at Bristol Myers Squibb as a Cybersecurity Governance Analyst, allowed Fuentes to discover her passion. "I was drawn to the idea of safeguarding individuals' data and fostering a sense of safety and security for them."
The co-op at BMS also gave Fuentes opportunities to transfer her extracurricular experiences to her professional life. She came to Drexel as a student athlete, playing for the women's tennis team for her first 6 years as a student, the last 2 of which she served as captain. Fuentes also notably served as the DEI chair for the Student Athlete Advisory Committee and as the co-founder and vice president of the Black Student Athlete Union, both of which saw Fuentes at the forefront of DEI initiatives in student athletics on campus. Not only did Fuentes grow as a leader who can engage with her community in creative ways, a form of growth that was "very unique to Drexel," but her experiences in leading DEI initiatives ultimately allowed her to incorporate them into her role at BMS.
“That experience shifted my path,” Fuentes said. "I'm very passionate about representation in tech, and I hope to create awareness for, and mentor underrepresented groups in STEM."
With her direction now in focus, Fuentes decided to pursue a master's degree in cybersecurity , but without a technical background, she was intimidated by the prospect of learning code. Fortunately, Drexel's faculty provided Fuentes with the support she needed to succeed in her technical courses, particularly Mark Boady, PhD, associate teaching professor of computer science, and Michelle Tarbutton, assistant teaching professor of information science [both CCI]. Boady's data structures and algorithms course allowed Fuentes to learn the C coding language in a non-judgemental environment, and she benefited from the guidance of Tarbutton in an information forensics course. Tarbutton emerged as both an inspiration and mentor to her.

Their courses posed considerable challenges, yet I excelled in them," Fuentes explained. "A significant factor in my success was the belief my professors had in me. Their encouragement instilled a sense of confidence in my abilities."
This newfound confidence led Fuentes to a graduate co-op at Vanguard , where she evaluated and recommended deployment models for sale point implementations as a Risk and Security Engineer, while continuing her involvement in DEI initiatives. According to Fuentes, her time at Vanguard "solidified [her] in interest in the strategic aspects of cybersecurity" and "combined technical expertise with [her] deep commitment to ethical practices and equity."
Despite being new to the field, Fuentes also learned the importance of networking and putting herself out there, which led to her receiving a post-grad offer to participate in Vanguard's Technology Leadership Program. "I've been provided with so much support and guidance throughout my time at Drexel," she stated. "The connections and relationships I've made here have been invaluable to my personal and professional success."
Fuentes will cap off her Drexel experience as the graduate student speaker during the College of Engineering’s commencement ceremonies on Thursday, June 13. As someone with a passion for writing and spoken word, Fuentes is excited to speak to her peers, and she's also "deeply honored and humbled" to represent her cohort, who she believes are "some of the most extraordinarily talented and brilliant individuals."
"I am thrilled to come together at commencement to celebrate our dedication and hard work,” Fuentes stated. “I don’t think of this as an ending but rather an exciting beginning.”
Learn more about a master's in Cybersecurity at Drexel.
In This Article
Areas of study, departments.

- Applied Cybersecurity and Information Technology (B.S.)
- Academic Programs
View all Illinois Tech Cybersecurity Programs
Gain a comprehensive understanding of cybersecurity and information technology through the cross-disciplinary Bachelor of Science in Applied Cybersecurity and Information Technology. Learn how cybersecurity, technology, management, compliance, and legal issues intersect through this well-rounded program. Experienced information technology professionals and those new to the field can prepare to become cybersecurity and information technology practitioners, investigators, managers, and leaders in one of the fastest growing job sectors. Additional mathematical skills prepare for research and entry into the Master of Science in Applied Cybersecurity and Digital Forensics program.
Study information security, information assurance, ethical hacking, vulnerability analysis and control, securing databases, steganography, mobile device forensics, operating system security, business continuity response, disaster recovery, legal and ethical issues, auditing, evidence, and intrusion detection. Work with forensic tools and techniques used to investigate and analyze network-related incidents and preserve digital evidence.
Program Overview
The cross-disciplinary Bachelor of Science in Applied Cybersecurity and Information Technology program places an emphasis on cybersecurity, technology, management, compliance, and legal issues. Develop the mathematical skills needed to prepare for research and entry into the Master of Science in Applied Cybersecurity and Digital Forensics program.
Career Opportunities
Graduates of the Bachelor of Science in Applied Cybersecurity and Information Technology will be prepared to fill a variety of roles within the industry, such as:
- Information security officer
- Security manager
- Security administrator
- Cybersecurity analyst
- Cybersecurity specialist
- Vulnerability researcher/exploit developer
View Details
Students of this program must be admitted to Illinois Tech. Previous coursework or experience in technology is helpful but not required.
Information Security Analyst Career Snapshot
Median salary.
U.S. Bureau of Labor Statistics
Best Tech Jobs
U.S. News & World Report
Unemployment Rate

Cyber Scholarship Program
Mark Littlefield earned an award from the United States Department of Defense (DoD) Cyber Scholarship Program. Littlefield was eligible to apply for the scholarship because Illinois Tech has been designated as a National Center of Academic Excellence in Cyber Defense Education by the National Security Agency (NSA) and the U.S. Department of Homeland Security.
North American Defense and Security Academic Alliance (NADSAA)
The North American Aerospace Defense Command (NORAD) and US Northern Command (USNORTHCOM) North American Defense and Security Academic Alliance ( NADSAA ) exists as a collaborative information-based enterprise dedicated to strengthening and normalizing relationships between the two commands and academic institutions. This relationship stimulates and develops new thinking, examines cross-organizational solutions, and helps cultivate future generations of Defense and Security practitioners.
Internship Opportunities
The NORAD and USNORTHCOM Volunteer Student Internship Program (N&NC VSIP) is part of a larger effort by NORAD and USNORTHCOM to help cultivate future generations of Defense and Security practitioners. N&NC VSIP internships provide exposure to NORAD and USNORTHCOM missions and responsibilities, while working alongside current military and civilian professionals dedicated to the defense of North America.
Gain valuable hands-on experience related to their education endeavors while working in a joint, interagency and international environment at NORAD and USNORTHCOM with a N&NC VSIP internship. Potentially earn academic credit for work performed, and some may qualify to receive a Department of Defense SECRET clearance.

National Center of Academic Excellence in Cyber Defense Education
The United States Department of Homeland Security and the National Security Agency have designated Illinois Institute of Technology as a National Center of Academic Excellence in Cyber Defense Education.

Featured Faculty

Maurice E. Dawson

Program Objectives and Outcomes
Bachelor of science in applied cybersecurity and information technology program educational objectives.
The Bachelor of Science in Applied Cybersecurity and Information Technology degree produces graduates who are able to:
- Problem solve, create, and effectively communicate innovative answers to provide technology solutions for the problems of business, industry, government, non-profit organizations, and individuals
- Perform requirements analysis, design and administration of computer and network-based systems conforming to policy and best practices, and monitor and support continuing development of relevant policy and best practices as appropriate
- Design and implement an enterprise security program using both policy and technology to implement technical, operational, and managerial controls, which will technically secure enterprise information assets and resources to deter, detect, and prevent the success of attacks and intrusions
- Investigate information security incidents and violation of law using computer resources in a manner such that all evidence is admissible in a court of law
- Apply current technical and mathematical concepts and practices in the core information technologies and recognize the need to engage in continuing professional development
Bachelor of Science in Applied Cybersecurity and Information Technology Student Outcomes
Bachelor of Science in Applied Cybersecurity and Information Technology graduates should be able to:
- Analyze a complex computing problem and to apply principles of computing and other relevant disciplines to identify solutions
- Design, implement, and evaluate a computer-based solution to meet a given set of computing requirements in the context of the program’s discipline
- Communicate effectively in a variety of professional contexts
- Recognize professional responsibility and make informed judgments in computing practice based on legal and ethical principles
- Function effectively as a member or leader of a team engaged in activities appropriate to the program’s discipline
- Identify and analyze user needs and take them into account in the selection, creation, evaluation and administration of computing-based systems
- Assist in the creation of an effective project plan
- Apply security principles and practices to maintain operations in the presence of risks and threats
Learn more...

IMAGES
VIDEO
COMMENTS
A Ph.D. in cybersecurity prepares graduates for advanced, high-level job opportunities, including roles in research, education and management. Cybersecurity Ph.D. programs allow students and ...
The best cybersecurity PhD programs for 2024. Capella University. Doctor of Information Technology. Ad. Georgia Institute of Technology. Atlanta, Georgia. Northeastern University. Boston, Massachusetts. Marymount University, School of Technology and Innovation.
Program Overview. The Master of Science in Applied Cybersecurity and Digital Forensics program prepares professionals for the rapidly growing fields of cybersecurity, forensics, and information assurance. Upskill for leadership roles in business, law enforcement, military, government, and other organizations.
Illinois Tech, Chicago's only tech-focused university, offers a wide scope of cybersecurity undergraduate, graduate, and certificate programs to build a cyber career path from entry-level to advanced research. As hacking, data breaches, and ransomware threats continue to increase, cybersecurity continues to be one of the hottest career fields.
The financial assistance for the Ph.D. program under MoE (Ministry of Education) and all other funding categories except PMRF and External category across all departments is 5 years. All the departments at IITH offer PhD program. The eligibility criteria for PhD admission in the engineering departments is a Masters degree. If you think you are ...
Details about Refund policy for the Masters and PhD admission process for the Autumn Semester 2024-25 New; Detailed Advertisement; Schedule; Information Brochure (2024-25) Online Application Portal Last day for submission of completed online application form is extended by ONE day : 11 th April, 2024 [5:00 pm, TOMORROW]
Interdisciplinary (M.Tech) in Cyber Security. Launched the new PG program!! Students and professionals from CS/EE/MA/EC interested in cybersecurity and want to explore more in the domain can apply. ... The last date for submission of online application for PG and PhD Programmes for admission for 1st semester 2024-25 extended upto 08 April 2024 ...
Cybersecurity doctorates offer two programs — the Ph.D. (doctor of philosophy degree) or the D.Sc. (doctor of science degree). The Ph.D. focuses on research and theory while the D.Sc. emphasizes application and action. Students who earn a Ph.D. generally want to add to the body of research or teach at the postsecondary level.
The department of Computer Science and Engineering at IIT Kanpur has been offering a good number of courses in Cyber Security related subjects for the last 4 years. Multiple faculty members in the department are engaged in research projects related to cyber security. Therefore, the department feels that it has a critical mass in terms of ...
The CoE-CSIA co-ordinates the Cyber Security initiatives in the institute. Amar Nath and Shashi Khosla School of Information Technology, IIT Delhi. Hauz Khas, New Delhi 110016, India. + (91) (11) 2659-6056. eoaesit [@]admin.iitd.ernet.in. SIT IIT DELHI.
IIT Kanpur's new courses in Cybersecurity will meet demand for trained cyber-soldiers to protect industry and country. MTech, MS by Research, and BT-MT Dual Degree programs to be available from August 2021 and admissions to commence during the April-May 2021 cycle. Kanpur, December 15, 2020: In today's digital world, vulnerability of the ...
Computer Science (Ph.D.) Pursue an academic or industrial research career through this doctoral program. Coursework revolves around seven core groups: theory of computation, systems, programming languages, networks and security, databases, software engineering, and computational intelligence. The amount of coursework is dependent on previous ...
Masters in Cyber Security; Elevate your Cyber Defense Game e-Masters in Cyber Security. Build capabilities to combat an evolving threat landscape. Join the next generation of Cyber Security professionals with IIT Kanpur online masters degree program. Study with industry experts, develop hands-on skills and stay ahead in the field. No GATE Score ...
Indian Institute of Technology, Kanpur Department of Computer Science and Engineering ... Name of the Specialization: Cyber Security . IIT Kanpur Computer Science and Engineering department is presenting an e-Masters program in Cyber Security to address the national need of cyber security manpower. ... Admission process will be as rigorous as ...
Indian Institute of Technology Delhi An Institution of Eminence ... B.Tech. Students of NIT Sikkim to be Eligible for Direct Admission to IIT Delhi's PhD Programmes Read More. ... IIT Delhi Establishes Alumnus Endowed "Shri. G.K. Chandiramani Chair for Cyber Security" ...
Amplify growth in the ever-growing digital age that sparks the volume of attacks and nature of cyber threats. Now eradicate these prominent cyber heists with India's leading IITs, IIT Palakkad- Post Graduation Certification in Cyber Security.This new age cyber security programme is opportune; ever-increasing cyber threats to businesses and government bodies.
About Program. This Executive Post Graduate Certification Program in Ethical Hacking by iHUB DivyaSampark, IIT Roorkee, offers 10 modules and a career-accelerating capstone project to elevate your professional journey. This course will help you gain expertise in Networks, SOC, Application Security, Risk Analysis, and Mitigation via live classes ...
View all Illinois Tech Cybersecurity Programs. Illinois Tech's Master of Cybersecurity Engineering degree program will provide students with extensive knowledge, techniques, tools, analysis, policies, and methodologies to solve complex cybersecurity problems of relevance to the engineering field. Students will gain advanced training on ...
About Program. The Ph. D. in Cyber Security Systems and Networks is a Doctoral program provided by Amritha vishwa vidyapeetham.The call for applications will generally be posted twice a year on the website. However, Amrita Vishwa Vidyapeetham will accept applications throughout the year.
This master's program will educate students with techniques, tools, analysis, policies, and methodologies to solve complex cyber security problems of relevance to the engineering field. There is a strong demand for security professionals in industries with the increase in cyber threats to their systems. This program will prepare students with ...
The Global Cyber Security Capacity Centre (GCSCC) is an international centre for research on efficient and effective cybersecurity capacity-building, promoting an increase in the scale, pace ...
Naureen Hoque, a Ph.D. candidate in the Computing and Information Sciences program under the supervision of Assistant Professor Hanif Rahbari, presented her poster "Exposing New Denial of Service Vulnerability in Connection Establishment of Wi-Fi Systems" at the Women in CyberSecurity 2024 Conference, April 11-13 in Nashville, Tenn.Her submission was recognized with a student scholarship.
Through Illinois Institute of Technology's cybersecurity master's degree program, you'll gain a deep understanding of data and information security, hardware and software security, and systems and network security. You'll develop the skills and knowledge to mitigate cyber risks while increasing data and systems protection, planning ...
Last month, research from our Network Security Lab received the winning team award for the 2024 Siemen's Tech Sustainability through Cybersecurity Challenge.PhD candidates, Amal Alshehri and Burak Tufekci, as well as Assistant Professor, Dr. Cihan Tunc, were one of the finalist research groups (out of 22 projects) and their project "OTZET: Operational Technology Zero Trust Engine for ...
Brown also answered student questions about cybersecurity, use of innovative technologies in Ukraine, climate change as a national security threat, and promoting cooperation between branches of the U.S. military. Luke Hughes (SFS'27) asked Brown what his message would be to incoming Georgetown students who are considering joining the ROTC.
The Master of Cyber Forensics and Security is cross-disciplinary program that focuses on technology, management, compliance, and legal issues. Experienced information technology professionals and those new to the field can build the skills to become cybersecurity and forensics practitioners, investigators, managers, and leaders.
Fuentes was considering a career as an attorney - that was, until she was introduced to the world of cybersecurity. "There wasn't one set moment that led me to the field," Fuentes explained. A course on data, privacy, and law, along with co-op positions at GSK in identity & access management and at Bristol Myers Squibb as a Cybersecurity ...
Bachelor of Science in Applied Cybersecurity and Information Technology graduates should be able to: Analyze a complex computing problem and to apply principles of computing and other relevant disciplines to identify solutions. Design, implement, and evaluate a computer-based solution to meet a given set of computing requirements in the context ...