IEEE Account
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

Search form
Review of computer engineering studies.

- ISSN: 2369-0755 (print); 2369-0763 (online)
- Indexing & Archiving: EBSCOhost Cabell's Directory Publons ScienceOpen Google Scholar Index Copernicus CrossRef Portico Microsoft Academic CNKI Scholar Baidu Scholar
- Subject: Computer Sciences Engineering
Review of Computer Engineering Studies (RCES) is an international, scholarly and peer-reviewed journal dedicated to providing scientists, engineers and technicians with the latest developments on computer science. The journal offers a window into the most recent discoveries in four categories, namely, computing (computing theory, scientific computing, cloud computing, high-performance computing, numerical and symbolic computing), system (database systems, real-time systems, operating systems, warning systems, decision support systems, information processes and systems, systems integration), intelligence (robotics, bio-informatics, web intelligence, artificial intelligence), and application (security, networking, software engineering, pattern recognition, e-science and e-commerce, signal and image processing, control theory and applications). The editorial board welcomes original, substantiated papers on the above topics, which could provoke new science interest and benefit those devoted to computer science. The journal is published quarterly by the IIETA.
The RCES is an open access journal. All contents are available for free, that is, users are entitled to read, download, duplicate, distribute, print, search or link to the full texts of the articles in this journal without prior consent from the publisher or the author.
Focus and Scope
The RCES welcomes original research papers, technical notes and review articles on the following disciplines:
- Computing theory
- Scientific computing
- Cloud computing
- High-performance computing
- Numerical and symbolic computing
- Database systems
- Real-time systems
- Operating systems
- Warning systems
- Decision support systems
- Information processes and systems
- Systems integration
- Bio-informatics
- Web intelligence
- Artificial intelligence
- Software engineering
- Pattern recognition
- E-science and e-commerce
- Signal and image processing
- Control theory and applications
Publication Frequency
The RCES is published quarterly by the IIETA, with four regular issues (excluding special issues) and one volume per year.
Peer Review Statement
The IIETA adopts a double blind review process. Once submitted, a paper dealing with suitable topics will be sent to the editor-in-chief or managing editor, and then be reviewed by at least two experts in the relevant field. The reviewers are either members of our editorial board or special external experts invited by the journal. In light of the reviewers’ comments, the editor-in-chief or managing editor will make the final decision over the publication, and return the decision to the author.
There are four possible decisions concerning the paper: acceptance, minor revision, major revision and rejection. Acceptances means the paper will be published directly without any revision. Minor revision means the author should make minor changes to the manuscript according to reviewers’ comments and submit the revised version to the IIETA. The revised version will be accepted or rejected at the discretion of the editor-in-chief or managing editor. Major revision means the author should modify the manuscript significantly according to reviewers’ comments and submit the revised version to the IIETA. The revised version will be accepted or rejected at the discretion of the editor-in-chief or managing editor. Rejection means the submitted paper will not be published.
If a paper is accepted, the editor-in-chief or managing editor will send an acceptance letter to the author, and ask the author to prepare the paper in MS Word using the template of IIETA.
Plagiarism Policy
Plagiarism is committed when one author uses another work without permission, credit, or acknowledgment. Plagiarism takes different forms, from literal copying to paraphrasing the work of another. The IIETA uses CrossRef to screen for unoriginal material. Authors submitting to an IIETA journal should be aware that their paper may be submitted to CrossRef at any point during the peer-review or production process. Any allegations of plagiarism made to a journal will be investigated by the editor-in-chief or managing editor. If the allegations appear to be founded, we will request all named authors of the paper to give an explanation of the overlapping material. If the explanation is not satisfactory, we will reject the submission, and may also reject future submissions.
For instructions on citing any of IIETA’s journals as well as our Ethics Statement , see Policies and Standards .
Indexing Information
Web: https://www.portico.org/
- Index Copernicus
Web: http://journals.indexcopernicus.com
- Google Scholar
Web: http://scholar.google.com
- CNKI Scholar
Web: http://scholar.cnki.net
Included in
- Crossref.org
Web: https://www.crossref.org/
ISSN: 2369-0755 (print); 2369-0763 (online)
For Submission Inquiry
Email: [email protected]

- Just Published
- Featured Articles
- Most Read and Cited
- Winters’ Multiplicative Model Based Analysis of the Development and Prospects of New Energy Electric Vehicles in China Zhishuo Jin, Yubing Qian
- Agent-based Analysis and Simulation of Online Shopping Behavior in the Context of Online Promotion Xiaoyi Deng
- Study of Two Kinds of Analysis Methods of Intrusion Tolerance System State Transition Model Zhiyong Luo, Xu Yang, Guanglu Sun, Zhiqiang Xie
- A Review on Automated Billing for Smart Shopping System Using IOT Priyanka S. Sahare, Anup Gade, Jayant Rohankar
- A Review on Automated Billing for Smart Shopping System Using IOT Priyanka S. Sahare, Anup Gade, Jayant Rohank
- Algorithm Research on the Analysis of College Student Score Jinxin Ma, Limin Cui
Phone: + 1 825 436 9306
Email: [email protected]
Subscription
Language support
Please sign up to receive notifications on new issues and newsletters from IIETA
Select Journal/Journals:
Copyright © 2024 IIETA. All Rights Reserved.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Computer science articles from across Nature Portfolio
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching large volumes of information or encrypting data so that it can be stored and transmitted securely.
Latest Research and Reviews
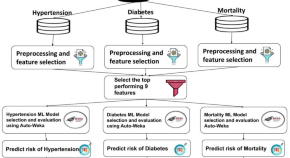
FIT calculator: a multi-risk prediction framework for medical outcomes using cardiorespiratory fitness data
- Radwa Elshawi
- Sherif Sakr
- Jonathan K. Ehrman
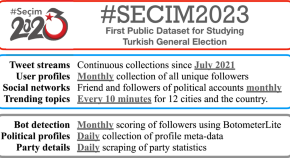
First public dataset to study 2023 Turkish general election
- Nihat Mugurtay
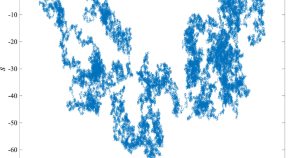
Exploiting high-quality reconstruction image encryption strategy by optimized orthogonal compressive sensing
- Lincheng Yang
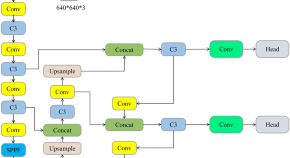
Helmet wearing detection algorithm based on improved YOLOv5
- Benchi Jiang
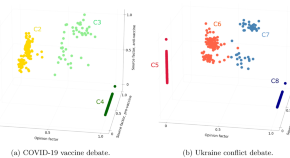
Gaining a better understanding of online polarization by approaching it as a dynamic process
- Célina Treuillier
- Sylvain Castagnos
- Armelle Brun
Plant disease recognition using residual convolutional enlightened Swin transformer networks
- Ponugoti Kalpana
- Laith Abualigah
News and Comment

AI now beats humans at basic tasks — new benchmarks are needed, says major report
Stanford University’s 2024 AI Index charts the meteoric rise of artificial-intelligence tools.
- Nicola Jones
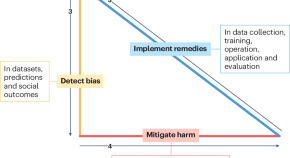
Medical artificial intelligence should do no harm
Bias and distrust in medicine have been perpetuated by the misuse of medical equations, algorithms and devices. Artificial intelligence (AI) can exacerbate these problems. However, AI also has potential to detect, mitigate and remedy the harmful effects of bias to build trust and improve healthcare for everyone.
- Melanie E. Moses
- Sonia M. Gipson Rankin

AI hears hidden X factor in zebra finch love songs
Machine learning detects song differences too subtle for humans to hear, and physicists harness the computing power of the strange skyrmion.
- Nick Petrić Howe
- Benjamin Thompson
Three reasons why AI doesn’t model human language
- Johan J. Bolhuis
- Stephen Crain
- Andrea Moro

Generative artificial intelligence in chemical engineering
Generative artificial intelligence will transform the way we design and operate chemical processes, argues Artur M. Schweidtmann.
- Artur M. Schweidtmann

Why scientists trust AI too much — and what to do about it
Some researchers see superhuman qualities in artificial intelligence. All scientists need to be alert to the risks this creates.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Help | Advanced Search
Computer Science > Artificial Intelligence
Title: designqa: a multimodal benchmark for evaluating large language models' understanding of engineering documentation.
Abstract: This research introduces DesignQA, a novel benchmark aimed at evaluating the proficiency of multimodal large language models (MLLMs) in comprehending and applying engineering requirements in technical documentation. Developed with a focus on real-world engineering challenges, DesignQA uniquely combines multimodal data-including textual design requirements, CAD images, and engineering drawings-derived from the Formula SAE student competition. Different from many existing MLLM benchmarks, DesignQA contains document-grounded visual questions where the input image and input document come from different sources. The benchmark features automatic evaluation metrics and is divided into segments-Rule Comprehension, Rule Compliance, and Rule Extraction-based on tasks that engineers perform when designing according to requirements. We evaluate state-of-the-art models like GPT4 and LLaVA against the benchmark, and our study uncovers the existing gaps in MLLMs' abilities to interpret complex engineering documentation. Key findings suggest that while MLLMs demonstrate potential in navigating technical documents, substantial limitations exist, particularly in accurately extracting and applying detailed requirements to engineering designs. This benchmark sets a foundation for future advancements in AI-supported engineering design processes. DesignQA is publicly available at: this https URL .
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .

- USF Research
- USF Libraries
Digital Commons @ USF > College of Engineering > Computer Science and Engineering > Theses and Dissertations
Computer Science and Engineering Theses and Dissertations
Theses/dissertations from 2023 2023.
Refining the Machine Learning Pipeline for US-based Public Transit Systems , Jennifer Adorno
Insect Classification and Explainability from Image Data via Deep Learning Techniques , Tanvir Hossain Bhuiyan
Brain-Inspired Spatio-Temporal Learning with Application to Robotics , Thiago André Ferreira Medeiros
Evaluating Methods for Improving DNN Robustness Against Adversarial Attacks , Laureano Griffin
Analyzing Multi-Robot Leader-Follower Formations in Obstacle-Laden Environments , Zachary J. Hinnen
Secure Lightweight Cryptographic Hardware Constructions for Deeply Embedded Systems , Jasmin Kaur
A Psychometric Analysis of Natural Language Inference Using Transformer Language Models , Antonio Laverghetta Jr.
Graph Analysis on Social Networks , Shen Lu
Deep Learning-based Automatic Stereology for High- and Low-magnification Images , Hunter Morera
Deciphering Trends and Tactics: Data-driven Techniques for Forecasting Information Spread and Detecting Coordinated Campaigns in Social Media , Kin Wai Ng Lugo
Automated Approaches to Enable Innovative Civic Applications from Citizen Generated Imagery , Hye Seon Yi
Theses/Dissertations from 2022 2022
Towards High Performing and Reliable Deep Convolutional Neural Network Models for Typically Limited Medical Imaging Datasets , Kaoutar Ben Ahmed
Task Progress Assessment and Monitoring Using Self-Supervised Learning , Sainath Reddy Bobbala
Towards More Task-Generalized and Explainable AI Through Psychometrics , Alec Braynen
A Multiple Input Multiple Output Framework for the Automatic Optical Fractionator-based Cell Counting in Z-Stacks Using Deep Learning , Palak Dave
On the Reliability of Wearable Sensors for Assessing Movement Disorder-Related Gait Quality and Imbalance: A Case Study of Multiple Sclerosis , Steven Díaz Hernández
Securing Critical Cyber Infrastructures and Functionalities via Machine Learning Empowered Strategies , Tao Hou
Social Media Time Series Forecasting and User-Level Activity Prediction with Gradient Boosting, Deep Learning, and Data Augmentation , Fred Mubang
A Study of Deep Learning Silhouette Extractors for Gait Recognition , Sneha Oladhri
Analyzing Decision-making in Robot Soccer for Attacking Behaviors , Justin Rodney
Generative Spatio-Temporal and Multimodal Analysis of Neonatal Pain , Md Sirajus Salekin
Secure Hardware Constructions for Fault Detection of Lattice-based Post-quantum Cryptosystems , Ausmita Sarker
Adaptive Multi-scale Place Cell Representations and Replay for Spatial Navigation and Learning in Autonomous Robots , Pablo Scleidorovich
Predicting the Number of Objects in a Robotic Grasp , Utkarsh Tamrakar
Humanoid Robot Motion Control for Ramps and Stairs , Tommy Truong
Preventing Variadic Function Attacks Through Argument Width Counting , Brennan Ward
Theses/Dissertations from 2021 2021
Knowledge Extraction and Inference Based on Visual Understanding of Cooking Contents , Ahmad Babaeian Babaeian Jelodar
Efficient Post-Quantum and Compact Cryptographic Constructions for the Internet of Things , Rouzbeh Behnia
Efficient Hardware Constructions for Error Detection of Post-Quantum Cryptographic Schemes , Alvaro Cintas Canto
Using Hyper-Dimensional Spanning Trees to Improve Structure Preservation During Dimensionality Reduction , Curtis Thomas Davis
Design, Deployment, and Validation of Computer Vision Techniques for Societal Scale Applications , Arup Kanti Dey
AffectiveTDA: Using Topological Data Analysis to Improve Analysis and Explainability in Affective Computing , Hamza Elhamdadi
Automatic Detection of Vehicles in Satellite Images for Economic Monitoring , Cole Hill
Analysis of Contextual Emotions Using Multimodal Data , Saurabh Hinduja
Data-driven Studies on Social Networks: Privacy and Simulation , Yasanka Sameera Horawalavithana
Automated Identification of Stages in Gonotrophic Cycle of Mosquitoes Using Computer Vision Techniques , Sherzod Kariev
Exploring the Use of Neural Transformers for Psycholinguistics , Antonio Laverghetta Jr.
Secure VLSI Hardware Design Against Intellectual Property (IP) Theft and Cryptographic Vulnerabilities , Matthew Dean Lewandowski
Turkic Interlingua: A Case Study of Machine Translation in Low-resource Languages , Jamshidbek Mirzakhalov
Automated Wound Segmentation and Dimension Measurement Using RGB-D Image , Chih-Yun Pai
Constructing Frameworks for Task-Optimized Visualizations , Ghulam Jilani Abdul Rahim Quadri
Trilateration-Based Localization in Known Environments with Object Detection , Valeria M. Salas Pacheco
Recognizing Patterns from Vital Signs Using Spectrograms , Sidharth Srivatsav Sribhashyam
Recognizing Emotion in the Wild Using Multimodal Data , Shivam Srivastava
A Modular Framework for Multi-Rotor Unmanned Aerial Vehicles for Military Operations , Dante Tezza
Human-centered Cybersecurity Research — Anthropological Findings from Two Longitudinal Studies , Anwesh Tuladhar
Learning State-Dependent Sensor Measurement Models To Improve Robot Localization Accuracy , Troi André Williams
Human-centric Cybersecurity Research: From Trapping the Bad Guys to Helping the Good Ones , Armin Ziaie Tabari
Theses/Dissertations from 2020 2020
Classifying Emotions with EEG and Peripheral Physiological Data Using 1D Convolutional Long Short-Term Memory Neural Network , Rupal Agarwal
Keyless Anti-Jamming Communication via Randomized DSSS , Ahmad Alagil
Active Deep Learning Method to Automate Unbiased Stereology Cell Counting , Saeed Alahmari
Composition of Atomic-Obligation Security Policies , Yan Cao Albright
Action Recognition Using the Motion Taxonomy , Maxat Alibayev
Sentiment Analysis in Peer Review , Zachariah J. Beasley
Spatial Heterogeneity Utilization in CT Images for Lung Nodule Classication , Dmitrii Cherezov
Feature Selection Via Random Subsets Of Uncorrelated Features , Long Kim Dang
Unifying Security Policy Enforcement: Theory and Practice , Shamaria Engram
PsiDB: A Framework for Batched Query Processing and Optimization , Mehrad Eslami
Composition of Atomic-Obligation Security Policies , Danielle Ferguson
Algorithms To Profile Driver Behavior From Zero-permission Embedded Sensors , Bharti Goel
The Efficiency and Accuracy of YOLO for Neonate Face Detection in the Clinical Setting , Jacqueline Hausmann
Beyond the Hype: Challenges of Neural Networks as Applied to Social Networks , Anthony Hernandez
Privacy-Preserving and Functional Information Systems , Thang Hoang
Managing Off-Grid Power Use for Solar Fueled Residences with Smart Appliances, Prices-to-Devices and IoT , Donnelle L. January
Novel Bit-Sliced In-Memory Computing Based VLSI Architecture for Fast Sobel Edge Detection in IoT Edge Devices , Rajeev Joshi
Edge Computing for Deep Learning-Based Distributed Real-time Object Detection on IoT Constrained Platforms at Low Frame Rate , Lakshmikavya Kalyanam
Establishing Topological Data Analysis: A Comparison of Visualization Techniques , Tanmay J. Kotha
Machine Learning for the Internet of Things: Applications, Implementation, and Security , Vishalini Laguduva Ramnath
System Support of Concurrent Database Query Processing on a GPU , Hao Li
Deep Learning Predictive Modeling with Data Challenges (Small, Big, or Imbalanced) , Renhao Liu
Countermeasures Against Various Network Attacks Using Machine Learning Methods , Yi Li
Towards Safe Power Oversubscription and Energy Efficiency of Data Centers , Sulav Malla
Design of Support Measures for Counting Frequent Patterns in Graphs , Jinghan Meng
Automating the Classification of Mosquito Specimens Using Image Processing Techniques , Mona Minakshi
Models of Secure Software Enforcement and Development , Hernan M. Palombo
Functional Object-Oriented Network: A Knowledge Representation for Service Robotics , David Andrés Paulius Ramos
Lung Nodule Malignancy Prediction from Computed Tomography Images Using Deep Learning , Rahul Paul
Algorithms and Framework for Computing 2-body Statistics on Graphics Processing Units , Napath Pitaksirianan
Efficient Viewshed Computation Algorithms On GPUs and CPUs , Faisal F. Qarah
Relational Joins on GPUs for In-Memory Database Query Processing , Ran Rui
Micro-architectural Countermeasures for Control Flow and Misspeculation Based Software Attacks , Love Kumar Sah
Efficient Forward-Secure and Compact Signatures for the Internet of Things (IoT) , Efe Ulas Akay Seyitoglu
Detecting Symptoms of Chronic Obstructive Pulmonary Disease and Congestive Heart Failure via Cough and Wheezing Sounds Using Smart-Phones and Machine Learning , Anthony Windmon
Toward Culturally Relevant Emotion Detection Using Physiological Signals , Khadija Zanna
Theses/Dissertations from 2019 2019
Beyond Labels and Captions: Contextualizing Grounded Semantics for Explainable Visual Interpretation , Sathyanarayanan Narasimhan Aakur
Empirical Analysis of a Cybersecurity Scoring System , Jaleel Ahmed
Phenomena of Social Dynamics in Online Games , Essa Alhazmi
A Machine Learning Approach to Predicting Community Engagement on Social Media During Disasters , Adel Alshehri
Interactive Fitness Domains in Competitive Coevolutionary Algorithm , ATM Golam Bari
Measuring Influence Across Social Media Platforms: Empirical Analysis Using Symbolic Transfer Entropy , Abhishek Bhattacharjee
A Communication-Centric Framework for Post-Silicon System-on-chip Integration Debug , Yuting Cao
Authentication and SQL-Injection Prevention Techniques in Web Applications , Cagri Cetin
Multimodal Emotion Recognition Using 3D Facial Landmarks, Action Units, and Physiological Data , Diego Fabiano
Robotic Motion Generation by Using Spatial-Temporal Patterns from Human Demonstrations , Yongqiang Huang
A GPU-Based Framework for Parallel Spatial Indexing and Query Processing , Zhila Nouri Lewis
A Flexible, Natural Deduction, Automated Reasoner for Quick Deployment of Non-Classical Logic , Trisha Mukhopadhyay
An Efficient Run-time CFI Check for Embedded Processors to Detect and Prevent Control Flow Based Attacks , Srivarsha Polnati
Force Feedback and Intelligent Workspace Selection for Legged Locomotion Over Uneven Terrain , John Rippetoe
Detecting Digitally Forged Faces in Online Videos , Neilesh Sambhu
Malicious Manipulation in Service-Oriented Network, Software, and Mobile Systems: Threats and Defenses , Dakun Shen
Advanced Search
- Email Notifications and RSS
- All Collections
- USF Faculty Publications
- Open Access Journals
- Conferences and Events
- Theses and Dissertations
- Textbooks Collection
Useful Links
- Rights Information
- SelectedWorks
- Submit Research
Home | About | Help | My Account | Accessibility Statement | Language and Diversity Statements
Privacy Copyright
Open Access. Powered by Scholars. Published by Universities. ®

- Digital Commons Network ™
- / Engineering
Computer Engineering Commons ™

Popular Articles
Based on downloads in June 2023
Introduction To Mips Assembly Language Programming , Charles W. Kann Gettysburg College
Introduction To Mips Assembly Language Programming , Charles W. Kann
Open educational resources.
This book was written to introduce students to assembly language programming in MIPS. As with all assembly language programming texts, it covers basic operators and instructions, subprogram calling, loading and storing memory, program control, and the conversion of the assembly language program into machine code.
However this book was not written simply as a book on assembly language programming. The larger purpose of this text is to show how concepts in Higher Level Languages (HLL), such as Java or C/C++, are represented in assembly. By showing how program constructs from these HLL map into assembly, the concepts will be easier …
Go to article
The Perceived Business Benefit Of Cloud Computing: An Exploratory Study , Thomas Chen, Ta-Tao Chuang, Kazuo Nakatani Global ECommerce Service, Inc
The Perceived Business Benefit Of Cloud Computing: An Exploratory Study , Thomas Chen, Ta-Tao Chuang, Kazuo Nakatani
Journal of international technology and information management.
The objective of the research is to study the benefits of cloud computing perceived by adopters and examine the impact of moderating factors on the relationship between the type of cloud computing and the perceived benefit. The moderating factors include firm size and value-chain activities. A measurement instrument of a 5-point Likert scale was administered on businesses of different sizes in Taiwan. The benefit of cloud computing measured in the study were: cost reduction, improved capability and enhanced scalability. The results show that the perceived benefit of cloud computing varies depending on the type of cloud computing, the value chain …
The Effects Of Computer And Information Technology On Education , Iwasan D. Kejawa Ed.D University of Nebraska - Lincoln
The Effects Of Computer And Information Technology On Education , Iwasan D. Kejawa Ed.D
School of computing: faculty publications.
In the society of ours, is it true really that computers and information technology have contributed immensely to the way we learn? After observing and reading various educational paraphernalia and scanning the environment research has shown that the educational systems have greatly been impacted by computers and information technology. With the growth of technology, the ways we learn have been improved tremendously. Innovative technologies have contributed to the innovation of learning in the education arena and outside. The traditional ways of conveying instructions to learners have been augmented with the use of computers information technologies. The educational system of our …
Computer Network Design For Universities In Developing Countries , Rafid Salih Sarhan AlSarhan Valparaiso University
Computer Network Design For Universities In Developing Countries , Rafid Salih Sarhan Alsarhan
Information technology capstone research project reports.
The purpose of this project is to design a suitable network system for universities in developing countries. The aim was to design a network with high-quality security and low cost, in such a way that network devices of universities in developing countries, will meet standards associated with the universities in developed countries. This project will help to enhance education in developing countries. There are many devices that were used in designing the network, such as routers, switches, backup, firewall, and servers. All devices were connected to each other to make integration network system and configured by putting IP addresses to …
Credit Card Fraud Detection Using Machine Learning Techniques , Nermin Samy Elhusseny, shimaa mohamed ouf, Amira M. Idrees AMI BIS Helwan University
Credit Card Fraud Detection Using Machine Learning Techniques , Nermin Samy Elhusseny, Shimaa Mohamed Ouf, Amira M. Idrees Ami
Future computing and informatics journal.
This is a systematic literature review to reflect the previous studies that dealt with credit card fraud detection and highlight the different machine learning techniques to deal with this problem. Credit cards are now widely utilized daily. The globe has just begun to shift toward financial inclusion, with marginalized people being introduced to the financial sector. As a result of the high volume of e-commerce, there has been a significant increase in credit card fraud. One of the most important parts of today's banking sector is fraud detection. Fraud is one of the most serious concerns in terms of monetary …
Quantum Computing: Principles And Applications , Yoshito Kanamori, Seong-Moo Yoo University of Alaska Anchorage
Quantum Computing: Principles And Applications , Yoshito Kanamori, Seong-Moo Yoo
The development of quantum computers over the past few years is probably one of the significant advancements in the history of quantum computing. D-Wave quantum computer has been available for more than eight years. IBM has made its quantum computer accessible via its cloud service. Also, Microsoft, Google, Intel, and NASA have been heavily investing in the development of quantum computers and their applications. The quantum computer seems to be no longer just for physicists and computer scientists but also for information system researchers. This paper introduces the basic concepts of quantum computing and describes well-known quantum applications for non-physicists. …
Comparative Study Of Snort 3 And Suricata Intrusion Detection Systems , Cole Hoover University of Arkansas, Fayetteville
Comparative Study Of Snort 3 And Suricata Intrusion Detection Systems , Cole Hoover
Computer science and computer engineering undergraduate honors theses.
Network Intrusion Detection Systems (NIDS) are one layer of defense that can be used to protect a network from cyber-attacks. They monitor a network for any malicious activity and send alerts if suspicious traffic is detected. Two of the most common open-source NIDS are Snort and Suricata. Snort was first released in 1999 and became the industry standard. The one major drawback of Snort has been its single-threaded architecture. Because of this, Suricata was released in 2009 and uses a multithreaded architecture. Snort released Snort 3 last year with major improvements from earlier versions, including implementing a new multithreaded architecture …
Método De Programación Para Plc's Basado En El Estándar Iec61131. Caso De Estudio Proceso De Elaboración De Pan , Daniel Sebastián Molina Cortés, Jader Alvarino Garzón Universidad de La Salle, Bogotá
Método De Programación Para Plc's Basado En El Estándar Iec61131. Caso De Estudio Proceso De Elaboración De Pan , Daniel Sebastián Molina Cortés, Jader Alvarino Garzón
Ingeniería en automatización.
En este trabajo se presenta un método de programación, desarrollado mediante la aplicación de modelos software, basados en el estándar IEC 61131 parte 3 y 5, con la finalidad de mostrar las ventajas de conocer el estándar, tomando como caso de estudio el proceso de elaboración de croissant de la empresa Donut Factory. En primer lugar, se define el método para la implementación del proyecto, corresponde a, el diseño top-down y la implementación bottom-up, partiendo de este método se realiza su respectivo desarrollo, iniciando con una descripción del proceso, elaboración de diagramas para identificar los instrumentos, una descomposición del proceso …
Parameter Analysis Of An Adaptive, Fault-Tolerant Attitude Control System Using Lazy Learning , Matthew Russell Liberty University
Parameter Analysis Of An Adaptive, Fault-Tolerant Attitude Control System Using Lazy Learning , Matthew Russell
Senior honors theses.
Several key requirements would be met in an ideal fault-tolerant, adaptive spacecraft attitude controller, all centered around increasing tolerance to actuator non-idealities and other unknown quantities. This study seeks to better understand the application of lazy local learning to attitude control by characterizing the effect of bandwidth and the number of training points on the system’s performance. Using NASA’s 42 simulation framework, the experiment determined that in nominal operating scenarios, the actuator input/output relationship is linear. Once enough information is available to capture this linearity, additional training data and differing bandwidths did not significantly affect the system’s performance.
Bibliometric Analysis Of One-Stage And Two-Stage Object Detection , Aditya Lohia, Kalyani Dhananjay Kadam, Rahul Raghvendra Joshi, Dr. Anupkumar M. Bongale Symbiosis International University
Bibliometric Analysis Of One-Stage And Two-Stage Object Detection , Aditya Lohia, Kalyani Dhananjay Kadam, Rahul Raghvendra Joshi, Dr. Anupkumar M. Bongale
Library philosophy and practice (e-journal).
Object Detection using deep learning has seen a boom in the recent couple of years. Observing the trend and its research, it is important to summarize bibliometrics related to object detection which will help researchers contribute to this subject area. This paper details bibliometrics for one-stage object detection and two-stage object detection. This uses Scopus database for data analysis. This also uses tools like Sciencescape, Gephi, etc. It can be observed that the advancements to the field of object detection are seen in recent years and explored to its full extent. It is observed that Chinese universities and researchers are …
All Articles in Computer Engineering
23,530 full-text articles. Page 1 of 927 .
Data Engineering: Building Software Efficiency In Medium To Large Organizations , Alessandro De La Torre 2024 Whittier College
Data Engineering: Building Software Efficiency In Medium To Large Organizations , Alessandro De La Torre
Whittier scholars program.
The introduction of PoetHQ, a mobile application, offers an economical strategy for colleges, potentially ushering in significant cost savings. These savings could be redirected towards enhancing academic programs and services, enriching the educational landscape for students. PoetHQ aims to democratize access to crucial software, effectively removing financial barriers and facilitating a richer educational experience. By providing an efficient software solution that reduces organizational overhead while maximizing accessibility for students, the project highlights the essential role of equitable education and resource optimization within academic institutions.
Optimization Of Memory Management Using Machine Learning , Luke Bartholomew 2024 Southern Adventist University
Optimization Of Memory Management Using Machine Learning , Luke Bartholomew
Campus research day.
This paper is a proposed solution to the problem of memory safety using machine learning. Memory overload and corruption cause undesirable behaviors in a system that are addressed by memory safety implementations. This project uses machine learning models to classify different states of system memory from a dataset collected from a Raspberry Pi System. These models can then be used to classify real run time memory data and increase memory safety overall in a system.
Enhancing Cyber Resilience: Development, Challenges, And Strategic Insights In Cyber Security Report Websites Using Artificial Inteligence , Pooja Sharma 2024 Harrisburg University of Science and Technology
Enhancing Cyber Resilience: Development, Challenges, And Strategic Insights In Cyber Security Report Websites Using Artificial Inteligence , Pooja Sharma
Harrisburg university dissertations and theses.
In an era marked by relentless cyber threats, the imperative of robust cyber security measures cannot be overstated. This thesis embarks on an in-depth exploration of the historical trajectory and contemporary relevance of penetration testing methodologies, elucidating their evolution from nascent origins to indispensable tools in the cyber security arsenal. Moreover, it undertakes the ambitious task of conceptualizing and implementing a cyber security report website, meticulously designed to fortify cyber resilience in the face of ever-evolving threats in the digital realm.
The research journey commences with an insightful examination of the historical antecedents of penetration testing, tracing its genesis in …
The Role Of Attention Mechanisms In Enhancing Transparency And Interpretability Of Neural Network Models In Explainable Ai , Bhargav Kotipalli 2024 Harrisburg University of Science and Technology
The Role Of Attention Mechanisms In Enhancing Transparency And Interpretability Of Neural Network Models In Explainable Ai , Bhargav Kotipalli
In the rapidly evolving field of artificial intelligence (AI), deep learning models' interpretability
and reliability are severely hindered by their complexity and opacity. Enhancing the
transparency and interpretability of AI systems for humans is the primary objective of the
emerging field of explainable AI (XAI). The attention mechanisms at the heart of XAI's work
are based on human cognitive processes. Neural networks can now dynamically focus on
relevant parts of the input data thanks to these mechanisms, which enhances interpretability
and performance. This report covers in-depth talks of attention mechanisms in neural networks
within XAI, as well as an analysis …
Decoding The Future: Integration Of Artificial Intelligence In Web Development , Dhiraj Choithramani 2024 Harrisburg University of Science and Technology
Decoding The Future: Integration Of Artificial Intelligence In Web Development , Dhiraj Choithramani
The thesis explores AI's profound impact on web development, particularly in front-end and back-end processes. AI revolutionizes UI prototyping by automating design creation, enhancing both efficiency and aesthetics. It also aids in code review, content generation, and process flow experimentation, streamlining development workflows. Through AI-driven tools like GitHub's Copilot and Wix ADI, developers benefit from coding assistance and innovative design capabilities. Despite some challenges, AI's evolving role promises to reshape web development, offering unprecedented efficiency and user-centric solutions.
Enhancing Mobile App User Experience: A Deep Learning Approach For System Design And Optimization , Deepesh Haryani 2024 Harrisburg University of Science and Technology
Enhancing Mobile App User Experience: A Deep Learning Approach For System Design And Optimization , Deepesh Haryani
This paper presents a comprehensive framework for enhancing user experience in mobile applications through the integration of deep learning systems. The proposed system design encompasses various components, including data collection and preprocessing, model development and training, integration with mobile applications, dataset management service, model training service, model serving, hyperparameter optimization, metadata and artifact store, and workflow orchestration. Each component is meticulously designed with a focus on scalability, efficiency, isolation, and critical analysis. Innovative design principles are employed to ensure seamless integration, usability, and automation. Additionally, the paper discusses distributed training service design, advanced optimization techniques, and decision criteria for hyperparameter …
Predictive Ai Applications For Sar Cases In The Us Coast Guard , Joshua Nelson 2024 Old Dominion University
Predictive Ai Applications For Sar Cases In The Us Coast Guard , Joshua Nelson
Cybersecurity undergraduate research showcase.
This paper explores the potential integration of predictive analytics AI into the United States Coast Guard's (USCG) Search and Rescue Optimal Planning System (SAROPS) for deep sea and nearshore search and rescue (SAR) operations. It begins by elucidating the concept of predictive analytics AI and its relevance in military applications, particularly in enhancing SAR procedures. The current state of SAROPS and its challenges, including complexity and accuracy issues, are outlined. By integrating predictive analytics AI into SAROPS, the paper argues for streamlined operations, reduced training burdens, and improved accuracy in locating drowning personnel. Drawing on insights from military AI applications …
Human-Machine Communication: Complete Volume. Volume 7 Special Issue: Mediatization , 2024 University of Central Florida
Human-Machine Communication: Complete Volume. Volume 7 Special Issue: Mediatization
Human-machine communication.
This is the complete volume of HMC Volume 7. Special Issue on Mediatization
Artificial Sociality , Simone Natale, Iliana Depounti 2024 University of Turin, Italy
Artificial Sociality , Simone Natale, Iliana Depounti
This article proposes the notion of Artificial Sociality to describe communicative AI technologies that create the impression of social behavior. Existing tools that activate Artificial Sociality include, among others, Large Language Models (LLMs) such as ChatGPT, voice assistants, virtual influencers, socialbots and companion chatbots such as Replika. The article highlights three key issues that are likely to shape present and future debates about these technologies, as well as design practices and regulation efforts: the modelling of human sociality that foregrounds it, the problem of deception and the issue of control from the part of the users. Ethical, social and cultural …
Mediatization And Human-Machine Communication: Trajectories, Discussions, Perspectives , Andreas Hepp, Göran Bolin, Andrea L. Guzman, Wiebke Loosen 2024 University of Bremen
Mediatization And Human-Machine Communication: Trajectories, Discussions, Perspectives , Andreas Hepp, Göran Bolin, Andrea L. Guzman, Wiebke Loosen
As research fields, mediatization and Human-Machine Communication (HMC) have distinct historical trajectories. While mediatization research is concerned with the fundamental interrelation between the transformation of media and communications and cultural and societal changes, the much younger field of HMC delves into human meaning-making in interactions with machines. However, the recent wave of “deep mediatization,” characterized by an increasing emphasis on general communicative automation and the rise of communicative AI, highlights a shared interest in technology’s role within human interaction. This introductory article examines the trajectories of both fields, demonstrating how mediatization research “zooms out” from overarching questions of societal and …
Cyber Attacks Against Industrial Control Systems , Adam Kardorff 2024 Louisiana State University
Cyber Attacks Against Industrial Control Systems , Adam Kardorff
Lsu master's theses.
Industrial Control Systems (ICS) are the foundation of our critical infrastructure, and allow for the manufacturing of the products we need. These systems monitor and control power plants, water treatment plants, manufacturing plants, and much more. The security of these systems is crucial to our everyday lives and to the safety of those working with ICS. In this thesis we examined how an attacker can take control of these systems using a power plant simulator in the Applied Cybersecurity Lab at LSU. Running experiments on a live environment can be costly and dangerous, so using a simulated environment is the …
Enhancing Information Architecture With Machine Learning For Digital Media Platforms , Taylor N. Mietzner 2024 Georgia Southern University
Enhancing Information Architecture With Machine Learning For Digital Media Platforms , Taylor N. Mietzner
Honors college theses.
Modern advancements in machine learning are transforming the technological landscape, including information architecture within user experience design. With the unparalleled amount of user data generated on online media platforms and applications, an adjustment in the design process to incorporate machine learning for categorizing the influx of semantic data while maintaining a user-centric structure is essential. Machine learning tools, such as the classification and recommendation system, need to be incorporated into the design for user experience and marketing success. There is a current gap between incorporating the backend modeling algorithms and the frontend information architecture system design together. The aim of …
In-Depth Examination Of Gas Consumption In E-Will Smart Contract: A Case Study , Manal Mansour, May Salama, Hala Helmi, Mona F.M Mursi 2024 Faculty of Engineering, Shoubra, Benha University, Egypt
In-Depth Examination Of Gas Consumption In E-Will Smart Contract: A Case Study , Manal Mansour, May Salama, Hala Helmi, Mona F.M Mursi
Journal of engineering research.
In recent years, blockchain technology, coupled with smart contracts, has played a pivotal role in the development of distributed applications. Numerous case studies have emerged, showcasing the remarkable potential of this technology across various applications. Despite its widespread adoption in the industry, there exists a significant gap between the practical implementation of blockchain and the analytical and academic studies dedicated to understanding its nuances.
This paper aims to bridge this divide by presenting an empirical case study focused on the e-will contract, with a specific emphasis on gas-related challenges. By closely examining the e-will contract case study, we seek to …
A Soft Two-Layers Voting Model For Fake News Detection , Hnin Ei Wynne, Khaing Thanda Swe 2024 Department of Computer Engineering and Information Technology, Mandalay Technology University
A Soft Two-Layers Voting Model For Fake News Detection , Hnin Ei Wynne, Khaing Thanda Swe
The proliferation of fake news has become a complex and challenge problem in recent year, and presenting various unsolved issues within the research domain. Among these challenges, a critical concern is the development of effective models capable of accurately distinguish between fake and real news. While numerous techniques have been proposed for fake news detection, achieving optimal accuracy remains elusive. This paper introduces a novel fake news detection approach employing a two-layered weighted voting classifier. In contrast to conventional methods that assign equal weights to all classifiers, our proposed approach utilizes a selective weighting approach to solve the current issue. …
Exploring Human Aging Proteins Based On Deep Autoencoders And K-Means Clustering , Sondos M. Hammad, Mohamed Talaat Saidahmed, Elsayed A. Sallam, Reda Elbasiony 2024 Computers and Automatic Control Engineering, Faculty of Engineering, Tanta University, Egypt
Exploring Human Aging Proteins Based On Deep Autoencoders And K-Means Clustering , Sondos M. Hammad, Mohamed Talaat Saidahmed, Elsayed A. Sallam, Reda Elbasiony
Aging significantly affects human health and the overall economy, yet understanding of the underlying molecular mechanisms remains limited. Among all human genes, almost three hundred and five have been linked to human aging. While certain subsets of these genes or specific aging-related genes have been extensively studied. There has been a lack of comprehensive examination encompassing the entire set of aging-related genes. Here, the main objective is to overcome understanding based on an innovative approach that combines the capabilities of deep learning. Particularly using One-Dimensional Deep AutoEncoder (1D-DAE). Followed by the K-means clustering technique as a means of unsupervised learning. …
Protecting Return Address Integrity For Risc-V Via Pointer Authentication , yuhe zhao 2024 University of Massachusetts Amherst
Protecting Return Address Integrity For Risc-V Via Pointer Authentication , Yuhe Zhao
Masters theses.
Embedded systems based on lightweight microprocessors are becoming more prevalent in various applications. However, the security of them remains a significant challenge due to the limited resources and exposure to external threats. Especially, some of these devices store sensitive data and control critical devices, making them high-value targets for attackers. Software security is particularly important because attackers can easily access these devices on the internet and obtain control of them by injecting malware.
Return address (RA) hijacking is a common software attack technique used to compromise control flow integrity (CFI) by manipulating memory, such as return-to-libc attacks. Several methods have …
Blockchain Design For A Secure Pharmaceutical Supply Chain , Zhe Xu 2024 University of Massachusetts Amherst
Blockchain Design For A Secure Pharmaceutical Supply Chain , Zhe Xu
In the realm of pharmaceuticals, particularly during the challenging times of the COVID-19 pandemic, the supply chain for drugs has faced significant strains. The increased demand for vaccines and therapeutics has revealed critical weaknesses in the current drug supply chain management systems. If not addressed, these challenges could lead to severe societal impacts, including the rise of counterfeit medications and diminishing trust in government authorities.
The study identified that more than the current strategies, such as the Drug Supply Chain Security Act (DSCSA) in the U.S., which focuses on unique authentication and traceability codes for prescription drugs, is needed to …
Extracting Dnn Architectures Via Runtime Profiling On Mobile Gpus , Dong Hyub Kim 2024 University of Massachusetts Amherst
Extracting Dnn Architectures Via Runtime Profiling On Mobile Gpus , Dong Hyub Kim
Due to significant investment, research, and development efforts over the past decade, deep neural networks (DNNs) have achieved notable advancements in classification and regression domains. As a result, DNNs are considered valuable intellectual property for artificial intelligence providers. Prior work has demonstrated highly effective model extraction attacks which steal a DNN, dismantling the provider’s business model and paving the way for unethical or malicious activities, such as misuse of personal data, safety risks in critical systems, or spreading misinformation. This thesis explores the feasibility of model extraction attacks on mobile devices using aggregated runtime profiles as a side-channel to leak …
An Efficient Privacy-Preserving Framework For Video Analytics , Tian Zhou 2024 University of Massachusetts Amherst
An Efficient Privacy-Preserving Framework For Video Analytics , Tian Zhou
Doctoral dissertations.
With the proliferation of video content from surveillance cameras, social media, and live streaming services, the need for efficient video analytics has grown immensely. In recent years, machine learning based computer vision algorithms have shown great success in various video analytic tasks. Specifically, neural network models have dominated in visual tasks such as image and video classification, object recognition, object detection, and object tracking. However, compared with classic computer vision algorithms, machine learning based methods are usually much more compute-intensive. Powerful servers are required by many state-of-the-art machine learning models. With the development of cloud computing infrastructures, people are able …
Revolutionizing Feature Selection: A Breakthrough Approach For Enhanced Accuracy And Reduced Dimensions, With Implications For Early Medical Diagnostics , Shabia Shabir Khan, Majid Shafi Kawoosa, Bonny Bannerjee, Subhash C. Chauhan, Sheema Khan 2024 Islamic University of Science and Technology
Revolutionizing Feature Selection: A Breakthrough Approach For Enhanced Accuracy And Reduced Dimensions, With Implications For Early Medical Diagnostics , Shabia Shabir Khan, Majid Shafi Kawoosa, Bonny Bannerjee, Subhash C. Chauhan, Sheema Khan
Research symposium.
Background: The system's performance may be impacted by the high-dimensional feature dataset, attributed to redundant, non-informative, or irrelevant features, commonly referred to as noise. To mitigate inefficiency and suboptimal performance, our goal is to identify the optimal and minimal set of features capable of representing the entire dataset. Consequently, the Feature Selector (Fs) serves as an operator, transforming an m-dimensional feature set into an n-dimensional feature set. This process aims to generate a filtered dataset with reduced dimensions, enhancing the algorithm's efficiency.
Methods: This paper introduces an innovative feature selection approach utilizing a genetic algorithm with an ensemble crossover operation …
Popular Institutions
Featured Publications
Popular authors.
- Digital Communications and Networking (2122)
- Computer and Systems Architecture (1636)
- Data Storage Systems (1463)
- Other Computer Engineering (1362)
- Robotics (1200)
- Hardware Systems (526)
- Digital Circuits (239)
International Journal of Computer Engineering in Research Trends
Welcome to the International Journal of Computer Engineering in Research Trends (IJCERT). As a leading peer-reviewed, open-access journal, we specialize in disseminating innovative research in computer science engineering and related disciplines. Our focus encompasses a wide range of topics, including but not limited to computer architecture, networks, software engineering, information security, artificial intelligence, machine learning, data science, robotics, cyber-physical systems, and the Internet of Things.
IJCERT is an indispensable resource for both seasoned researchers and emerging scholars in the realm of computer science and engineering. We take pride in publishing top-tier research that significantly advances the field. Our journal serves as a dynamic platform for discovering emerging research trends and connecting with fellow professionals.
Our commitment at IJCERT extends beyond publication. We strive to push the frontiers of research in computer engineering and allied areas. Our meticulous, peer-reviewed process ensures the dissemination of only the most impactful and relevant studies, offering our readership reliable and authoritative content. Being an open-access journal amplifies the reach and influence of the research we feature, making it universally accessible.
We offer numerous advantages to our contributors, including comprehensive author support, indexing services post-publication, and the provision of digitally watermarked e-certificates. At the heart of our mission lies the drive to cultivate collaboration and innovation in computer engineering and adjacent fields. Our goal is to significantly contribute to the enrichment of knowledge and foster the development of groundbreaking ideas and technologies.
In summary, IJCERT stands as a beacon of excellence in the scholarly landscape, committed to elevating research, fostering collaboration, and furthering advancements in computer engineering and related disciplines.
Journal Details
Geographical Distribution of Authors:
Afghanistan, Albania, Angola, Bahrain, Bangladesh, Bolivia, Brazil, China, Denmark, Ethiopia, Greece, India, Indonesia, Iran, Iraq, Ireland, Jamaica, Kenya, Kuwait , Malaysia, Nepal, Nigeria, Pakistan, the Philippines, Saudi Arabia, Singapore, South Africa, Turkey, the United Arab Emirates, the United Kingdom, and the United States
Editorial Geographical Distribution:
India, Egypt, Turkey, Malaysia, Canada, Iran, Algeria, China, Nigeria, the Kingdom of Saudi Arabia, and Pakistan
Editorial Contribution Percentage in Articles Per Year: 28%
Aim and scope
The primary objective of our journal is to serve as a scholarly platform and a key reference point for the broad dissemination of research findings that elevate learning, teaching, and research in the areas of computer science, engineering, and related fields. We are dedicated to uniting a diverse community of researchers, academicians, professionals, scholars, and students from various related disciplines and technological domains.
Policy of the Journal
Our journal is committed to publishing original, high-quality research papers that encapsulate the most recent and significant developments in computer science engineering and its allied disciplines. Emphasizing originality and academic rigor, we ensure that each article we publish contributes meaningfully to the field.
A key aspect of our policy is to enhance the global visibility and citation impact of the research we feature. To achieve this, all published articles are submitted to well-respected research indexing databases. This approach not only broadens the reach of our authors' work but also integrates it into the broader scholarly conversation, fostering greater engagement and dissemination within the scientific community.
IJCERT stands as a globally recognized, rapidly expanding scientific research journal, renowned for its trustworthiness and leadership in the field. We are proudly accredited by the National Science Library (NSL), a part of the National Institute of Science Communication and Information Resources (NISCAIR), under the esteemed Council of Scientific and Industrial Research in New Delhi, India. This approval underscores our commitment to maintaining the highest standards in scientific publishing and research dissemination
Important Notice
To maintain the integrity and quality of our publication, we urge all authors, conference coordinators, conveners, and guest editors to rigorously verify the originality of their manuscripts before submission to the International Journal of Computer Engineering in Research Trends (IJCERT). It is essential to ensure that submissions are not concurrently under consideration by other journals or have been previously published.
In cases where a submission is found to be a duplicate, contains fabricated data, or is plagiarized at any stage of the review or publication process, IJCERT will enforce strict actions, including:
- • Immediate rejection of the implicated manuscript.
- • Prohibition of future submissions by the author(s) involved to IJCERT.
- • Formal notification to the affiliated institution's head.
- • Circulation of blacklisted authors among editors-in-chief of leading journals.
- We employ Turnitin, a globally recognized plagiarism detection tool, to screen submissions for plagiarism. While previously articles found plagiarized were only rejected, we are now compelled to adopt more stringent measures in response to ethical violations by a minority of authors. These instances of misconduct not only consume substantial time and resources but also hinder the journal's ability to process and publish legitimate research.
We appreciate your cooperation in upholding the high standards of academic integrity that IJCERT represents.
The publisher and the editorial team of the journal assume no responsibility for instances of plagiarism or any other ethical issues that may arise in any published article. The responsibility for the content, including the ideas and viewpoints expressed, rests solely with the respective author(s) of the article. It is imperative that authors uphold the highest standards of academic integrity and rigor in their work, as the publisher and editorial team focus on facilitating the dissemination of research and do not partake in the creation or validation of the article's content.
Announcements
Call for papers for the upcoming issue.
Last Date of Submission: August 1, 2024
Current Issue
Vol. 11 No. 2 (2024): February (2024) Issue
Published: 2024-02-27
Research Articles
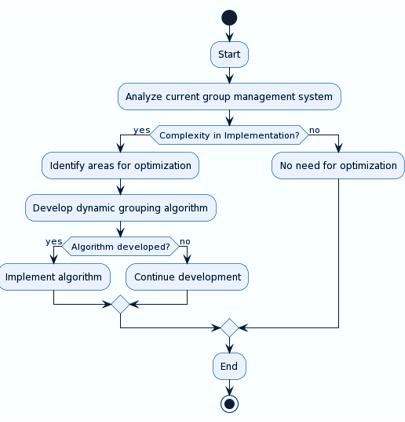
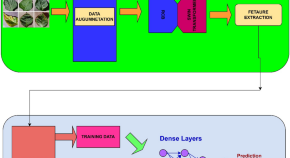
Optimizing Group Management and Cryptographic Techniques for Secure and Efficient MTC Communication

Enhancing Cloud Service Selection and Orchestration with DALMOCS: A Dynamic Adaptive Learning and Multi-Criteria Decision Analysis Approach
computer science Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Hiring CS Graduates: What We Learned from Employers
Computer science ( CS ) majors are in high demand and account for a large part of national computer and information technology job market applicants. Employment in this sector is projected to grow 12% between 2018 and 2028, which is faster than the average of all other occupations. Published data are available on traditional non-computer science-specific hiring processes. However, the hiring process for CS majors may be different. It is critical to have up-to-date information on questions such as “what positions are in high demand for CS majors?,” “what is a typical hiring process?,” and “what do employers say they look for when hiring CS graduates?” This article discusses the analysis of a survey of 218 recruiters hiring CS graduates in the United States. We used Atlas.ti to analyze qualitative survey data and report the results on what positions are in the highest demand, the hiring process, and the resume review process. Our study revealed that a software developer was the most common job the recruiters were looking to fill. We found that the hiring process steps for CS graduates are generally aligned with traditional hiring steps, with an additional emphasis on technical and coding tests. Recruiters reported that their hiring choices were based on reviewing resume’s experience, GPA, and projects sections. The results provide insights into the hiring process, decision making, resume analysis, and some discrepancies between current undergraduate CS program outcomes and employers’ expectations.
A Systematic Literature Review of Empiricism and Norms of Reporting in Computing Education Research Literature
Context. Computing Education Research (CER) is critical to help the computing education community and policy makers support the increasing population of students who need to learn computing skills for future careers. For a community to systematically advance knowledge about a topic, the members must be able to understand published work thoroughly enough to perform replications, conduct meta-analyses, and build theories. There is a need to understand whether published research allows the CER community to systematically advance knowledge and build theories. Objectives. The goal of this study is to characterize the reporting of empiricism in Computing Education Research literature by identifying whether publications include content necessary for researchers to perform replications, meta-analyses, and theory building. We answer three research questions related to this goal: (RQ1) What percentage of papers in CER venues have some form of empirical evaluation? (RQ2) Of the papers that have empirical evaluation, what are the characteristics of the empirical evaluation? (RQ3) Of the papers that have empirical evaluation, do they follow norms (both for inclusion and for labeling of information needed for replication, meta-analysis, and, eventually, theory-building) for reporting empirical work? Methods. We conducted a systematic literature review of the 2014 and 2015 proceedings or issues of five CER venues: Technical Symposium on Computer Science Education (SIGCSE TS), International Symposium on Computing Education Research (ICER), Conference on Innovation and Technology in Computer Science Education (ITiCSE), ACM Transactions on Computing Education (TOCE), and Computer Science Education (CSE). We developed and applied the CER Empiricism Assessment Rubric to the 427 papers accepted and published at these venues over 2014 and 2015. Two people evaluated each paper using the Base Rubric for characterizing the paper. An individual person applied the other rubrics to characterize the norms of reporting, as appropriate for the paper type. Any discrepancies or questions were discussed between multiple reviewers to resolve. Results. We found that over 80% of papers accepted across all five venues had some form of empirical evaluation. Quantitative evaluation methods were the most frequently reported. Papers most frequently reported results on interventions around pedagogical techniques, curriculum, community, or tools. There was a split in papers that had some type of comparison between an intervention and some other dataset or baseline. Most papers reported related work, following the expectations for doing so in the SIGCSE and CER community. However, many papers were lacking properly reported research objectives, goals, research questions, or hypotheses; description of participants; study design; data collection; and threats to validity. These results align with prior surveys of the CER literature. Conclusions. CER authors are contributing empirical results to the literature; however, not all norms for reporting are met. We encourage authors to provide clear, labeled details about their work so readers can use the study methodologies and results for replications and meta-analyses. As our community grows, our reporting of CER should mature to help establish computing education theory to support the next generation of computing learners.
Light Diacritic Restoration to Disambiguate Homographs in Modern Arabic Texts
Diacritic restoration (also known as diacritization or vowelization) is the process of inserting the correct diacritical markings into a text. Modern Arabic is typically written without diacritics, e.g., newspapers. This lack of diacritical markings often causes ambiguity, and though natives are adept at resolving, there are times they may fail. Diacritic restoration is a classical problem in computer science. Still, as most of the works tackle the full (heavy) diacritization of text, we, however, are interested in diacritizing the text using a fewer number of diacritics. Studies have shown that a fully diacritized text is visually displeasing and slows down the reading. This article proposes a system to diacritize homographs using the least number of diacritics, thus the name “light.” There is a large class of words that fall under the homograph category, and we will be dealing with the class of words that share the spelling but not the meaning. With fewer diacritics, we do not expect any effect on reading speed, while eye strain is reduced. The system contains morphological analyzer and context similarities. The morphological analyzer is used to generate all word candidates for diacritics. Then, through a statistical approach and context similarities, we resolve the homographs. Experimentally, the system shows very promising results, and our best accuracy is 85.6%.
A genre-based analysis of questions and comments in Q&A sessions after conference paper presentations in computer science
Gender diversity in computer science at a large public r1 research university: reporting on a self-study.
With the number of jobs in computer occupations on the rise, there is a greater need for computer science (CS) graduates than ever. At the same time, most CS departments across the country are only seeing 25–30% of women students in their classes, meaning that we are failing to draw interest from a large portion of the population. In this work, we explore the gender gap in CS at Rutgers University–New Brunswick, a large public R1 research university, using three data sets that span thousands of students across six academic years. Specifically, we combine these data sets to study the gender gaps in four core CS courses and explore the correlation of several factors with retention and the impact of these factors on changes to the gender gap as students proceed through the CS courses toward completing the CS major. For example, we find that a significant percentage of women students taking the introductory CS1 course for majors do not intend to major in CS, which may be a contributing factor to a large increase in the gender gap immediately after CS1. This finding implies that part of the retention task is attracting these women students to further explore the major. Results from our study include both novel findings and findings that are consistent with known challenges for increasing gender diversity in CS. In both cases, we provide extensive quantitative data in support of the findings.
Designing for Student-Directedness: How K–12 Teachers Utilize Peers to Support Projects
Student-directed projects—projects in which students have individual control over what they create and how to create it—are a promising practice for supporting the development of conceptual understanding and personal interest in K–12 computer science classrooms. In this article, we explore a central (and perhaps counterintuitive) design principle identified by a group of K–12 computer science teachers who support student-directed projects in their classrooms: in order for students to develop their own ideas and determine how to pursue them, students must have opportunities to engage with other students’ work. In this qualitative study, we investigated the instructional practices of 25 K–12 teachers using a series of in-depth, semi-structured interviews to develop understandings of how they used peer work to support student-directed projects in their classrooms. Teachers described supporting their students in navigating three stages of project development: generating ideas, pursuing ideas, and presenting ideas. For each of these three stages, teachers considered multiple factors to encourage engagement with peer work in their classrooms, including the quality and completeness of shared work and the modes of interaction with the work. We discuss how this pedagogical approach offers students new relationships to their own learning, to their peers, and to their teachers and communicates important messages to students about their own competence and agency, potentially contributing to aims within computer science for broadening participation.
Creativity in CS1: A Literature Review
Computer science is a fast-growing field in today’s digitized age, and working in this industry often requires creativity and innovative thought. An issue within computer science education, however, is that large introductory programming courses often involve little opportunity for creative thinking within coursework. The undergraduate introductory programming course (CS1) is notorious for its poor student performance and retention rates across multiple institutions. Integrating opportunities for creative thinking may help combat this issue by adding a personal touch to course content, which could allow beginner CS students to better relate to the abstract world of programming. Research on the role of creativity in computer science education (CSE) is an interesting area with a lot of room for exploration due to the complexity of the phenomenon of creativity as well as the CSE research field being fairly new compared to some other education fields where this topic has been more closely explored. To contribute to this area of research, this article provides a literature review exploring the concept of creativity as relevant to computer science education and CS1 in particular. Based on the review of the literature, we conclude creativity is an essential component to computer science, and the type of creativity that computer science requires is in fact, a teachable skill through the use of various tools and strategies. These strategies include the integration of open-ended assignments, large collaborative projects, learning by teaching, multimedia projects, small creative computational exercises, game development projects, digitally produced art, robotics, digital story-telling, music manipulation, and project-based learning. Research on each of these strategies and their effects on student experiences within CS1 is discussed in this review. Last, six main components of creativity-enhancing activities are identified based on the studies about incorporating creativity into CS1. These components are as follows: Collaboration, Relevance, Autonomy, Ownership, Hands-On Learning, and Visual Feedback. The purpose of this article is to contribute to computer science educators’ understanding of how creativity is best understood in the context of computer science education and explore practical applications of creativity theory in CS1 classrooms. This is an important collection of information for restructuring aspects of future introductory programming courses in creative, innovative ways that benefit student learning.
CATS: Customizable Abstractive Topic-based Summarization
Neural sequence-to-sequence models are the state-of-the-art approach used in abstractive summarization of textual documents, useful for producing condensed versions of source text narratives without being restricted to using only words from the original text. Despite the advances in abstractive summarization, custom generation of summaries (e.g., towards a user’s preference) remains unexplored. In this article, we present CATS, an abstractive neural summarization model that summarizes content in a sequence-to-sequence fashion while also introducing a new mechanism to control the underlying latent topic distribution of the produced summaries. We empirically illustrate the efficacy of our model in producing customized summaries and present findings that facilitate the design of such systems. We use the well-known CNN/DailyMail dataset to evaluate our model. Furthermore, we present a transfer-learning method and demonstrate the effectiveness of our approach in a low resource setting, i.e., abstractive summarization of meetings minutes, where combining the main available meetings’ transcripts datasets, AMI and International Computer Science Institute(ICSI) , results in merely a few hundred training documents.
Exploring students’ and lecturers’ views on collaboration and cooperation in computer science courses - a qualitative analysis
Factors affecting student educational choices regarding oer material in computer science, export citation format, share document.
University Library, University of Illinois at Urbana-Champaign

Electrical and Computer Engineering Research Resources: Find Articles & Papers
- Find Articles & Papers
- High-Impact Journals
- Standards & Technical Reports
- Patents & Government Documents
- E-Books & Reference
- Dissertations & Theses
- Additional Resources
Engineering Easy Search
University library search engines.
- Grainger Engineering Library Homepage With specialized searches for Engineering and the Physical Sciences.
- Easy Search The easiest way to locate University Library resources, materials, and more!
- Find Online Journals Search by title or by subject to view our subscription details, including date ranges and where you can access full text.
- Journal and Article Locator Finds electronic or print copy of articles by using a citation.

Engineering Article Databases
- Engineering Village This link opens in a new window Search for articles, conference paper, and report information in all areas of engineering. Full-text is often available through direct download.
- Scopus This link opens in a new window Search periodicals, conference proceedings, technical reports, trade literature, patents, books, and press releases in all engineering fields. Some full-text available as direct downloads.
- Web of Science (Core Collection) This link opens in a new window Search for articles in science and engineering. Also provides Science Citation Index that tracks citations in science and technical journals published since 1981. Journal Citation Reports are also available through ISI.
Electrical & Computer Engineering
- ACM Digital Library This site provides access to tables of contents, abstracts, reviews, and full text of every article ever published by ACM and bibliographic citations from major publishers in computing.
- ENGnetBASE A collection of best-selling engineering handbooks and reference titles. Includes access to sub-collections: CivilENGINEERINGnetBASE, ElectricalENGINEERINGnetBASE, GeneralENGINEERINGnetBASE, IndustrialENGINEERINGnetBASE, MechanicalENGINEERINGnetBASE, MiningENGINEERINGnetBASE.
- IEEE Xplore Provides full-text access to IEEE transactions, IEEE and IEE journals, magazines, and conference proceedings published since 1988, and all current IEEE standards; brings additional search and access features to IEEE/IEE digital library users. Browsable by books & e-books, conference publications, education and learning, journals and magazines, standards and by topic. Also provides links to IEEE standards, IEEE spectrum and other sites.
- INSPEC Database providing access to bibliographic citations and abstracts of the scientific and technical literature in physics, electrical engineering, electronics, communications, control engineering, computers and computing, information technology, manufacturing and production engineering. Material covered includes journal articles, conference proceedings, reports, dissertations, patents and books published around the world.
- Microelectronics Packaging Materials Database (MPMD) The MPMD database contains data and information on thermal, mechanical, electrical and physical properties of electronics packaging materials. Available in a Web-based format. The database is continually updated and expanded.
- SPIE Digital Library Contains full-text papers on optics and photonics from SPIE journals and proceedings published since 1990. Approximately 15,000 new papers will be added each year.
Subject Guide

Ask a Librarian
- Next: High-Impact Journals >>
- Last Updated: Jun 16, 2023 9:35 AM
- URL: https://guides.library.illinois.edu/ece
Exploring and expanding new directions of inquiry
A unique and robust research environment
At Michigan, faculty and students in CSE have the unique opportunity to collaborate with peers from across 19 highly-acclaimed schools and colleges to conduct impactful, broad ranging, and highly interdisciplinary research.

Resources at the University include leading schools of medicine, business, information, art, engineering, and public policy; facilities such as high performance computing clusters and the Mcity test facility for autonomous vehicle testing; institutes of robotics and data science; initiatives in precision health and biosciences; and more. CSE researchers also have long-standing relationships with industrial partners.

Research areas
Our 12 key areas of research reflect the depth and pervasiveness of modern computing.
CSE research areas >
Labs and centers
Explore CSE’s five labs and numerous faculty and affiliated research centers.
CSE labs and centers >

Undergraduate research
About 150 undergraduate students conduct research on EECS faculty projects in a typical year.
See the opportunities >
A Lightweight Quantized CNN Model for Plant Disease Recognition
- Research Article-Computer Engineering and Computer Science
- Published: 20 September 2023
- Volume 49 , pages 4097–4108, ( 2024 )
Cite this article
- Abdul Fattah Rakib 1 ,
- Rashik Rahman 1 ,
- Alim Al Razi 1 &
- A. S. M. Touhidul Hasan ORCID: orcid.org/0000-0002-0929-6499 2
176 Accesses
Explore all metrics
Plant health conditions are becoming more prevalent in smart farming, and diagnosing plant diseases usually involves a visual inspection and a physical examination by experts. Detecting the signs of a disease at an early stage may prevent the spreading of pathogens in the farmland. However, these examinations are computationally costly and time-consuming. Complex machine learning algorithms such as convolutional neural networks cannot run on the resource constraint IoT devices since they require high-configuration hardware for training and testing. Therefore, this paper proposes an energy-efficient and computationally lightweight solution deployed on an IoT device, i.e., esp32-cam, that can recognize nine (9) different plant diseases using a quantized CNN (Q-CNN) approach. Q-CNN speeds up computation and reduces the model size while maintaining optimal performance. The memory overhead of the convolutional layers and fully connected layers are compressed via model quantization. The size of the developed model is only 28 KB with exclusive int8 quantization and is utterly attainable on low computational edge devices. Experimental outcomes demonstrate that the proposed approach can perform better than existing methods, gaining an overall \(F_1\) accuracy of 98% on resource-constrained IoT devices.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Similar content being viewed by others

An ultra-lightweight efficient network for image-based plant disease and pest infection detection
Beibei Wang, Chenxiao Zhang, … Yan Gong
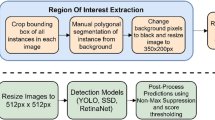
LWCNN: a lightweight convolutional neural network for agricultural crop protection
Sundaresan Raman, Manan Soni, … Vinay Chamola

Deep Residual Learning Approach forPlant Disease Recognition
https://www.worldbank.org/en/news/feature/2016/05/17/bangladeshi’s-agriculture-a-poverty-reducer-in-need-of-modernization .
Strange, R.N.; Scott, P.R.: Plant disease: a threat to global food security. Annu. Rev. Phytopathol. 43 , 83–116 (2005)
Article CAS PubMed Google Scholar
Karol, A.M.A.; Gulhane, D.; Chandiwade, T.: Plant disease detection using CNN & remedy. Int. J. Adv. Res. Electr. Electron. Instrum. Eng 8 (3), 622–626 (2019)
Google Scholar
Riley, M.; Williamson, M.; Maloy, O.: Plant disease diagnosis. The plant health instructor (2002). https://doi.org/10.1094/PHI-I-2002-1021
Martinelli, F.; Scalenghe, R.; Davino, S.; Panno, S.; Scuderi, G.; Ruisi, P.; Villa, P.; Stroppiana, D.; Boschetti, M.; Goulart, L.R.; et al.: Advanced methods of plant disease detection. A review. Agron. Sustain. Dev. 35 (1), 1–25 (2015)
Article Google Scholar
Nagaraju, M.; Chawla, P.: Systematic review of deep learning techniques in plant disease detection. Int. J. Syst. Assur. Eng. Manag. 11 (3), 547–560 (2020)
Thorat, A.; Kumari, S.; Valakunde, N.D.: An IoT based smart solution for leaf disease detection. In: 2017 International Conference on Big Data, IoT and Data Science (BID), pp. 193–198, IEEE (2017)
Rehman, T.U.; Mahmud, M.S.; Chang, Y.K.; Jin, J.; Shin, J.: Current and future applications of statistical machine learning algorithms for agricultural machine vision systems. Comput. Electron. Agric. 156 , 585–605 (2019)
Saleem, M.H.; Potgieter, J.; Arif, K.M.: Plant disease detection and classification by deep learning. Plants 8 (11), 468 (2019)
Article PubMed PubMed Central Google Scholar
Kamilaris, A.; Prenafeta-Boldú, F.X.: Deep learning in agriculture: a survey. Comput. Electron. Agric. 147 , 70–90 (2018)
Dhingra, G.; Kumar, V.; Joshi, H.D.: Study of digital image processing techniques for leaf disease detection and classification. Multimed. Tools Appl. 77 (15), 19951–20000 (2018)
Chaitra, S.; Ghana, S.; Singh, S.; Poddar, P.: Deep learning model for image-based plant diseases detection on edge devices. In: 2021 6th International Conference for Convergence in Technology (I2CT), pp. 1–5 . IEEE (2021)
De Vita, F.; Nocera, G.; Bruneo, D.; Tomaselli, V.; Giacalone, D.; Das, S.K.: Quantitative analysis of deep leaf: a plant disease detector on the smart edge. In: 2020 IEEE International Conference on Smart Computing (SMARTCOMP), pp. 49–56. IEEE (2020)
Molina-Villa, M.A.; Solaque-Guzmán, L.E.; et al.: Machine vision system for weed detection using image filtering in vegetables crops. Revista Facultad de Ingeniería Universidad de Antioquia 80 , 124–130 (2016)
Shirzadifar, A.M.; et al: Automatic weed detection system and smart herbicide sprayer robot for corn fields. In: 2013 First RSI/ISM International Conference on Robotics and Mechatronics (ICRoM), pp. 468–473. IEEE (2013)
Dankhara, F.; Patel, K.; Doshi, N.: Analysis of robust weed detection techniques based on the internet of things (IoT). Proc. Comput. Sci. 160 , 696–701 (2019)
Mohanty, S.: Plant Village Dataset (2016). https://github.com/spMohanty/PlantVillage-Dataset
Kumar, S.S.; Raghavendra, B.: Diseases detection of various plant leaf using image processing techniques: a review. In: 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), pp. 313–316. IEEE (2019)
Ramesh, S.; Hebbar, R.; Niveditha, M.; Pooja, R.; Shashank, N.; Vinod, P.; et al: Plant disease detection using machine learning. In: 2018 International Conference on Design Innovations for 3Cs Compute Communicate Control (ICDI3C), pp. 41–45 . IEEE (2018)
Sankar, M.; Mudgal, D.; Jalinder, M.M.; et al: Green leaf disease detection using raspberry pi. In: 2019 1st International Conference on Innovations in Information and Communication Technology (ICIICT), pp. 1–6. IEEE (2019)
Kaur, S.; Pandey, S.; Goel, S.: Semi-automatic leaf disease detection and classification system for soybean culture. IET Image Proc. 12 (6), 1038–1048 (2018)
Basavaiah, J.; Arlene Anthony, A.: Tomato leaf disease classification using multiple feature extraction techniques. Wireless Pers. Commun. 115 (1), 633–651 (2020)
Yashwanth, M.; Chandra, M.L.; Pallavi, K.; Showkat, D.; Kumar, P.S.: Agriculture automation using deep learning methods implemented using keras. In: 2020 IEEE International Conference for Innovation in Technology (INOCON), pp. 1–6. IEEE (2020)
Hidayatuloh, A.; Nursalman, M.; Nugraha, E.: Identification of tomato plant diseases by leaf image using squeezenet model. In: 2018 International Conference on Information Technology Systems and Innovation (ICITSI), pp. 199–204 . IEEE (2018)
Sardogan, M.; Tuncer, A.; Ozen, Y.: Plant leaf disease detection and classification based on cnn with lvq algorithm. In: 2018 3rd International Conference on Computer Science and Engineering (UBMK), pp. 382–385. IEEE (2018)
Ale, L.; Sheta, A.; Li, L.; Wang, Y.; Zhang, N.: Deep learning based plant disease detection for smart agriculture. In: 2019 IEEE Globecom Workshops (GC Wkshps), pp. 1–6. IEEE (2019)
Ponnusamy, V.; Coumaran, A.; Shunmugam, A.S.; Rajaram, K.; Senthilvelavan, S.: Smart glass: Real-time leaf disease detection using yolo transfer learning. In: 2020 International Conference on Communication and Signal Processing (ICCSP), pp. 1150–1154 . IEEE (2020)
Anh, P.T.; Duc, H.T.M.: A benchmark of deep learning models for multi-leaf diseases for edge devices. In: 2021 International Conference on Advanced Technologies for Communications (ATC), pp. 318–323 . IEEE (2021)
Wang, R.; Zhang, W.; Ding, J.; Xia, M.; Wang, M.; Rao, Y.; Jiang, Z.: Deep neural network compression for plant disease recognition. Symmetry 13 (10), 1769 (2021)
Article ADS Google Scholar
Elhassouny, A.; Smarandache, F.: Smart mobile application to recognize tomato leaf diseases using convolutional neural networks. In: 2019 International Conference of Computer Science and Renewable Energies (ICCSRE), pp. 1–4 . IEEE (2019)
Li, F.; Liu, Z.; Shen, W.; Wang, Y.; Wang, Y.; Ge, C.; Sun, F.; Lan, P.: A remote sensing and airborne edge-computing based detection system for pine wilt disease. IEEE Access 9 , 66346–66360 (2021)
Al-gaashani, M.S.; Shang, F.; Muthanna, M.S.; Khayyat, M.; Abd El-Latif, A.A.: Tomato leaf disease classification by exploiting transfer learning and feature concatenation. IET Image Proc. 16 (3), 913–925 (2022)
Liu, G.; Peng, J.; El-Latif, A.A.A.: Sk-mobilenet: a lightweight adaptive network based on complex deep transfer learning for plant disease recognition. Arabian J.D Sci. Eng. 48 (2), 1661–75 (2022)
Workshop, D.: Getting started with the ESP32-CAM (2020). https://dronebotworkshop.com/esp32-cam-intro/
Wu, H.; Judd, P.; Zhang, X.; Isaev, M.; Micikevicius, P.: Integer quantization for deep learning inference: Principles and empirical evaluation. arXiv preprint (2020). arXiv:2004.09602
Download references
Acknowledgements
The authors thank the anonymous reviewers and editor for their invaluable comments on our manuscript.
Author information
Authors and affiliations.
Department of CSE, University of Asia Pacific, Dhaka, 1205, Bangladesh
Abdul Fattah Rakib, Rashik Rahman & Alim Al Razi
Computer Science and Information Technology, School of Science and Engineering, University of Missouri-Kansas City, 5110 Rockhill Road, Kansas City, MO, 64110, USA
A. S. M. Touhidul Hasan
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to A. S. M. Touhidul Hasan .
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Rakib, A.F., Rahman, R., Razi, A.A. et al. A Lightweight Quantized CNN Model for Plant Disease Recognition. Arab J Sci Eng 49 , 4097–4108 (2024). https://doi.org/10.1007/s13369-023-08280-z
Download citation
Received : 07 June 2022
Accepted : 31 August 2023
Published : 20 September 2023
Issue Date : March 2024
DOI : https://doi.org/10.1007/s13369-023-08280-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Quantized CNN
- Plant disease recognition
- IoT edge device
- Find a journal
- Publish with us
- Track your research
- How it works
Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computing Engineering Dissertation Topics
Published by Jamie Walker at January 10th, 2023 , Revised On August 18, 2023
Over a period of time, dissertations have become an inherent component of higher education studies. They are not only entrenched within the master or a PhD. Degree but also in undergraduate programmes. Computer engineering dissertations allow the researchers to choose a topic of particular interest to them and research further into the topic to add to the current body of literature.
However, choosing a topic from an extensive list of topics is always easier than working on the first topic you find interesting.
To help you get started with brainstorming for computer topic ideas, we have developed a list of the latest computer engineering dissertation topics that can be used for writing your computer engineering dissertation.
These topics have been developed by PhD-qualified writers of our team , so you can trust to use these topics for drafting your dissertation.
You may also want to start your dissertation by requesting a brief research proposal from our writers on any of these topics, which includes an introduction to the problem, research questions , aim and objectives , literature review along with the proposed methodology of research to be conducted. Let us know if you need any help in getting started.
Check our example dissertations to get an idea of how to structure your dissertation .
You can review step by step guide on how to write your dissertation here.
View our free dissertation topics database.
Computer Engineering Dissertation Topics
Computers are the greatest innovation of the modern era and have done wonders for mankind. There is only one language that computers understand; the binary. But there are various high-level coding languages that even computers do not understand and therefore use a compiler for translation.
Computing refers to computer hardware or software coding development technology and covers all aspects of computer technologies. It is the practical and scientific study of the implementation of computing information. Computing is also interchangeably known as computer sciences.
A computing engineer or a computer scientist specializes in practical work, the theory of computing, and the design of computational systems. Essentially, it is the study of structure, expression, mechanization, and feasibility of algorithms (logical procedures) that cause processing, communication, representation, access of information, and acquisition in a computer. This area has a wide range of topics, some of which have been listed below:
- Risk calculation in the application and development process.
- Generation of the java application.
- Implementing a behavioural based approach to detect cheating in online games.
- Analysis of coding environment of different applications.
- Identification of different languages used for coding.
- Identification of stake holder’s interest in App development process.
- Role of visualization in complex hierarchal structures of computing.
- Analysing the requirements of Inventory Management Software.
- Development of single-player simulation game.
- Investigation of web teaching aid system.
- Development of online based library management system.
- Implementation of Electronic banking system.
2022 Computing Engineering Dissertation Topics
Topic 1: an investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility..
Research Aim: This study aims to investigate the applications of blockchain within the energy sector. This study will identify how blockchain can be used to produce electricity from the comfort of home. Moreover, this study aims to introduce the concept of e-mobility through blockchain, according to which blockchain can be used to share the car ride with the other commuters residing at nearby places. Another objective of this research is to develop a framework that could assess blockchain’s use for the consumers staying within a budget and letting them assess how much money they have been spending so far.
Topic 2: Investigating the Issues that Impact Data Security in Cloud-Based Blockchain Technology: An Global Tourism Industry Case Study
Research Aim: This research focuses on a significant shift in trend found in the worldwide tourist business, which is the usage of the cloud for data and services. It attempts to supply the requirements for this implementation owing to the demand for ease, saving, and improved service providing. Furthermore, it will also focus on the limits of traditional blockchain technology primitives and assess control models. These constraints are related to security issues involving data in a cloud environment in the global tourism industry.
Topic 3: Is Digital Technology overtaking Human Interactions in the Medical Fields? An Examination of the Use of Computational biology and Machine Leaning in Patient Diagnosis and Treatment.
Research Aim: The current study seeks to examine how digital technology is replacing human interactions in the medical industry in the importance of computational biology and machine learning in patient diagnosis and treatment. This study will set forth the theoretical foundations and significance of computational biology and machine learning and will also make recommendations for further enhancement.
Topic 4: Evaluating the use of databases and information retrieval systems in the perspective of the United States National security policy.
Research Aim: The current study aims to evaluate the use of databases and information retrieval systems from the perspective of United States national security policy. This study addresses the databases and information retrieval system to provide a clear understanding. It will also focus on specific elements d criteria in the united state’s national security and highlights the benefits and drawbacks of employing them to enhance national security strategy in the united states.
Topic 5: Development of growing infusion of computer technology in the area of medicine- examining NHS policies.
Research Aim: This research aims to examine the development of the growing infusion of computer technology in the area of medicine by evaluating existing NHS policy. The study will provide a theoretical framework for the application of computer science technologies in medicine and will also set out the benefits of using contemporary computer technology as well as analyse the drawbacks that have occurred as a result of the growth of this new technology in this field. It will also focus on the policies employed by NHS to assist the development of technologies in the UK healthcare sector.
Computer Engineering Dissertation Topics for 2021
A 3-d visualization system for ultrasound images.
Research Aim: This research will focus on the visualization of 3-D ultrasound images and their medical therapy benefits.
Reliable and realistic study of remote communication systems in telephony and multipath faded systems
Research Aim: This research’s primary emphasis is on telephony’s practical implementation in a remote communication system.
Establishing a Neural Network Device
Research Aim: In terms of energy efficiency, the human brain is much greater than any modern supercomputer. A whole new generation of energy-efficient, brain-like computers is being designed for this study.
Methods for Artifact EEG Brain function study, caused by sugar, salt, fat, and their replacements
Research Aim: This study relies on the procedure for calculating sweetness taste is developed and validated. Part of the project includes modern electrode technologies to capture the purest possible brain signal from EEG equipment.
Find 100s of dissertation topics in your other academic subjects in our free topics database.
The impact of Covid-19 on tech spends in 2021
Research Aim: This research aims to study the impact of Covid-19 on tech spends in 2021.
Analysis of information system built for e-learning
Research Aim: This research aims to analyze the information system built for e-learning
Advantages and disadvantages of an information system
Research Aim: This research aims to address the advantages and disadvantages of an information system.
Covid-19 Computer Engineering Research Topics
Research to study the effects of coronavirus on it industries.
Research Aim: This research will focus on the impacts of COVID-19 on the growth of IT industries highlighting the issues responsible for it and the possible solutions to overcome them.
Research to identify the impact of Coronavirus on the computer science research community
Research Aim: Coronavirus has infected thousands of people and has been responsible for the deaths of several innocent people worldwide. This study will focus on identifying the effects of this pandemic on the computer science research community.
Research to study the impacts of COVID-19 on tech spends in 2021
Research Aim: As a result of COVID-19, the economy of the entire world has been disrupted. The purpose of this research is to know the tech expenditures after COVID-19 became widespread. How are the tech industries dealing with the challenging situation created by COVID-19?
Research to identify the contribution of computer science to control the spread of Coronavirus pandemic
Research Aim: This research aims at identifying the contributions and efforts made by computer engineers to control the pandemic. What is the role of computer scientists during the pandemic?
Research to identify the unemployment of computer engineers after the Coronavirus pandemic
Research Aim: This research will focus on identifying the increased unemployment issues raised after the COVID-19 pandemic and finding out the possible solutions to overcome the reduced unemployment of computer engineers.
Hardware, Network and Security Dissertation Topics
Network security is very crucial for any organisation. It is dependent upon a well-managed network through the implementation of policies drafted by network administrators to manage the access of the organisational information. Network security provides stability, safety, integrity, reliability, and utility of data and network.
It works efficiently with the latest hardware equipment and updated software. Network security offers many advantages to businesses, such as protection against any disruption to keep employees motivated, energetic, regular, and productive.
In certain instances, a virus may break into the network security. However, the network administrator generally uses an anti-virus program to prevent this sort of attack.
Therefore, it will be fair to say that network security plays a vital role in maintaining a business’s reputation and operations which is the most important asset to any organisation. Below is a list of topics that you can base your dissertation on:
- Performance analysis of transmission control protocol over Ethernet LAN.
- Gateway usage for the intrusion detection system.
- Impact of security machinimas in online transactions.
- Investigation of smart card specification.
- Importance of router placement in the network.
- Level of customer’s trust in E-banking.
- Role of antivirus in a shared network.
- Application of database technologies for data network management.
- Network worm: A headache to networking.
- Implementation of various tools in programming language.
- Study of retroactive data structures.
- Role of Voice over Internet Protocol over Ethernet LAN.
- The usefulness of data transfer security over Wi-Fi Network.
- Influence of signal strength of Wi-Fi upon data transfer.
- Analysis of tree inclusion complexities.
- Analysis of the implementation of the set procedure.
- Analysis of the application of programming tools.
- Implementation of File Sharing System in Network.
- Study of virus behaviours in the secured programming environment.
- Investigation of issues of user’s security and data protection over the network.
- Benefits of network security to customers.
- Improvements of mobile data service for future usage.
- Study of Asymmetry k-center variant.
- Analysis of issues in emerging 4G networks.
- Role of dynamic proxies in a mobile environment to support Remote method Invocation.
Software, Programming and Algorithm Dissertation Topics
In layman language, the software is collectively known as the “combination of operating information and all the programs that are being used by the computer.” It is a set of instructions to direct computers to perform a specific task depending upon thususer’s instructions.
The software can be written in both high and low-level languages. Low-level language is also known as machine code and is faster because it doesn’t require any compiler and directly communicates with the computer. A high-level language is pretty similar to a human language, and therefore can be easily understood by the developers. High-level language requires the compiler to translate commands to the computer.
Programming and algorithms can be termed as commands given to the computer to perform actions. Programming leads to executable programs from a computing problem and involves developing, generating, and analysing algorithms. Algorithms refer to an act done involving a step-by-step process to solve a problem. It is a set of logic written in software.
There are two types of software; operating software that helps in operation and system software necessary to run a system. Operating software can be rewritten and changed according to demand, but system software cannot be altered. If developers require any alterations, they would have to develop new software.
There are various topics that can be considered for research dissertation purposes under this theme, a list of which is given below.
- Application of algorithms.
- Importance of approximation algorithms on graphs.
- Critical analysis of data structures on trees.
- Evaluation and implementation of new algorithms.
- System software: A link to communicate hardware.
- Difference between binary dispatching and multiple dispatching.
- Analysis of plan sweep techniques.
- Investigation of software support to drivers of devices.
- Intelligent interface for database systems.
- Analysis of function and types of union-find.
- The usefulness of different coding languages.
- Application of basic hardware knowledge and math skills.
- Analysis of the design of converter based on new moduli.
- Analysis of information travelling via software.
- Evaluation and implementation of heuristic algorithms.
- Development of applications using Java.
- Analysis of fault tolerance in a network by using simulation.
- Importance of system software for computers.
- Effects of larger integer module operations.
- Consequences of wrong commands in coding.
- Investigation of the coding language of system software.
- Analysis of feasibility environment of platform.
- Evaluation of heuristic algorithms for generating clusters.
- Critical analysis of fixed control variable.
- Analysis of design of converter with large dynamic range.
- Ways to recover corrupted software.
- Analysis of fault tolerance of sorting network.
- Analysis of the difference between LAN and WAN.
- Development of an algorithm for a one-way hashing system.
- Relation between dynamic access and fixed values.
- Importance of right language selection while coding.
- Study of optimization problems.
- Analysis of security frameworks for web services.
- Investigating algorithms techniques.
- Partial persistence of algorithms vs others.
- Study of time and space problems of algorithmic functions.
- Effects of linear and logarithmic factors over programming.
- Discussion about union-find with deletion.
- Importance of data structure for bridge core problems.
- Consequences of fault in interconnected networks.
- Difference between rooted and unrooted tree.
Information Systems Dissertation Topics
Information systems refer to a group of people and computers that are being used for the interpretation of all kinds of information. Computer-based information systems are a very interesting topic for research. It includes all information regarding decision making, management support, and operations and can also be used to access the database.
There is an obvious difference between computer systems, information systems, and business processes. The information system provides the tools to manage businesses successfully.
An information system can be said to be a workstation where humans and machines work together towards the success of a business. One such example is Wal-Mart. The company is entirely based on information systems and has connected its suppliers, vendors, customers and together.
It deals with a large number of data and consists of hardware, software, network, and telecommunications of the operation. Below is a list of research topics in the field of information systems for you to base your dissertation on:
- Analysis of challenges in building information systems for any organisation.
- Impact of cyberinfrastructure on the customer.
- Role of information system in scientific innovations.
- The usefulness of information systems for businesses.
- Advantages of information systems.
- Access to information systems by employees anywhere in the world.
- Preparation of a database management system.
- Analysis and solution of database management systems.
- Study of support of information system to hardware.
- Managing information systems of big stores, The case of Walmart.
- Analysis of information system built for E-learning.
- Critical analysis of the changing nature of the web.
- Role of information system in decision making of disruptions.
- Examine customer response through the information system.
- Investigate the impact of a virus in the network
- Relationship between I.T education and an organization.
- Role of information system in global warming.
- Investigate the reason for adopting green information systems.
- Analysis of the between social networks and information systems.
- Role of information system in dealing with complex business problems.
Important Notes:
As a computing engineering student looking to get good grades, it is essential to develop new ideas and experiment with existing computing engineering theories – i.e., to add value and interest in your research topic.
The field of computing engineering is vast and interrelated to so many other academic disciplines like civil engineering , finance , construction , law , healthcare , mental health , artificial intelligence , tourism , physiotherapy , sociology , management , marketing and nursing . That is why it is imperative to create a project management dissertation topic that is articular, sound, and actually solves a practical problem that may be rampant in the field.
We can’t stress how important it is to develop a logical research topic; it is the basis of your entire research. There are several significant downfalls to getting your topic wrong; your supervisor may not be interested in working on it, the topic has no academic creditability, the research may not make logical sense, there is a possibility that the study is not viable.
This impacts your time and efforts in writing your dissertation as you may end up in the cycle of rejection at the very initial stage of the dissertation. That is why we recommend reviewing existing research to develop a topic, taking advice from your supervisor, and even asking for help in this particular stage of your dissertation.
While developing a research topic, keeping our advice in mind will allow you to pick one of the best computing engineering dissertation topics that fulfill your requirement of writing a research paper and add to the body of knowledge.
Therefore, it is recommended that when finalizing your dissertation topic, you read recently published literature to identify gaps in the research that you may help fill.
Remember- dissertation topics need to be unique, solve an identified problem, be logical, and be practically implemented. Take a look at some of our sample computing engineering dissertation topics to get an idea for your own dissertation.
How to Structure your Dissertation on Computing Engineering
A well-structured dissertation can help students to achieve a high overall academic grade.
- A Title Page
- Acknowledgements
- Declaration
- Abstract: A summary of the research completed
- Table of Contents
- Introduction : This chapter includes the project rationale, research background, key research aims and objectives, and the research problems to be addressed. An outline of the structure of a dissertation can also be added to this chapter.
- Literature Review : This chapter presents relevant theories and frameworks by analysing published and unpublished literature available on the chosen research topic, in light of research questions to be addressed. The purpose is to highlight and discuss the relative weaknesses and strengths of the selected research area whilst identifying any research gaps. Break down of the topic, and key terms can have a positive impact on your dissertation and your tutor.
- Methodology: The data collection and analysis methods and techniques employed by the researcher are presented in the Methodology chapter which usually includes research design, research philosophy, research limitations, code of conduct, ethical consideration, data collection methods and data analysis strategy .
- Findings and Analysis: Findings of the research are analysed in detail under the Findings and Analysis chapter. All key findings/results are outlined in this chapter without interpreting the data or drawing any conclusions. It can be useful to include graphs , charts, and tables in this chapter to identify meaningful trends and relationships.
- Discussion and Conclusion: The researcher presents his interpretation of results in this chapter, and states whether the research hypothesis has been verified or not. An essential aspect of this section of the paper is to draw a linkage between the results and evidence from the literature. Recommendations with regards to implications of the findings and directions for the future may also be provided. Finally, a summary of the overall research, along with final judgments, opinions, and comments, must be included in the form of suggestions for improvement.
- References: This should be completed in accordance with your University’s requirements
- Bibliography
- Appendices: Any additional information, diagrams, graphs that were used to complete the dissertation but not part of the dissertation should be included in the Appendices chapter. Essentially, the purpose is to expand the information/data.
About ResearchProspect Ltd
ResearchProspect is a UK-based academic writing service that provides help with Dissertation Proposal Writing , Ph.D. Proposal Writing , Dissertation Writing , Dissertation Editing and Improvement .
For further assistance with your dissertation, take a look at our full dissertation writing service .
Our team of writers is highly qualified. Our writers are experts in their respective fields. They have been working in the industry for a long time. Thus they are aware of the issues and the trends of the industry they are working in.
Need more Topics.?
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find dissertation topics about computing engineering.
To find computing engineering dissertation topics:
- Explore emerging technologies.
- Investigate industry challenges.
- Review recent research papers.
- Consider AI, cybersecurity, IoT.
- Brainstorm software/hardware innovations.
- Select a topic aligning with your passion and career aspirations.
You May Also Like
US foreign policy has evolved significantly since the country’s inception. Since 1776, the US government has employed various strategies to protect and advance its interests abroad
Need interesting coronavirus (Covid-19) nursing dissertation topics? Here are the trending dissertation titles so you can choose the most suitable one.
We have compiled a list of 30 appealing dissertation topic ideas on company law and corporate law for you to excel in your company law dissertation.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
ScholarWorks@UMass Amherst
Home > Engineering > ECE > Electrical & Computer Engineering Masters Theses Collection

Electrical & Computer Engineering Masters Theses Collection
Theses from 2024 2024.
Extracting DNN Architectures Via Runtime Profiling On Mobile GPUs , Dong Hyub Kim, Electrical & Computer Engineering
Semantic-Aware Blockchain Architecture Design for Lifelong Edge-enabled Metaverse , Ning Wang, Electrical & Computer Engineering
Blockchain Design for a Secure Pharmaceutical Supply Chain , Zhe Xu, Electrical & Computer Engineering
Collaborative Caching and Computation Offloading for Intelligent Transportation Systems enabled by Satellite-Airborne-Terrestrial Networks , Shulun Yang, Electrical & Computer Engineering
Protecting Return Address Integrity for RISC-V via Pointer Authentication , yuhe zhao, Electrical & Computer Engineering
Theses from 2023 2023
Fingerprinting for Chiplet Architectures Using Power Distribution Network Transients , Matthew G. Burke, Electrical & Computer Engineering
Design and Fabrication of a Trapped Ion Quantum Computing Testbed , Christopher A. Caron, Electrical & Computer Engineering
Analog Cancellation of a Known Remote Interference: Hardware Realization and Analysis , James M. Doty, Electrical & Computer Engineering
Electrothermal Properties of 2D Materials in Device Applications , Samantha L. Klein, Electrical & Computer Engineering
Ablation Study on Deeplabv3+ for Semantic Segmentation , Bowen Lei, Electrical & Computer Engineering
A Composability-Based Transformer Pruning Framework , Yuping Lin, Electrical & Computer Engineering
A Model Extraction Attack on Deep Neural Networks Running on GPUs , Jonah G. O'Brien Weiss, Electrical & Computer Engineering
Heterogeneous IoT Network Architecture Design for Age of Information Minimization , Xiaohao Xia, Electrical & Computer Engineering
Theses from 2022 2022
Theory and Analysis of Backprojection Processing for Interferometric SAR , Marc Closa Tarres, Electrical & Computer Engineering
Unpaired Skeleton-to-Photo Translation for Sketch-to-Photo Synthesis , Yuanzhe Gu, Electrical & Computer Engineering
Integration of Digital Signal Processing Block in SymbiFlow FPGA Toolchain for Artix-7 Devices , Andrew T. Hartnett, Electrical & Computer Engineering
Planar Ultra-Wideband Modular Antenna (PUMA) Arrays for High-Volume Manufacturing on Organic Laminates and BGA Interfaces , James R. LaCroix, Electrical & Computer Engineering
Planar Transmission-Line Metamaterials on an Irregular Grid , Tina E. Maurer, Electrical & Computer Engineering
Formally Verifiable Synthesis Flow In FPGAs , Anurag V. Muttur, Electrical & Computer Engineering
Theses from 2021 2021
Graph-Algorithm Based Verification on Network Configuration Robustness , Zibin Chen, Electrical & Computer Engineering
A Cloud Infrastructure for Large Scale Health Monitoring in Older Adult Care Facilities , Uchechukwu Gabriel David, Electrical & Computer Engineering
Internet Infrastructures for Large Scale Emulation with Efficient HW/SW Co-design , Aiden K. Gula, Electrical & Computer Engineering
Mtemp: An Ambient Temperature Estimation Method Using Acoustic Signal on Mobile Devices , Hao Guo, Electrical & Computer Engineering
BENCHMARKING SMALL-DATASET STRUCTURE-ACTIVITY-RELATIONSHIP MODELS FOR PREDICTION OF WNT SIGNALING INHIBITION , Mahtab Kokabi, Electrical & Computer Engineering
ACTION : Adaptive Cache Block Migration in Distributed Cache Architectures , Chandra Sekhar Mummidi, Electrical & Computer Engineering
Modeling and Characterization of Optical Metasurfaces , Mahsa Torfeh, Electrical & Computer Engineering
TickNet: A Lightweight Deep Classifier for Tick Recognition , Li Wang, Electrical & Computer Engineering
Lecture Video Transformation through An Intelligent Analysis and Post-processing System , Xi Wang, Electrical & Computer Engineering
Correcting For Terrain Interference, Attenuation, and System Bias for a Dual Polarimetric, X-Band Radar , Casey Wolsieffer, Electrical & Computer Engineering
Theses from 2020 2020
Numerical Simulation of Thermoelectric Transport in Bulk and Nanostructured SiSn Alloys , Venkatakrishna Dusetty, Electrical & Computer Engineering
Deep Reinforcement Learning For Distributed Fog Network Probing , Xiaoding Guan, Electrical & Computer Engineering
COMPRESSIVE PARAMETER ESTIMATION VIA APPROXIMATE MESSAGE PASSING , Shermin Hamzehei, Electrical & Computer Engineering
Metric Learning via Linear Embeddings for Human Motion Recognition , ByoungDoo Kong, Electrical & Computer Engineering
Compound Effects of Clock and Voltage Based Power Side-Channel Countermeasures , Jacqueline Lagasse, Electrical & Computer Engineering
Network Virtualization and Emulation using Docker, OpenvSwitch and Mininet-based Link Emulation , Narendra Prabhu, Electrical & Computer Engineering
Thermal Transport Modeling Of Semiconductor Materials From First Principles , Aliya Qureshi, Electrical & Computer Engineering
CROSSTALK BASED SIDE CHANNEL ATTACKS IN FPGAs , Chethan Ramesh, Electrical & Computer Engineering
Accelerating RSA Public Key Cryptography via Hardware Acceleration , Pavithra Ramesh, Electrical & Computer Engineering
Real-Time TDDFT-Based Filtered Spectroscopy , Ivan Williams, Electrical & Computer Engineering
Perception System: Object and Landmark Detection for Visually Impaired Users , Chenguang Zhang, Electrical & Computer Engineering
Theses from 2019 2019
An Empirical Analysis of Network Traffic: Device Profiling and Classification , Mythili Vishalini Anbazhagan, Electrical & Computer Engineering
Pre-Travel Training And Real-Time Guidance System For People With Disabilities In Indoor Environments , Binru Cao, Electrical & Computer Engineering
Energy Efficiency of Computation in All-spin Logic: Projections and Fundamental Limits , Zongya Chen, Electrical & Computer Engineering
Improving Resilience of Communication in Information Dissemination for Time-Critical Applications , Rajvardhan Somraj Deshmukh, Electrical & Computer Engineering
InSAR Simulations for SWOT and Dual Frequency Processing for Topographic Measurements , Gerard Masalias Huguet, Electrical & Computer Engineering
A Study on Controlling Power Supply Ramp-Up Time in SRAM PUFs , Harshavardhan Ramanna, Electrical & Computer Engineering
The UMass Experimental X-Band Radar (UMAXX): An Upgrade of the CASA MA-1 to Support Cross-Polarization Measurements , Jezabel Vilardell Sanchez, Electrical & Computer Engineering
A Video-Based System for Emergency Preparedness and Recovery , Juechen Yin, Electrical & Computer Engineering
Theses from 2018 2018
Phonon Transport at Boundaries and Interfaces in Two-Dimensional Materials , Cameron Foss, Electrical & Computer Engineering
SkinnySensor: Enabling Battery-Less Wearable Sensors Via Intrabody Power Transfer , Neev Kiran, Electrical & Computer Engineering
Immersive Pre-travel Training Application for Seniors and People with Disabilities , Yang Li, Electrical & Computer Engineering
Analog Computing using 1T1R Crossbar Arrays , Yunning Li, Electrical & Computer Engineering
On-Chip Communication and Security in FPGAs , Shivukumar Basanagouda Patil, Electrical & Computer Engineering
CROWDSOURCING BASED MICRO NAVIGATION SYSTEM FOR VISUALLY IMPAIRED , Quan Shi, Electrical & Computer Engineering
AN EVALUATION OF SDN AND NFV SUPPORT FOR PARALLEL, ALTERNATIVE PROTOCOL STACK OPERATIONS IN FUTURE INTERNETS , Bhushan Suresh, Electrical & Computer Engineering
Applications Of Physical Unclonable Functions on ASICS and FPGAs , Mohammad Usmani, Electrical & Computer Engineering
Improvements to the UMASS S-Band FM-CW Vertical Wind Profiling Radar: System Performance and Data Analysis. , Joseph Waldinger, Electrical & Computer Engineering
Theses from 2017 2017
AutoPlug: An Automated Metadata Service for Smart Outlets , Lurdh Pradeep Reddy Ambati, Electrical & Computer Engineering
SkyNet: Memristor-based 3D IC for Artificial Neural Networks , Sachin Bhat, Electrical & Computer Engineering
Navigation Instruction Validation Tool and Indoor Wayfinding Training System for People with Disabilities , Linlin Ding, Electrical & Computer Engineering
Energy Efficient Loop Unrolling for Low-Cost FPGAs , Naveen Kumar Dumpala, Electrical & Computer Engineering
Effective Denial of Service Attack on Congestion Aware Adaptive Network on Chip , Vijaya Deepak Kadirvel, Electrical & Computer Engineering
VIRTUALIZATION OF CLOSED-LOOP SENSOR NETWORKS , Priyanka Dattatri Kedalagudde, Electrical & Computer Engineering
The Impact of Quantum Size Effects on Thermoelectric Performance in Semiconductor Nanostructures , Adithya Kommini, Electrical & Computer Engineering
MAGNETO-ELECTRIC APPROXIMATE COMPUTATIONAL FRAMEWORK FOR BAYESIAN INFERENCE , Sourabh Kulkarni, Electrical & Computer Engineering
Time Domain SAR Processing with GPUs for Airborne Platforms , Dustin Lagoy, Electrical & Computer Engineering
Query on Knowledge Graphs with Hierarchical Relationships , Kaihua Liu, Electrical & Computer Engineering
HIGH PERFORMANCE SILVER DIFFUSIVE MEMRISTORS FOR FUTURE COMPUTING , Rivu Midya, Electrical & Computer Engineering
Achieving Perfect Location Privacy in Wireless Devices Using Anonymization , Zarrin Montazeri, Electrical & Computer Engineering
KaSI: a Ka-band and S-band Cross-track Interferometer , Gerard Ruiz Carregal, Electrical & Computer Engineering
Analyzing Spark Performance on Spot Instances , Jiannan Tian, Electrical & Computer Engineering
Indoor Navigation For The Blind And Visually Impaired: Validation And Training Methodology Using Virtual Reality , Sili Wang, Electrical & Computer Engineering
Efficient Scaling of a Web Proxy Cluster , Hao Zhang, Electrical & Computer Engineering
ORACLE GUIDED INCREMENTAL SAT SOLVING TO REVERSE ENGINEER CAMOUFLAGED CIRCUITS , Xiangyu Zhang, Electrical & Computer Engineering
Theses from 2016 2016
Seamless Application Delivery Using Software Defined Exchanges , Divyashri Bhat, Electrical & Computer Engineering
PROCESSOR TEMPERATURE AND RELIABILITY ESTIMATION USING ACTIVITY COUNTERS , Mayank Chhablani, Electrical & Computer Engineering
PARQ: A MEMORY-EFFICIENT APPROACH FOR QUERY-LEVEL PARALLELISM , Qianqian Gao, Electrical & Computer Engineering
Accelerated Iterative Algorithms with Asynchronous Accumulative Updates on a Heterogeneous Cluster , Sandesh Gubbi Virupaksha, Electrical & Computer Engineering
Improving Efficiency of Thermoelectric Devices Made of Si-Ge, Si-Sn, Ge-Sn, and Si-Ge-Sn Binary and Ternary Alloys , Seyedeh Nazanin Khatami, Electrical & Computer Engineering
6:1 PUMA Arrays: Designs and Finite Array Effects , Michael Lee, Electrical & Computer Engineering
Protecting Controllers against Denial-of-Service Attacks in Software-Defined Networks , Jingrui Li, Electrical & Computer Engineering
INFRASTRUCTURE-FREE SECURE PAIRING OF MOBILE DEVICES , Chunqiu Liu, Electrical & Computer Engineering
Extrinsic Effects on Heat and Electron Transport In Two-Dimensional Van-Der Waals Materials- A Boltzmann Transport Study , Arnab K. Majee, Electrical & Computer Engineering
SpotLight: An Information Service for the Cloud , Xue Ouyang, Electrical & Computer Engineering
Localization, Visualization And Evacuation Guidance System In Emergency Situations , Jingyan Tang, Electrical & Computer Engineering
Variation Aware Placement for Efficient Key Generation using Physically Unclonable Functions in Reconfigurable Systems , Shrikant S. Vyas, Electrical & Computer Engineering
EVALUATING FEATURES FOR BROAD SPECIES BASED CLASSIFICATION OF BIRD OBSERVATIONS USING DUAL-POLARIZED DOPPLER WEATHER RADAR , Sheila Werth, Electrical & Computer Engineering
Theses from 2015 2015
Quality Factor of Horizontal Wire Dipole Antennas near Planar Conductor or Dielectric Interface , Adebayo Gabriel Adeyemi, Electrical & Computer Engineering
Evaluation of Two-Dimensional Codes for Digital Information Security in Physical Documents , Shuai Chen, Electrical & Computer Engineering
Design and Implementation of a High Performance Network Processor with Dynamic Workload Management , Padmaja Duggisetty, Electrical & Computer Engineering
Wavelet-Based Non-Homogeneous Hidden Markov Chain Model For Hyperspectral Signature Classification , Siwei Feng, Electrical & Computer Engineering
DEVELOPMENT OF INFRARED AND TERAHERTZ BOLOMETERS BASED ON PALLADIUM AND CARBON NANOTUBES USING ROLL TO ROLL PROCESS , Amulya Gullapalli, Electrical & Computer Engineering
Development of Prototypes of a Portable Road Weather Information System , Meha Kainth, Electrical & Computer Engineering
ADACORE: Achieving Energy Efficiency via Adaptive Core Morphing at Runtime , Nithesh Kurella, Electrical & Computer Engineering
Architecting SkyBridge-CMOS , Mingyu Li, Electrical & Computer Engineering
Function Verification of Combinational Arithmetic Circuits , Duo Liu, Electrical & Computer Engineering
ENERGY EFFICIENCY EXPLORATION OF COARSE-GRAIN RECONFIGURABLE ARCHITECTURE WITH EMERGING NONVOLATILE MEMORY , Xiaobin Liu, Electrical & Computer Engineering
Development of a Layout-Level Hardware Obfuscation Tool to Counter Reverse Engineering , Shweta Malik, Electrical & Computer Engineering
Energy Agile Cluster Communication , Muhammad Zain Mustafa, Electrical & Computer Engineering
Architecting NP-Dynamic Skybridge , Jiajun Shi, Electrical & Computer Engineering
Advanced Search
- Notify me via email or RSS
- Collections
- Disciplines
Author Corner
- Login for Faculty Authors
- Faculty Author Gallery
- Expert Gallery
- University Libraries
- Electrical and Computer Engineering Website
- UMass Amherst
This page is sponsored by the University Libraries.
© 2009 University of Massachusetts Amherst • Site Policies
Privacy Copyright
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Computer Engineering
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
- Last »
- Computer Science Follow Following
- Artificial Intelligence Follow Following
- Software Engineering Follow Following
- Data Mining Follow Following
- Machine Learning Follow Following
- Computer Networks Follow Following
- Engineering Follow Following
- Image Processing Follow Following
- Wireless Sensor Networks Follow Following
- Cloud Computing Follow Following
Enter the email address you signed up with and we'll email you a reset link.
- Academia.edu Publishing
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Browse Works
- Engineering
Computer Engineering
Computer engineering research papers/topics, case-based reasoning system for prediction of fuel consumption by haulage trucks in open–pit mines.
Abstract: The shovel-truck system is commonly used in open-pit mining operations. Truck haulage cost constitutes about 26% of open-pit mining costs as the trucks are mostly powered by diesel whose cost is escalating annually. Therefore, reducing fuel consumption could lead to a significant decrease in overall mining costs. Various methods have been proposed to improve fuel efficiency in open-pit mines. Case-based reasoning (CBR) can be used to estimate fuel consumption by haulage trucks. In ...
Meteorological influence on eLoran accuracy
Abstract: Stringent accuracy requirements need to be met for eLoran deployment in marine navigation and harbour entrance and approach. A good accuracy model is therefore required to predict the positioning accuracy at the user’s receiver locations. Accuracy depends on the variations of additional secondary factors (ASFs) and the primary factor delay. The changes in the air refractive index caused variations in the primary factor (PF) delay of the eLoran signal, and current eLoran accuracy ...
A Model for Providing List of Reliable Providers for Grid Computing
Abstract: Grid computing is an interconnected computer system, where machines share resources that are highly heterogeneous. Reliability is the probability that a process will successfully perform its prescribed task without any failure at a given point of time. Hence, ensuring reliable transactions plays a vital role in grid computing. The main objective of the paper is to develop a reliable and robust two way trust model for the Grid system. Thus the goals of this proposed trust model are ...
Query Processing with Respect to Location in Wireless Broadcasting
Abstract: The wireless communication involves a client server communication i.e. the client needs to send a request for performing a process; it can perform only after the response of the server. Large number of request will result the load balance in the server, which cause process delay. It has been resolved by using wireless broadcast client server communication. To communicate with server the client use fee based cellular type network to achieve a responsible operating range. For avoidin...
A preliminary application of a machine learning model for the prediction of the load variation in three-point bending tests based on acoustic emission signals
Abstract: The load variation during three-point bending (TPB) tests on prismatic Nestos (Greece) marble specimens instrumented by piezoelectric sensors is predicted using acoustic emission (AE) signals. The slope of the cumulative amplitude vs the predicted load curve is potentially useful for determining the forthcoming specimen failure as well as the indirect tensile strength of the material. The optimum artificial neural networks (ANN) model was selected based on a comparison of different...
Enhancing Personalization and Sales Conversion in E-Commerce: The Role of AI in the App Shop Experience
A shopping application that can be easily designed and built using the Flutter framework. “Shop AI” offers customers a good platform and efficient shopping experience in terms of convenience and functionality. this report focusing on the design and development framework. It explores application architecture and shows how Flutter’s versatility helps developers create cross-platform, responsive, and visually appealing user interfaces. Discover the main features of ”Shop AI” by searchi...
Algorithms and Data Structures Part 4: Searching and Sorting (Wikipedia Book 2014)
Searching 1 Search algorithm 1 Linear search 3 Binary search algorithm 6 Sorting 14 Sorting algorithm 14 Bubble sort 25 Quicksort 31 Merge sort 43 Insertion sort 52 Heapsort 59 References Article Sources and Contributors 66 Image Sources, Licenses and Contributors 68
E-Store Project Software Requirements Specification Version <4.0>
Introduction The introduction of the Software Requirements Specification (SRS) provides an overview of the entire SRS with purpose, scope, definitions, acronyms, abbreviations, references and overview of the SRS. The aim of this document is to gather and analyze and give an in-depth insight of the complete Marvel Electronics and Home Entertainment software system by defining the problem statement in detail. Nevertheless, it also concentrates on the capabilities required by stakeholders and...
Skin Cancer Diagnostics with a Smartphone App
Melanoma is one of the deadliest types of skin cancer and can be difficult to treat when it's advanced. To reduce mortality rates, early detection is key. In order to do this, computer-aided systems have been developed to help dermatologists diagnose the condition. To make it more accessible to the public, researchers are working on creating portable, at-home diagnostic systems. An Android-based smartphone application utilizing image capture, preprocessing, and segmentation was developed to e...
Design Control and Monitoring System Of Water Distribution Networks
ABSTRACT Nowadays, water distribution network automation is becoming more and more popular day by day due to its numerous advantages, an internet-based water distribution network system focuses on monitoring and controlling water distribution network instance. Water distribution network face wastage of water due to improper water supply management, non-monitoring in real time, this caused scarcity of water, scarcity of water consider mainly problem in cities. water distribution network auto...
2D Radar Antenna Orientation and Control
ABSTRACT The RADAR system is the first step and much more important and it has much more effect than the other step in the RADAR system works. The RADAR is used in different applications and systems, almost of these applications need high precision, and it's depending on the accuracy of RADAR ANTENNA orientation. Much research has been done and different systems designed to obtain a result within a permissible range. Design RADAR ANTENNA orientation and control system using FPGA and stepper m...
Design and Optimization of W-Tailored Optical Fiber
ABSTRACT This research work studies the temperature effects in W-shaped core refractive index optical fiber. The work designs an optimized W-tailored optical fiber (OWTOF) that checks the effect of rising temperatures in W-tailored optical fiber (WTOF) for better communication. Initially, an introduction to the general concept of optical fibers including tailored optical fibers (TOF), temperature effects and models is presented as a background. This is followed by studies on existing litera...
Design of Digital Image Enhancement System Using Noise Filtering Techniques
ABSTRACT Noise Reduction in digital image is one of the most important and difficult techniques in image research. The aim of Noise Reduction in digital image is to improve the visual appearance of an image, or to provide a better transform representation for another automated image processing. Many images like medical images, satellite images, aerial images and even real-life photographs suffer from viewing, removing blurring and noise, increasing contrast, etc. Reducing noise from the dig...
Design And Implementation Of An Automated Inventory Management System Case Study: Smart Shoppers Masaka
ABSTRACT The general purpose was to develop an efficient Inventory Management System (IMS) that improves service delivery at Smart shoppers’ Masaka. The main objectives were to collect and analyze user requirements that provide the researchers with enough information of what the system users want the system to accomplish, to design an Automated Inventory Management System, to implement a prototype and to test and validate the designed prototype. The methodology used includes Interviews, Que...
Inspired Safari Adventures Official Website
ABSTRACT This project is aimed to work as one of the marketing procedures and cores for Inspired Safari Adventures which acts as a general online website were the all public can view and understand more about the company. The users of this website are generally all the people who want to know about Inspired Safari Adventures in reference to the website components for example understanding the company location activities and so much more as illustrated in the website. The other users include i...
Projects, thesis, seminars, research papers, termpapers topics in Computer Engineering. Computer Engineering projects, thesis, seminars and termpapers topic and materials
Popular Papers/Topics
Building and assembling a computer system, digital combination lock system, design and construction of four-way traffic light, microcontroller based digital code lock, a technical report on student industrial work experience scheme (siwes) on laptop repair, design of a patient heartbeat and temperature monitor using rf, automobile battery preservative, network interconnection devices, smart card technology, design and implementation of a software intercom on lan, design & construction of 8 channel buzzer using microcontroller, appliances control through sms, design and simulation of a secured wireless network (a case study of houdegbe north american university benin), microcontroller based automation system, design and implementation of an internet of things (iot) based smart waste bin for fill level monitoring and biodegradability detection.
Privacy Policy | Refund Policy | Terms | Copyright | © 2024, Afribary Limited. All rights reserved.
Princeton University
Princeton engineering, grad alum avi wigderson wins turing award for groundbreaking insights in computer science.
By Scott Lyon
April 10, 2024

Avi Wigderson has won the 2023 Turing Award from the Association for Computing Machinery. Photos by Andrea Kane, courtesy of the Institute for Advanced Study
Princeton graduate alumnus Avi Wigderson has won the 2023 A.M. Turing Award from the Association for Computing Machinery (ACM), recognizing his profound contributions to the mathematical underpinnings of computation.
The Turing Award is considered the highest honor in computer science, often called the “Nobel Prize of Computing.”
Wigderson, the Herbert H. Maass Professor in the Institute for Advanced Study ’s School of Mathematics, earned his Ph.D. from Princeton in 1983 in what was then the Department of Electrical Engineering and Computer Science.
In addition to the Turing Award, he is also the recipient of the 2021 Abel Prize , considered the highest honor in mathematics, from the Norwegian Academy of Science and Letters. He is the only person ever to have won both the Abel Prize and the Turing Award.
“Mathematics is foundational to computer science and Wigderson’s work has connected a wide range of mathematical sub-areas to theoretical computer science,” ACM President Yannis Ioannidis said in a statement released by the organization.
“Avi Wigderson is a giant in the field of theoretical computer science, bringing fundamental insights to deep questions about what can — or cannot — be computed efficiently,” said Jennifer Rexford , Princeton’s provost and Gordon Y.S. Wu Professor of Engineering . “He is also a wonderful colleague and a longtime friend of the University.”

Wigderson is best known for his work on computational complexity theory, especially the role of randomness in computation. Namely, in a series of highly influential works from the 1990s, Wigderson and colleagues proved that computation can be efficient without randomness, shaping algorithm design ever since. He has also established important ideas in several other areas, including protocol design and cryptography, which enables much of today’s digital infrastructure.
While his work is primarily mathematical, the notions he is trying to understand through that work are computational, Wigderson said in a video released by the Institute for Advanced Study (IAS). That approach has earned him a reputation as one of the most versatile minds in either discipline.
“He is one of the most central people in theoretical computer science, generally,” said Ran Raz , a professor of computer science at Princeton, who was Wigderson’s graduate student at the Hebrew University in Jerusalem.
Wigderson has influenced countless students and thinkers, having mentored more than 100 postdocs and collaborated with an unusually broad range of scholars. “He is always able to make connections between things,” Raz said.
“He’s an inspiration,” said Pravesh Kothari , an assistant professor of computer science at Princeton and a former postdoctoral advisee of Wigderson’s at IAS. “He’s a role model. If I could become 10 percent of the researcher he is, it would be a fantastic success for my career.” Kothari also said Wigderson implores young researchers to view the entire endeavor as one field. And that approach shows up in all of his work, connecting disparate problems from sub-disciplines that are normally seen as unrelated.
His research has “set the agenda in theoretical computer science” for decades, Google Senior Vice President Jeff Dean said in the ACM press release. His work has also found its way directly into everyday life.
In a series of findings at the intersection of mathematics and computer science, Wigderson cemented what is known as the zero-knowledge proof, critical in cryptography and digital security. The technique has found purchase in modern applications of privacy, compliance, identity verification and blockchain technology.
Raz said he was amazed at how far Wigderson’s ideas had traveled, from the depths of mathematics to the technologies that enable global enterprise to the everyday lives of billions of people. “It’s quite amazing that these things can be made practical,” Raz said.
Szymon Rusinkiewicz , the David M. Siegel ’83 Professor of Computer Science and department chair, added that Wigderson has been a great friend to Princeton’s computer science community, including to students and young scholars. “He has had a great influence throughout the world of computer science, and we especially feel that at Princeton, where he has been a great mentor and collaborator.”
Wigderson is the recipient of numerous other awards, including the 1994 IMU Abacus Medal, the 2009 Gödel Prize and the 2019 Donald E. Knuth Prize. He is currently a Fellow of the ACM, a member of the American Academy of Arts and Sciences and a member of the National Academy of Sciences.
At Princeton, in addition to his Ph.D., he earned an M.S.E. in 1981, an M.A. in 1982, and he later served on Princeton’s computer science faculty from 1990 to 1992. He joined IAS in 1999, where he established the program in Computer Science and Discrete Mathematics.
Related News

Episode 4: Bethany Beardslee Winham and Chris Winham

Engineering students recognize exceptional teachers and mentors

The science of static shock jolted into the 21st century

Episode 3: Haydn Seek

Episode 1: Stanley Jordan Pulls Out All the Stops

Episode 2: That Magic Touch

Applied Math
Related department.

Computer Science

IMAGES
VIDEO
COMMENTS
This conceptual research paper is written to discuss the implementation of the A.D.A.B model in technology -based and technical subjects such as Computer Science, Engineering, Technical and so on ...
Covers applications of computer science to the mathematical modeling of complex systems in the fields of science, engineering, and finance. Papers here are interdisciplinary and applications-oriented, focusing on techniques and tools that enable challenging computational simulations to be performed, for which the use of supercomputers or ...
Communications Preferences. Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore. Contact Us.
Journal of Computer Science and Technology is an international platform publishing high quality, refereed papers in all aspects of computer science and technology. Sponsored by the Institute of Computing Technology (ICT), Chinese Academy of Sciences (CAS), and China Computer Federation (CCF). Jointly published by ICT, CAS and Springer on a ...
The journal Computers & Electrical Engineering provides rapid publication of topical research into the integration of computer technology and computational techniques with electrical and communication and information systems. The journal publishes papers featuring novel implementations of …. View full aims & scope.
Review of Computer Engineering Studies (RCES) is an international, scholarly and peer-reviewed journal dedicated to providing scientists, engineers and technicians with the latest developments on computer science.The journal offers a window into the most recent discoveries in four categories, namely, computing (computing theory, scientific computing, cloud computing, high-performance computing ...
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching ...
University of Nevada, Reno - Department of Computer Science and Engineering. Date Written: April 11, 2024 ... This paper explores Generative Artificial Intelligence (GenAI) as a groundbreaking solution. By leveraging multi-modal and semantic communication techniques, GenAI can generate text and image data, significantly enhancing information ...
This research introduces DesignQA, a novel benchmark aimed at evaluating the proficiency of multimodal large language models (MLLMs) in comprehending and applying engineering requirements in technical documentation. Developed with a focus on real-world engineering challenges, DesignQA uniquely combines multimodal data-including textual design requirements, CAD images, and engineering drawings ...
Human-centered Cybersecurity Research — Anthropological Findings from Two Longitudinal Studies, Anwesh Tuladhar. PDF. Learning State-Dependent Sensor Measurement Models To Improve Robot Localization Accuracy, Troi André Williams. PDF. Human-centric Cybersecurity Research: From Trapping the Bad Guys to Helping the Good Ones, Armin Ziaie Tabari
All Articles in Computer Engineering. 23,498 full-text articles. Page 1 of 926. Optimization Of Memory Management Using Machine Learning , Luke Bartholomew 2024 Southern Adventist University. Enhancing Information Architecture With Machine Learning For Digital Media Platforms , Taylor N. Mietzner 2024 Georgia Southern University.
View All Issues. International Journal of Computer Engineering in Research Trends (IJCERT) is a peer-reviewed, open access journal that publishes high-quality research papers, reviews, short communications, and notes in the field of computer science engineering and its research trends. The journal covers a wide range of topics in computer ...
Journal of Engineering Research (JER) is an international, peer reviewed journal which publishes full length original research papers, reviews and case studies related to all areas of Engineering such as: Civil, Mechanical, Industrial, Electrical, Computer, Chemical, Petroleum, Aerospace, Architectural, etc. JER is intended to serve a wide range of educationists, scientists, specialists ...
Original research papers, state-of-the-art reviews are invited for publication in all areas of Computer Science & Computer Engineering. Authors are solicited to contribute to the journal by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the areas ...
Computer science ( CS ) majors are in high demand and account for a large part of national computer and information technology job market applicants. Employment in this sector is projected to grow 12% between 2018 and 2028, which is faster than the average of all other occupations. Published data are available on traditional non-computer ...
Electrical and Computer Engineering Research Resources: Find Articles & Papers. ... Contains full-text papers on optics and photonics from SPIE journals and proceedings published since 1990. Approximately 15,000 new papers will be added each year. Subject Guide. Grainger Engineering Library
A unique and robust research environment. At Michigan, faculty and students in CSE have the unique opportunity to collaborate with peers from across 19 highly-acclaimed schools and colleges to conduct impactful, broad ranging, and highly interdisciplinary research. Resources at the University include leading schools of medicine, business ...
Therefore, this paper proposes an energy-efficient and computationally lightweight solution deployed on an IoT device, i.e., esp32-cam, that can recognize nine (9) different plant diseases using a quantized CNN (Q-CNN) approach. Q-CNN speeds up computation and reduces the model size while maintaining optimal performance.
Best Papers of 2020. Each year, the International Council on Systems Engineering (INCOSE) selects a Best Paper award from among the papers published the previous year in Systems Engineering. The Editorial Board considers the papers in this virtual issue to be among the best from those published in 2020. We hope this virtual issue will provide ...
2022 Computing Engineering Dissertation Topics. Topic 1: An investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility. Research Aim: This study aims to investigate the applications of blockchain within the energy sector.
6:1 PUMA Arrays: Designs and Finite Array Effects, Michael Lee, Electrical & Computer Engineering. PDF. Protecting Controllers against Denial-of-Service Attacks in Software-Defined Networks, Jingrui Li, Electrical & Computer Engineering. PDF. INFRASTRUCTURE-FREE SECURE PAIRING OF MOBILE DEVICES, Chunqiu Liu, Electrical & Computer Engineering. PDF
Recent papers in Computer Engineering. Top Papers. Most Cited Papers. Most Downloaded Papers. Newest Papers. People. IRJET- The Effect of Blended Mix (NaOH-Na2SiO3) Over the Compressive Strength Development of Geopolymer Concrete using M-Sand Subjected to Adverse Environments of Acid and Sulphate. This proposed experimental investigation is to ...
Computer Engineering Research Papers/Topics . Case-based reasoning system for prediction of fuel consumption by haulage trucks in open-pit mines. Abstract: The shovel-truck system is commonly used in open-pit mining operations. Truck haulage cost constitutes about 26% of open-pit mining costs as the trucks are mostly powered by diesel whose ...
The Turing Award is considered the highest honor in computer science, often called the "Nobel Prize of Computing." Wigderson, the Herbert H. Maass Professor in the Institute for Advanced Study's School of Mathematics, earned his Ph.D. from Princeton in 1983 in what was then the Department of Electrical Engineering and Computer Science.