Understanding IP Address Assignment: A Complete Guide

Introduction
In today's interconnected world, where almost every aspect of our lives relies on the internet, understanding IP address assignment is crucial for ensuring online security and efficient network management. An IP address serves as a unique identifier for devices connected to a network, allowing them to communicate with each other and access the vast resources available on the internet. Whether you're a technical professional, a network administrator, or simply an internet user, having a solid grasp of how IP addresses are assigned within the same network can greatly enhance your ability to troubleshoot connectivity issues and protect your data.
The Basics of IP Addresses
Before delving into the intricacies of IP address assignment in the same network, it's important to have a basic understanding of what an IP address is. In simple terms, an IP address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It consists of four sets of numbers separated by periods (e.g., 192.168.0.1) and can be either IPv4 or IPv6 format.
IP Address Allocation Methods
There are several methods used for allocating IP addresses within a network. One commonly used method is Dynamic Host Configuration Protocol (DHCP). DHCP allows devices to obtain an IP address automatically from a central server, simplifying the process of managing large networks. Another method is static IP address assignment, where an administrator manually assigns specific addresses to devices within the network. This method provides more control but requires careful planning and documentation.

Considerations for Efficient IP Address Allocation
Efficient allocation of IP addresses is essential for optimizing network performance and avoiding conflicts. When assigning IP addresses, administrators need to consider factors such as subnetting, addressing schemes, and future scalability requirements. By carefully planning the allocation process and implementing best practices such as using private IP ranges and avoiding overlapping subnets, administrators can ensure smooth operation of their networks without running out of available addresses.
IP Address Assignment in the Same Network
When two routers are connected within the same network, they need to obtain unique IP addresses to communicate effectively. This can be achieved through various methods, such as using different subnets or configuring one router as a DHCP server and the other as a client. Understanding how IP address assignment works in this scenario is crucial for maintaining proper network functionality and avoiding conflicts.
Basics of IP Addresses
IP addresses are a fundamental aspect of computer networking that allows devices to communicate with each other over the internet. An IP address, short for Internet Protocol address, is a unique numerical label assigned to each device connected to a network. It serves as an identifier for both the source and destination of data packets transmitted across the network.
The structure of an IP address consists of four sets of numbers separated by periods (e.g., 192.168.0.1). Each set can range from 0 to 255, resulting in a total of approximately 4.3 billion possible unique combinations for IPv4 addresses. However, with the increasing number of devices connected to the internet, IPv6 addresses were introduced to provide a significantly larger pool of available addresses.
IPv4 addresses are still predominantly used today and are divided into different classes based on their range and purpose. Class A addresses have the first octet reserved for network identification, allowing for a large number of hosts within each network. Class B addresses reserve the first two octets for network identification and provide a balance between network size and number of hosts per network. Class C addresses allocate the first three octets for network identification and are commonly used in small networks.
With the depletion of available IPv4 addresses, IPv6 was developed to overcome this limitation by utilizing 128-bit addressing scheme, providing an enormous pool of potential IP addresses - approximately 3.4 x 10^38 unique combinations.
IPv6 addresses are represented in hexadecimal format separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). The longer length allows for more efficient routing and eliminates the need for Network Address Translation (NAT) due to its vast address space.
Understanding these basics is essential when it comes to assigning IP addresses in a network. Network administrators must consider various factors such as the number of devices, network topology, and security requirements when deciding on the IP address allocation method.
In the next section, we will explore different methods of IP address assignment, including Dynamic Host Configuration Protocol (DHCP) and static IP address assignment. These methods play a crucial role in efficiently managing IP addresses within a network and ensuring seamless communication between devices.
Methods of IP Address Assignment
IP address assignment is a crucial aspect of network management and plays a vital role in ensuring seamless connectivity and efficient data transfer. There are primarily two methods of assigning IP addresses in a network: dynamic IP address assignment using the Dynamic Host Configuration Protocol (DHCP) and static IP address assignment.
Dynamic IP Address Assignment using DHCP
Dynamic IP address assignment is the most commonly used method in modern networks. It involves the use of DHCP servers, which dynamically allocate IP addresses to devices on the network. When a device connects to the network, it sends a DHCP request to the DHCP server, which responds by assigning an available IP address from its pool.
One of the key benefits of dynamic IP address assignment is its simplicity and scalability. With dynamic allocation, network administrators don't have to manually configure each device's IP address. Instead, they can rely on the DHCP server to handle this task automatically. This significantly reduces administrative overhead and makes it easier to manage large networks with numerous devices.
Another advantage of dynamic allocation is that it allows for efficient utilization of available IP addresses. Since addresses are assigned on-demand, there is no wastage of unused addresses. This is particularly beneficial in scenarios where devices frequently connect and disconnect from the network, such as in public Wi-Fi hotspots or corporate environments with a high turnover rate.
However, dynamic allocation does have some drawbacks as well. One potential issue is that devices may receive different IP addresses each time they connect to the network. While this might not be an issue for most users, it can cause problems for certain applications or services that rely on consistent addressing.
Additionally, dynamic allocation introduces a dependency on the DHCP server. If the server goes down or becomes unreachable, devices will not be able to obtain an IP address and will be unable to connect to the network. To mitigate this risk, redundant DHCP servers can be deployed for high availability.
Static IP Address Assignment
Static IP address assignment involves manually configuring each device's IP address within the network. Unlike dynamic allocation, where addresses are assigned on-demand, static assignment requires administrators to assign a specific IP address to each device.
One of the main advantages of static IP address assignment is stability. Since devices have fixed addresses, there is no risk of them receiving different addresses each time they connect to the network. This can be beneficial for applications or services that require consistent addressing, such as servers hosting websites or databases.
Static assignment also provides greater control over network resources. Administrators can allocate specific IP addresses to devices based on their requirements or security considerations. For example, critical servers or network infrastructure devices can be assigned static addresses to ensure their availability and ease of management.
However, static IP address assignment has its limitations as well. It can be time-consuming and error-prone, especially in large networks with numerous devices. Any changes to the network topology or addition/removal of devices may require manual reconfiguration of IP addresses, which can be a tedious task.
Furthermore, static allocation can lead to inefficient utilization of available IP addresses. Each device is assigned a fixed address regardless of whether it is actively using the network or not. This can result in wastage of unused addresses and may pose challenges in scenarios where addressing space is limited.
In order to efficiently allocate IP addresses within a network, there are several important considerations that need to be taken into account. By carefully planning and managing the allocation process, network administrators can optimize their IP address usage and ensure smooth operation of their network.
One of the key factors to consider when assigning IP addresses is the size of the network. The number of devices that will be connected to the network determines the range of IP addresses that will be required. It is essential to accurately estimate the number of devices that will need an IP address in order to avoid running out of available addresses or wasting them unnecessarily.
Another consideration is the type of devices that will be connected to the network. Different devices have different requirements in terms of IP address assignment. For example, servers and other critical infrastructure typically require static IP addresses for stability and ease of access. On the other hand, client devices such as laptops and smartphones can often use dynamic IP addresses assigned by a DHCP server.
The physical layout of the network is also an important factor to consider. In larger networks with multiple subnets or VLANs, it may be necessary to segment IP address ranges accordingly. This allows for better organization and management of IP addresses, making it easier to troubleshoot issues and implement security measures.
Security is another crucial consideration when allocating IP addresses. Network administrators should implement measures such as firewalls and intrusion detection systems to protect against unauthorized access or malicious activities. Additionally, assigning unique IP addresses to each device enables better tracking and monitoring, facilitating quick identification and response in case of any security incidents.
Efficient utilization of IP address ranges can also be achieved through proper documentation and record-keeping. Maintaining an up-to-date inventory of all assigned IP addresses helps prevent conflicts or duplicate assignments. It also aids in identifying unused or underutilized portions of the address space, allowing for more efficient allocation in the future.
Furthermore, considering future growth and scalability is essential when allocating IP addresses. Network administrators should plan for potential expansion and allocate IP address ranges accordingly. This foresight ensures that there will be sufficient addresses available to accommodate new devices or additional network segments without disrupting the existing infrastructure.
In any network, the assignment of IP addresses is a crucial aspect that allows devices to communicate with each other effectively. When it comes to IP address assignment in the same network, there are specific considerations and methods to ensure efficient allocation. In this section, we will delve into how two routers in the same network obtain IP addresses and discuss subnetting and IP address range distribution.
To understand how two routers in the same network obtain IP addresses, it's essential to grasp the concept of subnetting. Subnetting involves dividing a larger network into smaller subnetworks or subnets. Each subnet has its own unique range of IP addresses that can be assigned to devices within that particular subnet. This division helps manage and organize large networks efficiently.
When it comes to assigning IP addresses within a subnet, there are various methods available. One common method is manual or static IP address assignment. In this approach, network administrators manually assign a specific IP address to each device within the network. Static IP addresses are typically used for devices that require consistent connectivity and need to be easily identifiable on the network.
Another widely used method for IP address assignment is Dynamic Host Configuration Protocol (DHCP). DHCP is a networking protocol that enables automatic allocation of IP addresses within a network. With DHCP, a server is responsible for assigning IP addresses dynamically as devices connect to the network. This dynamic allocation ensures efficient utilization of available IP addresses by temporarily assigning them to connected devices when needed.
When considering efficient allocation of IP addresses in the same network, several factors come into play. One important consideration is proper planning and design of subnets based on anticipated device count and future growth projections. By carefully analyzing these factors, administrators can allocate appropriate ranges of IP addresses for each subnet, minimizing wastage and ensuring scalability.
Additionally, implementing proper security measures is crucial when assigning IP addresses in the same network. Network administrators should consider implementing firewalls, access control lists (ACLs), and other security mechanisms to protect against unauthorized access and potential IP address conflicts.
Furthermore, monitoring and managing IP address usage is essential for efficient allocation. Regular audits can help identify any unused or underutilized IP addresses that can be reclaimed and allocated to devices as needed. This proactive approach ensures that IP addresses are utilized optimally within the network.
The proper assignment of IP addresses is crucial for maintaining network security and efficiency. Throughout this guide, we have covered the basics of IP addresses, explored different methods of IP address assignment, and discussed considerations for efficient allocation.
In conclusion, understanding IP address assignment in the same network is essential for network administrators and technical professionals. By following proper allocation methods such as DHCP or static IP assignment, organizations can ensure that each device on their network has a unique identifier. This not only enables effective communication and data transfer but also enhances network security by preventing unauthorized access.
Moreover, considering factors like subnetting, scalability, and future growth can help optimize IP address allocation within a network. Network administrators should carefully plan and allocate IP addresses to avoid conflicts or wastage of resources.
Overall, a well-managed IP address assignment process is vital for the smooth functioning of any network. It allows devices to connect seamlessly while ensuring security measures are in place. By adhering to best practices and staying updated with advancements in networking technology, organizations can effectively manage their IP address assignments.
In conclusion, this guide has provided a comprehensive overview of IP address assignment in the same network. We hope it has equipped you with the knowledge needed to make informed decisions regarding your network's IP address allocation. Remember that proper IP address assignment is not only important for connectivity but also plays a significant role in maintaining online security and optimizing network performance.
Enhance Online Security: The Ultimate Guide to Conceal Your IP Address
Alternative Methods to Conceal Your IP Address Without a VPN
Maintain Privacy: Learn How to Alter Your IP Address
The Significance of IP Address for Online Security and Privacy
Comprehensive Handbook on VPNs, IP Addresses, and Proxy Servers

Blog Post View
How are ip addresses assigned.

When you're connected to a network, your computer or smart device will obtain an IP address either from your ISP or your router. There are 2 ways how you can assign an IP address to your device: (1) dynamically via DHCP or (2) statically by manually assigning an IP address yourself. In either case, you must use the IP address that is provided to you by your ISP, or the IP range you allocated yourself within your private space (i.e. private IP address).
How are IP addresses allocated?
Before we can discuss IP assignment, we need to understand how IP addresses are allocated. There are two versions of IP addresses: IPv4 (version 4) and IPv6 (version 6). There are numerical differences , but they essentially serves the same purpose by uniquely identifying a device on the Internet. There are a few organizations that allocate and manage IP addresses globally, and they are:
- ICAAN (The Internet Corporation for Names & Numbers): ICANN manages supply of all IPv4 and IPv6 addresses as well as domain name system ( DNS ) and Root Servers.
- IANA (Internet Assigned Numbers Authority): IANA is a part of ICANN that maintains technical aspect of the DNS. DNS is the system that translates human-readable domain names to machine friendly IP addresses.
- ARIN (American Registry for Internet Numbers): ARIN is a region specific organization that manages IP addresses for the USA, Canada, Caribbean and North Atlantic islands.
- ISP (Internet Service Providers): ISPs reach out to ARIN and register blocks of IP addresses (i.e. class A, B and C). In addition to ISPs, large corporations may reach out to ARIN to register blocks of IP address for their corporate use.
- RIR (Regional Internet Registry): Much like the ARIN for managing IP address for North American region, RIR manages IP addresses for rest of the world.
As ARIN and RIR manages IP addresses for the region, they allocate and deallocate IP addresses for countries, ISPs and corporations. A larger blocks of IP addresses are assigned to countries, the accuracy of IP location for country level is approximately 95% - 98% depending on the provider.
Once one or more blocks of IP addresses are assigned to an ISP or Corporation, the organization assigns the IP address to its customers. When you purchase the Internet Service from an ISP, you have an option to obtain static (non-changing) or dynamic (changing) IP Address(es). Most home users obtain a dynamic IP address, and small businesses may obtain static IP addresses. The IP addresses obtained from an ISP are "public" IP addresses which are a globally unique number within the Internet.
Once the IP address is obtained by your router from your ISP, you have an option to create a private network by assigning private IP addresses to your devices that are not globally unique, but unique within your private network.
IP addresses are governed by ICANN, and ARIN and RIR are responsible for allocating IP addresses to ISPs and Corporations within its regions. IANA manages DNS for translating domain names to IP addresses. The IP addresses are then assigned to individuals or small businesses either statically or dynamically via DHCP, and every computing devices on the Internet must have an IP address to communicate with each other.
Share this post
Comments (0), leave a comment.
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.
Reply Comment
Do not sell or share my personal information..
At IPLocation.net, we prioritize the privacy and security of our visitors. We want you to feel confident and comfortable when browsing our website. That's why we want to assure you that we do not sell or share any personal information collected from our website. Your trust is important to us. Whether you're browsing our site for information, or engaging with our content, rest assured that any data you provide remains strictly confidential. We adhere to stringent privacy policies and comply with all relevant regulations to safeguard your information. Your privacy matters, and we are committed to maintaining the highest standards of data protection. If you have any questions or concerns regarding our privacy practices, please don't hesitate to reach out to us.
© 2006 - 2024, Brand Media, Inc. All rights reserved.
What Is An IP Address? How Does It Work?
Discover how IP addresses work and what IP addresses are available.
- Get A Threat Assessment
- Read the Outbreak Alerts Report

IP Address Definition and Explanation
An Internet Protocol (IP) address is the unique identifying number assigned to every device connected to the internet. An IP address definition is a numeric label assigned to devices that use the internet to communicate. Computers that communicate over the internet or via local networks share information to a specific location using IP addresses.
IP addresses have two distinct versions or standards. The Internet Protocol version 4 (IPv4) address is the older of the two, which has space for up to 4 billion IP addresses and is assigned to all computers. The more recent Internet Protocol version 6 (IPv6) has space for trillions of IP addresses, which accounts for the new breed of devices in addition to computers. There are also several types of IP addresses, including public, private, static, and dynamic IP addresses .
Every device with an internet connection has an IP address, whether it's a computer, laptop, IoT device, or even toys. The IP addresses allow for the efficient transfer of data between two connected devices, allowing machines on different networks to talk to each other.
How does an IP address work?
An IP address works in helping your device, whatever you are accessing the internet on, to find whatever data or content is located to allow for retrieval.
Common tasks for an IP address include both the identification of a host or a network, or identifying the location of a device. An IP address is not random. The creation of an IP address has the basis of math. The Internet Assigned Numbers Authority (IANA) allocates the IP address and its creation. The full range of IP addresses can go from 0.0.0.0 to 255.255.255.255.
With the mathematical assignment of an IP address, the unique identification to make a connection to a destination can be made.
Public IP address
A public IP address, or external-facing IP address, applies to the main device people use to connect their business or home internet network to their internet service provider (ISP). In most cases, this will be the router. All devices that connect to a router communicate with other IP addresses using the router’s IP address.
Knowing an external-facing IP address is crucial for people to open ports used for online gaming, email and web servers, media streaming, and creating remote connections.
Private IP address
A private IP address, or internal-facing IP address, is assigned by an office or home intranet (or local area network) to devices, or by the internet service provider (ISP). The home/office router manages the private IP addresses to the devices that connect to it from within that local network. Network devices are thus mapped from their private IP addresses to public IP addresses by the router.
Private IP addresses are reused across multiple networks, thus preserving valuable IPv4 address space and extending addressability beyond the simple limit of IPv4 addressing (4,294,967,296 or 2^32).
In the IPv6 addressing scheme, every possible device has its own unique identifier assigned by the ISP or primary network organization, which has a unique prefix. Private addressing is possible in IPv6, and when it's used it's called Unique Local Addressing (ULA).
Static IP address
All public and private addresses are defined as static or dynamic. An IP address that a person manually configures and fixes to their device’s network is referred to as a static IP address. A static IP address cannot be changed automatically. An internet service provider may assign a static IP address to a user account. The same IP address will be assigned to that user for every session.
Dynamic IP address
A dynamic IP address is automatically assigned to a network when a router is set up. The Dynamic Host Configuration Protocol (DHCP) assigns the distribution of this dynamic set of IP addresses. The DHCP can be the router that provides IP addresses to networks across a home or an organization.
Each time a user logs into the network, a fresh IP address is assigned from the pool of available (currently unassigned) IP addresses. A user may randomly cycle through several IP addresses across multiple sessions.

Get a Cybersecurity Threat Assessment
Know your vulnerabilities - get the facts about your security risk and at no cost.
What Is IPv4?
IPv4 is the fourth version of the IP. It is one of the core protocols of the standards-based methods used to interconnect the internet and other networks. The protocol was first deployed on the Atlantic Packet Satellite Network (SATNET), which was a satellite network that formed a segment of the initial stages of the internet, in 1982. It is still used to route most internet traffic despite the existence of IPv6.
IPv4 is currently assigned to all computers. An IPv4 address uses 32-bit binary numbers to form a unique IP address. It takes the format of four sets of numbers, each of which ranges from 0 to 255 and represents an eight-digit binary number, separated by a period point.
IP Address Classes
Some IP addresses are reserved by the Internet Assigned Numbers Authority (IANA). These are typically reserved for networks that carry a specific purpose on the Transmission Control Protocol/Internet Protocol (TCP/IP) , which is used to interconnect devices. Four of these IP address classes include:
- 0.0.0.0 : This IP address in IPv4 is also known as the default network. It is the non-routeable meta address that designates an invalid, non-applicable, or unknown network target.
- 127.0.0.1 : This IP address is known as the loopback address, which a computer uses to identify itself regardless of whether it has been assigned an IP address.
- 169.254.0.1 to 169.254.254.254 : A range of addresses that are automatically assigned if a computer is unsuccessful in an attempt to receive an address from the DHCP.
- 255.255.255.255 : An address dedicated to messages that need to be sent to every computer on a network or broadcasted across a network.
Further reserved IP addresses are for what is known as subnet classes. Subnetworks are small computer networks that connect to a bigger network via a router. The subnet can be assigned its own IP address system, so that all devices connecting to it can communicate with each other without having to send data via the wider network.
The router on a TCP/IP network can be configured to ensure it recognizes subnets, then route the traffic onto the appropriate network. IP addresses are reserved for the following subnets:
- Class A : IP addresses between 10.0.0.0 and 10.255.255.255
- Class B : IP addresses between 172.16.0.0 and 172.31.255.255
- Class C : IP addresses between 192.186.0.0 and 192.168.255.255
- Class D or multicast : IP addresses between 224.0.0.0 and 239.255.255.255
- Class E, which are reserved for experimental usage : IP addresses between 240.0.0.0 and 254.255.255.254
IP addresses listed under Class A, Class B, and Class C are most commonly used in the creation of subnets. Addresses within the multicast or Class D have specific usage rules outlined in the Internet Engineering Task Force (IETF) guidelines, while the release of Class E addresses for public use was the cause of plenty of debate before the IPv6 standard was introduced.
Internet Addresses and Subnets
The IANA reserves specific IP address blocks for commercial organizations, government departments, and ISPs. When a user connects to the internet, their ISP assigns them an address from within one of the blocks assigned to it. If they only go online from one computer, then they can use the address assigned to it by their ISP.
However, most homes now use routers that share a network connection with multiple devices. So if a router is used to share the connection, then the ISP assigns the IP address to the router, and then a subnet is created for all computers that connect to it.
IP addresses that fall within a subnet have a network and a node. The subnet is identified by the network. The node, also known as the host, connects to the network and needs its own address. Computers separate the network and node via a subnet mask, which filters the appropriate IP address designation. When a large network is set up, the subnet mask that best fits the number of nodes or subnets required is determined.
When it comes to IP addresses within a subnet, the first address is reserved for the subnet, and the final one indicates the broadcast address for the subnet’s systems.
IPv4 vs. IPv6
IPv4 has not been able to cope with the massive explosion in the quantity and range of devices beyond simply mobile phones, desktop computers, and laptops. The original IP address format was not able to handle the number of IP addresses being created.
To address this problem, IPv6 was introduced. This new standard operates a hexadecimal format that means billions of unique IP addresses can now be created. As a result, the IPv4 system that could support up to around 4.3 billion unique numbers has been replaced by an alternative that, theoretically, offers unlimited IP addresses.
That is because an IPv6 IP address consists of eight groups that contain four hexadecimal digits, which use 16 distinct symbols of 0 to 9 followed by A to F to represent values of 10 to 15.
How Do I Locate My IP Address?
Windows computer users can look up their IP address by typing "cmd" into the search tab and hitting Enter, then typing "ipconfig" into the pop-up box. Mac computer users can find their IP address by heading into System Preferences and selecting Network.
To look up an IP address on a mobile phone, users need to head into Settings, then open the Wi-Fi menu and their network menu. The IP address should be listed under the Advanced section, depending on the phone they use.
IP address vs. MAC address
When you analyze an IP address vs. a MAC address, you can start with the similarities. For both of these IP address types, you are dealing with a unique identifier with an attachment to that device. The manufacturer of a network card or router is the provider of the MAC address, while the internet service provider (ISP) is the provider of the IP address.
The main difference between the two is that the MAC address is the physical address of a device. If you have five laptops on your home Wi-Fi network, you can identify each of those five laptops on your network via their MAC address.
The IP address works differently as it is the identifier of the connection of the network with that device. Other differences include:
- A MAC address is a 6-byte hexadecimal address while an IP address is a 4 or 16-byte address.
- A MAC address is in a data link layer, while an IP address is in a network layer.
- A third party will have a difficult time finding a MAC address, while it can easily find an IP address.
- MAC addresses are static, while IP addresses can change dynamically
- MAC addresses and IP addresses are necessary to get a network packet to a destination. However, no one can see your MAC address unless they are on your LAN
What are security threats related to IP addresses?
A variety of security threats are related to IP addresses. Cybercriminals can deceive devices to either reveal your IP address and pretend they are you or stalk it to track activity and take advantage. Online stalking and social engineering are the two leading security threats existing for IP addresses.
Some of the other security threats to an IP address include:
- Allowing a cybercriminal to use your IP address to track your location
- Using your IP address to target your network and launch a DDoS attack
- Using your IP address to download illegal content
5 ways to protect your IP address
There are multiple ways to protect your IP address from cybercriminals. Some of these options include:
- Make use of a proxy server
- Have your ISP make use of dynamic IP addresses
- Employ a NAT firewall to hide your private IP address
- Resetting your modem may change your IP address
Frequently Asked Questions about IP Address
1. what is the use of an ip address.
An IP address identifies every device connected to the internet. This enables computers and other internet-connected devices, such as mobile phones and Internet-of-Things (IoT) devices, to communicate over the internet and on local-area networks (LANs).
2. What happens if someone has your IP address?
The chances of being hacked through someone having your IP address is quite low. With an IP address, a user's location can be narrowed down to a specific area. A skilled cyber criminal could potentially work out who their ISP is and then use phishing attacks to find their personal details. A bigger concern might be IP addresses being sold on the dark web alongside other personal information.
An IP address is more likely to be used by content providers to target the user with content restrictions based on their geographical region. For example, services like Hulu and Netflix read IP addresses to prevent their U.S. content from being accessed by people outside the country.
3. What are the two types of IP addresses?
The two types of IP addresses are public IP addresses and private IP addresses. A public IP address is the main device people use to connect to the internet, which is typically their router. Private IP addresses are assigned to the devices that connect to the public IP address, such as desktop computers, mobile devices, laptops, printers, smart TVs, and tablets.
4. What is the 192.168 IP address?
The 192.168 IP address is where the private IP address range begins. This goes all the way through to 192.168.255.255. This IP address is not usually used on a network, and devices like computers and mobile phones will not be assigned it.
5. What is a loopback IP address?
The loopback IP address is 127.0.0.1. The loopback IP address is used by a computer to identify itself, regardless of whether or not it has been assigned an IP address.
Cybersecurity Resources
- Cybersecurity
- Types of Cyber Attacks
- IT vs OT Cybersecurity
- AI Cybersecurity
- Cyber Threat Intelligence
- Cybersecurity Management
- Network Security
- Data Security
- Email Security
- Endpoint Security
- Web Security
- Enterprise Security
- Cybersecurity Mesh
Quick Links
- Fortinet Products
- Fortinet Demos
- Analyst Reports
IP address, Network address, and Host address Explained
This tutorial explains IP addresses, network addresses, host addresses, and subnet masks in detail. Learn what IP addresses are and how they work in computer networks.
If objects connected in a group want to share or exchange something, they need a specific identity to refer to each other. This unique identity is known as the address. In simple terms, addresses are a way of organizing and locating objects in a single group or multiple groups. Addresses are mainly used for two reasons: to provide a unique identity to each object in the group and to find an object in the group.
A computer network is a group of computers and various networking devices that connect to share information and resources. To uniquely identify each computer or networking device in the network, computer networks also use addresses. Addresses in computer networks are known as IP addresses . An IP address consists of two components: the network address and the host address. The network address is used to find the subnet in which the computer or the device is located and the host address is used to find the computer or the device in the subnet. If a large computer network is divided into smaller groups, each group is known as a subnet .
IP addresses can be written in three notations: binary, dotted-decimal, and hexadecimal. From these notations, computers understand only binary notation. Binary notation is complex to write and understand. To make IP addresses human friendly, IP addresses are also written in dotted-decimal and hexadecimal notations. If IP addresses are written in dotted-decimal notation or hexadecimal notation, computers automatically convert them into binary notation before processing them.
There are two versions of IP addresses: IPv4 and IPv6. The length of IP addresses is different in both versions. Both versions also use different formats to differentiate between network addresses and host addresses. Let's understand IP addresses in both versions.
IP addresses in IPv4
IPv4 addresses are 32 bits in length. These bits are divided into four equal sections. Sections are separated by periods and written in a sequence. In measurement, 8 bits are equal to one byte or an octet. In simple words, an IP address consists of four bytes or octets separated by periods.
The following image shows how bits are arranged in IPv4 addresses.
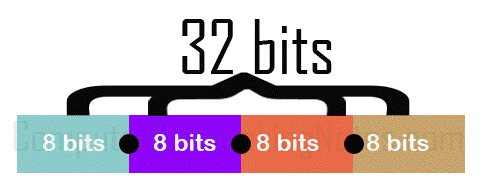
In binary notation, all four octets are written in binary format. For example, some IP addresses in binary format are listed below.
IPv4 addresses are written and used in dotted-decimal notation. In decimal notation, all four octets are written in decimal format. A decimal equivalent value of the octet is used in each section. For example, you can write the above IP addresses in decimal notation as shown below.
Subnet Mask
To separate network addresses from host addresses, IPv4 uses an additional component with IP addresses. This component is known as a subnet mask . In other words, in an IP address, how many bits are used in the network address and how many bits are left for the host address is determined by the subnet mask. The subnet mask is also 32 bits in length and uses the same notation that is used by the IP address.
The subnet mask assigns an individual bit for each bit of the IP address. If an IP bit belongs to the network portion, the subnet mask will turn on the assigned bit. If an IP bit belongs to the host portion, the subnet mask will turn off the assigned bit.
In binary notation, 1 (one) represents an ON bit while 0 (zero) represents an OFF bit. In dotted-decimal notation, a value range 1 to 255 represents an ON bit while a value 0 (zero) represents an OFF bit.
Following are the examples of subnet mask in binary notation: -
Following are the examples of subnet mask in decimal notation: -
An IP address is always used with the subnet mask. Without the subnet mask, an IP address is considered an ambiguous address.
Following are the examples of IP addresses with subnet mask in binary notation: -
Following are the examples of IP addresses with subnet mask in decimal notation: -
The following image shows how the subnet mask separate the network address from the host address in an IP address.

IP addresses in IPv6
IPv6 addresses are 128 bits in length. These bits are divided into eight equal sections. Sections are separated by colons (:) and written in a sequence. IPv6 addresses are written in hexadecimal notation.
The following image shows how bits are arranged in IPv6 addresses.
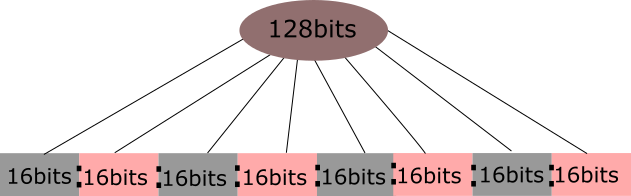
Following are the examples of IP addresses in IPv6: -
Instead of using an additional component to separate network addresses and host addresses, IPv6 defines the number of bits for both types of addresses. It defines the first 64 bits as the network address and the last 64 bits as the host address.
The following image shows how IPv6 separates the network address and host address in an IP address.

How do host addresses work?
In computer networks, IP addresses are assigned on interfaces. An interface connects a computer or a networking device to the network. In a computer network, all interfaces must be configured with unique IP addresses. If two or more interfaces are configured with the same IP address, the network will not work.
Let's understand it through an example.
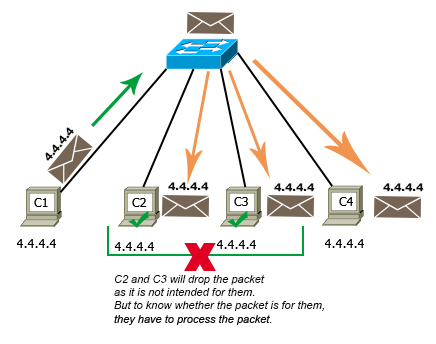
In a computer network, four computers named C1, C2, C3, and C4 are connected. All computers are configured with the same IP address. The configured IP address is 4.4.4.4/8. C1 sends a data packet to C4. Since the IP address of C4 is 4.4.4.4/8, C1 sets the destination address in the packet to 4.4.4.4/8.
The packet reaches C2, C3, and C4. They check the destination address of the packet to know whether the packet is intended for them. Since the destination address of the packet matches with the IP address configured on their interfaces, they all assume that the packet is intended for them, and they all process it.
After processing, C2 and C3 realize that the packet is not intended for them and they discard the packet. C4 accepts the packet. If C4 sends a reply packet, the reply packet will also follow the same path and will be processed by C2 and C3 unnecessarily.
The following image shows this example.
In a busy network where interfaces process millions of packets per second, an overlap of IP addresses can bring the entire network down. To avoid such a situation, computer networks use a unique IP address on each interface.
Let's take our example network again and make all IP addresses unique. To make all IP addresses unique, change their host addresses. For example, you can set the new IP addresses of C1, C2, C3, and C4 to 4.4.4.1/8, 4.4.4.2/8, 4.4.4.3/8, and 4.4.4.4/8, respectively.
After this change, when C1 sends packets to C4 and the packet reaches C2, C3, and C4, only C4 processes the packet. C2 and C3 immediately discard the packet because the destination address of the packet and the IP address of their interfaces are different.
The following image shows how a host address works in the network.
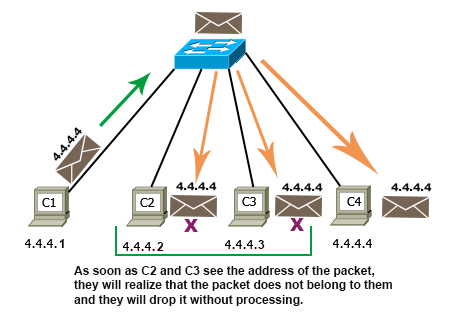
If all interfaces are configured with unique IP addresses, they can access each other easily.
How do network addresses work?
Just as a host address provides a unique identity to the interface in a subnet, a network address provides a unique identity to the subnet in the network. A network address is the common address of all interfaces that belong to a specific subnet.
Let's take an example to understand how network addresses work.
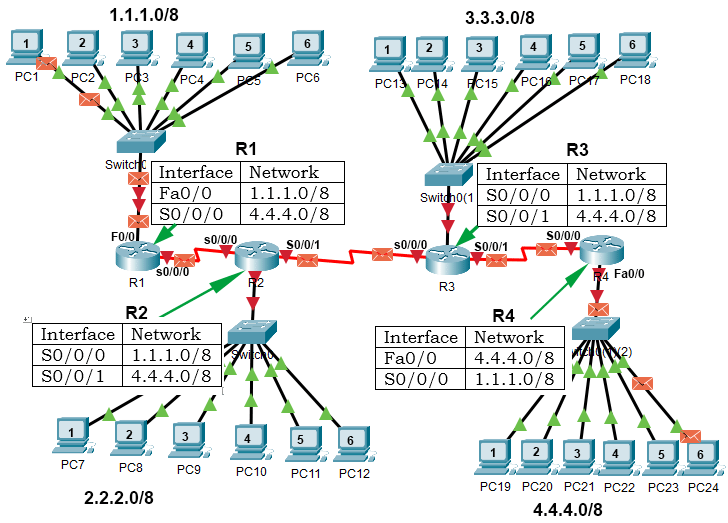
In a network, four subnets are connected. Network addresses of these subnets are 1.1.1, 2.2.2, 3.3.3, and 4.4.4. Each subnet contains 6 PCs. Host addresses of PC1, PC2, PC3, PC4, PC5, and PC6 are .1, .2, .3, .4, .5, and .6, respectively.
In IP addresses, network addresses are always written before host addresses. If we write the network address before the host address of a PC, we will get the IP address of that PC. The following image shows this process in our example network.

Hosts or PCs of different subnets cannot communicate or exchange data directly. To connect different subnets, routers are used. Routers are networking devices that connect different subnets or networks. Routers store the network addresses of all available subnets in their routing tables.
If a computer wants to send a data packet to a computer that belongs to another subnet, it sends the data packet to the gateway router. A gateway router is the router that connects the subnet to other subnets of the network. The gateway router forwards the data packet to the router that is connected to the destination subnet or know how to reach the destination subnet. To forward data packets, routers use only network addresses.
Let's understand it through our example. Our example network is divided into four subnets. To connect these subnets, four routers: R1, R2, R3, and R4 are used. R1, R2, R3, and R4 are connected to the first subnet (1.1.1.0/8), second subnet (2.2.2.0/8), third subnet (3.3.3.0/8), and the fourth subnet (4.4.4.0/8), respectively.
Now suppose, PC1 of the first subnet sends a data packet to PC6 of the fourth subnet. PC1 sets destination IP address in the packet to 4.4.4.6/8. In this IP address, 4.4.4 is the network address and .6 is the host address. The packet reaches R1. R1 checks its routing table and forwards the packet to R2. R2 follows the same procedure and forwards the packet to R3. R3 forwards the packet to R4 and R4 forwards the packet to the local network of the fourth subnet. The local network of the fourth subnet uses the host address of the packet to find the PC6.
The following image shows this procedure.
That's all for this tutorial. If you like this tutorial, please share it with friends via your favorite social networking sites and subscribe to our YouTube channel.
By ComputerNetworkingNotes Updated on 2024-03-21 07:00:01 IST
ComputerNetworkingNotes Networking Tutorials IP address, Network address, and Host address Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

- Standards & Protocols
- Data Center
- Unified Communications

Enterprise Networking Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Table of Contents
What is an IP address?
An Internet Protocol (IP) address is like a phone number for your computer. Just like you need to dial a phone number to reach someone, your computer (or computing device, such as a smartphone or tablet) needs an IP address to reach other devices on the network.
The history of IPv4 dates back to the early 1980s when the internet was a private network solely used by the military. Despite its initial intended purpose, it quickly grew in popularity, leading to an eventual shortage of IPv4 addresses due to all the different networks and devices now accessing the internet.
The total pool of 4.3 billion IPv4 addresses initially seemed like ample amounts; however, this figure quickly proved incapable of meeting demands. The depletion of available IPv4 began as early as the 1990s. Clever technical networking tricks have managed to delay this exhaustion and allow us access to IPv4 transactions even today.
IPv6 is the most recent variation of the Internet Protocol, granting more computer systems and devices access to the internet than ever before. IPv6 is designed to enable routing only within a local area network (LAN) or subnetwork.
How IP addressing works
There are two types of IP addresses, IPv4 and IPv6, and they work a little differently from each other—specifically, IPv4 is a 32-bit address while IPv6 is 128 bits.
IPv4 addressing
IPv4 uses 32 bits, and its address format is usually a unique string of numbers and letters that looks something like this: 123.123.123.123. Each IP address comprises four sets of numbers separated by periods, each ranging from 0 to 255.
IPv4 addresses are composed of two parts: the network ID and the host ID. The network ID identifies the network a device is connected to, while the host ID identifies a specific device on that network.
The network ID is typically expressed in dotted decimal notation, which is a series of three numbers separated by dots. Each number can range from 0 to 255, forming an 8-bit binary number. The host ID is also expressed in dotted decimal notation, but it can be any combination of numbers up to 32 bits long.
For example, take the IP address 192.168.1.20.
The first part, 192.168.1, represents the network ID, while the last part, 20, represents the device ID.
Usually, a device ID 1 is allocated to the router while subsequent numbers 2 and onwards are used to identify other devices on the network.
Together, these two parts make up an IPv4 address and allow devices to communicate with each other over the internet. By knowing both the network ID and host ID, devices can send and receive data from one another without knowing each other’s exact location or IP address.
IPv6 addressing
Like IPv4, an IPv6 address is made up of two distinct parts: a network component and a participant/node component. However, IPv6 uses 128 bits for its address instead of the 32 bits allowed by IPv4. This provides users with a much greater range of addresses than IPv4, enabling every device to have a unique address.
Represented in hexadecimal format, each IPv6 address includes eight groups separated by colons. For example, 2620:0aba2:0d01:2042:0100:8c4d:d370:72b4.
6 types of IP addresses
Within the two types of IPv4 and IPv6 addresses, there are also several other classifications to be aware of: internal versus external IPv4, static versus dynamic IP addresses, and special address formats for particular purposes.
Internal IPv4 addresses (local/private)
Internal IPv4 addresses are used for private networks, such as LANs. They’re not visible on the public internet; only devices connected to the same subnetwork can see each other’s internal IP address. These IP addresses generally start with 192.168.x.x, 10.0.x.x, or 172.16-31.x.x and cannot be accessed from directly outside the network. In other words, they are not globally routable.
External IPv4 addresses (public)
External IPv4 addresses are used to connect to the public internet and make websites available on the World Wide Web. They’re assigned by internet service providers (ISPs) and are usually dynamic, meaning they can change over time. They do not start with 192.168 or 10.0, as these numbers signify private IP addresses. Being public IP addresses means they’re globally routable.
Static IP addresses
A static IP address remains constant over time, allowing for a more reliable connection on the network. This type of address is beneficial when computers need to access the same resource regularly, such as remote desktop access and file sharing between devices. Static IPs remain unchanged until manually changed by an administrator.
Dynamic IP addresses
A dynamic IP address changes each time you connect to a new network. This type of address is beneficial for reducing the amount of IP address space needed from the ISP, as well as providing a more secure connection. Dynamic IP addresses are assigned to each computer or device on the network when they join it. External IP addresses are almost always dynamic.
Special IP addresses
Special IP addresses are used to identify particular services, such as servers, web hosting, and other uses. These special-use IP addresses include the IANA IPv4 Special-Purpose Address Registry, loopback addresses, wildcard addresses, multicast addresses, limited broadcasts, and directed broadcasts.
IANA IPv4 Special-Purpose Address Registry
IANA IPv4 Special-Purpose Address Registry is a registry managed by the Internet Engineering Task Force (IETF) for protocol assignments in the address block of 192.0.0.0/24. It consists of all the current IETF assignments from this particular address block and provides a convenient centralized database for tracking protocol assignment usage. It’s an important resource for those needing special-purpose IP addresses, as it provides easy access to the latest updates and provides information about IETF-assigned protocol assignments.
Loopback address
A loopback address is a special IP address that serves as a virtual interface, allowing your computer to connect to itself. It’s usually used for testing or diagnostics purposes, such as checking network configurations and running programs that require two or more network connections simultaneously. On IPv4, this address ranges from 127.0.0.1 to 127.255.255.255.
Wildcard address
A wildcard address is a special IP address that matches any host or domain name, allowing for a broad range of access from the same source IP address. It’s commonly used for websites and applications needing multiple services from the same IP address. Wildcard addresses are usually in the form of an asterisk (*) followed by a number or string that matches any IP address.
Multicast address
A multicast address is a special type of IP address used for sending data to multiple computers on a network simultaneously. It’s a helpful tool for sending large files, such as multimedia streams and video, as it reduces bandwidth usage by sending the same data stream to multiple computers at once. Multicast addresses range between 224.0.0.1 and 239.255.255.255 on IPv4 networks.
Limited broadcast
A limited broadcast is a special type of IP address used to send data to a specific subnet. It’s used to find the gateway address on a network or to send messages out to all hosts within a certain range. Limited broadcasts are usually in the form of an IP address with all 255s in the last octet.
Directed broadcast
A directed broadcast is a special type of IP address used to send data to all computers on an external network. It’s usually used for network administration, such as notifying all computers on the network about a change in configuration or retrieving information from multiple sources.
Different formats of IPv6 addresses
Since IPv6 addresses consist of 128 bits (in contrast to IPv4’s 32 bits), they allow for much greater variation and flexibility than IPv4. Three of the most common types of IPv6 addresses are global unicast, link local, and unique local addresses.
Global unicast address
Global unicast addresses are globally unique IP addresses assigned to a single interface or host. These addresses are used for communication between two systems over the public internet, or within a private network. Global unicast addresses are structured in eight 16-bit blocks, each separated by a colon (e.g., 2001:0db8:0000:0000:0000:ff00:0042:8329).
Link-local address
Link-local addresses are used for communication between nodes on the same local link or subnet. Link-local addresses are not routable over the public internet but can be used within a private network. Link-local addresses start with fe80::/10 and have a 64-bit interface identifier appended at the end (e.g., fe80::d3b0:f2f7:a5b1).
Unique local address
Unique local addresses (ULAs) are similar to global unicast addresses, but they are only intended for use within private networks and cannot be routed over the public internet. ULAs start with fc00::/7 and have a 40-bit randomly generated interface identifier appended at the end (e.g., fd37:6c82:f9a5::1).
How to find your IP address
Knowing your IP address can be useful in many different ways, from troubleshooting network issues to accessing geo-restricted content. Here’s how you can look up your IP address on Mac and Windows computers.
How to find your IP address on a Mac (OS X 10.5 and later)
There are two methods for finding your IP address on macOS devices: through your System Preferences, or in your macOS Terminal.
How to find your IP address in macOS using System Preferences
- Go to the Apple menu and select System Preferences.
- Click on Network.
- Select your active network connection, such as AirPort or Ethernet, from the list on the left.
- Your IP address will be displayed in the IPv4 Address field to the right.
How to find your IP address in macOS Terminal
- Open the Terminal application located in Applications > Utilities.
- For Ethernet: ipconfig getifaddr en1
- For Wi-Fi: ipconfig getifaddr en0
- For public IP address: curl ifconfig.me
- The command will return your IP address.
How to find your IP address on Windows 11
On Windows, you can find your IP address in your system settings, or via command prompt.
- How to find your IP address in your Windows Settings
- Open the Settings app.
- Click on Network & internet.
- Click Properties, and scroll down to see your IP address.
How to find your IP address in Windows using Command Prompt
- Open the Command Prompt by typing cmd into the Windows search bar.
- To find your public IP address, type nslookup myip.opendns.com. resolver1.opendns.com into the Command Prompt and press Enter.
- Your IP address will be listed under IPv4 Address.
How to find your IP address on any device
The fastest and easiest way to find your public IPv4 or IPv6 address is simply to fire up Google, type in “my ip,” and click search.
Why you might want to know your IP address
One of the most common reasons you would want to find your IP address is to troubleshoot network issues. Your IP address can help you identify problems with your internet connection or router, as well as help diagnose any technical issues you may be having with other devices on the same network.
You may also want to access geo-restricted content. Many websites and streaming services use your IP address to determine where you are located and block access if you’re outside their allowed area. Knowing your IP address can help you bypass these restrictions by using a virtual private network (VPN) .
In addition, knowing your IP address is necessary when setting up new devices on your network. For example, when configuring a wireless printer or router, you must know the IP address to connect it properly.
Further, if you need to access a device remotely over the internet, you’ll need to know its IP address and your own to configure the connection.
Finally, some people are just curious. It’s always interesting to know more about how the internet works, and understanding what an IP address is and how it functions can be a great way to learn more about the technology behind it all.
IP address security threats
IP address information is valuable to cybercriminals, as it can be used to track and target you or your business. Some of the main security threats include tracking and online stalking, spoofing, hacking your devices, or attacking your network.
- Tracking and online stalking: Criminals or people/entities with nefarious intentions can use IP address information to find out where you are geographically located and use other services to determine your identity or even where you live.
- Spoofing: Spoofing attacks are when a cyber attacker creates data packets with a false IP source address in order to trick the firewall or receiver into believing it’s safe.
- Hacking your devices: Knowing your IP address can allow malicious actors to identify vulnerabilities in your device and attempt to gain access or even seize control.
- Attacking your network: Cybercriminals can also use IP addresses to target a group of devices, such as a home network or business servers, in an attempt to gain access and carry out malicious activities. Knowing the IP addresses of an organization is also a prelude to a DDoS attack .
Many of these risks can be mitigated by using a virtual private network (VPN) or taking other security measures, such as regularly changing your IP address and maintaining an effective, advanced firewall .
Bottom line: Understanding IP addresses
IP addresses are an integral component of the internet and how it functions. It’s important to understand the basics of how IP addresses work and the different types of IP addresses.
Knowing your own IP address can come in handy for purposes as diverse as gaming, setting up remote access, or troubleshooting network issues.
It’s also important to be aware of the potential security threats associated with having an active IP address and take the necessary steps to mitigate the risks.
Using a virtual private network (VPN) to hide your IP address can help protect your network and let you browse more freely. Here’s a guide to the top VPN services available today.

Related Articles
Top 9 enterprise wi-fi solutions for businesses in 2024, what is a router in networking core function explained, what is optical networking complete explanation, get the free newsletter.
Subscribe to Daily Tech Insider for top news, trends, and analysis.
Latest Articles
9 best network switches for 2024: speed and features compared, 8 best firewalls for small & medium business (smb) networks, top 10 mobile security threats for devices, networks, and apps — and how to prevent them, follow us on social media, explore more.

Home Network IP address Assignment
IP address can be assigned:
- Automatically
Manual IP Address Assignment
Manually assigned addresses are known as static addresses.
When assigning a static IP address you will also need to enter other important address information.
The screen shot below shows the static address assignment on my Windows 10 computer however all devices have a similar form for the IP address assignment.
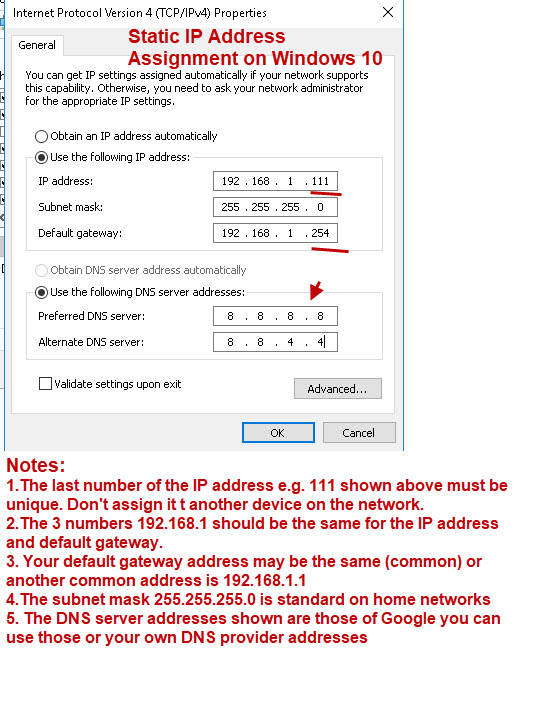
1. My home network use the network address 192.168.1 (first three numbers) also common is 192.168.0 and 10.x.x.x
2. The default gateway is the address of your home router. This is assigned to the router as a static IP address. Common gateway addresses use the first or last addresses of the range which are 1 and 254 .
3. The subnet mask is important as is usually 255.255.255.0
4. You need the address of 1 DNS server to access websites on the Internet. The Google DNS server is available to use for free but you can use your ISP DNS servers.
5. You can choose to manually assign the DNS addresses and automatically assign the IP address or vice versa.
6. Make a note of the addresses you assign so as to avoid address conflicts .

Automatic IP Address Assignment- DHCP
This is the default configuration on most devices.
This is what it looks like on my Windows 10 computer.
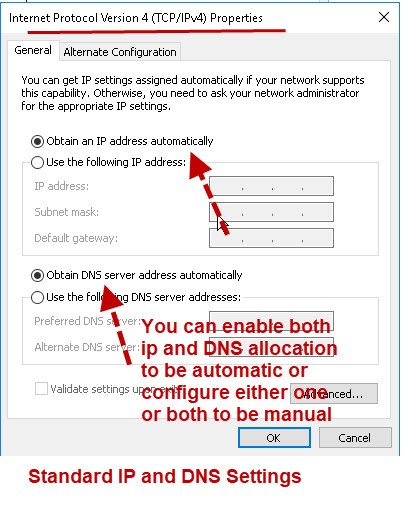
On home networks this service is provided by the home router which has DHCP enabled by default.
If no DHCP server is available Windows machines (some versions) will auto assign an address. This address starts with 169.254
e.g. 169.254.0.1
No DNS server address will be allocated which means that you will not have access to the internet unless you know the IP address of the server.
Finding Your IP Address,Gateway Address etc?
You may need to find out what DNS servers you are using or the IP or MAC address of:
- Your Home Router.
- Your own computer/tablet/phone
The main tool you use is the ipconfig (windows) or ifconfig (linux) tool.
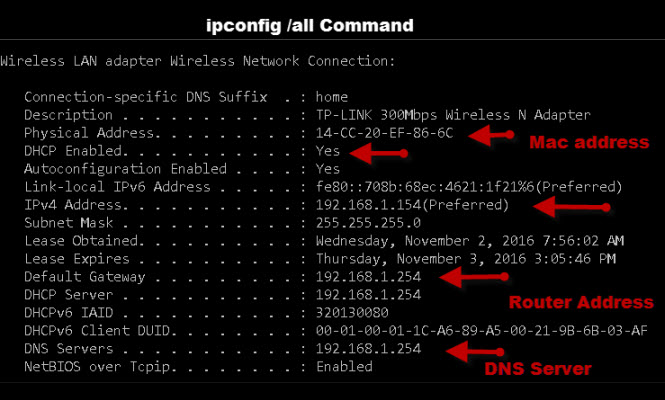
The screen shot below shows the ipconfig command use with the /all switch. i.e. ipconfig/all
Common Questions and Basic Troubleshooting
Q- what happens if dhcp fails.
A- Because IP addresses are leased from the DHCP server your client machine will keep its existing address until the lease expires usually 1 day. and so will run normally for a while.
New machines joining the network will not get an IP address and may auto assign one depending on the device.
They will not work with existing machines and because they don’t have a DNS server address they wont be able to access the Internet.
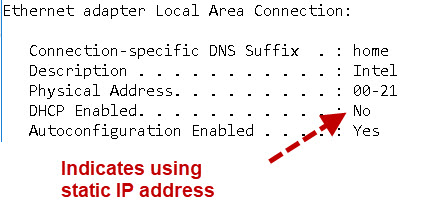
Q -How do I know if I have a static IP address or a automatically assigned one?
A- You can look at the network adapter properties or on Windows open a command line and type
ipconfig /all
If you see the entry DHCP Enabled .. No then you are using a static IP address.
Q- What happens if a have two DHCP servers on my Home Network?
A- This may cause strange behaviour and is to be avoided. On home networks the home router provides the DHCP service by default. If you try to reuse old routers as Wireless access points then you can run into this problem
Q -What is The IP address of my router or default gateway?
A- You can find it using the ipconfig command line tool (ifconfig on Linux) as shown above. When viewing your configuration some devices refer to it as the default router whereas other use the term default gateway.
In the screen shot above it is 192.168.1.254
Your home router generally comes with a static IP address assigned. Common addresses are:
192.168.1.254 and 192.168.1.1
However you can change it if you want, but because this is the main device on the home network I would leave it as it is. If you do change it you will need to make changes on any devices that use a static IP address.
Q- What happens if I assign the same IP address to two separate devices?
A- You get an IP address conflict and the devices wont work.
Q- Do I need to subnet my Home Network?
A- Almost certainly no. See Home network Subnet masks explained .
Q- What is ARP?
A- ARP stands for address resolution protocol and translates an IP address to a MAC address.
Related tutorials and Resources
- How to Setup and Configure your Home Router
- Setting Up Static IP Addresses on Windows 10
- Understanding DHPC on Home Networks
- Name Resolution on Home Networks
- Setting Up A DNS Server using DNSMasq
- Understanding Multicast DNS
- Home networking Course
I thoroughly enjoyed reading this and other articles on “home networks”. As a long time computer user & developer, I found your writing style refreshing. I look forward to future essays on related topics such as home router configuration, home LAN “tuning” &”trouble shooting”. ~~~ 0:¬ Dan
Very helpful. Thank you. Would you say it is beneficial to assign IP addresses or just allow the system to get on with it?
You should always let the system do it unless you really have a need to do it manually you might find this useful https://youtu.be/2yOMNugsdE0 rgds Steve
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Privacy Overview
Subnet Cheat Sheet – 24 Subnet Mask, 30, 26, 27, 29, and other IP Address CIDR Network References

As a developer or network engineer, you may need to occasionally look up subnet mask values and figure out what they mean.
To make your life easier, the freeCodeCamp community has made this simple cheat sheet. Just scroll or use Ctrl/Cmd + f to find the value you're looking for.
Here are the charts, followed by some explanations of what they mean.
* /31 is a special case detailed in RFC 3021 where networks with this type of subnet mask can assign two IP addresses as a point-to-point link.
And here's a table of the decimal to binary conversions for subnet mask and wildcard octets:
Note that the wildcard is just the inverse of the subnet mask.
If you are new to network engineering, you can get a better idea of how computer networks work here .
Finally, this cheat sheet and the rest of the article is focused on IPv4 addresses, not the newer IPv6 protocol. If you'd like to learn more about IPv6, check out the article on computer networks above.
How Do IP Address Blocks Work?
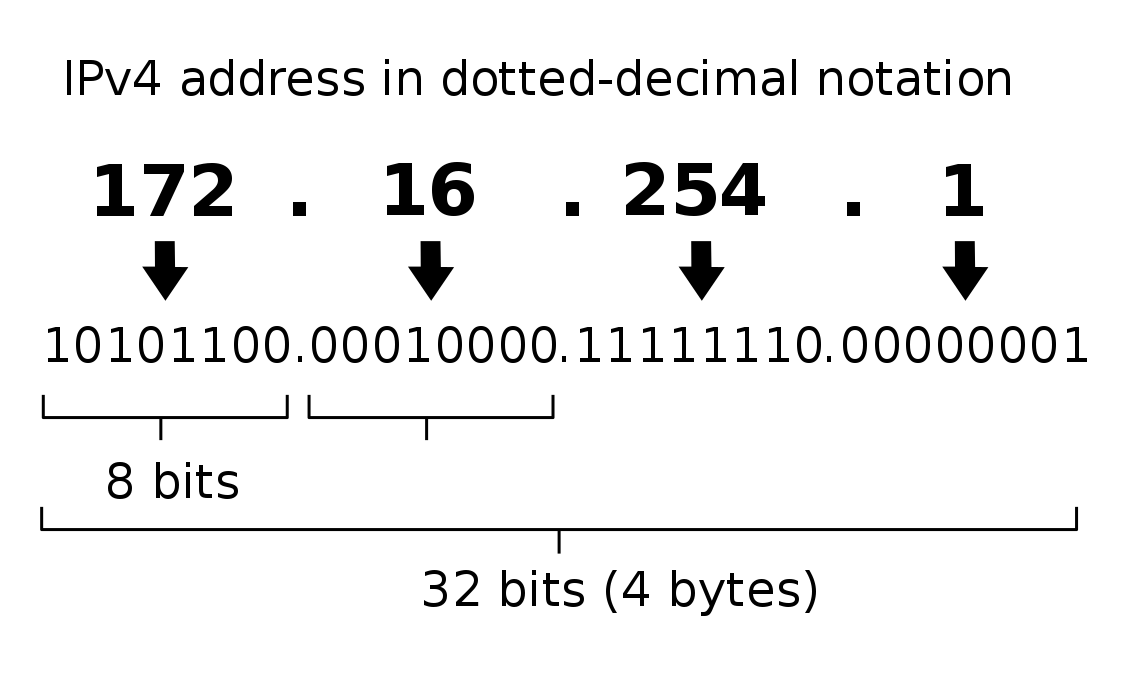
IPv4 addresses like 192.168.0.1 are really just decimal representations of four binary blocks.
Each block is 8 bits, and represents numbers from 0-255. Because the blocks are groups of 8 bits, each block is known as an octet . And since there are four blocks of 8 bits, every IPv4 address is 32 bits.
For example, here's what the IP address 172.16.254.1 looks like in binary:
To convert an IP address between its decimal and binary forms, you can use this chart:
The chart above represents one 8 bit octive.
Now lets say you want to convert the IP address 168.210.225.206 . All you need to do is break the address into four blocks ( 168 , 210 , 225 , and 206 ), and convert each into binary using the chart above.
Remember that in binary, 1 is the equivalent to "on" and 0 is "off". So to convert the first block, 168 , into binary, just start from the beginning of the chart and place a 1 or 0 in that cell until you get a sum of 168 .
For example:
128 + 32 + 8 = 168, which in binary is 10101000 .
If you do this for the rest of the blocks, you'd get 10101000.11010010.11100001.11001110 .
What is Subnetting?
If you look at the table above, it can seem like the number of IP addresses is practically unlimited. After all, there are almost 4.2 billion possible IPv4 addresses available.
But if you think about how much the internet has grown, and how many more devices are connected these days, it might not surprise you to hear that there's already a shortage of IPv4 addresses .
Because the shortage was recognized years ago, developers came up with a way to split up an IP address into smaller networks called subnets.
This process, called subnetting, uses the host section of the IP address to break it down into those smaller networks or subnets.
Generally, an IP address is made up of network bits and host bits:
So generally, subnetting does two things: it gives us a way to break up networks into subnets, and allows devices to determine whether another device/IP address is on the same local network or not.
A good way to think about subnetting is to picture your wireless network at home.
Without subnetting, every internet connected device would need its own unique IP address.
But since you have a wireless router, you just need one IP address for your router. This public or external IP address is usually handled automatically, and is assigned by your internet service provider (ISP).
Then every device connected to that router has its own private or internal IP address:
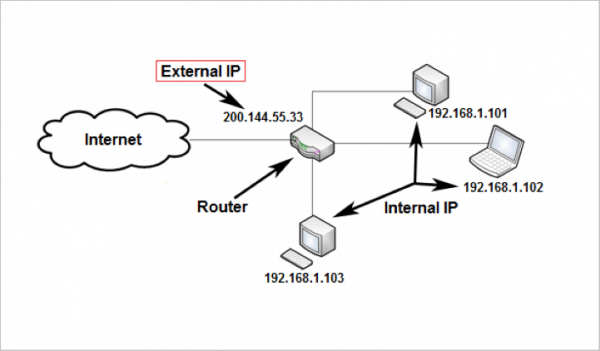
Now if your device with the internal IP address 192.168.1.101 wants to communicate with another device, it'll use the IP address of the other device and the subnet mask.
The combination of the IP addresses and subnet mask allows the device at 192.168.1.101 to figure out if the other device is on the same network (like the device at 192.168.1.103 ), or on a completely different network somewhere else online.
Interestingly, the external IP address assigned to your router by your ISP is probably part of a subnet, which might include many other IP addresses for nearby homes or businesses. And just like internal IP addresses, it also needs a subnet mask to work.
How Subnet Masks Work
Subnet masks function as a sort of filter for an IP address. With a subnet mask, devices can look at an IP address, and figure out which parts are the network bits and which are the host bits.
Then using those things, it can figure out the best way for those devices to communicate.
If you've poked around the network settings on your router or computer, you've likely seen this number: 255.255.255.0 .
If so, you've seen a very common subnet mask for simple home networks.
Like IPv4 addresses, subnet masks are 32 bits. And just like converting an IP address into binary, you can do the same thing with a subnet mask.
For example, here's our chart from earlier:
Now let's convert the first octet, 255:
Pretty simple, right? So any octet that's 255 is just 11111111 in binary. This means that 255.255.255.0 is really 11111111.11111111.11111111.00000000 in binary.
Now let's look at a subnet mask and IP address together and calculate which parts of the IP address are the network bits and host bits.
Here are the two in both decimal and binary:
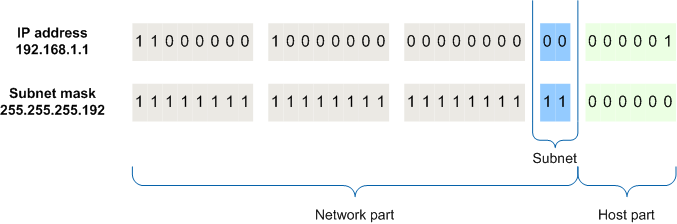
With the two laid out like this, it's easy to separate 192.168.0.101 into network bits and host bits.
Whenever a bit in a binary subnet mask is 1, then the same bit in a binary IP address is part of the network, not the host.
Since the octet 255 is 11111111 in binary, that whole octet in the IP address is part of the network. So the first three octets, 192.168.0 , is the network portion of the IP address, and 101 is the host portion.
In other words, if the device at 192.168.0.101 wants to communicate with another device, using the subnet mask it knows that anything with the IP address 192.168.0.xxx is on the same local network.
Another way to express this is with a network ID, which is just the network portion of the IP address. So the network ID of the address 192.168.0.101 with a subnet mask of 255.255.255.0 is 192.168.0.0 .
And it's the same for the other devices on the local network ( 192.168.0.102 , 192.168.0.103 , and so on).
What Does CIDR Mean and What is CIDR Notation?
CIDR stands for Classless Inter-Domain Routing, and is used in IPv4, and more recently, IPv6 routing.
CIDR was introduced in 1993 as a way to slow the usage of IPv4 addresses, which were quickly being exhausted under the older Classful IP addressing system that the internet was first built on.
CIDR encompasses a couple of major concepts.
The first is Variable Length Submasking (VLSM), which basically allowed network engineers to create subnets within subnets. And those subnets could be different sizes, so there would be fewer unused IP addresses.
The second major concept CIDR introduced is CIDR notation.
CIDR notation is really just shorthand for the subnet mask, and represents the number of bits available to the IP address. For instance, the /24 in 192.168.0.101/24 is equivalent to the IP address 192.168.0.101 and the subnet mask 255.255.255.0 .
How to Calculate CIDR Noation
To figure out the CIDR notation for a given subnet mask, all you need to do is convert the subnet mask into binary, then count the number of ones or "on" digits. For example:
Because there's three octets of ones, there are 24 "on" bits meaning that the CIDR notation is /24 .
You can write it either way, but I'm sure you'll agree that /24 is a whole lot easier to write than 255.255.255.0 .
This is usually done with an IP address, so let's take a look at the same subnet mask with an IP address:
The first three octets of the subnet mask are all "on" bits, so that means that the same three octets in the IP address are all network bits.
Let's take a look at the last forth octet in a bit more detail:
In this case, because all the bits for this octet in the subnet mask are "off", we can be certain that all of the corresponding bits for this octet in the IP address are part of the host.
When you write CIDR notation it's usually done with the network ID. So the CIDR notation of the IP address 192.168.0.101 with a subnet mask of 255.255.255.0 is 192.168.0.0/24 .
To see more examples of how to calculate the CIDR notation and network ID for a given IP address and subnet mask, check out this video:
Classful IP Addressing
Now that we've gone over some basic examples of subnetting and CIDR, let's zoom out and look at what's known as Classful IP addressing.
Back before subnetting was developed, all IP addresses fell into a particular class:
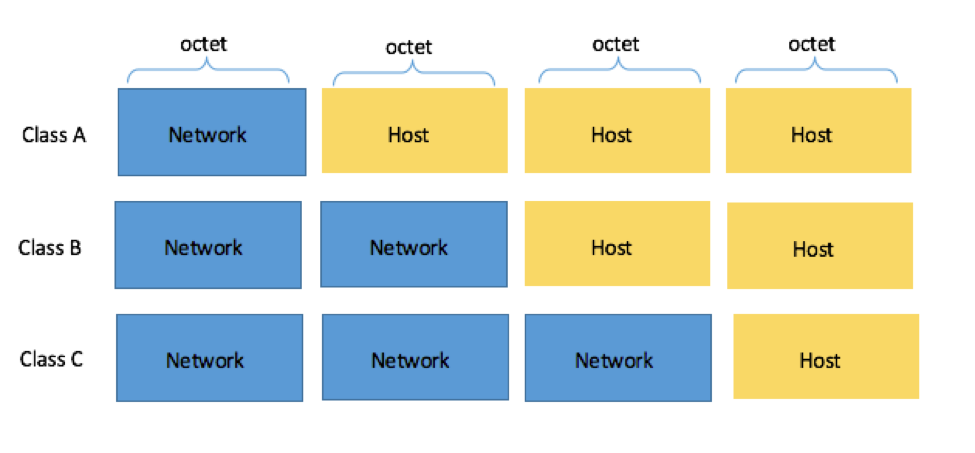
Note that there are class D and E IP addresses, but we'll go into these in more detail a bit later.
Classful IP addresses gave network engineers a way to provide different organizations with a range of valid IP addresses.
There were a lot of issues with this approach that eventually lead to subnetting. But before we get into those, let's take a closer look at the different classes.
Class A IP Addresses
For Class A IP addresses, the first octet (8 bits / 1 byte) represent the network ID, and the remaining three octets (24 bits / 3 bytes) are the host ID.
Class A IP addresses range from 1.0.0.0 to 127.255.255.255 , with a default mask of 255.0.0.0 (or /8 in CIDR).
This means that Class A addressing can have a total of 128 (2 7 ) networks and 16,777,214 (2 24 -2) usable addresses per network.
Also, note that the range 127.0.0.0 to 127.255.255.255 within the Class A range is reserved for host loopback address (see RFC5735 ).
Class B IP Addresses
For Class B IP addresses, the first two octets (16 bits / 2 bytes) represent the network ID and the remaining two octets (16 bits / 2 bytes) are the host ID.
Class B IP addresses range from 128.0.0.0 to 191.255.255.255 , with a default subnet mask of 255.255.0.0 (or /16 in CIDR).
Class B addressing can have 16,384 (2 14 ) network addresses and 65,534 (2 16 ) usable addresses per network.
Class C IP Addresses
For Class C IP addresses, the first three octets (24 bits / 3 bytes) represent the network ID and the last octet (8 bits / 1 bytes) is the host ID.
Class C IP Addresses range from 192.0.0.0 to 223.255.255.255 , with a default subnet mask of 255.255.255.0 (or /24 in CIDR).
Class C translates to 2,097,152 (2 21 ) networks and 254 (2 8 -2) usable addresses per network.
Class D and Class E IP Addresses
The last two classes are Class D and Class E.
Class D IP addresses are reserved for multicasts. They occupy the range from 224.0.0.0 through 239.255.255.255 .
Class E IP addresses are experimental, and are anything over 240.0.0.0 .
The Issue with Classful IP Addresses
The main issue with classful IP addresses is that it wasn't efficient, and could lead to a lot of wasted IP addresses.
For example, imagine that you're part of a large organization back then. Your company has 1,000 employees, meaning that it would fall into class B.
But if you look above, you'll see that a class B network can support up to 65,534 usable addresses. That's way more than your organization would likely need, even if each employee had multiple devices with a unique address.
And there was no way your organization could fall back to class C – there just wouldn't be enough usable IP addresses.
So while classful IP addresses were used around the time IPv4 addresses became widespread, it quickly became clear that a better system would be necessary to ensure we wouldn't use up all of the ~4.2 billion usable addresses.
Classful IP addresses haven't been used since they were replaced by CIDR in 1993, and are mostly studied to understand early internet architecture, and why subnetting is important.
I hope this cheat sheet has been a helpful reference for you
If you found this helpful, please share it with your friends so more people can benefit from it.
Also, feel free to reach out on Twitter and let me know what you think.
Read more posts .
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
How-To Geek
How to assign a static ip address in windows 10 or windows 11.
When organizing your home network it's easier to assign each computer it's own IP address than using DHCP. Here we will take a look at doing it in XP,
Quick Links
What is a static ip address, assign static ip addresses via your router, how to set a static ip address in windows 11, how to set a static ip address in windows 10, how to set a static ip address in windows 7 or 8 using "network connections", set a static ip address in windows vista, set a static ip address in windows xp, key takeaways.
- To set a static IP address in Windows 10 or 11, open Settings -> Network & Internet and click Properties for your active network.
- Choose the "Edit" button next to IP assignment and change the type to Manual.
- Flip the IPv4 switch to "On", fill out your static IP details, and click Save.
Sometimes, it's better to assign a PC its own IP address rather than letting your router assign one automatically. Join us as we take a look at assigning a static IP address in Windows.
A static IP address is manually set to a permanent, fixed address rather than being assigned automatically by your router using a procotol known as Dynamic Host Configuration Protocol (DHCP). DHCP is a handy way for devices to connect to your network more easily, because you don't have to configure IP addressing for each new device yourself. The downside to automatic addressing is that it's possible for a device's IP address to change from time to time, which is why people choose static IPs for certain types of devices. For example:
- You have a device like a home media server that you want to be able to find using the same IP address or host name each time.
- You have certain apps that can only connect to network devices using their IP address. In particular, many older networking apps suffer this limitation.
- You forward ports through your router to devices on your network. Some routers play nice with port forwarding and dynamic IP addresses; others do not.
Whatever your reason, assigning static IP addresses to devices is not difficult, but you do have a choice to make---whether to do it from the router or on the device itself.
Related: How to Set a Static IP Address in Ubuntu
While this article covers assigning static IP addresses to PCs within Windows itself, there is another way to go about it. Many routers allow you to assign a pool of IP addresses that are handed out to specific devices (based on the device's physical, or MAC address). This method offers a couple of significant advantages:
- IP addresses are still managed by the router, meaning that you won't have to make (and keep up with) changes on each individual device.
- It's easier to assign addresses within the same IP address pool your router uses.
This article is about assigning static IP addresses directly to PCs running Windows. We've already got a great guide on How to Set Static IP Addresses On Your Router , so if that's the way you want to go, be sure to give it a read.
With all that in mind, though, let's take a look at how to assign static IP addresses within any version of Windows.
Related: How to Find Your Router's IP Address on Any Computer, Smartphone, or Tablet
To set a static IP address in Windows 11, you'll want to open Settings, go to Network & Internet, and then find the Properties for your network. Inside there you'll be able to click the Edit button for IP Assignment and then fill out the manual network details.
First, open up the Settings app and then find Network & Internet on the left-hand side. You'll be presented with a panel that shows your current network connection. You can click where it says "Properties" right underneath the network, or if you have multiple network connections you can drill down into the specific network to see the IP address details for each one . In this case it's called "Ethernet", but you will most likely see "Wi-Fi" as the option to choose.
Once you've drilled down into the network connection that you want to set a manual IP for, scroll down until you see "IP Assignment" and then click the Edit button to the right.
Once there, you'll flip the drop-down to "Manual" and switch the IPv4 switch to "On". At this point you can fill out your network details and click Save to finish.
You can also use the old-school Network Connections panel in Windows 11, so if you prefer to use that method, keep reading.
If you're interested in more advanced networking, you might need to set up a static TCP/IP route , reset the entire TCP/IP stack on Windows , check open TCP/IP ports , find your MAC address on Windows , or find your IP address from the Command Prompt . We've got you covered there too.
To set a static IP address in Windows 10, you'll need to open the Settings app and drill down to Network & Internet. From there you'll select Properties for your network, and then the Edit button next to IP Assignment where you can input a manual IP address.
First, open the Settings app and locate the Network & Internet button.
On the next screen you'll see your network status, which should show you your active network. Here you'll want to click the Properties button. If you have multiple different networks, you could select them from the left-hand menu---in our case you'll notice we have both Wi-Fi and Ethernet networks, so you'll want to pick the one that you are trying to set a manual IP address for. You'll notice this is the same method we use when we're trying to find an IP address on Windows 10 .
On the network properties screen, scroll down until you see "IP settings" and click the Edit button under "IP assignment".
In the resulting popup window, change the Edit IP settings dropdown to Manual and then flip the IPv4 switch to "On". Fill out the details, click Save, and you should be good to go.
You might need to reboot to get all of your applications to work properly, just because it's Windows.
It's worth noting that you can use the old Network Connections method to set an IP address in any version of Windows, so if you prefer that method, keep reading.
To change the computer's IP address in Windows 7, you'll need to open the "Network Connections" window. Hit Windows+R, type "ncpa.cpl" into the Run box, and then hit Enter.
In the "Network Connections" window, right-click the adapter for which you want to set a static IP address, and then select the "Properties" command.
In the properties window for the adapter, select "Internet Protocol Version 4 (TCP/IPv4)" and then click the "Properties" button.
Select the "Use the following IP address" option, and then type in the IP address, subnet mask, and default gateway that corresponds with your network setup. Next, type in your preferred and alternate DNS server addresses. Finally, select the "Validate settings upon exit" option so that Windows immediately checks your new IP address and corresponding information to ensure that it works. When you're ready, click the "OK" button.
And then close out of the network adapter's properties window.
Windows automatically runs network diagnostics to verify that the connection is good. If there are problems, Windows will give you the option of running the Network troubleshooting wizard. However, if you do run into trouble, the wizard likely won't do you too much good. It's better to check that your settings are valid and try again.
Changing your IP from DHCP to a Static address in Vista is similar to other versions of Windows, but getting to the correct location is a bit different. Open the Start Menu, right-click on Network, and select Properties.
The Network and Sharing Center opens...click on Manage network connections.
Right-click on the network adapter you want to assign an IP address and click Properties.
Highlight Internet Protocol Version 4 (TCP/IPv4) then click the Properties button.
Now change the IP, Subnet mask, Default Gateway, and DNS Server Addresses. When you're finished click OK.
You'll need to close out of Local Area Connection Properties for the settings to go into effect.
Open the Command Prompt and use the
command to verify that the changes were successful.
To set a Static IP in Windows XP, right-click the "My Network Places" icon, and then select "Properties."
Right-click the adapter for which you want to set the IP, and then select "Properties" from the context menu.
Select the "Internet Protocol (TCP/IP)" entry, and then click the "Properties" button.
Select the "Use the following IP address" option. Type in the IP address, subnet mask, default gateway, and DNS server addresses you want to use. When you're finished, click the "OK" button.
You will need to close out of the adapter's properties window before the changes go into effect.
And you can verify your new settings by using the
command at the command prompt.
By and large, it's better to let most of your devices have their IP addresses assigned automatically by your router. Occasionally, though, you might want to set a static IP address for a particular device. While you can set static IP addresses directly on your devices (and this article has shown you how to do just that on Windows PCs), we still recommending setting up static IP addressing on your router if possible. It will just make life easier.
Related: How to Find Any Device's IP Address, MAC Address, and Other Network Connection Details
Methods of Assigning IP Addresses

This section discusses methods of assigning IP addresses to end systems and explains their influence on administrative overhead. Address assignment includes assigning an IP address, a default gateway, one or more domain name servers that resolve names to IP addresses, time servers, and so forth. Before selecting the desired IP address assignment method, the following questions should be answered:
■ How many devices need an IP address?
■ Which devices require static IP address assignment?
■ Is IP address renumbering expected in the future?
■ Is the administrator required to track devices and their IP addresses?
■ Do additional parameters (default gateway, name server, and so forth) have to be configured?
■ Are there any availability issues?
■ Are there any security issues?
Static Versus Dynamic IP Address Assignment Methods
Following are the two basic IP address assignment strategies:
■ Static: An IP address is statically assigned to a system. The network administrator configures the IP address, default gateway, and name servers manually by entering them into a special file or files on the end system with either a graphical or text interface. Static address assignment is an extra burden for the administrator—especially on large-scale networks— who must configure the address on every end system in the network.
■ Dynamic: IP addresses are dynamically assigned to the end systems. Dynamic address assignment relieves the administrator of manually assigning an address to every network device. Instead, the administrator must set up a server to assign the addresses. On that server, the administrator defines the address pools and additional parameters that should be sent to the host (default gateway, name servers, time servers, and so forth). On the host, the administrator enables the host to acquire the address dynamically; this is often the default. When IP address reconfiguration is needed, the administrator reconfigures the server, which then performs the host-renumbering task. Examples of available address assignment protocols include Reverse Address Resolution Protocol, Boot Protocol, and DHCP. DHCP is the newest and provides the most features.
When to Use Static or Dynamic Address Assignment
To select either a static or dynamic end system IP address assignment method or a combination of
the two, consider the following:
■ Node type: Network devices such as routers and switches typically have static addresses. End-user devices such as PCs typically have dynamic addresses.
■ The number of end systems: If there are more than 30 end systems, dynamic address assignment is preferred. Static assignment can be used for smaller networks.
■ Renumbering: If renumbering is likely to happen and there are many end systems, dynamic address assignment is the best choice. With DHCP, only DHCP server reconfiguration is needed; with static assignment, all hosts must be reconfigured.
■ Address tracking: If the network policy requires address tracking, the static address assignment method might be easier to implement than the dynamic address assignment method. However, address tracking is also possible with dynamic address assignment with additional DHCP server configuration.
■ Additional parameters: DHCP is the easiest solution when additional parameters must be configured. The parameters have to be entered only on the DHCP server, which then sends the address and those parameters to the clients.
■ High availability: Statically assigned IP addresses are always available. Dynamically assigned IP addresses must be acquired from the server; if the server fails, the addresses cannot be acquired. To ensure reliability, a redundant DHCP server is required.
■ Security: With dynamic IP address assignment, anyone who connects to the network can acquire a valid IP address, in most cases. This might be a security risk. Static IP address assignment poses only a minor security risk.
The use of one address assignment method does not exclude the use of another in a different part of the network.
Guidelines for Assigning IP Addresses in the Enterprise Network
The typical enterprise network uses both static and dynamic address assignment methods. As shown in Figure 6-14, the static IP address assignment method is typically used for campus network infrastructure devices, in the Server Farm and Enterprise Data Center modules, and in the modules of the Enterprise Edge (the E-Commerce, Internet Connectivity, Remote Access and VPN, and WAN and MAN and Site-to-Site VPN modules). Static addresses are required for systems such as servers or network devices, in which the IP address must be known at all times for connectivity, general access, or management.
Figure 6-14 IP Address Assignment in an Enterprise Network
Enterprise Campus
Server Farm
Enterprise Edge
Continue reading here: Name Resolution
Was this article helpful?
Recommended Books
- Network Design: Principles and Practices
- Network Design and Management
- Network Design Cookbook: Architecting Cisco Networks
- Network Design Fundamentals
Related Posts
- Determining the Size of the Network
- Distribution Layer Functionality
- Configuring a Routed Port
- Hierarchical IP Address Design and Summarization
- Answers to the Chapter 6 QA Section
- IP Standard Access Lists - Network Design
Readers' Questions
How do know that your network is configured to assign an ip address to the thermostat?
To determine if your network is configured to assign an IP address to the thermostat, you can follow these steps: Check if your thermostat is connected to Wi-Fi: Ensure that your thermostat is successfully connected to your home Wi-Fi network. Most thermostats have an indicator light or display that shows the Wi-Fi connectivity status. Access your router's settings: Open a web browser on a device connected to the same network as your thermostat and enter your router's IP address (e.g., 192.168.1.1) in the address bar. Consult your router's user manual or contact your internet service provider for assistance if you don't know the router's IP address. Log in to your router's admin interface: Enter your router's admin username and password to log in to the router's settings page. If you haven't changed the login credentials, you may find the default ones on the router or in its manual. Locate the DHCP settings: DHCP (Dynamic Host Configuration Protocol) is responsible for assigning IP addresses to devices on your network. Find the DHCP settings page in your router's admin interface. It might be under a section like "LAN settings," "Network settings," "DHCP settings," or similar. Verify DHCP is enabled: Ensure that DHCP is enabled or turned on in your router's settings. This setting allows your router to assign IP addresses dynamically. Typically, DHCP is enabled by default. Check the assigned IP address table: Look for a section or tab in your router's settings that displays the list of devices connected to your network along with their assigned IP addresses. The table may be labeled as "Connected Devices," "Device list," "DHCP Client List," or alike. Ensure your thermostat appears in the list and has been assigned an IP address. If your thermostat appears in the assigned IP address table, it means your network is configured to assign an IP address to it. If it doesn't, you may need to troubleshoot the thermostat's Wi-Fi connection or contact the manufacturer's support for further assistance.
What protocol automatically configures ip configuration for a client?
The protocol that automatically configures IP configuration for a client is called DHCP (Dynamic Host Configuration Protocol). It allows clients to obtain IP addresses, subnet masks, default gateways, and other network configuration parameters automatically from a DHCP server. This eliminates the need for manual configuration of IP addresses on each client device.
Which protocol can configure a computer's ip address and subnet mask automatically?
The Dynamic Host Configuration Protocol (DHCP) is designed to automatically configure a computer's IP address and subnet mask. By using DHCP, a computer can obtain network configuration information including IP address, subnet mask, default gateway, and DNS server(s) without manual intervention.
When using fixed allocation dhcp, what is used to determine a computer's ip?
When using fixed allocation DHCP (Dynamic Host Configuration Protocol), the computer's Media Access Control (MAC) address is used to determine its IP (Internet Protocol) address. The DHCP server maintains a mapping between MAC addresses and IP addresses, known as a DHCP reservation. When a computer with a specific MAC address requests an IP address from the DHCP server, it checks if a reservation exists for that MAC address. If a reservation is found, the DHCP server assigns the corresponding IP address to the computer.
Which type of server dynamically assigns an ip address to a host?
A dynamic host configuration protocol (DHCP) server is responsible for assigning dynamic IP addresses to hosts on a network.
Which allocation method can be used with a dynamic host configuration?
The Dynamic Host Configuration Protocol (DHCP) typically uses the "Dynamic Allocation" method for allocating IP addresses to client devices. In this method, a pool of IP addresses is created, and the DHCP server selects an available address from that pool and assigns it to the requesting device. The address is leased to the device for a specific period, known as the lease duration. Once the lease expires, the address can be released back to the pool and assigned to another device. This allows for efficient and flexible allocation of IP addresses in dynamic network environments.
Which address should be configured as the default gateway address of a client device?
The default gateway address for a client device should be the IP address of the router or gateway that connects the client device to the network. This router or gateway is responsible for forwarding network traffic between the client device and other networks or the internet.
How to statically assign an ip address?
To statically assign an IP address, follow these steps: On your device, go to the network settings. This can usually be found in the control panel or system preferences. Look for the network adapter or connection that you want to configure and select it. Go to the properties or settings of the network adapter. Look for an option such as "Internet Protocol Version 4 (TCP/IPv4)" and select it. Click on the "Properties" button or double-click on the selected option. In the properties window, select the option to "Use the following IP address". Enter the desired IP address, subnet mask, default gateway, and DNS server addresses. Contact your network administrator or Internet Service Provider (ISP) for the appropriate values if you're unsure. Click on "OK" or "Apply" to save the changes. Please note that the steps to assign a static IP address may vary slightly depending on the operating system and device you are using.
Why is dhcp for ipv4 preferred for use on large networks?
There are several reasons why DHCP (Dynamic Host Configuration Protocol) for IPv4 is preferred for use on large networks: Efficient IP address management: Large networks typically have a large number of devices that need unique IP addresses. DHCP allows for automated IP address allocation, ensuring that each device connected to the network receives a unique IP address without manual configuration. This eliminates the need for manual IP address management, making it easier to handle IP address assignments on a large scale. Centralized control: DHCP allows for centralized management and control over IP address allocation. Network administrators can configure DHCP servers to provide specific IP address ranges, subnet masks, default gateways, and other network settings. This centralized control simplifies the network administration process and ensures consistency across the network. Scalability: DHCP is highly scalable, allowing for the dynamic allocation and re-allocation of IP addresses as devices join or leave the network. As new devices connect to the network, DHCP servers can quickly assign them IP addresses from the available pool. Similarly, when devices disconnect or are powered off, their IP addresses can be released back to the pool for subsequent allocation. Reduced configuration errors: Manual configuration of IP addresses on a large network can be error-prone, leading to network connectivity issues or IP address conflicts. With DHCP, the chances of configuration errors are minimized as the IP addresses are assigned automatically. This improves network reliability and reduces troubleshooting efforts. Network flexibility: Large networks often require network reconfiguration or changes, such as adding new subnets or modifying IP address ranges. DHCP simplifies these network changes by allowing administrators to modify the DHCP server configuration, rather than manually updating settings on each individual device. Overall, DHCP for IPv4 offers a more efficient, scalable, and reliable method of IP address allocation and management on large networks, thereby reducing administrative overhead and providing greater control over network resources.
How to assign ip address to a clents?
To assign an IP address to a client, you will need to follow these steps: Access your router's settings: In order to assign an IP address to a client, you need to be connected to the network router or have administrative access to its settings. Determine the client's MAC address: The Media Access Control (MAC) address is a unique identifier assigned to a network interface card (NIC) of a client. You can usually find the MAC address on the client's network settings or by using command prompts such as "ipconfig /all" (Windows) or "ifconfig" (Linux/Mac). Reserve an IP address in the router's settings: Access your router's settings interface (generally through a web browser by entering the router's IP address). Look for a section such as "DHCP Reservation" or "Address Reservation" and select it. Locate the option to add a new reservation and enter the client's MAC address along with the IP address you want to assign to it. Save and apply the changes: Once you have entered the necessary information, save the changes and apply them. This will ensure that the router reserves the assigned IP address for the client in the future. Restart the client device: To ensure the client receives the new assigned IP address, it is recommended to restart the client device. This will trigger it to request an IP address from the router, and if the reservation was successful, it will be assigned the specific IP address you specified. Note: The specific process may vary slightly depending on the router model and firmware version. Consult your router's manual or manufacturer's website for detailed instructions if needed.
What methods are used to assign tcp/ip parameters to network hosts (select two.)?
Dynamic Host Configuration Protocol (DHCP): DHCP is a network management protocol that automatically assigns IP addresses and other TCP/IP parameters to network hosts. It allows hosts to obtain necessary network configuration settings from a DHCP server dynamically. Manual Configuration: In this method, the TCP/IP parameters are manually assigned to network hosts by network administrators. This involves manually configuring the IP address, subnet mask, default gateway, and other parameters in the network host's settings. It requires manual input and configuration on each host individually.
Which network address and subnet mask does apipa use (select two.)?
-Network Address: 169.254.0.0 -Subnet Mask: 255.255.0.0
Which part of the network assigns an ip address?
The Dynamic Host Configuration Protocol (DHCP) assigns IP addresses to devices on a network.
Which organization is responsible for allocating public ip addresses?
The Internet Assigned Numbers Authority (IANA) is responsible for allocating public IP addresses. It is an organization that works under the supervision of the Internet Corporation for Assigned Names and Numbers (ICANN). IANA administers the global Internet Protocol address space and other Internet Protocol-related symbols and numbers.
Is responsible for the internet's domain name system and the allocation of ip addresses?
The Internet Corporation for Assigned Names and Numbers (ICANN) is responsible for the internet's domain name system and the allocation of IP addresses.
What is the name of the organization responsible for assigning public ip addresses?
The organization responsible for assigning public IP addresses is the Internet Assigned Numbers Authority (IANA).
How to change static ip address?
1. Open the Control Panel. 2. Go to Network and Internet > Network and Sharing Center. 3. Click the Change Adapter Settings link on the left-hand side. 4. Right-click on the active network adapter and select Properties. 5. Select the Internet Protocol Version 4 (TCP/IPv4) option and click the Properties button. 6. Select the Use the following IP address option and enter the static IP address, subnet mask, and default gateway. 7. Click Okay to save the settings.
What protocol is responsible for assigning ip addresses to hosts on most networks?
The Dynamic Host Configuration Protocol (DHCP) is responsible for assigning IP addresses to hosts on most networks.
Which protocol assigns ip address to the client connected in the internet?
The Dynamic Host Configuration Protocol (DHCP) is responsible for assigning IP addresses to clients who are connected to the Internet.
What are the types of ip address assignment?
Static IP address: This type of IP address assignment is a permanent address assigned to a device by an administrator. Dynamic IP address: This type of IP address assignment is a temporary address assigned to a device by a DHCP server. Private IP address: This type of IP address is used for internal networks and is typically assigned for the use of devices within a local network. Public IP address: This type of IP address is used for public networks and is assigned by an internet service provider (ISP).
Which protocol provides a way to automate the ip configuration?
Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables a server to automatically assign an IP address to a computer from a defined range of numbers configured for a given network.
Which protocol assigns ip address to the client?
Dynamic Host Configuration Protocol (DHCP) is the protocol used to assign IP addresses to client devices.
Which two automatic addressing assignments are supported by dhcpv4 (choose two.)?
Dynamic Host Configuration Protocol (DHCP) Automatic Private IP Addressing (APIPA)
Which protocol should you use if you want to dynamically assign ip addresses to network clients?
The Dynamic Host Configuration Protocol (DHCP) should be used if you want to dynamically assign IP addresses to network clients.
What protocol is used to assign computers on a lan dynamic ip addresses?
Dynamic Host Configuration Protocol (DHCP)
How to manually assign ip address?
Open the Control Panel. Click on Network and Sharing Center. Choose Change adapter settings. Right click on the connection whose IP address you want to assign manually and select Properties. Select Internet Protocol Version 4 (TCP/IPv4). Click on the Properties button. Select the option "Use the following IP address". Enter the appropriate IP address and Subnet mask values. Enter the Default Gateway Address. Enter the Preferred and Alternate DNS server addresses. Click OK and then close out of all other open windows. Test your new settings.
How to assign ip address to devices?
Connect the device to the network. Use a DHCP server to assign an IP address to the device. Configure the device with a static IP address. Connect the device to a router and set the router to assign IP addresses to the device. Configure the device manually with a static IP address.
How to assign ip adress?
Open the Control Panel. Select "Network and Internet". Select "Network and Sharing Center". Select "Change adapter settings". Right-click on the network connection you want to change the IP address for and select "Properties". Select "Internet Protocol Version 4 (TCP/IPv4)". Select "Properties". Select "Use the following IP address". Enter the desired IP address. Enter the subnet mask. Enter the default gateway. Select "OK" to save the settings and close the window.
Why is dhcp preferred for use on large networks?
DHCP is preferred for use on large networks because it helps to automate the network configuration process. It eliminates the need for manual configuration of network settings. DHCP also helps reduce the risk of errors, by assigning the same IP address each time a computer connects to the network. It ensures that each client has its own unique IP address, allowing devices to communicate with each other. This increases the performance and reliability of the network.
Which two types of devices are typically assigned static ip addresses (choose two.)?
Servers Network Printers
How do you assign a server with an IP address?
To assign an IP address to a server, you will need to access the server's network settings in its operating system or hardware. From there, you can assign a static IP address or a dynamic one using DHCP.
What are the ways of assigning the Ip address?
There are several ways to assign an IP address to a device. Here are some common methods: Dynamic Host Configuration Protocol (DHCP): DHCP is commonly used in modern networks, where a central server automatically assigns IP addresses to devices on the network. The DHCP server manages a pool of available IP addresses and leases them to devices on request. Manual Configuration: This involves manually assigning a static IP address to a device. It is typically used for devices that require a consistent IP address, such as servers or network printers. The administrator manually enters the desired IP address, along with other network settings, directly into the device's network configuration. Zero-configuration Networking (Zeroconf): Zeroconf, also known as Automatic Private IP Addressing (APIPA), allows devices on a network to automatically assign IP addresses to themselves without a central server. It is commonly used in small home or office networks where there is no DHCP server available. Link-Local Addressing: Link-local addresses are IP addresses that are automatically assigned to devices on a local network segment without the need for a DHCP server. These addresses are typically used for network troubleshooting or communication within a small local network. Static IP Reservation: In some cases, network administrators may choose to use DHCP but reserve specific IP addresses for certain devices. This ensures that these devices always receive the same IP address each time they connect to the network. Dynamic DNS (DDNS): DDNS allows devices with dynamic IP addresses (addresses that change periodically) to be accessed by a hostname instead of the IP address. It involves using a service that updates the DNS records whenever the device's IP address changes. The method used to assign IP addresses depends on the network setup, device requirements, and network administrator's preferences.
Which method is used to assign ip address?
Dynamic Host Configuration Protocol (DHCP) is a network protocol used to assign IP addresses to devices on a network.
How to allocate ip address for network design?
Determine the IP address range to be allocated: Determine the total number of IP addresses needed and then calculate the appropriate IP address range based on the number of devices that need to be connected. Design the subnet mask: Design a subnet mask to divide the IP address range into subnets. Allocate the IP addresses: Allocate IP addresses to each device on the network based on their individual subnet masks. Configure the network devices: Configure the network devices with their assigned IP addresses and the appropriate subnet mask. Test the network: Test the network to ensure that all devices are assigned the correct IP addresses and the network is functioning properly.
How are IP adresses assigned to nodes in a network?
IP addresses are assigned to nodes in a network through DHCP (Dynamic Host Configuration Protocol). A DHCP server assigns a unique IP address to each node in a network from a pool of available IP addresses. The node then requests a lease from the DHCP server and stores the address for the duration of the lease.
When should a network administrator assign static IP addresses to network devices?
A network administrator should assign static IP addresses to network devices when the devices need to be accessed remotely and securely, or when the device needs to host services such as a web server, FTP server, or database. Static IP addresses are also useful for assigning devices to VLANs, managing traffic flow to and from the device, and configuring quality of service (QoS).
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Understanding IP address assignment and routing of hosted network
The hosted network ("Wifi tethering" or "wireless access point") can be enabled with:
So far, so good.
However, the following things are completely unclear to me (and nowhere to be found):
Is the hosted network adapter supposed to have an IP address (non 169.x) or not? If no , how is it supposed to be used? (of course, I can statically assign an IP to an interface but ideally this would happen automatically without generating collisions). If yes what is the exact mechanism (service etc.) that assigns the IP address?
How do wireless clients obtain IP addresses? There must be a DHCP service of some sort. What is the exact mechanism?
How exactly does the routing work between the wireless clients and the internet interface? As usual, I can manually execute a route command but there must be a mechanism that configures this properly. How?
The reason that I ask these questions:
- When I execute netsh wlan start hostednetwork , the "Microsoft Hosted Network Virtual Adapter" adapter (most of the time, not always!) has 169.254.74.242 assigned. In my opinion, this is wrong and should be 192.168.137.1. I want to debug what the heck is going wrong.
- When wireless clients connect they do not get an IP address assigned. I want to debug what the heck is going on. (e.g., is a DHCP service dead or so?)
- When I assign all IP addresses manually, I can ping the wireless clients and the wireless clients ping the host computer but they still cannot access the internet, although the internet connection is shared. I want to debug what the heck is going on where (e.g., which route entries, if any, should I expect to see, which firewall rules etc.)
I have tried restarting Windows, restarting SharedAccess service, stopping and starting hostednetwork. Even deleting the hosted network interface from the device manager.
- wireless-networking
- internet-sharing
2 Answers 2
I think Windows' built-in "Internet Connection Sharing" feature should handle all of this for you, so just use that, unless the real intent behind the question boils down to "How do I manually use the command line to set up all the things Internet Connection Sharing would have set up for me automatically?".
Some background info may help here, to clear up possible misconceptions.
[By the way, you didn't say what your existing Internet-connected interface is, so for convenience' sake I'm going to assume it is an Ethernet NIC connected to an existing Ethernet LAN that already has a DHCP server and an IP router on it.]
Wi-Fi is a layer 2 technology like Ethernet. It's independent of layer 3 technologies like IP. Wi-Fi, by design, doesn't really know anything about IP. The interface doesn't need an IP address, nor does it need to serve out IP addresses via DHCP or anything else, nor does it need to do IP routing.
For example, you could just enable layer 2 bridging between your Wi-Fi interface and your Ethernet interface, so that your wireless clients are just transparently connected to your existing Ethernet LAN. That way wireless clients could get IP address leases via DHCP from your existing DHCP server on your Ethernet LAN, and they'd all be on the same subnet with the rest of your LAN, so that service discovery protocols work.
If you want to enable IP forwarding (basic IP routing) or NAT (NAPT) gatewaying between Wi-Fi and Ethernet, you can. If you do that, you'll probably want to manually give the Wi-Fi interface an IP address on a different subnet than your existing Ethernet LAN. You'll probably want to use an RFC 1918 private subnet that's not already in use on your home network or on any other private network you ever VPN into. You may also want to enable DHCP service on the Wi-Fi interface to serve out other addresses on that new subnet to any wireless clients that join the network.
- I see, thanks! So everything is inside the SharedAccess service? I think I have to re-phrase my question a bit. The reason I am asking is that this piece of *** is not doing what I expect and nowhere details are found how to debug or what should even be the expected state. Maybe you know a little bit more details. I updated the question. – divB Jan 26, 2021 at 6:58
Thank you for the clear info about the "hostednetwork" feature in Windows. In your answer I see this phrase: "you could just enable layer 2 bridging between your Wi-Fi interface and your Ethernet interface..." That's exactly what I'ld like to do, but I don't know how to manage this in Windows (10). I have on my laptop Ethernet LAN access to the internet, but also to a NAS on my LAN. How can I bridge my LAN to WiFi, so my mobile phone is able to connect -through my laptop- to the LAN, using WiFi (direct)?
- As it’s currently written, your answer is unclear. Please edit to add additional details that will help others understand how this addresses the question asked. You can find more information on how to write good answers in the help center . – Community Bot Aug 5, 2022 at 21:19
- If you have a new question, please ask it by clicking the Ask Question button. Include a link to this question if it helps provide context. - From Review – DarkDiamond Aug 5, 2022 at 21:24
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged windows networking wireless-networking netsh internet-sharing ..
- The Overflow Blog
- How do mixture-of-experts layers affect transformer models?
- What a year building AI has taught Stack Overflow
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- What are the reasons for CORS failure errors to not be available to JS?
- How to rotate an electron mathematically?
- What’s going on with John 7:16, “My teaching is not my own, but his who sent me”?
- Resultant gravitational field due to two masses equalling zero
- Bad "breakup" with supervisor. What do I do?
- Confusing use of "if" in "Advanced Grammar in Use"
- How to break off outlet yoke tabs without bending
- Winning chance in coins game with fixing
- Sci-Fi novel where explorers from Earth visited 3 planets
- Mathematica 11.3.0, .nb file running for too long on Windows 10
- A man is high above Earth. He is attacked by aliens who can alter the laws of probability to make their enemies extraordinarily unlucky
- Change skin in "cloned" minecraft
- Could I file a complaint against discrimination in my favor?
- How can I set a Discord mute button for M3 MacBook Air running Sonoma?
- Baseball caught: Ownership? Can one leave?
- In "Silent Enemy", why didn't they just drop Echo Three?
- Delete trailing whitespace on save, but only for yaml files
- Do the "set ability score to 19" magic items function while using Wild Shape?
- ". . . those who feel able to answer this call for help, have a strong cup of coffee and be on your way."
- How long is a second on the moon?
- My workmate wants me to teach her art but I would prefer to maintain a work-only boundary
- In what sense is our death more desirable or in some way ‘better’ than our birth in Ecclesiastes 7:1?
- Are theorems in mathematics that have only been proved by contradiction applicable anywhere outside of mathematics?
- Why does a product of elements smaller than 1 converge to infinity?
Blog Category
- Career Tips
- Job Hunting
- Making Money
- All Featured
- All Hall of Fame
- Network Management
- Study Tools
- Troubleshooting
- All Uncategorized
CBT IT Certification Training
Unlimited IT Certification Courses via Streaming Video
Remember me
- Lost your password?
Enter your username or email:
- Back to login
Network Design – Designing Advanced IP Addressing
October 19, 2021 By Paul Browning Leave a Comment
This blog post covers the following network design topics:
- Summarizable and structured addressing designs
- IPv6 for Enterprise Campus design considerations
When designing IP addressing at a professional level, several issues must be taken into consideration. This blog post will cover generic IP addressing designs, including subnets and summarizable blocks design recommendations, address planning, and advanced addressing concepts, in addition to IPv6 design considerations, which will be covered in the last section of the post.
Importance of IP Addressing for Network Design
One of the major concerns in the network design phase is ensuring that the IP addressing scheme is properly designed. This aspect should be carefully planned and an implementation strategy should exist for the structural, hierarchical, and contiguous allocation of IP address blocks. A solid addressing scheme should be hierarchical, structural, and modular .
These features will add value to the continually improving concept of the Enterprise Campus design. This is also important in scaling any of the dynamic routing protocols. A solid IP addressing scheme helps routing protocols function in an optimal manner, using RIPv2, EIGRP, OSPF, or BGP. Facilitating summarization and the ability to summarize addresses provides several advantages for the network:
- Shorter Access Control Lists (ACLs)
- Reduces the overhead on routers (the performance difference is noticeable, especially on older routers)
- Faster convergence of routing protocols
- Addresses can be summarized to help isolate trouble domains
- Overall improvement of network stability
Address summarization is also important when there is a need to distribute addresses from one routing domain into another, as it impacts both the configuration effort and the overhead in the routing processing. In addition, having a solid IP addressing scheme not only makes ACLs easier to implement and more efficient for security, policy, and QoS purposes, but also it facilitates advanced routing policies and techniques (such as zone-based policy firewalls), where modular components and object groupings that are based on the defined IP addressing schemes can be created.
Solid IP address planning supports several features in an organization:
- Route summarization
- A more scalable network
- A more stable network
- Faster convergence
Subnet Network Design Recommendations
The importance of IP addressing is reflected in the new requirements that demand greater consideration of IP addressing, as the following examples illustrate:
- The transition to VoIP Telephony and the additional subnet ranges required to support voice services. Data and voice VLANs are usually segregated, and in some scenarios, twice as many subnets may be needed when implementing Telephony in the network .
- Layer 3 switching at the edge, replacing the Layer 2 switching with multi-layer switches. This involves more subnets needed at the Enterprise Edge, so t he number of smaller subnets will increase . There should be as little re-addressing as necessary, and making efficient use of the address space should be a priority. Sometimes, Layer 3 switching moved to the edge will involve a redesign of the IP addressing hierarchy.
- The company’s needs are changing and sometimes servers will be isolated by functions or roles (also called segmentation). For example, the accounting server, the development subnets, and the call-center subnets can be separated from an addressing standpoint. Identifying the subnets and ACLs based on corporate requirements can also add complexity to the environment .
- Many organizations use technologies like Network Admission Control (NAC), Cisco 802.1x (IBNS), or Microsoft NAP. These types of deployments will be dynamically assigning VLANs based on the user login or port-based authentication. In this situation, an ACL can actually manage connectivity to different servers and network resources based on the source subnet (which is based on the user role). Using NAC over a wired or wireless network will add more complexity to the IP addressing scheme.
- Many network topologies involve having separated VLANs (i.e., data, voice, and wireless). Using 802.1x may also involve a guest VLAN or a restricted VLAN , and authorization policies can be assigned based on VLAN membership from an Authentication, Authorization, and Accounting (AAA) server.
- Using role-based security techniques might require different sets of VPN clients, such as administrators, customers, vendors, guests, or extranets, so different groups can be implemented for different VPN client pools. This role-based access can be managed through a group password technique for each Cisco VPN client; every group can be assigned a VPN endpoint address from a different pool of addresses. If the pools are subnets of a summarizable block, then routing traffic back to the client can also be accomplished in a simplified fashion.
- Network designers should also consider that Network Address Translation (NAT) and Port Address Translation (PAT) can be applied on customer edge routers (often on the PIX firewall or on the ASA devices). NAT and PAT should not be used internally on the LAN or within the Enterprise Network to simplify the troubleshooting process. NAT can be used in a data center to support the Out-of-Band (OOB) management of the VLAN (i.e., on devices that cannot route or cannot find a default gateway for the OOB management of the VLAN).
You can read Ciscos network design guide here .
Summarization
After planning the network design for a IPv4 addressing scheme and determining the number and types of necessary addresses, a hierarchical design might be necessary. This design is useful when finding a scalable solution for a large organization and this involves address summarization. Summarization reduces the number of routes in the routing table and involves taking a series of network prefixes and representing them as a single summary address. It also involves reducing the CPU load and the memory utilization on network devices. In addition, this technique reduces processing overhead because routers advertise a single prefix instead of many smaller ones.
A summarizable address is one that contains blocks with sequential numbers in one of the octets . The sequential patterns must fit a binary bit pattern, with X numbers in a row, where X is a power of 2. The first number in this sequence must be a multiple of X. For example, 128 numbers in a row could be summarized with multiples starting at 0 or 128. If there are 64 numbers in a row (2 6 ), these will be represented in multiples of 64, such as 0, 64, 128, or 192, and 32 numbers in a row can be summarized with the multiples 0, 32, 64, and so on. This process can be easily accomplished using software subnet calculators.
Another planning aspect of summarizable blocks involves medium or large blocks of server farms or data centers. Servers can be grouped based on their functions and on their level of mission criticality, and they can all be in different subnets. In addition, with servers that are attached to different Access Layer switches, it is easier to assign subnets that will provide a perfect pattern for wildcarding in the ACLs. Simple wildcard rules and efficient ACLs are desired, as complex ACLs are very difficult to deal with, especially for new engineers who must take over an existing project.
When implementing the hierarchical addressing scheme for network design, it is important to have a good understanding of the math behind it and how route summarization works. Below is an example of combining a group of Class C addresses into an aggregate address. Summarization is a way to represent several networks in a single summarized route. In a real-world scenario, a subnet calculator can be used to automatically generate the most appropriate aggregate route from a group of addresses.
In this example, the Enterprise Campus backbone (Core Layer) submodule is connected to several other buildings. In a single building, there are several networks in use:
- A network for the server farm
- A network for the management area
- A few networks for the Access Layer submodule (that serve several departments)
The goal is to take all of these networks and aggregate them into one single address that can be stored at the edge distribution submodule or at the Core Layer of the network. The first thing to understand when implementing a hierarchical addressing structure is the use of continuous blocks of IP addresses . In this example, the addresses 192.100.168.0 through 192.100.175.0 are used:
In this scenario, network design summarization will be based on a location where all of the uppermost bits are identical. Looking at the first address above, the first 8 bits equal the decimal 192, the next 8 bits equal the decimal 100, and the last 8 bits are represented by 0. The only octet that changes is the third one; to be more specific, only the last 3 bits in that octet change when going through the address range.
The summarization process requires writing the third octet in binary format and then looking for the common bits on the left side. In the example above, all of the bits are identical up to the last three bits in the third octet. With 21 identical bits, all of the addresses will be summarized to 192.100.168.0/21.
After deciding on a hierarchical addressing design and understanding the math involved in this process, the next approach will be a modular and scalable design, which will involve deciding how to divide the organization (i.e., Enterprise Network modules, submodules, and remote locations) in terms of addressing. This includes deciding whether to apply a hierarchical address to each module/submodule or to the entire Enterprise Network.
Another aspect to consider is the way summarization may affect the routing protocols used. Summarization usually affects routing because it reduces the size of the routing tables, the processor, and memory utilization, and it offers a much faster convergence of the routed network. The following are the most important advantages of using route aggregation:
- Lower device processing overhead
- Improved network stability
- Ease of future growth
Figure 1 below offers another example of a large organization network design using a campus with multiple buildings:

Figure 1 – Network Design Addressing for a Large Organization with Multiple Buildings
The internal private addressing will use the popular 10.0.0.0/8 range. Within the organization’s domain, two separate building infrastructures (on the same campus or in remote buildings) will be aggregated using the 10.128.0.0/16 and 10.129.0.0/16 ranges.
Going deeper within each building, the addressing scheme can be broken down within different departments, using the 10.128.1.0, 10.128.2.0 or the 10.129.1.0, 10.128.2.0 networks with a 24-bit mask. Because of the scalable design, another tier could be included above the departmental addresses that would be within the 10.129.0.0/21 range, for example. Moving beyond that point leads to the Enterprise Edge module and its various submodules (e.g., e-commerce, Internet connectivity, etc.) that can have point-to-point connections to different ISPs. Variable Length Subnet Masking (VLSM) can be used to break down the addressing scheme further.
To summarize, from a network designer standpoint, it is very important to tie the addressing scheme to the modular Enterprise Network design . The advantages of using route summarization and aggregation are numerous but the most important ones are as follows:
- Isolates changes to the topology to a particular module
- Isolates routing updates to a particular module
- Fewer updates need to be sent up the hierarchy (preventing all of the updates from going through the entire network infrastructure)
- Lower overall recalculation of the entire network when links fail (e.g., a change in a routing table does not converge to the entire network); for example, route flapping in a particular department is constrained within the specific department and does not have a cascading effect on other modules (considering the example above)
- Narrow scope of route advertisement propagation
- Summarized module is easier to troubleshoot
Routing Protocols and Summarization for Network Design
Different routing protocols handle summarization in different manners. Routing Information Protocol (RIP) version 2 (RIPv2) has classful origins (it summarizes by default), although it can act in a classless manner because it sends subnet mask information in the routing updates.
Because of its classful origins, RIPv2 performs automatic summarization on classful boundaries, so any time RIPv2 is advertising a network across a different major network boundary, it summarizes to the classful mask without asking for permission. This can lead to big problems in the routing infrastructure of discontiguous networks. RIPv2’s automatic summarization behavior should be disabled in many situations to gain full control of the network routing operations.
In addition to the automatic summarization feature, RIPv2 allows for manual route summarization to be performed at the interface level . The recommendation is to disable automatic summarization and configure manual summarization where necessary. RIPv2 does not allow for summarization below the classful address. The next example involves the following prefixes:
210.22.10.0/24
210.22.9.0/24
210.22.8.0/24
RIPv2 will not allow the summarization of addresses above a /22 address because these are Class C addresses, and this would involve trying to summarize beneath this class. This is a limitation due to the classful origin of RIP.
EIGRP functions similar to RIPv2 regarding summarization, as EIGRP also has classful origins because it is an enhanced version of the Interior Gateway Routing Protocol (IGRP). EIGRP automatically summarizes on classful boundaries and, just like with RIPv2, this feature can be disabled and manual summarization can be configured on specific interfaces. The biggest issue with this behavior is that there might be discontiguous networks and this could cause problems with any of the automatic summarization mechanisms described.

Figure 2 – Discontiguous Network Issue
An example of a discontiguous network issue is illustrated in Figure 2 above. The 172.16.10.0/24 subnet is on the left side and the 172.16.12.0/24 subnet is on the right side. These networks are divided by a different major network in the middle (172.20.60.0/24), which causes a problem. Applying EIGRP in this scenario, automatic summarization will be enabled by default, with summarization toward the middle of the topology (172.16.0.0) from both sides, and this will cause great confusion to that device. As a result of this confusion, the device might send one packet to the left side and one packet to the right side, so there will be packets going in the wrong direction to get to a particular destination. To solve this issue, the automatic summarization feature should be disabled in discontiguous networks. Another possible fix to this problem is designing the addressing infrastructure better so that no discontiguous subnets are present.
OSPF does not have an automatic summarization feature but two different forms of summarization can be designed:
- Summarization between the internal areas
- Summarization from another separate domain
Two separate commands are used to handle these different summarization types. Summarizing from one area to another involves a Type 3 Link-State Advertisement (LSA). Summarizing from another domain involves two types of LSAs in the summarization process: a Type 4 LSA, which advertises the existence of the summarizing device (e.g. the OSPF Autonomous System Border Router – ASBR), and the actual summary of information, carried in a Type 5 LSA.
Border Gateway Protocol (BGP) uses a single type of summarization called aggregation , and this is accomplished during the routing process. BGP is used to summarize automatically, just like RIPv2 and EIGRP, but this behavior has been automatically disabled by the 12.2(8)T IOS code.
Variable Length Subnet Masking and Structured Addressing
A structured addressing plan involves the concept of Variable Length Subnet Masking (VLSM), a technology that all of the modern routing protocols can easily handle. VLSM provides efficiency, as it disseminates an addressing plan that does not waste address space (i.e., it assigns only the number of addresses needed for a certain subnetwork). VLSM also accommodates efficient summarization. The most important benefits of VLSM and summarization include the following:
- Less CPU utilization on network devices
- Less memory utilization on network devices
- Smaller convergence domains

Figure 3 – VLSM Example (Part 1)
VLSM functions by taking unused subnets from the address space used and further subnets them. Figure 3 above starts with the major network of 172.16.0.0/16 (not shown in the example), which is initially subnetted using a 24-bit mask, resulting in two large subnets on the two router interfaces (Fa0/0 and Fa0/1), 172.16.1.0/24 and 172.16.2.0/24, respectively. Two key formulas can be used when calculating the number of subnets and hosts using VLSM. An example of the subnet and host split in the address is shown below in Figure 4:

Figure 4 – VLSM Subnet and Host Split
The formula for calculating the number of subnets is 2 s , where “s” is the number of borrowed subnet bits. In Figure 3.3 above, the network expanded from a /16 network to a /24 network by borrowing 8 bits. This means 2 8 = 256 subnets can be created with this scheme.
The formula for calculating the number of hosts that can exist in a particular subnet is 2 h -2, where “h” is the number of host bits. Two hosts are subtracted from the 2 h formula because the all-zeros host portion of the address represents the major network itself and the all-ones host portion of the address represents the broadcast address for the specific segment, as illustrated below:
- Major networks (all zeros in the host portion): 172.16.1.0 and 172.16.2.0
- Broadcast networks (all ones in the host portion): 172.16.1.255 and 172.16.2.255
After summarizing the 172.16.0.0/16 address space into 172.16.1.0/24 and 172.16.2.0/24, further subnetting might be needed to accommodate smaller networks, which can be achieved by taking one of the next available subnets (after the subnetting process), for example, 172.16.3.0/24. This will create additional subnets such as those below:
172.16.3.32/27
172.16.3.64/27
The /27 subnets are suitable for smaller networks and can accommodate the number of machines in those areas. The number of hosts that can be accommodated is 2 5 -2=30.

Figure 5 – VLSM Example (Part 2)
A subnet might be needed for the point-to-point link that will connect two network areas, and this can be accomplished by further subnetting one of the available subnets in the /27 scheme, for example 172.16.3.96/27. This can be subnetted with a /30 to obtain 172.16.3.100/30, which offers just two host addresses: 172.16.3.101 and 172.16.3.102. This scheme perfectly suits the needs for the point-to-point connections (one address for each end of the link). By performing VLSM calculations, subnets that can accommodate just the right number of hosts in a particular area can be obtained.
Private versus Public Addressing
As a network design expert, after determining the number of necessary IP addresses, the next big decision is to find out whether private, public, or a combination of private and public addresses will be used. Private internetwork addresses are defined in RFC 1918 and are used internally within the network. From a real-world standpoint, because of the limitation of the number of public IP addresses, NAT techniques are usually used to translate the private internal numbers to external public addresses. Internally, one of the following three ranges of addresses can be used:
- 0.0.0/8 (10.0.0.0 to 10.255.255.255), usually used in large organizations
- 16.0.0/12 (172.16.0.0 to 172.31.255.255), usually used in medium organizations
- 168.0.0/16 (192.168.0.0 to 192.168.255.255), usually used in small organizations
Any address that falls within the three private address ranges cannot be routed on the Internet. Service Provider Edge devices usually have policies and ACLs configured to ensure that any packet containing a private address that arrives at an inbound interface will be dropped.
All of the other addresses are public addresses that are allocated to ISPs or other point of presence nodes on the Internet. ISPs can then assign Class A, B, or C addresses to customers to use on devices that are exposed to the Internet, such as:
- Web servers
- DNS servers
- FTP servers
- Other servers that run public-accessible services
When deciding to use private, public, or a combination of private and public addresses for your network design, one of the following four types of connections will be used:
- No Internet connectivity
- Only one public address (or a few) for users to access the Web
- Web access for users and public-accessible servers
- Every end-system has a public IP address
No Internet connectivity would imply that all of the connections between the locations are private links and the organization would not be connected to the Internet in any of its nodes. In this case, there is no need for any public IP addresses because the entire address scheme can be from the private address ranges.
Another situation would be the one in which there is Internet connectivity from all of the organization’s locations but there are no servers to run public-accessible services (e.g., Web, FTP, or others). In this case, a public IP address is needed that will allow users to access the Web. NAT can be used to translate traffic from the internal network to the outside network, so the internal networks contain only private IP addresses and the external link can use just one public address.
The third scenario is one of the most common, especially when considering the growth of enterprise networking. This involves having user Internet connectivity (just like in the previous scenario) but also having public-accessible servers. Public IP addresses must be used to connect to the Internet and access specific servers (e.g., Web, FTP, DNS, and others). The internal network should use private IP addresses and NAT to translate them into public addresses.
The most highly unlikely scenario would be the one in which every end-system is publicly accessible from the global Internet . This is a dangerous situation because the entire network is exposed to Internet access and this implies high security risks. To mitigate these risks, strong firewall protection policies must be implemented in every location. In addition to the security issues, this scenario is also not very effective because many IP addresses are wasted and this is very expensive. All of these factors make this scenario one not to be used in modern networks.
The two most common solutions from the scenarios presented above are as follows:
- One or a few public addresses for users to access the Web
- A few public addresses that provide Web access for users and public-accessible servers
Both scenarios imply using private internal addresses and NAT to reach outside networks.
For a deeper analysis of these aspects, it is useful to focus on how they map to the Cisco Enterprise Architecture model and where private and public addresses should be used, which is illustrated in Figure 6 below:

Figure 6 – Cisco Enterprise Architecture Model Addressing Scheme
First, in the figure above, assume that there is some kind of Internet presence in the organization that offers services either to internal users in the Access Layer submodule or to different public-accessible servers (e.g., Web, FTP, or others) in the Enterprise Edge module. Regardless of what modules receive Internet access, NAT is run in the edge distribution submodule to translate between the internal addressing structure used in the Enterprise Campus and the external public IP addressing structure. NAT mechanisms can also be used in the Enterprise Edge module.
Using the 10.0.0.0/8 range internally, both in the Enterprise Campus module and in the network management submodule, Enterprise Campus devices that use private IP addresses include all of its component submodules:
- Access Layer
- Distribution Layer
- Server farm
The edge distribution submodule will use a combination of private and public IP addresses. The Enterprise Edge module will use a combination of private and public addresses, depending on each submodule. The remote access submodule can use a combination of private and public addresses but it will need to support some kind of NAT techniques. The WAN submodule can use either private addresses (when connecting to other remote sites) or public addresses (when connected to outside locations for a backup solution).
Address Planning
An important issue in the IP addressing design is how the addresses will be assigned. One way would be to use static assigning and the other way would be to use dynamic protocols such as the Dynamic Host Configuration Protocol (DHCP). Deciding on the address allocation method requires answering the following questions:
- How many end-systems are there?
For a small number of hosts (less than 50), consider using statically/manually assigned addresses; however, if there are several hundred systems, use DHCP to speed up the address allocation process (i.e., avoid manual address allocation).
- What does the security policy demand?
Some organizations demand the use of static IP addressing for every host or for every node to create a more secure environment. For example, an outsider cannot plug in a station to the network, automatically get an IP address, and have access to internal resources. The organization’s security policy might demand static addressing, regardless of the network size.
- What is the likelihood of renumbering?
This includes the possibility of acquisitions and mergers in the near future. If the likelihood of renumbering is high, DHCP should be used.
- Are there any high availability demands?
If the organization has high availability demands, DHCP should be used in a redundant server architecture.
In addition, static addressing should always be used on certain modules in certain devices:
- Corporate servers
- Network management workstations
- Standalone servers in the Access Layer submodule
- Printers and other peripheral devices in the Access Layer submodule
- Public-accessible servers in the Enterprise Edge module
- Remote Access Layer submodule devices
- WAN submodule devices
Role-Based Addressing
From a Cisco standpoint, the best way to implement role-based addressing is to have it mapped to the corporate structure or to the roles of the servers or end-user stations. Using an example based on the 10.0.0.0/8 network, consider the first octet to be the major network number, the second octet to be the number assigned to the closet (i.e., the server room or wiring closets throughout the organization), the third octet to be the VLAN numbers, and the last octet to be the number of hosts. An address of 10.X.Y.Z would imply the following octet definitions:
- X = closet numbers
- Y = VLAN numbers
- Z = host numbers
This is an easy mechanism that can be used with Layer 3 closets. Role-based addressing avoids binary arithmetic , so if there are more than 256 closets, for example (more than can be identified in the second octet), some bits can be borrowed from the beginning of the third octet because there will not be 256 VLANs for every switch. Thereafter, advanced binary arithmetic or bit splitting can be used to adapt the addressing structure to specific needs. Bit splitting can be used with routing protocols, as well as route summarization, to help number the necessary summarizable blocks. In this case, addresses will be split into a network part, an area part, a subnet part, and a host part.
Network designers might not always have the luxury of using the summarizable blocks around simple octet boundaries and sometimes this is not even necessary, especially when some bit splitting techniques would better accommodate the organization and the role-based addressing scheme. This usually involves some binary math, such as the example below:
172.16.aaaassss.sshhhhhh
The first octet is 172 and the second octet is 16. The “a” bits in the third octet identify the area and the “s” bits identify the network subnet or VLAN. Six bits are reserved for the hosts in the forth octet. This offers 62 hosts per VLAN or subnet, or 2 16 -2 (two host addresses will be reserved for the network address – all zeros in the last bits and the broadcast address and all ones in the last bits).
This logical scheme will result in the following address ranges, based on the network areas:
- Area 0: 172.16.0.0 to 172.16.15.255
- Area 1: 172.16.16.0 to 172.16.31.255
- Area 2: 172.16.32.0 to 172.16.47.255
Subnet calculations should be made to ensure that the right type of bit splitting is used to represent the subnet and VLANs. Remember that a good summarization technique is to take the last subnet in every area and divide it so that the /30 subnet can be used for any WAN or point-to-point links. This will maximize the address space so for each WAN link there will be only two addresses with a /30 or .252 subnet mask.
Most organizations have their addressing schemes mapped out onto spreadsheets or included in different reports and stored as part of their documentation for the network topology. This should be done very systematically and hierarchically, regardless of the addressing scheme used. Always take into consideration the possible growth of the company through mergers or acquisitions.
Network Address Translation Applications
Although the goal with IPv6 is to avoid the need for NAT, NAT for IPv4 will still be used for a while. NAT is one of the mechanisms used in the transition from IPv4 to IPv6, so it will not disappear any time soon. In addition, it is a very functional tool for working with IPv4 addressing. NAT and PAT (or NAT Overload) are usually carried out on ASA devices, which have powerful tools to accomplish these tasks in many forms:
- Dynamic NAT
- Identity NAT
A recommended best practice is to try to avoid using NAT on internal networks, except for situations in which NAT is required as a stop-gap measure during mergers or migrations. NAT should not be performed between the Access Layer and the Distribution Layer or between the Distribution Layer and the Core Layer. Following this recommendation will prevent address translation between OSPF areas, for example.
Organizations with a merger in progress usually use the same internal network addressing schemes and these can be managed with NAT overlapping techniques (also referred to as bidirectional NAT), which translates between the two organizations when they have an overlapping internal IP addressing space that uses RFC 1918 addressing.
If there are internal servers or servers in the DMZ that are reached using translated addresses, it is a good practice to isolate these servers into their own address space and VLAN, possibly using private VLANs. NAT is often used to support content load balancing servers, which usually must be isolated by implementing address translation.
NAT can also be used in the data center submodule to support a management VLAN that is Out-of-Band from production traffic. It should also be implemented on devices that cannot route or cannot define a gateway for the management VLAN. This results in smaller management VLANs, not a single large management VLAN that covers the entire data center. In addition, large companies or Internet entities can exchange their summary routes, and then they can translate with NAT blocks into the network. This will offer faster convergence but the downside is an increased troubleshooting process because of the use of NAT or PAT.
PAT is harder to troubleshoot because one or a few IP addresses are used to represent hundreds or even thousands of internal hosts, all using TCP and UDP ports to create logical sockets. This increases the complexity of the troubleshooting process because it is difficult to know what IP address is assigned to a particular host. Each host uses a shared IP address and a port number. If the organization is connected to several different partners or vendors, each partner can be represented by a different NAT block, which can be translated in the organization.
Network Design for IPv6 Addressing
CCDP certification requires a solid understanding of the IP version 6 specifications, addressing, and some of the design issues. The IPv6 protocol is based on RFC 2460. From a network designer standpoint, the most important features offered by IPv6 include the following:
- A 128-bit address space
- Supports hierarchical addressing and auto-configuration
- Every host can have a globally unique IPv6 address; no need for NAT
- Hosts can have multiple addresses
- Efficient fixed header size for IPv6 packets
- Enhanced security and privacy headers
- Improved multicasting and QoS
- Dedicated IPv6 routing protocols: RIPng, OSPFv3, Integrated IS-ISv6, BGP4+
- Every major vendor supports IPv6
IPv6 is a mechanism that was created to overcome the limitations of the current IPv4 standard . One of the major shortcomings of IPv4 is that it uses a 32-bit address space. Because of the classful system and the growth of the Internet, the 32-bit address space has proven to be insufficient. The key factors that led to the evolution of IPv6 were large institutions, Enterprise Networks, and ISPs that demanded a larger pool of IP addresses for different applications and services.
Address Representation
IPv4 uses a 32-bit address space, so it offers around 4.2 billion possible addresses, including the multicast, experimental, and private ones. The IPv6 address space is 128 bits, so it offers around 3.4×10 38 possible addressable nodes. The address space is so large that there are about 5×10 28 addresses per person in the world. IPv6 also gives every user multiple global addresses that can be used for a wide variety of devices (e.g., PDAs, cell phones, and IP-enabled devices). IPv6 addresses will last a very long time. An IPv6 packet contains the following fields, as depicted in Figure 7 below:

Figure 7 – IPv6 Packet Fields
Knowing what is in the IPv4 header is important from a network designer standpoint because many of the fields in the header are used for features such as QoS or protocol type. The IPv6 header offers additional functionality, even though some fields from the IPv4 header have been eliminated, such as the Fragment Offset field and the Flags field.
The Version field, as in the IPv4 header, offers information about the IP protocol version. The Traffic Class field is used to tag the packet with the class of traffic it uses in its DiffServ mechanisms. IPv6 also adds a Flow Label field, which can be used for QoS mechanisms, by tagging a flow. This can be used for multilayer switching techniques and will offer faster packet switching on the network devices. The Payload Length field is the same as the Total Length field in IPv4.
The Next Header is an important IPv6 field. The value of this field determines the type of information that follows the basic IPv6 header. It can be a Transport Layer packet like TCP or UDP or it can designate an extension header. The Next Header field is the equivalent of the Protocol field in IPv4. The next field is Hop Limit, which designates the maximum number of hops an IP packet can traverse. Each hop/router decrements this field by one, so this is similar to the TTL field in IPv4. There is no Checksum field in the IPv6 header , so the router can decrement the Hop Limit field without recalculating the checksum. Finally, there is the 128-bit source address and the 128-bit destination address.
In addition to these fields there are a number of extension headers. The extension headers and the data portion of the packet will follow the eight fields covered thus far. The total length of an extension header’s chain can be variable because the number of extension headers is not fixed. There are different types of extension headers, such as the following:
- Routing header
- Fragmentation header
- Authentication header
- IPsec ESP header
- Hop-by-Hop Options header
The IPv4 address is comprised of a string of 32 bits represented in four octets using a dotted decimal format. IPv6, on the other hand, is comprised of 128 bits represented in eight groups of 16 bits using a hexadecimal format (i.e., 16 bits separated by colons), for example:
2001:43aa:0000:0000:11b4:0031:0000:c110.
Considering the complex format of IPv6 addresses, some rules were developed to shorten them:
- One or more successive 16-bit groups that consist of all zeros can be omitted and represented by two colons (::).
- If a 16-bit group begins with one or more zeros, the leading zeros can be omitted.
Considering the IPv6 example above, here are its shortened representations:
2001:43aa::11b4:0031:0000:c110
2001:43aa::11b4:0031:0:c110
2001:43aa::11b4:31:0:c110
In a mixed IPv4 and IPv6 environment, the IPv4 address can be embedded in the IPv6 address, specifically in the last 32 bits.
The prefix portion in IPv6 is the number of contiguous bits that represent the network host. For example, the address 2001:0000:0000:0AABC:0000:0000:0000:0000/60 can be represented as 2001:0:0:ABC::/60.
Several types of IPv6 addresses are required for various applications. When compared to IPv4 address types (i.e., unicast, multicast, and broadcast), IPv6 presents some differences: special multicast addresses are used instead of broadcast addressing, and a new address type was defined called anycast.
Anycast addresses are generally assigned to servers located in different geographical locations. By connecting to the anycast address, users will reach the closest server. Anycast addresses are also called one-to-nearest addresses. The IPv6 multicast address is a one-to-many address that identifies a set of hosts that will receive the packet. This is similar to an IPv4 Class D multicast address . IPv6 multicast addresses also supersede the broadcast function of IPv4 broadcast. IPv6 broadcast functionality is an all-nodes multicast behavior. The following are well-known multicast addresses that should be remembered:
- FF01::1 = all-nodes multicast address (broadcast)
- FF02::2 = all-routers multicast address (used for link-local address mechanisms)
Another important multicast address is the solicited node multicast address, which is created automatically and placed on the interface. This is used by the IPv6 Neighbor Discovery process to improve upon IPv4 ARP. A special IPv6 address is 0:0:0:0:0:0:0:1, which is the IPv6 loopback address, equivalent to the 127.0.0.1 IPv4 loopback address. This can also be represented as ::1/128.
The link-local addresses are significant only to individual nodes on a single link. Routers forward packets with a link-local source or destination address beyond the local link. Link-local addresses can be configured automatically or manually. Global unicast addresses are globally unique and routable and are defined in RFC 2374 and RFC 3587.

Figure 8 – IPv6 Global Unicast Address Format
Based on the IPv6 global unicast address format shown in Figure 8 above, the first 23 bits represent the registry, the first 32 bits represent the ISP prefix, the first 48 bits are the site prefix, and /64 represents the subnet prefix. The remaining bits are allocated to the interface ID.
The global unicast address and the anycast address share the same format. The unicast address space actually allocates the anycast address. To devices that are not configured for anycast, these addresses will appear as unicast addresses.
IPv6 global unicast addressing allows aggregation upward to the ISP. A single interface may be assigned multiple addresses of any type (i.e., unicast, anycast, and multicast). However, every IPv6-enabled interface must have a loopback address and a link-local address.
The IPv6 global unicast address is structured as presented above in Figure 3.8 to facilitate aggregation and reduce its number in the global routing tables, just like with IPv4. Global unicast addresses are defined by a global routing prefix, a subnet ID, and an interface ID. Typically, a global unicast address is made up of a 48-bit global routing prefix and a 16-bit subnet identifier.
IPv6 Mechanisms
As with IPv4, there are different mechanisms available for IPv6 and the most important of these includes the following:
- IPv6 Neighbor Discovery (ND)
- Name resolution
- Path Maximum Transmission Unit (MTU) Discovery
- IPv6 security
- IPv6 routing protocols
The Internet Control Message Protocol (ICMP) was modified to support IPv6 and is one of the most important mechanisms that support IPv6 functionality. ICMPv6 uses a Next Header number of 58. ICMP provides informational messages (e.g., Echo Request and Echo Reply) and error messages (e.g., Destination Unreachable, Packet Too Big, and Time Exceeded). IPv6 also uses ICMPv6 to determine important parameters, such as neighbor availability, Path MTU Discovery, destination addresses, or port reachability.
IPv6 uses a Neighbor Discovery protocol (RFC 2461), unlike IPv4, which uses the Address Resolution Protocol (ARP). IPv6 hosts use ND to implement “plug and play” functionality and to discover all other nodes on the same link. ND is also used in checking for duplicate addresses and finding the routers on a specific link. ND uses the ICMPv6 message structure in its operations and its type codes are 133 through 137:
- Router Solicitation
- Router Advertisement
- Neighbor Solicitation
- Neighbor Advertisement
Neighbor Discovery goes beyond the capabilities of ARP, as it performs many functions:
- Address Auto-Configuration (a host can find its full address without using DHCP)
- Duplicate Address Detection (DAD)
- Prefix Discovery (learns prefixes on local links)
- Link MTU Discovery
- Hop Count Discovery
- Next-Hop Determination
- Address Resolution
- Router Discovery (allows routers to find other local routers)
- Neighbor Reachability Detection
- Redirection
- Proxy Behavior
- Default Router Selection
Many of the features mentioned above have IPv4 equivalencies but some of them are unique to IPv6 and provide additional functionalities.
One of the important features made possible by the ND process is DAD, as defined in RFC 4862. This is accomplished through Neighbor Solicitation messages that are exchanged before the interface is allowed to use a global unicast address on the link, and this can determine whether the particular address is unique. The Target Address field in these specific packets is set to the IPv6 address for which duplication is being detected and the source address is set to unspecified (::).
The IPv6 stateless Auto-Configuration feature avoids using DHCP to maintain a mapping for the address assignment. This is a very low-overhead manner in which to disseminate addresses and it accommodates low-overhead re-addressing. In this process, the router sends a Router Advertisement message to advertise the prefix and its ability to act as a default gateway. The host receives this information and uses the EUI-64 format to generate the host portion of the address. After the host generates the address, it starts the DAD process to ensure that the address is unique on the network.
IPv4 performs Name Resolution by using A records in the DNS. RFC 3596 offers a new DNS record type to support the transition to IPv6 Name Resolution, which is AAAA (Quad A). The Quad A record will return an IPv6 address based on a given domain name.
IPv6 does not allow packet fragmentation through the network (except for the source of the packet), so the MTU of every link in an IPv6 implementation must be 1280 bytes or greater. The ICMPv6 Packet Too Big error message determines the path MTU because nodes along the path will send this message to the sending hosts if the packet is larger than the outgoing interface MTU.
DHCPv6 is an updated version of DHCP that offers dynamic address assignment for version 6 hosts. DHCPv6 is described in RD 3315 and provides the same functionality as DHCP but it offers more control, as it supports renumbering without numbers.
IPv6 also has some security mechanisms. Unlike IPv4, IPv6 natively supports IPsec (an open security framework) with two mechanisms: the Authentication Header (AH) and the Encapsulating Security Payload (ESP).
The support for IPsec in IPv6 is mandatory, unlike with IPv4. By making it mandatory in all the IPv6 nodes, secure communication can be created with any node in the network. An example of mandatory and leveraged IPsec in IPv6 is OSPF, which carries out its authentication using only IPsec. Another example of the IPsec IPv6 mechanism is the IPsec Site-to-Site Virtual Tunnel Interface, which allows easy creation of virtual tunnels between two IPv6 routers to very quickly form a site-to-site secured Virtual Private Network (VPN).
The following new routing protocols were developed for IPv6:
- RIPng (RIP new generation)
- Integrated Intermediate System-to-Intermediate System Protocol (IS-IS)
- EIGRP for IPv6
- BGP4 multiprotocol extensions for IPv6
Transitioning from IPv4 to IPv6
Because IPv6 almost always comes as an upgrade to the existing IPv4 infrastructure, IPv6 network design and implementation considerations must include different transition mechanisms between these two protocol suites. The IPv4 to IPv6 transition can be very challenging, and during the transition period it is very likely that both protocols will coexist on the network .
The designers of the IPv6 protocol suite have suggested that IPv4 will not go away anytime soon, and it will strongly coexist with IPv6 in combined addressing schemes. The key to all IPv4 to IPv6 transition mechanisms is dual-stack functionality, which allows a device to operate both in IPv4 mode and in IPv6 mode.
One of the most important IPv4 to IPv6 transition mechanisms involves tunneling between dual-stack devices and this can be implemented in different flavors:
- Generic Routing Encapsulation (GRE) – default tunnel mode
- IPv6IP (less overhead, no CLNS transport)
- 6to4 (embeds IPv4 address into IPv6 prefix to provide automatic tunnel endpoint determination); automatically generates tunnels based on the utilized addressing scheme
- Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) – automatic host-to-router and host-to-host tunneling

Figure 9 – IPv6 over IPv4 Tunneling
Analyzing Figure 9 above, the IPv4 island contains two dual-stack routers that run both the IPv4 and the IPv6 protocol stacks. These two routers will be able to support the transition mechanisms by tunneling IPv6 inside IPv4, and the two routers each connect to an IPv6 island. To carry IPv6 traffic between the two edge islands, a tunnel is created between the two routers that encapsulate IPv6 packets inside IPv4 packets. These packets are sent through the IPv4 cloud as regular IPv4 packets and they get de-encapsulated when they reach the other end. An IPv6 packet generated in the left-side network reaches a destination in the right-side network, so it is very easy to tunnel IPv6 inside IPv4 because of the dual-stack routers at the edge of the IPv4 infrastructure. Static tunneling methods are generally used when dealing with point-to-point links, while dynamic tunneling methods work best when using point-to-multipoint connections.
Network Address Translation Protocol Translation (NAT-PT) is another technology that can be utilized to carry out the transition to an IPv6 network. NAT-PT is often confused with NAT but it is a completely different technology. Simple NAT can also be used in IPv6 but this is very rare because IPv6 offers a very large address space and private addresses are not necessary. NAT-PT is another translation mechanism that will dynamically convert IPv4 addresses to IPv6 addresses, and vice-versa.
Another static tunneling technology is IPv6IP, which encapsulates IPv4 packets directly into IPv6. This is also called manual tunneling. Another type of static tunnel that can be created is a GRE tunnel that encapsulates the IPv6 packets within a GRE packet. GRE tunneling might be necessary when using special applications and services, like the IS-IS routing protocol for IPv6.
The dynamic tunnel types include the 6to4 tunnel, which is appropriate when a group of destinations needs to be connected dynamically utilizing IPv6. ISATAP is a unique type of host-to-router dynamic tunnel, unlike the previously mentioned tunneling techniques, which are router-to-router. ISATAP allows hosts to dynamically get to their IPv6 default gateway.
IPv6 Compared to IPv4
A network designer should have a very clear picture of the advantages IPv6 has over IPv4. The enhancements of IPv6 can be summarized as follows:
- IPv6 uses hexadecimal notation instead of dotted-decimal notation (IPv4).
- IPv6 has an expanded address space, from 32 bits to 128 bits .
- IPv6 addresses are globally unique due to the extended address space, eliminating the need for NAT.
- IPv6 has a fixed header length (40 bytes), allowing vendors to improve switching efficiency.
- IPv6 supports enhanced options (that offer new features) by placing extension headers between the IPv6 header and the Transport Layer header.
- IPv6 offers Address Auto-Configuration, providing for the dynamic assignment of IP addresses even without a DHCP server.
- IPv6 offers support for labeling traffic flows.
- IPv6 has security capabilities built-in, including authentication and privacy via IPsec
- IPv6 offers Path MTU Discovery before sending packets to a destination, eliminating the need for fragmentation.
- IPv6 supports site multi-homing.
- IPv6 uses the ND protocol instead of ARP.
- IPv6 uses AAAA DNS records instead of A records (IPv4).
- IPv6 uses site-local addressing instead of RFC 1918 (IPv4).
- IPv4 and IPv6 use different routing protocols.
- IPv6 provides for anycast addressing.
You can learn more about network design for security and wireless in our Cisco CCNP Encor course here .
Good IP addressing for network design uses summarizable blocks of addresses that enable route summarization and provide a number of benefits:
- Reduced router workload and routing traffic
- Increased network stability
- Significantly simplified troubleshooting
Creating and using summary routes depends on the use of summarizable blocks of addresses . Sequential numbers in an octet may denote a block of IP addresses as summarizable. For sequential numbers to be summarizable, the block must be X numbers in a row, where X is a power of 2, and the first number in the sequence must be a multiple of X. The created sequence will then end one before the next multiple of X in all cases.
Efficiently assigning IP addresses to the network is a critical network design decision, impacting the scalability of the network and the routing protocols that can be used. IPv4 addressing has the following characteristics:
- IPv4 addresses are 32 bits in length.
- IPv4 addresses are divided into various classes (e.g., Class A networks accommodate more than 16 million unique IP addresses, Class B networks support more than 65 thousand IP addresses, and Class C networks permit 254 usable IP addresses). Originally, organizations applied for an entire network in one of these classes. Today, however, subnetting allows an ISP to give a customer just a portion of a network’s address space, in an attempt to conserve the depleting pool of IP addresses. Conversely, ISPs can use supernetting (also known as Classless Inter-Domain Routing – CIDR) to aggregate the multiple network address spaces that they have. Aggregating multiple network address spaces into one address reduces the amount of route entries a router must maintain.
- Devices such as PCs can be assigned a static IP address, by hard coding the IP address in the device’s configuration. Alternatively, devices can dynamically obtain an address from a DHCP server , for example.
- Because names are easier to remember than IP addresses are, most publicly accessible Web resources are reachable by their name. However, routers must determine the IP address with which the name is associated to route traffic to that destination. Therefore, a DNS server can perform the translation between domain names and their corresponding IP addresses.
- Some IP addresses are routable through the public Internet, whereas other IP addresses are considered private and are intended for use within an organization. Because these private IP addresses might need to communicate outside the LAN, NAT can translate a private IP address into a public IP address. In fact, multiple private IP addresses can be represented by a single public IP address using NAT. This type of NAT is called Port Address Translation (PAT) because the various communication flows are identified by the port numbers they use to communicate with outside resources.
When beginning to design IP addressing for a network, the following aspects must be determined:
- The number of network locations that need IP addressing
- The number of devices requiring an IP address at each location
- Customer-specific IP addressing requirements (e.g., static IP addressing versus dynamic IP addressing)
- The number of IP addresses that need to be contained in each subnet (e.g., a 48-port switch in a wiring closet might belong to a subnet that supports 64 IP addresses)
A major challenge with IPv4 is the limited number of available addresses . A newer version of IP, specifically IPv6, addresses this concern. An IPv6 address is 128 bits long, compared to the 32-bit length of an IPv4 address.
To make such a large address more readable, an IPv6 address uses hexadecimal numbers and the 128-bit address is divided into eight fields. Each field is separated by a colon, as opposed to the four fields in an IPv4 address, which are each separated by a period. To further reduce the complexity of the IPv6 address, leading 0s in a field are optional and if one or more consecutive fields contain all 0s, those fields can be represented by a double colon (::). A double colon can be used only once in an address; otherwise, it would be impossible to know how many 0s are present between each pair of colons.
Consider some of the benefits offered by IPv6:
- IPv6 dramatically increases the number of available addresses.
- Hosts can have multiple IPv6 addresses, allowing those hosts to multi-home to multiple ISPs.
- Other benefits include enhancements relating to QoS, security, mobility, and multicast technologies.
Unlike IPv4, IPv6 does not use broadcasts. Instead, IPv6 uses the following methods for sending traffic from a source to one or more destinations:
- Unicast (one-to-one): Unicast support in IPv6 allows a single source to send traffic to a single destination, just as unicast functions in IPv4.
- Anycast (one-to-nearest): A group of interfaces belonging to nodes with similar characteristics (e.g., interfaces in replicated FTP servers) can be assigned an anycast address. When a host wants to reach one of those nodes, the host can send traffic to the anycast address and the node belonging to the anycast group that is closest to the sender will respond.
- Multicast (one-to-many): Like IPv4, IPv6 supports multicast addressing, where multiple nodes can join a multicast group. The sender sends traffic to the multicast IP address and all members of the multicast group receive the traffic.
The migration of an IPv4 network to an IPv6 network can take years because of the expenditures of upgrading equipment. Therefore, during the transition, IPv4-speaking devices and IPv6-speaking devices need to coexist on the same network. Consider the following solutions for maintaining both IPv4 and IPv6 devices in the network:
- Dual stack: Some systems (including Cisco routers) can simultaneously run both IPv4 and IPv6, allowing communication to both IPv4 and IPv6 devices.
- Tunneling: To send an IPv6 packet across a network that uses only IPv4, the IPv6 packet can be encapsulated and tunneled through the IPv4 network.
- Translation: A device, such as a Cisco router, could sit between an IPv4 network and an IPv6 network and translate between the two addressing formats.
IPv6 allows the use of static routing and supports specific dynamic routing protocols that are variations of the IPv4 routing protocols modified or redesigned to support IPv6:
Network Design Quiz
Related posts:.

Leave a Reply
Your email address will not be published. Required fields are marked *

Insert/edit link
Enter the destination URL
Or link to existing content
IP Address Assignment
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
How To Get A Network Switch To Assign IP

- Internet & Connectivity
- WiFi & Ethernet

Introduction
Understanding the basics of network switches and ip address assignment.
Network switches play a vital role in the functioning of computer networks, serving as the central point for connecting devices and facilitating the seamless transfer of data. When it comes to assigning IP addresses within a network, network switches are essential components that enable efficient communication between devices. In this article, we will delve into the fundamental concepts of network switches and explore the process of configuring and assigning IP addresses to devices connected to the switch.
The process of assigning IP addresses to devices connected to a network switch is crucial for enabling effective communication and data transfer. Understanding the intricacies of network switches and IP address assignment is essential for network administrators, IT professionals, and individuals seeking to optimize network performance.
Network switches are hardware devices that operate at the data link layer of the OSI model, facilitating the transfer of data between devices within a local area network (LAN). Unlike hubs, which simply broadcast data to all connected devices, switches intelligently forward data packets only to the intended recipient, thereby optimizing network efficiency and reducing unnecessary network traffic.
In the context of IP address assignment, a network switch serves as a central point through which devices can be interconnected and assigned unique IP addresses. This process is fundamental for enabling devices to communicate with each other and access network resources effectively.
Throughout this article, we will explore the various aspects of network switches and delve into the configuration and assignment of IP addresses, providing a comprehensive guide for network administrators and individuals seeking to gain a deeper understanding of these critical networking components. Let's embark on this journey to unravel the intricacies of network switches and the process of assigning IP addresses within a network.
Understanding Network Switches
Network switches are integral components of modern computer networks, playing a pivotal role in facilitating efficient data transfer and communication among connected devices. These devices operate at the data link layer of the OSI model, enabling the seamless exchange of data within a local area network (LAN).
Unlike traditional hubs that indiscriminately broadcast data to all connected devices, network switches utilize a method known as packet switching to intelligently forward data packets only to the intended recipients. This dynamic routing of data enhances network efficiency by reducing unnecessary traffic and optimizing data transfer speeds.
One of the key advantages of network switches is their ability to create dedicated communication channels between devices, thereby minimizing data collisions and congestion within the network. By establishing individual communication paths, switches enable devices to transmit and receive data simultaneously, enhancing network performance and overall throughput.
Modern network switches often incorporate advanced features such as VLAN (Virtual Local Area Network) support, Quality of Service (QoS) capabilities, and Power over Ethernet (PoE) functionality. VLAN support allows for the segmentation of a single physical network into multiple virtual networks, enhancing security and network management. QoS features enable the prioritization of specific types of network traffic, ensuring optimal performance for critical applications and services. Additionally, PoE functionality empowers switches to deliver power to connected devices such as IP phones, wireless access points, and surveillance cameras over the Ethernet cable , eliminating the need for separate power sources.
Understanding the various types of network switches, including unmanaged, managed, and layer 3 switches, is essential for network administrators and IT professionals. Unmanaged switches are plug-and-play devices that operate without the need for configuration, making them suitable for small-scale deployments. In contrast, managed switches offer greater flexibility and control, allowing for advanced configuration, monitoring, and optimization of network performance. Layer 3 switches, also known as multilayer switches, possess routing capabilities and can make forwarding decisions based on IP addresses, enhancing network scalability and efficiency.
By comprehending the functionalities and capabilities of network switches, individuals can harness the full potential of these critical networking components to build robust and high-performing computer networks.
Configuring the Network Switch
Configuring a network switch is a fundamental aspect of network administration, enabling administrators to optimize network performance, enhance security, and ensure seamless connectivity among devices. Whether deploying a new switch or reconfiguring an existing one, the configuration process involves several key steps to tailor the switch’s settings to the specific requirements of the network.
1. Accessing the Switch: Before initiating the configuration process, it is essential to access the switch’s management interface. This can typically be achieved through a web-based interface or a command-line interface (CLI) using protocols such as HTTP, HTTPS, Telnet, or SSH. Access credentials, including usernames and passwords, are required to log in and begin the configuration process.
2. Initial Setup: Upon accessing the switch, the initial setup involves configuring basic settings such as the switch’s hostname, management IP address, subnet mask, and default gateway. These parameters are essential for enabling remote management and facilitating communication with other devices within the network.
3. VLAN Configuration: For managed switches, configuring Virtual Local Area Networks (VLANs) is a critical step in network segmentation and resource isolation. VLAN configuration involves creating, assigning ports to, and defining the characteristics of individual VLANs to optimize network security and performance.
4. Port Configuration: Each port on the network switch can be customized to accommodate specific network requirements. Administrators can configure port settings such as speed, duplex mode, and flow control to ensure optimal connectivity and data transfer rates based on the connected devices’ capabilities.
5. Quality of Service (QoS) Settings: Implementing QoS settings enables administrators to prioritize network traffic based on predefined rules, ensuring that critical applications receive the necessary bandwidth and network resources. QoS configuration is particularly beneficial for optimizing the performance of voice, video, and data-intensive applications within the network.
6. Security Configuration: Enhancing network security is paramount in the configuration process. This involves implementing measures such as port security, MAC address filtering, and IEEE 802.1X authentication to mitigate unauthorized access and safeguard the network against potential threats.
7. Firmware Updates and Backup: Regular firmware updates and configuration backups are essential for maintaining the switch’s stability and security. Administrators should ensure that the switch’s firmware is up to date and create backups of the configuration settings to facilitate swift recovery in the event of a system failure or configuration loss.
By meticulously configuring network switches to align with the specific requirements and security policies of the network, administrators can establish a robust and reliable network infrastructure capable of meeting the organization’s communication and data transfer needs.
Assigning IP Addresses
Assigning IP addresses to devices within a network is a critical process that enables seamless communication and data transfer. Network switches play a pivotal role in facilitating the assignment of unique IP addresses to connected devices, ensuring efficient network operation and resource accessibility.
1. DHCP Configuration: Dynamic Host Configuration Protocol (DHCP) is a commonly used method for automatically assigning IP addresses to devices within a network. When a device connects to the network, the DHCP server, often integrated into the network switch or managed by a dedicated server, dynamically allocates an IP address from a predefined pool, along with essential network configuration parameters such as subnet mask, default gateway, and DNS servers. DHCP simplifies the IP address assignment process, eliminating the need for manual configuration and minimizing the risk of address conflicts.
2. Static IP Address Assignment: In certain scenarios, static IP address assignment may be preferred for specific devices within the network. Network administrators can manually assign static IP addresses to devices, ensuring that each device retains a consistent and predefined IP address. This approach is beneficial for devices that necessitate fixed addressing, such as servers, network printers, and network-attached storage (NAS) devices.
3. Subnetting and IP Address Range Management: When assigning IP addresses, understanding subnetting principles and effectively managing IP address ranges is crucial. Subnetting allows for the segmentation of a larger network into smaller, more manageable subnetworks, optimizing network performance and resource allocation. By carefully managing IP address ranges and subnet configurations, administrators can efficiently utilize available IP addresses and minimize potential address conflicts.
4. IPv6 Address Assignment: With the proliferation of Internet of Things (IoT) devices and the exhaustion of IPv4 addresses, the adoption of IPv6 has become increasingly prevalent. Network switches must support IPv6 address assignment to accommodate the growing number of devices requiring unique IP addresses. IPv6 address assignment involves configuring devices with globally routable IPv6 addresses, ensuring seamless connectivity and future-proofing the network infrastructure.
5. Quality of Service (QoS) for IP Address Assignment: Implementing QoS policies for IP address assignment processes can optimize network performance and resource allocation. By prioritizing DHCP traffic and IP address assignment requests, administrators can ensure that devices connecting to the network receive timely and efficient IP address assignments, minimizing potential delays and enhancing overall user experience.
By leveraging the capabilities of network switches and employing best practices for IP address assignment, administrators can establish a robust and scalable network infrastructure capable of accommodating diverse devices and applications while facilitating seamless communication and data exchange.
Verifying IP Assignments
After the process of IP address assignment, it is essential to verify the successful allocation and configuration of IP addresses to connected devices within the network. This verification process ensures that devices can communicate effectively, access network resources, and operate without connectivity issues.
1. Network Discovery Tools: Utilizing network discovery tools such as ping, traceroute, and network scanning utilities allows administrators to verify the connectivity and reachability of devices within the network. By pinging assigned IP addresses and conducting traceroute analyses, administrators can confirm the responsiveness and accessibility of devices, ensuring seamless communication across the network.
2. DHCP Lease Status: For dynamically assigned IP addresses through DHCP, monitoring the lease status of IP addresses is crucial. DHCP servers maintain lease records for assigned IP addresses, indicating the duration of the lease and the associated devices. Administrators can verify lease durations and renewal processes to ensure that devices retain valid IP addresses and that the DHCP server effectively manages address allocation.
3. Switch Port Status: Network switches provide insights into the status of individual switch ports and the devices connected to them. Administrators can verify the association of assigned IP addresses with specific switch ports, confirming that devices are connected to the appropriate ports and are successfully communicating within the network.
4. IP Address Conflict Resolution: Address conflicts can arise when duplicate IP addresses are assigned within the network, leading to connectivity issues and communication disruptions. Verifying the absence of IP address conflicts through network monitoring tools and conflict resolution procedures is essential for maintaining network stability and ensuring uninterrupted device communication.
5. Device Configuration Review: Reviewing the configuration settings of individual devices, including their assigned IP addresses, subnet masks, default gateways, and DNS server settings, provides a comprehensive overview of the network connectivity status. This review ensures that devices are configured with accurate network parameters, facilitating seamless communication and resource accessibility.
6. IPv6 Address Verification: In networks utilizing IPv6 addressing, administrators must verify the successful assignment and configuration of IPv6 addresses to devices. This involves confirming the presence of globally routable IPv6 addresses on devices and ensuring their compatibility with IPv6-enabled network services and applications.
By diligently verifying IP assignments through network discovery tools, DHCP lease monitoring, switch port status checks, and device configuration reviews, administrators can uphold the integrity and functionality of the network, ensuring that devices are equipped with valid and accessible IP addresses to facilitate efficient communication and data exchange.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Crowdfunding
- Cryptocurrency
- Digital Banking
- Digital Payments
- Investments
- Console Gaming
- Mobile Gaming
- VR/AR Gaming
- Gadget Usage
- Gaming Tips
- Online Safety
- Software Tutorials
- Tech Setup & Troubleshooting
- Buyer’s Guides
- Comparative Analysis
- Gadget Reviews
- Service Reviews
- Software Reviews
- Mobile Devices
- PCs & Laptops
- Smart Home Gadgets
- Content Creation Tools
- Digital Photography
- Video & Music Streaming
- Online Security
- Online Services
- Web Hosting
- WiFi & Ethernet
- Browsers & Extensions
- Communication Platforms
- Operating Systems
- Productivity Tools
- AI & Machine Learning
- Cybersecurity
- Emerging Tech
- IoT & Smart Devices
- Virtual & Augmented Reality
- Latest News
- AI Developments
- Fintech Updates
- Gaming News
- New Product Launches
- AI Writing How Its Changing the Way We Create Content
- How to Find the Best Midjourney Alternative in 2024 A Guide to AI Anime Generators
Related Post
Ai writing: how it’s changing the way we create content, unleashing young geniuses: how lingokids makes learning a blast, 10 best ai math solvers for instant homework solutions, 10 best ai homework helper tools to get instant homework help, 10 best ai humanizers to humanize ai text with ease, sla network: benefits, advantages, satisfaction of both parties to the contract, related posts.

How To Configure An Extreme Network Switch Without A Console Cable

Why Would A Layer 2 Switch Need An IP Address

How To Make Workstation Network Like A Server

How Do You Configure A Cisco Switch On VMware Workstation

Can’t Get Network Printer To Print When Plugged Into Network Switch

How To Get IP Address Of A Network Switch

What Is A Hyper-V Virtual Ethernet Adapter

Why Does My IP Address Change
Recent stories.

How to Find the Best Midjourney Alternative in 2024: A Guide to AI Anime Generators

How to Know When it’s the Right Time to Buy Bitcoin

How to Sell Counter-Strike 2 Skins Instantly? A Comprehensive Guide

10 Proven Ways For Online Gamers To Avoid Cyber Attacks And Scams

- Privacy Overview
- Strictly Necessary Cookies
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

What is a dedicated IP address for a VPN and do you need one?
I f you’ve ever used a VPN you’ve likely come across the term “dedicated IP address.” But what exactly is a dedicated IP address, and do you need one?
With a typical shared VPN connection, many users are all connected to a server with the same IP address. A dedicated IP address on the other hand, is a fixed IP that is used only by you. There are both advantages and disadvantages to using a dedicated IP over a shared IP.
Here I’ll lay out what exactly a dedicated IP address is, the pros and cons of using one, and help you figure out if it’s the right choice for you. And if you’re in the market for a VPN, then don’t forget to check out our best VPN services to see our recommendations.
What is a dedicated IP address for a VPN?
In short, a dedicated IP address is a static, or fixed, IP address that never changes and is used by only one person. This differs from a normal VPN IP address, which is shared by other users of the same VPN and is often changed each time you connect.
Just like a normal VPN connection, a dedicated IP address still hides your real home IP address, but you’ll always connect to the same IP on that specific VPN server.
Most of the leading VPN services such as NordVPN , Private Internet Access , Surfshark , and others offer the option to upgrade to a dedicated IP address for an additional monthly charge.
What are the advantages of a dedicated IP over a shared IP?
Bypass streaming service restrictions.
Sam Singleton
Some websites such as Netflix are sensitive to IP changes and block traffic if you’re using a shared VPN. A dedicated IP address can help fix this issue since your IP will never change. Also, a dedicated IP address is less likely to be recognized as part of a VPN since it will only be associated with your specific traffic.
Avoid annoying captchas
When a lot of people are sharing the same VPN server, websites may misidentify the traffic as coming from a bot, therefore issuing a captcha test for all requests from users. This can be extremely annoying — I can’t be the only one who is sick of choosing all the pictures with bicycles in them.
By using a dedicated IP address, this issue can be alleviated as only your traffic will be coming from the server, making it seem much less suspicious.
Easy and secure access to remote networks
If you need to access a remote network for work, using a shared IP address with a VPN can be an issue as your IP address will frequently change — remote networks don’t always like this. With a dedicated IP address you can get all of the security and privacy benefits of a VPN connection while accessing your workplace network since your IP address will always be the same.
Are there any disadvantages to using a dedicated IP?
You have to pay for a dedicated ip address.
Most VPN services that offer the option of a dedicated IP address won’t hand it out for free — you’ll need to pay up. The extra monthly cost of a dedicated IP address subscription can add up and unless you definitely need one for a specific reason, it might not be worth the expense.
Decreased anonymity
One of the reasons that VPNs do such a great job of protecting user anonymity is that oftentimes hundreds or thousands of users are accessing the same shared VPN server. This makes it very difficult to determine what traffic is coming from what user. A dedicated IP address takes away this level of anonymity as it ties the IP address traffic to you as the sole user — some find that this defeats the main purpose of using a VPN.
Geographical limitations
By opting for a dedicated IP address, you’ll need to choose a location and that location will never change. A regular shared VPN connection on the other hand allows for users to connect to servers all over the world and thereby spoof their real location to bypass geo-restricted content. With a dedicated IP address you’ll miss out on this advantage except in the country you choose for your dedicated IP.
Do you need a dedicated IP VPN?
So the question still remains, do you actually need a dedicated IP address with your VPN? That will ultimately depend on your intended use, but the short answer: probably not.
For the majority of people, a dedicated IP will mean adding an extra monthly expense without much upside. There are of course niche use cases where a dedicated IP will be hugely beneficial.
People who travel or work from home and want a consistent, secure way to remotely log in to their workplace network immediately come to mind. Or maybe you want to protect all of your smart-home devices on the same network; then the dedicated route might be the way to go.
There are tradeoffs to both shared and dedicated IP VPNs. While there is usually an additional expense for a dedicated IP address, it isn’t anything outrageous. If you’re not sure, trying it out for a month or two won’t break the bank. Who knows, it might be the solution you’ve been looking for, and if not, no harm done.
- Find a Lawyer
- Ask a Lawyer
- Research the Law
- Law Schools
- Laws & Regs
- Newsletters
- Justia Connect
- Pro Membership
- Basic Membership
- Justia Lawyer Directory
- Platinum Placements
- Gold Placements
- Justia Elevate
- Justia Amplify
- PPC Management
- Google Business Profile
- Social Media
- Justia Onward Blog
This docket was last retrieved on April 3, 2024. A more recent docket listing may be available from PACER .
Use the links below to access additional information about this case on the US Court's PACER system. A subscription to PACER is required.
Access this case on the Illinois Northern District Court's Electronic Court Filings (ECF) System
- Search for Party Aliases
- Associated Cases
- Case File Location
- Case Summary
- Docket Report
- History/Documents
- Related Transactions
- Check Status
Disclaimer: Justia Dockets & Filings provides public litigation records from the federal appellate and district courts. These filings and docket sheets should not be considered findings of fact or liability, nor do they necessarily reflect the view of Justia.
Why Is My Information Online?
Subscribe to Justia's Free Newsletters featuring summaries of federal and state court opinions .
- Bankruptcy Lawyers
- Business Lawyers
- Criminal Lawyers
- Employment Lawyers
- Estate Planning Lawyers
- Family Lawyers
- Personal Injury Lawyers
- Estate Planning
- Personal Injury
- Business Formation
- Business Operations
- Intellectual Property
- International Trade
- Real Estate
- Financial Aid
- Course Outlines
- Law Journals
- US Constitution
- Regulations
- Supreme Court
- Circuit Courts
- District Courts
- Dockets & Filings
- State Constitutions
- State Codes
- State Case Law
- Legal Blogs
- Business Forms
- Product Recalls
- Justia Connect Membership
- Justia Premium Placements
- Justia Elevate (SEO, Websites)
- Justia Amplify (PPC, GBP)
- Testimonials

IMAGES
VIDEO
COMMENTS
In simple terms, an IP address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It consists of four sets of numbers separated by periods (e.g., 192.168..1) and can be either IPv4 or IPv6 format. IP Address Allocation Methods.
A device's IP address actually consists of two separate parts: Network ID: The network ID is a part of the IP address starting from the left that identifies the specific network on which the device is located. On a typical home network, where a device has the IP address 192.168.1.34, the 192.168.1 part of the address will be the network ID.
An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface identification, and location addressing.. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number.
When you're connected to a network, your computer or smart device will obtain an IP address either from your ISP or your router. There are 2 ways how you can assign an IP address to your device: (1) dynamically via DHCP or (2) statically by manually assigning an IP address yourself. In either case, you must use the IP address that is provided to you by your ISP, or the IP range you allocated ...
An Internet Protocol (IP) address is the unique identifying number assigned to every device connected to the internet. An IP address definition is a numeric label assigned to devices that use the internet to communicate. Computers that communicate over the internet or via local networks share information to a specific location using IP addresses.
1. IP addresses are assigned by ICANN, so that won't happen. But there's also a more fundamental reason. IP addresses are used for routing. When a packet comes into a router, it compares the IP address against entries in its routing table, and sends the packet on through the appropriate outgoing line.
Each IP address must be unique on its own network. Networks can be isolated from one another, and they can be bridged and translated to provide access between distinct networks. ... For instance, for class A addresses, the addresses from 10.0.0.0 to 10.255.255.255 are reserved for private network assignment. For class B, this range is 172.16. ...
To uniquely identify each computer or networking device in the network, computer networks also use addresses. Addresses in computer networks are known as IP addresses. An IP address consists of two components: the network address and the host address. The network address is used to find the subnet in which the computer or the device is located ...
IPv4 addressing. IPv4 uses 32 bits, and its address format is usually a unique string of numbers and letters that looks something like this: 123.123.123.123. Each IP address comprises four sets of numbers separated by periods, each ranging from 0 to 255. IPv4 addresses are composed of two parts: the network ID and the host ID.
We are responsible for global coordination of the Internet Protocol addressing systems, as well as the Autonomous System Numbers used for routing Internet traffic. Currently there are two types of Internet Protocol (IP) addresses in active use: IP version 4 (IPv4) and IP version 6 (IPv6). IPv4 was initially deployed on 1 January 1983 and is ...
RTR1 DHCP assigned IP address. configure terminal, or "conf t" will bring to exec mode, which allows you to start making configuration changes. under interface, you assign the ip address as DHCP , "ip address dhcp" Enable the port or interface, "no shutdown" As per below configuration and output, GE0/2 is assigned an IP address, and method shown is DHCP instead of manual.
The screen shot below shows the static address assignment on my Windows 10 computer however all devices have a similar form for the IP address assignment. Notes: 1. My home network use the network address 192.168.1 (first three numbers) also common is 192.168. and 10.x.x.x. 2. The default gateway is the address of your home router. This is ...
Class C IP Addresses. For Class C IP addresses, the first three octets (24 bits / 3 bytes) represent the network ID and the last octet (8 bits / 1 bytes) is the host ID. Class C IP Addresses range from 192.0.0.0 to 223.255.255.255, with a default subnet mask of 255.255.255. (or /24 in CIDR).
Key Takeaways. To set a static IP address in Windows 10 or 11, open Settings -> Network & Internet and click Properties for your active network. Choose the "Edit" button next to IP assignment and change the type to Manual. Flip the IPv4 switch to "On", fill out your static IP details, and click Save. Sometimes, it's better to assign a PC its ...
To manually assign an IP address on a Mac, follow these steps: Click on the Apple menu in the top-left corner of the screen and select "System Preferences.". In the System Preferences window, click on "Network.". Select the network connection you want to configure from the list on the left (e.g., Wi-Fi, Ethernet).
Static Versus Dynamic IP Address Assignment Methods. Following are the two basic IP address assignment strategies: Static: An IP address is statically assigned to a system. The network administrator configures the IP address, default gateway, and name servers manually by entering them into a special file or files on the end system with either a ...
Some large / 8 blocks of IPv4 addresses, the former Class A network blocks, are assigned in whole to single organizations or related groups of organizations, either by the Internet Corporation for Assigned Names and Numbers (ICANN), through the Internet Assigned Numbers Authority (IANA), or a regional Internet registry.. Each / 8 block contains 256 3 = 2 24 = 16,777,216 addresses, which covers ...
The answer: dynamic IP address assignment. Dynamic IP address assignment. Most network devices temporarily lease an IP address configuration from a central server called a Dynamic Host Configuration Protocol server. Administrators configure the DHCP server with a pool of available IP addresses and any additional options.
The hosted network ("Wifi tethering" or "wireless access point") can be enabled with: netsh wlan set hostednetwork mode=allow ssid=[name] key=[password] netsh wlan start hostednetwork. So far, so good. However, the following things are completely unclear to me (and nowhere to be found): Is the hosted network adapter supposed to have an IP ...
Aggregating multiple network address spaces into one address reduces the amount of route entries a router must maintain. Devices such as PCs can be assigned a static IP address, by hard coding the IP address in the device's configuration. Alternatively, devices can dynamically obtain an address from a DHCP server, for example.
Internet Protocol (IP) addresses must be unique on a given network for proper routing and communication. Proper IP address planning can facilitate not only management of route aggregation, but also the application of security policies, implementation of application‐specific routing treatment, and governance of geographic‐specific guidelines. Regional Internet Registries (RIRs ...
DHCP simplifies the IP address assignment process, eliminating the need for manual configuration and minimizing the risk of address conflicts. 2. Static IP Address Assignment: In certain scenarios, static IP address assignment may be preferred for specific devices within the network. Network administrators can manually assign static IP ...
Here, you can manually assign an IP address within the 10.0.0.x range. For example, you might assign 10.0.0.2 to your virtual machine. Ensure that the subnet mask remains 255.255.255. .
A dedicated IP address on the other hand, is a fixed IP that is used only by you. ... If you need to access a remote network for work, using a shared IP address with a VPN can be an issue as your ...
301 Moved Permanently. openresty
2> IP Sec overlay on MS Peering connection. Microsoft Peering is the interconnection between Microsoft's global network (AS8075) and customer/ISP network for the purpose of exchanging internet traffic from/to Microsoft online services and Microsoft Azure Services or connections to/from public IP address range on Azure. Carriers or Service ...
If all parties consent to have the currently assigned United States Magistrate Judge conduct all proceedings in this case, including trial, the entry of final judgment, and all post-trial proceedings, all parties must sign their names on the attached #Consent To# form.