This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

List Azure role assignments using Azure PowerShell
- 6 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To determine what resources users, groups, service principals, or managed identities have access to, you list their role assignments. This article describes how to list role assignments using Azure PowerShell.
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az .
If your organization has outsourced management functions to a service provider who uses Azure Lighthouse , role assignments authorized by that service provider won't be shown here. Similarly, users in the service provider tenant won't see role assignments for users in a customer's tenant, regardless of the role they've been assigned.
Prerequisites
- PowerShell in Azure Cloud Shell or Azure PowerShell
List role assignments for the current subscription
The easiest way to get a list of all the role assignments in the current subscription (including inherited role assignments from root and management groups) is to use Get-AzRoleAssignment without any parameters.
List role assignments for a subscription
To list all role assignments at a subscription scope, use Get-AzRoleAssignment . To get the subscription ID, you can find it on the Subscriptions blade in the Azure portal or you can use Get-AzSubscription .
List role assignments for a user
To list all the roles that are assigned to a specified user, use Get-AzRoleAssignment .
To list all the roles that are assigned to a specified user and the roles that are assigned to the groups to which the user belongs, use Get-AzRoleAssignment .
List role assignments for a resource group
To list all role assignments at a resource group scope, use Get-AzRoleAssignment .
List role assignments for a management group
To list all role assignments at a management group scope, use Get-AzRoleAssignment . To get the management group ID, you can find it on the Management groups blade in the Azure portal or you can use Get-AzManagementGroup .
List role assignments for a resource
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list.
This following example shows how to list the role assignments for a storage account. Note that this command also lists role assignments at higher scopes, such as resource groups and subscriptions, that apply to this storage account.
If you want to just list role assignments that are assigned directly on a resource, you can use the Where-Object command to filter the list.
List role assignments for classic service administrator and co-administrators
To list role assignments for the classic subscription administrator and co-administrators, use Get-AzRoleAssignment .
List role assignments for a managed identity
Get the object ID of the system-assigned or user-assigned managed identity.
To get the object ID of a user-assigned managed identity, you can use Get-AzADServicePrincipal .
To list the role assignments, use Get-AzRoleAssignment .
- Assign Azure roles using Azure PowerShell
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...
All about Microsoft 365
Generate a report of Azure AD role assignments via the Graph API or PowerShell
A while back, I published a short article and script to illustrate the process of obtaining a list of all Azure AD role assignments. The examples therein use the old MSOnline and Azure AD PowerShell modules, which are now on a deprecation path. Thus, it’s time to update the code to leverage the “latest and greatest”. Quotes are there for a reason…
The updated script comes in two flavors. The first one is based on direct web requests against the Graph API endpoints and uses application permissions, thus is suitable for automation scenarios. Do make sure to replace the authentication variables, which you can find on lines 11-13. Better yet, replace the whole authentication block (lines 7-36) with your preferred “connect to Graph” function. Also make sure that sufficient permissions are granted to the service principal under which you will be running the script. Those include the Directory.Read.All scope for fetching regular role assignments and performing directory-wide queries, and the RoleManagement.Read.Directory for PIM roles.
The second flavor is based on the cmdlets included as part of the Microsoft Graph SDK for PowerShell. As authentication is handled via the Connect-MGGraph cmdlet, the script is half the size of the first one. And it would’ve been even smaller were it not for few annoying bugs Microsoft is yet to address.
In all fairness, switching to the Graph does offer some improvements, such as being able to use a single call to list all role assignments. This is made possible thanks to the /roleManagement/directory/roleAssignments endpoint (or calling the Get-MgRoleManagementDirectoryRoleAssignment cmdlet). Previously, we had to iterate over each admin role and list its members, which is not exactly optimal, and given the fact that the list of built-in roles has now grown to over 90, it does add up. On the negative side, we have a bunch of GUIDs in the output, most of which we will want to translate to human-readable values, as they designate the user, group or service principal to which a given role has been assigned, as well as the actual role. One way to go about this is to use the $expand operator (or the – ExpandProperty parameter if using the SDK) to request the full object.
While this is the quickest method, the lack of support for the $select operator inside an $expand query means we will be fetching a lot more data than what we need for the report. In addition, there seems to be an issue with the definition of the expandable properties for this specific endpoint, as trying to use the handy $expand=* value will result in an error ( “Could not find a property named ‘appScope’ on type ‘Microsoft.DirectoryServices.RoleAssignment'” ). In effect, to fetch both the expanded principal object and the expanded roleDefinition object, we need to run two separate queries and merge the results. Hopefully Microsoft will address this issue in the future (the /roleManagement/directory/roleEligibilitySchedules we will use to fetch PIM eligible role assignments does support $expand=* query).
Another option is to collect all the principalIDs and issue a POST request against the /directoryObjects/getByIds endpoint (or the corresponding Get-MgDirectoryObjectById cmdlet), which does have a proper support for $select . A single query can be used to “translate” up to 1000 principal values, which should be sufficient for most scenarios. With the information gathered from the query, we can construct a hash-table and use it to lookup the property values we want to expose in our report. Lastly, you can also query each principalID individually, but that’s the messiest option available.
Apart from role assignments obtained via the /roleManagement/directory/roleAssignments call, the script can also include any PIM eligible role assignments. To fetch those, invoke the script with the – IncludePIMEligibleAssignments switch. It will then call the /v1.0/roleManagement/directory/roleEligibilitySchedules endpoint, or similarly, use the Get-MgRoleManagementDirectoryRoleEligibilitySchedule cmdlet. Some minor adjustments are needed to ensure the output between the two is uniform, which includes the aforementioned issue with expanding the navigation properties. But hey, it wouldn’t be a Microsoft product if everything worked out of the box 🙂
Here are some examples on how to run the scripts. The first example uses the Graph API version and no parameters. For the second one, we invoke the – IncludePIMEligibleAssignments parameter in order to include PIM eligible role assignments as well. The last example does the same thing, but for the Graph SDK version of the script.
And with that, we’re ready to build the output. Thanks to the $expand operator and the workarounds used above, we should be able to present sufficient information about each role assignment, while minimizing the number of calls made. The output is automatically exported to a CSV in the script folder, and includes the following fields:
- Principal – an identifier for the user, group or service principal to which the role has been assigned. Depending on the object type, an UPN, appID or GUID value will be presented.
- PrincipalDisplayName – the display name for the principal.
- PrincipalType – the object type of the principal.
- AssignedRole – the display name of the role assigned.
- AssignedRoleScope – the assignment scope, either the whole directory (“/”) or a specific administrative unit.
- AssignmentType – the type of assignment (“Permanent” or “Eligible”).
- IsBuiltIn – indicates whether the role is a default one, or custom-created one.
- RoleTemplate – the GUID for the role template.
Now, it’s very important to understand that this script only covers Azure AD admin roles, either default or custom ones, and optionally eligible PIM-assignable roles (do note that the PIM cmdlets/endpoints do not cover all custom role scenarios). Apart from these, there are numerous workload-specific roles that can be granted across Office 365, such as the Exchange Online Roles and assignments, Roles in the Security and Compliance Center, site collection permissions in SharePoint Online, and so on. Just because a given user doesn’t appear in the admin role report, it doesn’t mean that he cannot have other permissions granted!
In addition, one should make sure to cover any applications (service principals) that have been granted permissions to execute operations against your tenant. Such permissions can range from being able to read directory data to full access to user’s messages and files, so it’s very important to keep track on them. We published an article that can get you started with a sample script a while back.
9 thoughts on “ Generate a report of Azure AD role assignments via the Graph API or PowerShell ”
- Pingback: Reporting on Entra ID directory role assignments (including PIM) - Blog
This script is very nicely written, however the output of the Powershell Graph SDK version is incorrect (I didn’t check the other).
If I am eligible to activate a role I’ll be in the eligible list. However once I activate the role, my activated role assignment will show up in the list of role assignments from “Get-MgRoleManagementDirectoryRoleAssignment”. The output of that command doesn’t include a ‘status’ property. Your script assumes that if there’s no ‘status’ then the assignment is permanent, however that’s not accurate. So every eligible user who has activated a role shows up twice in the output of your script – once as as eligible for the role and once as a permanent assignment.
I came across your script because I’m trying to accomplish a similar task. My goal is to enumerate all the users who have eligible or permanent role assignments. I think the answer may be that if a user is in the eligible list, and also in the role assignment list, for the same role, then you can assume that the role assignment came from activation, but that doesn’t really seem very satisfactory.
Thanks Matt. The script is a bit outdated by now, I don’t even know if it runs with the “V2” Graph SDK. I’ll update it at some point 🙂
To further address your comment – neither the Get-MgRoleManagementDirectoryRoleAssignment nor the Get-MgRoleManagementDirectoryRoleEligibilitySchedule cmdlet returns sufficient information in order to determine whether a given (eligible) role assignment is currently activated. You can get this information via Get-MgRoleManagementDirectoryRoleAssignmentScheduleInstance, should be easy enough to add to the next iteration of the script.
Hi, thks for your great work. do you know why i dont see the eligible assignements ?
Seems they made some changes and you can no longer use $expand=* on the /v1.0 endpoint. Try using /beta, should work there. I’ll update the script when I get some time.
I’ve updated the script, let me know if you are still having issues.
Awesome, thank you very much.
Merci merci merci !!! Thanks thanks thanks !!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Building a comprehensive report on Azure AD admin role assignments in Powershell
Keeping an eye on azure ad administrative role assignments is crucial for tenant security and compliance. forget about the built-in pim report in the azure ad portal - take reporting to the next level and build your own report with graph, kql and powershell..
Unassigning inactive roles, verifying that all role holders have registered MFA and are active users, auditing service principals, role-assignable groups and guests with roles, move users from active to eligible roles in PIM ( Privileged Identity Management ), and making sure that no synchronized users have privileged roles are just a few ideas for why you should be reporting on this topic.
In this blogpost I will showcase how to gather data from various sources and compile it all into an actionable status report. Since different tenants have different needs and ways of working, I’m providing examples so that you can write your own custom-tailored script.
The report will list the following records:
- Users with eligible or active Azure AD admin roles - including details on last role activation date, role assignment and expiration dates, MFA status and last sign-in date, admin owner account status etc.
- Service Principals / Applications and Managed Identities with active Azure AD admin roles - including details on last authentication date, tenant ownership, etc.
- Role-assignable groups with eligible or active Azure AD admin roles
Note : Role-assignable groups granted one or more Azure AD admin roles will be listed in the report but users with active or eligible membership to such groups will currently not be listed.
See the Report examples chapter for details.

Prerequisites
Connecting to graph and log analytics, mfa registration details, role assignments, principal last sign-in date, eligible role last activation date, default mfa method and capability, admin account owner, service principal owner organization, report examples, example script.
These Powershell modules are required:
- Graph Powershell SDK
- Azure Powershell
Other prerequisites:
- Global Reader role (or other AAD roles granting enough read-access)
- Admin consent to any required non-consented Graph scopes (read-only) in Graph Powershell SDK.
- Reader-role on the Log Analytics workspace where the Azure AD Sign-in and Audit logs are exported.
Connect to Graph with the Graph Powershell SDK using the required read-only scopes, and select the beta endpoint as required by some of the cmdlets:
Then connect to Azure with the Azure Powershell module, for running KQL queries on the Log Analytics workspace data. Read my Query Azure AD logs with KQL from Powershell blogpost for more information on running KQL queries in Powershell. Update the various parameters according to your environment.
Extracting data
We need to extract data from various sources using Microsoft Graph and KQL queries in Log Analytics.
To report on MFA registration details for Azure AD admin role holders it is likely most efficient to extract all registration details and create a hashtable for quick lookup, depending on the number of users in the tenant.
Assigned roles are active role assignments. This query will also return eligible role assignments which are currently activated through PIM, so we’ll filter those out as they will just be duplicates in the report as they are also listed as eligible roles.
Eligible roles are role assignments requiring activation in PIM.
Then we combine the two assignment types into one array. Use the Select-Object cmdlet to pick out a few records while developing and testing the script.
Now we have all the assignment objects we need in the $allRoleAssignments array, and will process each of those objects in a foreach loop to fetch other necessary data. In the following examples I’ve populated the $roleObject variable with one object from the $allRoleAssignments array.
Since the $allRoleAssignments array may contain both users and Service Principals with active or eligible role assignments, the $roleObject.Principal.AdditionalProperties.'@odata.type property will tell which principal type the current object is - either '#microsoft.graph.user or #microsoft.graph.servicePrincipal . And for Service Principals we can differentiate on types in the $roleObject.Principal.AdditionalProperties.servicePrincipalType property - which is either Application or ManagedIdentity .
The quickest way to get an Azure AD user’s last sign-in date is to query Graph for the user and selecting signInActivity .
For Service Principals we need to query the Azure AD logs in Log Analytics with KQL to fetch the date when the Service Principal last signed in.
KQL query for Service Principal of type Application :
KQL query for Service Principals of type ManagedIdentity :
We also need to fetch the latest date of eligible role activations for users. If $roleObject.AssignmentType equals null and the principal is a user, the following KQL query can help out:
Users with administrative roles and no registered MFA method can be a security risk, depending on tenant configuration and conditional access policies. It’s best to avoid it - while also report on the default type of MFA methods active role assignees have. We already have the $mfaRegistrationDetailsHashmap hashtable and can query it for each processed role where the principal is a user.
If you’re following Microsoft best-practises and separating normal user accounts from administrative roles, you should be having a separate admin account for each user who requires privileged roles and access.
When having separate admin accounts it’s also important to check account status of the admin account owners if possible - to make sure that all admin accounts of terminated employees have been disabled and/or deleted. This query will depend on how you identify admin account owners in your tenant, the following example extracts the owner’s accountName from the UPN and queries Graph for any user with that onPremisesSamAccountName + employeeId .
Service Principals of multi-tenant app registrations can be owned by other Azure AD tenants and consented to in your tenant. It’s important to know about these and understand why they have privileged roles.
If $roleObject.Principal.AdditionalProperties.appOwnerOrganizationId is not null , query Graph for the tenant properties of the owner organization.
$spOwnerOrg.displayName will contain the tenant organization name, and $spOwnerOrg.defaultDomainName the tenant’s default domain’, which can provide a better clue of what the Service Principal is used for and by whom.
Note : Know 100% what you’re doing before removing any privileged roles from Service Principals, especially from Microsoft-owned apps which likely have the roles for a very good reason.
That’s about it, we now have the data necessary to compile an actionable status report on all active and eligible Azure AD role assignments.
Compiling the report
We can now construct a PSCustomObject per role assignment with the collected data.
User with eligible role assignment:
User with active role assignment and owner account details:
Service Principal with role assignment:
Managed Identity with role assignment:
Role-assignable group with role assignment:
In case you need more tips on creating a reporting powershell script for this report, take a look at the example script I’ve published on GitHub .
Thanks for reading!
Be sure to provide any feedback on Twitter or LinkedIn .
- ← Previous Post
- Next Post →
Get-AzRoleAssignment
In this Azure PowerShell article, we will discuss the syntax and usage of the Get-AzRoleAssignment PowerShell cmdlet with a few examples.
Table of Contents
Syntax of Get-AzRoleAssignment
Wrapping up.
Get-AzRoleAssignment is an excellent Azure PowerShell cmdlet that can get you the lists of all the role assignments under your subscription or a specific scope.
Below is the syntax of the Get-AzRoleAssignment Azure PowerShell cmdlet.
Let’s discuss some examples of implementation of the Get-AzRoleAssignment PowerShell command.
You can execute the Azure PowerShell cmdlet below to help you get the list of all the role assignments under my current subscription.
After executing the above PowerShell command, I got the below output.
You can see the output below

You can also use the below Azure PowerShell command to get the list of role assignments under the specified service principal “http://tsinfotechnologies.com”.
Execute the below PowerShell command that can help you to get the list of role assignments under a specified tsinfo website scope.
You may also like following the articles below
- New-AzRoleAssignment
- Get-AzRoleDefinition
- Get-AzResource
In this Azure article, we have discussed the syntax and usage of the Get-AzRoleAssignment Azure PowerShell cmdlet. Thanks for reading this article !!!

I am Rajkishore, and I have over 14 years of experience in Microsoft Azure and AWS, with good experience in Azure Functions, Storage, Virtual Machine, Logic Apps, PowerShell Commands, CLI Commands, Machine Learning, AI, Azure Cognitive Services, DevOps, etc. Not only that, I do have good real-time experience in designing and developing cloud-native data integrations on Azure or AWS, etc. I hope you will learn from these practical Azure tutorials. Read more .

Get PIM Role Assignment Status For Azure AD Using Powershell
If you’re like me and you love to run reports to get valuable information for your tenant and settings, the get PIM role assignment status is the script for you. Recently I was running a report to audit user permissions in Azure AD and realized that my data was off by a bit. I knew some users were added to Privilege Identity Management (PIM) roles but they weren’t showing up in my report.
The reason they weren’t showing up is because I was using the Get-AzureADDirectoryRoleMember cmdlet and that only shows users with current or activated access. If a user was not elevated in PIM, they basically didn’t have access so it skewing my results.
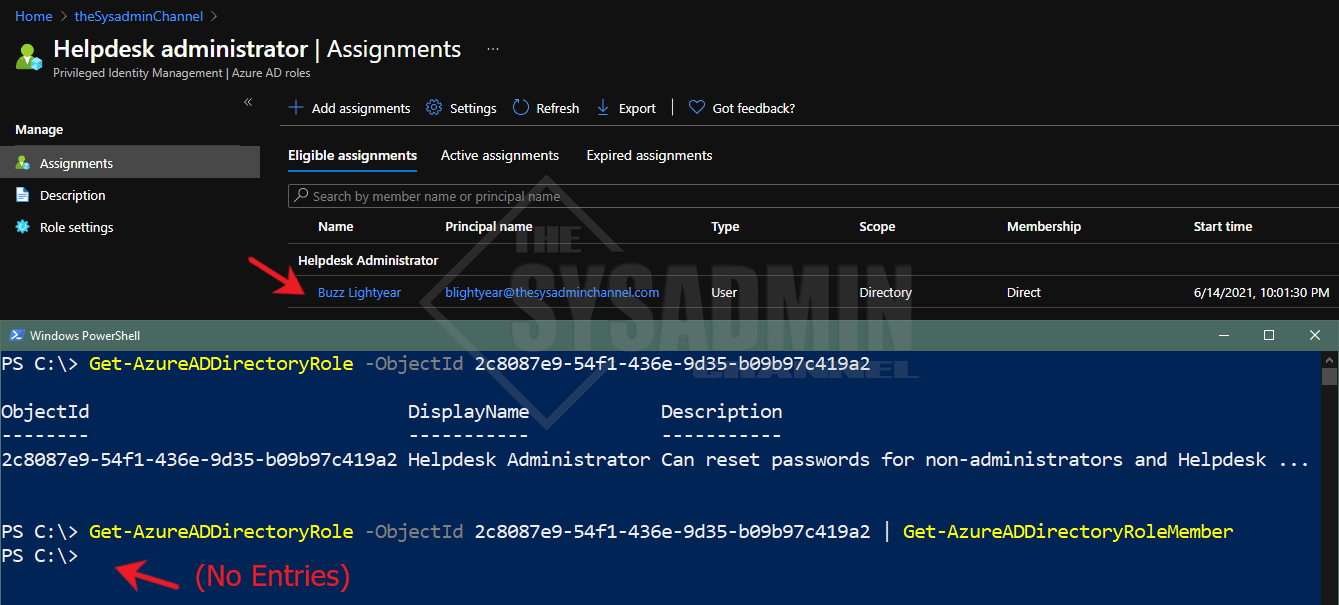
To give you a better idea of what I’m talking about, the above is a sample of the Helpdesk Administrators role. In the Azure AD GUI, the user is added as an eligible role, meaning he can elevate his just in time access. However in Powershell, since the role is not activated, it is not going to display.
Therefore we are going to use the Get-AzureADMSPrivilegedRoleDefinition Azure AD cmdlet to display the list of roles available and the Get-AzureADMSPrivilegedRoleAssignment to filter for the user we’re specifying.
Requirements for this script to work
In order to make this work you’ll need the following:
- AzureADPreview Powershell module .
I want to emphasize the “preview” in the name of the module. Using just the regular AzureAD module is not not going to work so that’s something to keep in mind.
Script Parameters
Userprincipalname.
Specify the UserPrincipalName for the user you want to check roles for.
Specify the RoleName you want to filter for. This will display all PIM roles that are granted directly or through a group.
By default it will use the TenantId from your current session. If you’re connected to a multi-tenant, you can specify the tenant here.
By using this script you’ll be able to see all the people who have standing access as well as PIM eligible roles.
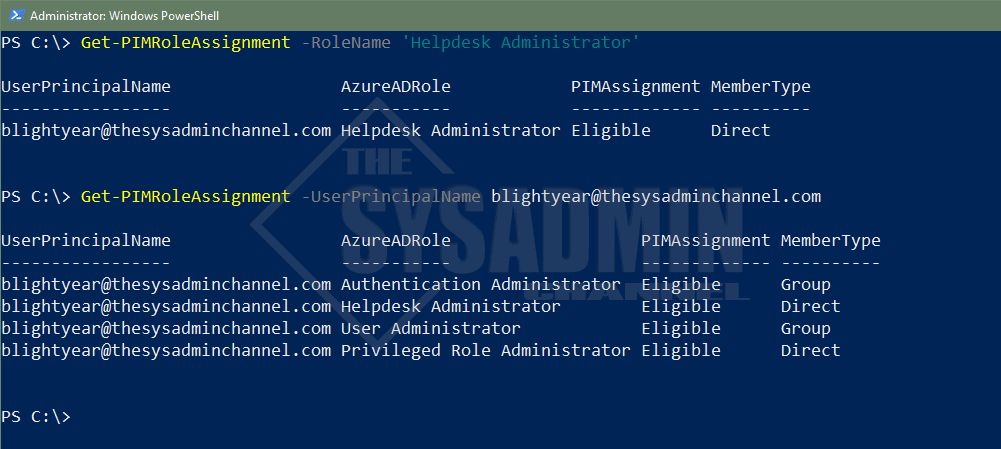
We can now see that the Helpdesk Administrator is now showing up in our output and in the Assignment column it is labeled as Eligible. We’ll also take note that we can see if the member type is added through a group or if it was added directly. This script will support that option.
Get PIM role assignment status for Azure AD using Powershell will now be in your arsenal of cool tips and tricks for your Syadmin role. If you’re interested in more scripts like this, be sure to check out our Powershell Gallery or Azure Content . Finally, be sure to check out our Youtube Channel for any video content.
Paul Contreras
Hi, my name is Paul and I am a Sysadmin who enjoys working on various technologies from Microsoft, VMWare, Cisco and many others. Join me as I document my trials and tribulations of the daily grind of System Administration.
Is there a possibility we could get an updated version of this using Microsoft Graph or Graph API? I cannot find any suitable alternatives now that the azure cmdlets are depreciated.
Yes. I have the script already created, just need to create an article
Could you upload this script, please? This is wonderfull.
See my updated post for the Graph API version. https://thesysadminchannel.com/get-entra-id-pim-role-assignment-using-graph-api/
See my updated post for the Graph API script. https://thesysadminchannel.com/get-entra-id-pim-role-assignment-using-graph-api/
it was a great job but riles are changed and groups extract cannot work
What about a similar Script for Azure resource roles?
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Azure AD - List Role Assignments
Retrieving a list of all Azure AD role assignments sounds easy enough, right? Well, there are some things to consider, here is waht.
Table of Contents
Introduction.
Unfortunately, its not straight forward, to get list of all Azure AD role assignments, unless you are not using Privileged Identity Management (PIM). First, we need the Microsoft Graph PowerShell SDK. Follow these steps . Currently, to retrieve eligible, its required to set the Microsoft Graph profile to beta . Also, those information can only be queried using the Windpws PowerShell.
The gist can either be found here or explained in detail below.
I hope this makes your life a little simpler 😉
- Share on Facebook
- Share on Twitter
- global.share_on_linkedin
- global.share_on_xing

IT Insights Blog
Knowledge Delivered
We are passionate about IT and we are passionate about sharing. The only possible way for us to express our needs is to collect, enrich and share our knowledge and our everyday experiences. This blog contains knowledge from the field and our goal is to provide helpful articles for everyone that comes across a similar problem or just wants to gain some practical knowledge about cloud technologies.
Automatically generate PowerShell Markdown documentation - Part 1
This blog series introduces a PowerShell module that automatically generated MarkDown documentation of your PowerShell Scripts and modules. It also gives an introduction into Abstract Syntax Trees (ASTs) in PowerShell.
Get Server Manager Features from configuration file
Enable wake-on-lan (wol) with powershell.
With every recent Windows 10 update, and they happen a lot, Windows unfortunately also resets the power settings of the network adapters. Since I like to start both my PC and notebook from a remote location or from within the same network, I wrote a little PowerShell function to enable Wake-on-LAN (WoL) again.
Azure Active Directory License Assignment for Groups
The Azure Active Directory has for some time been offering the ability to assign licenses to users such as EMS, Office 365 (Exchange, SharePoint, etc.), but can also provide groups with licenses. As soon as a user is added to a group, if there are still enough licenses available, the user will receive the corresponding license assigned to the group. This works with synchronized groups from the local Active Directory as well as with Azure AD Security and dynamic groups.
Azure DevOps PowerShell Module - Part 1
If you are like me - at least in terms of lazyness - you automate the stuff that you face more than once. Recently, I came accross the reoccuring task of creating Azure DevOps projects with several teams over and over again.
Static Websites with Azure - Static site generators
This blog series explains what static site generators are, why we have chosen a static site generator for our blog, how static sites can be implemented using only Microsoft Azure technologies and when you should consider using them vs. a CMS like WordPress.
Process low level NtSecurityDescriptor
The SECURITY_DESCRIPTOR structure stores security related attributes of an object. It determines, who can access the object and which additional permissions are assigned. Because sometimes you are confronted with the “raw” NtSecurityDescriptor e.g. in Active Directory related scenarios, I tried give an overview about all parts of it.
Exchange hybrid user migration
During an Exchange online migration, some preparations must take plce in advance so users can be migrated easily to the cloud. A typical error in the mailbox migration process occurs because of the mail domain (property: smtp/proxyaddresses) with the message “Target mailbox doesn’t have an smtp proxy”.

Global Azure Bootcamp 2019
Once every year, all the worldwide Azure communities come together to the Global Azure Bootcamp. This year on April 27th it’s the sixth time and we are proud to be part of it the fourth time in a row!
75 posts found

PowerShell Basics: Query Azure Role Based Access Control Assignments
The scenario: what role based access control does somebody have, azure deny assignments.

A great way to learn PowerShell is to set up a scenario in the Azure portal, then try different PowerShell commands to see if you can get the same results. In this article, we'll use Azure Role Based Access control, as it's both visible in the Azure Portal and we have some PowerShell commands for it.
If you're taking over an existing Azure environment, or if you organization has been running Azure for a while without enforced consistency of your Role Based Access Control, you might want to explore your existing RBAC assignments at scale or query the permissions for a specific user. RBAC assignments display in the Access control (IAM) blade of Azure resources, resource groups, subscriptions. Because you can assign a role to a user (or group) on an individual resource, their roles and permissions across your Azure environment may vary, and it's time consuming to check the IAM blade of everything.
Fortunately, we can use PowerShell commands and different display formats, to get the data we want. For the purposes of learning PowerShell, you can use the Azure portal to set up RBAC for different test users (and as part of group memberships) on your resources, resource groups and subscription, so you know what results the PowerShell commands should return.
To keep things simple, I'm running these commands in Cloud Shell inside the Azure Portal.
PowerShell: Get-AzRoleAssignment
Azure RBAC is supported by a number of PowerShell commands, but for this scenario our friend is “ Get-AzRoleAssignment “.
Looking at the structure of PowerShell, because this is a “ Get ” command, it's going to query Azure for some information and return the results to us. “ AzRoleAssignment ” is the base for this command. The command also has a “ New- ” variation, for adding a new assignment, and a “ Remove- ” variation for removing a role assignment.
Note: If you see older blogs or scripts using “Get-AzureRmRoleAssignment”, that was an earlier name for this command before the Az updates. You can often replace the AzureRm bit with just Az, but not in every case as some commands have been deprecated.
If you have multiple subscriptions, Cloud Shell will default to one of them, and your commands will query that subscription and it's associated resources. You can run “ Get-AzContext ” to see which subscription is selected, and run “ Set-AzContext -SubscriptionName “My other subscription”” to change to a different one. (Note I've placed the actual name of my other subscription in it's own set of brackets because it has spaces in it).
Let's start by just running this command and getting a list of all of the RBAC assignments:
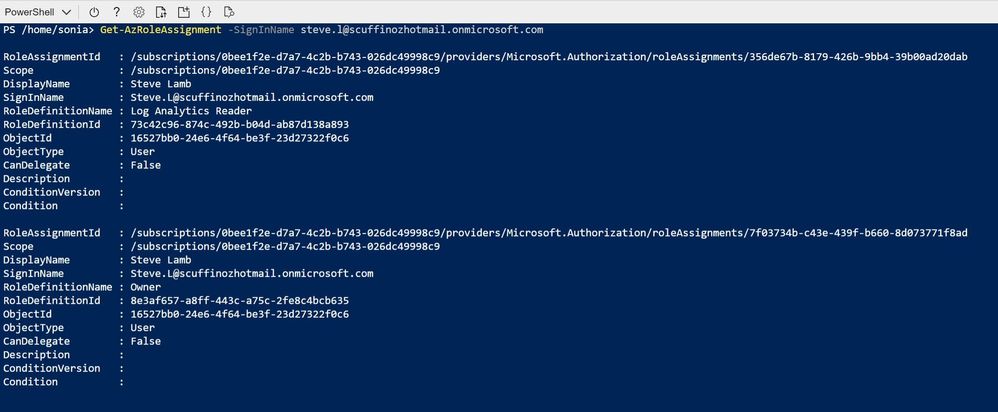
Next, let's narrow that down so we are only looking for role assignments for one particular user. The Get-AzRoleAssignment command has a range of different parameters we can add which will act as a filter. We'll use SignInName , which you can find in the user's details in Azure Active Directory , if you don't know the exact format (and replace my steve.l example name):
This gives us a long list of Steve's role assignments:
Now I want to play with the formatting to make it a little more readable onscreen.
I can format the output of this PowerShell command a few different ways, including as a list or as a table. The output above show sme all of the information that is returned by the query though, so I can use that to further refine the display:
I'm using the ‘pipe' character of | (which is Shift + on my keyboard), then the short version of the “ format-list ” command, then I'm listing just the properties I want to be displayed (DisplayName, RoleDefinitionName and Scope). The pipe tells the first command to send it's output to the second command.

For more formatting command examples, visit Using Format Commands to Change Output View .
Hmm, that could still be a pretty long list if Steve had more role assignments. Let's try a table view instead with “ format-table ” or FT for short:
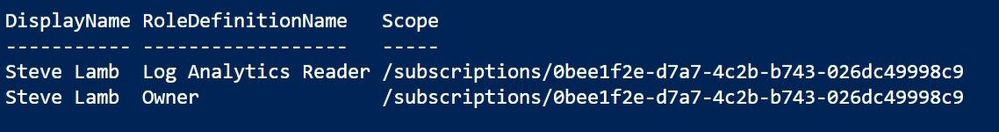
That's better! So, Steve has a pretty high level of access at the top level of my subscription (Owner) plus a Log Analytics Reader role assignment which isn't needed – I can go and tidy that up. But if I run that same command for a different user, I'm seeing a different scope:

Sonia's account is showing the scope as the SCuffSubsMG, not the subscription ID. That's because her Owner access to the current subscription is determined by a role assignment that has been added at the management group level, and as this subscription belongs to that management group, the role assignment is inherited too.
There's one more important thing we need to include – what if our user is a member of a group that has been assigned a role? Our commands so far won't include that. We need to add “ -ExpandPrincipalGroups “.
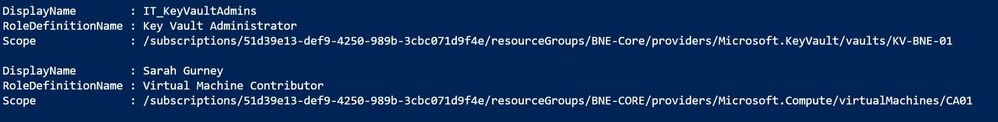
Now I can see that as well as being listed as an individual with the Virtual Machine Contributor role to VM CA01, Sarah is also a member of the IT_KeyVaultAdmins group, who have Key Vault Administrator access to the KV-BNE-01 key vault.
There's one type of Azure role assignment that won't display with Get-AzRoleAssignment, and that's an Azure deny assignment . You can't manually assign someone a deny assignment – they are created and used by Azure to protect system-managed resources. Azure Blueprints and Azure managed apps are the only way that they can be created.
You can query where they are being used in your subscription, by using the Get-AzDenyAssignment command.
Now you've learnt about the capabilities and structure of this command, go and explore with different command parameters. If you get stuck, visit List Azure role assignments using PowerShell or Remove Azure role assignments for more inspiration.
Get-AzRoleAssignment has the full command syntax, parameters, inputs and outputs.
And many of the basic PowerShell concepts we've explored here, like Get/Set/Remove and output formatting, are applicable to a ton of other PowerShell commands too. You're now on your way to understanding and exploring more of PowerShell, especially for scenarios where you can't easily retrieve the same information in the Azure portal.
This article was originally published by Microsoft's SQL Server Blog . You can find the original article here .
Related Posts
- What's the difference between Azure AD Graph, Azure Resource Graph and Microsoft Graph?
- Using Azure Automation with Multiple Tenants
- Unlocking Azure Secrets: Using Identities for Key Vault Access
- Tracking the Source of ADFS Account Lockouts
- Threat matrix for storage

COMMENTS
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list. Azure PowerShell.
Navigate to the resource/resource group/subscription in the portal -> Access control (IAM) -> Role assignments, you can filter with the parameters you want. Or you can use the Azure powershell Get-AzRoleAssignment or REST API, it depends on your requirement. Sample: 1.You have a list of ObjectIds of the users, you can use the script as below.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
A while back, I published a short article and script to illustrate the process of obtaining a list of all Azure AD role assignments. The examples therein use the old MSOnline and Azure AD PowerShell modules, which are now on a deprecation path. Thus, it's time to update the code to leverage the "latest and greatest".
Role assignments. Assigned roles are active role assignments. This query will also return eligible role assignments which are currently activated through PIM, so we'll filter those out as they will just be duplicates in the report as they are also listed as eligible roles. # Get assigned role assignments Write-Host -ForegroundColor Yellow ...
Get-AzRoleAssignment -ServicePrincipalName <String> Get-AzRoleAssignment -Scope . Let's discuss some examples of implementation of the Get-AzRoleAssignment PowerShell command. Example-1: You can execute the Azure PowerShell cmdlet below to help you get the list of all the role assignments under my current subscription. Get-AzRoleAssignment
If you're like me and you love to run reports to get valuable information for your tenant and settings, the get PIM role assignment status is the script for you. Recently I was running a report to audit user permissions in Azure AD and realized that my data was off by a bit. I knew some users were added to Privilege Identity Management (PIM ...
Unfortunately, its not straight forward, to get list of all Azure AD role assignments, unless you are not using Privileged Identity Management (PIM). First, we need the Microsoft Graph PowerShell SDK. Follow these steps. Currently, to retrieve eligible, its required to set the Microsoft Graph profile to beta. Also, those information can only be ...
1. Usually we use the Get-AzRoleAssignment command to list all the role assignments that are valid on the scope. If no parameters are specified, this command will return all the role assignments made under the subscription. For your problem, you want to use a security group to filter this list, just use the Azure AD group ObjectId parameter:
Get-AzRoleAssignment with ExpandPrincipalGroups for group membership role assignments. Now I can see that as well as being listed as an individual with the Virtual Machine Contributor role to VM CA01, Sarah is also a member of the IT_KeyVaultAdmins group, who have Key Vault Administrator access to the KV-BNE-01 key vault.. Azure deny assignments
The above process will add your role assignment to a particular group, and you can also add or remove members from the group to grant or revoke access to resources. Reference: Assign Azure roles using Azure PowerShell - Azure RBAC | Microsoft Learn
As announced at Microsoft Secure last month, Copilot for Security is now available for purchase as of April 1, 2024. Customers can get started by provisioning capacity to run all Copilot workloads, both for standalone and for those embedded in our security products beginning with Microsoft Defender XDR. With a flexible, consumption-based ...
Based on your requirement you can change the scope and add the filter to get the role assignments. Refer the below MsDoc: List Azure role assignments using the REST API - Azure RBAC. Currently it is not feasible to retrieve the role assignments via Azure Resource Graph. Alternatively, you can make use of Azure PowerShell or Azure CLI.
Unfortunately, there is no roleDefinitionName and principalName in the Role Assignments - List REST API response. For 'principalName' we could use Service Principals - Get REST API to get it. The objectId value is the principalId that you get from Role Assignments - List REST API. Update2:
I can use the following to get all roles assigned to a given client application: var graphClient = new GraphServiceClient(new DefaultAzureCredential()); var assignments = graphClient.ServicePrincipals[<client-application-id>].AppRoleAssignments.GetAsync().Result;