
Top 100+ Computer Engineering Project Topics [Updated]

Computer engineering projects offer a captivating blend of creativity and technical prowess, allowing enthusiasts to dive into a world where innovation meets functionality. Whether you’re fascinated by hardware design, software development, networking, or artificial intelligence, there’s a wide array of project topics to explore within the realm of computer engineering. In this blog, we’ll delve into some intriguing computer engineering project topics, catering to both beginners and seasoned enthusiasts alike.
What Is A CSE Project?
Table of Contents
A CSE project refers to a project within the field of Computer Science and Engineering (CSE). These projects involve the application of computer science principles and engineering techniques to develop software, hardware, or systems that solve real-world problems or advance technology.
CSE projects can range from developing new algorithms and programming languages to designing and building computer hardware, networking systems, software applications, or artificial intelligence systems.
They often require interdisciplinary knowledge and skills in areas such as programming, data structures, algorithms, software engineering, hardware design, networking, and more.
How Do I Start A CSE Project?
Starting a CSE (Computer Science and Engineering) project can be an exciting endeavor, but it requires careful planning and preparation. Here’s a step-by-step guide to help you get started:
- Define Your Project Scope and Goals:
- Identify the problem or opportunity you want to address with your project.
- Clearly define the objectives and outcomes you aim to achieve.
- Determine the scope of your project, including the technologies, tools, and resources you’ll need.
- Conduct Research:
- Research existing solutions and technologies related to your project idea.
- Identify any gaps or opportunities for innovation in the field.
- Explore relevant literature, academic papers, online resources, and case studies to gain insights and inspiration.
- Choose a Project Topic:
- Based on your research, select a specific topic or area of focus for your project.
- Take into account your passions, abilities, and the assets at your disposal.
- Make sure that the topic you select corresponds with the aims and objectives of your project.
- Develop a Project Plan:
- Make a thorough plan for your project by writing down all the things you need to do, when you need to do them, and what you want to achieve at different points.
- Break the project into smaller parts that are easier to handle, and if you’re working with others, make sure everyone knows what they’re responsible for.
- Define the deliverables and criteria for success for each phase of the project.
- Gather Resources:
- Identify the software, hardware, and other resources you’ll need for your project.
- Set up development environments, programming tools, and any necessary infrastructure.
- Consider collaborating with peers, mentors, or experts who can provide guidance and support.
- Design Your Solution:
- Develop a conceptual design or architecture for your project.
- Define the system requirements, data structures, algorithms, and user interfaces.
- Consider usability, scalability, security, and other factors in your design decisions.
- Implement Your Project:
- Start building your project based on the design and specifications you’ve developed.
- Write code, design user interfaces, implement algorithms, and integrate components as needed.
- Test your project continuously throughout the development process to identify and fix any issues early on.
- Iterate and Refine:
- Iterate on your project based on feedback and testing results.
- Refine your implementation, make improvements, and address any issues or challenges that arise.
- Continuously evaluate your progress against your project plan and adjust as necessary.
- Document Your Work:
- Keep detailed documentation of your project, including design decisions, code comments, and user manuals.
- Document any challenges you faced, solutions you implemented, and lessons learned throughout the project.
- Present Your Project:
- Prepare a presentation or demo showcasing your project’s features, functionality, and achievements.
- Communicate your project’s goals, methodology, results, and impact effectively to your audience.
- Solicit feedback from peers, instructors, or industry professionals to gain insights and improve your project.
By following these steps and staying organized, focused, and adaptable, you can successfully start and complete a CSE project that not only enhances your skills and knowledge but also makes a meaningful contribution to the field of computer science and engineering.
Top 100+ Computer Engineering Project Topics
- Design and Implementation of a Simple CPU
- Development of a Real-time Operating System Kernel
- Construction of a Digital Signal Processor (DSP)
- Designing an FPGA-based Video Processing System
- Building a GPU for Parallel Computing
- Development of a Low-Power Microcontroller System
- Designing an Efficient Cache Memory Architecture
- Construction of a Network-on-Chip (NoC) for Multicore Systems
- Development of a Hardware-based Encryption Engine
- Designing a Reconfigurable Computing Platform
- Building a RISC-V Processor Core
- Development of a Custom Instruction Set Architecture (ISA)
- Designing an Energy-Efficient Embedded System
- Construction of a High-Speed Serial Communication Interface
- Developing a Real-time Embedded System for Robotics
- Designing an IoT-based Home Automation System
- Building a Wearable Health Monitoring Device
- Development of a Wireless Sensor Network for Environmental Monitoring
- Designing an Automotive Control System
- Building a GPS Tracking System for Vehicles
- Development of a Smart Grid Monitoring System
- Designing a Digital Audio Processor for Music Synthesis
- Building a Speech Recognition System
- Developing a Biometric Authentication System
- Designing a Facial Recognition Security System
- Construction of an Autonomous Drone
- Development of a Gesture Recognition Interface
- Designing an Augmented Reality Application
- Building a Virtual Reality Simulator
- Developing a Haptic Feedback System
- Designing a Real-time Video Streaming Platform
- Building a Multimedia Content Delivery Network (CDN)
- Development of a Scalable Web Server Architecture
- Designing a Peer-to-Peer File Sharing System
- Building a Distributed Database Management System
- Developing a Blockchain-based Voting System
- Designing a Secure Cryptocurrency Exchange Platform
- Building an Anonymous Communication Network
- Development of a Secure Email Encryption System
- Designing a Network Intrusion Detection System (NIDS)
- Building a Firewall with Deep Packet Inspection (DPI)
- Developing a Vulnerability Assessment Tool
- Designing a Secure Password Manager Application
- Building a Malware Analysis Sandbox
- Development of a Phishing Detection System
- Designing a Chatbot for Customer Support
- Building a Natural Language Processing (NLP) System
- Developing an AI-powered Personal Assistant
- Designing a Recommendation System for E-commerce
- Building an Intelligent Tutoring System
- Development of a Sentiment Analysis Tool
- Designing an Autonomous Vehicle Navigation System
- Building a Traffic Management System
- Developing a Smart Parking Solution
- Designing a Remote Health Monitoring System
- Building a Telemedicine Platform
- Development of a Medical Image Processing Application
- Designing a Drug Discovery System
- Building a Healthcare Data Analytics Platform
- Developing a Smart Agriculture Solution
- Designing a Crop Monitoring System
- Building an Automated Irrigation System
- Developing a Food Quality Inspection Tool
- Designing a Supply Chain Management System
- Building a Warehouse Automation Solution
- Developing a Inventory Optimization Tool
- Designing a Smart Retail Store System
- Building a Self-checkout System
- Developing a Customer Behavior Analytics Platform
- Designing a Fraud Detection System for Banking
- Building a Risk Management Solution
- Developing a Personal Finance Management Application
- Designing a Stock Market Prediction System
- Building a Portfolio Management Tool
- Developing a Smart Energy Management System
- Designing a Home Energy Monitoring Solution
- Building a Renewable Energy Integration Platform
- Developing a Smart Grid Demand Response System
- Designing a Disaster Management System
- Building an Emergency Response Coordination Tool
- Developing a Weather Prediction and Monitoring System
- Designing a Climate Change Mitigation Solution
- Building a Pollution Monitoring and Control System
- Developing a Waste Management Optimization Tool
- Designing a Smart City Infrastructure Management System
- Building a Traffic Congestion Management Solution
- Developing a Public Safety and Security Platform
- Designing a Citizen Engagement and Participation System
- Building a Smart Transportation Network
- Developing a Smart Water Management System
- Designing a Water Quality Monitoring and Control System
- Building a Flood Detection and Response System
- Developing a Coastal Erosion Prediction Tool
- Designing an Air Quality Monitoring and Control System
- Building a Green Building Energy Optimization Solution
- Developing a Sustainable Transportation Planning Tool
- Designing a Wildlife Conservation Monitoring System
- Building a Biodiversity Mapping and Protection Platform
- Developing a Natural Disaster Early Warning System
- Designing a Remote Sensing and GIS Integration Solution
- Building a Climate Change Adaptation and Resilience Platform
7 Helpful Tips for Final Year Engineering Project
Embarking on a final year engineering project can be both exhilarating and daunting. Here are seven helpful tips to guide you through the process and ensure the success of your project:
Start Early and Plan Thoroughly
- Begin planning your project as soon as possible to allow ample time for research, design, and implementation.
- Break down your project into smaller tasks and create a detailed timeline with milestones to track your progress.
- Consider any potential challenges or obstacles you may encounter and plan contingencies accordingly.
Choose the Right Project
- Select a project that aligns with your interests, skills, and career goals.
- Ensure that the project is feasible within the time and resource constraints of your final year.
- Seek advice from professors, mentors, or industry professionals to help you choose a project that is both challenging and achievable.
Conduct Thorough Research
- Invest time in researching existing solutions, technologies, and literature related to your project idea.
- Identify gaps or opportunities for innovation that your project can address.
- Keep track of relevant papers, articles, and resources to inform your design and implementation decisions.
Communicate Effectively
- Maintain regular communication with your project advisor or supervisor to seek guidance and feedback.
- Collaborate effectively with teammates, if applicable, by establishing clear channels of communication and dividing tasks appropriately.
- Practice effective communication skills when presenting your project to classmates, professors, or industry professionals.
Focus on Quality and Innovation
- Strive for excellence in every aspect of your project, from design and implementation to documentation and presentation.
- Try to come up with new ideas and find ways to make them better than what’s already out there.
- Make sure you do your work carefully and make it the best it can be.
Test and Iterate
- Test your project rigorously throughout the development process to identify and address any issues or bugs.
- Solicit feedback from peers, advisors, or end-users to gain insights and improve your project.
- Iterate on your design and implementation based on feedback and testing results to refine your solution and enhance its functionality.
Manage Your Time Effectively
- Prioritize tasks and allocate time wisely to ensure that you meet deadlines and deliverables.
- Break down larger tasks into smaller, manageable chunks and tackle them one at a time.
- Stay organized with tools such as calendars, to-do lists, and project management software to track your progress and stay on schedule.
By following these tips and staying focused, disciplined, and proactive, you can navigate the challenges of your final year engineering project with confidence and achieve outstanding results. Remember to stay flexible and adaptable, and don’t hesitate to seek help or advice when needed. Good luck!
Computer engineering project topics offer a unique opportunity to blend creativity with technical expertise, empowering enthusiasts to explore diverse domains of computing while tackling real-world challenges. Whether you’re interested in hardware design, software development, networking, or artificial intelligence, there’s a wealth of project topics to inspire innovation and learning.
By starting these projects, people who are passionate about it can improve their abilities, learn more, and add to the changing world of technology. So, get ready to work hard, let your imagination flow, and begin an exciting adventure of learning and discovery in the amazing field of computer engineering.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
Leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
- How it works
Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computing Engineering Dissertation Topics
Published by Jamie Walker at January 10th, 2023 , Revised On August 18, 2023
Over a period of time, dissertations have become an inherent component of higher education studies. They are not only entrenched within the master or a PhD. Degree but also in undergraduate programmes. Computer engineering dissertations allow the researchers to choose a topic of particular interest to them and research further into the topic to add to the current body of literature.
However, choosing a topic from an extensive list of topics is always easier than working on the first topic you find interesting.
To help you get started with brainstorming for computer topic ideas, we have developed a list of the latest computer engineering dissertation topics that can be used for writing your computer engineering dissertation.
These topics have been developed by PhD-qualified writers of our team , so you can trust to use these topics for drafting your dissertation.
You may also want to start your dissertation by requesting a brief research proposal from our writers on any of these topics, which includes an introduction to the problem, research questions , aim and objectives , literature review along with the proposed methodology of research to be conducted. Let us know if you need any help in getting started.
Check our example dissertations to get an idea of how to structure your dissertation .
You can review step by step guide on how to write your dissertation here.
View our free dissertation topics database.
Computer Engineering Dissertation Topics
Computers are the greatest innovation of the modern era and have done wonders for mankind. There is only one language that computers understand; the binary. But there are various high-level coding languages that even computers do not understand and therefore use a compiler for translation.
Computing refers to computer hardware or software coding development technology and covers all aspects of computer technologies. It is the practical and scientific study of the implementation of computing information. Computing is also interchangeably known as computer sciences.
A computing engineer or a computer scientist specializes in practical work, the theory of computing, and the design of computational systems. Essentially, it is the study of structure, expression, mechanization, and feasibility of algorithms (logical procedures) that cause processing, communication, representation, access of information, and acquisition in a computer. This area has a wide range of topics, some of which have been listed below:
- Risk calculation in the application and development process.
- Generation of the java application.
- Implementing a behavioural based approach to detect cheating in online games.
- Analysis of coding environment of different applications.
- Identification of different languages used for coding.
- Identification of stake holder’s interest in App development process.
- Role of visualization in complex hierarchal structures of computing.
- Analysing the requirements of Inventory Management Software.
- Development of single-player simulation game.
- Investigation of web teaching aid system.
- Development of online based library management system.
- Implementation of Electronic banking system.
2022 Computing Engineering Dissertation Topics
Topic 1: an investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility..
Research Aim: This study aims to investigate the applications of blockchain within the energy sector. This study will identify how blockchain can be used to produce electricity from the comfort of home. Moreover, this study aims to introduce the concept of e-mobility through blockchain, according to which blockchain can be used to share the car ride with the other commuters residing at nearby places. Another objective of this research is to develop a framework that could assess blockchain’s use for the consumers staying within a budget and letting them assess how much money they have been spending so far.
Topic 2: Investigating the Issues that Impact Data Security in Cloud-Based Blockchain Technology: An Global Tourism Industry Case Study
Research Aim: This research focuses on a significant shift in trend found in the worldwide tourist business, which is the usage of the cloud for data and services. It attempts to supply the requirements for this implementation owing to the demand for ease, saving, and improved service providing. Furthermore, it will also focus on the limits of traditional blockchain technology primitives and assess control models. These constraints are related to security issues involving data in a cloud environment in the global tourism industry.
Topic 3: Is Digital Technology overtaking Human Interactions in the Medical Fields? An Examination of the Use of Computational biology and Machine Leaning in Patient Diagnosis and Treatment.
Research Aim: The current study seeks to examine how digital technology is replacing human interactions in the medical industry in the importance of computational biology and machine learning in patient diagnosis and treatment. This study will set forth the theoretical foundations and significance of computational biology and machine learning and will also make recommendations for further enhancement.
Topic 4: Evaluating the use of databases and information retrieval systems in the perspective of the United States National security policy.
Research Aim: The current study aims to evaluate the use of databases and information retrieval systems from the perspective of United States national security policy. This study addresses the databases and information retrieval system to provide a clear understanding. It will also focus on specific elements d criteria in the united state’s national security and highlights the benefits and drawbacks of employing them to enhance national security strategy in the united states.
Topic 5: Development of growing infusion of computer technology in the area of medicine- examining NHS policies.
Research Aim: This research aims to examine the development of the growing infusion of computer technology in the area of medicine by evaluating existing NHS policy. The study will provide a theoretical framework for the application of computer science technologies in medicine and will also set out the benefits of using contemporary computer technology as well as analyse the drawbacks that have occurred as a result of the growth of this new technology in this field. It will also focus on the policies employed by NHS to assist the development of technologies in the UK healthcare sector.
Computer Engineering Dissertation Topics for 2021
A 3-d visualization system for ultrasound images.
Research Aim: This research will focus on the visualization of 3-D ultrasound images and their medical therapy benefits.
Reliable and realistic study of remote communication systems in telephony and multipath faded systems
Research Aim: This research’s primary emphasis is on telephony’s practical implementation in a remote communication system.
Establishing a Neural Network Device
Research Aim: In terms of energy efficiency, the human brain is much greater than any modern supercomputer. A whole new generation of energy-efficient, brain-like computers is being designed for this study.
Methods for Artifact EEG Brain function study, caused by sugar, salt, fat, and their replacements
Research Aim: This study relies on the procedure for calculating sweetness taste is developed and validated. Part of the project includes modern electrode technologies to capture the purest possible brain signal from EEG equipment.
Find 100s of dissertation topics in your other academic subjects in our free topics database.
The impact of Covid-19 on tech spends in 2021
Research Aim: This research aims to study the impact of Covid-19 on tech spends in 2021.
Analysis of information system built for e-learning
Research Aim: This research aims to analyze the information system built for e-learning
Advantages and disadvantages of an information system
Research Aim: This research aims to address the advantages and disadvantages of an information system.
Covid-19 Computer Engineering Research Topics
Research to study the effects of coronavirus on it industries.
Research Aim: This research will focus on the impacts of COVID-19 on the growth of IT industries highlighting the issues responsible for it and the possible solutions to overcome them.
Research to identify the impact of Coronavirus on the computer science research community
Research Aim: Coronavirus has infected thousands of people and has been responsible for the deaths of several innocent people worldwide. This study will focus on identifying the effects of this pandemic on the computer science research community.
Research to study the impacts of COVID-19 on tech spends in 2021
Research Aim: As a result of COVID-19, the economy of the entire world has been disrupted. The purpose of this research is to know the tech expenditures after COVID-19 became widespread. How are the tech industries dealing with the challenging situation created by COVID-19?
Research to identify the contribution of computer science to control the spread of Coronavirus pandemic
Research Aim: This research aims at identifying the contributions and efforts made by computer engineers to control the pandemic. What is the role of computer scientists during the pandemic?
Research to identify the unemployment of computer engineers after the Coronavirus pandemic
Research Aim: This research will focus on identifying the increased unemployment issues raised after the COVID-19 pandemic and finding out the possible solutions to overcome the reduced unemployment of computer engineers.
Hardware, Network and Security Dissertation Topics
Network security is very crucial for any organisation. It is dependent upon a well-managed network through the implementation of policies drafted by network administrators to manage the access of the organisational information. Network security provides stability, safety, integrity, reliability, and utility of data and network.
It works efficiently with the latest hardware equipment and updated software. Network security offers many advantages to businesses, such as protection against any disruption to keep employees motivated, energetic, regular, and productive.
In certain instances, a virus may break into the network security. However, the network administrator generally uses an anti-virus program to prevent this sort of attack.
Therefore, it will be fair to say that network security plays a vital role in maintaining a business’s reputation and operations which is the most important asset to any organisation. Below is a list of topics that you can base your dissertation on:
- Performance analysis of transmission control protocol over Ethernet LAN.
- Gateway usage for the intrusion detection system.
- Impact of security machinimas in online transactions.
- Investigation of smart card specification.
- Importance of router placement in the network.
- Level of customer’s trust in E-banking.
- Role of antivirus in a shared network.
- Application of database technologies for data network management.
- Network worm: A headache to networking.
- Implementation of various tools in programming language.
- Study of retroactive data structures.
- Role of Voice over Internet Protocol over Ethernet LAN.
- The usefulness of data transfer security over Wi-Fi Network.
- Influence of signal strength of Wi-Fi upon data transfer.
- Analysis of tree inclusion complexities.
- Analysis of the implementation of the set procedure.
- Analysis of the application of programming tools.
- Implementation of File Sharing System in Network.
- Study of virus behaviours in the secured programming environment.
- Investigation of issues of user’s security and data protection over the network.
- Benefits of network security to customers.
- Improvements of mobile data service for future usage.
- Study of Asymmetry k-center variant.
- Analysis of issues in emerging 4G networks.
- Role of dynamic proxies in a mobile environment to support Remote method Invocation.
Software, Programming and Algorithm Dissertation Topics
In layman language, the software is collectively known as the “combination of operating information and all the programs that are being used by the computer.” It is a set of instructions to direct computers to perform a specific task depending upon thususer’s instructions.
The software can be written in both high and low-level languages. Low-level language is also known as machine code and is faster because it doesn’t require any compiler and directly communicates with the computer. A high-level language is pretty similar to a human language, and therefore can be easily understood by the developers. High-level language requires the compiler to translate commands to the computer.
Programming and algorithms can be termed as commands given to the computer to perform actions. Programming leads to executable programs from a computing problem and involves developing, generating, and analysing algorithms. Algorithms refer to an act done involving a step-by-step process to solve a problem. It is a set of logic written in software.
There are two types of software; operating software that helps in operation and system software necessary to run a system. Operating software can be rewritten and changed according to demand, but system software cannot be altered. If developers require any alterations, they would have to develop new software.
There are various topics that can be considered for research dissertation purposes under this theme, a list of which is given below.
- Application of algorithms.
- Importance of approximation algorithms on graphs.
- Critical analysis of data structures on trees.
- Evaluation and implementation of new algorithms.
- System software: A link to communicate hardware.
- Difference between binary dispatching and multiple dispatching.
- Analysis of plan sweep techniques.
- Investigation of software support to drivers of devices.
- Intelligent interface for database systems.
- Analysis of function and types of union-find.
- The usefulness of different coding languages.
- Application of basic hardware knowledge and math skills.
- Analysis of the design of converter based on new moduli.
- Analysis of information travelling via software.
- Evaluation and implementation of heuristic algorithms.
- Development of applications using Java.
- Analysis of fault tolerance in a network by using simulation.
- Importance of system software for computers.
- Effects of larger integer module operations.
- Consequences of wrong commands in coding.
- Investigation of the coding language of system software.
- Analysis of feasibility environment of platform.
- Evaluation of heuristic algorithms for generating clusters.
- Critical analysis of fixed control variable.
- Analysis of design of converter with large dynamic range.
- Ways to recover corrupted software.
- Analysis of fault tolerance of sorting network.
- Analysis of the difference between LAN and WAN.
- Development of an algorithm for a one-way hashing system.
- Relation between dynamic access and fixed values.
- Importance of right language selection while coding.
- Study of optimization problems.
- Analysis of security frameworks for web services.
- Investigating algorithms techniques.
- Partial persistence of algorithms vs others.
- Study of time and space problems of algorithmic functions.
- Effects of linear and logarithmic factors over programming.
- Discussion about union-find with deletion.
- Importance of data structure for bridge core problems.
- Consequences of fault in interconnected networks.
- Difference between rooted and unrooted tree.
Information Systems Dissertation Topics
Information systems refer to a group of people and computers that are being used for the interpretation of all kinds of information. Computer-based information systems are a very interesting topic for research. It includes all information regarding decision making, management support, and operations and can also be used to access the database.
There is an obvious difference between computer systems, information systems, and business processes. The information system provides the tools to manage businesses successfully.
An information system can be said to be a workstation where humans and machines work together towards the success of a business. One such example is Wal-Mart. The company is entirely based on information systems and has connected its suppliers, vendors, customers and together.
It deals with a large number of data and consists of hardware, software, network, and telecommunications of the operation. Below is a list of research topics in the field of information systems for you to base your dissertation on:
- Analysis of challenges in building information systems for any organisation.
- Impact of cyberinfrastructure on the customer.
- Role of information system in scientific innovations.
- The usefulness of information systems for businesses.
- Advantages of information systems.
- Access to information systems by employees anywhere in the world.
- Preparation of a database management system.
- Analysis and solution of database management systems.
- Study of support of information system to hardware.
- Managing information systems of big stores, The case of Walmart.
- Analysis of information system built for E-learning.
- Critical analysis of the changing nature of the web.
- Role of information system in decision making of disruptions.
- Examine customer response through the information system.
- Investigate the impact of a virus in the network
- Relationship between I.T education and an organization.
- Role of information system in global warming.
- Investigate the reason for adopting green information systems.
- Analysis of the between social networks and information systems.
- Role of information system in dealing with complex business problems.
Important Notes:
As a computing engineering student looking to get good grades, it is essential to develop new ideas and experiment with existing computing engineering theories – i.e., to add value and interest in your research topic.
The field of computing engineering is vast and interrelated to so many other academic disciplines like civil engineering , finance , construction , law , healthcare , mental health , artificial intelligence , tourism , physiotherapy , sociology , management , marketing and nursing . That is why it is imperative to create a project management dissertation topic that is articular, sound, and actually solves a practical problem that may be rampant in the field.
We can’t stress how important it is to develop a logical research topic; it is the basis of your entire research. There are several significant downfalls to getting your topic wrong; your supervisor may not be interested in working on it, the topic has no academic creditability, the research may not make logical sense, there is a possibility that the study is not viable.
This impacts your time and efforts in writing your dissertation as you may end up in the cycle of rejection at the very initial stage of the dissertation. That is why we recommend reviewing existing research to develop a topic, taking advice from your supervisor, and even asking for help in this particular stage of your dissertation.
While developing a research topic, keeping our advice in mind will allow you to pick one of the best computing engineering dissertation topics that fulfill your requirement of writing a research paper and add to the body of knowledge.
Therefore, it is recommended that when finalizing your dissertation topic, you read recently published literature to identify gaps in the research that you may help fill.
Remember- dissertation topics need to be unique, solve an identified problem, be logical, and be practically implemented. Take a look at some of our sample computing engineering dissertation topics to get an idea for your own dissertation.
How to Structure your Dissertation on Computing Engineering
A well-structured dissertation can help students to achieve a high overall academic grade.
- A Title Page
- Acknowledgements
- Declaration
- Abstract: A summary of the research completed
- Table of Contents
- Introduction : This chapter includes the project rationale, research background, key research aims and objectives, and the research problems to be addressed. An outline of the structure of a dissertation can also be added to this chapter.
- Literature Review : This chapter presents relevant theories and frameworks by analysing published and unpublished literature available on the chosen research topic, in light of research questions to be addressed. The purpose is to highlight and discuss the relative weaknesses and strengths of the selected research area whilst identifying any research gaps. Break down of the topic, and key terms can have a positive impact on your dissertation and your tutor.
- Methodology: The data collection and analysis methods and techniques employed by the researcher are presented in the Methodology chapter which usually includes research design, research philosophy, research limitations, code of conduct, ethical consideration, data collection methods and data analysis strategy .
- Findings and Analysis: Findings of the research are analysed in detail under the Findings and Analysis chapter. All key findings/results are outlined in this chapter without interpreting the data or drawing any conclusions. It can be useful to include graphs , charts, and tables in this chapter to identify meaningful trends and relationships.
- Discussion and Conclusion: The researcher presents his interpretation of results in this chapter, and states whether the research hypothesis has been verified or not. An essential aspect of this section of the paper is to draw a linkage between the results and evidence from the literature. Recommendations with regards to implications of the findings and directions for the future may also be provided. Finally, a summary of the overall research, along with final judgments, opinions, and comments, must be included in the form of suggestions for improvement.
- References: This should be completed in accordance with your University’s requirements
- Bibliography
- Appendices: Any additional information, diagrams, graphs that were used to complete the dissertation but not part of the dissertation should be included in the Appendices chapter. Essentially, the purpose is to expand the information/data.
About ResearchProspect Ltd
ResearchProspect is a UK-based academic writing service that provides help with Dissertation Proposal Writing , Ph.D. Proposal Writing , Dissertation Writing , Dissertation Editing and Improvement .
For further assistance with your dissertation, take a look at our full dissertation writing service .
Our team of writers is highly qualified. Our writers are experts in their respective fields. They have been working in the industry for a long time. Thus they are aware of the issues and the trends of the industry they are working in.
Need more Topics.?
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find dissertation topics about computing engineering.
To find computing engineering dissertation topics:
- Explore emerging technologies.
- Investigate industry challenges.
- Review recent research papers.
- Consider AI, cybersecurity, IoT.
- Brainstorm software/hardware innovations.
- Select a topic aligning with your passion and career aspirations.
You May Also Like
Keeping your baby healthy and growing properly starts at birth. Nurses who specialize in child health can help! Nurses who specialize in child health educate parents about safety, hygiene, and nutrition to prevent common childhood illnesses.
Need interesting and manageable Media dissertation topics or thesis? Here are the trending Operations Media dissertation titles so you can choose the most suitable one.
There are a limited number of banking and finance dissertation topics available. This is why we also help students with their finance assignments by providing them with subject ideas.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
Research Topics & Ideas: CompSci & IT
50+ Computer Science Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a computer science-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software engineering.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the CompSci domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: CompSci Research Topics
- Algorithms & data structures
- Artificial intelligence ( AI )
- Computer networking
- Database systems
- Human-computer interaction
- Information security (IS)
- Software engineering
- Examples of CompSci dissertation & theses
Topics/Ideas: Algorithms & Data Structures
- An analysis of neural network algorithms’ accuracy for processing consumer purchase patterns
- A systematic review of the impact of graph algorithms on data analysis and discovery in social media network analysis
- An evaluation of machine learning algorithms used for recommender systems in streaming services
- A review of approximation algorithm approaches for solving NP-hard problems
- An analysis of parallel algorithms for high-performance computing of genomic data
- The influence of data structures on optimal algorithm design and performance in Fintech
- A Survey of algorithms applied in internet of things (IoT) systems in supply-chain management
- A comparison of streaming algorithm performance for the detection of elephant flows
- A systematic review and evaluation of machine learning algorithms used in facial pattern recognition
- Exploring the performance of a decision tree-based approach for optimizing stock purchase decisions
- Assessing the importance of complete and representative training datasets in Agricultural machine learning based decision making.
- A Comparison of Deep learning algorithms performance for structured and unstructured datasets with “rare cases”
- A systematic review of noise reduction best practices for machine learning algorithms in geoinformatics.
- Exploring the feasibility of applying information theory to feature extraction in retail datasets.
- Assessing the use case of neural network algorithms for image analysis in biodiversity assessment
Topics & Ideas: Artificial Intelligence (AI)
- Applying deep learning algorithms for speech recognition in speech-impaired children
- A review of the impact of artificial intelligence on decision-making processes in stock valuation
- An evaluation of reinforcement learning algorithms used in the production of video games
- An exploration of key developments in natural language processing and how they impacted the evolution of Chabots.
- An analysis of the ethical and social implications of artificial intelligence-based automated marking
- The influence of large-scale GIS datasets on artificial intelligence and machine learning developments
- An examination of the use of artificial intelligence in orthopaedic surgery
- The impact of explainable artificial intelligence (XAI) on transparency and trust in supply chain management
- An evaluation of the role of artificial intelligence in financial forecasting and risk management in cryptocurrency
- A meta-analysis of deep learning algorithm performance in predicting and cyber attacks in schools

Topics & Ideas: Networking
- An analysis of the impact of 5G technology on internet penetration in rural Tanzania
- Assessing the role of software-defined networking (SDN) in modern cloud-based computing
- A critical analysis of network security and privacy concerns associated with Industry 4.0 investment in healthcare.
- Exploring the influence of cloud computing on security risks in fintech.
- An examination of the use of network function virtualization (NFV) in telecom networks in Southern America
- Assessing the impact of edge computing on network architecture and design in IoT-based manufacturing
- An evaluation of the challenges and opportunities in 6G wireless network adoption
- The role of network congestion control algorithms in improving network performance on streaming platforms
- An analysis of network coding-based approaches for data security
- Assessing the impact of network topology on network performance and reliability in IoT-based workspaces

Topics & Ideas: Database Systems
- An analysis of big data management systems and technologies used in B2B marketing
- The impact of NoSQL databases on data management and analysis in smart cities
- An evaluation of the security and privacy concerns of cloud-based databases in financial organisations
- Exploring the role of data warehousing and business intelligence in global consultancies
- An analysis of the use of graph databases for data modelling and analysis in recommendation systems
- The influence of the Internet of Things (IoT) on database design and management in the retail grocery industry
- An examination of the challenges and opportunities of distributed databases in supply chain management
- Assessing the impact of data compression algorithms on database performance and scalability in cloud computing
- An evaluation of the use of in-memory databases for real-time data processing in patient monitoring
- Comparing the effects of database tuning and optimization approaches in improving database performance and efficiency in omnichannel retailing
Topics & Ideas: Human-Computer Interaction
- An analysis of the impact of mobile technology on human-computer interaction prevalence in adolescent men
- An exploration of how artificial intelligence is changing human-computer interaction patterns in children
- An evaluation of the usability and accessibility of web-based systems for CRM in the fast fashion retail sector
- Assessing the influence of virtual and augmented reality on consumer purchasing patterns
- An examination of the use of gesture-based interfaces in architecture
- Exploring the impact of ease of use in wearable technology on geriatric user
- Evaluating the ramifications of gamification in the Metaverse
- A systematic review of user experience (UX) design advances associated with Augmented Reality
- A comparison of natural language processing algorithms automation of customer response Comparing end-user perceptions of natural language processing algorithms for automated customer response
- Analysing the impact of voice-based interfaces on purchase practices in the fast food industry

Topics & Ideas: Information Security
- A bibliometric review of current trends in cryptography for secure communication
- An analysis of secure multi-party computation protocols and their applications in cloud-based computing
- An investigation of the security of blockchain technology in patient health record tracking
- A comparative study of symmetric and asymmetric encryption algorithms for instant text messaging
- A systematic review of secure data storage solutions used for cloud computing in the fintech industry
- An analysis of intrusion detection and prevention systems used in the healthcare sector
- Assessing security best practices for IoT devices in political offices
- An investigation into the role social media played in shifting regulations related to privacy and the protection of personal data
- A comparative study of digital signature schemes adoption in property transfers
- An assessment of the security of secure wireless communication systems used in tertiary institutions
Topics & Ideas: Software Engineering
- A study of agile software development methodologies and their impact on project success in pharmacology
- Investigating the impacts of software refactoring techniques and tools in blockchain-based developments
- A study of the impact of DevOps practices on software development and delivery in the healthcare sector
- An analysis of software architecture patterns and their impact on the maintainability and scalability of cloud-based offerings
- A study of the impact of artificial intelligence and machine learning on software engineering practices in the education sector
- An investigation of software testing techniques and methodologies for subscription-based offerings
- A review of software security practices and techniques for protecting against phishing attacks from social media
- An analysis of the impact of cloud computing on the rate of software development and deployment in the manufacturing sector
- Exploring the impact of software development outsourcing on project success in multinational contexts
- An investigation into the effect of poor software documentation on app success in the retail sector
CompSci & IT Dissertations/Theses
While the ideas we’ve presented above are a decent starting point for finding a CompSci-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various CompSci-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- An array-based optimization framework for query processing and data analytics (Chen, 2021)
- Dynamic Object Partitioning and replication for cooperative cache (Asad, 2021)
- Embedding constructural documentation in unit tests (Nassif, 2019)
- PLASA | Programming Language for Synchronous Agents (Kilaru, 2019)
- Healthcare Data Authentication using Deep Neural Network (Sekar, 2020)
- Virtual Reality System for Planetary Surface Visualization and Analysis (Quach, 2019)
- Artificial neural networks to predict share prices on the Johannesburg stock exchange (Pyon, 2021)
- Predicting household poverty with machine learning methods: the case of Malawi (Chinyama, 2022)
- Investigating user experience and bias mitigation of the multi-modal retrieval of historical data (Singh, 2021)
- Detection of HTTPS malware traffic without decryption (Nyathi, 2022)
- Redefining privacy: case study of smart health applications (Al-Zyoud, 2019)
- A state-based approach to context modeling and computing (Yue, 2019)
- A Novel Cooperative Intrusion Detection System for Mobile Ad Hoc Networks (Solomon, 2019)
- HRSB-Tree for Spatio-Temporal Aggregates over Moving Regions (Paduri, 2019)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Fast-Track Your Research Topic
If you’re still feeling a bit unsure about how to find a research topic for your Computer Science dissertation or research project, check out our Topic Kickstarter service.
You Might Also Like:

Investigating the impacts of software refactoring techniques and tools in blockchain-based developments.
Steps on getting this project topic
I want to work with this topic, am requesting materials to guide.
Information Technology -MSc program
It’s really interesting but how can I have access to the materials to guide me through my work?
That’s my problem also.
Investigating the impacts of software refactoring techniques and tools in blockchain-based developments is in my favour. May i get the proper material about that ?
BLOCKCHAIN TECHNOLOGY
I NEED TOPIC
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
Explore your training options in 10 minutes Get Started
- Graduate Stories
- Partner Spotlights
- Bootcamp Prep
- Bootcamp Admissions
- University Bootcamps
- Coding Tools
- Software Engineering
- Web Development
- Data Science
- Tech Guides
- Tech Resources
- Career Advice
- Online Learning
- Internships
- Apprenticeships
- Tech Salaries
- Associate Degree
- Bachelor's Degree
- Master's Degree
- University Admissions
- Best Schools
- Certifications
- Bootcamp Financing
- Higher Ed Financing
- Scholarships
- Financial Aid
- Best Coding Bootcamps
- Best Online Bootcamps
- Best Web Design Bootcamps
- Best Data Science Bootcamps
- Best Technology Sales Bootcamps
- Best Data Analytics Bootcamps
- Best Cybersecurity Bootcamps
- Best Digital Marketing Bootcamps
- Los Angeles
- San Francisco
- Browse All Locations
- Digital Marketing
- Machine Learning
- See All Subjects
- Bootcamps 101
- Full-Stack Development
- Career Changes
- View all Career Discussions
- Mobile App Development
- Cybersecurity
- Product Management
- UX/UI Design
- What is a Coding Bootcamp?
- Are Coding Bootcamps Worth It?
- How to Choose a Coding Bootcamp
- Best Online Coding Bootcamps and Courses
- Best Free Bootcamps and Coding Training
- Coding Bootcamp vs. Community College
- Coding Bootcamp vs. Self-Learning
- Bootcamps vs. Certifications: Compared
- What Is a Coding Bootcamp Job Guarantee?
- How to Pay for Coding Bootcamp
- Ultimate Guide to Coding Bootcamp Loans
- Best Coding Bootcamp Scholarships and Grants
- Education Stipends for Coding Bootcamps
- Get Your Coding Bootcamp Sponsored by Your Employer
- GI Bill and Coding Bootcamps
- Tech Intevriews
- Our Enterprise Solution
- Connect With Us
- Publication
- Reskill America
- Partner With Us
- Resource Center
- Bachelor’s Degree
- Master’s Degree
The Top 10 Most Interesting Computer Science Research Topics
Computer science touches nearly every area of our lives. With new advancements in technology, the computer science field is constantly evolving, giving rise to new computer science research topics. These topics attempt to answer various computer science research questions and how they affect the tech industry and the larger world.
Computer science research topics can be divided into several categories, such as artificial intelligence, big data and data science, human-computer interaction, security and privacy, and software engineering. If you are a student or researcher looking for computer research paper topics. In that case, this article provides some suggestions on examples of computer science research topics and questions.
Find your bootcamp match
What makes a strong computer science research topic.
A strong computer science topic is clear, well-defined, and easy to understand. It should also reflect the research’s purpose, scope, or aim. In addition, a strong computer science research topic is devoid of abbreviations that are not generally known, though, it can include industry terms that are currently and generally accepted.
Tips for Choosing a Computer Science Research Topic
- Brainstorm . Brainstorming helps you develop a few different ideas and find the best topic for you. Some core questions you should ask are, What are some open questions in computer science? What do you want to learn more about? What are some current trends in computer science?
- Choose a sub-field . There are many subfields and career paths in computer science . Before choosing a research topic, ensure that you point out which aspect of computer science the research will focus on. That could be theoretical computer science, contemporary computing culture, or even distributed computing research topics.
- Aim to answer a question . When you’re choosing a research topic in computer science, you should always have a question in mind that you’d like to answer. That helps you narrow down your research aim to meet specified clear goals.
- Do a comprehensive literature review . When starting a research project, it is essential to have a clear idea of the topic you plan to study. That involves doing a comprehensive literature review to better understand what has been learned about your topic in the past.
- Keep the topic simple and clear. The topic should reflect the scope and aim of the research it addresses. It should also be concise and free of ambiguous words. Hence, some researchers recommended that the topic be limited to five to 15 substantive words. It can take the form of a question or a declarative statement.
What’s the Difference Between a Research Topic and a Research Question?
A research topic is the subject matter that a researcher chooses to investigate. You may also refer to it as the title of a research paper. It summarizes the scope of the research and captures the researcher’s approach to the research question. Hence, it may be broad or more specific. For example, a broad topic may read, Data Protection and Blockchain, while a more specific variant can read, Potential Strategies to Privacy Issues on the Blockchain.
On the other hand, a research question is the fundamental starting point for any research project. It typically reflects various real-world problems and, sometimes, theoretical computer science challenges. As such, it must be clear, concise, and answerable.
How to Create Strong Computer Science Research Questions
To create substantial computer science research questions, one must first understand the topic at hand. Furthermore, the research question should generate new knowledge and contribute to the advancement of the field. It could be something that has not been answered before or is only partially answered. It is also essential to consider the feasibility of answering the question.
Top 10 Computer Science Research Paper Topics
1. battery life and energy storage for 5g equipment.
The 5G network is an upcoming cellular network with much higher data rates and capacity than the current 4G network. According to research published in the European Scientific Institute Journal, one of the main concerns with the 5G network is the high energy consumption of the 5G-enabled devices . Hence, this research on this topic can highlight the challenges and proffer unique solutions to make more energy-efficient designs.
2. The Influence of Extraction Methods on Big Data Mining
Data mining has drawn the scientific community’s attention, especially with the explosive rise of big data. Many research results prove that the extraction methods used have a significant effect on the outcome of the data mining process. However, a topic like this analyzes algorithms. It suggests strategies and efficient algorithms that may help understand the challenge or lead the way to find a solution.
3. Integration of 5G with Analytics and Artificial Intelligence
According to the International Finance Corporation, 5G and AI technologies are defining emerging markets and our world. Through different technologies, this research aims to find novel ways to integrate these powerful tools to produce excellent results. Subjects like this often spark great discoveries that pioneer new levels of research and innovation. A breakthrough can influence advanced educational technology, virtual reality, metaverse, and medical imaging.
4. Leveraging Asynchronous FPGAs for Crypto Acceleration
To support the growing cryptocurrency industry, there is a need to create new ways to accelerate transaction processing. This project aims to use asynchronous Field-Programmable Gate Arrays (FPGAs) to accelerate cryptocurrency transaction processing. It explores how various distributed computing technologies can influence mining cryptocurrencies faster with FPGAs and generally enjoy faster transactions.
5. Cyber Security Future Technologies
Cyber security is a trending topic among businesses and individuals, especially as many work teams are going remote. Research like this can stretch the length and breadth of the cyber security and cloud security industries and project innovations depending on the researcher’s preferences. Another angle is to analyze existing or emerging solutions and present discoveries that can aid future research.
6. Exploring the Boundaries Between Art, Media, and Information Technology
The field of computers and media is a vast and complex one that intersects in many ways. They create images or animations using design technology like algorithmic mechanism design, design thinking, design theory, digital fabrication systems, and electronic design automation. This paper aims to define how both fields exist independently and symbiotically.
7. Evolution of Future Wireless Networks Using Cognitive Radio Networks
This research project aims to study how cognitive radio technology can drive evolution in future wireless networks. It will analyze the performance of cognitive radio-based wireless networks in different scenarios and measure its impact on spectral efficiency and network capacity. The research project will involve the development of a simulation model for studying the performance of cognitive radios in different scenarios.
8. The Role of Quantum Computing and Machine Learning in Advancing Medical Predictive Systems
In a paper titled Exploring Quantum Computing Use Cases for Healthcare , experts at IBM highlighted precision medicine and diagnostics to benefit from quantum computing. Using biomedical imaging, machine learning, computational biology, and data-intensive computing systems, researchers can create more accurate disease progression prediction, disease severity classification systems, and 3D Image reconstruction systems vital for treating chronic diseases.
9. Implementing Privacy and Security in Wireless Networks
Wireless networks are prone to attacks, and that has been a big concern for both individual users and organizations. According to the Cyber Security and Infrastructure Security Agency CISA, cyber security specialists are working to find reliable methods of securing wireless networks . This research aims to develop a secure and privacy-preserving communication framework for wireless communication and social networks.
10. Exploring the Challenges and Potentials of Biometric Systems Using Computational Techniques
Much discussion surrounds biometric systems and the potential for misuse and privacy concerns. When exploring how biometric systems can be effectively used, issues such as verification time and cost, hygiene, data bias, and cultural acceptance must be weighed. The paper may take a critical study into the various challenges using computational tools and predict possible solutions.
Other Examples of Computer Science Research Topics & Questions
Computer research topics.
- The confluence of theoretical computer science, deep learning, computational algorithms, and performance computing
- Exploring human-computer interactions and the importance of usability in operating systems
- Predicting the limits of networking and distributed systems
- Controlling data mining on public systems through third-party applications
- The impact of green computing on the environment and computational science
Computer Research Questions
- Why are there so many programming languages?
- Is there a better way to enhance human-computer interactions in computer-aided learning?
- How safe is cloud computing, and what are some ways to enhance security?
- Can computers effectively assist in the sequencing of human genes?
- How valuable is SCRUM methodology in Agile software development?
Choosing the Right Computer Science Research Topic
Computer science research is a vast field, and it can be challenging to choose the right topic. There are a few things to keep in mind when making this decision. Choose a topic that you are interested in. This will make it easier to stay motivated and produce high-quality research for your computer science degree .
Select a topic that is relevant to your field of study. This will help you to develop specialized knowledge in the area. Choose a topic that has potential for future research. This will ensure that your research is relevant and up-to-date. Typically, coding bootcamps provide a framework that streamlines students’ projects to a specific field, doing their search for a creative solution more effortless.
Computer Science Research Topics FAQ
To start a computer science research project, you should look at what other content is out there. Complete a literature review to know the available findings surrounding your idea. Design your research and ensure that you have the necessary skills and resources to complete the project.
The first step to conducting computer science research is to conceptualize the idea and review existing knowledge about that subject. You will design your research and collect data through surveys or experiments. Analyze your data and build a prototype or graphical model. You will also write a report and present it to a recognized body for review and publication.
You can find computer science research jobs on the job boards of many universities. Many universities have job boards on their websites that list open positions in research and academia. Also, many Slack and GitHub channels for computer scientists provide regular updates on available projects.
There are several hot topics and questions in AI that you can build your research on. Below are some AI research questions you may consider for your research paper.
- Will it be possible to build artificial emotional intelligence?
- Will robots replace humans in all difficult cumbersome jobs as part of the progress of civilization?
- Can artificial intelligence systems self-improve with knowledge from the Internet?
About us: Career Karma is a platform designed to help job seekers find, research, and connect with job training programs to advance their careers. Learn about the CK publication .
What's Next?
Get matched with top bootcamps
Ask a question to our community, take our careers quiz.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *


- Advisers & Contacts
- Bachelor of Arts & Bachelor of Science in Engineering
- Prerequisites
- Declaring Computer Science for AB Students
- Declaring Computer Science for BSE Students
- Class of '25, '26 & '27 - Departmental Requirements
- Class of 2024 - Departmental Requirements
- COS126 Information
- Important Steps and Deadlines
- Independent Work Seminars
- Guidelines and Useful Information
Undergraduate Research Topics
- AB Junior Research Workshops
- Undergraduate Program FAQ
- How to Enroll
- Requirements
- Certificate Program FAQ
- Interdepartmental Committee
- Minor Program
- Funding for Student Group Activities
- Mailing Lists and Policies
- Study Abroad
- Jobs & Careers
- Admissions Requirements
- Breadth Requirements
- Pre-FPO Checklist
- FPO Checklist
- M.S.E. Track
- M.Eng. Track
- Departmental Internship Policy (for Master's students)
- General Examination
- Fellowship Opportunities
- Travel Reimbursement Policy
- Communication Skills
- Course Schedule
- Course Catalog
- Research Areas
- Interdisciplinary Programs
- Technical Reports
- Computing Facilities
- Researchers
- Technical Staff
- Administrative Staff
- Graduate Students
- Undergraduate Students
- Graduate Alumni
- Climate and Inclusion Committee
- Resources for Undergraduate & Graduate Students
- Outreach Initiatives
- Resources for Faculty & Staff
- Spotlight Stories
- Job Openings
- Undergraduate Program
- Independent Work & Theses
Suggested Undergraduate Research Topics

How to Contact Faculty for IW/Thesis Advising
Send the professor an e-mail. When you write a professor, be clear that you want a meeting regarding a senior thesis or one-on-one IW project, and briefly describe the topic or idea that you want to work on. Check the faculty listing for email addresses.
Parastoo Abtahi, Room 419
Available for single-semester IW and senior thesis advising, 2024-2025
- Research Areas: Human-Computer Interaction (HCI), Augmented Reality (AR), and Spatial Computing
- Input techniques for on-the-go interaction (e.g., eye-gaze, microgestures, voice) with a focus on uncertainty, disambiguation, and privacy.
- Minimal and timely multisensory output (e.g., spatial audio, haptics) that enables users to attend to their physical environment and the people around them, instead of a 2D screen.
- Interaction with intelligent systems (e.g., IoT, robots) situated in physical spaces with a focus on updating users’ mental model despite the complexity and dynamicity of these systems.
Ryan Adams, Room 411
Research areas:
- Machine learning driven design
- Generative models for structured discrete objects
- Approximate inference in probabilistic models
- Accelerating solutions to partial differential equations
- Innovative uses of automatic differentiation
- Modeling and optimizing 3d printing and CNC machining
Andrew Appel, Room 209
Available for Fall 2024 IW advising, only
- Research Areas: Formal methods, programming languages, compilers, computer security.
- Software verification (for which taking COS 326 / COS 510 is helpful preparation)
- Game theory of poker or other games (for which COS 217 / 226 are helpful)
- Computer game-playing programs (for which COS 217 / 226)
- Risk-limiting audits of elections (for which ORF 245 or other knowledge of probability is useful)
Sanjeev Arora, Room 407
- Theoretical machine learning, deep learning and its analysis, natural language processing. My advisees would typically have taken a course in algorithms (COS423 or COS 521 or equivalent) and a course in machine learning.
- Show that finding approximate solutions to NP-complete problems is also NP-complete (i.e., come up with NP-completeness reductions a la COS 487).
- Experimental Algorithms: Implementing and Evaluating Algorithms using existing software packages.
- Studying/designing provable algorithms for machine learning and implementions using packages like scipy and MATLAB, including applications in Natural language processing and deep learning.
- Any topic in theoretical computer science.
David August, Room 221
Not available for IW or thesis advising, 2024-2025
- Research Areas: Computer Architecture, Compilers, Parallelism
- Containment-based approaches to security: We have designed and tested a simple hardware+software containment mechanism that stops incorrect communication resulting from faults, bugs, or exploits from leaving the system. Let's explore ways to use containment to solve real problems. Expect to work with corporate security and technology decision-makers.
- Parallelism: Studies show much more parallelism than is currently realized in compilers and architectures. Let's find ways to realize this parallelism.
- Any other interesting topic in computer architecture or compilers.
Mark Braverman, 194 Nassau St., Room 231
- Research Areas: computational complexity, algorithms, applied probability, computability over the real numbers, game theory and mechanism design, information theory.
- Topics in computational and communication complexity.
- Applications of information theory in complexity theory.
- Algorithms for problems under real-life assumptions.
- Game theory, network effects
- Mechanism design (could be on a problem proposed by the student)
Sebastian Caldas, 221 Nassau Street, Room 105
- Research Areas: collaborative learning, machine learning for healthcare. Typically, I will work with students that have taken COS324.
- Methods for collaborative and continual learning.
- Machine learning for healthcare applications.
Bernard Chazelle, 194 Nassau St., Room 301
- Research Areas: Natural Algorithms, Computational Geometry, Sublinear Algorithms.
- Natural algorithms (flocking, swarming, social networks, etc).
- Sublinear algorithms
- Self-improving algorithms
- Markov data structures
Danqi Chen, Room 412
- My advisees would be expected to have taken a course in machine learning and ideally have taken COS484 or an NLP graduate seminar.
- Representation learning for text and knowledge bases
- Pre-training and transfer learning
- Question answering and reading comprehension
- Information extraction
- Text summarization
- Any other interesting topics related to natural language understanding/generation
Marcel Dall'Agnol, Corwin 034
- Research Areas: Theoretical computer science. (Specifically, quantum computation, sublinear algorithms, complexity theory, interactive proofs and cryptography)
- Research Areas: Machine learning
Jia Deng, Room 423
- Research Areas: Computer Vision, Machine Learning.
- Object recognition and action recognition
- Deep Learning, autoML, meta-learning
- Geometric reasoning, logical reasoning
Adji Bousso Dieng, Room 406
- Research areas: Vertaix is a research lab at Princeton University led by Professor Adji Bousso Dieng. We work at the intersection of artificial intelligence (AI) and the natural sciences. The models and algorithms we develop are motivated by problems in those domains and contribute to advancing methodological research in AI. We leverage tools in statistical machine learning and deep learning in developing methods for learning with the data, of various modalities, arising from the natural sciences.
Robert Dondero, Corwin Hall, Room 038
- Research Areas: Software engineering; software engineering education.
- Develop or evaluate tools to facilitate student learning in undergraduate computer science courses at Princeton, and beyond.
- In particular, can code critiquing tools help students learn about software quality?
Zeev Dvir, 194 Nassau St., Room 250
- Research Areas: computational complexity, pseudo-randomness, coding theory and discrete mathematics.
- Independent Research: I have various research problems related to Pseudorandomness, Coding theory, Complexity and Discrete mathematics - all of which require strong mathematical background. A project could also be based on writing a survey paper describing results from a few theory papers revolving around some particular subject.
Benjamin Eysenbach, Room 416
- Research areas: reinforcement learning, machine learning. My advisees would typically have taken COS324.
- Using RL algorithms to applications in science and engineering.
- Emergent behavior of RL algorithms on high-fidelity robotic simulators.
- Studying how architectures and representations can facilitate generalization.
Christiane Fellbaum, 1-S-14 Green
- Research Areas: theoretical and computational linguistics, word sense disambiguation, lexical resource construction, English and multilingual WordNet(s), ontology
- Anything having to do with natural language--come and see me with/for ideas suitable to your background and interests. Some topics students have worked on in the past:
- Developing parsers, part-of-speech taggers, morphological analyzers for underrepresented languages (you don't have to know the language to develop such tools!)
- Quantitative approaches to theoretical linguistics questions
- Extensions and interfaces for WordNet (English and WN in other languages),
- Applications of WordNet(s), including:
- Foreign language tutoring systems,
- Spelling correction software,
- Word-finding/suggestion software for ordinary users and people with memory problems,
- Machine Translation
- Sentiment and Opinion detection
- Automatic reasoning and inferencing
- Collaboration with professors in the social sciences and humanities ("Digital Humanities")
Adam Finkelstein, Room 424
- Research Areas: computer graphics, audio.
Robert S. Fish, Corwin Hall, Room 037
- Networking and telecommunications
- Learning, perception, and intelligence, artificial and otherwise;
- Human-computer interaction and computer-supported cooperative work
- Online education, especially in Computer Science Education
- Topics in research and development innovation methodologies including standards, open-source, and entrepreneurship
- Distributed autonomous organizations and related blockchain technologies
Michael Freedman, Room 308
- Research Areas: Distributed systems, security, networking
- Projects related to streaming data analysis, datacenter systems and networks, untrusted cloud storage and applications. Please see my group website at http://sns.cs.princeton.edu/ for current research projects.
Ruth Fong, Room 032
- Research Areas: computer vision, machine learning, deep learning, interpretability, explainable AI, fairness and bias in AI
- Develop a technique for understanding AI models
- Design a AI model that is interpretable by design
- Build a paradigm for detecting and/or correcting failure points in an AI model
- Analyze an existing AI model and/or dataset to better understand its failure points
- Build a computer vision system for another domain (e.g., medical imaging, satellite data, etc.)
- Develop a software package for explainable AI
- Adapt explainable AI research to a consumer-facing problem
Note: I am happy to advise any project if there's a sufficient overlap in interest and/or expertise; please reach out via email to chat about project ideas.
Tom Griffiths, Room 405
Available for Fall 2024 single-semester IW advising, only
Research areas: computational cognitive science, computational social science, machine learning and artificial intelligence
Note: I am open to projects that apply ideas from computer science to understanding aspects of human cognition in a wide range of areas, from decision-making to cultural evolution and everything in between. For example, we have current projects analyzing chess game data and magic tricks, both of which give us clues about how human minds work. Students who have expertise or access to data related to games, magic, strategic sports like fencing, or other quantifiable domains of human behavior feel free to get in touch.
Aarti Gupta, Room 220
- Research Areas: Formal methods, program analysis, logic decision procedures
- Finding bugs in open source software using automatic verification tools
- Software verification (program analysis, model checking, test generation)
- Decision procedures for logical reasoning (SAT solvers, SMT solvers)
Elad Hazan, Room 409
- Research interests: machine learning methods and algorithms, efficient methods for mathematical optimization, regret minimization in games, reinforcement learning, control theory and practice
- Machine learning, efficient methods for mathematical optimization, statistical and computational learning theory, regret minimization in games.
- Implementation and algorithm engineering for control, reinforcement learning and robotics
- Implementation and algorithm engineering for time series prediction
Felix Heide, Room 410
- Research Areas: Computational Imaging, Computer Vision, Machine Learning (focus on Optimization and Approximate Inference).
- Optical Neural Networks
- Hardware-in-the-loop Holography
- Zero-shot and Simulation-only Learning
- Object recognition in extreme conditions
- 3D Scene Representations for View Generation and Inverse Problems
- Long-range Imaging in Scattering Media
- Hardware-in-the-loop Illumination and Sensor Optimization
- Inverse Lidar Design
- Phase Retrieval Algorithms
- Proximal Algorithms for Learning and Inference
- Domain-Specific Language for Optics Design
Peter Henderson , 302 Sherrerd Hall
- Research Areas: Machine learning, law, and policy
Kyle Jamieson, Room 306
- Research areas: Wireless and mobile networking; indoor radar and indoor localization; Internet of Things
- See other topics on my independent work ideas page (campus IP and CS dept. login req'd)
Alan Kaplan, 221 Nassau Street, Room 105
Research Areas:
- Random apps of kindness - mobile application/technology frameworks used to help individuals or communities; topic areas include, but are not limited to: first response, accessibility, environment, sustainability, social activism, civic computing, tele-health, remote learning, crowdsourcing, etc.
- Tools automating programming language interoperability - Java/C++, React Native/Java, etc.
- Software visualization tools for education
- Connected consumer devices, applications and protocols
Brian Kernighan, Room 311
- Research Areas: application-specific languages, document preparation, user interfaces, software tools, programming methodology
- Application-oriented languages, scripting languages.
- Tools; user interfaces
- Digital humanities
Zachary Kincaid, Room 219
- Research areas: programming languages, program analysis, program verification, automated reasoning
- Independent Research Topics:
- Develop a practical algorithm for an intractable problem (e.g., by developing practical search heuristics, or by reducing to, or by identifying a tractable sub-problem, ...).
- Design a domain-specific programming language, or prototype a new feature for an existing language.
- Any interesting project related to programming languages or logic.
Gillat Kol, Room 316
Aleksandra korolova, 309 sherrerd hall.
- Research areas: Societal impacts of algorithms and AI; privacy; fair and privacy-preserving machine learning; algorithm auditing.
Advisees typically have taken one or more of COS 226, COS 324, COS 423, COS 424 or COS 445.
Pravesh Kothari, Room 320
- Research areas: Theory
Amit Levy, Room 307
- Research Areas: Operating Systems, Distributed Systems, Embedded Systems, Internet of Things
- Distributed hardware testing infrastructure
- Second factor security tokens
- Low-power wireless network protocol implementation
- USB device driver implementation
Kai Li, Room 321
- Research Areas: Distributed systems; storage systems; content-based search and data analysis of large datasets.
- Fast communication mechanisms for heterogeneous clusters.
- Approximate nearest-neighbor search for high dimensional data.
- Data analysis and prediction of in-patient medical data.
- Optimized implementation of classification algorithms on manycore processors.
Xiaoyan Li, 221 Nassau Street, Room 104
- Research areas: Information retrieval, novelty detection, question answering, AI, machine learning and data analysis.
- Explore new statistical retrieval models for document retrieval and question answering.
- Apply AI in various fields.
- Apply supervised or unsupervised learning in health, education, finance, and social networks, etc.
- Any interesting project related to AI, machine learning, and data analysis.
Lydia Liu, Room 414
- Research Areas: algorithmic decision making, machine learning and society
- Theoretical foundations for algorithmic decision making (e.g. mathematical modeling of data-driven decision processes, societal level dynamics)
- Societal impacts of algorithms and AI through a socio-technical lens (e.g. normative implications of worst case ML metrics, prediction and model arbitrariness)
- Machine learning for social impact domains, especially education (e.g. responsible development and use of LLMs for education equity and access)
- Evaluation of human-AI decision making using statistical methods (e.g. causal inference of long term impact)
Wyatt Lloyd, Room 323
- Research areas: Distributed Systems
- Caching algorithms and implementations
- Storage systems
- Distributed transaction algorithms and implementations
Alex Lombardi , Room 312
- Research Areas: Theory
Margaret Martonosi, Room 208
- Quantum Computing research, particularly related to architecture and compiler issues for QC.
- Computer architectures specialized for modern workloads (e.g., graph analytics, machine learning algorithms, mobile applications
- Investigating security and privacy vulnerabilities in computer systems, particularly IoT devices.
- Other topics in computer architecture or mobile / IoT systems also possible.
Jonathan Mayer, Sherrerd Hall, Room 307
Available for Spring 2025 single-semester IW, only
- Research areas: Technology law and policy, with emphasis on national security, criminal procedure, consumer privacy, network management, and online speech.
- Assessing the effects of government policies, both in the public and private sectors.
- Collecting new data that relates to government decision making, including surveying current business practices and studying user behavior.
- Developing new tools to improve government processes and offer policy alternatives.
Mae Milano, Room 307
- Local-first / peer-to-peer systems
- Wide-ares storage systems
- Consistency and protocol design
- Type-safe concurrency
- Language design
- Gradual typing
- Domain-specific languages
- Languages for distributed systems
Andrés Monroy-Hernández, Room 405
- Research Areas: Human-Computer Interaction, Social Computing, Public-Interest Technology, Augmented Reality, Urban Computing
- Research interests:developing public-interest socio-technical systems. We are currently creating alternatives to gig work platforms that are more equitable for all stakeholders. For instance, we are investigating the socio-technical affordances necessary to support a co-op food delivery network owned and managed by workers and restaurants. We are exploring novel system designs that support self-governance, decentralized/federated models, community-centered data ownership, and portable reputation systems. We have opportunities for students interested in human-centered computing, UI/UX design, full-stack software development, and qualitative/quantitative user research.
- Beyond our core projects, we are open to working on research projects that explore the use of emerging technologies, such as AR, wearables, NFTs, and DAOs, for creative and out-of-the-box applications.
Christopher Moretti, Corwin Hall, Room 036
- Research areas: Distributed systems, high-throughput computing, computer science/engineering education
- Expansion, improvement, and evaluation of open-source distributed computing software.
- Applications of distributed computing for "big science" (e.g. biometrics, data mining, bioinformatics)
- Software and best practices for computer science education and study, especially Princeton's 126/217/226 sequence or MOOCs development
- Sports analytics and/or crowd-sourced computing
Radhika Nagpal, F316 Engineering Quadrangle
- Research areas: control, robotics and dynamical systems
Karthik Narasimhan, Room 422
- Research areas: Natural Language Processing, Reinforcement Learning
- Autonomous agents for text-based games ( https://www.microsoft.com/en-us/research/project/textworld/ )
- Transfer learning/generalization in NLP
- Techniques for generating natural language
- Model-based reinforcement learning
Arvind Narayanan, 308 Sherrerd Hall
Research Areas: fair machine learning (and AI ethics more broadly), the social impact of algorithmic systems, tech policy
Pedro Paredes, Corwin Hall, Room 041
My primary research work is in Theoretical Computer Science.
* Research Interest: Spectral Graph theory, Pseudorandomness, Complexity theory, Coding Theory, Quantum Information Theory, Combinatorics.
The IW projects I am interested in advising can be divided into three categories:
1. Theoretical research
I am open to advise work on research projects in any topic in one of my research areas of interest. A project could also be based on writing a survey given results from a few papers. Students should have a solid background in math (e.g., elementary combinatorics, graph theory, discrete probability, basic algebra/calculus) and theoretical computer science (226 and 240 material, like big-O/Omega/Theta, basic complexity theory, basic fundamental algorithms). Mathematical maturity is a must.
A (non exhaustive) list of topics of projects I'm interested in: * Explicit constructions of better vertex expanders and/or unique neighbor expanders. * Construction deterministic or random high dimensional expanders. * Pseudorandom generators for different problems. * Topics around the quantum PCP conjecture. * Topics around quantum error correcting codes and locally testable codes, including constructions, encoding and decoding algorithms.
2. Theory informed practical implementations of algorithms Very often the great advances in theoretical research are either not tested in practice or not even feasible to be implemented in practice. Thus, I am interested in any project that consists in trying to make theoretical ideas applicable in practice. This includes coming up with new algorithms that trade some theoretical guarantees for feasible implementation yet trying to retain the soul of the original idea; implementing new algorithms in a suitable programming language; and empirically testing practical implementations and comparing them with benchmarks / theoretical expectations. A project in this area doesn't have to be in my main areas of research, any theoretical result could be suitable for such a project.
Some examples of areas of interest: * Streaming algorithms. * Numeric linear algebra. * Property testing. * Parallel / Distributed algorithms. * Online algorithms. 3. Machine learning with a theoretical foundation
I am interested in projects in machine learning that have some mathematical/theoretical, even if most of the project is applied. This includes topics like mathematical optimization, statistical learning, fairness and privacy.
One particular area I have been recently interested in is in the area of rating systems (e.g., Chess elo) and applications of this to experts problems.
Final Note: I am also willing to advise any project with any mathematical/theoretical component, even if it's not the main one; please reach out via email to chat about project ideas.
Iasonas Petras, Corwin Hall, Room 033
- Research Areas: Information Based Complexity, Numerical Analysis, Quantum Computation.
- Prerequisites: Reasonable mathematical maturity. In case of a project related to Quantum Computation a certain familiarity with quantum mechanics is required (related courses: ELE 396/PHY 208).
- Possible research topics include:
1. Quantum algorithms and circuits:
- i. Design or simulation quantum circuits implementing quantum algorithms.
- ii. Design of quantum algorithms solving/approximating continuous problems (such as Eigenvalue problems for Partial Differential Equations).
2. Information Based Complexity:
- i. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems in various settings (for example worst case or average case).
- ii. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems under new tractability and error criteria.
- iii. Necessary and sufficient conditions for tractability of Weighted problems.
- iv. Necessary and sufficient conditions for tractability of Weighted Problems under new tractability and error criteria.
3. Topics in Scientific Computation:
- i. Randomness, Pseudorandomness, MC and QMC methods and their applications (Finance, etc)
Yuri Pritykin, 245 Carl Icahn Lab
- Research interests: Computational biology; Cancer immunology; Regulation of gene expression; Functional genomics; Single-cell technologies.
- Potential research projects: Development, implementation, assessment and/or application of algorithms for analysis, integration, interpretation and visualization of multi-dimensional data in molecular biology, particularly single-cell and spatial genomics data.
Benjamin Raphael, Room 309
- Research interests: Computational biology and bioinformatics; Cancer genomics; Algorithms and machine learning approaches for analysis of large-scale datasets
- Implementation and application of algorithms to infer evolutionary processes in cancer
- Identifying correlations between combinations of genomic mutations in human and cancer genomes
- Design and implementation of algorithms for genome sequencing from new DNA sequencing technologies
- Graph clustering and network anomaly detection, particularly using diffusion processes and methods from spectral graph theory
Vikram Ramaswamy, 035 Corwin Hall
- Research areas: Interpretability of AI systems, Fairness in AI systems, Computer vision.
- Constructing a new method to explain a model / create an interpretable by design model
- Analyzing a current model / dataset to understand bias within the model/dataset
- Proposing new fairness evaluations
- Proposing new methods to train to improve fairness
- Developing synthetic datasets for fairness / interpretability benchmarks
- Understanding robustness of models
Ran Raz, Room 240
- Research Area: Computational Complexity
- Independent Research Topics: Computational Complexity, Information Theory, Quantum Computation, Theoretical Computer Science
Szymon Rusinkiewicz, Room 406
- Research Areas: computer graphics; computer vision; 3D scanning; 3D printing; robotics; documentation and visualization of cultural heritage artifacts
- Research ways of incorporating rotation invariance into computer visiontasks such as feature matching and classification
- Investigate approaches to robust 3D scan matching
- Model and compensate for imperfections in 3D printing
- Given a collection of small mobile robots, apply control policies learned in simulation to the real robots.
Olga Russakovsky, Room 408
- Research Areas: computer vision, machine learning, deep learning, crowdsourcing, fairness&bias in AI
- Design a semantic segmentation deep learning model that can operate in a zero-shot setting (i.e., recognize and segment objects not seen during training)
- Develop a deep learning classifier that is impervious to protected attributes (such as gender or race) that may be erroneously correlated with target classes
- Build a computer vision system for the novel task of inferring what object (or part of an object) a human is referring to when pointing to a single pixel in the image. This includes both collecting an appropriate dataset using crowdsourcing on Amazon Mechanical Turk, creating a new deep learning formulation for this task, and running extensive analysis of both the data and the model
Sebastian Seung, Princeton Neuroscience Institute, Room 153
- Research Areas: computational neuroscience, connectomics, "deep learning" neural networks, social computing, crowdsourcing, citizen science
- Gamification of neuroscience (EyeWire 2.0)
- Semantic segmentation and object detection in brain images from microscopy
- Computational analysis of brain structure and function
- Neural network theories of brain function
Jaswinder Pal Singh, Room 324
- Research Areas: Boundary of technology and business/applications; building and scaling technology companies with special focus at that boundary; parallel computing systems and applications: parallel and distributed applications and their implications for software and architectural design; system software and programming environments for multiprocessors.
- Develop a startup company idea, and build a plan/prototype for it.
- Explore tradeoffs at the boundary of technology/product and business/applications in a chosen area.
- Study and develop methods to infer insights from data in different application areas, from science to search to finance to others.
- Design and implement a parallel application. Possible areas include graphics, compression, biology, among many others. Analyze performance bottlenecks using existing tools, and compare programming models/languages.
- Design and implement a scalable distributed algorithm.
Mona Singh, Room 420
- Research Areas: computational molecular biology, as well as its interface with machine learning and algorithms.
- Whole and cross-genome methods for predicting protein function and protein-protein interactions.
- Analysis and prediction of biological networks.
- Computational methods for inferring specific aspects of protein structure from protein sequence data.
- Any other interesting project in computational molecular biology.
Robert Tarjan, 194 Nassau St., Room 308
- Research Areas: Data structures; graph algorithms; combinatorial optimization; computational complexity; computational geometry; parallel algorithms.
- Implement one or more data structures or combinatorial algorithms to provide insight into their empirical behavior.
- Design and/or analyze various data structures and combinatorial algorithms.
Olga Troyanskaya, Room 320
- Research Areas: Bioinformatics; analysis of large-scale biological data sets (genomics, gene expression, proteomics, biological networks); algorithms for integration of data from multiple data sources; visualization of biological data; machine learning methods in bioinformatics.
- Implement and evaluate one or more gene expression analysis algorithm.
- Develop algorithms for assessment of performance of genomic analysis methods.
- Develop, implement, and evaluate visualization tools for heterogeneous biological data.
David Walker, Room 211
- Research Areas: Programming languages, type systems, compilers, domain-specific languages, software-defined networking and security
- Independent Research Topics: Any other interesting project that involves humanitarian hacking, functional programming, domain-specific programming languages, type systems, compilers, software-defined networking, fault tolerance, language-based security, theorem proving, logic or logical frameworks.
Shengyi Wang, Postdoctoral Research Associate, Room 216
Available for Fall 2024 single-semester IW, only
- Independent Research topics: Explore Escher-style tilings using (introductory) group theory and automata theory to produce beautiful pictures.
Kevin Wayne, Corwin Hall, Room 040
- Research Areas: design, analysis, and implementation of algorithms; data structures; combinatorial optimization; graphs and networks.
- Design and implement computer visualizations of algorithms or data structures.
- Develop pedagogical tools or programming assignments for the computer science curriculum at Princeton and beyond.
- Develop assessment infrastructure and assessments for MOOCs.
Matt Weinberg, 194 Nassau St., Room 222
- Research Areas: algorithms, algorithmic game theory, mechanism design, game theoretical problems in {Bitcoin, networking, healthcare}.
- Theoretical questions related to COS 445 topics such as matching theory, voting theory, auction design, etc.
- Theoretical questions related to incentives in applications like Bitcoin, the Internet, health care, etc. In a little bit more detail: protocols for these systems are often designed assuming that users will follow them. But often, users will actually be strictly happier to deviate from the intended protocol. How should we reason about user behavior in these protocols? How should we design protocols in these settings?
Huacheng Yu, Room 310
- data structures
- streaming algorithms
- design and analyze data structures / streaming algorithms
- prove impossibility results (lower bounds)
- implement and evaluate data structures / streaming algorithms
Ellen Zhong, Room 314
Opportunities outside the department.
We encourage students to look in to doing interdisciplinary computer science research and to work with professors in departments other than computer science. However, every CS independent work project must have a strong computer science element (even if it has other scientific or artistic elements as well.) To do a project with an adviser outside of computer science you must have permission of the department. This can be accomplished by having a second co-adviser within the computer science department or by contacting the independent work supervisor about the project and having he or she sign the independent work proposal form.
Here is a list of professors outside the computer science department who are eager to work with computer science undergraduates.
Maria Apostolaki, Engineering Quadrangle, C330
- Research areas: Computing & Networking, Data & Information Science, Security & Privacy
Branko Glisic, Engineering Quadrangle, Room E330
- Documentation of historic structures
- Cyber physical systems for structural health monitoring
- Developing virtual and augmented reality applications for documenting structures
- Applying machine learning techniques to generate 3D models from 2D plans of buildings
- Contact : Rebecca Napolitano, rkn2 (@princeton.edu)
Mihir Kshirsagar, Sherrerd Hall, Room 315
Center for Information Technology Policy.
- Consumer protection
- Content regulation
- Competition law
- Economic development
- Surveillance and discrimination
Sharad Malik, Engineering Quadrangle, Room B224
Select a Senior Thesis Adviser for the 2020-21 Academic Year.
- Design of reliable hardware systems
- Verifying complex software and hardware systems
Prateek Mittal, Engineering Quadrangle, Room B236
- Internet security and privacy
- Social Networks
- Privacy technologies, anonymous communication
- Network Science
- Internet security and privacy: The insecurity of Internet protocols and services threatens the safety of our critical network infrastructure and billions of end users. How can we defend end users as well as our critical network infrastructure from attacks?
- Trustworthy social systems: Online social networks (OSNs) such as Facebook, Google+, and Twitter have revolutionized the way our society communicates. How can we leverage social connections between users to design the next generation of communication systems?
- Privacy Technologies: Privacy on the Internet is eroding rapidly, with businesses and governments mining sensitive user information. How can we protect the privacy of our online communications? The Tor project (https://www.torproject.org/) is a potential application of interest.
Ken Norman, Psychology Dept, PNI 137
- Research Areas: Memory, the brain and computation
- Lab: Princeton Computational Memory Lab
Potential research topics
- Methods for decoding cognitive state information from neuroimaging data (fMRI and EEG)
- Neural network simulations of learning and memory
Caroline Savage
Office of Sustainability, Phone:(609)258-7513, Email: cs35 (@princeton.edu)
The Campus as Lab program supports students using the Princeton campus as a living laboratory to solve sustainability challenges. The Office of Sustainability has created a list of campus as lab research questions, filterable by discipline and topic, on its website .
An example from Computer Science could include using TigerEnergy , a platform which provides real-time data on campus energy generation and consumption, to study one of the many energy systems or buildings on campus. Three CS students used TigerEnergy to create a live energy heatmap of campus .
Other potential projects include:
- Apply game theory to sustainability challenges
- Develop a tool to help visualize interactions between complex campus systems, e.g. energy and water use, transportation and storm water runoff, purchasing and waste, etc.
- How can we learn (in aggregate) about individuals’ waste, energy, transportation, and other behaviors without impinging on privacy?
Janet Vertesi, Sociology Dept, Wallace Hall, Room 122
- Research areas: Sociology of technology; Human-computer interaction; Ubiquitous computing.
- Possible projects: At the intersection of computer science and social science, my students have built mixed reality games, produced artistic and interactive installations, and studied mixed human-robot teams, among other projects.
David Wentzlaff, Engineering Quadrangle, Room 228
Computing, Operating Systems, Sustainable Computing.
- Instrument Princeton's Green (HPCRC) data center
- Investigate power utilization on an processor core implemented in an FPGA
- Dismantle and document all of the components in modern electronics. Invent new ways to build computers that can be recycled easier.
- Other topics in parallel computer architecture or operating systems
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Computer science articles from across Nature Portfolio
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching large volumes of information or encrypting data so that it can be stored and transmitted securely.
Latest Research and Reviews
Uncertainty-driven mixture convolution and transformer network for remote sensing image super-resolution
- Xiaomin Zhang
Co-ordinate-based positional embedding that captures resolution to enhance transformer’s performance in medical image analysis
- Badhan Kumar Das
- Gengyan Zhao
- Andreas Maier
A new method based on YOLOv5 and multiscale data augmentation for visual inspection in substation
- Junjie Chen
The benefits, risks and bounds of personalizing the alignment of large language models to individuals
Tailoring the alignment of large language models (LLMs) to individuals is a new frontier in generative AI, but unbounded personalization can bring potential harm, such as large-scale profiling, privacy infringement and bias reinforcement. Kirk et al. develop a taxonomy for risks and benefits of personalized LLMs and discuss the need for normative decisions on what are acceptable bounds of personalization.
- Hannah Rose Kirk
- Bertie Vidgen
- Scott A. Hale
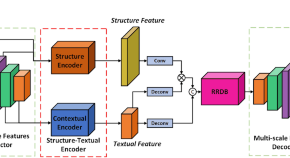
Dual-branch feature encoding framework for infrared images super-resolution reconstruction

The use of residual analysis to improve the error rate accuracy of machine translation
- Ľubomír Benko
- Dasa Munkova
News and Comment

AI now beats humans at basic tasks — new benchmarks are needed, says major report
Stanford University’s 2024 AI Index charts the meteoric rise of artificial-intelligence tools.
- Nicola Jones
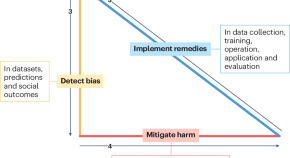
Medical artificial intelligence should do no harm
Bias and distrust in medicine have been perpetuated by the misuse of medical equations, algorithms and devices. Artificial intelligence (AI) can exacerbate these problems. However, AI also has potential to detect, mitigate and remedy the harmful effects of bias to build trust and improve healthcare for everyone.
- Melanie E. Moses
- Sonia M. Gipson Rankin

AI hears hidden X factor in zebra finch love songs
Machine learning detects song differences too subtle for humans to hear, and physicists harness the computing power of the strange skyrmion.
- Nick Petrić Howe
- Benjamin Thompson
Three reasons why AI doesn’t model human language
- Johan J. Bolhuis
- Stephen Crain
- Andrea Moro

Generative artificial intelligence in chemical engineering
Generative artificial intelligence will transform the way we design and operate chemical processes, argues Artur M. Schweidtmann.
- Artur M. Schweidtmann

Why scientists trust AI too much — and what to do about it
Some researchers see superhuman qualities in artificial intelligence. All scientists need to be alert to the risks this creates.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
- Privacy Policy
Buy Me a Coffee

Home » 500+ Computer Science Research Topics
500+ Computer Science Research Topics

Computer Science is a constantly evolving field that has transformed the world we live in today. With new technologies emerging every day, there are countless research opportunities in this field. Whether you are interested in artificial intelligence, machine learning, cybersecurity, data analytics, or computer networks, there are endless possibilities to explore. In this post, we will delve into some of the most interesting and important research topics in Computer Science. From the latest advancements in programming languages to the development of cutting-edge algorithms, we will explore the latest trends and innovations that are shaping the future of Computer Science. So, whether you are a student or a professional, read on to discover some of the most exciting research topics in this dynamic and rapidly expanding field.
Computer Science Research Topics
Computer Science Research Topics are as follows:
- Using machine learning to detect and prevent cyber attacks
- Developing algorithms for optimized resource allocation in cloud computing
- Investigating the use of blockchain technology for secure and decentralized data storage
- Developing intelligent chatbots for customer service
- Investigating the effectiveness of deep learning for natural language processing
- Developing algorithms for detecting and removing fake news from social media
- Investigating the impact of social media on mental health
- Developing algorithms for efficient image and video compression
- Investigating the use of big data analytics for predictive maintenance in manufacturing
- Developing algorithms for identifying and mitigating bias in machine learning models
- Investigating the ethical implications of autonomous vehicles
- Developing algorithms for detecting and preventing cyberbullying
- Investigating the use of machine learning for personalized medicine
- Developing algorithms for efficient and accurate speech recognition
- Investigating the impact of social media on political polarization
- Developing algorithms for sentiment analysis in social media data
- Investigating the use of virtual reality in education
- Developing algorithms for efficient data encryption and decryption
- Investigating the impact of technology on workplace productivity
- Developing algorithms for detecting and mitigating deepfakes
- Investigating the use of artificial intelligence in financial trading
- Developing algorithms for efficient database management
- Investigating the effectiveness of online learning platforms
- Developing algorithms for efficient and accurate facial recognition
- Investigating the use of machine learning for predicting weather patterns
- Developing algorithms for efficient and secure data transfer
- Investigating the impact of technology on social skills and communication
- Developing algorithms for efficient and accurate object recognition
- Investigating the use of machine learning for fraud detection in finance
- Developing algorithms for efficient and secure authentication systems
- Investigating the impact of technology on privacy and surveillance
- Developing algorithms for efficient and accurate handwriting recognition
- Investigating the use of machine learning for predicting stock prices
- Developing algorithms for efficient and secure biometric identification
- Investigating the impact of technology on mental health and well-being
- Developing algorithms for efficient and accurate language translation
- Investigating the use of machine learning for personalized advertising
- Developing algorithms for efficient and secure payment systems
- Investigating the impact of technology on the job market and automation
- Developing algorithms for efficient and accurate object tracking
- Investigating the use of machine learning for predicting disease outbreaks
- Developing algorithms for efficient and secure access control
- Investigating the impact of technology on human behavior and decision making
- Developing algorithms for efficient and accurate sound recognition
- Investigating the use of machine learning for predicting customer behavior
- Developing algorithms for efficient and secure data backup and recovery
- Investigating the impact of technology on education and learning outcomes
- Developing algorithms for efficient and accurate emotion recognition
- Investigating the use of machine learning for improving healthcare outcomes
- Developing algorithms for efficient and secure supply chain management
- Investigating the impact of technology on cultural and societal norms
- Developing algorithms for efficient and accurate gesture recognition
- Investigating the use of machine learning for predicting consumer demand
- Developing algorithms for efficient and secure cloud storage
- Investigating the impact of technology on environmental sustainability
- Developing algorithms for efficient and accurate voice recognition
- Investigating the use of machine learning for improving transportation systems
- Developing algorithms for efficient and secure mobile device management
- Investigating the impact of technology on social inequality and access to resources
- Machine learning for healthcare diagnosis and treatment
- Machine Learning for Cybersecurity
- Machine learning for personalized medicine
- Cybersecurity threats and defense strategies
- Big data analytics for business intelligence
- Blockchain technology and its applications
- Human-computer interaction in virtual reality environments
- Artificial intelligence for autonomous vehicles
- Natural language processing for chatbots
- Cloud computing and its impact on the IT industry
- Internet of Things (IoT) and smart homes
- Robotics and automation in manufacturing
- Augmented reality and its potential in education
- Data mining techniques for customer relationship management
- Computer vision for object recognition and tracking
- Quantum computing and its applications in cryptography
- Social media analytics and sentiment analysis
- Recommender systems for personalized content delivery
- Mobile computing and its impact on society
- Bioinformatics and genomic data analysis
- Deep learning for image and speech recognition
- Digital signal processing and audio processing algorithms
- Cloud storage and data security in the cloud
- Wearable technology and its impact on healthcare
- Computational linguistics for natural language understanding
- Cognitive computing for decision support systems
- Cyber-physical systems and their applications
- Edge computing and its impact on IoT
- Machine learning for fraud detection
- Cryptography and its role in secure communication
- Cybersecurity risks in the era of the Internet of Things
- Natural language generation for automated report writing
- 3D printing and its impact on manufacturing
- Virtual assistants and their applications in daily life
- Cloud-based gaming and its impact on the gaming industry
- Computer networks and their security issues
- Cyber forensics and its role in criminal investigations
- Machine learning for predictive maintenance in industrial settings
- Augmented reality for cultural heritage preservation
- Human-robot interaction and its applications
- Data visualization and its impact on decision-making
- Cybersecurity in financial systems and blockchain
- Computer graphics and animation techniques
- Biometrics and its role in secure authentication
- Cloud-based e-learning platforms and their impact on education
- Natural language processing for machine translation
- Machine learning for predictive maintenance in healthcare
- Cybersecurity and privacy issues in social media
- Computer vision for medical image analysis
- Natural language generation for content creation
- Cybersecurity challenges in cloud computing
- Human-robot collaboration in manufacturing
- Data mining for predicting customer churn
- Artificial intelligence for autonomous drones
- Cybersecurity risks in the healthcare industry
- Machine learning for speech synthesis
- Edge computing for low-latency applications
- Virtual reality for mental health therapy
- Quantum computing and its applications in finance
- Biomedical engineering and its applications
- Cybersecurity in autonomous systems
- Machine learning for predictive maintenance in transportation
- Computer vision for object detection in autonomous driving
- Augmented reality for industrial training and simulations
- Cloud-based cybersecurity solutions for small businesses
- Natural language processing for knowledge management
- Machine learning for personalized advertising
- Cybersecurity in the supply chain management
- Cybersecurity risks in the energy sector
- Computer vision for facial recognition
- Natural language processing for social media analysis
- Machine learning for sentiment analysis in customer reviews
- Explainable Artificial Intelligence
- Quantum Computing
- Blockchain Technology
- Human-Computer Interaction
- Natural Language Processing
- Cloud Computing
- Robotics and Automation
- Augmented Reality and Virtual Reality
- Cyber-Physical Systems
- Computational Neuroscience
- Big Data Analytics
- Computer Vision
- Cryptography and Network Security
- Internet of Things
- Computer Graphics and Visualization
- Artificial Intelligence for Game Design
- Computational Biology
- Social Network Analysis
- Bioinformatics
- Distributed Systems and Middleware
- Information Retrieval and Data Mining
- Computer Networks
- Mobile Computing and Wireless Networks
- Software Engineering
- Database Systems
- Parallel and Distributed Computing
- Human-Robot Interaction
- Intelligent Transportation Systems
- High-Performance Computing
- Cyber-Physical Security
- Deep Learning
- Sensor Networks
- Multi-Agent Systems
- Human-Centered Computing
- Wearable Computing
- Knowledge Representation and Reasoning
- Adaptive Systems
- Brain-Computer Interface
- Health Informatics
- Cognitive Computing
- Cybersecurity and Privacy
- Internet Security
- Cybercrime and Digital Forensics
- Cloud Security
- Cryptocurrencies and Digital Payments
- Machine Learning for Natural Language Generation
- Cognitive Robotics
- Neural Networks
- Semantic Web
- Image Processing
- Cyber Threat Intelligence
- Secure Mobile Computing
- Cybersecurity Education and Training
- Privacy Preserving Techniques
- Cyber-Physical Systems Security
- Virtualization and Containerization
- Machine Learning for Computer Vision
- Network Function Virtualization
- Cybersecurity Risk Management
- Information Security Governance
- Intrusion Detection and Prevention
- Biometric Authentication
- Machine Learning for Predictive Maintenance
- Security in Cloud-based Environments
- Cybersecurity for Industrial Control Systems
- Smart Grid Security
- Software Defined Networking
- Quantum Cryptography
- Security in the Internet of Things
- Natural language processing for sentiment analysis
- Blockchain technology for secure data sharing
- Developing efficient algorithms for big data analysis
- Cybersecurity for internet of things (IoT) devices
- Human-robot interaction for industrial automation
- Image recognition for autonomous vehicles
- Social media analytics for marketing strategy
- Quantum computing for solving complex problems
- Biometric authentication for secure access control
- Augmented reality for education and training
- Intelligent transportation systems for traffic management
- Predictive modeling for financial markets
- Cloud computing for scalable data storage and processing
- Virtual reality for therapy and mental health treatment
- Data visualization for business intelligence
- Recommender systems for personalized product recommendations
- Speech recognition for voice-controlled devices
- Mobile computing for real-time location-based services
- Neural networks for predicting user behavior
- Genetic algorithms for optimization problems
- Distributed computing for parallel processing
- Internet of things (IoT) for smart cities
- Wireless sensor networks for environmental monitoring
- Cloud-based gaming for high-performance gaming
- Social network analysis for identifying influencers
- Autonomous systems for agriculture
- Robotics for disaster response
- Data mining for customer segmentation
- Computer graphics for visual effects in movies and video games
- Virtual assistants for personalized customer service
- Natural language understanding for chatbots
- 3D printing for manufacturing prototypes
- Artificial intelligence for stock trading
- Machine learning for weather forecasting
- Biomedical engineering for prosthetics and implants
- Cybersecurity for financial institutions
- Machine learning for energy consumption optimization
- Computer vision for object tracking
- Natural language processing for document summarization
- Wearable technology for health and fitness monitoring
- Internet of things (IoT) for home automation
- Reinforcement learning for robotics control
- Big data analytics for customer insights
- Machine learning for supply chain optimization
- Natural language processing for legal document analysis
- Artificial intelligence for drug discovery
- Computer vision for object recognition in robotics
- Data mining for customer churn prediction
- Autonomous systems for space exploration
- Robotics for agriculture automation
- Machine learning for predicting earthquakes
- Natural language processing for sentiment analysis in customer reviews
- Big data analytics for predicting natural disasters
- Internet of things (IoT) for remote patient monitoring
- Blockchain technology for digital identity management
- Machine learning for predicting wildfire spread
- Computer vision for gesture recognition
- Natural language processing for automated translation
- Big data analytics for fraud detection in banking
- Internet of things (IoT) for smart homes
- Robotics for warehouse automation
- Machine learning for predicting air pollution
- Natural language processing for medical record analysis
- Augmented reality for architectural design
- Big data analytics for predicting traffic congestion
- Machine learning for predicting customer lifetime value
- Developing algorithms for efficient and accurate text recognition
- Natural Language Processing for Virtual Assistants
- Natural Language Processing for Sentiment Analysis in Social Media
- Explainable Artificial Intelligence (XAI) for Trust and Transparency
- Deep Learning for Image and Video Retrieval
- Edge Computing for Internet of Things (IoT) Applications
- Data Science for Social Media Analytics
- Cybersecurity for Critical Infrastructure Protection
- Natural Language Processing for Text Classification
- Quantum Computing for Optimization Problems
- Machine Learning for Personalized Health Monitoring
- Computer Vision for Autonomous Driving
- Blockchain Technology for Supply Chain Management
- Augmented Reality for Education and Training
- Natural Language Processing for Sentiment Analysis
- Machine Learning for Personalized Marketing
- Big Data Analytics for Financial Fraud Detection
- Cybersecurity for Cloud Security Assessment
- Artificial Intelligence for Natural Language Understanding
- Blockchain Technology for Decentralized Applications
- Virtual Reality for Cultural Heritage Preservation
- Natural Language Processing for Named Entity Recognition
- Machine Learning for Customer Churn Prediction
- Big Data Analytics for Social Network Analysis
- Cybersecurity for Intrusion Detection and Prevention
- Artificial Intelligence for Robotics and Automation
- Blockchain Technology for Digital Identity Management
- Virtual Reality for Rehabilitation and Therapy
- Natural Language Processing for Text Summarization
- Machine Learning for Credit Risk Assessment
- Big Data Analytics for Fraud Detection in Healthcare
- Cybersecurity for Internet Privacy Protection
- Artificial Intelligence for Game Design and Development
- Blockchain Technology for Decentralized Social Networks
- Virtual Reality for Marketing and Advertising
- Natural Language Processing for Opinion Mining
- Machine Learning for Anomaly Detection
- Big Data Analytics for Predictive Maintenance in Transportation
- Cybersecurity for Network Security Management
- Artificial Intelligence for Personalized News and Content Delivery
- Blockchain Technology for Cryptocurrency Mining
- Virtual Reality for Architectural Design and Visualization
- Natural Language Processing for Machine Translation
- Machine Learning for Automated Image Captioning
- Big Data Analytics for Stock Market Prediction
- Cybersecurity for Biometric Authentication Systems
- Artificial Intelligence for Human-Robot Interaction
- Blockchain Technology for Smart Grids
- Virtual Reality for Sports Training and Simulation
- Natural Language Processing for Question Answering Systems
- Machine Learning for Sentiment Analysis in Customer Feedback
- Big Data Analytics for Predictive Maintenance in Manufacturing
- Cybersecurity for Cloud-Based Systems
- Artificial Intelligence for Automated Journalism
- Blockchain Technology for Intellectual Property Management
- Virtual Reality for Therapy and Rehabilitation
- Natural Language Processing for Language Generation
- Machine Learning for Customer Lifetime Value Prediction
- Big Data Analytics for Predictive Maintenance in Energy Systems
- Cybersecurity for Secure Mobile Communication
- Artificial Intelligence for Emotion Recognition
- Blockchain Technology for Digital Asset Trading
- Virtual Reality for Automotive Design and Visualization
- Natural Language Processing for Semantic Web
- Machine Learning for Fraud Detection in Financial Transactions
- Big Data Analytics for Social Media Monitoring
- Cybersecurity for Cloud Storage and Sharing
- Artificial Intelligence for Personalized Education
- Blockchain Technology for Secure Online Voting Systems
- Virtual Reality for Cultural Tourism
- Natural Language Processing for Chatbot Communication
- Machine Learning for Medical Diagnosis and Treatment
- Big Data Analytics for Environmental Monitoring and Management.
- Cybersecurity for Cloud Computing Environments
- Virtual Reality for Training and Simulation
- Big Data Analytics for Sports Performance Analysis
- Cybersecurity for Internet of Things (IoT) Devices
- Artificial Intelligence for Traffic Management and Control
- Blockchain Technology for Smart Contracts
- Natural Language Processing for Document Summarization
- Machine Learning for Image and Video Recognition
- Blockchain Technology for Digital Asset Management
- Virtual Reality for Entertainment and Gaming
- Natural Language Processing for Opinion Mining in Online Reviews
- Machine Learning for Customer Relationship Management
- Big Data Analytics for Environmental Monitoring and Management
- Cybersecurity for Network Traffic Analysis and Monitoring
- Artificial Intelligence for Natural Language Generation
- Blockchain Technology for Supply Chain Transparency and Traceability
- Virtual Reality for Design and Visualization
- Natural Language Processing for Speech Recognition
- Machine Learning for Recommendation Systems
- Big Data Analytics for Customer Segmentation and Targeting
- Cybersecurity for Biometric Authentication
- Artificial Intelligence for Human-Computer Interaction
- Blockchain Technology for Decentralized Finance (DeFi)
- Virtual Reality for Tourism and Cultural Heritage
- Machine Learning for Cybersecurity Threat Detection and Prevention
- Big Data Analytics for Healthcare Cost Reduction
- Cybersecurity for Data Privacy and Protection
- Artificial Intelligence for Autonomous Vehicles
- Blockchain Technology for Cryptocurrency and Blockchain Security
- Virtual Reality for Real Estate Visualization
- Natural Language Processing for Question Answering
- Big Data Analytics for Financial Markets Prediction
- Cybersecurity for Cloud-Based Machine Learning Systems
- Artificial Intelligence for Personalized Advertising
- Blockchain Technology for Digital Identity Verification
- Virtual Reality for Cultural and Language Learning
- Natural Language Processing for Semantic Analysis
- Machine Learning for Business Forecasting
- Big Data Analytics for Social Media Marketing
- Artificial Intelligence for Content Generation
- Blockchain Technology for Smart Cities
- Virtual Reality for Historical Reconstruction
- Natural Language Processing for Knowledge Graph Construction
- Machine Learning for Speech Synthesis
- Big Data Analytics for Traffic Optimization
- Artificial Intelligence for Social Robotics
- Blockchain Technology for Healthcare Data Management
- Virtual Reality for Disaster Preparedness and Response
- Natural Language Processing for Multilingual Communication
- Machine Learning for Emotion Recognition
- Big Data Analytics for Human Resources Management
- Cybersecurity for Mobile App Security
- Artificial Intelligence for Financial Planning and Investment
- Blockchain Technology for Energy Management
- Virtual Reality for Cultural Preservation and Heritage.
- Big Data Analytics for Healthcare Management
- Cybersecurity in the Internet of Things (IoT)
- Artificial Intelligence for Predictive Maintenance
- Computational Biology for Drug Discovery
- Virtual Reality for Mental Health Treatment
- Machine Learning for Sentiment Analysis in Social Media
- Human-Computer Interaction for User Experience Design
- Cloud Computing for Disaster Recovery
- Quantum Computing for Cryptography
- Intelligent Transportation Systems for Smart Cities
- Cybersecurity for Autonomous Vehicles
- Artificial Intelligence for Fraud Detection in Financial Systems
- Social Network Analysis for Marketing Campaigns
- Cloud Computing for Video Game Streaming
- Machine Learning for Speech Recognition
- Augmented Reality for Architecture and Design
- Natural Language Processing for Customer Service Chatbots
- Machine Learning for Climate Change Prediction
- Big Data Analytics for Social Sciences
- Artificial Intelligence for Energy Management
- Virtual Reality for Tourism and Travel
- Cybersecurity for Smart Grids
- Machine Learning for Image Recognition
- Augmented Reality for Sports Training
- Natural Language Processing for Content Creation
- Cloud Computing for High-Performance Computing
- Artificial Intelligence for Personalized Medicine
- Virtual Reality for Architecture and Design
- Augmented Reality for Product Visualization
- Natural Language Processing for Language Translation
- Cybersecurity for Cloud Computing
- Artificial Intelligence for Supply Chain Optimization
- Blockchain Technology for Digital Voting Systems
- Virtual Reality for Job Training
- Augmented Reality for Retail Shopping
- Natural Language Processing for Sentiment Analysis in Customer Feedback
- Cloud Computing for Mobile Application Development
- Artificial Intelligence for Cybersecurity Threat Detection
- Blockchain Technology for Intellectual Property Protection
- Virtual Reality for Music Education
- Machine Learning for Financial Forecasting
- Augmented Reality for Medical Education
- Natural Language Processing for News Summarization
- Cybersecurity for Healthcare Data Protection
- Artificial Intelligence for Autonomous Robots
- Virtual Reality for Fitness and Health
- Machine Learning for Natural Language Understanding
- Augmented Reality for Museum Exhibits
- Natural Language Processing for Chatbot Personality Development
- Cloud Computing for Website Performance Optimization
- Artificial Intelligence for E-commerce Recommendation Systems
- Blockchain Technology for Supply Chain Traceability
- Virtual Reality for Military Training
- Augmented Reality for Advertising
- Natural Language Processing for Chatbot Conversation Management
- Cybersecurity for Cloud-Based Services
- Artificial Intelligence for Agricultural Management
- Blockchain Technology for Food Safety Assurance
- Virtual Reality for Historical Reenactments
- Machine Learning for Cybersecurity Incident Response.
- Secure Multiparty Computation
- Federated Learning
- Internet of Things Security
- Blockchain Scalability
- Quantum Computing Algorithms
- Explainable AI
- Data Privacy in the Age of Big Data
- Adversarial Machine Learning
- Deep Reinforcement Learning
- Online Learning and Streaming Algorithms
- Graph Neural Networks
- Automated Debugging and Fault Localization
- Mobile Application Development
- Software Engineering for Cloud Computing
- Cryptocurrency Security
- Edge Computing for Real-Time Applications
- Natural Language Generation
- Virtual and Augmented Reality
- Computational Biology and Bioinformatics
- Internet of Things Applications
- Robotics and Autonomous Systems
- Explainable Robotics
- 3D Printing and Additive Manufacturing
- Distributed Systems
- Parallel Computing
- Data Center Networking
- Data Mining and Knowledge Discovery
- Information Retrieval and Search Engines
- Network Security and Privacy
- Cloud Computing Security
- Data Analytics for Business Intelligence
- Neural Networks and Deep Learning
- Reinforcement Learning for Robotics
- Automated Planning and Scheduling
- Evolutionary Computation and Genetic Algorithms
- Formal Methods for Software Engineering
- Computational Complexity Theory
- Bio-inspired Computing
- Computer Vision for Object Recognition
- Automated Reasoning and Theorem Proving
- Natural Language Understanding
- Machine Learning for Healthcare
- Scalable Distributed Systems
- Sensor Networks and Internet of Things
- Smart Grids and Energy Systems
- Software Testing and Verification
- Web Application Security
- Wireless and Mobile Networks
- Computer Architecture and Hardware Design
- Digital Signal Processing
- Game Theory and Mechanism Design
- Multi-agent Systems
- Evolutionary Robotics
- Quantum Machine Learning
- Computational Social Science
- Explainable Recommender Systems.
- Artificial Intelligence and its applications
- Cloud computing and its benefits
- Cybersecurity threats and solutions
- Internet of Things and its impact on society
- Virtual and Augmented Reality and its uses
- Blockchain Technology and its potential in various industries
- Web Development and Design
- Digital Marketing and its effectiveness
- Big Data and Analytics
- Software Development Life Cycle
- Gaming Development and its growth
- Network Administration and Maintenance
- Machine Learning and its uses
- Data Warehousing and Mining
- Computer Architecture and Design
- Computer Graphics and Animation
- Quantum Computing and its potential
- Data Structures and Algorithms
- Computer Vision and Image Processing
- Robotics and its applications
- Operating Systems and its functions
- Information Theory and Coding
- Compiler Design and Optimization
- Computer Forensics and Cyber Crime Investigation
- Distributed Computing and its significance
- Artificial Neural Networks and Deep Learning
- Cloud Storage and Backup
- Programming Languages and their significance
- Computer Simulation and Modeling
- Computer Networks and its types
- Information Security and its types
- Computer-based Training and eLearning
- Medical Imaging and its uses
- Social Media Analysis and its applications
- Human Resource Information Systems
- Computer-Aided Design and Manufacturing
- Multimedia Systems and Applications
- Geographic Information Systems and its uses
- Computer-Assisted Language Learning
- Mobile Device Management and Security
- Data Compression and its types
- Knowledge Management Systems
- Text Mining and its uses
- Cyber Warfare and its consequences
- Wireless Networks and its advantages
- Computer Ethics and its importance
- Computational Linguistics and its applications
- Autonomous Systems and Robotics
- Information Visualization and its importance
- Geographic Information Retrieval and Mapping
- Business Intelligence and its benefits
- Digital Libraries and their significance
- Artificial Life and Evolutionary Computation
- Computer Music and its types
- Virtual Teams and Collaboration
- Computer Games and Learning
- Semantic Web and its applications
- Electronic Commerce and its advantages
- Multimedia Databases and their significance
- Computer Science Education and its importance
- Computer-Assisted Translation and Interpretation
- Ambient Intelligence and Smart Homes
- Autonomous Agents and Multi-Agent Systems.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like


200+ Funny Research Topics

500+ Sports Research Topics

300+ American History Research Paper Topics

500+ Cyber Security Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics

- USF Research
- USF Libraries
Digital Commons @ USF > College of Engineering > Computer Science and Engineering > Theses and Dissertations
Computer Science and Engineering Theses and Dissertations
Theses/dissertations from 2023 2023.
Refining the Machine Learning Pipeline for US-based Public Transit Systems , Jennifer Adorno
Insect Classification and Explainability from Image Data via Deep Learning Techniques , Tanvir Hossain Bhuiyan
Brain-Inspired Spatio-Temporal Learning with Application to Robotics , Thiago André Ferreira Medeiros
Evaluating Methods for Improving DNN Robustness Against Adversarial Attacks , Laureano Griffin
Analyzing Multi-Robot Leader-Follower Formations in Obstacle-Laden Environments , Zachary J. Hinnen
Secure Lightweight Cryptographic Hardware Constructions for Deeply Embedded Systems , Jasmin Kaur
A Psychometric Analysis of Natural Language Inference Using Transformer Language Models , Antonio Laverghetta Jr.
Graph Analysis on Social Networks , Shen Lu
Deep Learning-based Automatic Stereology for High- and Low-magnification Images , Hunter Morera
Deciphering Trends and Tactics: Data-driven Techniques for Forecasting Information Spread and Detecting Coordinated Campaigns in Social Media , Kin Wai Ng Lugo
Automated Approaches to Enable Innovative Civic Applications from Citizen Generated Imagery , Hye Seon Yi
Theses/Dissertations from 2022 2022
Towards High Performing and Reliable Deep Convolutional Neural Network Models for Typically Limited Medical Imaging Datasets , Kaoutar Ben Ahmed
Task Progress Assessment and Monitoring Using Self-Supervised Learning , Sainath Reddy Bobbala
Towards More Task-Generalized and Explainable AI Through Psychometrics , Alec Braynen
A Multiple Input Multiple Output Framework for the Automatic Optical Fractionator-based Cell Counting in Z-Stacks Using Deep Learning , Palak Dave
On the Reliability of Wearable Sensors for Assessing Movement Disorder-Related Gait Quality and Imbalance: A Case Study of Multiple Sclerosis , Steven Díaz Hernández
Securing Critical Cyber Infrastructures and Functionalities via Machine Learning Empowered Strategies , Tao Hou
Social Media Time Series Forecasting and User-Level Activity Prediction with Gradient Boosting, Deep Learning, and Data Augmentation , Fred Mubang
A Study of Deep Learning Silhouette Extractors for Gait Recognition , Sneha Oladhri
Analyzing Decision-making in Robot Soccer for Attacking Behaviors , Justin Rodney
Generative Spatio-Temporal and Multimodal Analysis of Neonatal Pain , Md Sirajus Salekin
Secure Hardware Constructions for Fault Detection of Lattice-based Post-quantum Cryptosystems , Ausmita Sarker
Adaptive Multi-scale Place Cell Representations and Replay for Spatial Navigation and Learning in Autonomous Robots , Pablo Scleidorovich
Predicting the Number of Objects in a Robotic Grasp , Utkarsh Tamrakar
Humanoid Robot Motion Control for Ramps and Stairs , Tommy Truong
Preventing Variadic Function Attacks Through Argument Width Counting , Brennan Ward
Theses/Dissertations from 2021 2021
Knowledge Extraction and Inference Based on Visual Understanding of Cooking Contents , Ahmad Babaeian Babaeian Jelodar
Efficient Post-Quantum and Compact Cryptographic Constructions for the Internet of Things , Rouzbeh Behnia
Efficient Hardware Constructions for Error Detection of Post-Quantum Cryptographic Schemes , Alvaro Cintas Canto
Using Hyper-Dimensional Spanning Trees to Improve Structure Preservation During Dimensionality Reduction , Curtis Thomas Davis
Design, Deployment, and Validation of Computer Vision Techniques for Societal Scale Applications , Arup Kanti Dey
AffectiveTDA: Using Topological Data Analysis to Improve Analysis and Explainability in Affective Computing , Hamza Elhamdadi
Automatic Detection of Vehicles in Satellite Images for Economic Monitoring , Cole Hill
Analysis of Contextual Emotions Using Multimodal Data , Saurabh Hinduja
Data-driven Studies on Social Networks: Privacy and Simulation , Yasanka Sameera Horawalavithana
Automated Identification of Stages in Gonotrophic Cycle of Mosquitoes Using Computer Vision Techniques , Sherzod Kariev
Exploring the Use of Neural Transformers for Psycholinguistics , Antonio Laverghetta Jr.
Secure VLSI Hardware Design Against Intellectual Property (IP) Theft and Cryptographic Vulnerabilities , Matthew Dean Lewandowski
Turkic Interlingua: A Case Study of Machine Translation in Low-resource Languages , Jamshidbek Mirzakhalov
Automated Wound Segmentation and Dimension Measurement Using RGB-D Image , Chih-Yun Pai
Constructing Frameworks for Task-Optimized Visualizations , Ghulam Jilani Abdul Rahim Quadri
Trilateration-Based Localization in Known Environments with Object Detection , Valeria M. Salas Pacheco
Recognizing Patterns from Vital Signs Using Spectrograms , Sidharth Srivatsav Sribhashyam
Recognizing Emotion in the Wild Using Multimodal Data , Shivam Srivastava
A Modular Framework for Multi-Rotor Unmanned Aerial Vehicles for Military Operations , Dante Tezza
Human-centered Cybersecurity Research — Anthropological Findings from Two Longitudinal Studies , Anwesh Tuladhar
Learning State-Dependent Sensor Measurement Models To Improve Robot Localization Accuracy , Troi André Williams
Human-centric Cybersecurity Research: From Trapping the Bad Guys to Helping the Good Ones , Armin Ziaie Tabari
Theses/Dissertations from 2020 2020
Classifying Emotions with EEG and Peripheral Physiological Data Using 1D Convolutional Long Short-Term Memory Neural Network , Rupal Agarwal
Keyless Anti-Jamming Communication via Randomized DSSS , Ahmad Alagil
Active Deep Learning Method to Automate Unbiased Stereology Cell Counting , Saeed Alahmari
Composition of Atomic-Obligation Security Policies , Yan Cao Albright
Action Recognition Using the Motion Taxonomy , Maxat Alibayev
Sentiment Analysis in Peer Review , Zachariah J. Beasley
Spatial Heterogeneity Utilization in CT Images for Lung Nodule Classication , Dmitrii Cherezov
Feature Selection Via Random Subsets Of Uncorrelated Features , Long Kim Dang
Unifying Security Policy Enforcement: Theory and Practice , Shamaria Engram
PsiDB: A Framework for Batched Query Processing and Optimization , Mehrad Eslami
Composition of Atomic-Obligation Security Policies , Danielle Ferguson
Algorithms To Profile Driver Behavior From Zero-permission Embedded Sensors , Bharti Goel
The Efficiency and Accuracy of YOLO for Neonate Face Detection in the Clinical Setting , Jacqueline Hausmann
Beyond the Hype: Challenges of Neural Networks as Applied to Social Networks , Anthony Hernandez
Privacy-Preserving and Functional Information Systems , Thang Hoang
Managing Off-Grid Power Use for Solar Fueled Residences with Smart Appliances, Prices-to-Devices and IoT , Donnelle L. January
Novel Bit-Sliced In-Memory Computing Based VLSI Architecture for Fast Sobel Edge Detection in IoT Edge Devices , Rajeev Joshi
Edge Computing for Deep Learning-Based Distributed Real-time Object Detection on IoT Constrained Platforms at Low Frame Rate , Lakshmikavya Kalyanam
Establishing Topological Data Analysis: A Comparison of Visualization Techniques , Tanmay J. Kotha
Machine Learning for the Internet of Things: Applications, Implementation, and Security , Vishalini Laguduva Ramnath
System Support of Concurrent Database Query Processing on a GPU , Hao Li
Deep Learning Predictive Modeling with Data Challenges (Small, Big, or Imbalanced) , Renhao Liu
Countermeasures Against Various Network Attacks Using Machine Learning Methods , Yi Li
Towards Safe Power Oversubscription and Energy Efficiency of Data Centers , Sulav Malla
Design of Support Measures for Counting Frequent Patterns in Graphs , Jinghan Meng
Automating the Classification of Mosquito Specimens Using Image Processing Techniques , Mona Minakshi
Models of Secure Software Enforcement and Development , Hernan M. Palombo
Functional Object-Oriented Network: A Knowledge Representation for Service Robotics , David Andrés Paulius Ramos
Lung Nodule Malignancy Prediction from Computed Tomography Images Using Deep Learning , Rahul Paul
Algorithms and Framework for Computing 2-body Statistics on Graphics Processing Units , Napath Pitaksirianan
Efficient Viewshed Computation Algorithms On GPUs and CPUs , Faisal F. Qarah
Relational Joins on GPUs for In-Memory Database Query Processing , Ran Rui
Micro-architectural Countermeasures for Control Flow and Misspeculation Based Software Attacks , Love Kumar Sah
Efficient Forward-Secure and Compact Signatures for the Internet of Things (IoT) , Efe Ulas Akay Seyitoglu
Detecting Symptoms of Chronic Obstructive Pulmonary Disease and Congestive Heart Failure via Cough and Wheezing Sounds Using Smart-Phones and Machine Learning , Anthony Windmon
Toward Culturally Relevant Emotion Detection Using Physiological Signals , Khadija Zanna
Theses/Dissertations from 2019 2019
Beyond Labels and Captions: Contextualizing Grounded Semantics for Explainable Visual Interpretation , Sathyanarayanan Narasimhan Aakur
Empirical Analysis of a Cybersecurity Scoring System , Jaleel Ahmed
Phenomena of Social Dynamics in Online Games , Essa Alhazmi
A Machine Learning Approach to Predicting Community Engagement on Social Media During Disasters , Adel Alshehri
Interactive Fitness Domains in Competitive Coevolutionary Algorithm , ATM Golam Bari
Measuring Influence Across Social Media Platforms: Empirical Analysis Using Symbolic Transfer Entropy , Abhishek Bhattacharjee
A Communication-Centric Framework for Post-Silicon System-on-chip Integration Debug , Yuting Cao
Authentication and SQL-Injection Prevention Techniques in Web Applications , Cagri Cetin
Multimodal Emotion Recognition Using 3D Facial Landmarks, Action Units, and Physiological Data , Diego Fabiano
Robotic Motion Generation by Using Spatial-Temporal Patterns from Human Demonstrations , Yongqiang Huang
A GPU-Based Framework for Parallel Spatial Indexing and Query Processing , Zhila Nouri Lewis
A Flexible, Natural Deduction, Automated Reasoner for Quick Deployment of Non-Classical Logic , Trisha Mukhopadhyay
An Efficient Run-time CFI Check for Embedded Processors to Detect and Prevent Control Flow Based Attacks , Srivarsha Polnati
Force Feedback and Intelligent Workspace Selection for Legged Locomotion Over Uneven Terrain , John Rippetoe
Detecting Digitally Forged Faces in Online Videos , Neilesh Sambhu
Malicious Manipulation in Service-Oriented Network, Software, and Mobile Systems: Threats and Defenses , Dakun Shen
Advanced Search
- Email Notifications and RSS
- All Collections
- USF Faculty Publications
- Open Access Journals
- Conferences and Events
- Theses and Dissertations
- Textbooks Collection
Useful Links
- Rights Information
- SelectedWorks
- Submit Research
Home | About | Help | My Account | Accessibility Statement | Language and Diversity Statements
Privacy Copyright

Computer Engineering: Articles & Journals
- Articles & Journals
- Books & Ebooks
- Standards & Patents
- Citing & Writing Help
- Using AI in Research This link opens in a new window
Journal Title Abbreviations
- All that JAS (Journal Abbreviations Sources)
- Web of Science Journal Title Abbreviations list shows the abbreviations used for journal titles as cited works
Find Articles in Research Databases
- Recommended databases
- Consider these, also
- OneSearch
- Google Scholar
- What is peer review?
Depending on your topic, these databases also may be relevant.
Selected full text articles from journals in a wide range of subjects, plus magazines, reports, books, and more
Selected full text articles from journals, magazines, conference proceedings, and more
Selected full text articles from journals, trade, and popular magazines covering scientific and technical fields
Advanced Search
Sample search: "critical thinking" AND "higher education" (race OR racial) AND (discriminat* OR prejudic*) Select limiters (articles from scholarly publications, etc.) on results screen
While it doesn't offer some of the sophisticated options available in research databases, Google Scholar can be helpful. See instructions for customizing Google Scholar to provide Full Text @ UHCL links in results.

A peer-reviewed (or refereed ) journal:
- uses experts from the same subject field or profession as the author to evaluate a manuscript prior to acceptance for publication
- has articles that report on research studies or provide scholarly analysis of topics
- may include book reviews, editorials, or other brief items that are not considered scholarly articles
- Anatomy of a Scholarly Article Explains key elements from the first & last page of a typical scholarly or academic article. North Carolina State Univ. Libraries
Peer Review in 3 Minutes
(3:15) Explains the academic publishing process for research articles and scholarly journals, including the quality control process of peer review. North Carolina State Univ. Libraries
Get Full Text for an Article
If a database lacks immediate full text, click Find It @ UHCL in results to check for full text from another source. Follow Available Online links in OneSearch to a resource with full text for UH Clear Lake users as shown below.

If full text is not found, submit an article request .
- Request a book, article, or other item ILLiad Interlibrary Loan logon
Other Sources
Links to reliable websites and research guides.
- TechRepublic: Research Library Includes webcasts, white papers, file downloads and more with information on various aspects of technology. Also has blogs and forums.
- CompInfo The Computer Information Center One-stop reference resource for corporate IT, computer software, computers, and communication.
- The Virtual Library: Electrical and Electronics Engineering The WWW Virtual Library (VL) is the oldest catalogue of the Web, started by Tim Berners-Lee, the creator of HTML and of the Web itself. It is run by a loose confederation of volunteers, who compile pages of key links for areas in which they are expert. The VL pages are widely recognised as being amongst the highest-quality guides to particular sections of the Web.
- WWW Computer Architecture Page University of Wisconsin page with links to tools, conferences, people and organizations in Computer Architecture.
- << Previous: Home
- Next: Books & Ebooks >>
- Last Updated: Feb 28, 2024 10:46 AM
- URL: https://uhcl.libguides.com/CENG
Exploring Cutting-Edge Trends: Engineering Research Paper Topics
Table of contents
- 1 How to Choose the Best Engineering Topic for Your Research
- 2.1 Genetic Engineering Research Paper Topics
- 2.2 Nuclear Engineering Research Paper Topics
- 2.3 Research Topics on Security Engineering
- 2.4 Mining and Geological Engineering Research Paper Topics
- 2.5 Mechanical Engineering Research Topics
- 2.6 Materials Engineering Essay Topics
- 2.7 Marine Engineering Research Paper Topics
- 2.8 Industrial Engineering Research Paper Topics
- 2.9 Environmental Engineering Research Paper Topics
- 2.10 Electrical Engineering Research Topics
- 2.11 Computer and Software Engineering Research Topic
- 2.12 Civil Engineering Research Topics
- 2.13 Biomedical Engineering Research Ideas
- 2.14 Automobile Engineering Research Paper Topic
- 2.15 Agricultural Engineering Research Topics
- 2.16 Aerospace Engineering Research Paper Topics
- 2.17 Electrical and Nanoengineering Research Topic
- 2.18 Engineering STEM Research Topics
- 2.19 Engineering Research Topics in Robotics and Automation
- 2.20 Transportation Engineering Research Topics
Embarking on an engineering research paper marks the beginning of a quest for knowledge that could redefine established norms and innovate practices. It’s a thrilling dive into the depths of technical ingenuity and problem-solving. To commence, one must select a beacon—a topic that not only ignites curiosity but also holds the potential to contribute meaningfully to the field. Whether it’s unraveling the complexities of renewable energy systems or exploring the frontiers of nanotechnology, the chosen subject should challenge and inspire. In this realm, precision, relevance, and forward-thinking drive the spirit of inquiry as researchers forge paths that could shape the future of technology.
Selecting the perfect engineering research topics is fundamental in charting a course for breakthroughs and engaging conversations. The purpose of this guide is to help curious individuals find an engineering research topic that fits their interests and the field’s pulse, guaranteeing a journey full of deep learning and significant results.
How to Choose the Best Engineering Topic for Your Research
Choosing the best engineering research topic begins with identifying your areas of interest. Reflect on the subjects that excite you the most and the current issues facing the engineering world. Once you’ve pinpointed your interests, delve into the latest industry trends, advancements, and scholarly discussions. Conferences, journals, and industry publications are gold mines for the newest challenges and innovations that crave exploration.
Next, evaluate the feasibility of the topics on your list. Consider factors such as resource availability, time constraints, and the scope of potential research. Consult with peers and mentors to gauge the relevance and depth of your chosen topic. It’s also wise to factor in the potential for practical application and the contribution your research could make to the field.
Finally, aim for originality. A unique research topic not only stands out but also adds value to the engineering community. By merging your passion with a gap in existing research, you can craft a topic that is both personally rewarding and professionally commendable.
Best Current Research Topics for Engineering
Explore the forefront of innovation with the best current research topics for engineering, a thrilling showcase of groundbreaking ideas poised to redefine technological frontiers and spark transformative advancements in the field.
Genetic Engineering Research Paper Topics
Venture into the realm of genetic engineering, where the potential for innovation intersects with ethical considerations. These engineering research paper topics offer a unique lens into the intricate dance of DNA manipulation and its far-reaching implications.
- CRISPR Cas-9 Precision and its Impact on Genome Editing Techniques
- Gene Therapy Advances for Inherited Disorders
- Synthetic Biology and the Construction of Artificial Life Forms
- Ethical Boundaries in Human Genetic Enhancement
- Genetic Engineering in Agriculture and Crop Resilience
- The Role of Genetic Engineering in Combating Rare Diseases
- Bioprinting Human Tissues for Transplantation and Testing
- Gene Editing’s Potential in Extending Human Lifespan
- Implications of Genetic Privacy in an Era of Genome Editing
- Bioinformatics and the Future of Personalized Medicine in Genetic Engineering
Nuclear Engineering Research Paper Topics
Delving into nuclear engineering offers a glimpse into the powerhouse of energy generation and its safety challenges. The following engineering research topics unpack the complexities of nuclear energy and its role in a sustainable future.
- Advancements in Nuclear Fusion Reactor Design
- Mitigation Strategies for Nuclear Reactor Disasters
- Radioactive Waste Management and Long-Term Containment Solutions
- The Development of Thorium as an Alternative Nuclear Fuel
- Innovations in Nuclear Reactor Safety and Accident Tolerance
- Nuclear Energy’s Role in the Global Transition to Clean Power
- Enhancing Radiation Shielding Techniques for Space Exploration
- Proliferation Risks of Nuclear Materials and Technologies
- Economic Analysis of Lifecycle Costs for Nuclear Power Plants
- Public Perception and Acceptance of Nuclear Energy in the 21st Century
Research Topics on Security Engineering
Security engineering stands at the vanguard of protecting information and infrastructure in our increasingly digital world. These engineering topics to research delve into state-of-the-art defenses and the evolving landscape of threats.
- Quantum Cryptography and the Future of Secure Communication
- Biometric Security Systems and Privacy Implications
- Artificial Intelligence in Cyber Threat Detection and Response
- Blockchain Applications for Decentralized Security Architectures
- Secure Software Development Life Cycle for Emerging Technologies
- Internet of Things (IoT) Security in Smart City Implementations
- Advanced Persistent Threats and Counteracting Network Security Measures
- Social Engineering Attacks and Human-Centric Security Strategies
- Forensic Methods for Detecting Insider Threats
- Risk Management Frameworks for Cloud Computing Security
Mining and Geological Engineering Research Paper Topics
Mining and geological engineering form the bedrock of our quest for natural resources, balancing extraction techniques with environmental stewardship. Here are vital engineering topics to write about that address today’s challenges and future solutions.
- Autonomous and Remote-Controlled Mining Machinery Innovations
- Environmental Impact Assessments of Hydraulic Fracturing Practices
- Geostatistical Analysis of Mineral Resource Estimation
- Slope Stability and Landslide Prevention in Open-Pit Mines
- The Application of Geospatial Technologies in Mineral Exploration
- Mine Rehabilitation and Post-Mining Ecosystem Restoration
- Advancements in Offshore Drilling Technology and Impact Mitigation
- Earthquake Prediction Models and Mining Induced Seismicity
- Rare Earth Element Extraction Techniques and Economic Viability
- Subsidence Engineering and Mitigation in Underground Mining Operations
Mechanical Engineering Research Topics
Mechanical engineering is the cornerstone of innovation, driving forward advancements in technology and industry. These engineering topics for research paper explore the cutting-edge developments and challenges within the mechanical realm.
- 3D Printing of Biodegradable Materials for Sustainable Manufacturing
- Nanotechnology in Mechanical Engineering: Enhancing Material Properties
- Robotics and Automation in Precision Assembly Lines
- Energy Harvesting Techniques for Self-Powered Electronic Devices
- Fluid Dynamics Analysis in Reducing Aerodynamic Drag for Vehicles
- Wearable Technology Innovations for Human Performance Monitoring
- Advanced Composite Materials for Aerospace Application Efficiency
- Thermal Management Systems in Electric Vehicle Battery Packs
- Vibration Analysis for Predictive Maintenance in Heavy Machinery
- Bioinspired Design: Mimicking Nature for Mechanical Solutions
Materials Engineering Essay Topics
Materials engineering is at the forefront of technological progress, shaping the way we build the future with innovative substances and composites. These engineering essay topics delve into the synthesis, analysis, and application of materials that could revolutionize industries.
- Graphene Integration in Electronics and Energy Storage Devices
- Biodegradable Polymers in Sustainable Packaging Solutions
- Self-healing Material Technologies and Their Long-term Durability
- Advanced Ceramics for High-Temperature Structural Applications
- Nanomaterials for Targeted Drug Delivery Systems
- Smart Textiles in Wearable Technology and Their Functionalities
- Metallic Glass Synthesis for Industrial Application
- Corrosion Resistance Strategies in Marine Engineering Materials
- High Entropy Alloys and Their Mechanical Properties
- Photovoltaic Materials for Enhanced Solar Cell Efficiency
Marine Engineering Research Paper Topics
Marine engineering embodies the spirit of exploration and innovation, navigating the challenges of the sea with advanced technology and design. The following topics in engineering dive deep into the ocean’s mysteries and the engineering solutions that sustain life and commerce on the waves.
- Wave Energy Conversion Systems and Coastal Power Generation
- Hull Design Optimization for Fuel Efficiency in Cargo Ships
- Ballast Water Treatment Technologies to Combat Marine Invasions
- Underwater Acoustic Communication Systems for Submersible Vehicles
- Corrosion Resistant Materials for Prolonged Marine Infrastructure Lifespan
- Autonomous Marine Vehicles and Their Navigational Algorithms
- Impact of Climate Change on Ship-Borne Disease Spread
- Sustainable Fishing Techniques and Equipment Design
- Arctic Drilling Equipment and Ice Management Strategies
- Marine Robotics for Deep-Sea Exploration and Resource Extraction
Industrial Engineering Research Paper Topics
Industrial engineering is a nexus of productivity, efficiency, and innovation, integrating complex systems and processes. These interesting engineering topics dissect the intricacies of industry operations and the pursuit of technological advancements for systemic improvements.
- Ergonomic Design in Manufacturing Workstations to Boost Efficiency
- Machine Learning Applications for Supply Chain Optimization
- System Dynamics Modeling for Predictive Production Planning
- Green Manufacturing Practices and Circular Economy Integration
- Human-robot Collaboration and Safety in the Workplace
- Quality Control Enhancements through Statistical Process Control
- Lean Manufacturing Techniques and Waste Reduction Strategies
- Smart Factory Implementations in Industry 4.0
- Simulation of Logistics Networks for Urban Congestion Alleviation
- Cognitive Ergonomics in Industrial Systems Design
Environmental Engineering Research Paper Topics
Environmental engineering is a vital subset of civil engineering, dedicated to creating harmony between construction and the natural world. These topics focus on sustainable development and ecological preservation within the built environment.
- Phytoremediation Techniques in Soil and Water Decontamination
- Carbon Capture and Storage Solutions in Urban Planning
- Impact of Green Roofs on Urban Microclimates
- Sustainable Wastewater Treatment and Reuse Strategies
- Air Quality Management and Pollution Control in Metropolises
- Eco-friendly Concrete Alternatives in Civil Construction
- Bioreactor Landfills and Methane Harvesting Technologies
- Riverbank Filtration Systems for Potable Water Supplies
- Noise Pollution Reduction in Highway Engineering
- GIS Applications in Hazardous Waste Site Remediation
Electrical Engineering Research Topics
Electrical engineering propels countless innovations, from microelectronics to massive power grids. The following topics highlight the dynamic and essential developments reshaping the electrical landscape.
- Wireless Power Transfer Systems for Electric Vehicle Charging
- Organic Photovoltaic Cells for Improved Solar Energy Harvesting
- Nano-electromechanical Systems in Medical Device Engineering
- Energy Storage Solutions in High-Density Lithium-Ion Batteries
- Smart Grid Technologies for Distributed Energy Resources Management
- Electromagnetic Field Effects on Human Health
- Machine Vision Algorithms for Automated Quality Inspection
- Flexible Electronics for Wearable Technology Applications
- High-frequency Trading Algorithms and Market Impact Analysis
- Quantum Computing and Its Role in Cryptography
Computer and Software Engineering Research Topic
Computer and software engineering stands at the cutting edge of innovation, constantly evolving to meet the demands of a digital future. These software engineering research topics delve into the algorithms, systems, and applications driving progress in this ever-expanding field.
- Agile Methodologies Impact on Software Development Lifecycle
- Cybersecurity in Cloud Computing Environments
- Application of Artificial Intelligence in Automated Code Generation
- Blockchain Technology Beyond Cryptocurrency
- Human-Computer Interaction and User Experience Optimization
- Internet of Things Security Protocols for Smart Home Systems
- Machine Learning Techniques in Predictive Software Analytics
- Virtual Reality Integration in Software Testing Environments
- Software Solutions for Big Data Management and Analysis
- Ethical Implications of Autonomous Decision-making Systems

Civil Engineering Research Topics
Civil engineering is a pillar of societal development, encompassing the design and construction of infrastructure that underpins our daily lives. The research topics in civil engineering listed below address the contemporary challenges and technological strides shaping the field’s future.
- Seismic Retrofitting Techniques for Aging Infrastructure
- Sustainable Urban Drainage Systems and Flood Risk Mitigation
- Smart Materials for Self-repairing Concrete Structures
- Advanced Geotechnical Methods for Landslide Prevention
- The Role of Civil Engineering in Urban Heat Island Reduction
- Lifecycle Assessment of Green Building Materials
- Integration of Autonomous Vehicles into Urban Traffic Management
- 3D Printing in Rapid Construction and Design Prototyping
- Water Reclamation and Reuse in Megacities
- Innovations in Bridge Engineering for Enhanced Longevity and Durability
Biomedical Engineering Research Ideas
Biomedical engineering merges the intricate world of medicine with the precision of engineering, opening new frontiers in healthcare. While these are not topics, they embody a similar spirit of technical innovation applied to biological systems.
- Tissue Engineering Strategies for 3D-Printed Organs
- Wearable Biosensors for Real-Time Health Monitoring
- Nanorobots in Targeted Drug Delivery Systems
- Neural Engineering for Brain-Machine Interface Development
- Biocompatible Materials for Implantable Medical Devices
- Advanced Prosthetics Controlled by Electromyographic Signals
- Artificial Intelligence in Diagnostic Imaging Techniques
- Biomimicry in Medical Device Design
- Regenerative Medicine and Stem Cell Therapy Applications
- Computational Modeling for Personalized Medicine Treatment Plans
Automobile Engineering Research Paper Topic
Automobile engineering is continuously evolving, driven by the quest for sustainability, efficiency, and cutting-edge technology. Although distinct from software engineering topics for research, these themes share a focus on innovation and design in the quest for advancement.
- Electric Vehicle Battery Management Systems for Optimal Performance
- Autonomous Vehicle Sensor Integration and Data Fusion
- Hydrogen Fuel Cell Advancements for Zero-Emission Cars
- Aerodynamic Design for Enhanced Fuel Efficiency in Commercial Vehicles
- Advanced Driver-Assistance Systems and their Impact on Traffic Safety
- Smart Materials for Lightweight and Durable Automotive Components
- Integration of IoT in Vehicle-to-Vehicle Communication Systems
- Predictive Maintenance in Automotive Engineering using Machine Learning
- Noise, Vibration, and Harshness Reduction Techniques in Car Design
- The Impact of Vehicle Electrification on Urban Planning and Infrastructure
Agricultural Engineering Research Topics
Agricultural engineering fuses the knowledge of engineering with agricultural practice to solve crucial challenges in food production and farming sustainability. While not inherently controversial engineering topics, these subjects often stir debate due to their significance in global food security and environmental impact.
- Precision Farming Technologies to Maximize Crop Yield
- Water Resource Management for Sustainable Irrigation Practices
- Genetic Engineering of Crops for Climate Resilience
- Renewable Energy Systems in Agriculture
- Robotics and Automation in Precision Livestock Farming
- Post-Harvest Technology for Reducing Food Loss
- Soil Health Monitoring Techniques for Enhanced Nutrient Management
- Agrochemicals Delivery Systems and Their Environmental Footprint
- Controlled Environment Agriculture for Urban Farming Efficiency
- Bioenergy Production from Agricultural Waste Management Systems
Aerospace Engineering Research Paper Topics
Aerospace engineering takes us beyond the confines of Earth, embracing the vastness of space with technologies that defy gravity. These topics, while distinct from genetic engineering research topics, are similarly ambitious, exploring the limits of human ingenuity and the potential for discovery beyond our atmosphere.
- Materials Engineering for High-Stress Aerospace Applications
- Computational Fluid Dynamics in Hypersonic Vehicle Design
- Satellite Swarm Navigation Techniques for Space Exploration
- Innovative Propulsion Systems for Deep Space Missions
- Bioastronautics: Sustaining Life in Space Environments
- Impact of Microgravity on Mechanical Systems Design
- Unmanned Aerial Vehicle Aerodynamics for Mars Reconnaissance
- Thermal Protection Systems in Re-entry Vehicle Engineering
- Design Optimization of Spacecraft Life Support Systems
- Advanced Rocketry and the Viability of Space Tourism
Electrical and Nanoengineering Research Topic
Electrical engineering is a dynamic field that encompasses the study and application of electricity and electronics, propelling countless modern innovations. These topics extend into the realm of topic, probing into the minutiae of materials and processes that power our electronic devices.
- Nanoscale Semiconductor Devices for Next-Generation Computing
- Organic Light-Emitting Diodes in Flexible Display Technology
- Quantum Dot Solar Cells for Enhanced Photovoltaic Efficiency
- Nanomaterials in High-Density Energy Storage Solutions
- Nano-antennas for Improved Wireless Communication Systems
- Magnetic Nanoparticles in Medical Imaging and Diagnostics
- Nanotechnology in Electromagnetic Interference Shielding
- Nanostructured Materials for Advanced Sensor Technologies
- Nanofabrication Techniques for Superconducting Electronics
- Energy Harvesting at the Nanoscale for Self-Powered Devices
Engineering STEM Research Topics
Engineering STEM is an ever-expanding field, pivotal to the advancements in how we connect and interact with technology. These engineering STEM research topics address the latest innovations and challenges in creating more efficient, robust, and sophisticated communication systems.
- 5G Network Infrastructure and its Socioeconomic Impacts
- Machine Learning Algorithms for Enhanced Signal Processing
- Organic Transistors in Flexible Electronics
- Wearable Communication Devices for Health Monitoring
- Low Earth Orbit Satellite Constellations for Global Internet Coverage
- Signal Encryption Techniques for Secure Communication Channels
- Energy-Efficient Routing Protocols in Mobile Ad-hoc Networks
- Integration of LiFi for Next-Generation Wireless Communication
- Quantum Computing’s Role in Advancing Cryptography
- The Evolution of Underwater Acoustic Sensor Networks
Engineering Research Topics in Robotics and Automation
Robotics and automation stand at the forefront of engineering, blending artificial intelligence with mechanical prowess to innovate how tasks are performed. These research topics delve into the transformative potential of robots and automated systems, from intricate surgeries to industrial assembly lines.
- Swarm Robotics Coordination Algorithms for Disaster Relief Operations
- Collaborative Robots and Human-Robot Interaction Safety Protocols
- Adaptive Control Systems for Precision Agriculture Robotics
- Augmented Reality in Enhancing Robotic Assembly Line Training
- AI-Driven Predictive Maintenance in Industrial Automation
- Soft Robotics Applications in Minimally Invasive Surgery
- Development of Energy-Efficient Actuators for Sustainable Robotics
- Machine Vision Systems for Quality Control in Manufacturing
- Robotic Exoskeletons for Rehabilitation and Enhanced Mobility
- Automation in Smart Grids for Optimized Energy Distribution
Transportation Engineering Research Topics
Transportation engineering is a key driver in the advancement of mobility solutions, focusing on the design, construction, and maintenance of efficient transport systems. These research topics investigate the development of safer, more sustainable, and technologically advanced transportation networks.
- Impact of Autonomous Vehicles on Urban Traffic Flow
- Eco-Friendly Pavement Materials and Their Lifecycle Assessment
- Smart Traffic Signal Systems for Reduced Congestion
- Electrification of Public Transit and Infrastructure Challenges
- Pedestrian Flow Dynamics in Urban Planning
- Bridge Health Monitoring Using IoT Sensors
- High-Speed Rail Systems and Cross-Border Integration Challenges
- Adaptive Cruise Control Systems in Vehicle Safety Enhancement
- Drone Technology in Expedited Cargo Delivery
- Multi-Modal Transportation Planning for Improved Accessibility
Readers also enjoyed

WHY WAIT? PLACE AN ORDER RIGHT NOW!
Just fill out the form, press the button, and have no worries!
We use cookies to give you the best experience possible. By continuing we’ll assume you board with our cookie policy.
- Write my thesis
- Thesis writers
- Buy thesis papers
- Bachelor thesis
- Master's thesis
- Thesis editing services
- Thesis proofreading services
- Buy a thesis online
- Write my dissertation
- Dissertation proposal help
- Pay for dissertation
- Custom dissertation
- Dissertation help online
- Buy dissertation online
- Cheap dissertation
- Dissertation editing services
- Write my research paper
- Buy research paper online
- Pay for research paper
- Research paper help
- Order research paper
- Custom research paper
- Cheap research paper
- Research papers for sale
- Thesis subjects
- How It Works
100 Great Computer Science Research Topics Ideas for 2023
Being a computer student in 2023 is not easy. Besides studying a constantly evolving subject, you have to come up with great computer science research topics at some point in your academic life. If you’re reading this article, you’re among many other students that have also come to this realization.
Interesting Computer Science Topics
Awesome research topics in computer science, hot topics in computer science, topics to publish a journal on computer science.
- Controversial Topics in Computer Science
Fun AP Computer Science Topics
Exciting computer science ph.d. topics, remarkable computer science research topics for undergraduates, incredible final year computer science project topics, advanced computer science topics, unique seminars topics for computer science, exceptional computer science masters thesis topics, outstanding computer science presentation topics.
- Key Computer Science Essay Topics
Main Project Topics for Computer Science
- We Can Help You with Computer Science Topics
Whether you’re earnestly searching for a topic or stumbled onto this article by accident, there is no doubt that every student needs excellent computer science-related topics for their paper. A good topic will not only give your essay or research a good direction but will also make it easy to come up with supporting points. Your topic should show all your strengths as well.
Fortunately, this article is for every student that finds it hard to generate a suitable computer science topic. The following 100+ topics will help give you some inspiration when creating your topics. Let’s get into it.
One of the best ways of making your research paper interesting is by coming up with relevant topics in computer science . Here are some topics that will make your paper immersive:
- Evolution of virtual reality
- What is green cloud computing
- Ways of creating a Hopefield neural network in C++
- Developments in graphic systems in computers
- The five principal fields in robotics
- Developments and applications of nanotechnology
- Differences between computer science and applied computing
Your next research topic in computer science shouldn’t be tough to find once you’ve read this section. If you’re looking for simple final year project topics in computer science, you can find some below.
- Applications of the blockchain technology in the banking industry
- Computational thinking and how it influences science
- Ways of terminating phishing
- Uses of artificial intelligence in cyber security
- Define the concepts of a smart city
- Applications of the Internet of Things
- Discuss the applications of the face detection application
Whenever a topic is described as “hot,” it means that it is a trendy topic in computer science. If computer science project topics for your final years are what you’re looking for, have a look at some below:
- Applications of the Metaverse in the world today
- Discuss the challenges of machine learning
- Advantages of artificial intelligence
- Applications of nanotechnology in the paints industry
- What is quantum computing?
- Discuss the languages of parallel computing
- What are the applications of computer-assisted studies?
Perhaps you’d like to write a paper that will get published in a journal. If you’re searching for the best project topics for computer science students that will stand out in a journal, check below:
- Developments in human-computer interaction
- Applications of computer science in medicine
- Developments in artificial intelligence in image processing
- Discuss cryptography and its applications
- Discuss methods of ransomware prevention
- Applications of Big Data in the banking industry
- Challenges of cloud storage services in 2023
Controversial Topics in Computer Science
Some of the best computer science final year project topics are those that elicit debates or require you to take a stand. You can find such topics listed below for your inspiration:
- Can robots be too intelligent?
- Should the dark web be shut down?
- Should your data be sold to corporations?
- Will robots completely replace the human workforce one day?
- How safe is the Metaverse for children?
- Will artificial intelligence replace actors in Hollywood?
- Are social media platforms safe anymore?
Are you a computer science student looking for AP topics? You’re in luck because the following final year project topics for computer science are suitable for you.
- Standard browser core with CSS support
- Applications of the Gaussian method in C++ development in integrating functions
- Vital conditions of reducing risk through the Newton method
- How to reinforce machine learning algorithms.
- How do artificial neural networks function?
- Discuss the advancements in computer languages in machine learning
- Use of artificial intelligence in automated cars
When studying to get your doctorate in computer science, you need clear and relevant topics that generate the reader’s interest. Here are some Ph.D. topics in computer science you might consider:
- Developments in information technology
- Is machine learning detrimental to the human workforce?
- How to write an algorithm for deep learning
- What is the future of 5G in wireless networks
- Statistical data in Maths modules in Python
- Data retention automation from a website using API
- Application of modern programming languages
Looking for computer science topics for research is not easy for an undergraduate. Fortunately, these computer science project topics should make your research paper easy:
- Ways of using artificial intelligence in real estate
- Discuss reinforcement learning and its applications
- Uses of Big Data in science and medicine
- How to sort algorithms using Haskell
- How to create 3D configurations for a website
- Using inverse interpolation to solve non-linear equations
- Explain the similarities between the Internet of Things and artificial intelligence
Your dissertation paper is one of the most crucial papers you’ll ever do in your final year. That’s why selecting the best ethics in computer science topics is a crucial part of your paper. Here are some project topics for the computer science final year.
- How to incorporate numerical methods in programming
- Applications of blockchain technology in cloud storage
- How to come up with an automated attendance system
- Using dynamic libraries for site development
- How to create cubic splines
- Applications of artificial intelligence in the stock market
- Uses of quantum computing in financial modeling
Your instructor may want you to challenge yourself with an advanced science project. Thus, you may require computer science topics to learn and research. Here are some that may inspire you:
- Discuss the best cryptographic protocols
- Advancement of artificial intelligence used in smartphones
- Briefly discuss the types of security software available
- Application of liquid robots in 2023
- How to use quantum computers to solve decoherence problem
- macOS vs. Windows; discuss their similarities and differences
- Explain the steps taken in a cyber security audit
When searching for computer science topics for a seminar, make sure they are based on current research or events. Below are some of the latest research topics in computer science:
- How to reduce cyber-attacks in 2023
- Steps followed in creating a network
- Discuss the uses of data science
- Discuss ways in which social robots improve human interactions
- Differentiate between supervised and unsupervised machine learning
- Applications of robotics in space exploration
- The contrast between cyber-physical and sensor network systems
Are you looking for computer science thesis topics for your upcoming projects? The topics below are meant to help you write your best paper yet:
- Applications of computer science in sports
- Uses of computer technology in the electoral process
- Using Fibonacci to solve the functions maximum and their implementations
- Discuss the advantages of using open-source software
- Expound on the advancement of computer graphics
- Briefly discuss the uses of mesh generation in computational domains
- How much data is generated from the internet of things?
A computer science presentation requires a topic relevant to current events. Whether your paper is an assignment or a dissertation, you can find your final year computer science project topics below:
- Uses of adaptive learning in the financial industry
- Applications of transitive closure on graph
- Using RAD technology in developing software
- Discuss how to create maximum flow in the network
- How to design and implement functional mapping
- Using artificial intelligence in courier tracking and deliveries
- How to make an e-authentication system
Key Computer Science Essay Topics
You may be pressed for time and require computer science master thesis topics that are easy. Below are some topics that fit this description:
- What are the uses of cloud computing in 2023
- Discuss the server-side web technologies
- Compare and contrast android and iOS
- How to come up with a face detection algorithm
- What is the future of NFTs
- How to create an artificial intelligence shopping system
- How to make a software piracy prevention algorithm
One major mistake students make when writing their papers is selecting topics unrelated to the study at hand. This, however, will not be an issue if you get topics related to computer science, such as the ones below:
- Using blockchain to create a supply chain management system
- How to protect a web app from malicious attacks
- Uses of distributed information processing systems
- Advancement of crowd communication software since COVID-19
- Uses of artificial intelligence in online casinos
- Discuss the pillars of math computations
- Discuss the ethical concerns arising from data mining
We Can Help You with Computer Science Topics, Essays, Thesis, and Research Papers
We hope that this list of computer science topics helps you out of your sticky situation. We do offer other topics in different subjects. Additionally, we also offer professional writing services tailor-made for you.
We understand what students go through when searching the internet for computer science research paper topics, and we know that many students don’t know how to write a research paper to perfection. However, you shouldn’t have to go through all this when we’re here to help.
Don’t waste any more time; get in touch with us today and get your paper done excellently.
Leave a Reply Cancel reply
University Library, University of Illinois at Urbana-Champaign

Electrical and Computer Engineering Research Resources: Find Articles & Papers
- Find Articles & Papers
- High-Impact Journals
- Standards & Technical Reports
- Patents & Government Documents
- E-Books & Reference
- Dissertations & Theses
- Additional Resources
Engineering Easy Search
University library search engines.
- Grainger Engineering Library Homepage With specialized searches for Engineering and the Physical Sciences.
- Easy Search The easiest way to locate University Library resources, materials, and more!
- Find Online Journals Search by title or by subject to view our subscription details, including date ranges and where you can access full text.
- Journal and Article Locator Finds electronic or print copy of articles by using a citation.
Engineering Article Databases
- Engineering Village This link opens in a new window Search for articles, conference paper, and report information in all areas of engineering. Full-text is often available through direct download.
- Scopus This link opens in a new window Search periodicals, conference proceedings, technical reports, trade literature, patents, books, and press releases in all engineering fields. Some full-text available as direct downloads.
- Web of Science (Core Collection) This link opens in a new window Search for articles in science and engineering. Also provides Science Citation Index that tracks citations in science and technical journals published since 1981. Journal Citation Reports are also available through ISI.
Electrical & Computer Engineering
- ACM Digital Library This site provides access to tables of contents, abstracts, reviews, and full text of every article ever published by ACM and bibliographic citations from major publishers in computing.
- ENGnetBASE A collection of best-selling engineering handbooks and reference titles. Includes access to sub-collections: CivilENGINEERINGnetBASE, ElectricalENGINEERINGnetBASE, GeneralENGINEERINGnetBASE, IndustrialENGINEERINGnetBASE, MechanicalENGINEERINGnetBASE, MiningENGINEERINGnetBASE.
- IEEE Xplore Provides full-text access to IEEE transactions, IEEE and IEE journals, magazines, and conference proceedings published since 1988, and all current IEEE standards; brings additional search and access features to IEEE/IEE digital library users. Browsable by books & e-books, conference publications, education and learning, journals and magazines, standards and by topic. Also provides links to IEEE standards, IEEE spectrum and other sites.
- INSPEC Database providing access to bibliographic citations and abstracts of the scientific and technical literature in physics, electrical engineering, electronics, communications, control engineering, computers and computing, information technology, manufacturing and production engineering. Material covered includes journal articles, conference proceedings, reports, dissertations, patents and books published around the world.
- Microelectronics Packaging Materials Database (MPMD) The MPMD database contains data and information on thermal, mechanical, electrical and physical properties of electronics packaging materials. Available in a Web-based format. The database is continually updated and expanded.
- SPIE Digital Library Contains full-text papers on optics and photonics from SPIE journals and proceedings published since 1990. Approximately 15,000 new papers will be added each year.
Subject Guide

Ask a Librarian
- Next: High-Impact Journals >>
- Last Updated: Jun 16, 2023 9:35 AM
- URL: https://guides.library.illinois.edu/ece
For enquiries call:
+1-469-442-0620

- Programming
Latest Computer Science Research Topics for 2024
Home Blog Programming Latest Computer Science Research Topics for 2024
Everybody sees a dream—aspiring to become a doctor, astronaut, or anything that fits your imagination. If you were someone who had a keen interest in looking for answers and knowing the “why” behind things, you might be a good fit for research. Further, if this interest revolved around computers and tech, you would be an excellent computer researcher!
As a tech enthusiast, you must know how technology is making our life easy and comfortable. With a single click, Google can get you answers to your silliest query or let you know the best restaurants around you. Do you know what generates that answer? Want to learn about the science going on behind these gadgets and the internet?
For this, you will have to do a bit of research. Here we will learn about top computer science thesis topics and computer science thesis ideas.
Why is Research in Computer Science Important?
Computers and technology are becoming an integral part of our lives. We are dependent on them for most of our work. With the changing lifestyle and needs of the people, continuous research in this sector is required to ease human work. However, you need to be a certified researcher to contribute to the field of computers. You can check out Advance Computer Programming certification to learn and advance in the versatile language and get hands-on experience with all the topics of C# application development.
1. Innovation in Technology
Research in computer science contributes to technological advancement and innovations. We end up discovering new things and introducing them to the world. Through research, scientists and engineers can create new hardware, software, and algorithms that improve the functionality, performance, and usability of computers and other digital devices.
2. Problem-Solving Capabilities
From disease outbreaks to climate change, solving complex problems requires the use of advanced computer models and algorithms. Computer science research enables scholars to create methods and tools that can help in resolving these challenging issues in a blink of an eye.
3. Enhancing Human Life
Computer science research has the potential to significantly enhance human life in a variety of ways. For instance, researchers can produce educational software that enhances student learning or new healthcare technology that improves clinical results. If you wish to do Ph.D., these can become interesting computer science research topics for a PhD.
4. Security Assurance
As more sensitive data is being transmitted and kept online, security is our main concern. Computer science research is crucial for creating new security systems and tactics that defend against online threats.
Top Computer Science Research Topics
Before starting with the research, knowing the trendy research paper ideas for computer science exploration is important. It is not so easy to get your hands on the best research topics for computer science; spend some time and read about the following mind-boggling ideas before selecting one.
1. Integrated Blockchain and Edge Computing Systems: A Survey, Some Research Issues, and Challenges
Welcome to the era of seamless connectivity and unparalleled efficiency! Blockchain and edge computing are two cutting-edge technologies that have the potential to revolutionize numerous sectors. Blockchain is a distributed ledger technology that is decentralized and offers a safe and transparent method of storing and transferring data.
As a young researcher, you can pave the way for a more secure, efficient, and scalable architecture that integrates blockchain and edge computing systems. So, let's roll up our sleeves and get ready to push the boundaries of technology with this exciting innovation!
Blockchain helps to reduce latency and boost speed. Edge computing, on the other hand, entails processing data close to the generation source, such as sensors and IoT devices. Integrating edge computing with blockchain technologies can help to achieve safer, more effective, and scalable architecture.
Moreover, this research title for computer science might open doors of opportunities for you in the financial sector.
2. A Survey on Edge Computing Systems and Tools
With the rise in population, the data is multiplying by manifolds each day. It's high time we find efficient technology to store it. However, more research is required for the same.
Say hello to the future of computing with edge computing! The edge computing system can store vast amounts of data to retrieve in the future. It also provides fast access to information in need. It maintains computing resources from the cloud and data centers while processing.
Edge computing systems bring processing power closer to the data source, resulting in faster and more efficient computing. But what tools are available to help us harness the power of edge computing?
As a part of this research, you will look at the newest edge computing tools and technologies to see how they can improve your computing experience. Here are some of the tools you might get familiar with upon completion of this research:
- Apache NiFi: A framework for data processing that enables users to gather, transform, and transfer data from edge devices to cloud computing infrastructure.
- Microsoft Azure IoT Edge: A platform in the cloud that enables the creation and deployment of cutting-edge intelligent applications.
- OpenFog Consortium: An organization that supports the advancement of fog computing technologies and architectures is the OpenFog Consortium.
3. Machine Learning: Algorithms, Real-world Applications, and Research Directions
Machine learning is the superset of Artificial Intelligence; a ground-breaking technology used to train machines to mimic human action and work. ML is used in everything from virtual assistants to self-driving cars and is revolutionizing the way we interact with computers. But what is machine learning exactly, and what are some of its practical uses and future research directions?
To find answers to such questions, it can be a wonderful choice to pick from the pool of various computer science dissertation ideas.
You will discover how computers learn several actions without explicit programming and see how they perform beyond their current capabilities. However, to understand better, having some basic programming knowledge always helps. KnowledgeHut’s Programming course for beginners will help you learn the most in-demand programming languages and technologies with hands-on projects.
During the research, you will work on and study
- Algorithm: Machine learning includes many algorithms, from decision trees to neural networks.
- Applications in the Real-world: You can see the usage of ML in many places. It can early detect and diagnose diseases like cancer. It can detect fraud when you are making payments. You can also use it for personalized advertising.
- Research Trend: The most recent developments in machine learning research, include explainable AI, reinforcement learning, and federated learning.
While a single research paper is not enough to bring the light on an entire domain as vast as machine learning; it can help you witness how applicable it is in numerous fields, like engineering, data science & analysis, business intelligence, and many more.
Whether you are a data scientist with years of experience or a curious tech enthusiast, machine learning is an intriguing and vital field that's influencing the direction of technology. So why not dig deeper?
4. Evolutionary Algorithms and their Applications to Engineering Problems
Imagine a system that can solve most of your complex queries. Are you interested to know how these systems work? It is because of some algorithms. But what are they, and how do they work? Evolutionary algorithms use genetic operators like mutation and crossover to build new generations of solutions rather than starting from scratch.
This research topic can be a choice of interest for someone who wants to learn more about algorithms and their vitality in engineering.
Evolutionary algorithms are transforming the way we approach engineering challenges by allowing us to explore enormous solution areas and optimize complex systems.
The possibilities are infinite as long as this technology is developed further. Get ready to explore the fascinating world of evolutionary algorithms and their applications in addressing engineering issues.
5. The Role of Big Data Analytics in the Industrial Internet of Things
Datasets can have answers to most of your questions. With good research and approach, analyzing this data can bring magical results. Welcome to the world of data-driven insights! Big Data Analytics is the transformative process of extracting valuable knowledge and patterns from vast and complex datasets, boosting innovation and informed decision-making.
This field allows you to transform the enormous amounts of data produced by IoT devices into insightful knowledge that has the potential to change how large-scale industries work. It's like having a crystal ball that can foretell.
Big data analytics is being utilized to address some of the most critical issues, from supply chain optimization to predictive maintenance. Using it, you can find patterns, spot abnormalities, and make data-driven decisions that increase effectiveness and lower costs for several industrial operations by analyzing data from sensors and other IoT devices.
The area is so vast that you'll need proper research to use and interpret all this information. Choose this as your computer research topic to discover big data analytics' most compelling applications and benefits. You will see that a significant portion of industrial IoT technology demands the study of interconnected systems, and there's nothing more suitable than extensive data analysis.
6. An Efficient Lightweight Integrated Blockchain (ELIB) Model for IoT Security and Privacy
Are you concerned about the security and privacy of your Internet of Things (IoT) devices? As more and more devices become connected, it is more important than ever to protect the security and privacy of data. If you are interested in cyber security and want to find new ways of strengthening it, this is the field for you.
ELIB is a cutting-edge solution that offers private and secure communication between IoT devices by fusing the strength of blockchain with lightweight cryptography. This architecture stores encrypted data on a distributed ledger so only parties with permission can access it.
But why is ELIB so practical and portable? ELIB uses lightweight cryptography to provide quick and effective communication between devices, unlike conventional blockchain models that need complicated and resource-intensive computations.
Due to its increasing vitality, it is gaining popularity as a research topic as someone aware that this framework works and helps reinstate data security is highly demanded in financial and banking.
7. Natural Language Processing Techniques to Reveal Human-Computer Interaction for Development Research Topics
Welcome to the world where machines decode the beauty of the human language. With natural language processing (NLP) techniques, we can analyze the interactions between humans and computers to reveal valuable insights for development research topics. It is also one of the most crucial PhD topics in computer science as NLP-based applications are gaining more and more traction.
Etymologically, natural language processing (NLP) is a potential technique that enables us to examine and comprehend natural language data, such as discussions between people and machines. Insights on user behaviour, preferences, and pain areas can be gleaned from these encounters utilizing NLP approaches.
But which specific areas should we leverage on using NLP methods? This is precisely what you’ll discover while doing this computer science research.
Gear up to learn more about the fascinating field of NLP and how it can change how we design and interact with technology, whether you are a UX designer, a data scientist, or just a curious tech lover and linguist.
8. All One Needs to Know About Fog Computing and Related Edge Computing Paradigms: A Complete Survey
If you are an IoT expert or a keen lover of the Internet of Things, you should leap and move forward to discovering Fog Computing. With the rise of connected devices and the Internet of Things (IoT), traditional cloud computing models are no longer enough. That's where fog computing and related edge computing paradigms come in.
Fog computing is a distributed approach that brings processing and data storage closer to the devices that generate and consume data by extending cloud computing to the network's edge.
As computing technologies are significantly used today, the area has become a hub for researchers to delve deeper into the underlying concepts and devise more and more fog computing frameworks. You can also contribute to and master this architecture by opting for this stand-out topic for your research.
Tips and Tricks to Write Computer Research Topics
Before starting to explore these hot research topics in computer science you may have to know about some tips and tricks that can easily help you.
- Know your interest.
- Choose the topic wisely.
- Make proper research about the demand of the topic.
- Get proper references.
- Discuss with experts.
By following these tips and tricks, you can write a compelling and impactful computer research topic that contributes to the field's advancement and addresses important research gaps.
From machine learning and artificial intelligence to blockchain, edge computing, and big data analytics, numerous trending computer research topics exist to explore.
One of the most important trends is using cutting-edge technology to address current issues. For instance, new IIoT security and privacy opportunities are emerging by integrating blockchain and edge computing. Similarly, the application of natural language processing methods is assisting in revealing human-computer interaction and guiding the creation of new technologies.
Another trend is the growing emphasis on sustainability and moral considerations in technological development. Researchers are looking into how computer science might help in innovation.
With the latest developments and leveraging cutting-edge tools and techniques, researchers can make meaningful contributions to the field and help shape the future of technology. Going for Full-stack Developer online training will help you master the latest tools and technologies.
Frequently Asked Questions (FAQs)
Research in computer science is mainly focused on different niches. It can be theoretical or technical as well. It completely depends upon the candidate and his focused area. They may do research for inventing new algorithms or many more to get advanced responses in that field.
Yes, moreover it would be a very good opportunity for the candidate. Because computer science students may have a piece of knowledge about the topic previously. They may find Easy thesis topics for computer science to fulfill their research through KnowledgeHut.
There are several scopes available for computer science. A candidate can choose different subjects such as AI, database management, software design, graphics, and many more.

Ramulu Enugurthi
Ramulu Enugurthi, a distinguished computer science expert with an M.Tech from IIT Madras, brings over 15 years of software development excellence. Their versatile career spans gaming, fintech, e-commerce, fashion commerce, mobility, and edtech, showcasing adaptability in multifaceted domains. Proficient in building distributed and microservices architectures, Ramulu is renowned for tackling modern tech challenges innovatively. Beyond technical prowess, he is a mentor, sharing invaluable insights with the next generation of developers. Ramulu's journey of growth, innovation, and unwavering commitment to excellence continues to inspire aspiring technologists.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Programming Batches & Dates
Computer Technology Research Paper Topics

This list of computer technology research paper topics provides the list of 33 potential topics for research papers and an overview article on the history of computer technology.
1. Analog Computers
Paralleling the split between analog and digital computers, in the 1950s the term analog computer was a posteriori projected onto pre-existing classes of mechanical, electrical, and electromechanical computing artifacts, subsuming them under the same category. The concept of analog, like the technical demarcation between analog and digital computer, was absent from the vocabulary of those classifying artifacts for the 1914 Edinburgh Exhibition, the first world’s fair emphasizing computing technology, and this leaves us with an invaluable index of the impressive number of classes of computing artifacts amassed during the few centuries of capitalist modernity. True, from the debate between ‘‘smooth’’ and ‘‘lumpy’’ artificial lines of computing (1910s) to the differentiation between ‘‘continuous’’ and ‘‘cyclic’’ computers (1940s), the subsequent analog–digital split became possible by the multitudinous accumulation of attempts to decontextualize the computer from its socio-historical use alternately to define the ideal computer technically. The fact is, however, that influential classifications of computing technology from the previous decades never provided an encompassing demarcation compared to the analog– digital distinction used since the 1950s. Historians of the digital computer find that the experience of working with software was much closer to art than science, a process that was resistant to mass production; historians of the analog computer find this to have been typical of working with the analog computer throughout all its aspects. The historiography of the progress of digital computing invites us to turn to the software crisis, which perhaps not accidentally, surfaced when the crisis caused by the analog ended. Noticeably, it was not until the process of computing with a digital electronic computer became sufficiently visual by the addition of a special interface—to substitute for the loss of visualization that was previously provided by the analog computer—that the analog computer finally disappeared.
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code, 2. artificial intelligence.
Artificial intelligence (AI) is the field of software engineering that builds computer systems and occasionally robots to perform tasks that require intelligence. The term ‘‘artificial intelligence’’ was coined by John McCarthy in 1958, then a graduate student at Princeton, at a summer workshop held at Dartmouth in 1956. This two-month workshop marks the official birth of AI, which brought together young researchers who would nurture the field as it grew over the next several decades: Marvin Minsky, Claude Shannon, Arthur Samuel, Ray Solomonoff, Oliver Selfridge, Allen Newell, and Herbert Simon. It would be difficult to argue that the technologies derived from AI research had a profound effect on our way of life by the beginning of the 21st century. However, AI technologies have been successfully applied in many industrial settings, medicine and health care, and video games. Programming techniques developed in AI research were incorporated into more widespread programming practices, such as high-level programming languages and time-sharing operating systems. While AI did not succeed in constructing a computer which displays the general mental capabilities of a typical human, such as the HAL computer in Arthur C. Clarke and Stanley Kubrick’s film 2001: A Space Odyssey, it has produced programs that perform some apparently intelligent tasks, often at a much greater level of skill and reliability than humans. More than this, AI has provided a powerful and defining image of what computer technology might someday be capable of achieving.
3. Computer and Video Games
Interactive computer and video games were first developed in laboratories as the late-night amusements of computer programmers or independent projects of television engineers. Their formats include computer software; networked, multiplayer games on time-shared systems or servers; arcade consoles; home consoles connected to television sets; and handheld game machines. The first experimental projects grew out of early work in computer graphics, artificial intelligence, television technology, hardware and software interface development, computer-aided education, and microelectronics. Important examples were Willy Higinbotham’s oscilloscope-based ‘‘Tennis for Two’’ at the Brookhaven National Laboratory (1958); ‘‘Spacewar!,’’ by Steve Russell, Alan Kotok, J. Martin Graetz and others at the Massachusetts Institute of Technology (1962); Ralph Baer’s television-based tennis game for Sanders Associates (1966); several networked games from the PLATO (Programmed Logic for Automatic Teaching Operations) Project at the University of Illinois during the early 1970s; and ‘‘Adventure,’’ by Will Crowther of Bolt, Beranek & Newman (1972), extended by Don Woods at Stanford University’s Artificial Intelligence Laboratory (1976). The main lines of development during the 1970s and early 1980s were home video consoles, coin-operated arcade games, and computer software.
4. Computer Displays
The display is an essential part of any general-purpose computer. Its function is to act as an output device to communicate data to humans using the highest bandwidth input system that humans possess—the eyes. Much of the development of computer displays has been about trying to get closer to the limits of human visual perception in terms of color and spatial resolution. Mainframe and minicomputers used ‘‘terminals’’ to display the output. These were fed data from the host computer and processed the data to create screen images using a graphics processor. The display was typically integrated with a keyboard system and some communication hardware as a terminal or video display unit (VDU) following the basic model used for teletypes. Personal computers (PCs) in the late 1970s and early 1980s changed this model by integrating the graphics controller into the computer chassis itself. Early PC displays typically displayed only monochrome text and communicated in character codes such as ASCII. Line-scanning frequencies were typically from 15 to 20 kilohertz—similar to television. CRT displays rapidly developed after the introduction of video graphics array (VGA) technology (640 by 480 pixels in16 colors) in the mid-1980s and scan frequencies rose to 60 kilohertz or more for mainstream displays; 100 kilohertz or more for high-end displays. These displays were capable of displaying formats up to 2048 by 1536 pixels with high color depths. Because the human eye is very quick to respond to visual stimulation, developments in display technology have tended to track the development of semiconductor technology that allows the rapid manipulation of the stored image.
5. Computer Memory for Personal Computers
During the second half of the twentieth century, the two primary methods used for the long-term storage of digital information were magnetic and optical recording. These methods were selected primarily on the basis of cost. Compared to core or transistorized random-access memory (RAM), storage costs for magnetic and optical media were several orders of magnitude cheaper per bit of information and were not volatile; that is, the information did not vanish when electrical power was turned off. However, access to information stored on magnetic and optical recorders was much slower compared to RAM memory. As a result, computer designers used a mix of both types of memory to accomplish computational tasks. Designers of magnetic and optical storage systems have sought meanwhile to increase the speed of access to stored information to increase the overall performance of computer systems, since most digital information is stored magnetically or optically for reasons of cost.
6. Computer Modeling
Computer simulation models have transformed the natural, engineering, and social sciences, becoming crucial tools for disciplines as diverse as ecology, epidemiology, economics, urban planning, aerospace engineering, meteorology, and military operations. Computer models help researchers study systems of extreme complexity, predict the behavior of natural phenomena, and examine the effects of human interventions in natural processes. Engineers use models to design everything from jets and nuclear-waste repositories to diapers and golf clubs. Models enable astrophysicists to simulate supernovas, biochemists to replicate protein folding, geologists to predict volcanic eruptions, and physiologists to identify populations at risk of lead poisoning. Clearly, computer models provide a powerful means of solving problems, both theoretical and applied.
7. Computer Networks
Computers and computer networks have changed the way we do almost everything—the way we teach, learn, do research, access or share information, communicate with each other, and even the way we entertain ourselves. A computer network, in simple terms, consists of two or more computing devices (often called nodes) interconnected by means of some medium capable of transmitting data that allows the computers to communicate with each other in order to provide a variety of services to users.
8. Computer Science
Computer science occupies a unique position among the scientific and technical disciplines. It revolves around a specific artifact—the electronic digital computer—that touches upon a broad and diverse set of fields in its design, operation, and application. As a result, computer science represents a synthesis and extension of many different areas of mathematics, science, engineering, and business.
9. Computer-Aided Control Technology
The story of computer-aided control technology is inextricably entwined with the modern history of automation. Automation in the first half of the twentieth century involved (often analog) processes for continuous automatic measurement and control of hardware by hydraulic, mechanical, or electromechanical means. These processes facilitated the development and refinement of battlefield fire-control systems, feedback amplifiers for use in telephony, electrical grid simulators, numerically controlled milling machines, and dozens of other innovations.
10. Computer-Aided Design and Manufacture
Computer-aided design and manufacture, known by the acronym CAD/CAM, is a process for manufacturing mechanical components, wherein computers are used to link the information needed in and produced by the design process to the information needed to control the machine tools that produce the parts. However, CAD/CAM actually constitutes two separate technologies that developed along similar, but unrelated, lines until they were combined in the 1970s.
11. Computer-User Interface
A computer interface is the point of contact between a person and an electronic computer. Today’s interfaces include a keyboard, mouse, and display screen. Computer user interfaces developed through three distinct stages, which can be identified as batch processing, interactive computing, and the graphical user interface (GUI). Today’s graphical interfaces support additional multimedia features, such as streaming audio and video. In GUI design, every new software feature introduces more icons into the process of computer– user interaction. Presently, the large vocabulary of icons used in GUI design is difficult for users to remember, which creates a complexity problem. As GUIs become more complex, interface designers are adding voice recognition and intelligent agent technologies to make computer user interfaces even easier to operate.
12. Early Computer Memory
Mechanisms to store information were present in early mechanical calculating machines, going back to Charles Babbage’s analytical engine proposed in the 1830s. It introduced the concept of the ‘‘store’’ and, if ever built, would have held 1000 numbers of up to 50 decimal digits. However, the move toward base-2 or binary computing in the 1930s brought about a new paradigm in technology—the digital computer, whose most elementary component was an on–off switch. Information on a digital system is represented using a combination of on and off signals, stored as binary digits (shortened to bits): zeros and ones. Text characters, symbols, or numerical values can all be coded as bits, so that information stored in digital memory is just zeros and ones, regardless of the storage medium. The history of computer memory is closely linked to the history of computers but a distinction should be made between primary (or main) and secondary memory. Computers only need operate on one segment of data at a time, and with memory being a scarce resource, the rest of the data set could be stored in less expensive and more abundant secondary memory.
13. Early Digital Computers
Digital computers were a marked departure from the electrical and mechanical calculating and computing machines in wide use from the early twentieth century. The innovation was of information being represented using only two states (on or off), which came to be known as ‘‘digital.’’ Binary (base 2) arithmetic and logic provided the tools for these machines to perform useful functions. George Boole’s binary system of algebra allowed any mathematical equation to be represented by simply true or false logic statements. By using only two states, engineering was also greatly simplified, and universality and accuracy increased. Further developments from the early purpose-built machines, to ones that were programmable accompanied by many key technological developments, resulted in the well-known success and proliferation of the digital computer.
14. Electronic Control Technology
The advancement of electrical engineering in the twentieth century made a fundamental change in control technology. New electronic devices including vacuum tubes (valves) and transistors were used to replace electromechanical elements in conventional controllers and to develop new types of controllers. In these practices, engineers discovered basic principles of control theory that could be further applied to design electronic control systems.
15. Encryption and Code Breaking
The word cryptography comes from the Greek words for ‘‘hidden’’ (kryptos) and ‘‘to write’’ (graphein)—literally, the science of ‘‘hidden writing.’’ In the twentieth century, cryptography became fundamental to information technology (IT) security generally. Before the invention of the digital computer at mid-century, national governments across the world relied on mechanical and electromechanical cryptanalytic devices to protect their own national secrets and communications, as well as to expose enemy secrets. Code breaking played an important role in both World Wars I and II, and the successful exploits of Polish and British cryptographers and signals intelligence experts in breaking the code of the German Enigma ciphering machine (which had a range of possible transformations between a message and its code of approximately 150 trillion (or 150 million million million) are well documented.
16. Error Checking and Correction
In telecommunications, whether transmission of data or voice signals is over copper, fiber-optic, or wireless links, information coded in the signal transmitted must be decoded by the receiver from a background of noise. Signal errors can be introduced, for example from physical defects in the transmission medium (semiconductor crystal defects, dust or scratches on magnetic memory, bubbles in optical fibers), from electromagnetic interference (natural or manmade) or cosmic rays, or from cross-talk (unwanted coupling) between channels. In digital signal transmission, data is transmitted as ‘‘bits’’ (ones or zeros, corresponding to on or off in electronic circuits). Random bit errors occur singly and in no relation to each other. Burst error is a large, sustained error or loss of data, perhaps caused by transmission problems in the connecting cables, or sudden noise. Analog to digital conversion can also introduce sampling errors.
17. Global Positioning System (GPS)
The NAVSTAR (NAVigation System Timing And Ranging) Global Positioning System (GPS) provides an unlimited number of military and civilian users worldwide with continuous, highly accurate data on their position in four dimensions— latitude, longitude, altitude, and time— through all weather conditions. It includes space, control, and user segments (Figure 6). A constellation of 24 satellites in 10,900 nautical miles, nearly circular orbits—six orbital planes, equally spaced 60 degrees apart, inclined approximately 55 degrees relative to the equator, and each with four equidistant satellites—transmits microwave signals in two different L-band frequencies. From any point on earth, between five and eight satellites are ‘‘visible’’ to the user. Synchronized, extremely precise atomic clocks—rubidium and cesium— aboard the satellites render the constellation semiautonomous by alleviating the need to continuously control the satellites from the ground. The control segment consists of a master facility at Schriever Air Force Base, Colorado, and a global network of automated stations. It passively tracks the entire constellation and, via an S-band uplink, periodically sends updated orbital and clock data to each satellite to ensure that navigation signals received by users remain accurate. Finally, GPS users—on land, at sea, in the air or space—rely on commercially produced receivers to convert satellite signals into position, time, and velocity estimates.
18. Gyrocompass and Inertial Guidance
Before the twentieth century, navigation at sea employed two complementary methods, astronomical and dead reckoning. The former involved direct measurements of celestial phenomena to ascertain position, while the latter required continuous monitoring of a ship’s course, speed, and distance run. New navigational technology was required not only for iron ships in which traditional compasses required correction, but for aircraft and submarines in which magnetic compasses cannot be used. Owing to their rapid motion, aircraft presented challenges for near instantaneous navigation data collection and reduction. Electronics furnished the exploitation of radio and the adaptation of a gyroscope to direction finding through the invention of the nonmagnetic gyrocompass.
Although the Cold War arms race after World War II led to the development of inertial navigation, German manufacture of the V-2 rocket under the direction of Wernher von Braun during the war involved a proto-inertial system, a two-gimballed gyro with an integrator to determine speed. Inertial guidance combines a gyrocompass with accelerometers installed along orthogonal axes, devices that record all accelerations of the vehicle in which inertial guidance has been installed. With this system, if the initial position of the vehicle is known, then the vehicle’s position at any moment is known because integrators record all directions and accelerations and calculate speeds and distance run. Inertial guidance devices can subtract accelerations due to gravity or other motions of the vehicle. Because inertial guidance does not depend on an outside reference, it is the ultimate dead reckoning system, ideal for the nuclear submarines for which they were invented and for ballistic missiles. Their self-contained nature makes them resistant to electronic countermeasures. Inertial systems were first installed in commercial aircraft during the 1960s. The expense of manufacturing inertial guidance mechanisms (and their necessary management by computer) has limited their application largely to military and some commercial purposes. Inertial systems accumulate errors, so their use at sea (except for submarines) has been as an adjunct to other navigational methods, unlike aircraft applications. Only the development of the global positioning system (GPS) at the end of the century promised to render all previous navigational technologies obsolete. Nevertheless, a range of technologies, some dating to the beginning of the century, remain in use in a variety of commercial and leisure applications.
19. Hybrid Computers
Following the emergence of the analog–digital demarcation in the late 1940s—and the ensuing battle between a speedy analog versus the accurate digital—the term ‘‘hybrid computer’’ surfaced in the early 1960s. The assumptions held by the adherents of the digital computer—regarding the dynamic mechanization of computational labor to accompany the equally dynamic increase in computational work—was becoming a universal ideology. From this perspective, the digital computer justly appeared to be technically superior. In introducing the digital computer to social realities, however, extensive interaction with the experienced analog computer adherents proved indispensable, especially given that the digital proponents’ expectation of progress by employing the available and inexpensive hardware was stymied by the lack of inexpensive software. From this perspective—as historiographically unwanted it may be by those who agree with the essentialist conception of the analog–digital demarcation—the history of the hybrid computer suggests that the computer as we now know it was brought about by linking the analog and the digital, not by separating them. Placing the ideal analog and the ideal digital at the two poles, all computing techniques that combined some features of both fell beneath ‘‘hybrid computation’’; the designators ‘‘balanced’’ or ‘‘true’’ were preserved for those built with appreciable amounts of both. True hybrids fell into the middle spectrum that included: pure analog computers, analog computers using digital-type numerical analysis techniques, analog computers programmed with the aid of digital computers, analog computers using digital control and logic, analog computers using digital subunits, analog computers using digital computers as peripheral equipment, balanced hybrid computer systems, digital computers using analog subroutines, digital computers with analog arithmetic elements, digital computers designed to permit analog-type programming, digital computers with analog-oriented compilers and interpreters, and pure digital computers.
20. Information Theory
Information theory, also known originally as the mathematical theory of communication, was first explicitly formulated during the mid-twentieth century. Almost immediately it became a foundation; first, for the more systematic design and utilization of numerous telecommunication and information technologies; and second, for resolving a paradox in thermodynamics. Finally, information theory has contributed to new interpretations of a wide range of biological and cultural phenomena, from organic physiology and genetics to cognitive behavior, human language, economics, and political decision making. Reflecting the symbiosis between theory and practice typical of twentieth century technology, technical issues in early telegraphy and telephony gave rise to a proto-information theory developed by Harry Nyquist at Bell Labs in 1924 and Ralph Hartley, also at Bell Labs, in 1928. This theory in turn contributed to advances in telecommunications, which stimulated the development of information theory per se by Claude Shannon and Warren Weaver, in their book The Mathematical Theory of Communication published in 1949. As articulated by Claude Shannon, a Bell Labs researcher, the technical concept of information is defined by the probability of a specific message or signal being picked out from a number of possibilities and transmitted from A to B. Information in this sense is mathematically quantifiable. The amount of information, I, conveyed by signal, S, is inversely related to its probability, P. That is, the more improbable a message, the more information it contains. To facilitate the mathematical analysis of messages, the measure is conveniently defined as I ¼ log2 1/P(S), and is named a binary digit or ‘‘bit’’ for short. Thus in the simplest case of a two-state signal (1 or 0, corresponding to on or off in electronic circuits), with equal probability for each state, the transmission of either state as the code for a message would convey one bit of information. The theory of information opened up by this conceptual analysis has become the basis for constructing and analyzing digital computational devices and a whole range of information technologies (i.e., technologies including telecommunications and data processing), from telephones to computer networks.
21. Internet
The Internet is a global computer network of networks whose origins are found in U.S. military efforts. In response to Sputnik and the emerging space race, the Advanced Research Projects Agency (ARPA) was formed in 1958 as an agency of the Pentagon. The researchers at ARPA were given a generous mandate to develop innovative technologies such as communications.
In 1962, psychologist J.C.R. Licklider from the Massachusetts Institute of Technology’s Lincoln Laboratory joined ARPA to take charge of the Information Processing Techniques Office (IPTO). In 1963 Licklider wrote a memo proposing an interactive network allowing people to communicate via computer. This project did not materialize. In 1966, Bob Taylor, then head of the IPTO, noted that he needed three different computer terminals to connect to three different machines in different locations around the nation. Taylor also recognized that universities working with IPTO needed more computing resources. Instead of the government buying machines for each university, why not share machines? Taylor revitalized Licklider’s idea, securing $1 million in funding, and hired 29-yearold Larry Roberts to direct the creation of ARPAnet.
In 1974, Robert Kahn and Vincent Cerf proposed the first internet-working protocol, a way for datagrams (packets) to be communicated between disparate networks, and they called it an ‘‘internet.’’ Their efforts created transmission control protocol/internet protocol (TCP/IP). In 1982, TCP/IP replaced NCP on ARPAnet. Other networks adopted TCP/IP and it became the dominant standard for all networking by the late 1990s.
In 1981 the U.S. National Science Foundation (NSF) created Computer Science Network (CSNET) to provide universities that did not have access to ARPAnet with their own network. In 1986, the NSF sponsored the NSFNET ‘‘backbone’’ to connect five supercomputing centers. The backbone also connected ARPAnet and CSNET together, and the idea of a network of networks became firmly entrenched. The open technical architecture of the Internet allowed numerous innovations to be grafted easily onto the whole. When ARPAnet was dismantled in 1990, the Internet was thriving at universities and technology- oriented companies. The NSF backbone was dismantled in 1995 when the NSF realized that commercial entities could keep the Internet running and growing on their own, without government subsidy. Commercial network providers worked through the Commercial Internet Exchange to manage network traffic.
22. Mainframe Computers
The term ‘‘computer’’ currently refers to a general-purpose, digital, electronic, stored-program calculating machine. The term ‘‘mainframe’’ refers to a large, expensive, multiuser computer, able to handle a wide range of applications. The term was derived from the main frame or cabinet in which the central processing unit (CPU) and main memory of a computer were kept separate from those cabinets that held peripheral devices used for input and output.
Computers are generally classified as supercomputers, mainframes, minicomputers, or microcomputers. This classification is based on factors such as processing capability, cost, and applications, with supercomputers the fastest and most expensive. All computers were called mainframes until the 1960s, including the first supercomputer, the naval ordnance research calculator (NORC), offered by International Business Machines (IBM) in 1954. In 1960, Digital Equipment Corporation (DEC) shipped the PDP-1, a computer that was much smaller and cheaper than a mainframe.
Mainframes once each filled a large room, cost millions of dollars, and needed a full maintenance staff, partly in order to repair the damage caused by the heat generated by their vacuum tubes. These machines were characterized by proprietary operating systems and connections through dumb terminals that had no local processing capabilities. As personal computers developed and began to approach mainframes in speed and processing power, however, mainframes have evolved to support a client/server relationship, and to interconnect with open standard-based systems. They have become particularly useful for systems that require reliability, security, and centralized control. Their ability to process large amounts of data quickly make them particularly valuable for storage area networks (SANs). Mainframes today contain multiple CPUs, providing additional speed through multiprocessing operations. They support many hundreds of simultaneously executing programs, as well as numerous input and output processors for multiplexing devices, such as video display terminals and disk drives. Many legacy systems, large applications that have been developed, tested, and used over time, are still running on mainframes.
23. Mineral Prospecting
Twentieth century mineral prospecting draws upon the accumulated knowledge of previous exploration and mining activities, advancing technology, expanding knowledge of geologic processes and deposit models, and mining and processing capabilities to determine where and how to look for minerals of interest. Geologic models have been developed for a wide variety of deposit types; the prospector compares geologic characteristics of potential exploration areas with those of deposit models to determine which areas have similar characteristics and are suitable prospecting locations. Mineral prospecting programs are often team efforts, integrating general and site-specific knowledge of geochemistry, geology, geophysics, and remote sensing to ‘‘discover’’ hidden mineral deposits and ‘‘measure’’ their economic potential with increasing accuracy and reduced environmental disturbance. Once a likely target zone has been identified, multiple exploration tools are used in a coordinated program to characterize the deposit and its economic potential.
24. Packet Switching
Historically the first communications networks were telegraphic—the electrical telegraph replacing the mechanical semaphore stations in the mid-nineteenth century. Telegraph networks were largely eclipsed by the advent of the voice (telephone) network, which first appeared in the late nineteenth century, and provided the immediacy of voice conversation. The Public Switched Telephone Network allows a subscriber to dial a connection to another subscriber, with the connection being a series of telephone lines connected together through switches at the telephone exchanges along the route. This technique is known as circuit switching, as a circuit is set up between the subscribers, and is held until the call is cleared.
One of the disadvantages of circuit switching is the fact that the capacity of the link is often significantly underused due to silences in the conversation, but the spare capacity cannot be shared with other traffic. Another disadvantage is the time it takes to establish the connection before the conversation can begin. One could liken this to sending a railway engine from London to Edinburgh to set the points before returning to pick up the carriages. What is required is a compromise between the immediacy of conversation on an established circuit-switched connection, with the ad hoc delivery of a store-and-forward message system. This is what packet switching is designed to provide.
25. Personal Computers
A personal computer, or PC, is designed for personal use. Its central processing unit (CPU) runs single-user systems and application software, processes input from the user, sending output to a variety of peripheral devices. Programs and data are stored in memory and attached storage devices. Personal computers are generally single-user desktop machines, but the term has been applied to any computer that ‘‘stands alone’’ for a single user, including portable computers.
The technology that enabled the construction of personal computers was the microprocessor, a programmable integrated circuit (or ‘‘chip’’) that acts as the CPU. Intel introduced the first microprocessor in 1971, the 4-bit 4004, which it called a ‘‘microprogrammable computer on a chip.’’ The 4004 was originally developed as a general-purpose chip for a programmable calculator, but Intel introduced it as part of Intel’s Microcomputer System 4-bit, or MCS-4, which also included read-only memory (ROM) and random-access memory (RAM) memory chips and a shift register chip. In August 1972, Intel followed with the 8-bit 8008, then the more powerful 8080 in June 1974. Following Intel’s lead, computers based on the 8080 were usually called microcomputers.
The success of the minicomputer during the 1960s prepared computer engineers and users for ‘‘single person, single CPU’’ computers. Digital Equipment Corporation’s (DEC) widely used PDP-10, for example, was smaller, cheaper, and more accessible than large mainframe computers. Timeshared computers operating under operating systems such as TOPS-10 on the PDP-10— co-developed by the Massachusetts Institute of Technology (MIT) and DEC in 1972—created the illusion of individual control of computing power by providing rapid access to personal programs and files. By the early 1970s, the accessibility of minicomputers, advances in microelectronics, and component miniaturization created expectations of affordable personal computers.
26. Printers
Printers generally can be categorized as either impact or nonimpact. Like typewriters, impact printers generate output by striking the page with a solid substance. Impact printers include daisy wheel and dot matrix printers. The daisy wheel printer, which was introduced in 1972 by Diablo Systems, operates by spinning the daisy wheel to the correct character whereupon a hammer strikes it, forcing the character through an inked ribbon and onto the paper. Dot matrix printers operate by using a series of small pins to strike a matrix or grid ribbon coated with ink. The strike of the pin forces the ink to transfer to the paper at the point of impact. Unlike daisy wheel printers, dot matrix printers can generate italic and other character types through producing different pin patterns. Nonimpact printers generate images by spraying or fusing ink to paper or other output media. This category includes inkjet printers, laser printers, and thermal printers. Whether they are inkjet or laser, impact or nonimpact, all modern printers incorporate features of dot matrix technology in their design: they operate by generating dots onto paper or other physical media.
27. Processors for Computers
A processor is the part of the computer system that manipulates the data. The first computer processors of the late 1940s and early 1950s performed three main functions and had three main components. They worked in a cycle to gather, decode, and execute instructions. They were made up of the arithmetic and logic unit, the control unit, and some extra storage components or registers. Today, most processors contain these components and perform these same functions, but since the 1960s they have developed different forms, capabilities, and organization. As with computers in general, increasing speed and decreasing size has marked their development.
28. Radionavigation
Astronomical and dead-reckoning techniques furnished the methods of navigating ships until the twentieth century, when exploitation of radio waves, coupled with electronics, met the needs of aircraft with their fast speeds, but also transformed all navigational techniques. The application of radio to dead reckoning has allowed vessels to determine their positions in all-weather by direction finding (known as radio direction finding, or RDF) or by hyperbolic systems. Another use of radio, radar (radio direction and rangefinding), enables vessels to determine their distance to, or their bearing from, objects of known position. Radionavigation complements traditional navigational methods by employing three frames of reference. First, radio enables a vessel to navigate by lines of bearing to shore transmitters (the most common use of radio). This is directly analogous to the use of lighthouses for bearings. Second, shore stations may take radio bearings of craft and relay to them computed positions. Third, radio beacons provide aircraft or ships with signals that function as true compasses.
29. Software Application Programs
At the beginning of the computer age around the late 1940s, inventors of the intelligent machine were not thinking about applications software, or any software other than that needed to run the bare machine to do mathematical calculating. It was only when Maurice Wilkes’ young protégé David Williams crafted a tidy set of initial orders for the EDSAC, an early programmable digital computer, that users could string together standard subroutines to a program and have the execution jump between them. This was the beginning of software as we know it—something that runs on a machine other than an operating system to make it do anything desired. ‘‘Applications’’ are software other than system programs that run the actual hardware. Manufacturers always had this software, and as the 1950s progressed they would ‘‘bundle’’ applications with hardware to make expensive computers more attractive. Some programming departments were even placed in the marketing departments.
30. Software Engineering
Software engineering aims to develop the programs that allow digital computers to do useful work in a systematic, disciplined manner that produces high-quality software on time and on budget. As computers have spread throughout industrialized societies, software has become a multibillion dollar industry. Both the users and developers of software depend a great deal on the effectiveness of the development process.
Software is a concept that didn’t even pertain to the first electronic digital computers. They were ‘‘programmed’’ through switches and patch cables that physically altered the electrical pathways of the machine. It was not until the Manchester Mark I, the first operational stored-program electronic digital computer, was developed in 1948 at the University of Manchester in England that configuring the machine to solve a specific problem became a matter of software rather than hardware. Subsequently, instructions were stored in memory along with data.
31. Supercomputers
Supercomputers are high-performance computing devices that are generally used for numerical calculation, for the study of physical systems either through numerical simulation or the processing of scientific data. Initially, they were large, expensive, mainframe computers, which were usually owned by government research labs. By the end of the twentieth century, they were more often networks of inexpensive small computers. The common element of all of these machines was their ability to perform high-speed floating-point arithmetic— binary arithmetic that approximates decimal numbers with a fixed number of bits—the basis of numerical computation.
With the advent of inexpensive supercomputers, these machines moved beyond the large government labs and into smaller research and engineering facilities. Some were used for the study of social science. A few were employed by business concerns, such as stock brokerages or graphic designers.
32. Systems Programs
The operating systems used in all computers today are a result of the development and organization of early systems programs designed to control and regulate the operations of computer hardware. The early computing machines such as the ENIAC of 1945 were ‘‘programmed’’ manually with connecting cables and setting switches for each new calculation. With the advent of the stored program computer of the late 1940s (the Manchester Mark I, EDVAC, EDSAC (electronic delay storage automatic calculator), the first system programs such as assemblers and compilers were developed and installed. These programs performed oft repeated and basic operations for computer use including converting programs into machine code, storing and retrieving files, managing computer resources and peripherals, and aiding in the compilation of new programs. With the advent of programming languages, and the dissemination of more computers in research centers, universities, and businesses during the late 1950s and 1960s, a large group of users began developing programs, improving usability, and organizing system programs into operating systems.
The 1970s and 1980s saw a turn away from some of the complications of system software, an interweaving of features from different operating systems, and the development of systems programs for the personal computer. In the early 1970s, two programmers from Bell Laboratories, Ken Thompson and Dennis Ritchie, developed a smaller, simpler operating system called UNIX. Unlike past system software, UNIX was portable and could be run on different computer systems. Due in part to low licensing fees and simplicity of design, UNIX increased in popularity throughout the 1970s. At the Xerox Palo Alto Research Center, research during the 1970s led to the development of system software for the Apple Macintosh computer that included a GUI (graphical user interface). This type of system software filtered the user’s interaction with the computer through the use of graphics or icons representing computer processes. In 1985, a year after the release of the Apple Macintosh computer, a GUI was overlaid on Microsoft’s then dominant operating system, MS-DOS, to produce Microsoft Windows. The Microsoft Windows series of operating systems became and remains the dominant operating system on personal computers.
33. World Wide Web
The World Wide Web (Web) is a ‘‘finite but unbounded’’ collection of media-rich digital resources that are connected through high-speed digital networks. It relies upon an Internet protocol suite that supports cross-platform transmission and makes available a wide variety of media types (i.e., multimedia). The cross-platform delivery environment represents an important departure from more traditional network communications protocols such as e-mail, telnet, and file transfer protocols (FTP) because it is content-centric. It is also to be distinguished from earlier document acquisition systems such as Gopher, which was designed in 1991, originally as a mainframe program but quickly implemented over networks, and wide area information systems (WAIS), also released in 1991. WAIS accommodated a narrower range of media formats and failed to include hyperlinks within their navigation protocols. Following the success of Gopher on the Internet, the Web quickly extended and enriched the metaphor of integrated browsing and navigation. This made it possible to navigate and peruse a wide variety of media types effortlessly on the Web, which in turn led to the Web’s hegemony as an Internet protocol.
History of Computer Technology

The modern computer—the (electronic) digital computer in which the stored program concept is realized and hence self-modifying programs are possible—was only invented in the 1940s. Nevertheless, the history of computing (interpreted as the usage of modern computers) is only understandable against the background of the many forms of information processing as well as mechanical computing devices that solved mathematical problems in the first half of the twentieth century. The part these several predecessors played in the invention and early history of the computer may be interpreted from two different perspectives: on the one hand it can be argued that these machines prepared the way for the modern digital computer, on the other hand it can be argued that the computer, which was invented as a mathematical instrument, was reconstructed to be a data-processing machine, a control mechanism, and a communication tool.
The invention and early history of the digital computer has its roots in two different kinds of developments: first, information processing in business and government bureaucracies; and second, the use and the search for mathematical instruments and methods that could solve mathematical problems arising in the sciences and in engineering.
Origins in Mechanical Office Equipment
The development of information processing in business and government bureaucracies had its origins in the late nineteenth century, which was not just an era of industrialization and mass production but also a time of continuous growth in administrative work. The economic precondition for this development was the creation of a global economy, which caused growth in production of goods and trade. This brought with it an immense increase in correspondence, as well as monitoring and accounting activities—corporate bureaucracies began to collect and process data in increasing quantities. Almost at the same time, government organizations became more and more interested in collating data on population and demographic changes (e.g., expanding tax revenues, social security, and wide-ranging planning and monitoring functions) and analyzing this data statistically.
Bureaucracies in the U.S. and in Europe reacted in a different way to these changes. While in Europe for the most part neither office machines nor telephones entered offices until 1900, in the U.S. in the last quarter of the nineteenth century the information-handling techniques in bureaucracies were radically changed because of the introduction of mechanical devices for writing, copying, and counting data. The rise of big business in the U.S. had caused a growing demand for management control tools, which was fulfilled by a new ideology of systematic management together with the products of the rising office machines industry. Because of a later start in industrialization, the government and businesses in the U.S. were not forced to reorganize their bureaucracies when they introduced office machines. This, together with an ideological preference for modern office equipment, was the cause of a market for office machines and of a far-reaching mechanization of office work in the U.S. In the 1880s typewriters and cash registers became very widespread, followed by adding machines and book-keeping machines in the 1890s. From 1880 onward, the makers of office machines in the U.S. underwent a period of enormous growth, and in 1920 the office machine industry annually generated about $200 million in revenue. In Europe, by comparison, mechanization of office work emerged about two decades later than in the U.S.—both Germany and Britain adopted the American system of office organization and extensive use of office machines for the most part no earlier than the 1920s.
During the same period the rise of a new office machine technology began. Punched card systems, initially invented by Herman Hollerith to analyze the U.S. census in 1890, were introduced. By 1911 Hollerith’s company had only about 100 customers, but after it had been merged in the same year with two other companies to become the Computing- Tabulating-Recording Company (CTR), it began a tremendous ascent to become the world leader in the office machine industry. CTR’s general manager, Thomas J. Watson, understood the extraordinary potential of these punched-card accounting devices, which enabled their users to process enormous amounts of data largely automatically, in a rapid way and at an adequate level of cost and effort. Due to Watson’s insights and his extraordinary management abilities, the company (which had since been renamed to International Business Machines (IBM)) became the fourth largest office machine supplier in the world by 1928—topped only by Remington Rand, National Cash Register (NCR), and the Burroughs Adding Machine Company.
Origin of Calculating Devices and Analog Instruments
Compared with the fundamental changes in the world of corporate and government bureaucracies caused by office machinery during the late nineteenth and early twentieth century, calculating machines and instruments seemed to have only a minor influence in the world of science and engineering. Scientists and engineers had always been confronted with mathematical problems and had over the centuries developed techniques such as mathematical tables. However, many new mathematical instruments emerged in the nineteenth century and increasingly began to change the world of science and engineering. Apart from the slide rule, which came into popular use in Europe from the early nineteenth century onwards (and became the symbol of the engineer for decades), calculating machines and instruments were only produced on a large scale in the middle of the nineteenth century.
In the 1850s the production of calculating machines as well as that of planimeters (used to measure the area of closed curves, a typical problem in land surveying) started on different scales. Worldwide, less than 2,000 calculating machines were produced before 1880, but more than 10,000 planimeters were produced by the early 1880s. Also, various types of specialized mathematical analog instruments were produced on a very small scale in the late nineteenth century; among them were integraphs for the graphical solution of special types of differential equations, harmonic analyzers for the determination of Fourier coefficients of a periodic function, and tide predictors that could calculate the time and height of the ebb and flood tides.
Nonetheless, in 1900 only geodesists and astronomers (as well as part of the engineering community) made extensive use of mathematical instruments. In addition, the establishment of applied mathematics as a new discipline took place at German universities on a small scale and the use of apparatus and machines as well as graphical and numerical methods began to flourish during this time. After World War I, the development of engineering sciences and of technical physics gave a tremendous boost to applied mathematics in Germany and Britain. In general, scientists and engineers became more aware of the capabilities of calculating machines and a change of the calculating culture—from the use of tables to the use of calculating machines—took place.
One particular problem that was increasingly encountered by mechanical and electrical engineers in the 1920s was the solution of several types of differential equations, which were not solvable by analytic solutions. As one important result of this development, a new type of analog instrument— the so called ‘‘differential analyzer’’—was invented in 1931 by the engineer Vannevar Bush at the Massachusetts Institute of Technology (MIT). In contrast to its predecessors—several types of integraphs—this machine (which was later called an analog computer) could be used not only to solve a special class of differential equation, but a more general class of differential equations associated with engineering problems. Before the digital computer was invented in the 1940s there was an intensive use of analog instruments (similar to Bush’s differential analyzer) and a number of machines were constructed in the U.S. and in Europe after the model of Bush’s machine before and during World War II. Analog instruments also became increasingly important in several fields such as the firing control of artillery on warships or the control of rockets. It is worth mentioning here that only for a limited class of scientific and engineering problems was it possible to construct an analog computer— weather forecasting and the problem of shock waves produced by an atomic bomb, for example, required the solution of partial differential equations, for which a digital computer was needed.
The Invention of the Computer
The invention of the electronic digital stored-program computer is directly connected with the development of numerical calculation tools for the solution of mathematical problems in the sciences and in engineering. The ideas that led to the invention of the computer were developed simultaneously by scientists and engineers in Germany, Britain, and the U.S. in the 1930s and 1940s. The first freely programmable program-controlled automatic calculator was developed by the civil engineering student Konrad Zuse in Germany. Zuse started development work on program-controlled computing machines in the 1930s, when he had to deal with extensive calculations in static, and in 1941 his Z3, which was based on electromechanical relay technology, became operational.
Several similar developments in the U.S. were in progress at the same time. In 1937 Howard Aiken, a physics student at Harvard University, approached IBM to build a program-controlled calculator— later called the ‘‘Harvard Mark I.’’ On the basis of a concept Aiken had developed because of his experiences with the numerical solution of partial differential equations, the machine was built and became operational in 1944. At almost the same time a series of important relay computers was built at the Bell Laboratories in New York following a suggestion by George R. Stibitz. All these developments in the U.S. were spurred by the outbreak of World War II. The first large-scale programmable electronic computer called the Colossus was built in complete secrecy in 1943 to 1944 at Bletchley Park in Britain in order to help break the German Enigma machine ciphers.
However, it was neither these relay calculators nor the Colossus that were decisive for the development of the universal computer, but the ENIAC (electronic numerical integrator and computer), which was developed at the Moore School of Engineering at the University of Pennsylvania. Extensive ballistic calculations were carried out there for the U.S. Army during World War II with the aid of the Bush ‘‘differential analyzer’’ and more than a hundred women (‘‘computors’’) working on mechanical desk calculators. Observing that capacity was barely sufficient to compute the artillery firing tables, the physicist John W. Mauchly and the electronic engineer John Presper Eckert started developing the ENIAC, a digital version of the differential analyzer, in 1943 with funding from the U.S. Army.
In 1944 the mathematician John von Neumann turned his attention to the ENIAC because of his mathematical work on the Manhattan Project (on the implosion of the hydrogen bomb). While the ENIAC was being built, Neumann and the ENIAC team drew up plans for a successor to the ENIAC in order to improve the shortcomings of the ENIAC concept, such as the very small memory and the time-consuming reprogramming (actually rewiring) required to change the setup for a new calculation. In these meetings the idea of a stored-program, universal machine evolved. Memory was to be used to store the program in addition to data. This would enable the machine to execute conditional branches and change the flow of the program. The concept of a computer in the modern sense of the word was born and in 1945 von Neumann wrote the important ‘‘First Draft of a Report on the EDVAC,’’ which described the stored-program, universal computer. The logical structure that was presented in this draft report is now referred to as the ‘‘von Neumann architecture.’’ This EDVAC report was originally intended for internal use but once made freely available it became the ‘‘bible’’ for computer pioneers throughout the world in the 1940s and 1950s. The first computer featuring the von Neumann architecture operated at Cambridge University in the U.K.; in June 1949 the EDSAC (electronic delay storage automatic computer) computer built by Maurice Wilkes—designed according to the EDVAC principles—became operational.
The Computer as a Scientific Instrument
As soon as the computer was invented, a growing demand for computers by scientists and engineers evolved, and numerous American and European universities started their own computer projects in the 1940s and 1950s. After the technical difficulties of building an electronic computer were solved, scientists grasped the opportunity to use the new scientific instrument for their research. For example, at the University of Gottingen in Germany, the early computers were used for the initial value problems of partial differential equations associated with hydrodynamic problems from atomic physics and aerodynamics. Another striking example was the application of von Neumann’s computer at the Institute for Advanced Study (IAS) in Princeton to numerical weather forecasts in 1950. As a result, numerical weather forecasts could be made on a regular basis from the mid-1950s onwards.
Mathematical methods have always been of a certain importance for science and engineering sciences, but only the use of the electronic digital computer (as an enabling technology) made it possible to broaden the application of mathematical methods to such a degree that research in science, medicine, and engineering without computer- based mathematical methods has become virtually inconceivable at the end of the twentieth century. A number of additional computer-based techniques, such as scientific visualization, medical imaging, computerized tomography, pattern recognition, image processing, and statistical applications, have become of the utmost significance for science, medicine, engineering, and social sciences. In addition, the computer changed the way engineers construct technical artifacts fundamentally because of the use of computer-based methods such as computer-aided design (CAD), computer-aided manufacture (CAM), computer-aided engineering, control applications, and finite-element methods. However, the most striking example seems to be the development of scientific computing and computer modeling, which became accepted as a third mode of scientific research that complements experimentation and theoretical analysis. Scientific computing and computer modeling are based on supercomputers as the enabling technology, which became important tools for modern science routinely used to simulate physical and chemical phenomena. These high-speed computers became equated with the machines developed by Seymour Cray, who built the fastest computers in the world for many years. The supercomputers he launched such as the legendary CRAY I from 1976 were the basis for computer modeling of real world systems, and helped, for example, the defense industry in the U.S. to build weapons systems and the oil industry to create geological models that show potential oil deposits.
Growth of Digital Computers in Business and Information Processing
When the digital computer was invented as a mathematical instrument in the 1940s, it could not have been foreseen that this new artifact would ever be of a certain importance in the business world. About 50 firms entered the computer business worldwide in the late 1940s and the early 1950s, and the computer was reconstructed to be a type of electronic data-processing machine that took the place of punched-card technology as well as other office machine technology. It is interesting to consider that there were mainly three types of companies building computers in the 1950s and 1960s: newly created computer firms (such as the company founded by the ENIAC inventors Eckert and Mauchly), electronics and control equipments firms (such as RCA and General Electric), and office appliance companies (such as Burroughs and NCR). Despite the fact that the first digital computers were put on the market by a German and a British company, U.S. firms dominated the world market from the 1950s onward, as these firms had the biggest market as well as financial support from the government.
Generally speaking, the Cold War exerted an enormous influence on the development of computer technology. Until the early 1960s the U.S. military and the defense industry were the central drivers of the digital computer expansion, serving as the main market for computer technology and shaping and speeding up the formation of the rising computer industry. Because of the U.S. military’s role as the ‘‘tester’’ for prototype hard- and software, it had a direct and lasting influence on technological developments; in addition, it has to be noted that the spread of computer technology was partly hindered by military secrecy. Even after the emergence of a large civilian computer market in the 1960s, the U.S. military maintained its influence by investing a great deal in computer in hard- and software and in computer research projects.
From the middle of the 1950s onwards the world computer market was dominated by IBM, which accounted for more than 70 percent of the computer industry revenues until the mid-1970s. The reasons for IBM’s overwhelming success were diverse, but the company had a unique combination of technical and organizational capabilities at its disposal that prepared it perfectly for the mainframe computer market. In addition, IBM benefited from enormous government contracts, which helped to develop excellence in computer technology and design. However, the greatest advantage of IBM was by no doubt its marketing organization and its reputation as a service-oriented firm, which was used to working closely with customers to adapt machinery to address specific problems, and this key difference between IBM and its competitors persisted right into the computer age.
During the late 1950s and early 1960s, the computer market—consisting of IBM and seven other companies called the ‘‘seven dwarves’’—was dominated by IBM, with its 650 and 1401 computers. By 1960 the market for computers was still small. Only about 7,000 computers had been delivered by the computer industry, and at this time even IBM was primarily a punched-card machine supplier, which was still the major source of its income. Only in 1960 did a boom in demand for computers start, and by 1970 the number of computers installed worldwide had increased to more than 100,000. The computer industry was on the track to become one of the world’s major industries, and was totally dominated by IBM.
The outstanding computer system of this period was IBM’s System/360. It was announced in 1964 as a compatible family of the same computer architecture, and employed interchangeable peripheral devices in order to solve IBM’s problems with a hotchpotch of incompatible product lines (which had evoked large problems in the development and maintenance of a great deal of different hardware and software products). Despite the fact that neither the technology used nor the systems programming were of a high-tech technology at the time, the System/360 established a new standard for mainframe computers for decades. Various computer firms in the U.S., Europe, Japan and even Russia, concentrated on copying components, peripherals for System/360 or tried to build System/360-compatible computers.
The growth of the computer market during the 1960s was accompanied by market shakeouts: two of the ‘‘seven dwarves’’ left the computer business after the first computer recession in the early 1970s, and afterwards the computer market was controlled by IBM and BUNCH (Burroughs, UNIVAC, NCR, Control Data, and Honeywell). At the same time, an internationalization of the computer market took place—U.S. companies controlled the world market for computers— which caused considerable fears over loss of national independence in European and Japanese national governments, and these subsequently stirred up national computing programs. While the European attempts to create national champions as well as the more general attempt to create a European-wide market for mainframe computers failed in the end, Japan’s attempt to found a national computer industry has been successful: Until today Japan is the only nation able to compete with the U.S. in a wide array of high-tech computer-related products.
Real-Time and Time-Sharing
Until the 1960s almost all computers in government and business were running batch-processing applications (i.e., the computers were only used in the same way as the punched-card accounting machines they had replaced). In the early 1950s, however, the computer industry introduced a new mode of computing named ‘‘real-time’’ in the business sector for the first time, which was originally developed for military purposes in MIT’s Whirlwind project. This project was initially started in World War II with the aim of designing an aircraft simulator by analog methods, and later became a part of a research and development program for the gigantic, computerized anti-aircraft defense system SAGE (semi-automatic ground environment) built up by IBM in the 1950s.
The demand for this new mode of computing was created by cultural and structural changes in economy. The increasing number of financial transactions in banks and insurance companies as well as increasing airline traveling activities made necessary new computer-based information systems that led finally to new forms of business evolution through information technology.
The case of the first computerized airline reservation system SABRE, developed for American Airlines by IBM in the 1950s and finally implemented in the early 1960s, serves to thoroughly illustrate these structural and structural changes in economy. Until the early 1950s, airline reservations had been made manually without any problems, but by 1953 this system was in crisis because increased air traffic and growing flight plan complexity had made reservation costs insupportable. SABRE became a complete success, demonstrating the potential of centralized real-time computing systems connected via a network. The system enabled flight agents throughout the U.S., who were equipped with desktop terminals, to gain a direct, real-time access to the central reservation system based on central IBM mainframe computers, while the airline was able to assign appropriate resources in response. Therefore, an effective combination of advantages was offered by SABRE—a better utilization of resources and a much higher customer convenience.
Very soon this new mode of computing spread around the business and government world and became commonplace throughout the service and distribution sectors of the economy; for example, bank tellers and insurance account representatives increasingly worked at terminals. On the one hand structural information problems led managers to go this way, and on the other hand the increasing use of computers as information handling machines in government and business had brought about the idea of computer-based accessible data retrieval. In the end, more and more IBM customers wanted to link dozens of operators directly to central computers by using terminal keyboards and display screens.
In the late 1950s and early 1960s—at the same time that IBM and American Airlines had begun the development of the SABRE airline reservation system—a group of brilliant computer scientists had a new idea for computer usage named ‘‘time sharing.’’ Instead of dedicating a multi-terminal system solely to a single application, they had the computer utility vision of organizing a mainframe computer so that several users could interact with it simultaneously. This vision was to change the nature of computing profoundly, because computing was no longer provided to naive users by programmers and systems analysts, and by the late 1960s time-sharing computers became widespread in the U.S.
Particularly important for this development had been the work of J.C.R. Licklider of the Advanced Research Project Agency (ARPA) of the U.S. Department of Defense. In 1960 Licklider had published a now-classic paper ‘‘Man–Computer Symbiosis’’ proposing the use of computers to augment human intellect and creating the vision of interactive computing. Licklider was very successful in translating his idea of a network allowing people on different computers to communicate into action, and convinced ARPA to start an enormous research program in 1962. Its budget surpassed that of all other sources of U.S. public research funding for computers combined. The ARPA research programs resulted in a series of fundamental moves forward in computer technology in areas such as computer graphics, artificial intelligence, and operating systems. For example, even the most influential current operating system, the general-purpose time-sharing system Unix, developed in the early 1970s at the Bell Laboratories, was a spin-off of an ambitious operating system project, Multics, funded by ARPA. The designers of Unix successfully attempted to keep away from complexity by using a clear, minimalist design approach to software design, and created a multitasking, multiuser operating system, which became the standard operating system in the 1980s.
Electronic Component Revolution
While the nature of business computing was changed by the new paradigms such as real time and time sharing, advances in solid-state components increasingly became a driving force for fundamental changes in the computer industry, and led to a dynamic interplay between new computer designs and new programming techniques that resulted in a remarkable series of technical developments. The technical progress of the mainframe computer had always run parallel to conversions in the electronics components. During the period from 1945 to 1965, two fundamental transformations in the electronics industry took place that were marked by the invention of the transistor in 1947 and the integrated circuit in 1957 to 1958. While the first generation of computers—lasting until about 1960—was characterized by vacuum tubes (valves) for switching elements, the second generation used the much smaller and more reliable transistors, which could be produced at a lower price. A new phase was inaugurated when an entire integrated circuit on a chip of silicon was produced in 1961, and when the first integrated circuits were produced for the military in 1962. A remarkable pace of progress in semiconductor innovations, known as the ‘‘revolution in miniature,’’ began to speed up the computer industry. The third generation of computers characterized by the use of integrated circuits began with the announcement of the IBM System/360 in 1964 (although this computer system did not use true integrated circuits). The most important effect of the introduction of integrated circuits was not to strengthen the leading mainframe computer systems, but to destroy Grosch’s Law, which stated that computing power increases as the square of its costs. In fact, the cost of computer power dramatically reduced during the next ten years.
This became clear with the introduction of the first computer to use integrated circuits on a full scale in 1965: the Digital Equipment Corporation (DEC) offered its PDP-8 computer for just $18,000, creating a new class of computers called minicomputers—small in size and low in cost—as well as opening up the market to new customers. Minicomputers were mainly used in areas other than general-purpose computing such as industrial applications and interactive graphics systems. The PDP-8 became the first widely successful minicomputer with over 50,000 items sold, demonstrating that there was a market for smaller computers. This success of DEC (by 1970 it had become the world’s third largest computer manufacturer) was supported by dramatic advances in solid-state technology. During the 1960s the number of transistors on a chip doubled every two years, and as a result minicomputers became continuously more powerful and more inexpensive at an inconceivable speed.
Personal Computing
The most striking aspect of the consequences of the exponential increase of the number of transistors on a chip during the 1960s—as stated by ‘‘Moore’s Law’’: the number of transistors on a chip doubled every two years—was not the lowering of the costs of mainframe computer and minicomputer processing and storage, but the introduction of the first consumer products based on chip technology such as hand-held calculators and digital watches in about 1970. More specifically, the market acts in these industries were changed overnight by the shift from mechanical to chip technology, which led to an enormous deterioration in prices as well as a dramatic industry shakeout. These episodes only marked the beginning of wide-ranging changes in economy and society during the last quarter of the twentieth century leading to a new situation where chips played an essential role in almost every part of business and modern life.
The case of the invention of the personal computer serves to illustrate that it was not sufficient to develop the microprocessor as the enabling technology in order to create a new invention, but how much new technologies can be socially constructed by cultural factors and commercial interests. When the microprocessor, a single-chip integrated circuit implementation of a CPU, was launched by the semiconductor company Intel in 1971, there was no hindrance to producing a reasonably priced microcomputer, but it took six years until the consumer product PC emerged. None of the traditional mainframe and minicomputer companies were involved in creating the early personal computer. Instead, a group of computer hobbyists as well as the ‘‘computer liberation’’ movement in the U.S. became the driving force behind the invention of the PC. These two groups were desperately keen on a low-priced type of minicomputer for use at home for leisure activities such as computer games; or rather they had the counterculture vision of an unreservedly available and personal access to an inexpensive computer utility provided with rich information. When in 1975 the Altair 8800, an Intel 8080 microprocessor-based computer, was offered as an electronic hobbyist kit for less than $400, these two groups began to realize their vision of a ‘‘personal computer.’’ Very soon dozens of computer clubs and computer magazines were founded around the U.S., and these computer enthusiasts created the personal computer by combining the Altair with keyboards, disk drives, and monitors as well as by developing standard software for it. Consequently, in only two years, a more or less useless hobbyist kit had been changed into a computer that could easily be transformed in a consumer product.
The computer hobbyist period ended in 1977, when the first standard machines for an emerging consumer product mass market were sold. These included products such as the Commodore Pet and the Apple II, which included its own monitor, disk drive, and keyboard, and was provided with several basic software packages. Over next three years, spreadsheet, word processing, and database software were developed, and an immense market for games software evolved. As a result, personal computers became more and more a consumer product for ordinary people, and Apple’s revenues shot to more than $500 million in 1982. By 1980, the personal computer had transformed into a business machine, and IBM decided to develop its own personal computer, which was introduced as the IBM PC in 1981. It became an overwhelming success and set a new industry standard.
Apple tried to compete by launching their new Macintosh computer in 1984 provided with a revolutionary graphical user interface (GUI), which set a new standard for a user-friendly human–computer interaction. It was based on technology created by computer scientists at the Xerox Palo Alto Research Center in California, who had picked up on ideas about human– computer interaction developed at the Stanford Research Institute and at the University of Utah. Despite the fact that the Macintosh’s GUI was far superior to the MS-DOS operating system of the IBM-compatible PCs, Apple failed to win the business market and remained a niche player with a market share of about 10 percent. The PC main branch was determined by the companies IBM had chosen as its original suppliers in 1981 for the design of the microprocessor (Intel) and the operating system (Microsoft). While IBM failed to seize power in the operating system software market for PCs in a software war with Microsoft, Microsoft achieved dominance not only of the key market for PC operating systems, but also the key market of office applications during the first half of the 1990s.
In the early 1990s computing again underwent further fundamental changes with the appearance of the Internet, and for the most computer users, networking became an integral part of what it means to have a computer. Furthermore, the rise of the Internet indicated the impending arrival of a new ‘‘information infrastructure’’ as well as of a ‘‘digital convergence,’’ as the coupling of computers and communications networks was often called.
In addition, the 1990s were a period of an information technology boom, which was mainly based on the Internet hype. For many years previously, it seemed to a great deal of managers and journalists that the Internet would become not just an indispensable business tool, but also a miracle cure for economic growth and prosperity. In addition, computer scientists and sociologists started a discussion predicting the beginning of a new ‘‘information age’’ based on the Internet as a ‘‘technological revolution’’ and reshaping the ‘‘material basis’’ of industrial societies.
The Internet was the outcome of an unusual collaboration of a military–industrial–academic complex that promoted the development of this extraordinary innovation. It grew out of a military network called the ARPAnet, a project established and funded by ARPA in the 1960s. The ARPAnet was initially devoted to support of data communications for defense research projects and was only used by a small number of researchers in the 1970s. Its further development was primarily promoted by unintentional forms of network usage. The users of the ARPAnet became very much attracted by the opportunity for communicating through electronic mail, which rapidly surpassed all other forms of network activities. Another unplanned spin-off of the ARPAnet was the Usenet (Unix User Network), which started in 1979 as a link between two universities and enabled its users to subscribe to newsgroups. Electronic mail became a driving force for the creation of a large number of new proprietary networks funded by the existing computer services industry or by organizations such as the NSF (NSFnet). Because networks users’ desire for email to be able to cross network boundaries, an ARPA project on ‘‘internetworking’’ became the origin for the ‘‘Internet’’—a network of networks linked by several layers of protocols such as TCP/IP (transmission control protocol/internet protocol), which quickly developed into the actual standard.
Only after the government funding had solved many of the most essential technical issues and had shaped a number of the most characteristic features of the Internet, did private sector entrepreneurs start Internet-related ventures and quickly developed user-oriented enhancements. Nevertheless, the Internet did not make a promising start and it took more than ten years before significant numbers of networks were connected. In 1980, the Internet had less than two hundred hosts, and during the next four years the number of hosts went up only to 1000. Only when the Internet reached the educational and business community of PC users in the late 1980s, did it start to become an important economic and social phenomenon. The number of hosts began an explosive growth in the late 1980s—by 1988 there were over 50,000 hosts. An important and unforeseen side effect of this development became the creation of the Internet into a new electronic publishing medium. The electronic publishing development that excited most interest in the Internet was the World Wide Web, originally developed at the CERN High Energy Physics Laboratory in Geneva in 1989. Soon there were millions of documents on the Internet, and private PC users became excited by the joys of surfing the Internet. A number of firms such as AOL soon provided low-cost network access and a range of consumer-oriented information services. The Internet boom was also helped by the Clinton–Gore presidential election campaign on the ‘‘information superhighway’’ and by the amazing news reporting on the national information infrastructure in the early 1990s. Nevertheless, for many observers it was astounding how fast the number of hosts on the Internet increased during the next few years—from more than 1 million in 1992 to 72 million in 1999.
The overwhelming success of the PC and of the Internet tends to hide the fact that its arrival marked only a branching in computer history and not a sequence. (Take, for example, the case of mainframe computers, which still continue to run, being of great importance to government facilities and the private sector (such as banks and insurance companies), or the case of supercomputers, being of the utmost significance for modern science and engineering.) Furthermore, it should be noted that only a small part of the computer applications performed today is easily observable—98 percent of programmable CPUs are used in embedded systems such as automobiles, medical devices, washing machines and mobile telephones.
Browse other Technology Research Paper Topics .
ORDER HIGH QUALITY CUSTOM PAPER

412 Computers Topics & Essay Examples
🏆 best computers topic ideas & essay examples, 👍 good essay topics about computers, 💡 easy computer science essay topics, 🥇 computer science argumentative essay topics, 🎓 good research topics about computers, 🔍 interesting computer topics to write about, ❓ computer essay questions.
Looking for interesting topics about computer science? Look no further! Check out this list of trending computer science essay topics for your studies. Whether you’re a high school, college, or postgraduate student, you will find a suitable title for computer essay in this list.
- Life Without Computers Essay One of the major contributions of the computer technology in the world has been the enhancement of the quality of communication.
- How Computers Affect Our Lives In the entertainment industry, many of the movies and even songs will not be in use without computers because most of the graphics used and the animations we see are only possible with the help […]
- Computer Use in Schools: Effects on the Education Field The learning efficiency of the student is significantly increased by the use of computers since the student is able to make use of the learning model most suited to him/her.
- Advantages and Disadvantages of Computer Graphics Essay One is able to put all of his/her ideas in a model, carry out tests on the model using graphical applications, and then make possible changes.
- The Causes and Effect of the Computer Revolution Starting the discussion with the positive effect of the issue, it should be stated that the implementation of the computer technologies in the modern world has lead to the fact that most of the processes […]
- Are We Too Dependent on Computers? The duration taken to restore the machine varies depending on the cause of the breakdown, expertise of the repairing engineer and the resources needed to restore the machine.
- Apex Computers: Problems of Motivation Among Subordinates In the process of using intangible incentives, it is necessary to use, first of all, recognition of the merits of employees.
- Are We Too Dependent on Computers? To reinforce this assertion, this paper shall consider the various arguments put forward in support of the view that computers are not overused. This demonstrates that in the education field, computers only serve as a […]
- Dependency on Computers For example, even the author of this paper is not only using the computer to type the essay but they are also relying on the grammar checker to correct any grammatical errors in the paper. […]
- Impact of Computers on Business This paper seeks to explore the impact of the computer and technology, as well as the variety of its aspects, on the business world.
- Impact on Operations Resources of JIT at Dell Computer JIT inventory system stresses on the amount of time required to produce the correct order; at the right place and the right time.
- Impact of Computer Based Communication It started by explaining the impact of the internet in general then the paper will concentrate on the use of Instant Messaging and blogs.
- How to Build a Computer? Preparation and Materials In order to build a personal computer, it is necessary to choose the performance that you want by considering the aspects such as the desired processor speed, the memory, and storage capacity. […]
- Computer Hardware: Past, Present, and Future Overall, one can identify several important trends that profoundly affected the development of hardware, and one of them is the need to improve its design, functionality, and capacity.
- Print and Broadcast Computer Advertisements The use of pictures and words to bring out the special features in any given computer and types of computers is therefore crucial in this type of advertisement because people have to see to be […]
- Computer Technology: Evolution and Developments The development of computer technology is characterized by the change in the technology used in building the devices. The semiconductors in the computers were improved to increase the scale of operation with the development of […]
- The Impact of Computer-Based Technologies on Business Communication The Importance of Facebook to Business Communication Facebook is one of the most popular social networking tools among college students and businesspersons. Blogs and Facebook can be used for the benefit of an organization.
- Computer’s Memory Management Memory management is one of the primary responsibilities of the OS, a role that is achieved by the use of the memory management unit.
- Introduction to Human-Computer Interaction It is a scope of study that explores how individuals view and ponder about computer related technologies, and also investigates both the human restrictions and the features that advance usability of computer structures.
- Solutions to Computer Viruses Efforts should also be made to ensure that once a computer system is infected with viruses, the information saved in it is salvaged.
- The Use of Computers in the Aviation Industry The complicated nature of the software enables the Autopilot to capture all information related to an aircraft’s current position and uses the information to guide the aircraft’s control system.
- Impact of Computer Technology on Economy and Social Life The rapid development of technologies and computer-human interactions influences not only the individual experience of a person but also the general conditions of social relations.
- Computers Will Not Replace Teachers On the other hand, real teachers can emotionally connect and relate to their students; in contrast, computers do not possess feeling and lack of empathy.
- The Drawbacks of Computers in Human Lives Since the invention of computers, they have continued to be a blessing in many ways and more specifically changing the lives of many people.
- Computers vs. Humans: What Can They Do? The differences between a human being and a computer can be partly explained by looking at their reaction to an external stimulus. To demonstrate this point, one can refer to chess computers that can assess […]
- Computers Have Changed Education for the Better Considering the significant effects that computers have had in the educational field, this paper will set out to illustrate how computer systems have changed education for the better.
- Challenges of Computer Technology Computer Technologies and Geology In fact, computer technologies are closely connected to any sphere of life, and it is not surprisingly that geology has a kind of dependence from the development of computers and innovative […]
- Human-Computer Interface in Nursing Practice HCI in the healthcare impacts the quality of the care and patients’ safety since it influences communication among care providers and between the latter and their clients.
- Pointing Devices of Human-Computer Interaction The footpad also has a navigation ball that is rolled to the foot to move the cursor on a computer screen.
- Computer System Review and Upgrade The main purpose of this computer program is going to be the more effective identification of the hooligan groups and their organisation with the purpose to reduce the violation actions.
- Hands-on Training Versus Computer Based Training From the above comparison of hands-on training and computer based training, it can be concluded that a company or an institution should choose its training methodology carefully.
- Advantages of Using Computers at Work I have learned what I hoped to learn in that I have become more aware of the advantages of using computers and why I should not take them for granted.
- How Computer Works? In order for a computer to function, stuff such as data or programs have to be put through the necessary hardware, where they would be processed to produce the required output.
- Apple Inc.’s Competitive Advantages in Computer Industry Competitive advantage is significant in any company A prerequisite of success It enhances sustainable profit growth It shows the company’s strengths Apple Inc.explores its core competencies to achieve it Apple Inc.is led by Tim […]
- Doing Business in India: Outsourcing Manufacturing Activities of a New Tablet Computer to India Another aim of the report is to analyse the requirements for the establishment of the company in India, studying the competitors in the industry and their experience.
- Computer Network Types and Classification For a computer to be functional it must meet three basic requirements, which are it must provide services, communications and most of all a connection whether wireless or physical.the connection is generally the hardware in […]
- Boot Process of a CISCO Router and Computer An understanding of the processes that would help in setting up the configuration of a router and its various elements can lead to relating the booting process of the router to that of any other […]
- Ethical and Illegal Computer Hacking For the ethical hackers, they pursue hacking in order to identify the unexploited areas or determine weaknesses in systems in order to fix them.
- Use of Robots in Computer Science Currently, the most significant development in the field of computer science is the inclusion of robots as teaching tools. The use of robots in teaching computer science has significantly helped to endow students with valuable […]
- Dell Computer Corporation: Competitive Advantages Rivkin et al.claim that Dell remains a company to beat in the personal computer industry despite the initiatives the rival companies have taken.
- Negative Impacts of Computer Technology For instance, they can erase human memory, enhance the ability of human memory, boost the effectiveness of the brain, utilize the human senses in computer systems, and also detect anomalies in the human body. The […]
- Key Issues Concerning Computer Security, Ethics, and Privacy The issues facing computer use such as defense, ethics, and privacy continue to rise with the advent of extra ways of information exchange.
- Ethics in Computer Technology: Cybercrimes The first one is the category of crimes that are executed using a computer as a weapon. The second type of crime is the one that uses a computer as an accessory to the crime.
- The Alliance for Childhood and Computers in Education Of course, there are certain benefits of computers and the abilities children may get, however, it is necessary to remember about the limits and pay enough attention to active life, healthy food, and real communication […]
- Computer Technology in the Student Registration Process The registration process became more efficient due to the reduction in the number of registration staff because they are only tasked with the transfer of the students’ information to their respective departments.
- Computers R Us Company’s Customer Satisfaction The company uses a survey to draw data-driven conclusions about the current customer satisfaction level within the business and the strategies that will most effectively increase their customer satisfaction.
- Career Options for a Computer Programmer Once the system or software has been installed and is running, the computer programmer’s focus is on offering support in maintaining the system.
- Keystone Computers & Networks Inc.’s Audit Plan The objectives of the audit are to identify and describe the objectives of the audit engagement and services that will be provided to the client by the audit team and to define the responsibilities of […]
- Corporate Governance in Satyam Computer Services LTD The Chief Executive Officer of the company in the UK serves as the chairman of the board, but his/her powers are controlled by the other board members.
- Computers and Information Gathering On the other hand, it would be correct to say that application of computers in gathering information has led to negative impacts in firms.
- Computer Fraud and Contracting The law does not provide the consumers with measures to enforcing the online contracts because the argument is that, it is impossible to tell the intention and the consent of the consumer when they signed […]
- Computers and Transformation From 1980 to 2020 The humanity dreams about innovative technologies and quantum machines, allowing to make the most complicated mathematical calculations in billionths of a second but forgets how quickly the progress of computers has occurred for the last […]
- Mathematics as a Basis in Computer Science For example, my scores in physics and chemistry were also comparable to those I obtained in mathematics, a further testament to the importance of mathematics in other disciplines.
- Computer Laboratory Staff and Their Work This will depend on the discretion of the staff to look into it that the rules that have been set in the system are followed dully. This is the work of the staff in this […]
- Computer-Based Systems Effective Implementation Under this methodology, there is a provision that gives attention to the needs of the people involved in the organization about the demands of the technology.
- Computer Hardware Components and Functions Hardware is the physical components of a computer, while the software is a collection of programs and related data to perform the computers desired function.
- Purchasing and Leasing Computer Equipment, Noting the Advantages and Disadvantages of Each In fact, this becomes hectic when the equipment ceases to be used in the organization before the end of the lease period. First, they should consider how fast the equipment needs to be updated and […]
- Effects of Computer Programming and Technology on Human Behavior Phones transitioned from the basic feature phones people used to own for the sole purpose of calling and texting, to smart phones that have amazing capabilities and have adapted the concepts of computers.
- Computer Graphics and Its Historical Background One of the examples of analog computer graphics can be seen in the game called Space Warriors, which was developed at the Massachusetts Institute of Technology. Hence, the entertainment industry was one of the main […]
- Computer Network: Data Flow and Protocol Layering The diagram below shows a simplex communication mode Half-duplex mode is one in which the flow of data is multidirectional; that is, information flow in both directions.
- Building a PC, Computer Structure The choices available are Western Digital 320GB and Seagate 320GB and my advice would be to go for Western Digital as it is a good performer all along.
- Human Mind Simply: A Biological Computer When contemplating the man-like intelligence of machines, the computer immediately comes to mind but how does the amind’ of such a machine compare to the mind of man?
- Computers in Education: More a Boon Than a Bane Thus, one of the greatest advantages of the computer as a tool in education is the fact that it builds the child’s capacity to learn things independently.
- Recommendations for Computer to Purchase This made me to look into and compare the different models of computers which can be good for the kind of work we do.
- The Influence of Computer on the Living Standards of People All Over the World In the past, people considered computers to be a reserve for scientist, engineers, the army and the government. Media is a field that has demonstrated the quality and value of computers.
- Computer Sciences Technology: Smart Clothes In this paper we find that the smart clothes are dated back to the early 20th century and they can be attributed to the works of artists and scientists.
- The American Military and the Evolution of Computer Technology From the Early 1940s to Early 1960s During the 1940s-1960, the American military was the only wouldriver’ of computer development and innovations.”Though most of the research work took place at universities and in commercial firms, military research organizations such as the Office […]
- Computer-Based Information Systems The present essay will seek to discuss computer-based information systems in the context of Porter’s competitive strategies and offer examples of how computer-based information systems can be used by different companies to gain a strategic […]
- Computer Technology in the Last 100 Years of Human History These communication tools are based on computer technology, and are the foundation of younger generations’ living. Computer technology is detrimental to the lives of younger generations because it fails.
- Human Computer Interface: Evolution and Changes The conferences will not require members to be there in person as the events can be transmitted to people in their homes and they can make suggestions too.
- Computer Aided Software Tools (CASE) The use of the repository is common to both the visual analyst and IBM rational software with varying differences evident on the utilization of services.
- Levels of Computer Science and Programming Languages For the programmer to create low-level programming languages, computer architecture is very necessary for machine coding in the Central Processing Unit of a computer.
- Computer-Based Communication Technology in Business Communication: Instant Messages and Wikis To solve the problems within the chosen filed, it is necessary to make people ready to challenges and provide them with the necessary amount of knowledge about IN and wikis’ peculiarities and properly explain the […]
- Computer Viruses: Spreading, Multiplying and Damaging A computer virus is a software program designed to interfere with the normal computer functioning by infecting the computer operating system.
- Pipeline Hazards in Computer Architecture Therefore, branch instructions are the primary reasons for these types of pipeline hazards to emerge. In conclusion, it is important to be able to distinguish between different pipeline types and their hazards in order to […]
- “Failure to Connect – How Computers Affect Our Children’s Minds and What We Can Do About It” by Jane M. Healy Detailed analysis of several chapters of the book will help to understand the impact of computer technologies on children’s health and mental development. To begin with, chapter 4 of the book deals with the impact […]
- Computer Forensics Tools and Evidence Processing The purpose of this paper is to analyze available forensic tools, identify and explain the challenges of investigations, and explain the legal implication of the First and Fourth Amendments as they relate to evidence processing […]
- The Popularity of Esports Among Computer Gamers E-sports or cybersports are the new terms that can sound odd to the men in the street but are well-known in the environment of video gamers.
- Strategic Marketing: Dell and ASUSTeK Computer Inc. Another factor contributing to the success of iPad is the use of stylish, supreme marketing and excellent branding of the products.
- Online Video and Computer Games Video and computer games emerged around the same time as role playing games during the 1970s, and there has always been a certain overlap between video and computer games and larger fantasy and sci-fi communities.
- How to Teach Elderly Relatives to Use the Computer The necessary safety information: Do not operate the computer if there is external damage to the case or the insulation of the power cables.
- Computer Problems: Review I was referred to the these three websites by my peers who told me they had experienced problems with their computers in the past and were of the opinion that these websites could provide me […]
- Computers: The History of Invention and Development It is treated as a reliable machine able to process and store a large amount of data and help out in any situation.”The storage, retrieval, and use of information are more important than ever” since […]
- Computer Virus User Awareness It is actually similar to a biological virus wherein both the computer and biological virus share the same characteristic of “infecting” their hosts and have the ability to be passed on from one computer to […]
- How Computers Negatively Affect Student Growth Accessibility and suitability: most of the school and student do not have computers that imply that they cannot use computer programs for learning, lack of availability of internet facilities’ availability also makes the students lack […]
- Bill Gates’ Contributions to Computer Technology Upon examination of articles written about Gates and quotations from Gates recounting his early childhood, several events stand out in significance as key to depicting the future potential of Gates to transform the world with […]
- Internship in the Computer Service Department In fact, I know that I am on track because I have been assessed by the leaders in the facility with the aim of establishing whether I have gained the required skills and knowledge.
- Human Computer Interaction in Web Based Systems The personalization of web services has been seen to improve the interaction that the user will have with the information presented by the machine.
- How Computers Work: Components and Power The CPU of the computer determines the ultimate performance of a computer because it is the core-processing unit of a computer as shown in figure 2 in the appendix.
- Computer R Us Company: Initiatives for Improving Customer Satisfaction The result of the second question shows that the overall satisfaction of female customers is higher than that of male customers. Therefore, there is a need to improve the level of satisfaction of the male […]
- Dell Computer Company and Michael Dell These numbers prove successful reputation of the company and make the organization improve their work in order to attract the attention of more people and help them make the right choice during the selection of […]
- Computer-Based Testing: Beneficial or Detrimental? Clariana and Wallace found out that scores variations were caused by settings of the system in computer-based and level of strictness of examiners in paper-based. According to Meissner, use of computer based tests enhances security […]
- Computer-Based Learning and Virtual Classrooms E-learning adds technology to instructions and also utilizes technologies to advance potential new approaches to the teaching and learning process. However, e-learners need to be prepared in the case of a technology failure which is […]
- Computer Based Learning in Elementary Schools The main purpose of the research is to consider the background of the chosen sphere, the elementary education, and discuss current business issues in the computer technologies which may be used in the sphere and […]
- Purchasing or Leasing Computer Equipment: Advantages and Disadvantages When the organization decides to lease this equipment for the installation, will be on the part of the owners and maintenance, as well.
- Introduction to Computer Graphics: Lesson Plans Students should form their own idea of computer graphics, learn to identify their types and features, and consider areas of application of the new direction in the visual arts.
- How to Build a Gaming Computer The first step to creating a custom build for a PC is making a list of all the necessary components. This explanation of how to build a custom gaming computer demonstrates that the process is […]
- PayPal and Human-Computer Interaction One of the strong points of the PayPal brand is its capacity to use visual design in the process of creating new users. The ability of the Paypal website to transform answers to the need […]
- Computer Technology Use in Psychologic Assessment The use of software systems in the evaluation may lead a practitioner to misjudge and exceed their own competency if it gives the school psychologists a greater sense of safety.
- Personal Computer: The Tool for Technical Report In addition to this, computers, via the use of reification, make it feasible to reconfigure a process representation so that first-time users can examine and comprehend many facets of the procedures.
- Altera Quartus Computer Aided Design Tool So, the key to successful binary additions is a full adder. The complete adder circuit takes in three numbers, A, B, and C, adds them together, and outputs the sum and carry.
- Computer-Aided Design in Knitted Apparel and Technical Textiles In doing so, the report provides an evaluation of the external context of CAD, a summary of the technology, and the various potential applications and recommendations of CAD.
- The Twelve-Cell Computer Battery Product: Weighted Average and Contracts Types There is a need to fully understand each of the choices, the cost, benefits, and risks involved for the individual or company to make the right decision.
- Computer Usage Evolution Through Years In the history of mankind, the computer has become one of the most important inventions. The diagnostics and treatment methods will be much easier with the help of computer intervention.
- How to Change a Computer Hard Drive Disk These instructions will allow the readers to change the HDD from a faulty computer step by step and switch on the computer to test the new HDD.
- Researching of Computer-Aided Design: Theory To draw a first-angle projection, one can imagine that the object is placed between the person drawing and the projection. To distinguish the first angle projection, technical drawings are marked with a specific symbol.
- Systems Development Life Cycle and Implementation of Computer Assisted Coding The potential risks the software must deal with are identified at this phase in addition to other system and hardware specifications.
- Why Is Speed More Important in Computer Storage Systems? While there are indications of how speed may be more significant than storage in the context of a computer system, both storage and speed are important to efficiency.
- Researching of Computer Simulation Theory Until then, people can only continue to study and try to come to unambiguous arguments regarding the possibility of human life in a computer simulation.
- Choosing a Computer for a Home Recording Studio The motherboard is responsible for the speed and stability of the system and should also have a large number of ports in case of many purposes of the computer in the studio.
- Computer Programming and Code The Maze game was the one I probably enjoyed the most since it was both engaging and not challenging, and I quickly understood what I needed to do.
- Computer-Aided-Design, Virtual and Augmented Realities in Business The usual applications of these technologies are in the field of data management, product visualization, and training; however, there is infinite potential in their development and integration with one another and this is why they […]
- Getting to Know Laptop Computers This report aims to discuss the composition of a laptop computer and the purpose of each element. To summarize, a laptop possesses the same functions as a desktop computer but is smaller in size.
- Computer-Mediated Communication Competence in Learning The study showed that knowledge of the CMC medium was the strongest influence on participation with a =.41. In addition to that, teachers can use the results of this study to improve students’ experience with […]
- The Evolution of Computers and Digitalization The evolution of computers was a long process, which started with the emergence of calculating machines. The repeated operations, which were the basis of their functioning, determined further progress.
- Anticipated Growth in Computer and Monitor Equipment Sales This presentations explores the computer equipment market to identify opportunities and device ways of using the opportunities to the advantage of EMI.
- Current Trends and Projects in Computer Networks and Security That means the management of a given organization can send a request to communicate to the network the intended outcome instead of coding and executing the single tasks manually.
- History of Computers: From Abacus to Modern PC Calculators were among the early machines and an example of this is the Harvard Mark 1 Early man was in need of a way to count and do calculations.
- Acme Corp.: Designing a Better Computer Mouse The approach that the company is taking toward the early stages of the development process is to only include design engineers and brainstorm ideas.
- Computer Forensic Incident All evidence should be collected in the presence of experts in order to avoid losing data as well as violating privacy rights.N.
- Computer Science Courses Project Management Second, the selected independent reviewers analyze the proposal according to the set criteria and submit the information to the NSF. The project is crucial for the school and the community, as students currently do not […]
- The Computer Science Club Project’s Budget Planning The budget for the program is provided in Table 1 below. Budget The narrative for the budget is provided below: The coordinator will spend 100% of his time controlling the quality of the provided services […]
- How Computer Based Training Can Help Teachers Learn New Teaching and Training Methods The content will be piloted in one of the high schools, in order to use the teachers as trainers for a reaching more schools with the same methodology.
- Approaches in Computer-Aided Design Process Challenges: The intricacy of the structure that resulted in the need to understand this process was the reason for this study.
- Acquiring Knowledge About Computers One of the key features of A.I.U.’s learning platform is the use of the Gradebook. The best feature of the instant messaging tool is the fact that it is easy to install with no additional […]
- Future of Forensic Accounting With Regards to Computer Use and CFRA There are different types of accounting; they include management accounting, product control, social accounting, non assurance services, resource consumption accounting, governmental accounting, project accounting, triple accounting, fund accounting and forensic accounting among others.
- Computer Museum: Personal Experience While in the Revolution, I got a chance to see a working replica of the Atanasoff-Berry Computer, which was the first real model of a working computer.
- Computer-Based Search Strategy Using Evidence-Based Research Methodology In this case, the question guiding my research is “Can additional choices of food and places to eat improve appetite and maintain weight in residents with dementia?” The population in this context will be the […]
- Recovering from Computer System Crashes In the event of a crash, the first step is to identify the type of crash and then determine the best way to recover from the crash.
- Effective Way to Handle a Computer Seizure Thus, it is important to device a method of investigation that may enhance the preservation and maintenance of the integrity of the evidence.
- VisualDX: Human-Computer Interaction VisualDX is structured such that the user is guided through the steps of using the software system without having to be a software specialist.
- Computer-Aided Software Engineering Tools Usage The inclusion of these tools will ensure that the time cycle is reduced and, at the same time, enhances the quality of the system.
- Training Nurses to Work With Computer Technologies and Information Systems The educational need at this stage will be to enhance the ability of the learners to work with computer technologies and information system.
- Computer Crime in the United Arab Emirates Computer crime is a new type of offense that is committed with the help of the computer and a network. This article aims at evaluating some of the laws established in the United Arab Emirates, […]
- Computer Science: “DICOM & HL7” In the transport of information, DICOM recognizes the receiver’s needs such as understanding the type of information required. This creates some form of interaction between the sender and the receiver of the information from one […]
- Computer Components in the Future It must be noted though that liquid cooling systems utilize more electricity compared to traditional fan cooling systems due to the use of both a pump and a radiator in order to dissipate the heat […]
- Majoring in Computer Science: Key Aspects Computer Science, abbreviated as CS, is the study of the fundamentals of information and computation procedures and of the hands-on methods for the execution and application in computer systems.
- How to Build a Desktop Personal Computer The processor will determine the speed of the system but the choice between the two major types-Intel and AMD- remains a matter of taste.
- Networking Concepts for Computer Science Students The firewall, on the other hand, is a hardware or software that secures a network against external threats. Based on these a single subnet mask is sufficient for the whole network.
- Trusted Computer System Evaluation Criteria The paper provides an overview of the concepts of security assurance and trusted systems, an evaluation of the ways of providing security assurance throughout the life cycle, an overview of the validation and verification, and […]
- Advanced Data & Computer Architecture Solid knowledge and understanding of the information architecture, access, storage mechanisms and technologies, internet mechanisms, and systems administration contribute to the complete knowledge of the whole system architecture.
- Computer Hardware: Structure, Purpose, Pros and Cons The main focus of the post is with respect to the security issues of web 2. 0 technologies is susceptible to is SQL injection attacks, which primarily entail the use of a code injection technique […]
- Assessing and Mitigating the Risks to a Hypothetical Computer System The security of information is very important for the success of any organization and therefore should be given the first priority in the organization’s strategic plans.
- Computer Technology: Databases Databases are components of Information Systems that are used when the Information Systems have large amounts of a, especially when the interfaces in the Information System are interactive, and when users can access the system […]
- The Reduction in Computer Performance The Check Disk utility available in Windows XP enables one to monitor the health of the hard disk. This utility will analyze the disk and display actions that can be undertaken to recover disk space.
- Advancements in Computer Science and Their Effects on Wireless Networks The most significant technological advancement witnessed in the 20th century was the expansion of World Wide Web in the 1990s. The wireless developments in the society have in addition greatly improved from the advent of […]
- Choosing an Appropriate Computer System for the Home Use It looked at the history of how personal computers have evolved to become one of the most adopted gargets in businesses and the personal lives of many individuals.
- Global Climate and Computer Science In an attempt to discover the role technology can play in the research of climate change, several approaches have been recommended by the UN’s Intergovernmental Panel on Climate Change.
- Threats to Computer Users This calls for increased vigilance and awareness by these users, to protect the confidentiality and their data and personal information. In most cases, the links lead to duplicates of authentic sites and require the unsuspecting […]
- Computer Network Security Legal Framework With the introduction of cloud computing, the need of data protection has been rising significantly within computer networks to facilitate the protection of Intellectual Property among the users.
- Computer Forensics and Audio Data Retrieval Advanced technology in the modern society has contributed to the increase in computer and computer supported criminal activities due to the soaring increases in the number of internet users across the world and computerization of […]
- Computer Sciences Technology: E-Commerce E-commerce is synonymous with e-business and entails the buying and selling of goods and services on the internet especially the World Wide Web.
- Computer Forensics: Data Acquisition Data acquisition is a branch of computer forensics concerned with the retrieval of data originally located on a suspect medium such as a hard drive.
- Computer Forensic Timeline Visualization Tool The necessity to save time in computer forensic investigations is the basis of the tool that Olssen and Boldt came up with.
- Personal Computer Evolution Overview It is important to note that the first evolution of a personal computer occurred in the first century. This is because of the slowness of the mainframe computers to process information and deliver the output.
- The Qatar Independence Schools’ Computer Network Security Control The result of the interviews mainly outlined several common themes and patterns in terms of the design of the proposed security system.
- Human-Computer Interaction and Communication As the person is interacting with the gadgets or the computers, he should be favored by the design in that the system should be in such a way that it supports human usability.
- Dependability of Computer Systems In the dependability on computer systems, reliability architects rely a great deal on statistics, probability and the theory of reliability. The purpose of reliability in computer dependability is to come up with a reliability requirement […]
- Computer Sciences Technology: Influencing Policy Letter It is clear that the Electronic Communication Act is outdated and should be revised to account for the recent developments in technology.
- Computer Control System in a Laboratory Setting In this case the iControl system is designed to control and monitor temperature variables of a hazardous liquid within a laboratory environment as well as other parameters such as smoke and light.
- Property and Computer Crimes
- Current Laws and Acts That Pertain to Computer Security
- Computer Network: Electronic Mail Server
- Evolution of Computers in Commercial Industries and Healthcare
- Honeypots and Honeynets in Network Security
- Viruses and Worms in Computers
- The Life, Achievement, and Legacy to Computer Systems of Bill Gates
- Life, Achievement, and Legacy to Computer Systems of Alan Turing
- Computer Sciences Technology and HTTPS Hacking Protection
- Protecting Computers From Security Threats
- Computer Sciences Technology: Admonition in IT Security
- Overview of Computer Languages – Python
- Research Tools Used by Computer Forensic Teams
- Maintenance and Establishment of Computer Security
- Computer Tech Company’s Medical Leave Problem
- Sales Plan for Computer Equipment
- Smartwatches: Computer on the Wrist
- Purpose of the Computer Information Science Course
- How to Sell Computers: PC Type and End User Correlation
- Technological Facilities: Computers in Education
- Computers’ Critical Role in Modern Life
- The Five Developments of the Computers
- History of the Personal Computer: From 1804 to Nowadays
- Malware: Code Red Computer Worm
- Sidetrack Computer Tech Business Description
- Strayer University’s Computer Labs Policy
- Computers Brief History: From Pre-Computer Hardware to Modern Computers
- Computer Assisted Language Learning in English
- Shaping and Profiting From the Computer Revolution: Bill Gates
- TUI University: Computer Capacity Evaluation
- The Effectiveness of the Computer
- Quasar Computers Company’s Economic Strategies
- Computer Security System: Identity Theft
- Analogical Reasoning in Computer Ethics
- Computer Security: Intrusion Detection System Policy
- Dell Computer Corporation: Management Control System
- Computer Mediated Communication Enhance or Inhibit
- Technical Communication: Principles of Computer Security
- How Computers Have Changed the Way People Communicate
- Principles of Computer Security
- Why to Choose Mac Over Windows Personal Computer
- Biometrics and Computer Security
- Computer Addiction: Side Effects and Possible Solutions
- Marketing: Graphic and Voice Capabilities of a Computer Software Technology
- “ESL Students’ Computer-Mediated Communication Practices” by Dong Shin
- Computer Systems: Technology Impact on Society
- State-Of-The-Art in Computer Numerical Control
- The Increasing Human Dependence on Computers
- Computer Adventure Games Analysis
- Legal and Ethical Issues in Computer Security
- Resolving Software Problem: Timberjack Company
- The Research of Computer Assisted Instructions
- Computer Security: Bell-Lapadula & Biba Models
- Mind, Brains, and Computer: Homunculus Theories
- Computer and Information Tech Program in Education
- The Concept of Computer Hardware and Software
- Computer Software and Wireless Information Systems
- Growing Compatibility Issues: Computers and User Privacy
- Computer Vision: Tracking the Hand Using Bayesian Models
- Modern Portable Computer – Battery Technology, LCD Displays, Low-Power CPUs
- Firewalls in Computer Security
- Use and Benefit of Computer Analysis
- Computer Financial Systems and the Labor Market
- Computer Engineer Stephen Wozniak
- Gaming System for Dell Computer: Media Campaign Issues
- Computers: Science and Scientists Review
- Uniform Law for Computer Information Transactions
- Computer Science. Open Systems Interconnection Model
- Personal Computer and Social Media Security
- Apple Inc. and Computer Market
- Computer Forensics in Criminal Investigation
- Computer Crimes: Viewing the Future
- Computer Forensics and Cyber Crime
- Computer Forensics: Identity Theft
- Computer Crime Investigation Processes and Analyses
- Dam Computers Company’s Strategic Business Planning
- Computer and Internet Security Notions
- Technical Requirements for Director Computer Work
- Allocating a Personal Computer
- Graphical Communication and Computer Modeling
- Computers and Web 2.0
- Computer Games and Instruction
- Zayed University’s Computer Security Internship
- Memex and Dynabook as Early Portable Computers
- IBM.com Website and Human-Computer Interaction
- IBM Website and Human-Computer Interaction
- Computer Hardware and Software Policies for Schools
- Education Goals in Computer Science Studies
- Enhancing Sepsis Collaborative: Computer Documentation
- Apple Ipad: History of the Tablet Computers and Their Connection to Asia
- Computer Emergency Readiness Team
- Computer Literacy: Parents and Guardians Role
- Computer Viruses, Their Types and Prevention
- Computers in Security, Education, Business Fields
- Graph Theory Application in Computer Science
- Epistemic Superiority Over Computer Simulations
- Computer Crimes and Internet Security
- The History of Computer Storage
- Personal Computers and Protection of Privacy
- Fertil Company’s Computer and Information Security
- Computer-Assisted Language Learning: Barriers
- Computer-Assisted Second Language Learning Tools
- Computer-Supported Collaborative Learning
- Computer Assisted Language Learning in L2 Education
- Computer-Assisted English Language Learning
- Computer Gaming Influence on the Academic Performance
- Computer Evolution, Its Future and Societal Impact
- Human Computer Interaction: Types of Special Needs
- PowerPoint Computer Program: Principles and Processes
- Computer and Digital Forensics and Cybercrimes
- Online and Computer-Based Technology Issues
- Computer Reservations System in Hotel
- VSphere Computer Networking: Planning and Configuring
- Cybercrime, Digital Evidence, Computer Forensics
- Human Overdependence on Computers
- Medical Uses of Computer-Mediated Communication
- Computer Architecture for a College Student
- Human-Computer Interaction in Health Care Settings
- Personal Computers in the U.S. Market
- HP Company’s Computer Networking Business
- Foreign Direct Investment in the South Korean Computer Industry
- Computer Mediated Interpersonal and Intercultural Communication
- Computer Apps for Productive Endeavors of Youth
- Computer-Mediated Communication Aspects and Influences
- Computer Security and Computer Criminals
- Dell Computers Company Planning and Organization
- Humanities and Computer Science Collaboration
- Globalization Influence on the Computer Technologies
- Euro Computer Systems and Order Fulfillment Center Conflict
- Computer Science Program in Colleges and Universities
- Computer Science: Threats to Internet Privacy
- EFL and ESL Learners: Computer-Aided Cooperative Learning
- Design and Installation of a Computer Network
- Computer Science Corporation Service Design
- Melissa Virus and Its Effects on Computers
- Computer Security – Information Assurance
- Computer-Based Technologies That Assist People With Disabilities
- Computer Mediated Learning
- Environmental Friendly Strategy for Quality Computers Limited
- Human-Computer Interaction: Tangible Video Bubbles
- “Interaction” in Human Computer Interaction: iPad’s Design Framework
- Corporate Governance: Satyam Computer Service Limited
- Quasar Company’s Optical Computers
- Implementing Computer Assisted Language Learning (CALL) in EFL Classrooms
- Computer Adaptive Testing and Using Computer Technology
- Computer Games: Morality in the Virtual World
- How Computer Based Training Can Help Teachers Learn New Teaching and Training Methods
- Human Computer Interaction – Heptic Technology in PlayMotion
- Apple Computer, Inc.: Maintaining the Music Business
- Computer Forensics and Digital Evidence
- The Usefulness of Computer Networks for Students
- Computer and Digital Music Players Industry: Apple Inc. Analysis
- Computer Manufacturer: Apple Computer Inc.
- Theft of Information and Unauthorized Computer Access
- Supply Chain Management at Dell Computers
- Turing Test From Computer Science
- The Computer-Mediated Learning Module
- Computer Security and Its Main Goals
- Apple Computer Inc. – History and Goals of This Multinational Corporation
- Computer Technology in Education
- Telecommunication and Computer Networking in Healthcare
- The Convergence of the Computer Graphics and the Moving Image
- Information Security Fundamentals: Computer Forensics
- Computer Forensics Related Ethics
- Microsoft Operating System for Personal Computers a Monopoly in the Markets
- People Are Too Dependent on Computers
- Computer-Mediated Communication: Study Evaluation
- Computer Assisted Language Learning in the Middle East
- Apple Computer, Inc. Organizational Culture and Ethics
- Computer-Based Information Systems and E-Business Strategy
- Analyses and Model Forms: Computer Sciences Corporation Case Study
- Computer Sciences Corporation: Michael Horton
- Review: “Computers Learn to Listen, and Some Talk Back” by Lohr and Markoff
- The Role of Computer Forensics in Criminology
- Paralinguistic Cues in Computer-Mediated Communications in Personality Traits
- Computer-Mediated Communication
- Comparison of Three Tablet Computers: Ipad2, Motorola Xoom and Samsung Galaxy
- Decker Computers: E-Commerce Website App
- Apple Computer Inc. Marketing
- The Future of Human Computer Interface and Interactions
- Third Age Living and Computer Technologies in Old Age Learning
- Ethics and Computer Security
- Human-Computer Interaction in Health Care
- Computer Technology and Networked Organizations
- Computer System Electronic Components
- Security of Your Computer and Ways of Protecting
- Computer Safety: Types and Technologies
- Reflections and Evaluations on Key Issues Concerning Computer
- ClubIT Computer Company: Information and Technology Solutions
- The Impact of Computers
- HP Computer Marketing Concept
- Tablet PCs Popularity and Application
- Computer Addiction in Modern Society
- The Evolution of the Personal Computer and the Internet
- Advancement of the Computer: Microchips and Semiconductors
- Computers in the Classroom: Pros and Cons
- Computer Cookies: What Are They and How Do They Work
- Modeling, Prototyping and CASE Tools: The Inventions to Support the Computer Engineering
- Ergotron Inc Computer Workstation Environment
- Experts Respond to Questions Better Than Computers
- Through a Computer Display and What People See There: Communication Technologies and the Quality of Social Interactions
- Computer Based Training Verses Instructor Lead Training
- Social Implications of Computer Technology: Cybercrimes
- Leasing Computers at Persistent Learning
- Tablet Computer Technology
- Ethics in Computer Hacking
- Computer Forensics and Investigations
- Preparing a Computer Forensics Investigation Plan
- Basic Operations of Computer Forensic Laboratories
- Information Technology: Computer Software
- Project Management and Computer Charting
- HP: Arguably the Best Computer Brand Today
- Computer Networks and Security
- The Computer Microchip Industry
- Computer Technician and Labor Market
- Network Security and Its Importance in Computer Networks
- Company Analysis: Apple Computer
- Preparation of Correspondences by Typewriters and Computers
- Responsibilities of Computer Professionals to Understanding and Protecting the Privacy Rights
- Computers & Preschool Children: Why They Are Required in Early Childhood Centers
- Computer and Telecommunication Technologies in the Worlds’ Economy
- Computer Survey Analysis: Preferences of the People
- Computer Security: Safeguard Private and Confidential Information
- Writing Argumentative Essay With Computer Aided Formulation
- Computer Communication Network in Medical Schools
- Computer Systems in Hospital
- Introduction to Computers Malicious Software (Trojan Horses)
- Computer Security Breaches and Hacking
- State Laws Regarding Computer Use and Abuse
- Apple Computer: The Twenty-First Century Innovator
- Computer Crimes Defense and Prevention
- Concept and Types of the Computer Networks
- How Have Computers Changed the Wage Structure?
- Do Computers and the Internet Help Students Learn?
- How Are Computers Used in Pavement Management?
- Are Americans Becoming Too Dependent on Computers?
- How Are Data Being Represented in Computers?
- Can Computers Replace Teachers?
- How Did Computers Affect the Privacy of Citizens?
- Are Computers Changing the Way Humans Think?
- How Are Computers and Technology Manifested in Every Aspect of an American’s Life?
- Can Computers Think?
- What Benefits Are Likely to Result From an Increasing Use of Computers?
- How Are Computers Essential in Criminal Justice Field?
- Are Computers Compromising Education?
- How Are Computers Used in the Military?
- Did Computers Really Change the World?
- How Have Computers Affected International Business?
- Should Computers Replace Textbooks?
- How Have Computers Made the World a Global Village?
- What Are the Advantages and Disadvantages for Society of the Reliance on Communicating via Computers?
- Will Computers Control Humans in the Future?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 26). 412 Computers Topics & Essay Examples. https://ivypanda.com/essays/topic/computers-essay-topics/
"412 Computers Topics & Essay Examples." IvyPanda , 26 Feb. 2024, ivypanda.com/essays/topic/computers-essay-topics/.
IvyPanda . (2024) '412 Computers Topics & Essay Examples'. 26 February.
IvyPanda . 2024. "412 Computers Topics & Essay Examples." February 26, 2024. https://ivypanda.com/essays/topic/computers-essay-topics/.
1. IvyPanda . "412 Computers Topics & Essay Examples." February 26, 2024. https://ivypanda.com/essays/topic/computers-essay-topics/.
Bibliography
IvyPanda . "412 Computers Topics & Essay Examples." February 26, 2024. https://ivypanda.com/essays/topic/computers-essay-topics/.
- Laptop Ideas
- Cyberspace Topics
- Internet Research Ideas
- Cyber Bullying Essay Ideas
- Hacking Essay Topics
- CyberCrime Topics
- Artificial Intelligence Questions
- Cyber Security Topics
- Electronics Engineering Paper Topics
- Virtualization Essay Titles
- Dell Topics
- Intel Topics
- Microsoft Topics
- Apple Topics
ScholarWorks@UMass Amherst
Home > Engineering > ECE > Electrical & Computer Engineering Masters Theses Collection

Electrical & Computer Engineering Masters Theses Collection
Theses from 2024 2024.
Extracting DNN Architectures Via Runtime Profiling On Mobile GPUs , Dong Hyub Kim, Electrical & Computer Engineering
Semantic-Aware Blockchain Architecture Design for Lifelong Edge-enabled Metaverse , Ning Wang, Electrical & Computer Engineering
Blockchain Design for a Secure Pharmaceutical Supply Chain , Zhe Xu, Electrical & Computer Engineering
Collaborative Caching and Computation Offloading for Intelligent Transportation Systems enabled by Satellite-Airborne-Terrestrial Networks , Shulun Yang, Electrical & Computer Engineering
Protecting Return Address Integrity for RISC-V via Pointer Authentication , yuhe zhao, Electrical & Computer Engineering
Theses from 2023 2023
Fingerprinting for Chiplet Architectures Using Power Distribution Network Transients , Matthew G. Burke, Electrical & Computer Engineering
Design and Fabrication of a Trapped Ion Quantum Computing Testbed , Christopher A. Caron, Electrical & Computer Engineering
Analog Cancellation of a Known Remote Interference: Hardware Realization and Analysis , James M. Doty, Electrical & Computer Engineering
Electrothermal Properties of 2D Materials in Device Applications , Samantha L. Klein, Electrical & Computer Engineering
Ablation Study on Deeplabv3+ for Semantic Segmentation , Bowen Lei, Electrical & Computer Engineering
A Composability-Based Transformer Pruning Framework , Yuping Lin, Electrical & Computer Engineering
A Model Extraction Attack on Deep Neural Networks Running on GPUs , Jonah G. O'Brien Weiss, Electrical & Computer Engineering
Heterogeneous IoT Network Architecture Design for Age of Information Minimization , Xiaohao Xia, Electrical & Computer Engineering
Theses from 2022 2022
Theory and Analysis of Backprojection Processing for Interferometric SAR , Marc Closa Tarres, Electrical & Computer Engineering
Unpaired Skeleton-to-Photo Translation for Sketch-to-Photo Synthesis , Yuanzhe Gu, Electrical & Computer Engineering
Integration of Digital Signal Processing Block in SymbiFlow FPGA Toolchain for Artix-7 Devices , Andrew T. Hartnett, Electrical & Computer Engineering
Planar Ultra-Wideband Modular Antenna (PUMA) Arrays for High-Volume Manufacturing on Organic Laminates and BGA Interfaces , James R. LaCroix, Electrical & Computer Engineering
Planar Transmission-Line Metamaterials on an Irregular Grid , Tina E. Maurer, Electrical & Computer Engineering
Formally Verifiable Synthesis Flow In FPGAs , Anurag V. Muttur, Electrical & Computer Engineering
Theses from 2021 2021
Graph-Algorithm Based Verification on Network Configuration Robustness , Zibin Chen, Electrical & Computer Engineering
A Cloud Infrastructure for Large Scale Health Monitoring in Older Adult Care Facilities , Uchechukwu Gabriel David, Electrical & Computer Engineering
Internet Infrastructures for Large Scale Emulation with Efficient HW/SW Co-design , Aiden K. Gula, Electrical & Computer Engineering
Mtemp: An Ambient Temperature Estimation Method Using Acoustic Signal on Mobile Devices , Hao Guo, Electrical & Computer Engineering
BENCHMARKING SMALL-DATASET STRUCTURE-ACTIVITY-RELATIONSHIP MODELS FOR PREDICTION OF WNT SIGNALING INHIBITION , Mahtab Kokabi, Electrical & Computer Engineering
ACTION : Adaptive Cache Block Migration in Distributed Cache Architectures , Chandra Sekhar Mummidi, Electrical & Computer Engineering
Modeling and Characterization of Optical Metasurfaces , Mahsa Torfeh, Electrical & Computer Engineering
TickNet: A Lightweight Deep Classifier for Tick Recognition , Li Wang, Electrical & Computer Engineering
Lecture Video Transformation through An Intelligent Analysis and Post-processing System , Xi Wang, Electrical & Computer Engineering
Correcting For Terrain Interference, Attenuation, and System Bias for a Dual Polarimetric, X-Band Radar , Casey Wolsieffer, Electrical & Computer Engineering
Theses from 2020 2020
Numerical Simulation of Thermoelectric Transport in Bulk and Nanostructured SiSn Alloys , Venkatakrishna Dusetty, Electrical & Computer Engineering
Deep Reinforcement Learning For Distributed Fog Network Probing , Xiaoding Guan, Electrical & Computer Engineering
COMPRESSIVE PARAMETER ESTIMATION VIA APPROXIMATE MESSAGE PASSING , Shermin Hamzehei, Electrical & Computer Engineering
Metric Learning via Linear Embeddings for Human Motion Recognition , ByoungDoo Kong, Electrical & Computer Engineering
Compound Effects of Clock and Voltage Based Power Side-Channel Countermeasures , Jacqueline Lagasse, Electrical & Computer Engineering
Network Virtualization and Emulation using Docker, OpenvSwitch and Mininet-based Link Emulation , Narendra Prabhu, Electrical & Computer Engineering
Thermal Transport Modeling Of Semiconductor Materials From First Principles , Aliya Qureshi, Electrical & Computer Engineering
CROSSTALK BASED SIDE CHANNEL ATTACKS IN FPGAs , Chethan Ramesh, Electrical & Computer Engineering
Accelerating RSA Public Key Cryptography via Hardware Acceleration , Pavithra Ramesh, Electrical & Computer Engineering
Real-Time TDDFT-Based Filtered Spectroscopy , Ivan Williams, Electrical & Computer Engineering
Perception System: Object and Landmark Detection for Visually Impaired Users , Chenguang Zhang, Electrical & Computer Engineering
Theses from 2019 2019
An Empirical Analysis of Network Traffic: Device Profiling and Classification , Mythili Vishalini Anbazhagan, Electrical & Computer Engineering
Pre-Travel Training And Real-Time Guidance System For People With Disabilities In Indoor Environments , Binru Cao, Electrical & Computer Engineering
Energy Efficiency of Computation in All-spin Logic: Projections and Fundamental Limits , Zongya Chen, Electrical & Computer Engineering
Improving Resilience of Communication in Information Dissemination for Time-Critical Applications , Rajvardhan Somraj Deshmukh, Electrical & Computer Engineering
InSAR Simulations for SWOT and Dual Frequency Processing for Topographic Measurements , Gerard Masalias Huguet, Electrical & Computer Engineering
A Study on Controlling Power Supply Ramp-Up Time in SRAM PUFs , Harshavardhan Ramanna, Electrical & Computer Engineering
The UMass Experimental X-Band Radar (UMAXX): An Upgrade of the CASA MA-1 to Support Cross-Polarization Measurements , Jezabel Vilardell Sanchez, Electrical & Computer Engineering
A Video-Based System for Emergency Preparedness and Recovery , Juechen Yin, Electrical & Computer Engineering
Theses from 2018 2018
Phonon Transport at Boundaries and Interfaces in Two-Dimensional Materials , Cameron Foss, Electrical & Computer Engineering
SkinnySensor: Enabling Battery-Less Wearable Sensors Via Intrabody Power Transfer , Neev Kiran, Electrical & Computer Engineering
Immersive Pre-travel Training Application for Seniors and People with Disabilities , Yang Li, Electrical & Computer Engineering
Analog Computing using 1T1R Crossbar Arrays , Yunning Li, Electrical & Computer Engineering
On-Chip Communication and Security in FPGAs , Shivukumar Basanagouda Patil, Electrical & Computer Engineering
CROWDSOURCING BASED MICRO NAVIGATION SYSTEM FOR VISUALLY IMPAIRED , Quan Shi, Electrical & Computer Engineering
AN EVALUATION OF SDN AND NFV SUPPORT FOR PARALLEL, ALTERNATIVE PROTOCOL STACK OPERATIONS IN FUTURE INTERNETS , Bhushan Suresh, Electrical & Computer Engineering
Applications Of Physical Unclonable Functions on ASICS and FPGAs , Mohammad Usmani, Electrical & Computer Engineering
Improvements to the UMASS S-Band FM-CW Vertical Wind Profiling Radar: System Performance and Data Analysis. , Joseph Waldinger, Electrical & Computer Engineering
Theses from 2017 2017
AutoPlug: An Automated Metadata Service for Smart Outlets , Lurdh Pradeep Reddy Ambati, Electrical & Computer Engineering
SkyNet: Memristor-based 3D IC for Artificial Neural Networks , Sachin Bhat, Electrical & Computer Engineering
Navigation Instruction Validation Tool and Indoor Wayfinding Training System for People with Disabilities , Linlin Ding, Electrical & Computer Engineering
Energy Efficient Loop Unrolling for Low-Cost FPGAs , Naveen Kumar Dumpala, Electrical & Computer Engineering
Effective Denial of Service Attack on Congestion Aware Adaptive Network on Chip , Vijaya Deepak Kadirvel, Electrical & Computer Engineering
VIRTUALIZATION OF CLOSED-LOOP SENSOR NETWORKS , Priyanka Dattatri Kedalagudde, Electrical & Computer Engineering
The Impact of Quantum Size Effects on Thermoelectric Performance in Semiconductor Nanostructures , Adithya Kommini, Electrical & Computer Engineering
MAGNETO-ELECTRIC APPROXIMATE COMPUTATIONAL FRAMEWORK FOR BAYESIAN INFERENCE , Sourabh Kulkarni, Electrical & Computer Engineering
Time Domain SAR Processing with GPUs for Airborne Platforms , Dustin Lagoy, Electrical & Computer Engineering
Query on Knowledge Graphs with Hierarchical Relationships , Kaihua Liu, Electrical & Computer Engineering
HIGH PERFORMANCE SILVER DIFFUSIVE MEMRISTORS FOR FUTURE COMPUTING , Rivu Midya, Electrical & Computer Engineering
Achieving Perfect Location Privacy in Wireless Devices Using Anonymization , Zarrin Montazeri, Electrical & Computer Engineering
KaSI: a Ka-band and S-band Cross-track Interferometer , Gerard Ruiz Carregal, Electrical & Computer Engineering
Analyzing Spark Performance on Spot Instances , Jiannan Tian, Electrical & Computer Engineering
Indoor Navigation For The Blind And Visually Impaired: Validation And Training Methodology Using Virtual Reality , Sili Wang, Electrical & Computer Engineering
Efficient Scaling of a Web Proxy Cluster , Hao Zhang, Electrical & Computer Engineering
ORACLE GUIDED INCREMENTAL SAT SOLVING TO REVERSE ENGINEER CAMOUFLAGED CIRCUITS , Xiangyu Zhang, Electrical & Computer Engineering
Theses from 2016 2016
Seamless Application Delivery Using Software Defined Exchanges , Divyashri Bhat, Electrical & Computer Engineering
PROCESSOR TEMPERATURE AND RELIABILITY ESTIMATION USING ACTIVITY COUNTERS , Mayank Chhablani, Electrical & Computer Engineering
PARQ: A MEMORY-EFFICIENT APPROACH FOR QUERY-LEVEL PARALLELISM , Qianqian Gao, Electrical & Computer Engineering
Accelerated Iterative Algorithms with Asynchronous Accumulative Updates on a Heterogeneous Cluster , Sandesh Gubbi Virupaksha, Electrical & Computer Engineering
Improving Efficiency of Thermoelectric Devices Made of Si-Ge, Si-Sn, Ge-Sn, and Si-Ge-Sn Binary and Ternary Alloys , Seyedeh Nazanin Khatami, Electrical & Computer Engineering
6:1 PUMA Arrays: Designs and Finite Array Effects , Michael Lee, Electrical & Computer Engineering
Protecting Controllers against Denial-of-Service Attacks in Software-Defined Networks , Jingrui Li, Electrical & Computer Engineering
INFRASTRUCTURE-FREE SECURE PAIRING OF MOBILE DEVICES , Chunqiu Liu, Electrical & Computer Engineering
Extrinsic Effects on Heat and Electron Transport In Two-Dimensional Van-Der Waals Materials- A Boltzmann Transport Study , Arnab K. Majee, Electrical & Computer Engineering
SpotLight: An Information Service for the Cloud , Xue Ouyang, Electrical & Computer Engineering
Localization, Visualization And Evacuation Guidance System In Emergency Situations , Jingyan Tang, Electrical & Computer Engineering
Variation Aware Placement for Efficient Key Generation using Physically Unclonable Functions in Reconfigurable Systems , Shrikant S. Vyas, Electrical & Computer Engineering
EVALUATING FEATURES FOR BROAD SPECIES BASED CLASSIFICATION OF BIRD OBSERVATIONS USING DUAL-POLARIZED DOPPLER WEATHER RADAR , Sheila Werth, Electrical & Computer Engineering
Theses from 2015 2015
Quality Factor of Horizontal Wire Dipole Antennas near Planar Conductor or Dielectric Interface , Adebayo Gabriel Adeyemi, Electrical & Computer Engineering
Evaluation of Two-Dimensional Codes for Digital Information Security in Physical Documents , Shuai Chen, Electrical & Computer Engineering
Design and Implementation of a High Performance Network Processor with Dynamic Workload Management , Padmaja Duggisetty, Electrical & Computer Engineering
Wavelet-Based Non-Homogeneous Hidden Markov Chain Model For Hyperspectral Signature Classification , Siwei Feng, Electrical & Computer Engineering
DEVELOPMENT OF INFRARED AND TERAHERTZ BOLOMETERS BASED ON PALLADIUM AND CARBON NANOTUBES USING ROLL TO ROLL PROCESS , Amulya Gullapalli, Electrical & Computer Engineering
Development of Prototypes of a Portable Road Weather Information System , Meha Kainth, Electrical & Computer Engineering
ADACORE: Achieving Energy Efficiency via Adaptive Core Morphing at Runtime , Nithesh Kurella, Electrical & Computer Engineering
Architecting SkyBridge-CMOS , Mingyu Li, Electrical & Computer Engineering
Function Verification of Combinational Arithmetic Circuits , Duo Liu, Electrical & Computer Engineering
ENERGY EFFICIENCY EXPLORATION OF COARSE-GRAIN RECONFIGURABLE ARCHITECTURE WITH EMERGING NONVOLATILE MEMORY , Xiaobin Liu, Electrical & Computer Engineering
Development of a Layout-Level Hardware Obfuscation Tool to Counter Reverse Engineering , Shweta Malik, Electrical & Computer Engineering
Energy Agile Cluster Communication , Muhammad Zain Mustafa, Electrical & Computer Engineering
Architecting NP-Dynamic Skybridge , Jiajun Shi, Electrical & Computer Engineering
Advanced Search
- Notify me via email or RSS
- Collections
- Disciplines
Author Corner
- Login for Faculty Authors
- Faculty Author Gallery
- Expert Gallery
- University Libraries
- Electrical and Computer Engineering Website
- UMass Amherst
This page is sponsored by the University Libraries.
© 2009 University of Massachusetts Amherst • Site Policies
Privacy Copyright
- Browse Works
- Engineering
Computer Engineering
Computer engineering research papers/topics, case-based reasoning system for prediction of fuel consumption by haulage trucks in open–pit mines.
Abstract: The shovel-truck system is commonly used in open-pit mining operations. Truck haulage cost constitutes about 26% of open-pit mining costs as the trucks are mostly powered by diesel whose cost is escalating annually. Therefore, reducing fuel consumption could lead to a significant decrease in overall mining costs. Various methods have been proposed to improve fuel efficiency in open-pit mines. Case-based reasoning (CBR) can be used to estimate fuel consumption by haulage trucks. In ...
Meteorological influence on eLoran accuracy
Abstract: Stringent accuracy requirements need to be met for eLoran deployment in marine navigation and harbour entrance and approach. A good accuracy model is therefore required to predict the positioning accuracy at the user’s receiver locations. Accuracy depends on the variations of additional secondary factors (ASFs) and the primary factor delay. The changes in the air refractive index caused variations in the primary factor (PF) delay of the eLoran signal, and current eLoran accuracy ...
A Model for Providing List of Reliable Providers for Grid Computing
Abstract: Grid computing is an interconnected computer system, where machines share resources that are highly heterogeneous. Reliability is the probability that a process will successfully perform its prescribed task without any failure at a given point of time. Hence, ensuring reliable transactions plays a vital role in grid computing. The main objective of the paper is to develop a reliable and robust two way trust model for the Grid system. Thus the goals of this proposed trust model are ...
Query Processing with Respect to Location in Wireless Broadcasting
Abstract: The wireless communication involves a client server communication i.e. the client needs to send a request for performing a process; it can perform only after the response of the server. Large number of request will result the load balance in the server, which cause process delay. It has been resolved by using wireless broadcast client server communication. To communicate with server the client use fee based cellular type network to achieve a responsible operating range. For avoidin...
A preliminary application of a machine learning model for the prediction of the load variation in three-point bending tests based on acoustic emission signals
Abstract: The load variation during three-point bending (TPB) tests on prismatic Nestos (Greece) marble specimens instrumented by piezoelectric sensors is predicted using acoustic emission (AE) signals. The slope of the cumulative amplitude vs the predicted load curve is potentially useful for determining the forthcoming specimen failure as well as the indirect tensile strength of the material. The optimum artificial neural networks (ANN) model was selected based on a comparison of different...
Enhancing Personalization and Sales Conversion in E-Commerce: The Role of AI in the App Shop Experience
A shopping application that can be easily designed and built using the Flutter framework. “Shop AI” offers customers a good platform and efficient shopping experience in terms of convenience and functionality. this report focusing on the design and development framework. It explores application architecture and shows how Flutter’s versatility helps developers create cross-platform, responsive, and visually appealing user interfaces. Discover the main features of ”Shop AI” by searchi...
Algorithms and Data Structures Part 4: Searching and Sorting (Wikipedia Book 2014)
Searching 1 Search algorithm 1 Linear search 3 Binary search algorithm 6 Sorting 14 Sorting algorithm 14 Bubble sort 25 Quicksort 31 Merge sort 43 Insertion sort 52 Heapsort 59 References Article Sources and Contributors 66 Image Sources, Licenses and Contributors 68
E-Store Project Software Requirements Specification Version <4.0>
Introduction The introduction of the Software Requirements Specification (SRS) provides an overview of the entire SRS with purpose, scope, definitions, acronyms, abbreviations, references and overview of the SRS. The aim of this document is to gather and analyze and give an in-depth insight of the complete Marvel Electronics and Home Entertainment software system by defining the problem statement in detail. Nevertheless, it also concentrates on the capabilities required by stakeholders and...
Skin Cancer Diagnostics with a Smartphone App
Melanoma is one of the deadliest types of skin cancer and can be difficult to treat when it's advanced. To reduce mortality rates, early detection is key. In order to do this, computer-aided systems have been developed to help dermatologists diagnose the condition. To make it more accessible to the public, researchers are working on creating portable, at-home diagnostic systems. An Android-based smartphone application utilizing image capture, preprocessing, and segmentation was developed to e...
Design Control and Monitoring System Of Water Distribution Networks
ABSTRACT Nowadays, water distribution network automation is becoming more and more popular day by day due to its numerous advantages, an internet-based water distribution network system focuses on monitoring and controlling water distribution network instance. Water distribution network face wastage of water due to improper water supply management, non-monitoring in real time, this caused scarcity of water, scarcity of water consider mainly problem in cities. water distribution network auto...
2D Radar Antenna Orientation and Control
ABSTRACT The RADAR system is the first step and much more important and it has much more effect than the other step in the RADAR system works. The RADAR is used in different applications and systems, almost of these applications need high precision, and it's depending on the accuracy of RADAR ANTENNA orientation. Much research has been done and different systems designed to obtain a result within a permissible range. Design RADAR ANTENNA orientation and control system using FPGA and stepper m...
Design and Optimization of W-Tailored Optical Fiber
ABSTRACT This research work studies the temperature effects in W-shaped core refractive index optical fiber. The work designs an optimized W-tailored optical fiber (OWTOF) that checks the effect of rising temperatures in W-tailored optical fiber (WTOF) for better communication. Initially, an introduction to the general concept of optical fibers including tailored optical fibers (TOF), temperature effects and models is presented as a background. This is followed by studies on existing litera...
Design of Digital Image Enhancement System Using Noise Filtering Techniques
ABSTRACT Noise Reduction in digital image is one of the most important and difficult techniques in image research. The aim of Noise Reduction in digital image is to improve the visual appearance of an image, or to provide a better transform representation for another automated image processing. Many images like medical images, satellite images, aerial images and even real-life photographs suffer from viewing, removing blurring and noise, increasing contrast, etc. Reducing noise from the dig...
Design And Implementation Of An Automated Inventory Management System Case Study: Smart Shoppers Masaka
ABSTRACT The general purpose was to develop an efficient Inventory Management System (IMS) that improves service delivery at Smart shoppers’ Masaka. The main objectives were to collect and analyze user requirements that provide the researchers with enough information of what the system users want the system to accomplish, to design an Automated Inventory Management System, to implement a prototype and to test and validate the designed prototype. The methodology used includes Interviews, Que...
Inspired Safari Adventures Official Website
ABSTRACT This project is aimed to work as one of the marketing procedures and cores for Inspired Safari Adventures which acts as a general online website were the all public can view and understand more about the company. The users of this website are generally all the people who want to know about Inspired Safari Adventures in reference to the website components for example understanding the company location activities and so much more as illustrated in the website. The other users include i...
Projects, thesis, seminars, research papers, termpapers topics in Computer Engineering. Computer Engineering projects, thesis, seminars and termpapers topic and materials
Popular Papers/Topics
Building and assembling a computer system, digital combination lock system, design and construction of four-way traffic light, microcontroller based digital code lock, a technical report on student industrial work experience scheme (siwes) on laptop repair, design of a patient heartbeat and temperature monitor using rf, automobile battery preservative, network interconnection devices, smart card technology, design and implementation of a software intercom on lan, design & construction of 8 channel buzzer using microcontroller, appliances control through sms, design and simulation of a secured wireless network (a case study of houdegbe north american university benin), microcontroller based automation system, design and implementation of an internet of things (iot) based smart waste bin for fill level monitoring and biodegradability detection.
Privacy Policy | Refund Policy | Terms | Copyright | © 2024, Afribary Limited. All rights reserved.
150+ Best Engineering Research Topics for Students To Consider
Table of Contents
Engineering is a wide field of study that is divided into various branches such as Civil, Electrical, Mechanical, Electronics, Chemical, etc. Basically, each branch has thousands of engineering research topics to focus on. Hence, when you are asked to prepare an engineering research paper or dissertation for your final year assignments, you might experience difficulties with identifying a perfect topic. But hereafter, you need not worry about topic selection because to make the topic selection process easier for you, here we have suggested some tips for choosing a good engineering research topic. Additionally, we have also shared a list of the best 150+ engineering research paper topics on various specializations. Continue reading this blog to get exclusive ideas for engineering research paper writing.
Engineering Research Paper Topic Selection Tips
When it comes to research in the field of engineering, identifying the best engineering research topic is the first step. So, during that process, in order to identify the right topic, consider the following tips.
- Choose a topic from the research area matching your interest.
- Give preference to a topic that has a large scope to conduct research activities.
- Pick a topic that has several reference materials and evidence supporting your analysis.
- Avoid choosing an already or frequently discussed topic. If the topic is popular, discuss it from a different perspective.
- Never choose a larger topic that is tough to complete before the deadline.
- Finalize the topic only if it satisfies your academic requirements.

List of the Best Engineering Research Topics
Are you searching for the top engineering project ideas? Would you have to complete your academic paper on the best engineering research topic? If yes, then take a look below. Here, we have suggested a few interesting engineering topics in various disciplines that you can consider for your research or dissertation.
Mechanical Engineering Research Topics
- How does the study of robotics benefit from a mechanical engineering background?
- How can a new composite substitute reduce costs in large heat exchangers?
- Which will become the predominant energy technology this century?
- Why structural analysis is considered the foundation of mechanical engineering?
- Why is cast iron used in the engines of large ships?
- What is the finite element approach and why is it essential?
- Why is the flow of fluids important in mechanical engineering?
- What impact does mechanical engineering have in the medical field?
- How do sports incorporate mechanical engineering theories?
- What is the process of thermal heat transfer in machines?
- How can solar panels reduce energy costs in developing countries?
- In what ways is mechanical engineering at the forefront of the field?
- How do various elements interact differently with energy?
- How can companies improve manufacturing through new mechanical theories?
Additional Research Paper Topics on Mechanical Engineering
- Power generation: Extremely low emission technology.
- Rail and wheel wear during the presence of third-body materials.
- Studying the impact of athletic shoe properties on running performance and injuries
- Evaluating teeth decay using patient-specific tools
- Nanotechnology.
- Describe the newly developed methods and applications in Vibration Systems
- Perspective or general Commentaries on the methods and protocols relevant to the research relating to Vibration Systems
- Software-related technology for Visibility of end-to-end operations for employee and management efficiencies
- What should be the best strategies to apply in the planning for consumer demand and responsiveness using data analytics
- Analysis of the monitoring of manufacturing processes using IOT/AI
- Critical analysis of the advancing digital manufacturing with artificial intelligence (AI) and machine learning (ML) Data Analytics
- Pyrolysis and Oxidation for Production and Consumption of Strongly Oxygenated Hydrocarbons as Chemical Energy Carriers: Explain
- Explore the most effective strategies for fatigue-fracture and failure prevention of automotive engines and the importance of such prevention
- Explore the turbomachinery performance and stability enhancement by means of end-wall flow modification
- Production optimization, engine performance, and tribological characteristics of biofuels and their blends in internal combustion engines as alternative fuels: Explain
Civil Engineering Research Topics
- The use of sustainable materials for construction: design and delivery methods.
- State-of-the-art practice for recycling in the construction industry.
- In-depth research on the wastewater treatment process
- Building Information Modelling in the construction industry
- Research to study the impact of sustainability concepts on organizational growth and development.
- The use of warm-mix asphalt in road construction
- Development of sustainable homes making use of renewable energy sources.
- The role of environmental assessment tools in sustainable construction
- Research to study the properties of concrete to achieve sustainability.
- A high-level review of the barriers and drivers for sustainable buildings in developing countries
- Sustainable technologies for the building construction industry
- Research regarding micromechanics of granular materials.
- Research to set up remote sensing applications to assist in the development of sustainable construction techniques.
- Key factors and risk factors associated with the construction of high-rise buildings.
- Use of a single-phase bridge rectifier
- Hydraulic Engineering: A Brief Overview
- Application of GIS techniques for planetary and space exploration
- Reengineering the manufacturing systems for the future.
- Production Planning and Control.
- Project Management.
- Quality Control and Management.
- Reliability and Maintenance Engineering.
Environmental Engineering Research Paper Topics
- Design and development of a system for measuring the carbon index of energy-intensive companies.
- Improving processes to reduce kWh usage.
- How can water conductivity probes help determine water quality and how can water be reused?
- A study of compressor operations on a forging site and mapping operations to identify and remove energy waste.
- A project to set up ways to measure natural gas flow ultrasonically and identify waste areas.
- Developing a compact device to measure energy use for a household.
- What are carbon credits and how can organizations generate them?
- Production of biogas is from organic coral waste.
- Analyzing the impact of the aviation industry on the environment and the potential ways to reduce it.
- How can voltage reduction devices help organizations achieve efficiency in electricity usage?
- What technologies exist to minimize the waste caused by offshore drilling?
- Identify the ways by which efficient control systems using information systems can be introduced to study the energy usage in a machining factory.
- The process mapping techniques to identify bottlenecks for the supply chain industry.
- Process improvement techniques to identify and remove waste in the automotive industry.
- In what ways do green buildings improve the quality of life?
- Discussion on the need to develop green cities to ensure environmental sustainability
- Process of carbon dioxide sequestration, separation, and utilization
- Development of facilities for wastewater treatment

Read more topics: Outstanding Environmental Science Topics for You to Consider
Electrical Engineering Research Topics
- Research to study transformer losses and reduce energy loss.
- How does an ultra-low-power integrated circuit work?
- Setting up a control system to monitor the process usage of compressors.
- Integration of smart metering pulsed outputs with wireless area networks and access to real-time data.
- What are the problems of using semiconductor topology?
- Developing effective strategies and methodical systems for paying as-you-go charging for electric vehicles.
- A detailed review and investigation into the key issues and challenges facing rechargeable lithium batteries.
- Trends and challenges in electric vehicles technologies
- Research to investigate, develop and introduce schemes to ensure efficient energy consumption by electrical machines.
- What is meant by regenerative braking?
- Smart charging of electric vehicles on the motorway
- Research to study metering techniques to control and improve efficiency.
- Develop a scheme to normalize compressor output to kWh.
- Research to introduce smart metering concepts to ensure efficient use of electricity.
- What is the most accurate method of forecasting electric loads?
- Fundamentals of Nanoelectronics
- Use of DC-to-DC converter in DC (Direct Current) power grid
- Development of Microgrid Integration
Electronics and Communications Engineering Research Topics
- Developing the embedded communication system for the national grid to optimize energy usage.
- Improvement of inter-symbol interference in optical communications.
- Defining the boundaries of electrical signals for current electronics systems.
- The limitation of fiber optic communication systems and the possibility of improving their efficiency.
- Gaussian pulse analysis and the improvement of this pulse to reduce errors.
- A study of the various forms of errors and the development of an equalization technique to reduce the error rates in data.
- Realizing the potential of RFID in the improvement of the supply chain.
- Design of high-speed communication circuits that effectively cut down signal noise.
- Radiation in integrated circuits and electronic devices.
- Spectral sensing research for water monitoring applications and frontier science and technology for chemical, biological, and radiological defense.
Computer and Software Engineering Research Topics
- How do businesses benefit from the use of data mining technologies?
- What are the risks of implementing radio-controlled home locks?
- To what extent should humans interact with computer technologies?
- Are financial trading systems operating over the web putting clients at risk?
- What challenges do organizations face with supply chain traceability?
- Do chatbot technologies negatively impact customer service?
- What does the future of computer engineering look like?
- What are the major concepts of software engineering?
- Are fingerprint-based money machines safe to use?
- What are the biggest challenges of using different programming languages?
- The role of risk management in information technology systems of organizations.
- In what ways does MOOD enhancement help software reliability?
- Are fingerprint-based voting systems the way of the future?
- How can one use an AES algorithm for the encryption of images?
- How can biological techniques be applied to software fault detection?
Read more: Creative Capstone Project Ideas For Students
Network and Cybersecurity Engineering Research Topics
- Write about Cybersecurity and malware connection.
- How to detect mobile phone hacking.
- Discuss Network intrusion detection and remedies.
- How to improve network security using attack graph models.
- Explain Modern virus encryption technology.
- Investigate the importance of algorithm encryption.
- Discuss the role of a firewall in securing networks.
- Write about the global cybersecurity strategy.
- Discuss the Privacy and security issues in chatbots.
- Write about Cloud security engineering specifics
Industrial Engineering Research Paper Topics
- The application of lean or Six Sigma in hospitals and services-related industries.
- The use of operation research techniques to reduce cost or improve efficiency.
- Advanced manufacturing techniques like additive manufacturing.
- Innovation as a Complex Adaptive System.
- CAD-based optimization in any manufacturing environment.
- Gap analysis in any manufacturing firm.
- The impact of 3D printing in the manufacturing sector.
- Simulating a real-life manufacturing environment into simulating software
- The rise of design and its use in the developing world.
- Building a network-based methodology to model supply chain systems.
- Risk optimization With P-order comic constraint
- Technology and its impact on mass customization
- How project management becomes more complex with disparate teams and outsourced functions?
- Scheduling problem for health care patients.
Biomedical Engineering Research Ideas
- How does the use of medical imaging help patients with higher risks?
- How can rehabilitation techniques be used to improve a patient’s quality of life?
- In what ways can biomaterials be used to deliver medications more efficiently?
- What impact does medical virtual reality have on a patient’s care?
- What advancements have been made in the field of neural technology?
- How does nanotechnology pave the way for further advancements in this field?
- What is computational biology and how does it impact our lives?
- How accurate are early diagnosis systems in detecting heart diseases?
- What does the future hold for technology-fueled medications?
- What are the guiding principles of biomedical engineering research?
Read more: Top Biology Research Topics for Academic Writing
Chemical Engineering Research Topics
- How can epoxy resins withstand the force generated by a firing gun?
- The use of software affected design aspects in chemical engineering.
- What challenges are there for biochemical engineering to support health?
- The advancements of plastic technology in the last half-century.
- How can chemical technologies be used to diagnose diseases?
- What are the most efficient pathways to the development of biofuels?
- How can charcoal particles be used to filter water in developing countries?
- Increased production of pharmacy drugs in many countries.
- How do complex fluids and polymers create more sustainable machinery?
Miscellaneous Engineering Research Ideas
- Sensing and controlling the intensity of light in LEDs.
- Design and development of a pressure sensor for a solar thermal panel.
- Development of microsensors to measure oil flow rate in tanks.
- How can organizations achieve success by reducing bottlenecks in the supply chain?
- Research to identify efficient logistics operations within a supply chain.
- Developing frameworks for sustainable assessments taking into account eco-engineering measures.
- Research to identify process improvement plans to support business strategies.
- What can engineers do to address the problems with climate change?
- The impact of training on knowledge performance index within the supply chain industry.
- Research to introduce efficiency within information systems and support the timely transfer of knowledge and information.
Final Words
Out of the 150+ engineering research paper topics and ideas suggested in this blog, choose any topic that is convenient for you to conduct research and write about. In case, you have not yet identified a good topic for your engineering research paper, reach out to us immediately. We have numerous PhD-certified experts in various engineering branches to offer help with research paper topic selection, writing, and editing in accordance with your requirements.
Especially, with the support of our scholarly writers, engineering students of all academic levels can complete their assignments on time and achieve the highest possible grades. Furthermore, taking our engineering assignment help would aid you in submitting high-quality and plagiarism-free research papers with proper citations and supporting evidence.

Related Post

220 Amazing Religious Research Paper Topics and Ideas

Read and Understand How to Write a Research Proposal

100+ Controversial Research Topics and Ideas to Focus On
About author.
Jacob Smith
I am an Academic Writer and have affection to share my knowledge through posts’. I do not feel tiredness while research and analyzing the things. Sometime, I write down hundred of research topics as per the students requirements. I want to share solution oriented content to the students.
Leave a Reply Cancel reply
You must be logged in to post a comment.
- Featured Posts
140 Unique Geology Research Topics to Focus On
200+ outstanding world history topics and ideas 2023, 190 excellent ap research topics and ideas, 150+ trending group discussion topics and ideas, 170 funny speech topics to blow the minds of audience, who invented exams learn the history of examination, how to focus on reading 15 effective tips for better concentration, what is a rhetorical analysis essay and how to write it, primary school teacher in australia- eligibility, job role, career options, and salary, 4 steps to build a flawless business letter format, get help instantly.
Raise Your Grades with Assignment Help Pro
- School of Engineering and Applied Sciences >
- Diversity & Inclusion >
- Camps for 6-12 Grade >
- CSExplore Camp >
- Ziarek, Lukasz (Luke)
Lukasz (Luke) Ziarek

Research Topics
Concurrency/parallelism; real-time Java; session types for distributed systems; visual debugging
Contact Information
338E Davis Hall
Buffalo NY, 14260
Phone: (716) 645-1596
Related Links
- PhD, Computer Science, Purdue University, 2011
- BS, Computer Science, University of Chicago, 2003
- IEEE Region One Technological Innovation (Academic) Award, 2023
- President Emeritus and Mrs. Meyerson Award for Distinguished Undergraduate Teaching and Mentoring, 2022
- NSF CAREER Award , 2018
- SEAS Early Career Teacher of the Year , 2016
- Halstead Award for Outstanding Research in Software Engineering, 2009
- Intel Fellowship, 2008
- GAANN Fellowship, 2004

IMAGES
VIDEO
COMMENTS
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on COMPUTER ENGINEERING. Find methods information, sources, references or conduct a literature review on ...
Explore relevant literature, academic papers, online resources, and case studies to gain insights and inspiration. Choose a Project Topic: Based on your research, select a specific topic or area of focus for your project. Take into account your passions, abilities, and the assets at your disposal.
This page provides a comprehensive list of computer science thesis topics, carefully curated to support students in identifying and selecting innovative and relevant areas for their academic research.Whether you are at the beginning of your research journey or are seeking a specific area to explore further, this guide aims to serve as an essential resource.
2022 Computing Engineering Dissertation Topics. Topic 1: An investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility. Research Aim: This study aims to investigate the applications of blockchain within the energy sector.
Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you've landed on this post, chances are you're looking for a computer science-related research topic, but aren't sure where to start.Here, we'll explore a variety of CompSci & IT-related research ideas and topic thought-starters ...
Computer science research topics can be divided into several categories, such as artificial intelligence, big data and data science, human-computer interaction, security and privacy, and software engineering. If you are a student or researcher looking for computer research paper topics. In that case, this article provides some suggestions on ...
Available for single-semester IW and senior thesis advising, 2024-2025. Research Areas: computational complexity, algorithms, applied probability, computability over the real numbers, game theory and mechanism design, information theory. Independent Research Topics: Topics in computational and communication complexity.
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching ...
Computer Science Research Topics. Computer Science Research Topics are as follows: Using machine learning to detect and prevent cyber attacks. Developing algorithms for optimized resource allocation in cloud computing. Investigating the use of blockchain technology for secure and decentralized data storage. Developing intelligent chatbots for ...
Human-centered Cybersecurity Research — Anthropological Findings from Two Longitudinal Studies, Anwesh Tuladhar. PDF. Learning State-Dependent Sensor Measurement Models To Improve Robot Localization Accuracy, Troi André Williams. PDF. Human-centric Cybersecurity Research: From Trapping the Bad Guys to Helping the Good Ones, Armin Ziaie Tabari
Selected full text articles for English-language journals, reports, conference papers, etc., in engineering, acoustics, chemistry, computers, metallurgy, physics, plastics, telecommunications, transportation, waste management, and more. Web of Science. Identifies articles and references from journals in science, the social sciences, and art and ...
These engineering research paper topics offer a unique lens into the intricate dance of DNA manipulation and its far-reaching implications. ... Computer and Software Engineering Research Topic. Computer and software engineering stands at the cutting edge of innovation, constantly evolving to meet the demands of a digital future. ...
Applications of computer science in medicine. Developments in artificial intelligence in image processing. Discuss cryptography and its applications. Discuss methods of ransomware prevention. Applications of Big Data in the banking industry. Challenges of cloud storage services in 2023.
Electrical and Computer Engineering Research Resources: Find Articles & Papers ... journals and magazines, standards and by topic. Also provides links to IEEE standards, IEEE spectrum and other sites. INSPEC. ... Contains full-text papers on optics and photonics from SPIE journals and proceedings published since 1990. Approximately 15,000 new ...
End To End . Predictive Software. The paper examines the principles of the Predictive Software Engineering (PSE) framework. The authors examine how PSE enables custom software development companies to offer transparent services and products while staying within the intended budget and a guaranteed budget.
Computer science ( CS ) majors are in high demand and account for a large part of national computer and information technology job market applicants. Employment in this sector is projected to grow 12% between 2018 and 2028, which is faster than the average of all other occupations. Published data are available on traditional non-computer ...
Top Computer Science Research Topics. Before starting with the research, knowing the trendy research paper ideas for computer science exploration is important. It is not so easy to get your hands on the best research topics for computer science; spend some time and read about the following mind-boggling ideas before selecting one. 1.
This list of computer technology research paper topics provides the list of 33 potential topics for research papers and an overview article on the history of computer technology.. 1. Analog Computers. Paralleling the split between analog and digital computers, in the 1950s the term analog computer was a posteriori projected onto pre-existing classes of mechanical, electrical, and ...
This paper seeks to explore the impact of the computer and technology, as well as the variety of its aspects, on the business world. Apex Computers: Problems of Motivation Among Subordinates. In the process of using intangible incentives, it is necessary to use, first of all, recognition of the merits of employees.
6:1 PUMA Arrays: Designs and Finite Array Effects, Michael Lee, Electrical & Computer Engineering. PDF. Protecting Controllers against Denial-of-Service Attacks in Software-Defined Networks, Jingrui Li, Electrical & Computer Engineering. PDF. INFRASTRUCTURE-FREE SECURE PAIRING OF MOBILE DEVICES, Chunqiu Liu, Electrical & Computer Engineering. PDF
Computer Engineering Research Papers/Topics . Case-based reasoning system for prediction of fuel consumption by haulage trucks in open-pit mines. Abstract: The shovel-truck system is commonly used in open-pit mining operations. Truck haulage cost constitutes about 26% of open-pit mining costs as the trucks are mostly powered by diesel whose ...
Civil Engineering Research Topics. The use of sustainable materials for construction: design and delivery methods. State-of-the-art practice for recycling in the construction industry. In-depth research on the wastewater treatment process. Building Information Modelling in the construction industry.
6/27/23 Biomedical Engineering; 6/1/15 Chemical and Biological Engineering; 3/8/24 Civil, Structural and Environmental Engineering; 9/27/23 Computer Science and Engineering; 3/12/24 Electrical Engineering; 12/22/23 Engineering Education; 4/17/24 Industrial and Systems Engineering; 5/30/23 Materials Design and Innovation; 4/12/24 Mechanical and ...