Terrorism Essay for Students and Teacher
500+ words essay on terrorism essay.
Terrorism is an act, which aims to create fear among ordinary people by illegal means. It is a threat to humanity. It includes person or group spreading violence, riots, burglaries, rapes, kidnappings, fighting, bombings, etc. Terrorism is an act of cowardice. Also, terrorism has nothing to do with religion. A terrorist is only a terrorist, not a Hindu or a Muslim.


Types of Terrorism
Terrorism is of two kinds, one is political terrorism which creates panic on a large scale and another one is criminal terrorism which deals in kidnapping to take ransom money. Political terrorism is much more crucial than criminal terrorism because it is done by well-trained persons. It thus becomes difficult for law enforcing agencies to arrest them in time.
Terrorism spread at the national level as well as at international level. Regional terrorism is the most violent among all. Because the terrorists think that dying as a terrorist is sacred and holy, and thus they are willing to do anything. All these terrorist groups are made with different purposes.
Causes of Terrorism
There are some main causes of terrorism development or production of large quantities of machine guns, atomic bombs, hydrogen bombs, nuclear weapons, missiles, etc. rapid population growth, Politics, Social, Economic problems, dissatisfaction of people with the country’s system, lack of education, corruption, racism, economic inequality, linguistic differences, all these are the major elements of terrorism, and terrorism flourishes after them. People use terrorism as a weapon to prove and justify their point of view. The riots among Hindus and Muslims are the most famous but there is a difference between caste and terrorism.
The Effects Of Terrorism
Terrorism spreads fear in people, people living in the country feel insecure because of terrorism. Due to terrorist attacks, millions of goods are destroyed, the lives of thousands of innocent people are lost, animals are also killed. Disbelief in humanity raises after seeing a terrorist activity, this gives birth to another terrorist. There exist different types of terrorism in different parts of the country and abroad.
Today, terrorism is not only the problem of India, but in our neighboring country also, and governments across the world are making a lot of effort to deal with it. Attack on world trade center on September 11, 2001, is considered the largest terrorist attack in the world. Osama bin Laden attacked the tallest building in the world’s most powerful country, causing millions of casualties and death of thousands of people.
Get the huge list of more than 500 Essay Topics and Ideas
Terrorist Attacks in India
India has suffered several terrorist attacks which created fear among the public and caused huge destruction. Here are some of the major terrorist attacks that hit India in the last few years: 1991 – Punjab Killings, 1993 – Bombay Bomb Blasts, RSS Bombing in Chennai, 2000 – Church Bombing, Red Fort Terrorist Attack,2001- Indian Parliament Attack, 2002 – Mumbai Bus Bombing, Attack on Akshardham Temple, 2003 – Mumbai Bombing, 2004 – Dhemaji School Bombing in Assam,2005 – Delhi Bombings, Indian Institute of Science Shooting, 2006 – Varanasi Bombings, Mumbai Train Bombings, Malegaon Bombings, 2007 – Samjhauta Express Bombings, Mecca Masjid Bombing, Hyderabad Bombing, Ajmer Dargah Bombing, 2008 – Jaipur Bombings, Bangalore Serial Blasts, Ahmedabad Bombings, Delhi Bombings, Mumbai Attacks, 2010 – Pune Bombing, Varanasi Bombing.
The recent ones include 2011 – Mumbai Bombing, Delhi Bombing, 2012 – Pune Bombing, 2013 – Hyderabad Blasts, Srinagar Attack, Bodh Gaya Bombings, Patna Bombings, 2014 – Chhattisgarh Attack, Jharkhand Blast, Chennai Train Bombing, Assam Violence, Church Street Bomb Blast, Bangalore, 2015 – Jammu Attack, Gurdaspur Attack, Pathankot Attack, 2016 – Uri Attack, Baramulla Attack, 2017 – Bhopal Ujjain Passenger Train Bombing, Amarnath Yatra Attack, 2018 Sukma Attack, 2019- Pulwama attack.
Agencies fighting Terrorism in India
Many police, intelligence and military organizations in India have formed special agencies to fight terrorism in the country. Major agencies which fight against terrorism in India are Anti-Terrorism Squad (ATS), Research and Analysis Wing (RAW), National Investigation Agency (NIA).
Terrorism has become a global threat which needs to be controlled from the initial level. Terrorism cannot be controlled by the law enforcing agencies alone. The people in the world will also have to unite in order to face this growing threat of terrorism.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


Essay on Terrorism
Students are often asked to write an essay on Terrorism in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Terrorism
Understanding terrorism.
Terrorism refers to the use of violence, often against civilians, to achieve political goals. It’s a form of fear-based manipulation, aiming to create panic and disrupt peace.
Impacts of Terrorism
Terrorism harms societies both physically and psychologically. It leads to loss of lives, property, and can cause trauma. It also hampers economic growth and societal harmony.
Countering Terrorism
Countering terrorism requires global cooperation. Nations must share intelligence, enforce strict laws, and promote education and understanding to prevent radicalization. Remember, peace and unity are our best defenses against terrorism.
Also check:
- Paragraph on Terrorism
- Speech on Terrorism
250 Words Essay on Terrorism
Terrorism, a term that sends chills down the spine, is an act of violence primarily intended to create fear, disrupt societal structures, and promote political or ideological agendas. It is a complex and multifaceted phenomenon, which has been escalating in frequency and intensity worldwide.
The Root Causes
The root causes of terrorism are multifarious. It can be triggered by political instability, socio-economic disparities, religious fanaticism, or ethnic tensions. Often, it is a combination of these factors, creating a fertile breeding ground for extremist ideologies.
The Impact of Terrorism
The impacts of terrorism are far-reaching and devastating. Beyond the immediate human toll, it disrupts economic stability, social harmony, and political structures. It instills fear, leading to changes in behavior and attitudes, and can even alter the course of history.
Counter-Terrorism Strategies
Counter-terrorism strategies are as diverse as the causes of terrorism. They range from military interventions to intelligence operations, from diplomatic negotiations to socio-economic reforms. However, the most effective strategies are those that address the root causes of terrorism, rather than merely responding to its symptoms.
Terrorism, a grave threat to global peace and security, requires a comprehensive and holistic approach to be effectively countered. By understanding its root causes and impacts, we can devise strategies to combat it, ensuring a safer world for future generations.
500 Words Essay on Terrorism
Introduction to terrorism.
Terrorism, a term that sends chills down the spine of many, is a complex phenomenon that has been the subject of extensive study and debate. It is characterized by acts of violence or threats aimed at creating fear, disrupting societal order, and advancing political, religious, or ideological goals.
The Evolution of Terrorism
Historically, terrorism was primarily a tool of the weak against the strong, a way to destabilize oppressive regimes or draw attention to a cause. However, the advent of the 21st century has seen its evolution into a more global menace, with the rise of transnational terrorist networks like Al-Qaeda and ISIS. The digital age has made it easier for these groups to recruit, radicalize, and coordinate attacks, making terrorism a borderless problem.
The Psychology of Terrorism
Understanding the psychology of terrorism is crucial in tackling it. Many terrorists are not psychopaths or inherently evil people, but individuals manipulated into believing that their violent actions are justified. Factors such as social exclusion, economic deprivation, political oppression, and religious indoctrination can contribute to this mindset. This underscores the importance of addressing root causes to prevent terrorism.
Terrorism’s impacts are multifaceted. The immediate effect is loss of life and property, but the ripple effects are far-reaching. It instills fear and insecurity, disrupts economic activity, and can lead to restrictive security measures that infringe on civil liberties. Moreover, it can exacerbate social divisions and fuel cycles of violence and retaliation.
Counter-terrorism strategies must be as multifaceted as the problem they aim to solve. Military and law enforcement responses are necessary to protect citizens and bring perpetrators to justice. However, these approaches should be paired with efforts to address the underlying social, economic, and political conditions that breed terrorism.
Preventive measures include promoting social inclusion, economic development, and political reforms. Moreover, countering extremist narratives online and offline is crucial to prevent radicalization. International cooperation is also essential given the transnational nature of modern terrorism.
Conclusion: The Future of Counter-Terrorism
The future of counter-terrorism lies in a balanced approach that combines hard and soft power. While military and law enforcement measures are necessary, they are not sufficient on their own. The fight against terrorism must also be a fight for hearts and minds, addressing the root causes of terrorism, and building inclusive societies where extremist narratives find no fertile ground.
In conclusion, terrorism is a complex problem that requires a nuanced understanding and multifaceted response. It is not just a security issue, but a social, economic, and political one. By addressing it in this holistic manner, we can hope to make progress in the ongoing struggle against this global menace.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Our Culture is Our Pride
- Essay on My Life My Health
- Essay on Banyan Tree
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Search Menu
- Browse content in Arts and Humanities
- Browse content in Archaeology
- Anglo-Saxon and Medieval Archaeology
- Archaeological Methodology and Techniques
- Archaeology by Region
- Archaeology of Religion
- Archaeology of Trade and Exchange
- Biblical Archaeology
- Contemporary and Public Archaeology
- Environmental Archaeology
- Historical Archaeology
- History and Theory of Archaeology
- Industrial Archaeology
- Landscape Archaeology
- Mortuary Archaeology
- Prehistoric Archaeology
- Underwater Archaeology
- Urban Archaeology
- Zooarchaeology
- Browse content in Architecture
- Architectural Structure and Design
- History of Architecture
- Residential and Domestic Buildings
- Theory of Architecture
- Browse content in Art
- Art Subjects and Themes
- History of Art
- Industrial and Commercial Art
- Theory of Art
- Biographical Studies
- Byzantine Studies
- Browse content in Classical Studies
- Classical History
- Classical Philosophy
- Classical Mythology
- Classical Literature
- Classical Reception
- Classical Art and Architecture
- Classical Oratory and Rhetoric
- Greek and Roman Papyrology
- Greek and Roman Epigraphy
- Greek and Roman Law
- Greek and Roman Archaeology
- Late Antiquity
- Religion in the Ancient World
- Digital Humanities
- Browse content in History
- Colonialism and Imperialism
- Diplomatic History
- Environmental History
- Genealogy, Heraldry, Names, and Honours
- Genocide and Ethnic Cleansing
- Historical Geography
- History by Period
- History of Emotions
- History of Agriculture
- History of Education
- History of Gender and Sexuality
- Industrial History
- Intellectual History
- International History
- Labour History
- Legal and Constitutional History
- Local and Family History
- Maritime History
- Military History
- National Liberation and Post-Colonialism
- Oral History
- Political History
- Public History
- Regional and National History
- Revolutions and Rebellions
- Slavery and Abolition of Slavery
- Social and Cultural History
- Theory, Methods, and Historiography
- Urban History
- World History
- Browse content in Language Teaching and Learning
- Language Learning (Specific Skills)
- Language Teaching Theory and Methods
- Browse content in Linguistics
- Applied Linguistics
- Cognitive Linguistics
- Computational Linguistics
- Forensic Linguistics
- Grammar, Syntax and Morphology
- Historical and Diachronic Linguistics
- History of English
- Language Evolution
- Language Reference
- Language Acquisition
- Language Variation
- Language Families
- Lexicography
- Linguistic Anthropology
- Linguistic Theories
- Linguistic Typology
- Phonetics and Phonology
- Psycholinguistics
- Sociolinguistics
- Translation and Interpretation
- Writing Systems
- Browse content in Literature
- Bibliography
- Children's Literature Studies
- Literary Studies (Romanticism)
- Literary Studies (American)
- Literary Studies (Asian)
- Literary Studies (European)
- Literary Studies (Eco-criticism)
- Literary Studies (Modernism)
- Literary Studies - World
- Literary Studies (1500 to 1800)
- Literary Studies (19th Century)
- Literary Studies (20th Century onwards)
- Literary Studies (African American Literature)
- Literary Studies (British and Irish)
- Literary Studies (Early and Medieval)
- Literary Studies (Fiction, Novelists, and Prose Writers)
- Literary Studies (Gender Studies)
- Literary Studies (Graphic Novels)
- Literary Studies (History of the Book)
- Literary Studies (Plays and Playwrights)
- Literary Studies (Poetry and Poets)
- Literary Studies (Postcolonial Literature)
- Literary Studies (Queer Studies)
- Literary Studies (Science Fiction)
- Literary Studies (Travel Literature)
- Literary Studies (War Literature)
- Literary Studies (Women's Writing)
- Literary Theory and Cultural Studies
- Mythology and Folklore
- Shakespeare Studies and Criticism
- Browse content in Media Studies
- Browse content in Music
- Applied Music
- Dance and Music
- Ethics in Music
- Ethnomusicology
- Gender and Sexuality in Music
- Medicine and Music
- Music Cultures
- Music and Media
- Music and Religion
- Music and Culture
- Music Education and Pedagogy
- Music Theory and Analysis
- Musical Scores, Lyrics, and Libretti
- Musical Structures, Styles, and Techniques
- Musicology and Music History
- Performance Practice and Studies
- Race and Ethnicity in Music
- Sound Studies
- Browse content in Performing Arts
- Browse content in Philosophy
- Aesthetics and Philosophy of Art
- Epistemology
- Feminist Philosophy
- History of Western Philosophy
- Metaphysics
- Moral Philosophy
- Non-Western Philosophy
- Philosophy of Language
- Philosophy of Mind
- Philosophy of Perception
- Philosophy of Science
- Philosophy of Action
- Philosophy of Law
- Philosophy of Religion
- Philosophy of Mathematics and Logic
- Practical Ethics
- Social and Political Philosophy
- Browse content in Religion
- Biblical Studies
- Christianity
- East Asian Religions
- History of Religion
- Judaism and Jewish Studies
- Qumran Studies
- Religion and Education
- Religion and Health
- Religion and Politics
- Religion and Science
- Religion and Law
- Religion and Art, Literature, and Music
- Religious Studies
- Browse content in Society and Culture
- Cookery, Food, and Drink
- Cultural Studies
- Customs and Traditions
- Ethical Issues and Debates
- Hobbies, Games, Arts and Crafts
- Lifestyle, Home, and Garden
- Natural world, Country Life, and Pets
- Popular Beliefs and Controversial Knowledge
- Sports and Outdoor Recreation
- Technology and Society
- Travel and Holiday
- Visual Culture
- Browse content in Law
- Arbitration
- Browse content in Company and Commercial Law
- Commercial Law
- Company Law
- Browse content in Comparative Law
- Systems of Law
- Competition Law
- Browse content in Constitutional and Administrative Law
- Government Powers
- Judicial Review
- Local Government Law
- Military and Defence Law
- Parliamentary and Legislative Practice
- Construction Law
- Contract Law
- Browse content in Criminal Law
- Criminal Procedure
- Criminal Evidence Law
- Sentencing and Punishment
- Employment and Labour Law
- Environment and Energy Law
- Browse content in Financial Law
- Banking Law
- Insolvency Law
- History of Law
- Human Rights and Immigration
- Intellectual Property Law
- Browse content in International Law
- Private International Law and Conflict of Laws
- Public International Law
- IT and Communications Law
- Jurisprudence and Philosophy of Law
- Law and Politics
- Law and Society
- Browse content in Legal System and Practice
- Courts and Procedure
- Legal Skills and Practice
- Primary Sources of Law
- Regulation of Legal Profession
- Medical and Healthcare Law
- Browse content in Policing
- Criminal Investigation and Detection
- Police and Security Services
- Police Procedure and Law
- Police Regional Planning
- Browse content in Property Law
- Personal Property Law
- Study and Revision
- Terrorism and National Security Law
- Browse content in Trusts Law
- Wills and Probate or Succession
- Browse content in Medicine and Health
- Browse content in Allied Health Professions
- Arts Therapies
- Clinical Science
- Dietetics and Nutrition
- Occupational Therapy
- Operating Department Practice
- Physiotherapy
- Radiography
- Speech and Language Therapy
- Browse content in Anaesthetics
- General Anaesthesia
- Neuroanaesthesia
- Clinical Neuroscience
- Browse content in Clinical Medicine
- Acute Medicine
- Cardiovascular Medicine
- Clinical Genetics
- Clinical Pharmacology and Therapeutics
- Dermatology
- Endocrinology and Diabetes
- Gastroenterology
- Genito-urinary Medicine
- Geriatric Medicine
- Infectious Diseases
- Medical Toxicology
- Medical Oncology
- Pain Medicine
- Palliative Medicine
- Rehabilitation Medicine
- Respiratory Medicine and Pulmonology
- Rheumatology
- Sleep Medicine
- Sports and Exercise Medicine
- Community Medical Services
- Critical Care
- Emergency Medicine
- Forensic Medicine
- Haematology
- History of Medicine
- Browse content in Medical Skills
- Clinical Skills
- Communication Skills
- Nursing Skills
- Surgical Skills
- Browse content in Medical Dentistry
- Oral and Maxillofacial Surgery
- Paediatric Dentistry
- Restorative Dentistry and Orthodontics
- Surgical Dentistry
- Medical Ethics
- Medical Statistics and Methodology
- Browse content in Neurology
- Clinical Neurophysiology
- Neuropathology
- Nursing Studies
- Browse content in Obstetrics and Gynaecology
- Gynaecology
- Occupational Medicine
- Ophthalmology
- Otolaryngology (ENT)
- Browse content in Paediatrics
- Neonatology
- Browse content in Pathology
- Chemical Pathology
- Clinical Cytogenetics and Molecular Genetics
- Histopathology
- Medical Microbiology and Virology
- Patient Education and Information
- Browse content in Pharmacology
- Psychopharmacology
- Browse content in Popular Health
- Caring for Others
- Complementary and Alternative Medicine
- Self-help and Personal Development
- Browse content in Preclinical Medicine
- Cell Biology
- Molecular Biology and Genetics
- Reproduction, Growth and Development
- Primary Care
- Professional Development in Medicine
- Browse content in Psychiatry
- Addiction Medicine
- Child and Adolescent Psychiatry
- Forensic Psychiatry
- Learning Disabilities
- Old Age Psychiatry
- Psychotherapy
- Browse content in Public Health and Epidemiology
- Epidemiology
- Public Health
- Browse content in Radiology
- Clinical Radiology
- Interventional Radiology
- Nuclear Medicine
- Radiation Oncology
- Reproductive Medicine
- Browse content in Surgery
- Cardiothoracic Surgery
- Gastro-intestinal and Colorectal Surgery
- General Surgery
- Neurosurgery
- Paediatric Surgery
- Peri-operative Care
- Plastic and Reconstructive Surgery
- Surgical Oncology
- Transplant Surgery
- Trauma and Orthopaedic Surgery
- Vascular Surgery
- Browse content in Science and Mathematics
- Browse content in Biological Sciences
- Aquatic Biology
- Biochemistry
- Bioinformatics and Computational Biology
- Developmental Biology
- Ecology and Conservation
- Evolutionary Biology
- Genetics and Genomics
- Microbiology
- Molecular and Cell Biology
- Natural History
- Plant Sciences and Forestry
- Research Methods in Life Sciences
- Structural Biology
- Systems Biology
- Zoology and Animal Sciences
- Browse content in Chemistry
- Analytical Chemistry
- Computational Chemistry
- Crystallography
- Environmental Chemistry
- Industrial Chemistry
- Inorganic Chemistry
- Materials Chemistry
- Medicinal Chemistry
- Mineralogy and Gems
- Organic Chemistry
- Physical Chemistry
- Polymer Chemistry
- Study and Communication Skills in Chemistry
- Theoretical Chemistry
- Browse content in Computer Science
- Artificial Intelligence
- Computer Architecture and Logic Design
- Game Studies
- Human-Computer Interaction
- Mathematical Theory of Computation
- Programming Languages
- Software Engineering
- Systems Analysis and Design
- Virtual Reality
- Browse content in Computing
- Business Applications
- Computer Security
- Computer Games
- Computer Networking and Communications
- Digital Lifestyle
- Graphical and Digital Media Applications
- Operating Systems
- Browse content in Earth Sciences and Geography
- Atmospheric Sciences
- Environmental Geography
- Geology and the Lithosphere
- Maps and Map-making
- Meteorology and Climatology
- Oceanography and Hydrology
- Palaeontology
- Physical Geography and Topography
- Regional Geography
- Soil Science
- Urban Geography
- Browse content in Engineering and Technology
- Agriculture and Farming
- Biological Engineering
- Civil Engineering, Surveying, and Building
- Electronics and Communications Engineering
- Energy Technology
- Engineering (General)
- Environmental Science, Engineering, and Technology
- History of Engineering and Technology
- Mechanical Engineering and Materials
- Technology of Industrial Chemistry
- Transport Technology and Trades
- Browse content in Environmental Science
- Applied Ecology (Environmental Science)
- Conservation of the Environment (Environmental Science)
- Environmental Sustainability
- Environmentalist Thought and Ideology (Environmental Science)
- Management of Land and Natural Resources (Environmental Science)
- Natural Disasters (Environmental Science)
- Nuclear Issues (Environmental Science)
- Pollution and Threats to the Environment (Environmental Science)
- Social Impact of Environmental Issues (Environmental Science)
- History of Science and Technology
- Browse content in Materials Science
- Ceramics and Glasses
- Composite Materials
- Metals, Alloying, and Corrosion
- Nanotechnology
- Browse content in Mathematics
- Applied Mathematics
- Biomathematics and Statistics
- History of Mathematics
- Mathematical Education
- Mathematical Finance
- Mathematical Analysis
- Numerical and Computational Mathematics
- Probability and Statistics
- Pure Mathematics
- Browse content in Neuroscience
- Cognition and Behavioural Neuroscience
- Development of the Nervous System
- Disorders of the Nervous System
- History of Neuroscience
- Invertebrate Neurobiology
- Molecular and Cellular Systems
- Neuroendocrinology and Autonomic Nervous System
- Neuroscientific Techniques
- Sensory and Motor Systems
- Browse content in Physics
- Astronomy and Astrophysics
- Atomic, Molecular, and Optical Physics
- Biological and Medical Physics
- Classical Mechanics
- Computational Physics
- Condensed Matter Physics
- Electromagnetism, Optics, and Acoustics
- History of Physics
- Mathematical and Statistical Physics
- Measurement Science
- Nuclear Physics
- Particles and Fields
- Plasma Physics
- Quantum Physics
- Relativity and Gravitation
- Semiconductor and Mesoscopic Physics
- Browse content in Psychology
- Affective Sciences
- Clinical Psychology
- Cognitive Psychology
- Cognitive Neuroscience
- Criminal and Forensic Psychology
- Developmental Psychology
- Educational Psychology
- Evolutionary Psychology
- Health Psychology
- History and Systems in Psychology
- Music Psychology
- Neuropsychology
- Organizational Psychology
- Psychological Assessment and Testing
- Psychology of Human-Technology Interaction
- Psychology Professional Development and Training
- Research Methods in Psychology
- Social Psychology
- Browse content in Social Sciences
- Browse content in Anthropology
- Anthropology of Religion
- Human Evolution
- Medical Anthropology
- Physical Anthropology
- Regional Anthropology
- Social and Cultural Anthropology
- Theory and Practice of Anthropology
- Browse content in Business and Management
- Business Ethics
- Business Strategy
- Business History
- Business and Technology
- Business and Government
- Business and the Environment
- Comparative Management
- Corporate Governance
- Corporate Social Responsibility
- Entrepreneurship
- Health Management
- Human Resource Management
- Industrial and Employment Relations
- Industry Studies
- Information and Communication Technologies
- International Business
- Knowledge Management
- Management and Management Techniques
- Operations Management
- Organizational Theory and Behaviour
- Pensions and Pension Management
- Public and Nonprofit Management
- Strategic Management
- Supply Chain Management
- Browse content in Criminology and Criminal Justice
- Criminal Justice
- Criminology
- Forms of Crime
- International and Comparative Criminology
- Youth Violence and Juvenile Justice
- Development Studies
- Browse content in Economics
- Agricultural, Environmental, and Natural Resource Economics
- Asian Economics
- Behavioural Finance
- Behavioural Economics and Neuroeconomics
- Econometrics and Mathematical Economics
- Economic History
- Economic Systems
- Economic Methodology
- Economic Development and Growth
- Financial Markets
- Financial Institutions and Services
- General Economics and Teaching
- Health, Education, and Welfare
- History of Economic Thought
- International Economics
- Labour and Demographic Economics
- Law and Economics
- Macroeconomics and Monetary Economics
- Microeconomics
- Public Economics
- Urban, Rural, and Regional Economics
- Welfare Economics
- Browse content in Education
- Adult Education and Continuous Learning
- Care and Counselling of Students
- Early Childhood and Elementary Education
- Educational Equipment and Technology
- Educational Strategies and Policy
- Higher and Further Education
- Organization and Management of Education
- Philosophy and Theory of Education
- Schools Studies
- Secondary Education
- Teaching of a Specific Subject
- Teaching of Specific Groups and Special Educational Needs
- Teaching Skills and Techniques
- Browse content in Environment
- Applied Ecology (Social Science)
- Climate Change
- Conservation of the Environment (Social Science)
- Environmentalist Thought and Ideology (Social Science)
- Natural Disasters (Environment)
- Social Impact of Environmental Issues (Social Science)
- Browse content in Human Geography
- Cultural Geography
- Economic Geography
- Political Geography
- Browse content in Interdisciplinary Studies
- Communication Studies
- Museums, Libraries, and Information Sciences
- Browse content in Politics
- African Politics
- Asian Politics
- Chinese Politics
- Comparative Politics
- Conflict Politics
- Elections and Electoral Studies
- Environmental Politics
- European Union
- Foreign Policy
- Gender and Politics
- Human Rights and Politics
- Indian Politics
- International Relations
- International Organization (Politics)
- International Political Economy
- Irish Politics
- Latin American Politics
- Middle Eastern Politics
- Political Behaviour
- Political Economy
- Political Institutions
- Political Methodology
- Political Communication
- Political Philosophy
- Political Sociology
- Political Theory
- Politics and Law
- Public Policy
- Public Administration
- Quantitative Political Methodology
- Regional Political Studies
- Russian Politics
- Security Studies
- State and Local Government
- UK Politics
- US Politics
- Browse content in Regional and Area Studies
- African Studies
- Asian Studies
- East Asian Studies
- Japanese Studies
- Latin American Studies
- Middle Eastern Studies
- Native American Studies
- Scottish Studies
- Browse content in Research and Information
- Research Methods
- Browse content in Social Work
- Addictions and Substance Misuse
- Adoption and Fostering
- Care of the Elderly
- Child and Adolescent Social Work
- Couple and Family Social Work
- Developmental and Physical Disabilities Social Work
- Direct Practice and Clinical Social Work
- Emergency Services
- Human Behaviour and the Social Environment
- International and Global Issues in Social Work
- Mental and Behavioural Health
- Social Justice and Human Rights
- Social Policy and Advocacy
- Social Work and Crime and Justice
- Social Work Macro Practice
- Social Work Practice Settings
- Social Work Research and Evidence-based Practice
- Welfare and Benefit Systems
- Browse content in Sociology
- Childhood Studies
- Community Development
- Comparative and Historical Sociology
- Economic Sociology
- Gender and Sexuality
- Gerontology and Ageing
- Health, Illness, and Medicine
- Marriage and the Family
- Migration Studies
- Occupations, Professions, and Work
- Organizations
- Population and Demography
- Race and Ethnicity
- Social Theory
- Social Movements and Social Change
- Social Research and Statistics
- Social Stratification, Inequality, and Mobility
- Sociology of Religion
- Sociology of Education
- Sport and Leisure
- Urban and Rural Studies
- Browse content in Warfare and Defence
- Defence Strategy, Planning, and Research
- Land Forces and Warfare
- Military Administration
- Military Life and Institutions
- Naval Forces and Warfare
- Other Warfare and Defence Issues
- Peace Studies and Conflict Resolution
- Weapons and Equipment

- < Previous chapter
(page 112) p. 112 Conclusion: war, terrorism, and future research
- Published: July 2013
- Cite Icon Cite
- Permissions Icon Permissions
The Conclusion sets out three important difficulties when researching the topic of modern war today: the unhelpful fragmentation of the research field on modern war, how to reconcile what people claim or remember about war and the actual historic reality, and the idea that modern war should be more honest about the fact that non-state terrorism represents a sub-species of war and about the terroristic activities used to incite war. The central issue here is the question of historical, analytical honesty. It should be acknowledged that states self-consciously use terrorizing violence for political ends during war. Redefining our understanding of war to include terrorism would help us to behave more cautiously in the future.
Signed in as
Institutional accounts.
- GoogleCrawler [DO NOT DELETE]
- Google Scholar Indexing
Personal account
- Sign in with email/username & password
- Get email alerts
- Save searches
- Purchase content
- Activate your purchase/trial code
Institutional access
- Sign in with a library card Sign in with username/password Recommend to your librarian
- Institutional account management
- Get help with access
Access to content on Oxford Academic is often provided through institutional subscriptions and purchases. If you are a member of an institution with an active account, you may be able to access content in one of the following ways:
IP based access
Typically, access is provided across an institutional network to a range of IP addresses. This authentication occurs automatically, and it is not possible to sign out of an IP authenticated account.
Sign in through your institution
Choose this option to get remote access when outside your institution. Shibboleth/Open Athens technology is used to provide single sign-on between your institution’s website and Oxford Academic.
- Click Sign in through your institution.
- Select your institution from the list provided, which will take you to your institution's website to sign in.
- When on the institution site, please use the credentials provided by your institution. Do not use an Oxford Academic personal account.
- Following successful sign in, you will be returned to Oxford Academic.
If your institution is not listed or you cannot sign in to your institution’s website, please contact your librarian or administrator.
Sign in with a library card
Enter your library card number to sign in. If you cannot sign in, please contact your librarian.
Society Members
Society member access to a journal is achieved in one of the following ways:
Sign in through society site
Many societies offer single sign-on between the society website and Oxford Academic. If you see ‘Sign in through society site’ in the sign in pane within a journal:
- Click Sign in through society site.
- When on the society site, please use the credentials provided by that society. Do not use an Oxford Academic personal account.
If you do not have a society account or have forgotten your username or password, please contact your society.
Sign in using a personal account
Some societies use Oxford Academic personal accounts to provide access to their members. See below.
A personal account can be used to get email alerts, save searches, purchase content, and activate subscriptions.
Some societies use Oxford Academic personal accounts to provide access to their members.
Viewing your signed in accounts
Click the account icon in the top right to:
- View your signed in personal account and access account management features.
- View the institutional accounts that are providing access.
Signed in but can't access content
Oxford Academic is home to a wide variety of products. The institutional subscription may not cover the content that you are trying to access. If you believe you should have access to that content, please contact your librarian.
For librarians and administrators, your personal account also provides access to institutional account management. Here you will find options to view and activate subscriptions, manage institutional settings and access options, access usage statistics, and more.
Our books are available by subscription or purchase to libraries and institutions.
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Rights and permissions
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore
Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Main Question Paper
- JEE Main Mock Test
- JEE Main Registration
- JEE Main Syllabus
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- GATE 2024 Result
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2023
- CAT 2023 College Predictor
- CMAT 2024 Registration
- XAT Cut Off 2024
- XAT Score vs Percentile 2024
- CAT Score Vs Percentile
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- DNB CET College Predictor
- DNB PDCET College Predictor
- NEET Application Form 2024
- NEET PG Application Form 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
- LSAT India 2024
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top Law Collages in Indore
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
- AIBE 18 Result 2023
- NID DAT Exam
- Pearl Academy Exam
Animation Courses
- Animation Courses in India
- Animation Courses in Bangalore
- Animation Courses in Mumbai
- Animation Courses in Pune
- Animation Courses in Chennai
- Animation Courses in Hyderabad
- Design Colleges in India
- Fashion Design Colleges in Bangalore
- Fashion Design Colleges in Mumbai
- Fashion Design Colleges in Pune
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Hyderabad
- Fashion Design Colleges in India
- Top Design Colleges in India
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- NIFT College Predictor
- UCEED College Predictor
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission
- UP B.Ed JEE 2024
- DDU Entrance Exam
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET PG Admit Card 2024
- IGNOU Date Sheet
- CUET Mock Test 2024
- CUET Application Form 2024
- CUET PG Syllabus 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Syllabus 2024
- IGNOU Exam Form 2024
- IGNOU Result
- CUET PG Courses 2024
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Access premium articles, webinars, resources to make the best decisions for career, course, exams, scholarships, study abroad and much more with
Plan, Prepare & Make the Best Career Choices
Essay on Terrorism
India has a lengthy history of terrorism. It is a cowardly act by terrorist organisations that want to sabotage the nation's tranquillity. It seeks to instil fear among the population. They seek to maintain a permanent climate of dread among the populace to prevent the nation from prospering. Here are a few sample essays on Terrorism .

100 Words Essay on Terrorism
Terrorism is the use of violence and intimidation in the pursuit of political and personal aims. It is a global phenomenon that has affected countries worldwide, causing harm to innocent civilians, damaging economies, and destabilizing governments. The causes of terrorism are complex and can include religious extremism, political oppression, and economic inequality.
Terrorist groups use a variety of tactics, including bombings, kidnappings, and hijackings, to achieve their goals. They often target symbols of government and military power, as well as civilians in crowded public spaces. The impact of terrorism on society is devastating, leading to loss of life, injury, and psychological trauma.
Combating terrorism requires a multifaceted approach, including intelligence gathering, law enforcement, and military action. Additionally, addressing underlying issues such as poverty and political marginalization is crucial in preventing the radicalization of individuals and the emergence of terrorist groups.
200 Words Essay on Terrorism
Terrorism is a complex and ever-evolving threat that affects countries and communities around the world. It involves the use of violence and intimidation to achieve political or ideological goals. The causes of terrorism can vary, but often include religious extremism, political oppression, and economic inequality.
To truly understand the impact of terrorism, it's important to consider not only the physical harm caused by terrorist attacks but also the emotional and psychological toll it takes on individuals and communities. The loss of life and injury caused to innocent civilians is devastating and can leave families and communities reeling for years to come. In addition, terrorism can cause physical damage to infrastructure and buildings, as well as economic disruption, leading to decreased tourism and investment.
To effectively combat terrorism, it's important to take a holistic approach that addresses not only the immediate threat of terrorist attacks but also the underlying issues that can lead to radicalization and the emergence of terrorist groups. This can include addressing poverty and economic inequality, promoting political and religious tolerance, and providing support and resources to individuals and communities at risk of radicalization.
It's also important to remember that the fight against terrorism is not just the responsibility of governments and law enforcement agencies, but also of individuals and communities. By promoting understanding and compassion, and by standing up against hate and extremism, we can all play a role in preventing terrorism and creating a more peaceful world.
500 Words Essay on Terrorism
According to a United Nations Security Council report from November 2004, terrorism is any act that is "intended to result in the death or serious bodily harm of civilians or non-combatants to intimidate the population or to compel the government or an international organisation to do or abstain from doing any act."
The Origins of Terrorism
The development or production of massive numbers of machine guns, atomic bombs, hydrogen bombs, nuclear weapons, missiles, and other weapons fuels terrorism. Rapid population growth, political, social, and economic problems, widespread discontent with the political system, a lack of education, racism, economic inequality, and linguistic discrepancies are all important contributors to the emergence of terrorism. Sometimes one uses terrorism to take a position and stick with it.
The Effects Of Terrorism
People become afraid of terrorism and feel unsafe in their nation. Terrorist attacks result in the destruction of millions of items, the death of thousands of innocent people, and the slaughter of animals. After seeing a terrorist incident, people become less inclined to believe in humanity, which breeds more terrorists.
Different forms of terrorism can be found both domestically and overseas. Today, governments worldwide are working hard to combat terrorism, which is an issue in India and our neighbouring nations. The 9/11 World Trade Centre attack is considered the worst terrorist act ever. Osama bin Laden attacked the tallest building in the world’s most powerful country, causing millions of casualties and the death of thousands of people.
The major incidents of the terrorist attack in India are—
12 March 1993 - A series of 13 bombs go off, killing 257
14 March 2003 - A bomb goes off in a train in Mulund, killing 10
29 October 2005 Delhi bombings
2005 Ram Janmabhoomi attack in Ayodhya
2006 Varanasi bombings
11 July 2006 - A series of seven bombs go off in trains, killing
26 November 2008 to 29 November 2008 - A series of coordinated attacks killed at least 170.
According to this data, India has experienced an upsurge in terrorist activity since 1980. India has fought four wars against terrorism , losing more than 6000 persons in total. Already, we have lost around 70000 citizens. Furthermore, we lost over 9000 security staff. In this country, about 6 lakh individuals have undergone.
Agencies In India Fighting Terrorism
There are numerous organisations working to rid our nation of terrorism. These organizations operate continuously, from the municipal to the national levels. To stop local terrorist activity, police forces have various divisions.
The police departments have a specialized intelligence and anti-terrorism division that is in charge of eliminating Naxalites and other terrorist organizations. The military is in charge of bombing terrorist targets outside of our country. These departments engage in counterinsurgency and other similar operations to dismantle various terrorist organisations.
There are numerous organisations that work to prevent terrorism. Anti-Terrorism Squad (ATS) , National Investigation Agency (NIA) , and Research and Analysis Wing are a few of the top organizations (RAW) . These are some of the main organizations working to rid India of terrorism.
Explore Career Options (By Industry)
- Construction
- Entertainment
- Manufacturing
- Information Technology
Bio Medical Engineer
The field of biomedical engineering opens up a universe of expert chances. An Individual in the biomedical engineering career path work in the field of engineering as well as medicine, in order to find out solutions to common problems of the two fields. The biomedical engineering job opportunities are to collaborate with doctors and researchers to develop medical systems, equipment, or devices that can solve clinical problems. Here we will be discussing jobs after biomedical engineering, how to get a job in biomedical engineering, biomedical engineering scope, and salary.
Data Administrator
Database professionals use software to store and organise data such as financial information, and customer shipping records. Individuals who opt for a career as data administrators ensure that data is available for users and secured from unauthorised sales. DB administrators may work in various types of industries. It may involve computer systems design, service firms, insurance companies, banks and hospitals.
Ethical Hacker
A career as ethical hacker involves various challenges and provides lucrative opportunities in the digital era where every giant business and startup owns its cyberspace on the world wide web. Individuals in the ethical hacker career path try to find the vulnerabilities in the cyber system to get its authority. If he or she succeeds in it then he or she gets its illegal authority. Individuals in the ethical hacker career path then steal information or delete the file that could affect the business, functioning, or services of the organization.
Data Analyst
The invention of the database has given fresh breath to the people involved in the data analytics career path. Analysis refers to splitting up a whole into its individual components for individual analysis. Data analysis is a method through which raw data are processed and transformed into information that would be beneficial for user strategic thinking.
Data are collected and examined to respond to questions, evaluate hypotheses or contradict theories. It is a tool for analyzing, transforming, modeling, and arranging data with useful knowledge, to assist in decision-making and methods, encompassing various strategies, and is used in different fields of business, research, and social science.
Geothermal Engineer
Individuals who opt for a career as geothermal engineers are the professionals involved in the processing of geothermal energy. The responsibilities of geothermal engineers may vary depending on the workplace location. Those who work in fields design facilities to process and distribute geothermal energy. They oversee the functioning of machinery used in the field.
Remote Sensing Technician
Individuals who opt for a career as a remote sensing technician possess unique personalities. Remote sensing analysts seem to be rational human beings, they are strong, independent, persistent, sincere, realistic and resourceful. Some of them are analytical as well, which means they are intelligent, introspective and inquisitive.
Remote sensing scientists use remote sensing technology to support scientists in fields such as community planning, flight planning or the management of natural resources. Analysing data collected from aircraft, satellites or ground-based platforms using statistical analysis software, image analysis software or Geographic Information Systems (GIS) is a significant part of their work. Do you want to learn how to become remote sensing technician? There's no need to be concerned; we've devised a simple remote sensing technician career path for you. Scroll through the pages and read.
Geotechnical engineer
The role of geotechnical engineer starts with reviewing the projects needed to define the required material properties. The work responsibilities are followed by a site investigation of rock, soil, fault distribution and bedrock properties on and below an area of interest. The investigation is aimed to improve the ground engineering design and determine their engineering properties that include how they will interact with, on or in a proposed construction.
The role of geotechnical engineer in mining includes designing and determining the type of foundations, earthworks, and or pavement subgrades required for the intended man-made structures to be made. Geotechnical engineering jobs are involved in earthen and concrete dam construction projects, working under a range of normal and extreme loading conditions.
Cartographer
How fascinating it is to represent the whole world on just a piece of paper or a sphere. With the help of maps, we are able to represent the real world on a much smaller scale. Individuals who opt for a career as a cartographer are those who make maps. But, cartography is not just limited to maps, it is about a mixture of art , science , and technology. As a cartographer, not only you will create maps but use various geodetic surveys and remote sensing systems to measure, analyse, and create different maps for political, cultural or educational purposes.
Budget Analyst
Budget analysis, in a nutshell, entails thoroughly analyzing the details of a financial budget. The budget analysis aims to better understand and manage revenue. Budget analysts assist in the achievement of financial targets, the preservation of profitability, and the pursuit of long-term growth for a business. Budget analysts generally have a bachelor's degree in accounting, finance, economics, or a closely related field. Knowledge of Financial Management is of prime importance in this career.
Product Manager
A Product Manager is a professional responsible for product planning and marketing. He or she manages the product throughout the Product Life Cycle, gathering and prioritising the product. A product manager job description includes defining the product vision and working closely with team members of other departments to deliver winning products.
Underwriter
An underwriter is a person who assesses and evaluates the risk of insurance in his or her field like mortgage, loan, health policy, investment, and so on and so forth. The underwriter career path does involve risks as analysing the risks means finding out if there is a way for the insurance underwriter jobs to recover the money from its clients. If the risk turns out to be too much for the company then in the future it is an underwriter who will be held accountable for it. Therefore, one must carry out his or her job with a lot of attention and diligence.
Finance Executive
Operations manager.
Individuals in the operations manager jobs are responsible for ensuring the efficiency of each department to acquire its optimal goal. They plan the use of resources and distribution of materials. The operations manager's job description includes managing budgets, negotiating contracts, and performing administrative tasks.
Bank Probationary Officer (PO)
Investment director.
An investment director is a person who helps corporations and individuals manage their finances. They can help them develop a strategy to achieve their goals, including paying off debts and investing in the future. In addition, he or she can help individuals make informed decisions.
Welding Engineer
Welding Engineer Job Description: A Welding Engineer work involves managing welding projects and supervising welding teams. He or she is responsible for reviewing welding procedures, processes and documentation. A career as Welding Engineer involves conducting failure analyses and causes on welding issues.
Transportation Planner
A career as Transportation Planner requires technical application of science and technology in engineering, particularly the concepts, equipment and technologies involved in the production of products and services. In fields like land use, infrastructure review, ecological standards and street design, he or she considers issues of health, environment and performance. A Transportation Planner assigns resources for implementing and designing programmes. He or she is responsible for assessing needs, preparing plans and forecasts and compliance with regulations.
An expert in plumbing is aware of building regulations and safety standards and works to make sure these standards are upheld. Testing pipes for leakage using air pressure and other gauges, and also the ability to construct new pipe systems by cutting, fitting, measuring and threading pipes are some of the other more involved aspects of plumbing. Individuals in the plumber career path are self-employed or work for a small business employing less than ten people, though some might find working for larger entities or the government more desirable.
Construction Manager
Individuals who opt for a career as construction managers have a senior-level management role offered in construction firms. Responsibilities in the construction management career path are assigning tasks to workers, inspecting their work, and coordinating with other professionals including architects, subcontractors, and building services engineers.
Urban Planner
Urban Planning careers revolve around the idea of developing a plan to use the land optimally, without affecting the environment. Urban planning jobs are offered to those candidates who are skilled in making the right use of land to distribute the growing population, to create various communities.
Urban planning careers come with the opportunity to make changes to the existing cities and towns. They identify various community needs and make short and long-term plans accordingly.
Highway Engineer
Highway Engineer Job Description: A Highway Engineer is a civil engineer who specialises in planning and building thousands of miles of roads that support connectivity and allow transportation across the country. He or she ensures that traffic management schemes are effectively planned concerning economic sustainability and successful implementation.
Environmental Engineer
Individuals who opt for a career as an environmental engineer are construction professionals who utilise the skills and knowledge of biology, soil science, chemistry and the concept of engineering to design and develop projects that serve as solutions to various environmental problems.
Naval Architect
A Naval Architect is a professional who designs, produces and repairs safe and sea-worthy surfaces or underwater structures. A Naval Architect stays involved in creating and designing ships, ferries, submarines and yachts with implementation of various principles such as gravity, ideal hull form, buoyancy and stability.
Orthotist and Prosthetist
Orthotists and Prosthetists are professionals who provide aid to patients with disabilities. They fix them to artificial limbs (prosthetics) and help them to regain stability. There are times when people lose their limbs in an accident. In some other occasions, they are born without a limb or orthopaedic impairment. Orthotists and prosthetists play a crucial role in their lives with fixing them to assistive devices and provide mobility.
Veterinary Doctor
Pathologist.
A career in pathology in India is filled with several responsibilities as it is a medical branch and affects human lives. The demand for pathologists has been increasing over the past few years as people are getting more aware of different diseases. Not only that, but an increase in population and lifestyle changes have also contributed to the increase in a pathologist’s demand. The pathology careers provide an extremely huge number of opportunities and if you want to be a part of the medical field you can consider being a pathologist. If you want to know more about a career in pathology in India then continue reading this article.
Speech Therapist
Gynaecologist.
Gynaecology can be defined as the study of the female body. The job outlook for gynaecology is excellent since there is evergreen demand for one because of their responsibility of dealing with not only women’s health but also fertility and pregnancy issues. Although most women prefer to have a women obstetrician gynaecologist as their doctor, men also explore a career as a gynaecologist and there are ample amounts of male doctors in the field who are gynaecologists and aid women during delivery and childbirth.
An oncologist is a specialised doctor responsible for providing medical care to patients diagnosed with cancer. He or she uses several therapies to control the cancer and its effect on the human body such as chemotherapy, immunotherapy, radiation therapy and biopsy. An oncologist designs a treatment plan based on a pathology report after diagnosing the type of cancer and where it is spreading inside the body.
Audiologist
The audiologist career involves audiology professionals who are responsible to treat hearing loss and proactively preventing the relevant damage. Individuals who opt for a career as an audiologist use various testing strategies with the aim to determine if someone has a normal sensitivity to sounds or not. After the identification of hearing loss, a hearing doctor is required to determine which sections of the hearing are affected, to what extent they are affected, and where the wound causing the hearing loss is found. As soon as the hearing loss is identified, the patients are provided with recommendations for interventions and rehabilitation such as hearing aids, cochlear implants, and appropriate medical referrals. While audiology is a branch of science that studies and researches hearing, balance, and related disorders.
Hospital Administrator
The hospital Administrator is in charge of organising and supervising the daily operations of medical services and facilities. This organising includes managing of organisation’s staff and its members in service, budgets, service reports, departmental reporting and taking reminders of patient care and services.
For an individual who opts for a career as an actor, the primary responsibility is to completely speak to the character he or she is playing and to persuade the crowd that the character is genuine by connecting with them and bringing them into the story. This applies to significant roles and littler parts, as all roles join to make an effective creation. Here in this article, we will discuss how to become an actor in India, actor exams, actor salary in India, and actor jobs.
Individuals who opt for a career as acrobats create and direct original routines for themselves, in addition to developing interpretations of existing routines. The work of circus acrobats can be seen in a variety of performance settings, including circus, reality shows, sports events like the Olympics, movies and commercials. Individuals who opt for a career as acrobats must be prepared to face rejections and intermittent periods of work. The creativity of acrobats may extend to other aspects of the performance. For example, acrobats in the circus may work with gym trainers, celebrities or collaborate with other professionals to enhance such performance elements as costume and or maybe at the teaching end of the career.

Video Game Designer
Career as a video game designer is filled with excitement as well as responsibilities. A video game designer is someone who is involved in the process of creating a game from day one. He or she is responsible for fulfilling duties like designing the character of the game, the several levels involved, plot, art and similar other elements. Individuals who opt for a career as a video game designer may also write the codes for the game using different programming languages.
Depending on the video game designer job description and experience they may also have to lead a team and do the early testing of the game in order to suggest changes and find loopholes.
Radio Jockey
Radio Jockey is an exciting, promising career and a great challenge for music lovers. If you are really interested in a career as radio jockey, then it is very important for an RJ to have an automatic, fun, and friendly personality. If you want to get a job done in this field, a strong command of the language and a good voice are always good things. Apart from this, in order to be a good radio jockey, you will also listen to good radio jockeys so that you can understand their style and later make your own by practicing.
A career as radio jockey has a lot to offer to deserving candidates. If you want to know more about a career as radio jockey, and how to become a radio jockey then continue reading the article.
Choreographer
The word “choreography" actually comes from Greek words that mean “dance writing." Individuals who opt for a career as a choreographer create and direct original dances, in addition to developing interpretations of existing dances. A Choreographer dances and utilises his or her creativity in other aspects of dance performance. For example, he or she may work with the music director to select music or collaborate with other famous choreographers to enhance such performance elements as lighting, costume and set design.
Videographer
Multimedia specialist.
A multimedia specialist is a media professional who creates, audio, videos, graphic image files, computer animations for multimedia applications. He or she is responsible for planning, producing, and maintaining websites and applications.
Social Media Manager
A career as social media manager involves implementing the company’s or brand’s marketing plan across all social media channels. Social media managers help in building or improving a brand’s or a company’s website traffic, build brand awareness, create and implement marketing and brand strategy. Social media managers are key to important social communication as well.
Copy Writer
In a career as a copywriter, one has to consult with the client and understand the brief well. A career as a copywriter has a lot to offer to deserving candidates. Several new mediums of advertising are opening therefore making it a lucrative career choice. Students can pursue various copywriter courses such as Journalism , Advertising , Marketing Management . Here, we have discussed how to become a freelance copywriter, copywriter career path, how to become a copywriter in India, and copywriting career outlook.
Careers in journalism are filled with excitement as well as responsibilities. One cannot afford to miss out on the details. As it is the small details that provide insights into a story. Depending on those insights a journalist goes about writing a news article. A journalism career can be stressful at times but if you are someone who is passionate about it then it is the right choice for you. If you want to know more about the media field and journalist career then continue reading this article.
For publishing books, newspapers, magazines and digital material, editorial and commercial strategies are set by publishers. Individuals in publishing career paths make choices about the markets their businesses will reach and the type of content that their audience will be served. Individuals in book publisher careers collaborate with editorial staff, designers, authors, and freelance contributors who develop and manage the creation of content.
In a career as a vlogger, one generally works for himself or herself. However, once an individual has gained viewership there are several brands and companies that approach them for paid collaboration. It is one of those fields where an individual can earn well while following his or her passion.
Ever since internet costs got reduced the viewership for these types of content has increased on a large scale. Therefore, a career as a vlogger has a lot to offer. If you want to know more about the Vlogger eligibility, roles and responsibilities then continue reading the article.
Individuals in the editor career path is an unsung hero of the news industry who polishes the language of the news stories provided by stringers, reporters, copywriters and content writers and also news agencies. Individuals who opt for a career as an editor make it more persuasive, concise and clear for readers. In this article, we will discuss the details of the editor's career path such as how to become an editor in India, editor salary in India and editor skills and qualities.
Linguistic meaning is related to language or Linguistics which is the study of languages. A career as a linguistic meaning, a profession that is based on the scientific study of language, and it's a very broad field with many specialities. Famous linguists work in academia, researching and teaching different areas of language, such as phonetics (sounds), syntax (word order) and semantics (meaning).
Other researchers focus on specialities like computational linguistics, which seeks to better match human and computer language capacities, or applied linguistics, which is concerned with improving language education. Still, others work as language experts for the government, advertising companies, dictionary publishers and various other private enterprises. Some might work from home as freelance linguists. Philologist, phonologist, and dialectician are some of Linguist synonym. Linguists can study French , German , Italian .
Public Relation Executive
Travel journalist.
The career of a travel journalist is full of passion, excitement and responsibility. Journalism as a career could be challenging at times, but if you're someone who has been genuinely enthusiastic about all this, then it is the best decision for you. Travel journalism jobs are all about insightful, artfully written, informative narratives designed to cover the travel industry. Travel Journalist is someone who explores, gathers and presents information as a news article.
Quality Controller
A quality controller plays a crucial role in an organisation. He or she is responsible for performing quality checks on manufactured products. He or she identifies the defects in a product and rejects the product.
A quality controller records detailed information about products with defects and sends it to the supervisor or plant manager to take necessary actions to improve the production process.
Production Manager
Merchandiser.
A QA Lead is in charge of the QA Team. The role of QA Lead comes with the responsibility of assessing services and products in order to determine that he or she meets the quality standards. He or she develops, implements and manages test plans.
Metallurgical Engineer
A metallurgical engineer is a professional who studies and produces materials that bring power to our world. He or she extracts metals from ores and rocks and transforms them into alloys, high-purity metals and other materials used in developing infrastructure, transportation and healthcare equipment.
Azure Administrator
An Azure Administrator is a professional responsible for implementing, monitoring, and maintaining Azure Solutions. He or she manages cloud infrastructure service instances and various cloud servers as well as sets up public and private cloud systems.
AWS Solution Architect
An AWS Solution Architect is someone who specializes in developing and implementing cloud computing systems. He or she has a good understanding of the various aspects of cloud computing and can confidently deploy and manage their systems. He or she troubleshoots the issues and evaluates the risk from the third party.
Computer Programmer
Careers in computer programming primarily refer to the systematic act of writing code and moreover include wider computer science areas. The word 'programmer' or 'coder' has entered into practice with the growing number of newly self-taught tech enthusiasts. Computer programming careers involve the use of designs created by software developers and engineers and transforming them into commands that can be implemented by computers. These commands result in regular usage of social media sites, word-processing applications and browsers.
ITSM Manager
Information security manager.
Individuals in the information security manager career path involves in overseeing and controlling all aspects of computer security. The IT security manager job description includes planning and carrying out security measures to protect the business data and information from corruption, theft, unauthorised access, and deliberate attack
Business Intelligence Developer
Applications for admissions are open..

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters

Aakash iACST Scholarship Test 2024
Get up to 90% scholarship on NEET, JEE & Foundation courses

Resonance Coaching
Enroll in Resonance Coaching for success in JEE/NEET exams

ALLEN JEE Exam Prep
Start your JEE preparation with ALLEN
NEET 2024 Most scoring concepts
Just Study 32% of the NEET syllabus and Score upto 100% marks

JEE Main high scoring chapters and topics
As per latest 2024 syllabus. Study 40% syllabus and score upto 100% marks in JEE
Everything about Education
Latest updates, Exclusive Content, Webinars and more.
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Cetifications
We Appeared in
University of Notre Dame
Notre Dame Philosophical Reviews
- Home ›
- Reviews ›
How Terrorism Is Wrong: Morality and Political Violence

Virginia Held, How Terrorism Is Wrong: Morality and Political Violence , Oxford University Press, 2008, 205pp., $45.00 (hbk), ISBN 9780195329599.
Reviewed by Igor Primoratz, University of Melbourne
This is a book on terrorism and political violence more generally, written by a philosopher and accordingly focusing on conceptual and moral, rather than empirical or historical, questions. The book is meant for fellow philosophers and political theorists, but it is written clearly and without philosophical jargon, and will be accessible, and of much interest, to the general reader too.
While political violence is a traditional topic in political and moral philosophy, terrorism -- the type of political violence generally considered most difficult to defend -- was not much discussed before the attacks in the US on 11 September 2001. Virginia Held is one of the few philosophers who gave it sustained attention before it became a fashionable topic. The present book is a collection of seven essays she has published over the last twenty-odd years and one previously unpublished paper. Some essays discuss terrorism or political violence generally, while others look into such related issues as the ways the media deals with political violence, or collective responsibility for ethnic hatred and violence. There is also an essay on the methods of moral inquiry.
In her approach to moral questions, Held combines consequentialism, deontological ethics and the ethics of care. The relevance of the last approach to discussing issues of political violence is rather limited, and Held's position on terrorism and political violence is grounded in consequentialist and deontological considerations of a more traditional type. So is just war theory, but Held's views are not a version of that theory. Indeed, she doubts that just war theory can be of much help in understanding and judging contemporary armed conflicts.
The title of the book might be thought somewhat misleading, as Held does not so much seek to show how terrorism is wrong as how it can be right. To be sure, a title highlighting the latter prospect probably would not have been a good idea in the current atmosphere of the "war on terror." This "war" is both driven and defended by a "moral clarity" claimed by leaders of some major powers and by many analysts and commentators. Held rightly challenges this facile "moral clarity," according to which all terrorism is morally the same, clearly distinct from war, and a monopoly of insurgents, who are both amoral and utterly irrational and fanatical, and therefore never to be engaged with in dialogue or negotiation. She goes on to argue that we should not adopt a sweeping moral rejection of all terrorism, whatever the cause it serves, the circumstances in which it does so, and the consequences of refraining from it; that terrorism is not "uniquely atrocious"; and that it is not necessarily morally worse than war.
The scope and import of any moral assessment of terrorism depends on just what is meant by "terrorism". Accordingly, Held discusses at some length the question of how the term should be defined. The usage over the two centuries or so since the term entered political and moral discourse in the West has been notoriously confusing, fraught with moral emotions and political passions, and plagued by relativism and double standards. It is in such cases that philosophy can demonstrate its relevance to public debates by clarifying central concepts and main positions, spotting missteps in argument, exposing prejudice and double standards, and thus facilitating more rational and discerning moral deliberation and choice. Most definitions of terrorism crafted by philosophers acknowledge the two traits that make up the core concept underlining all shifts in descriptive and evaluative meaning: terrorism is violence aiming at intimidation (fear, terror). Beyond this, philosophers tend to disagree, most importantly on whether terrorism is violence against civilians (non-combatants, innocent people), or can also target members of the military and security services and highly placed government officials. This is the question of a narrow vs. wide definition. A wide definition is in line with common use over two centuries, whereas a narrow definition is revisionary. Yet a narrow definition may be more appropriate in the context of moral assessment of violence and terrorism. Surely there is a considerable moral difference between planting a bomb in an office of (what is considered) an extremely oppressive government and killing a number of its officials, and planting a bomb in a coffee shop and killing a number of common citizens.
Held prefers a wide definition, for reasons I do not find convincing. One is common use. Held points out that the attack on the Marine barracks in Lebanon in 1983, or much Palestinian violence directed at Israeli soldiers, would not count as terrorism on a narrow definition, while the bombing of Dresden or Hiroshima would, and finds these implications unacceptable. To me, they seem just right. She quotes Walter Laqueur's remark that "most terrorist groups in the contemporary world have been attacking the military, the police, and the civilian population" (p. 55) as showing the inadequacy of a narrow definition. But surely the fact that a group has engaged in terrorism to an extent sufficient to consider it a terrorist group does not turn every act of political violence committed by the group into an act of terrorism. Finally, Held rejects narrow definitions on the ground that "it is not at all clear who the 'innocent' are as distinct from the 'legitimate' targets. We can perhaps agree that small children are innocent, but beyond this, there is little moral clarity" (pp. 19-20). Yet even if only "small children" were morally protected against violence that would be a weighty consideration, as indiscriminate political violence against civilians or common citizens is bound to kill and maim children too. Moreover, there are other classes of civilians that are just as clearly innocent in the relevant sense, i.e. innocent of the (alleged) injustice or oppression: opponents of the government, those too old or infirm to take part in political life, or those inculpably ignorant of the immorality of their government's policies.
The book offers two somewhat different definitions of terrorism: as "political violence that usually spreads fear beyond those attacked" and "perhaps more than anything else … resembles small-scale war" (p. 21), and as political violence employed with "the intention either to spread fear or to harm non-combatants" (p. 76). Both definitions run together war and terrorism, and imply that an act of war proper, i.e. one aimed at a legitimate military target, counts as terrorism. For, as Trotsky pointed out in his defense of the "red terror", "war … is founded upon intimidation… . [It] destroys only an insignificant part of the conquered army, intimidating the remainder and breaking their will" ( Terrorism and Communism , Ann Arbor: The University of Michigan Press, 1961, p. 58). Held accepts this implication of her position; I find it problematic.
Philosophers working with a wide definition of terrorism usually distinguish terrorism that targets the military and high government officials and terrorism that attacks common citizens, and argue that the former type of terrorism can be morally justified in certain circumstances, while the latter type is never, or almost never, justified. Held does not take this line. Her book offers two different justifications of terrorist violence, and both apply to the latter as well as the former kind of terrorism.
The first is in terms of the responsibility of citizens in a democracy for what their government does on their behalf. This justification is only suggested at several points in the book and is never developed and defended from likely objections. Held does not make it clear whether she sees common citizens as proper objects of terrorist violence because, as voters, they authorize the government's actions and policies (p. 20), or on account of various types and degrees of support they give the government (pp. 56, 78). Both these lines of argument are open to serious queries.
Held's second justification of terrorism, presented in chapter 4 )“Terrorism, Rights, and Political Goals”) is carefully spelled out. It focuses on the issue of human rights. When human rights of a person or group are not respected, what may we do in order to ensure that they are? On one view, known as consequentialism of rights, if the only way to ensure respect of a certain right of A and B is to infringe on the same right of C, we will be justified in doing so. Held does not accept such trade-offs in rights with the aim of maximizing their respect. But she points out that rights sometimes come into conflict, whether directly or indirectly. When that happens, we cannot avoid comparing the rights involved in terms of their stringency and making certain choices. That applies to the case of terrorism too. Terrorism violates some human rights of its victims. But its advocates claim that in certain circumstances a limited use of terrorism is the only way of bringing about a society in which the human rights of all will be respected.
Even when that is so, it is not enough to make resort to terrorism justified. But it will be justified if an additional condition is met: that of distributive justice. If there is a society where the human rights of a part of the population are respected, while the same rights of another part of the population are being violated, and if the only way of putting an end to that and bringing about a society in which human rights of all are respected is a limited use of terrorism, and finally, if terrorism is directed against members of the first group, which until now has been privileged as far as respect of human rights is concerned -- then terrorism will be morally justified. This is an argument of distributive justice, brought to bear on the problem of violations of human rights. It is more just to equalize the violations of human rights in a stage of transition to a society where the rights of all are respected, than to allow the group which has already suffered large-scale violations of human rights to suffer more such violations (assuming that in both cases we are dealing with violations of the same, or equally stringent, human rights). Human rights of many are going to be violated in any case. "If we must have rights violations, a more equitable distribution of such violations is better than a less equitable one" (p. 88).
This is an original, deontological cum consequentialist justification of terrorism. Neither the indispensable contribution of terrorism to bringing about equal respect of human rights of all nor the justice in the distribution of violations of such rights in the transition stage is, in itself, enough to justify its use. Each is necessary, and jointly the two are sufficient for its justification. Obviously, a critique that reduces Held's position to either of its prongs falls short of the mark. So does the objection that terrorism is as a matter of fact highly unlikely ever to help usher in a better, more just society. If so, that tells against terrorism, rather than against Held's (or any other) stringent moral requirements for a morally defensible recourse to it.
Another objection is that in allowing for sacrificing such basic human rights as the right to life and to bodily security of individual victims of terrorism for the sake of a more just distribution of violations of the same rights within a group in the course of transition to a stage where these rights will be respected throughout that group, Held adopts a collectivistic position that offends against the principles of separateness of persons and respect for persons. In response, Held argues that
to fail to achieve a more just distribution of violations of rights (through the use of terrorism if that is the only means available) is to fail to recognize that those whose rights are already not fairly respected are individuals in their own right, not merely members of a group … whose rights can be ignored. … Arguments for achieving a just distribution of rights violations need not be arguments … that are more than incidentally about groups. They can be arguments about individuals' rights to basic fairness. (pp. 89-90)
Still, a common citizen belonging to the relatively privileged section of the population has done nothing to forfeit her right to life. If she is killed by a terrorist seeking to make the distribution of right to life violations in the entire population more just, her right to life is violated for reasons to do with the group: for the sake of more justice within the group. This has nothing to do with her sins of commission or omission, and in this sense Held's is a collectivistic argument -- and an argument that I, for one, do not find convincing. Held argues that, if we fail to resort to terrorism in the circumstances described in her argument, we thereby fail to recognize that individuals belonging to the disadvantaged section of the population "are individuals in their own right," rather than merely members of a group whose human rights can be ignored. This argument is predicated on moral equivalence of acts and omissions, and on ascription of negative responsibility. This, too, I find problematic. We do not fail to respect the right to life of disadvantaged individuals when we fail to kill or maim other individuals, personally innocent of the plight of the former. The disadvantaged individuals do not have a right that we should engage in terrorism in their behalf, and we do not have a duty to do that. Indeed, I believe we have a duty not to do that.
Whether Held's two-prong justification of terrorism can be successfully defended against this and other possible objections or not, it remains an original, complex, and highly important position on the morality of terrorism. The essay presenting it is the centerpiece of Held's book and her most valuable contribution to the discussion of terrorism as far as fellow philosophers are concerned. The general reader will find much of interest in all the essays in this book. In the wider context of public debate about terrorism and the "war" against it, Held provides a strong antidote to the simplistic deliverances of "moral clarity" many of our political leaders and "public intellectuals" claim to possess.

Protecting Individual Privacy in the Struggle Against Terrorists: A Framework for Program Assessment (2008)
Chapter: 3 conclusions and recommendations, 3 conclusions and recommendations, 3.1 basic premises.
The committee’s work was informed by a number of basic premises. These premises framed the committee’s perspective in developing this report, and they can be regarded as the assumptions underlying the committee’s analysis and conclusions. The committee recognizes that others may have their own analyses with different premises, and so for analytical rigor, it is helpful to lay out explicitly the assumptions of the committee.
Premise 1. The United States faces two real and serious threats from terrorists. The first is from terrorist acts themselves, which could cause mass casualties, severe economic loss, and social dislocation to U.S. society. The second is from the possibility of inappropriate or disproportionate responses to the terrorist threat that can do more damage to the fabric of society than terrorists would be likely to do.
The events of September 11, 2001, provided vivid proof of the damage that a determined terrorist group can inflict on U.S. society. All evidence to date suggests that the United States continues to be a prime target for such terrorist groups as Al Qaeda, and future terrorist attacks could cause
major casualties, severe economic loss, and social disruption. 1 The danger of future terrorist attacks on the United States is both real and serious.
At the same time, inappropriate or disproportionate responses to the terrorist threat also pose serious dangers to society. History demonstrates that measures taken in the name of improving national security, especially in response to new threats or crises, have often proven to be both ineffective and offensive to the nation’s values and traditions of liberty and justice. 2 So the danger of unsuitable responses to the terrorist threat is also real and serious.
Given the existence of a real and serious terrorist threat, it is a reasonable public policy goal to focus on preventing attacks before they occur—a goal that requires detecting the planning for such attacks prior to their execution. Given the possibility of inappropriate or disproportionate responses, it is also necessary that programs intended to prevent terrorist attacks be developed and operated without undue compromises of privacy.
Premise 2. The terrorist threat to the United States, serious and real though it is, does not justify government authorities conducting activities or operations that contravene existing law.
The longevity of the United States as a stable political entity is rooted in large measure in the respect that government authorities have had for the rule of law. Regardless of the merits or inadequacies of any legal regime, government authorities are bound by its requirements until the legal regime is changed, and, in the long term, public confidence and trust in government depend heavily on a belief that the government is indeed adhering to the laws of the land. The premises above would not change even if the United States were facing exigent circumstances. If existing legal authorities (including any emergency action provisions, of which there are many) are inadequate or unclear to deal with a given situation
or contingency, government authorities should seek to change the law rather than to circumvent or disobey it.
A willingness of U.S. government authorities to circumvent or disobey the law in times of emergency is not unprecedented. For example, recently declassified Central Intelligence Agency (CIA) documents indicate widespread violations of the agency’s charter and applicable law in the 1960s and 1970s, during which time the CIA conducted surveillance operations on U.S. citizens under both Democratic and Republican presidents that were undertaken outside the agency’s charter. 3
The U.S. Congress has also changed laws that guaranteed confidentiality in order to gain access to individual information collected under guarantees. For example, Section 508 of the USA Patriot Act, passed in 2001, allows the U.S. Department of Justice (DOJ) to gain access to individual information originally collected by the National Center for Education Statistics under a pledge of confidentiality. In earlier times, the War Powers Act of 1942 retrospectively overrode the confidentiality provisions of the Census Bureau, and it is now known that bureau officials shared individually identifiable census information with other government agencies for the purposes of detaining foreign nationals. 4
Today, many laws provide statutory protection for privacy. Conforming to such protections is not only obligatory, but it also builds necessary discipline into counterterrorism efforts that serves other laudable purposes. By making the government stop and justify its effort to a senior official, a congressional committee, or a federal judge, warrant requirements and other privacy protections often help bring focus and precision to law enforcement and national security efforts. In point of fact, courts rarely refuse requests for judicial authorization to conduct surveillance. As government officials often note, one reason for these high success rates is the quality of internal decision making that the requirement to obtain judicial authorization requires.
Premise 3. Challenges to public safety and national security do not warrant fundamental changes in the level of privacy protection to which nonterrorists are entitled.
The United States is a strong nation for many reasons, not the least of which is its commitment to the rule of law, civil liberties, and respect
for diversity. Especially in times of challenge, it is important that this commitment remain strong and unwavering. New technological circumstances may necessitate an update of existing privacy laws and policy, but privacy and surveillance law already includes means of dealing with national security matters as well as criminal law investigations. As new technologies become more commonly used, these means will inevitably require extension and updating, but greater government access to private information does not trump the commitment to the bedrock civil liberties of the nation.
Note that the term “privacy” has multiple meanings depending on context and interpretation. Appendix L (“ The Science and Technology of Privacy Protection ”) explicates a technical definition of the term, and the term is often used in this report, as in everyday discourse, with a variety of informal meanings that are more or less consistent with the technical definition.
Premise 4. Exploitation of new science and technologies is an important dimension of national counterterrorism efforts.
Although the committee recognizes that other sciences and technologies are relevant as well, the terms of reference call for this report to focus on information technologies and behavioral surveillance techniques. The committee believes that when large amounts of information, personal and otherwise, are determined to be needed for the counterterrorist mission, the use of information technologies will be necessary and counterterrorist authorities will need to collect, manage, and analyze such information. Furthermore, it believes that behavioral surveillance techniques may have some potential for inferring intent from observed behavior if the underlying science proves sound—a capability that could be very useful in counterterrorist efforts “on the ground” if realized in the future.
Premise 5. To the extent reasonable and feasible, counterterrorist programs should be formulated to provide secondary benefits to the nation in other domains.
Counterterrorism programs are often expensive and controversial. In some cases, however, a small additional expenditure or programmatic adjustment may enable them to provide benefits that go beyond their role in preventing terrorism. Thus, they would be useful to the nation even if terror attacks do not occur. For example, hospital emergency reporting systems can improve medical care by prompt reporting of influenza, food poisoning, or other health problems, as well as alerting officials of bioterrorist and chemical attacks.
At the same time, policy makers must be aware of the phenomenon of “statutory mission creep”—in which the goals and missions of a program are expanded explicitly as the result of a specific policy action, such as congressional amendment of an existing law—and avoid its snares. In some instances, such as hospital emergency reporting systems, privacy interests may not be seriously compromised by their application to multiple missions. But in others, such as the use of systems designed for screening terrorists to identify ordinary criminals, privacy interests may be deeply implicated because of the vast and voluminous new data sets that must be brought to bear on the expanded mission. Mission creep may also go beyond the original understandings of policy makers regarding the scope and nature of a program that they initially approve, and thus effectively circumvent careful scrutiny. In some cases, a sufficient amount of mission creep may even result in a program whose operation is not strictly legal.
3.2 CONCLUSIONS REGARDING PRIVACY
The rich digital record that is made of people’s lives today provides many benefits to most people in the course of everyday life. Such data may also have utility for counterterrorist and law enforcement efforts. However, the use of such data for these purposes also raises concerns about the protection of privacy and civil liberties. Improperly used, programs that do not explicitly protect the rights of innocent individuals are likely to create second-class citizens whose freedoms to travel, engage in commercial transactions, communicate, and practice certain trades will be curtailed—and under some circumstances, they could even be improperly jailed.
3.2.1 Protecting Privacy
Conclusion 1. In the counterterrorism effort, some degree of privacy protection can be obtained through the use of a mix of technical and procedural mechanisms.
The primary goal of the nation’s counterterrorism effort is to prevent terrorist acts. In such an effort, identification of terrorists before they act becomes an important task, one that requires the accurate collection and analysis of their personal information. However, an imperfect understanding of which characteristics to search for, not to mention imperfect and inaccurate data, will necessarily draw unwarranted attention to many innocent individuals.
Thus, records containing personal information of terrorists cannot be
examined without violating the privacy of others, and so absolute privacy protection—in the sense that the privacy of nonterrorists cannot be compromised—is not possible if terrorists are to be identified.
This technical reality does not preclude putting into place strong mechanisms that provide substantial privacy protection. In particular, restrictions on the use of personal information ensure that innocent individuals are strongly protected during the examination of their personal information, and strong and vigorous oversight and audit mechanisms can help to ensure that these restrictions are obeyed.
How much privacy protection is afforded by technical and procedural mechanisms depends on critical design features of both the technology and the organization that uses it. Two examples of relevant technical mechanisms are encryption of all data transports to protect against accidental loss or compromise and individually logged 5 audit records that retain details of all queries, including those made by fully authorized individuals to protect against unauthorized use. 6 But the mere presence of such mechanisms does not ensure that they will be used, and such mechanisms should be regarded as one enabler—one set of necessary but not sufficient tools—for the robust independent program oversight described in Recommendation 1c below.
Relevant procedural mechanisms include restrictions on data collection and restrictions on use. In general, such mechanisms govern important dimensions of information collection and use, including an explication of what data are collected, whether collection is done openly or covertly, how widely the data are disseminated, how long they are retained, the decisions for which they are used, whether the processing is
performed by computer or human, and who has the right to grant permissions for subsequent uses.
Historically, privacy from government intrusion has been protected by limiting what information the government can collect: voice conversations collected through wiretapping, e-mail collected through access to stored data (authorized by the Electronic Communications Privacy Act, passed in 1986 and codified as 18 U.S.C. 2510), among others. However, in many cases today, the data in question have already been collected and access to them, under the third-party business records doctrine, will be readily granted with few strings attached. As a result, there is great potential for privacy intrusion arising from analysis of data that are accessible to government investigators with little or no restriction or oversight. In other words, powerful investigative techniques with significant privacy impact proceed in full compliance with existing law—but with significant unanswered privacy questions and associated concerns about data quality.
Analytical techniques that may be justified for the purpose of national security or counterterrorism investigations, even given their potential power for privacy intrusion, must come with assurances that the inferences drawn against an individual will not then be used for normal domestic criminal law enforcement purposes. Hence, what is called for, in addition to procedural safeguards for data quality, are usage limitations that provide for full exploitation on new investigative tools when needed (and justified) for national security purposes, but that prevent those same inferences from being used in criminal law enforcement activity.
An example—for illustration only—of the latter is the use of personal data for airline passenger screening. Privacy advocates have often expressed concerns that the government use of large-scale databases to identify passengers who pose a potential risk to the safety of an airplane could turn into far-reaching enforcement mechanisms for all manner of offenses, such as overdue tax bills or child support payments. One way of dealing with this privacy concern would be to apply a usage-limiting privacy rule that allows the use of databases for the purpose of counterterrorism but prohibits the use of these same databases and analysis for domestic law enforcement. Those suspicious of government intentions are likely to find a rule limiting usage rather less comforting than a rule limiting collection, out of concern that government authorities will find it easier to violate a rule limiting usage than a rule limiting collection. Nevertheless, well-designed and diligently enforced auditing and oversight processes may help over time to provide reassurance that the rule is being followed as well as to provide some actual protection for individuals.
Finally, in some situations, improving citizen privacy can have the
result of improving their security and vice versa. For example, improvements in the quality of data (i.e., more complete, more accurate data) used in identifying potential terrorists are likely to increase security by enhancing the effectiveness of information-based programs to identify terrorists and to decrease the adverse consequences that may occur due to confidentiality violations for the vast majority of innocent individuals. In addition, strong audit controls that record the details of all accesses to sensitive personal information serve both to protect the privacy of individuals and to reduce barriers to information sharing between agencies or analysts. (Agencies or analysts are often reluctant to share information, even among themselves, because they feel a need to protect sources and methods, and audit controls that limit information access provide a greater degree of reassurance that sensitive information will not be improperly distributed.)
Conclusion 2. Data quality is a major issue in the protection of the privacy of nonterrorists.
As noted in Chapter 1 , the issue of data quality arises internally as a result of measurement errors within databases and also as a consequence of efforts to link data or records across databases in the absence of clear, unique identifiers. Sharing personal information across agencies, even with “names” attached, offers no assurances that the linked data are sufficiently accurate for counterterrorism purposes; indeed, there are no metrics for accuracy that appear to be systematically used to assess such linking efforts.
Data of poor quality severely limit the value of data mining in a number of ways. First, the actual characteristics of individuals are often collected in error for a wide array of reasons, including definitional problems, identify theft, and misresponse on surveys.
These errors could obviously result in individuals being inaccurately represented by data mining algorithms as a threat when they are not (with the consequence that personal and private information about them might be inappropriately released for wider scrutiny). Second, poor data quality can be amplified during file matching, resulting in the erroneous merging of information for different individuals into a single file. Again, the results can be improper treatment of individuals as terrorist threats, but here the error is compounded, since entire clusters of information are now in error with respect to the individual who is linked to the information in the merged file.
Such problems are likely to be quite common and could greatly limit the utility of data mining methods used for counterterrorism. There are no obvious mechanisms for rectifying the current situation, other than col-
lecting similar information from multiple sources and using the duplicative nature of the information to correct inaccuracies. However, given that today the existence of alternate sources is relatively infrequent, correcting individual errors will be extraordinarily difficult.
3.2.2 Distinctions Between Capability and Intent
Conclusion 3. Inferences about intent and/or state of mind implicate privacy issues to a much greater degree than do assessments or determinations of capability.
Although it is true that capability and intent are both needed to pose a real threat, determining intent on the basis of external indicators is inherently a much more subjective enterprise than determining capability. Determining intent or state of mind is inherently an inferential process, usually based on indicators such as whom one talks to, what organizations one belongs to or supports, or what one reads or searches for online. Assessing capability is based on such indicators as purchase or other acquisition of suspect items, training, and so on. Recognizing that the distinction between capability and intent is sometimes unclear, it is nevertheless true that placing people under suspicion because of their associations and intellectual explorations is a step toward abhorrent government behavior, such as guilt by association and thought crime. This does not mean that government authorities should be categorically proscribed from examining indicators of intent under all circumstances—only that special precautions should be taken when such examination is deemed necessary.
3.3 CONCLUSIONS REGARDING THE ASSESSMENT OF COUNTERTERRORISM PROGRAMS
Conclusion 4. Program deployment and use must be based on criteria more demanding than “it’s better than doing nothing.”
In the aftermath of a disaster or terrorist incident, policy makers come under intense political pressure to respond with measures intended to prevent the event from occurring again. The policy impulse to do something (by which is usually meant something new) under these circumstances is understandable, but it is simply not true that doing something new is always better than doing nothing. Indeed, policy makers may deploy new information-based programs hastily, without a full consideration of (a) the actual usefulness of the program in distinguishing people or characteristic patterns of interest for follow-up from those not of inter-
est, (b) an assessment of the potential privacy impacts resulting from the use of the program, (c) the procedures and processes of the organization that will use the program, and (d) countermeasures that terrorists might use to foil the program.
The committee developed the framework presented in Chapter 2 to help decision makers determine the extent to which a program is effective in achieving its intended goals, compliant with the laws of the nation, and reflective of the values of society, especially with regard to the protection of data subjects’ privacy. This framework is intended to be applied by taking into account the organizational and human contexts into which any given program will be embedded as well as the countermeasures that terrorists might take to foil the program.
The framework is discussed in greater detail in Chapter 2 .
3.4 CONCLUSIONS REGARDING DATA MINING 7
3.4.1 policy and law regarding data mining.
Conclusion 5. The current policy regime does not adequately address violations of privacy that arise from information-based programs using advanced analytical techniques, such as state-of-the-art data mining and record linkage.
The current privacy policy regime was established prior to today’s world of broadband communications, networked computers, and enormous databases. In particular, it relies largely on limitations imposed on the collection and use of certain kinds of information, and it is essentially silent on the use of techniques that could be used to process and analyze already-collected information in ways that might compromise privacy.
For example, an activity for counterterrorist purposes, possibly a data mining activity, is likely to require the linking of data found in multiple databases. The literature on record linkage suggests that, even assuming the data found in any given database to be of high quality, the data derived from linkages (the “mosaic” consisting of the collection of linked data) are likely to be error-prone. Certainly, the better the quality of the individual lists, the fewer the errors that will be made in record linkage, but even with high-quality lists, the percentage of false matches and false nonmatches may still be uncomfortably high. In addition, it is also the case that certain data mining algorithms are less sensitive to record linkage errors as inputs, since they use redundant information in a way that can, at times, identify such errors and downweight or delete them. Again, even in the best circumstances, such problems are currently extremely
difficult to overcome. Error-prone data are, of course, both a threat to privacy (as innocent individuals are mistakenly associated with terrorist activity) and a threat to effectiveness (as terrorists are overlooked because they have been hidden by errors in the data that would have suggested a terrorist connection).
The committee also notes that the use of analytical techniques such as data mining is not limited to government purposes; private parties, including corporations, criminals, divorce lawyers, and private investigators, also have access to such techniques. The large-scale availability of data and advanced analytical techniques to private parties carries clear potential for abuses of various kinds that might lead to adverse consequences for some individuals, but a deep substantive examination of this issue is outside the primary focus of this report on government policy.
3.4.2 The Promise and Limitations of Data Mining
Chapter 1 (in Section 1.6.1 ) notes that data mining covers a wide variety of analytical approaches for using large databases for counterterrorist purposes, and in particular it should be regarded as being much broader than the common notion of a technology underlying automated terrorist identification.
Conclusion 6. Because data mining has proven to be valuable in private-sector applications, such as fraud detection, there is reason to explore its potential uses in countering terrorism. However, the problem of detecting and preempting a terrorist attack is vastly more difficult than problems addressed by such commercial applications.
As illustrated in Appendix H (“ Data Mining and Information Fusion ”), data mining has proven valuable in a number of private-sector applications. But the data used by analysts to track sales, banks to assess loan applications, credit card companies to detect fraud, and telephone companies to detect fraud are fundamentally different from counterterrorism data. For example, private-sector applications generally have access to a substantial amount of relatively complete and structured data. In some cases, their data are more accurate than government data, and, in others, large volumes of relevant data sometimes enable statistical techniques to compensate 8 to some extent for data of lower quality—thus, either way, reducing the data-cleaning effort required. In addition, a few false positives and false negatives are acceptable in private-sector
applications, because a few false positives can usually be cleared up by contact with clients without a significant draw on resources, and a few false negatives are tolerable. Ground truth—that is, knowledge of what is actually true that can be used to validate or verify a new measurement or technique—is available in many private-sector applications, a point that enables automated learning and refinement to take place. All of the relevant data are available—at once—in private-sector applications.
These attributes are very different in the counterterrorism domain. Ground truth is rarely available in tracking terrorists, in large part because terrorists and terrorist activity are rare. Data specifically associated with terrorists (targeted collection efforts) are sparse and mostly collected in unstructured form (free text, video, audio recordings). The availability of much of the relevant data depends on the specific nature of data collected earlier (e.g., information may be needed to obtain a search warrant that then leads to additional information). Data tracks of terrorists in commercial and government administrative databases (as contrasted with government intelligence databases) are co-mingled with enormously larger volumes of similar data associated with innocent individuals, and they are not in any way apparent or obvious from the fact of their collection—that is, it is generally unknown who is a terrorist in any such database. And links among records in databases of varying accuracy will tend to reflect accuracies characteristic of the most inaccurate of the databases involved.
Such differences are not described here to argue that data mining for counterterrorist applications is ipso facto unproductive or operationally useless. But the existence of these differences underscores the difficulty of productively applying data mining techniques in the counterterrorist domain.
Conclusion 7. The utility of pattern-based data mining is found primarily if not exclusively in its role in helping humans make better decisions about how to deploy scarce investigative resources, and action (such as arrest, search, denial of rights) should never be taken solely on the basis of a data mining result. Automated terrorist identification through data mining (or any other known methodology) is neither feasible as an objective nor desirable as a goal of technology development efforts.
As noted in Appendix H , subject-based data mining and pattern-based data mining have very different characteristics. The common example of pattern-based data mining is what might be called automated terrorist identification, by which is meant an automated process that examines large databases in search of any anomalous pattern that might indicate a terrorist plot in the making. Automated terrorist iden-
tification is not technically feasible because the notion of an anomalous pattern—in the absence of some well-defined ideas of what might constitute a threatening pattern—is likely to be associated with many more benign activities than terrorist activities. In this situation, the number of false leads is likely to exhaust any reasonable limit on investigative or analytical resources. For these reasons, the desirability of technology development efforts aimed at automated terrorist identification is highly questionable.
Other kinds of pattern-based data mining may be useful in helping analysts to search for known patterns of interest (i.e., when they have a basis for believing that such a pattern may signal terrorist intent). For example, analysts may determine that a pattern is suggestive of terrorist activity on the basis of historical experience. By searching for patterns known to be associated with (prior) terrorist incidents, it may well be possible to uncover tangible and useful evidence of similar terrorist plots in the making. The significance of uncovering such plots, even if they are similar to those that have occurred in the past, should not be underestimated. Terrorists learn from their past failures and successes, and to the extent that counterterrorist activities can force them to develop new—and unproven—approaches, they will be placed at a significant disadvantage.
Patterns of interest may also be identified by analysts thinking about sets of activities that are indicative of or associated with terrorist activity, even if there is no historical precedent for such associations. Under some circumstances, terrorists might well be limited in the options they might pursue in attacking a specific target. If so, it might be reasonable to search for patterns associated with the planning and execution of those options.
Still, patterns of interest identified using these techniques should be regarded as indicative rather than authoritative, and they should be used only to suggest when further investigation may be warranted rather than as definitive indications of terrorist activity. The committee believes that data mining routines should never be the sole arbiter prior to actions that have a substantial impact on people’s lives. Data mining should be used to help humans make decisions when the combination of human judgment and automated data mining results in better decisions than human judgment alone. But even when this is the case, it does not negate the fact that data mining routines, on their own, can make obvious mistakes in deciding the rankings and that the use of human judgment can dramatically reduce the rate of errors.
Conclusion 8. Although systems that support analysts in the identification of terrorists can be designed with features and functionality that enhance privacy
protection without significant loss to their primary mission, privacy-preserving examination of individually identifiable records is fundamentally a contradiction in terms.
Systems can often be designed in ways that enhance privacy without compromising their primary mission. For example, in searching for a weapon at a checkpoint, a scanner might generate anatomically correct images of a person’s body in graphic detail. Since what is of interest is not those images but rather the presence or absence of weapons, a system could be designed to detect the presence or absence of a weapon in a particular scan and that fact (presence or absence) reported rather than the image itself. Procedural protections could also be put into place: for example, an individual might be given the choice of going through an imaging scanner or undergoing a pat-down search. (Note also that a different and broader set of privacy implications arises if images are stored for further use, as they may well be for system assessments.)
Nevertheless, in the absence of a near-perfect profile of a terrorist, it is not possible, even in principle, to somehow examine the records of an individual (who might or might not be a terrorist) but to expose those records only if he or she actually is a terrorist. (A profile of a terrorist is intended to enable the sorting of individuals into those who match the profile and those who do not. If the profile is perfect, and the data contained in individual records are entirely accurate, all of those who match can be regarded with certainty as terrorists and all of those who do not match can be regarded with certainty as nonterrorists. In practice, profiles are never perfect and data are not entirely accurate, and so the notion of degrees of match is much more relevant than the notion of simply match or nonmatch.)
As a result, any realistic system examining databases containing information about terrorists will bring a mix of terrorists and nonterrorists to the attention of analysts, who will decide whether these individuals warrant further investigation. “Further investigation” in this nonroutine context necessarily results in an examination of the private personal information for these individuals, and it may result in tangible inconvenience and loss of various freedoms.
Conclusion 9. Research and development on data mining techniques using real population data are inherently invasive of privacy to some extent.
Much of data mining is focused on looking for patterns of behavior, characteristics, or transactions that are a priori plausible (i.e., plausible on the basis of expert judgment and experience) as possible indicators of terrorist activity. But these expert judgments about patterns of interest
must be empirically valid if they are to have significant operational utility, whereby validity is measured by a high true positive rate in identifying terrorist activity and a low false positive rate.
On one hand, a degree of empirical validity can be obtained through the use of synthetic and anonymized data or historical data. For example, large population databases can be seeded with data created to resemble data associated with real terrorist activity. Although such data are, by definition, based on assumptions about the nature and character of terrorist activities, the expert judgment of experienced counterterrorism analysts can provide such data with significant face validity. 9 By testing various algorithms in this environment, the simulated terrorist signatures provide a measure of ground truth against which various data mining approaches can be tested.
On the other hand and by definition, the use of synthetic data to simulate terrorist signatures does not provide real-world empirical validation. Only real data can be the basis for real-world empirical validation. Thus, another approach is to use historical data on terrorists. For example, a great deal is known today about the actual behavioral and activity signatures of the September 11, 2001, terrorists. Seeding large population databases with such data and requiring various algorithms to identify known terrorists provide a complementary approach to validation.
The use of historical data on terrorists is limited in one fundamental respect: it does not account for unprecedented events. But it is entirely reasonable to suggest that the successful application of proposed tools and techniques to known past events is a minimum and necessary (though not sufficient) metric of success.
Using real population databases—large databases filled with actual behavioral and activity data on actual individuals—presents a serious privacy issue. Almost all of these individuals will have no connection to terrorists, and the use of such data in this context means that their private personal information will indeed be compromised.
It is a policy decision as to whether the risks to privacy inherent in conducting research and development (R&D) on data mining techniques for counterterrorism using real population data are outweighed by the potential operational value of using those techniques. The committee
recommends that such R&D should be conducted on synthetic data (see Section 3.7 ), but if the decision is made to use real population data, the committee urges that policy makers face, acknowledge, and report on this issue explicitly.
3.5 CONCLUSIONS REGARDING DECEPTION DETECTION AND BEHAVIORAL SURVEILLANCE
Conclusion 10. Behavioral and physiological monitoring techniques might be able to play an important role in counterterrorism efforts when used to detect (a) anomalous states (individuals whose behavior and physiological states deviate from norms for a particular situation) and (b) patterns of activity with well-established links to underlying psychological states.
Scientific support for linkages between behavioral and physiological markers and mental state is strongest for elementary states (simple emotions, attentional processes, states of arousal, and cognitive processes), weak for more complex states (deception), and nonexistent for highly complex states (terrorist intent and beliefs). The status of the scientific evidence, the risk of false positives, and vulnerability to countermeasures argue for behavioral observation and physiological monitoring to be used at most as a preliminary screening method for identifying individuals who merit additional follow-up investigation. Indeed, there is no consensus in the relevant scientific community nor on the committee regarding whether any behavioral surveillance or physiological monitoring techniques are ready for use at all in the counterterrorist context given the present state of the science.
Conclusion 11. Further research is warranted for the laboratory development and refinement of methods for automated, remote, and rapid assessment of behavioral and physiological states that are anomalous for particular situations and for those that have well-established links to psychological states relevant to terrorist intent.
A number of techniques have been proposed for the machine-assisted detection of certain behavioral and physiological states. For example, advances in magnetic resonance imaging (MRI), electroencephalography (EEG), and other modern techniques have enabled measures of changes in brain activity associated with thoughts, feelings, and behaviors. 10 Research in image analysis has yielded improvements in machine recog-
nition of faces under a variety of circumstances (e.g., when a face is smiling or when it is frowning) and environments (e.g., in some nonlaboratory settings).
However, most of the work is still in the basic research stage, with much of the underlying science still to be validated or determined. If real-world utility of these techniques is to be realized, a number of issues—practical, technical, and fundamental—will have to be addressed, such as the limits to understanding, the largely unknown measurement validity of new technologies, the lack of standardization in the field, and the vulnerability to countermeasures. Public acceptability regarding the privacy implications of such techniques also remains to be demonstrated, especially if the resulting data are stored for unknown future uses or undefined lengths of time.
For example, the current state-of-the-art of functional MRI technology can identify changes in the hemodynamics in certain regions of the brain, thus signaling activity in those regions. But such results are not necessarily consistent across individuals (i.e., different areas in the brains of different individuals may be active under the same stimulus) or even in the same individual (i.e., a slightly different part of the brain may become active even in the same individual under the same stimulus). Certain regions of the brain may be active under a variety of different stimuli. In short, understanding of what these regions do is still primitive. Furthermore, even if simple associations can be made reliably in laboratory settings, this does not necessarily translate into usable technology in less controlled situations. Behavior of interest to detect, such as terrorist intent, occurs in an environment that is very different from the highly controlled behavioral science laboratory.
Conclusion 12. Technologies and techniques for behavioral observation have enormous potential for violating the reasonable expectations of privacy of individuals.
Because the inferential chain from behavioral observation to possible adverse judgment is both probabilistic and long, behavioral observation has enormous potential for violating the reasonable expectations of privacy of individuals. It would not be unreasonable to suppose that most individuals would be far less bothered and concerned by searches aimed at finding tangible objects that might be weapons or by queries aimed at authenticating their identity than by technologies and techniques whose use will inevitably force targeted individuals to explain and justify their mental and emotional states. Even if behavioral observation and physiological monitoring are used only as a preliminary screening methods for identifying individuals who merit additional follow-up investigation,
these individuals will be subject to suspicion that would not fall on others not so identified.
3.6 CONCLUSIONS REGARDING STATISTICAL AGENCIES
Conclusion 13. Census and survey data collected by the federal statistical agencies are not useful for terrorism prevention: such data have little or no content that would be useful for counterterrorism. The content and sampling fractions of household surveys as well as the lack of personal identifiers makes it highly unlikely that these data sets could be linked with any reasonable degree of precision to other databases of use in terrorism prevention.
The content of the data collected by the federal statistical agencies under the auspices of survey and census programs is generally inconsistent with the needs of counterterrorist activities, which require individually identifiable data. Even ignoring issues of access, the value of the data collected on national household or business surveys for terrorism prevention is minimal.
The reasons are several:
Censuses collect little information beyond name, address, and basic demographic data on age, sex, and race; such data are unlikely to be of much value for identifying terrorists or terrorist behavior.
Because a substantial proportion of individuals move frequently, the 10-year cycle of censuses means that the census information is unlikely to be timely, even in supplying current addresses.
The census long form, which has been collected on a sample basis (and its successor program, the American Community Survey, ACS) have more information but still very little that is directly relevant to predicting terrorist activity. Moreover, because these data are collected only for a sample, the probability that those of interest would be in the sample for a given year of the ACS is very slight, and, furthermore, the ability to match files without identifiers into other record systems would be limited. At best, these data might provide background information to provide a description of the socioeconomic make-up of a clustered group of blocks.
Other household surveys also collect little of direct relevance to terrorism prevention, and because they typically draw on much less than 1 percent of the population, the chances of identifying new information on an individual of interest are rather low.
Regarding establishment surveys, for terrorism detection one might be interested in businesses that have increased activity with people in
various parts of the world, but such information is not contained on federal statistical system business censuses and surveys.
A variety of surveys collect information relevant to crime prevention and public health. Data collections on criminal activity, such as the National Crime Victimization Survey and the Uniform Crime Reports, contain data on victims of crime, and they are most useful in identifying geographic areas in which such criminal activity seems to be prevalent. Health surveys, such as the National Health Information Survey, the National Health and Nutrition Examination Survey, and the National Ambulatory Medical Care Survey (largely collected by the National Center for Health Statistics) have value in broader public health programs, but they cannot provide timely information for purposes of biosurveillance or for addressing a bioterrorist attack.
In addition, statistical agencies often collect information under a promise of confidentiality, and the costs of altering or relaxing the rules for confidentiality protection are quite substantial. The quality of the data collected could be adversely affected as a consequence of respondents’ decreased willingness to cooperate. Statistical agencies typically collect information under a promise of confidentiality, and reneging on such officially provided assurances could substantially reduce the quality of the data collected, resulting in much poorer data on the state of the nation. 11
Aside from census and survey data, statistical agencies also hold considerable administrative data (which they have collected from other agencies); such data may be merged with data collected for statistical purposes and thus create the potential for data sets and databases that could at some point conceivably be useful for purposes of counterterrorism. While these derived data sets are currently protected by pledges of
confidentiality if any of the component data sets are so protected, some additional consideration needs to be given to such constructs and how to respond to requests for them from other government agencies.
3.7 RECOMMENDATIONS
In light of the conclusions presented above, the committee has two central recommendations. The first recommendation has subparts a-d.
3.7.1 Systematic Evaluation of Every Information- Based Counterterrorism Program
Recommendation 1. U.S. government agencies should be required to follow a systematic process (such as the one described in the frame work proposed in Chapter 2 ) to evaluate the effectiveness, lawfulness, and consistency with U.S. values of every information-based program, whether classified or unclassified, for detecting and countering terror ists before it can be deployed, and periodically thereafter.
Appendix J (“ The Total/Terrorist Information Awareness Program ”) recounts the story of the Total Information Awareness (TIA) program of the Defense Advanced Research Projects Agency (DARPA) and the intense controversy it engendered—which was a motivation for launching this study. The committee notes that in December 2003, the Department of Defense (DOD) inspector general’s (IG) audit of TIA concluded that the failure to consider privacy adequacy during the early development of TIA led DOD to “risk spending funds to develop systems that may not be either deployable or used to their fullest potential without costly revision.” 12 The DOD-IG report noted that this was particularly true with regard to the potential deployment of TIA for law enforcement: “DARPA need[ed] to consider how TIA will be used in terms of law enforcement to ensure that privacy is built into the developmental process.” 13 Greater consideration of how the technology might be used not only would have served privacy but also would probably have contributed to making TIA more useful.
The committee believes that a systematic approach to the development, procurement, and use of information-based counterterrorism programs is necessary if their full value is to be obtained. The framework
developed by the committee and provided in Chapter 2 is intended as a template for government decision makers to use in evaluating the effectiveness, appropriateness, and validity of every information-based counterterrorism program and system. The U.S. Department of Homeland Security (DHS)—and all agencies of the U.S. government with counterterrorism responsibilities—should adopt the framework described in Chapter 2 , or one similar to it, as a central element in their decision making about new deployments and existing programs in use. Failure to adopt such a systematic approach is likely to result in reduced operational effectiveness, wasted resources, privacy violations, mission creep, and diminished political support, not only for those programs but also for similar and perhaps for not-so-similar programs across the board.
To facilitate accountability, such evaluations (and the data on which they are based) should be made available to the broadest audience possible. Broad availability implies that these evaluations should be unclassified to the maximum extent possible—but even if evaluations are classified, they should still be performed and should be made available to those with the requisite clearances.
Such evaluations should be independent and comprehensive, and in particular they should assess both program effectiveness and privacy together, involving independent experts with the necessary technical, legal, and policy expertise to understand each of these areas and how interactions among them might affect the evaluation. For example, the meaning of privacy is in part technical, and an assessment of privacy cannot be left exclusively to individuals lacking such technical understanding.
Chapter 2 noted that much of the committee’s framework is not new and also that government decision makers have failed to implement many of the guidelines embedded in the framework even when they have been cognizant of them. It is the committee’s hope that by presenting to policy makers a comprehensive framework independent of any particular program, the pressures and exigencies associated with specific crises can be removed from the consideration and adoption of such a framework for application to all programs.
The committee also calls attention to four subrecommendations that derive from Recommendation 1.
Recommendation 1a. Periodically after a program has been operation ally deployed, and in particular before a program enters a new phase in its life cycle, policy makers should apply a framework such as the one proposed in Chapter 2 to the program before allowing it to continue operations or to proceed to the next phase.
A systematic approach such as the framework in Chapter 2 is not intended to be applied only once in the life cycle of any given program. As noted in Appendix D (“ The Life Cycle of Technology, Systems, and Programs ”), a program undergoes a number of different phases in its lifetime: identification of initial needs, research and technology development, systems development, and operational deployment and continual operational monitoring. Each of these phases provides a desirable opportunity for applying the framework to help decide whether and how the program should transition to the next phase. Each of the framework’s questions should still be asked. But the answers to those questions as well as the interpretation of the answers will vary depending on the phase. Such a review may result in a significant modification or even a cancellation of a given program.
The committee calls special attention to the importance of operational monitoring, whose purpose is to ensure that the initial deployed capability remains both effective at contributing to the mission for which it was designed and acceptable from a privacy standpoint. Often after initial deployment, the operational environment changes. Improved base technologies or entirely new technologies become available. Existing threat actors change their tactics, or entirely new threats emerge. Executive branch policies change, or new administrations take office. Analysts gain experience, or new analysts arrive. Interpretations of existing law change through court decisions, or new legislation is passed. Data-based models may change simply because more data have become available that change the parameters and estimates on which the models are based. Error rates may change for similar reasons. Because every program is necessarily embedded in this milieu, the net result is that successful programs are almost always dynamic, in that they evolve in response to such changing circumstances.
An evolved program is, by definition, not the same as the original program—and it is a fair question to ask whether the judgments made about any program in its original form would be valid for an evolved program. For these reasons, a policy regime is necessary that provides for periodic reassessment and reevaluation of a program after initial deployment, at the same time promoting and fostering necessary changes—whether technological, procedural, legal, ethical, or other.
Recommendation 1a is important to programs currently in existence—that is, programs in existence today, and especially programs that are operationally deployed today should be evaluated against the framework. To the best of the committee’s knowledge, no such evaluations have been performed for any data mining or deception detection programs in operation, although this is not to say that none have been done. If such evaluations have been performed, they should be made
available to policy makers (senior officials in the executive branch or the U.S. Congress), and if possible, the public as well. If not, they should be undertaken with all due speed. And if they cannot be performed without access to classified information, an independent group of experts with the requisite clearances should be chartered to perform such assessments.
Recommendation 1b. To protect the privacy of innocent people, the research and development of any information-based counterterrorism program should be conducted with synthetic population data. If and when a program meets the criteria for deployment in the committee’s illustrative framework described in Chapter 2 , it should be deployed only in a carefully phased manner, e.g., being field tested and evaluated at a modest number of sites before being scaled up for general use. At all stages of a phased deployment, data about individuals should be rigorously subjected to the full safeguards of the framework.
Almost by definition, technology in the R&D stage is nascent and unproven. Nascent and unproven technologies are not sufficiently robust or reliable to warrant risking the privacy of individuals—that is, the very uncertain (perhaps nonexistent) benefit that would be derived from their use does not justify the very real cost to privacy that would inevitably accompany their widespread use in operational settings. Thus, the committee advocates R&D based on synthetic population data whose use poses very little risk of violating the privacy of innocent individuals. In addition, the successful use of synthetic data in many fields, such as epidemiology, medicine, and chemistry, for testing methods provides another reason to explore its potential uses in counterterrorism.
The committee believes that realistic synthetic population data could probably be created along the lines originally suggested in Rubin and in Little and further developed by Fienberg et al. and Reiter, 14 for the specific purpose of providing the background against which terrorist signatures are sought. Furthermore, because it is difficult to create from entirely synthetic data large databases that are useful for testing and (partially) validating data mining techniques and algorithms, a partial substitute for entirely synthetic data is data derived from real population data in such a way that the individual identities of nonterrorists are masked
while preserving some of the important large-scale statistical properties of those data.
Using synthetic population data as the background, a measure of the utility of various data mining approaches can be obtained in R&D. Such results must be evaluated in the most rigorous and independent manner possible in order to determine if the program should move into deployment.
If the results are determined to be sufficiently promising (e.g., with sufficiently low false positive and false negative rates) that they offer significant operational capability, it is reasonable to apply the new capabilities to real data in an operational context. 15 But the change from synthetic to real data must be accompanied by a full array of operational safeguards that protect individuals from harm to their privacy, as suggested by the committee’s proposed framework. Put differently, if real data are to be used, they—and the individuals with whom they are associated—deserve the full benefit of the privacy protections associated with the program in question.
Transitioning to an operational context from R&D must also be done carefully and is best undertaken in small phases. The traditional approach to acquisition generally involves the deployment of operational capabilities in large blocks of capability (i.e., large functional components deployed on a wide scale). Experience indicates that this approach is often slow and cumbersome, and it increases technical, programmatic, and budgetary risks. The operational environment often changes significantly in the time between initial requirements specification and first deployment—thus, the capability may even be obsolete when it is first deployed. And deploying systems on a large scale before they are deployed on a small scale is almost always problematic, because small-scale operational trials are needed to shake out the inevitable bugs when R&D technologies meet the real world.
By contrast, phased deployment is based on a philosophy of “build-a-little, test-a-little, deploy-a-little.” Phased deployment recognizes that kinks and problems in the deployment of any new capability are inevitable, positing that by making small changes, system developers will be able to more easily identify and correct these problems than when everything changes all at once. Small changes are easier to reverse, should that become necessary. It also becomes feasible to test new capabilities offered by small changes in parallel with the baseline version, so that ground
truth provided by the baseline version can be used to validate the new capabilities when their domain of operation is the same.
The committee recognizes that, under this approach, operational capabilities will not have been subject to real-world empirical validation before deployment, although they will have had as much validation as possible with synthetic population data. And the phased deployment of privacy-sensitive capabilities reduces the likelihood of inappropriate or improper compromises of privacy from what they would have been under a more traditional acquisition model. 16
The approach recommended above (synthetic data before deployment, deployment only in measured phases) places a high premium on two actions. First, every effort must be made to create good synthetic data that are useful for testing the validity of machine-learning tools and are simultaneously very realistic. For synthetic terrorist data, both historical data and expert judgment play a role in developing signatures that might plausibly be associated with terrorist activity, and plausibility should be assessed through independent panels of judges without a vested interest in any given scenario. Such judges must also be trained in or experienced with evasion or obfuscation techniques. For synthetic population data, every use must be made of known techniques for confidentiality protection and statistical disclosure limitation 17 to reduce the likelihood that the privacy of individuals is compromised, and further research on the creation of better synthetic data to represent large-scale populations is certainly warranted.
Second, evaluation of R&D results must truly be independent and rigorous, with high standards of performance needed for a decision to deploy. As noted in Conclusion 4, the rule that “X is better than doing nothing” often drives deployment decisions, and, given the high potential costs to individual privacy of deployment, the benefits afforded by deployment must be more than marginal to warrant the potential cost.
Recommendation 1c. Any information-based counterterrorism program of the U.S. government should be subjected to robust, independent oversight of the operations of that program, a part of which would
entail a practice of using the same data mining technologies to “mine the miners and track the trackers.”
In practice, operational monitoring is generally the responsibility of the program managers and operational personnel. But as discussed in Appendix G (“ The Jurisprudence of Privacy Law and the Need for Independent Oversight ”), oversight is necessary to ensure that actual operations have been conducted in accordance with stated policies.
The reason is that, in many cases, decision makers formulate policies in order to balance competing imperatives. For example, the public demands both a high degree of effectiveness in countering terrorism and a high degree of privacy. Program administrators themselves face multiple challenges: motivating high performance, adhering to legal requirements, staying within budget, and so on. But if operational personnel adhere to some elements of a policy and not to others, the balance that decision makers intended to achieve will not be realized in practice.
The committee emphasizes that independent oversight is necessary to ensure that commitments to minimizing privacy intrusions embedded in policy statements are realized in practice. The reason is that losses of privacy are easy to discount under the pressure of daily operations, and those elements of policy intended to protect privacy are more likely to be ignored or compromised. Without effective oversight mechanisms in place, public trust is less likely to be forthcoming. In addition, oversight can support continuous improvement and guide administrators in making organizational change.
For example, program oversight is essential to ensure that those responsible for the program do not bypass procedures or technologies intended to protect privacy. Noncompliance with existing privacy-protecting laws, regulations, and best practices diminishes public support and creates an environment in which counterterrorism programs may be curtailed or eliminated. Indeed, even if shortcuts and bypasses increase effectiveness in a given case, in the long run scandals and public outcry about perceived abuses will reduce the political support for the programs or systems involved—and may deprive the nation of important tools useful in the counterterrorist mission. Even if a program is effective in the laboratory and expected to be so in the field, its deployment must be accompanied by strong technical and procedural safeguards to ensure that the privacy of individuals is not placed at undue risk.
Oversight is also needed to protect against abuse and mission creep. Experience and history indicate that in many programs that collect or use personal information, some individuals may violate safeguards intended to protect individual privacy. Hospital clerks have been known to exam-
ine the medical records of celebrities without having a legitimate reason for doing so, simply because they are curious. Police officers have been known to examine the records of individuals in motor vehicle information systems to learn about the personal lives of individuals with whom they interact in the course of daily business. And, of course, compromised insiders have been known to use the information systems of law enforcement and intelligence agencies to further nefarious ends.
The phenomenon of mission creep is illustrated by the Computer-Assisted Passenger Prescreening System II (CAPPS II) program, initially described in congressional testimony as an aviation security tool and not a law enforcement tool but which morphed in a few months to a system that would analyze information on persons “with [any] outstanding state or federal arrest warrants for crimes of violence.” 18
To guard against such practices, the committee advocates program oversight that mines the miners and tracks the trackers. That is, all operation and command histories and all accesses to data-based counterterrorism information systems should be logged on an individual basis, audited, and mined with the same technologies and the same zeal that are applied to combating terrorists. If, for example, such practices had been in place during Robert Hanssen’s tenure at the Federal Bureau of Investigation (FBI), his use of its computer systems for unauthorized purposes might have been discovered sooner.
Finally, the committee recognizes the phenomenon of statutory mission creep, as defined above in the discussion of Premise 5. It occurs, for example, because in responding to a crisis, policy makers will naturally focus on adapting existing programs and capabilities rather than creating new ones. On one hand, if successful, adaptation often promises to be less expensive and faster than creating a new program or capabilities from scratch. On the other hand, because an existing program is likely to be highly customized for specific purposes, adapting that program to serve other purposes effectively may prove difficult—perhaps even more difficult than creating a program from scratch. As importantly, adapting an existing program to new purposes may well be contrary to agreements and understandings established in order to initiate the original program in the first place.
The committee does not oppose expanding the goals and missions of a program under all circumstances. Nevertheless, it cautions that such expansion should not be undertaken hastily in response to crisis. In the committee’s view, following diligently the framework presented in Chapter 2 is an important step in exercising such caution.
Recommendation 1d. Counterterrorism programs should provide meaningful redress to any individuals inappropriately harmed by their operation.
Programs that are designed to balance competing interests (in the case of counterterrorism, collective security and individual privacy and civil liberties) will naturally be biased in one direction or another if their incentive/penalty structure is not designed to reflect this balance. The availability of redress to the individual harmed thus acts to promote the goal of compliance with stated policy—as does the operational oversight mentioned in Recommendation 1c—and to provide incentives for the government to improve the policies, technologies, and data underlying the operation of the program.
Although the committee makes no specific recommendation concerning the form of redress that is appropriate for any given privacy harm suffered by innocent individuals as the result of a counterterrorism program, it notes that many forms of redress are possible in principle, ranging from apology to monetary compensation. The most appropriate form of redress is likely to depend on the nature and purpose of the specific counterterrorism program involved. However, the committee believes that, at a minimum, an innocent individual should always be provided with at least an explicit acknowledgment of the harm suffered and an action that reduces the likelihood that such an incident will ever be repeated, such as correcting erroneous data that might have led to the harm. Note that responsibilities for correction should apply to the holder of erroneous data, regardless of whether the holder is the government or a third party.
The availability of redress might, in principle, enable terrorists to manipulate the system in order to increase their chances of remaining undetected. However, as noted in Item 7 of the committee’s framework on effectiveness, information-based programs should be robust and not easily circumvented by adversary countermeasures, and thus the possibility that terrorists might manipulate the system is not a sufficient argument against the idea of redress.
3.7.2 Periodic Review of U.S. Law, Policy, and Procedures for Protection of Privacy
Recommendation 2. The U.S. government should periodically review the nation’s laws, policies, and procedures that protect individuals’ private information for relevance and effectiveness in light of chang ing technologies and circumstances. In particular, Congress should reexamine existing law to consider how privacy should be protected in the context of information-based programs (e.g., data mining) for counterterrorism.
The technological environment in which policy is embedded is constantly changing. Although technological change is not new, the pace of technological change has dramatically increased in the digital age. As noted in Engaging Privacy and Information Technology in a Digital Age , advances in information technology make it easier and cheaper by orders of magnitude to gather, retain, and analyze information, and other trends have enabled access to new kinds of information that previously would have been next to impossible to gather about another individual. 19 Furthermore, new information technologies have eroded the privacy protection once provided through obscurity or the passage of time. Today, it is less expensive to store information electronically than to decide to get rid of it, and new and more powerful data mining techniques and technologies make it much easier to extract and identify personally identifiable patterns that were previously protected by the vast amounts of data “noise” around them.
The security environment is also constantly changing. New adversaries emerge, and counterterrorist efforts must account for the fact that new practices and procedures for organizing, training, planning, and acquiring resources may emerge as well. Most importantly, new attacks appear. The number of potential terrorist targets in the United States is large, 20 and
although the different types of attack on these targets may be limited, attacks might be executed in myriad ways.
As an example of a concern ripe for examination and possible action, the committee found common ground in the proposition that policy makers should seriously consider restrictions on how personal information is used in addition to restrictions on how records are collected and accessed. Usage restrictions could be an important and useful supplement to access and collection limitation rules in an era in which much of the personal information that can be the basis for privacy intrusion is already either publicly available or easily accessible on request without prior judicial oversight. Privacy protection in the form of information usage restrictions can provide a helpful tool that balances the need to use powerful investigative tools, such as data mining, for counterterrorism purposes and the imperative to regulate privacy intrusions of such techniques through accountable adherence to clearly stated privacy rules. ( Appendix G elaborates on this aspect of the recommendation.)
Such restrictions can serve an important function in helping to ensure that programs created to address a specific area stay focused on the problem that the programs were designed to address and in guarding against unauthorized or unconsidered expansion of government surveillance power. They also help to discourage mission creep, which often expands the set of purposes served by the program without explicit legislative authorization and into areas that are poorly matched by the original program’s structure and operation. An example of undesirable mission creep would be the use of personal data collected from the population acquired for counterterrorist purposes to uncover tax evaders or parents who have failed to make child support payments. This is not to say that finding such individuals is not a worthy social goal, but rather that the mismatch between such a goal and the intrusiveness of data collection measures for counterterrorist purposes is substantial indeed. Without clear legal rules defining the boundaries for use between counterterrorism and inappropriate law enforcement uses, debates over mission creep are likely to continue without constructive resolution.
A second example of a concern that may be ripe for legislative action involves the current legal uncertainty supporting private-sector liability for cooperation with government data mining programs. Such uncertainty creates real risk in the private sector, as indicated by the present variety of private lawsuits against telecommunications service providers, 21 and private-sector responsibilities and rights must be clarified along
with government powers and privacy protections. What exists today is a mix of law, regulation, and informal influence in which the legal rights and responsibilities of private-sector entities are highly uncertain and not well understood.
A coherent, comprehensive legal regime regulating information-intensive surveillance such as government data mining, would do much to reduce such uncertainty. As one example, such a regime might address the issue of liability limitation for private-sector data sources (database providers, etc.) that provide privacy-intrusive information to the government.
Without spelling out the precise scope and coverage of the comprehensive regime, the committee believes that to the extent that the government legally compels a private party to provide data or a private party otherwise complies with an apparently legal requirement to disclose information, it should not be subject to liability simply for the act of complying with the government compulsion or legal requirement. Any such legal protection should not extend to the content of the information it supplies, and the committee also believes that the regime should allow incentives for data providers to invest reasonable effort in ensuring the quality of the data they provide. Furthermore, they should provide effective legal remedies for those individuals who suffer harm as a result of provider negligence. Furthermore, the regime would necessarily preserve the ability of individuals to challenge the constitutionality of the underlying data access statute.
Listed below are other examples of how the adequacy of privacy-related law might be called into question by a changing environment ( Appendix F elaborates on these examples).
Conducting general searches. On one hand, the Fourth Amendment forbids general searches—that is, searches that are not limited as to the location of the search or the type of evidence the government is seeking—by requiring that all searches and seizures must be reasonable and that all warrants must state with particularity the item to be seized and the place to be searched. On the other hand, machine-aided searching of enormous digital transaction records is in some ways analogous to a general search. Such a search can be a dragnet that sweeps through millions or billions of records, often containing highly sensitive information. Much like a general search in colonial times was not limited to a particular person or place, a machine-aided search through digital databases can be very broad. How, if at all, should database searches be regulated by the Fourth Amendment or by statute?
A related issue is that the historical difficulty of physical access to ostensibly public information has provided a degree of privacy protection
for that information—what might be known as privacy through obscurity. But a search-enabled digital world erodes some of these previously inherent protections against invasions of privacy, changing the technological milieu that surrounds privacy jurisprudence.
Increased access to data; searches and surveillance of U.S. persons outside the United States. The Supreme Court has not yet addressed whether the Fourth Amendment applies to searches and surveillance for national security and intelligence purposes that involve U.S. persons 22 who are connected to a foreign power or that are conducted wholly outside the United States. 23 Lower courts, however, have found that there is an exception to the Fourth Amendment’s warrant requirement for searches conducted for intelligence purposes within the United States that involve only non-U.S. persons or agents of foreign powers. 24 The Supreme Court has yet to rule on this important issue, and Congress has not supplied any statutory language to fill the gap.
Third-party records. Two Supreme Court cases ( United States v. Miller , 1976, and Smith v. Maryland , 1979) 25 have established the precedent that there is no constitutionally based reasonable expectation of privacy for information held by a third party, and thus the government today has access unrestricted by the Fourth Amendment to private-sector records on every detail of how people live their lives. Today, these third-party transactional records are available to the government subject to a very low threshold—through subpoenas that can be written by almost any government agency without prior judicial oversight—and are one of the primary data feeds for a variety of counterterrorist data mining activities. Thus, the public policy response to privacy erosion as a result of data mining used with these records will have to address some combination of the scope of use for the data mining results, the legal standards for access to and use of transactional information, or both. 26 (See also Appendix G for
discussion of how usage limitations can fill gaps in current regulation of the confidentiality of third-party records.)
Electronic surveillance law. Today’s law regarding electronic surveillance is complex. Some of the complexity is due to the fact that the situations and circumstances in which electronic surveillance may be involved are highly varied, and policy makers have decided that different situations call for different regulations. But it is an open question as to whether these differences, noted and established in one particular set of circumstances, can be effectively maintained over time. Although there is broad agreement that today’s legal regime is not optimally aligned with the technological and circumstantial realities of the present, there is profound disagreement about whether the basic principles underlying today’s regime continue to be sound as well as in what directions changes to today’s regime ought to occur.
In making Recommendation 2, the committee intends the government’s reexamination of privacy law to cover the issues described above but not be limited to them. In short, Congress and the president should work together to ensure that the law is clear, appropriate, up to date, and responsive to real needs.
Greater clarity and coherence in the legal regime governing information-based programs would have many benefits, both for privacy protection and for the counterterrorist mission. It is perhaps obvious that greater clarity helps to protect privacy by eliminating what might be seen as loopholes in the law—ambiguities that can be exploited by well-meaning national security authorities, thereby overturning or circumventing the intent of previously established policy that balanced competing interests. But the benefits of greater clarity from the standpoint of improving the ability of the U.S. government to prosecute its counterterrorism responsibilities are less obvious and thus deserve some elaboration.
First and most importantly from this perspective, greater legal clarity would help to reduce public controversy over potentially important tools that might be used for counterterrorist purposes. Although many policy makers might wish that they had a free hand in pursuing the counterterrorist mission and that public debate and controversy would just go away, the reality is that public controversy does result when the government is seen as exploiting ambiguities and loopholes.
As discussed in Appendix I (“ Illustrative Government Data Mining Programs and Activity ”), a variety of government programs have been shut down, scaled back, delayed, or otherwise restricted over privacy considerations: TIA, CAPPS II for screening airline passengers, MATRIX (Multistate Anti-Terrorism Information Exchange) for linking law enforcement records across states with other government and private-sector
databases, and a number of data-sharing experiments between the U.S. government and various airlines. Public controversy about these efforts may have prematurely compromised counterterrorism tools that might have been useful. In addition, they have also made the government more wary of national security programs that involve data matching and made the private sector more reluctant to share personal information with the government in the future.
In this regard, this first rationale for greater clarity is consistent with the conclusion of the Technology and Privacy Advisory Committee: “[privacy] protections are essential so that the government can engage in appropriate data mining when necessary to fight terrorism and defend our nation. And we believe that those protections are needed to provide clear guidance to DOD personnel engaged in anti-terrorism activities.” 27
Second, greater legal clarity and coherence can enhance the effectiveness of certain information-based programs. For example, the Privacy Act of 1974 requires that personal data used by federal agencies be accurate, relevant, timely, and complete. On one hand, these requirements increase the likelihood that high-quality data are stored, thus enhancing the effectiveness of systems that use data subject to those requirements. On the other hand, both the FBI’s National Crime Information Center and the passenger screening database of the Transportation Security Administration have exemptions from some of these requirements; 28 to the extent that these exemptions result in lower-quality data, these systems are likely to perform less well.
Third, the absence of a clear legal framework is likely to have a profound effect on the innovation and research that are necessary to improve the accuracy and effectiveness of information-based programs. Such clarity is necessary to support the investment of financial, institutional, and human resources in often risky research that may not pay dividends for
decades. But that type of research is essential to counterterrorism efforts and to finding better ways of protecting privacy.
Finally, a clear and coherent legal framework will almost certainly be necessary to realize the potential of new technologies to fight terrorism. Because such technologies will operate in the political context of an American public concerned about privacy, the public—and congressional decision makers—will have to take measures that protect privacy when new technologies are deployed. All technological solutions will require a legal framework within which to operate, and there will always be gaps left by technological protections, which law will be essential to fill. Consequently, a lack of clarity in that framework may not only slow their development and deployment, as described above, but also make technological solutions entirely unworkable.
This page intentionally left blank.
All U.S. agencies with counterterrorism programs that collect or "mine" personal data -- such as phone records or Web sites visited -- should be required to evaluate the programs' effectiveness, lawfulness, and impacts on privacy. A framework is offered that agencies can use to evaluate such information-based programs, both classified and unclassified. The book urges Congress to re-examine existing privacy law to assess how privacy can be protected in current and future programs and recommends that any individuals harmed by violations of privacy be given a meaningful form of redress.
Two specific technologies are examined: data mining and behavioral surveillance. Regarding data mining, the book concludes that although these methods have been useful in the private sector for spotting consumer fraud, they are less helpful for counterterrorism because so little is known about what patterns indicate terrorist activity. Regarding behavioral surveillance in a counterterrorist context, the book concludes that although research and development on certain aspects of this topic are warranted, there is no scientific consensus on whether these techniques are ready for operational use at all in counterterrorism.
Welcome to OpenBook!
You're looking at OpenBook, NAP.edu's online reading room since 1999. Based on feedback from you, our users, we've made some improvements that make it easier than ever to read thousands of publications on our website.
Do you want to take a quick tour of the OpenBook's features?
Show this book's table of contents , where you can jump to any chapter by name.
...or use these buttons to go back to the previous chapter or skip to the next one.
Jump up to the previous page or down to the next one. Also, you can type in a page number and press Enter to go directly to that page in the book.
Switch between the Original Pages , where you can read the report as it appeared in print, and Text Pages for the web version, where you can highlight and search the text.
To search the entire text of this book, type in your search term here and press Enter .
Share a link to this book page on your preferred social network or via email.
View our suggested citation for this chapter.
Ready to take your reading offline? Click here to buy this book in print or download it as a free PDF, if available.
Get Email Updates
Do you enjoy reading reports from the Academies online for free ? Sign up for email notifications and we'll let you know about new publications in your areas of interest when they're released.

UPSC SUPER SIMPLIFIED
Your Goals. Our Mission.
Essay on terrorism

What is terrorism?
In the most comprehensive sense, terrorism is an intentional use of indiscriminate violence as a mechanism to create terror or fear in order to achieve a political, religious, or ideological objective. Terrorism is a form of asymmetric warfare. It is the use of violence against innocent civilians or non-combatants. The word terrorism has gained popularity following the attacks on the World Trade Centers New York in September 2001 also referred to as the 9/11 terrorist attacks.
History of terrorism
The nuisance of terrorism is as old as the Roman Empire. The roots and practice of terrorism can be traced back at least to the first century AD. The word terrorism itself was used for the first time to describe the acts of the Jacobin Club during the reign of terror in the French Revolution.
Types of terrorism
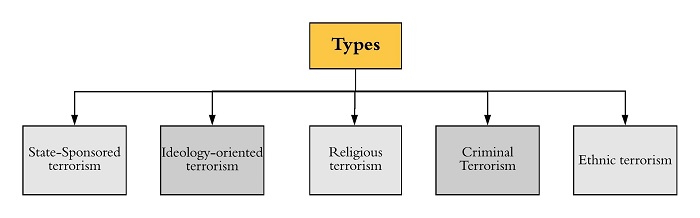
State-Sponsored terrorism
It is pursued in order to achieve such clearly stated foreign policy objectives. Massive-scale state-sponsored terrorism reemerged in international politics in the 1960s and 1970s. Now, along with religious terrorism, state-sponsored terrorism has greatly altered the design of terrorist attacks around the world. Since its independence, India has been having the same problems from Pakistan.
Ideology-oriented terrorism
Ideology-oriented terrorism is typically categorized into two: left-wing and right-wing terrorism.
Left-wing terrorism
It is violence against the ruling class, mostly by the lower classes, motivated by leftist ideology. These include the Red Army faction or the Baader Meinhof Gang in former West Germany, the Red Brigades in Italy, the Maoist groups in India and Nepal.
Right-wing Terrorism
Right-wing groups tend to seek to protect the status quo or to return to some past situation that they feel should have been preserved. Examples of this include: fascism in Italy, nazism in Germany, white supremacist movements in the USA known as the Ku Klux Klan (KKK).
Religious terrorism
Terrorist groups are notably motivated by religion. Religious terrorism is more destructive in nature. These groups are motivated either in whole or in part by a religious imperative that considers violence as a sacred duty. The theology of ISIS is in accordance with the Wahabi theological ideology.
Criminal Terrorism
Terrorist activities are used to aid in crime and criminal profit. For instance, in narco-terrorism, narcotics traffickers attempt to influence the policies of the Government by systematic threat or use by violence.
Ethnic terrorism
It is deliberate violence by a subnational ethnic group to advance its cause. Such violence usually focuses either on the creation of a separate state or on the elevation of the status of one ethnic group over others. Tamil Nationalist groups in Sri Lanka, insurgent groups in North East India, and the Khalistan movement are examples of ethnonationalism terrorist activities.
Reasons behind the terrorism
There are many reasons which make people or a group terrorist. Those reasons are political, religious, poverty, and lack of education.
The main cause of terrorism is perceived socio-political or historical injustice and a belief that violence will lead to change. People who choose this path when they have been stripped off their land or rights are denied the same. Examples- Hamas group of Palestine, Liberation Tigers of Tamil Eelam ( LTTE), Maoists and the United Liberation Front of Assam (ULFA)
Terrorist groups use a specific religious ideology to inspire people to join terrorist groups. For example, ISIS and Al-Qaeda use Islamic ideology making people follow them.
Socio-e conomic
Many people who join terrorist groups are illiterate and poor. Terrorism can spread like a virus in vulnerable and marginalized communities. These people can easily be pursued by terrorism groups.
A lack of employment and unequal growth encourages unemployed youth to indulge in criminal acts and narcotics.
However, the above arguments are partially true. Of the 9/11 conspirators, eight were engineers by education. Osama bin Laden’s father owned the largest construction company in the Kingdom of Saudi Arabia. So, terrorism is not always a result of illiteracy and poverty.
Intolerance
Because of the increasing population and decreasing resources, intolerance is growing in society. Increasing globalization of the society come to transcend national boundaries spreading terrorism.
The ineffective anti-terrorism legislation and misplaced judicial activism are somehow also responsible for growing terrorism.
Structural issues
There are structural inadequacies in the state apparatus namely weaknesses in the intelligence structure -human as well as technical, inadequate modernization of police paramilitary forces and the Armed Forces, unimaginative media management and coverage, reactive response, and slow government decision-making lack of clear strategy and policy on internal security.
In the Indian context, the reasons over the past few years have been numerous. Our consolidation as a secular, federal, and democratic state is still evolving and the fundamentalist forces often exploit a diversity of our multi-ethnic and multi-religious society.
Role of technology Terrorism is spreading fast in the modern era as technology is now available to conduct acts of terror and the targets of terrorism are more widespread than ever before. Sophisticated means of communications such as electronic media, print media, social media, and the Internet help terrorists to quickly promote their ideology and hate campaign and exploit cyber terrorism. There are secure and encrypted messaging apps like Telegram. It is the very messaging platform at Isis used to claim responsibility for attacks. For instance, the PlayStation primarily is a gaming device. Experts believe that ISIS terrorists use PlayStation to communicate. One can send private messages via the PlayStation Network. The FBI and the CIA believe that potential terrorists have been communicating via these networks. In the case of 26/11 Mumbai attacks, the terrorists came armed not just with guns and grenades but also carrying cell phones, GPS devices, and other high-tech gear. This level of sophistication is worrying. In the Christchurch massacre of New Zealand, the attack was not reported by bystanders or by security cameras at mosques. This had been live-streamed by the shooter himself on Facebook.
Global Terrorism Index (GTI) 2019
This report is annually released by the Sydney-based Institute for Economics and Peace. As per this report, India as the seventh-worst terrorism affected the country. Jammu & Kashmir is India’s most affected region by terrorism in 2018. Most of these attacks were perpetrated by the Hizbul Mujahideen (HM), Jaish-e-Mohammad (JeM), and Lashkar-e-Taiba (LeT). 8,437 Indians have lost their lives since 2001 at the hands of terrorists.

Why is India a victim of terror?
India is suffering from ethno-nationalist, religious, left-wing, and narco-terrorism. Some well-known examples of terrorist activities in India are Mumbai attacks of 26/11, 1993 Mumbai serial bomb blasts, attack on Akshardham temple in 2002, Mumbai train blasts 2006, Parliament attacks of 2001 attacks on Armed Forces camps in Pathankot and Uri.
India is geographically located between Asia’s two principal areas of illicit opium production -the Golden Crescent and the Golden Triangle. This leads to a heavy influx of drugs and arms.
Pakistan and China
India has a hostile neighbor in the form of Pakistan with a land border of 3,400 kilometers. Pakistan sponsors state terrorism and fundamentalist forces, particularly through its inter-services intelligence, also known as ISI.
Also, India has unresolved border issues with China. And China has active military and nuclear cooperation with Pakistan.
Porous border
India shares a contiguous and porous border with smaller SAARC nations such as Nepal, Bangladesh, Myanmar, and Sri Lanka. Accompanying problems such as illegal migration and smuggling in the border belt and resulting social tensions create a conducive environment for terrorism.
India has a long sea border of more than seven thousand kilometers prone to pirating and smuggling. During the 26/11 Mumbai attacks, terrorists had used sea routes to enter the country.
Terrorism has no religion Another troubling trend is that the so-called war on terror is seen as a war against Islam. This is irrational and dreadful for Muslims, as they now face religious discrimination and are socially disadvantaged. The Koran clearly says, ‘let there be no compulsion in religion’. Nothing could be more explicit than this. So, the entire mythology of the spread of Islam through the sword is unjustified. There is no sanctity of the Koran to spread the faith with the sword. If it was about religion, Christchurch would not have happened. Brenton Tarrant was a white supremacist and part of the alt-right. The dark face of terrorism neither has religion nor nationality. The religious interpretation is idiosyncratic. There are other political and social factors. These things are complex and this is where nuance is necessary.
Impact of terrorism
According to ourworldindata.org , over the past decade, terrorists killed an average of 21,000 people worldwide each year. Terrorism accounted for 0.05% of global deaths in 2017.
Schools have been bombed and burned in Gaza, Syria, Somalia, Nigeria, and elsewhere across the world in the last decade. Teachers were killed, and students were recruited as child soldiers.
Foreign investment
Terrorism affects FDI in many ways. Terrorism leads to insecurity and uncertainty in the country. This causes a lack of trust in foreign investors, forcing them to divert their resources from the host country to other, peaceful countries. Costly security measures decrease the returns on FDI. Terrorism also harms local infrastructure, such as roads, bridges, and communications. It prohibits foreign investment by raising the costs of doing business.
Domestic investment
Terrorism also reduces domestic investment as it becomes difficult for domestic investors to invest in a panic-ridden environment. In addition, public investment is also severely damaged as government projects such as roads, highways, canals, dams, bridges, highways, hospitals, and school construction also brought to an end in the presence of terrorist activities.
Tourists usually avoid visiting the city that has been attacked. For tourism-dependent economies, terrorist attacks can hit even harder.
A recent example is Sri Lanka (Easter bombing). Sri Lanka has made significant progress thanks to a tourism boom post 25-year civil war ended. However, the Easter bombing changed the picture. Among those killed in bombings were 45 foreigners. Tourists fled: the number of arrivals dropped. For several days following the attack, many businesses remained closed. A huge share of jobs was lost in the tourism sector.
Similarly, in Kashmir, tourism is the biggest source of livelihood in the state. But, terrorism ruined the tourism industry. The owners of hotels, guest houses, and houseboats, whose business is entirely dependent on the influx of tourists, suffer huge economic losses. By threatening visitors from visiting Kashmir, the terrorists are strangling a major source of jobs and making those who have become unemployed potential recruits to Pakistan-inspired separatism by violence.
Government spending
Terrorist attacks also increase defense and security spending and this reduces economic growth. If the cost of terror decreases, more money could be allocated to spending on infrastructure and that would lead to higher growth.
Steps already taken to combat and end terrorism
India has already achieved progress on various institutional and legislative mechanisms aimed at combating terrorism.
After the 26/11 Mumbai attacks, a national investigation agency also known as the NIA was formed to counter terrorist acts in the future.
The National Intelligence Grid also known as NATGRID is an integrated intelligence grid. It will link the databases of several departments and ministries of the government of India. NATGRID aims to gather detailed intelligence patterns that intelligence agencies can readily access. It collects and collates a variety of data from government databases such as tax and bank account information, credit card activity, visa and immigration records, and itineraries of train and air travel.
India has a multi-agency center also known as MAC for counterterrorism with a mandate of sharing terrorism-related intelligence inputs on a day-to-day basis.
Various legal frameworks are created such as the Terrorist And Disruptive Activities Act and the Prevention of Terrorism Act of 2002, along with the Unlawful Activities Prevention Act and the NIA Act of 2008.
How to overcome terrorism?
From the understanding of the nature of international terrorism that we are facing today, it is clear that a long term strategy is required to fight against terrorism. It has to be comprehensive on all fronts.
Core strategy
The strategy needs to be evolved to protect core values. These core values are to protect the sovereignty and territorial integrity, to consolidate as a secular, federal, democratic state with freedom of speech, equality, and justice, to promote socio-economic growth and development.
Socio-economic dimension
Socially, India must continue to promote liberal and secular polity by media, intelligentsia, and religious institutions.
There is a need to develop all regions more evenly throughout the country with greater development effort in the remote weaker sections of the society. Economic empowerment of the poor especially in areas like J&K and the Naxal belts would automatically drive out the extremist elements and their ideologies would be abandoned.
Education reforms
Education is the antidote against terrorism. Education provides the confidence and analytical skills youngsters need to condemn hatred and violence. We must teach values of peace, non-violence, fraternity. So, no one will be able to brainwash young minds.
Also, there is a tendency to brand students from madrasas as terrorists. This further, alienate Indian madrasas. There is an urgent need to de-stigmatize madrasas as a breeding ground for terrorism and address the outdated education system in the Madrasahs by modernization.
Upgrading communication systems
There is also a need to develop our communication networks so that television and telecommunication can spread to remote and border areas which are currently under the constant reach of Pakistani propaganda.
Military strategy
India should clearly spell out a counterterrorism doctrine. This should address the causes and not the symptoms alone. The aim of military operations is to create a secure and suitable environment so that social, economic, and political issues can be addressed effectively.
Effective border surveillance and management is also required to check infiltration. This should be achieved through technical means of surveillance backed by highly mobile specialized forces the other than the present system which is manpower intensive.
Foreign-based terrorists must be targeted at the bases, training camps, and sanctuaries to end the surrogate terrorism or the proxy wars.
India must leverage its improved ties with the first world countries. Platforms of multinational bodies like the UN, G20, BRICS, and the Shanghai Cooperation Organization should be utilized to further India’s agenda of anti-terrorism.
International cooperation
International terrorism can not be confronted alone successfully as has been our experience so far. All nations must join hands to combat it. Countries have to cooperate by intelligence exchange, joint operations, and investigations.
Pakistan sponsored proxy war
It must be further exposed and international pressure should be applied. We have to convey more vigorously the justness of our cause and Pakistan’s support for terrorism by both state and non-state actors, as well as trying to isolate Pakistan within the international community. A strong message must be conveyed to Pakistan.
Lessons from other nations
We have to learn from the experiences of other nations. However, at the same time, we need to realize clearly that a situation is particular to us and there are no direct lessons to learn except a revaluation of our own experience.
A strategy must be pragmatic and cannot be similar to the US model of global capacity or the Israeli strategy of massive and immediate retaliation, as the respective environment and capabilities are different.
Dr. Salman Farsi was said to have been involved in the Malegaon blasts. He was acquitted eight years later. By this time, he had nothing to fall back upon. He is a qualified Unani doctor. But, he even took to rearing goats to meet his needs. These outcomes can be easily avoided. The media, instead of calling each accused a terrorist, may perhaps restrict itself to calling them only an accused, and avoid displaying their photographs as if they have been convicted.
Other steps
There is a need to adopt proactive policies to confront the terrorists at the roots of the ideology of fundamentalists social evils and sources of terror funding like narcotics and drug trade.
India also needs to strengthen its anti-terrorism laws. There is a need to modernize and enlarge intelligence networks, State Police and paramilitary forces in training equipment and ethos.
There should be enough preventive measures against nuclear biological and chemical attacks as well as cyber terrorism.
This unconventional war can not be won by conventional methods. It can only be won by showing that our values are stronger, better, fairer, and more humane than the alternative. The values that will rule the future of humanity are those of peace, tolerance, liberty, respect for diversity, and not those of reaction, discord, and hatred.
You can also read-
BIOTERRORISM
Digital Divide In India
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Sign me up for the newsletter!
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- BJPsych Int
- v.15(1); 2018 Feb

Terrorism in Pakistan: the psychosocial context and why it matters
Asad tamizuddin nizami.
1 Assistant Professor, Institute of Psychiatry, World Health Organization Collaborating Centre for Mental Health, Benazir Bhutto Hospital, Rawalpindi Medical College, Rawalpindi, Pakistan; email moc.liamg@imazindasard
Tariq Mahmood Hassan
2 Assistant Professor, Providence Care Mental Health Services, Kingston, Canada
Sadia Yasir
3 Consultant Psychiatrist, Shifa International Hospital, Shifa College of Medicine, Islamabad, Pakistan
Mowaddat Hussain Rana
4 Director General, Centre for Trauma Research and Psychosocial Interventions, National University of Sciences and Technology (NUST), Islamabad, Pakistan
Fareed Aslam Minhas
5 Head Institute of Psychiatry, World Health Organization Collaborating Centre for Mental Health, Benazir Bhutto Hospital, Rawalpindi Medical College, Rawalpindi, Pakistan
Terrorism is often construed as a well-thought-out, extreme form of violence to perceived injustices. The after effects of terrorism are usually reported without understanding the underlying psychological and social determinants of the terrorist act. Since ‘9/11’ Pakistan has been at the epicentre of both terrorism and the war against it. This special paper helps to explain the psychosocial perspective of terrorism in Pakistan that leads to violent radicalisation. It identifies the terrorist acts in the background of Pakistan's history, current geopolitical and social scenario. The findings may also act as a guide on addressing this core issue.
Most nations are unable to reach a consensus on a legally binding definition of ‘terrorism.’ The term seems emotionally charged and, as such, governments have been devising their own definitions. So far the United Nations has been unable to devise an internationally agreed-upon definition of terrorism. Terrorism is suggested to be ‘the use of intimidation or fear for advancement of political objectives’ (Kruglanski & Fishman, 2006 ). Since the ‘9/11’ incident, Muslim countries in particular feel emotionally threatened with the word terrorism and perceive it as synonymous with the acts of terror carried out by so-called Muslim extremist groups. This is further complemented in the media by the unjust linking of such horrendous terror attacks to Islamic Jihad.
Terrorism has brought an enormous burden on South Asian countries through the adverse impacts on their social, economic, political and physical infrastructure. Pakistan has suffered particularly excessively from the social, economic and human costs due to terrorism (Daraz et al , 2012 ). Surprisingly, Pakistan is portrayed as being on the front line in the international war against terrorism and at the same time has been wrongly labelled as a sponsor of international terrorism. Terrorism in Pakistan is a multidimensional phenomenon and, among many precipitating factors, the psychosocial factors play an important role. This paper attempts to address what we believe are significant psychosocial determinants to terrorism in Pakistan.
Historical developments
Pakistan is a Muslim majority nation in South East Asia with India to its east, Iran and Afghanistan to its west, China and the landlocked Asian countries to its north and the Arabian Sea to its south. Pakistan gained independence from British colonial rule in 1947 and is the only Muslim country with nuclear weapons – a nuclear device was detonated in 1998 – and is thus part of the informally named ‘nuclear club.’ Pakistan is a federation of four provinces (Punjab, Sindh, Khyber Pakhtunkhwa (KPK) and Balochistan), a capital territory (Islamabad) and a group of federally administered tribal areas in the north west, along with the disputed area of Azad Jammu and Kashmir.
Pakistan is the world's sixth most populous country with an average population density of 229 people per km 2 (World Bank indicators; http://www.tradingeconomics.com/pakistan/urban-population-growth-annual-percent-wb-data.html ). Since independence in 1947, Pakistan has been challenged not only by the trauma inflicted by its colonial occupiers but also by the mass murder of people migrating to the ‘new’ country. Hundreds of thousands of people were killed, looted, raped or burnt alive. At the same time, the stability of this fledgling country was significantly hampered by the lack of resources. Just a few years later, due to political instability and separatist movements and terrorism, the east wing of the country was separated from Pakistan; this paved the way to the creation of a new country, Bangladesh, in 1971 (Wadhwani, 2011 ).
The Soviet–Afghan war, which began in 1979, provided a breeding ground for terrorism in the region. A fundamental change was witnessed that altered the very character of the existing Pakistani society. Withdrawal of the Soviets revealed a Pakistani society that had been forced into one of violence and weaponisation, plaguing Pakistan with so-called ‘Kalashnikov culture’ and ‘Talibanisation’ (Wadhwani, 2011 ).
Pakistan's social landscape has for the most part been plagued with illiteracy, disease, insecurity and injustice. Since the 9/11 incident, Pakistan has been intricately linked with the many facets of the ‘war on terrorism.’ Some argue that Pakistan is a breeding ground for terrorist outfits, but it is certain that all of this havoc has resulted in the significant loss of innocent lives as well as loss of economic revenue. These fragile conditions provide a fertile ground for terrorism to grow.
Psychological influence
The act of carrying out terrorist activity does not come from a single moment of inspiration but rather from a complex process of cognitive accommodation and assimilation over accumulating steps. It is wrongly reductionist to label the terrorists as mad or psychopaths (Atran, 2003 ; Horgan, 2008 ). Terrorists’ motivation may involve a deep, underlying quest for personal meaning and significance. Several analyses of such motives have appeared in recent years. There are differences in these analyses regarding the type and variety of motivational factors identified as critical to terrorism. Some authors identified a singular motivation as crucial; others listed a ‘cocktail’ of motives (Sageman, 2004 ; Bloom, 2005 ).
The socioeconomic adversity combined with political challenges were bound to have a detrimental impact on the psyche of the average Pakistani. A terrorist adopts a dichotomous way of identifying their victims, the black-and-white thought that ‘I am good’ and ‘you are evil,’ with no intermediary shades of grey. This thinking leaves no doubt in their minds and they find it easier to kill their opponents with little or no sense of remorse or guilt.
The unmanned army drone strikes killed and maimed thousands of innocent civilians in poor and difficult to access regions of Pakistan. This infuriated people, leading them to take up arms against the perceived aggressors. This triggering of the relatives of the deceased to engage in such activity is the culture of revenge in Pakistan, which unfortunately can last for generations.
Self-sacrifice and martyrdom has been explicitly used in almost all religions and is aggressively exploited by terrorist outfits who groom suicide bombers using the ideology of Islamist martyrdom (Atran, 2003 ). Some have argued that suicide bombers may actually be clinically suicidal and attempting to escape personal impasse (Lankford, 2013 ). In grooming young impressionable adolescents, extremist organisations brainwash these adolescents into believing that the ultimate self-sacrifice by suicide bombing will elevate their stature in the eyes of God and send them straight to heaven. This is associated with massive financial compensations to the deceased family. Terrorist organisations in Pakistan, through this process of brainwashing, have been able to convert young impressionable Muslim adolescents into a ‘suicide bomber in six weeks’ (Nizami et al , 2014 ). In the current scenario of the existing war on terror, this complex process of recruiting young adolescents as suicide bombers seems irreversible.
The contribution of the religious schools
In the West, Madrassas (Islamic religious schools) have gained a reputation of being a sinister influence on young impressionable Muslims. These institutions are not completely regulated and can vary from a single room to large institutions offering schooling and boarding to hundreds of students at a time. A survey of just over 50 000 households in Pakistan found that children in Urdu-medium government schools and madrassas were from poorer households than those in English-medium private schools. The primary reason for parents to send their children to madrassas as opposed to mainstream schools was that these institutions provided a good Islamic education. The second most common reason was that the madrassa provided education that is low in cost along with the provision of food and clothing (Cockcroft et al , 2009 ).
Another survey indicated that in Pakistan only a minority of the religious schools promoted an extremist view of Islam (Bano, 2007 ). An interrogation of 79 terrorists involved in anti-Western attacks found that very few had attended a madrassa. This suggests that terrorist groups may selectively recruit better qualified people for technically demanding tasks (Bergen & Pandey, 2006 ). However, the religious seminaries have been implicated as playing the role of recruitment centres for the suicide bombers (Nizami et al , 2014 ).
In an effort to break this incorrect perception the Darul Uloom Deoband, the largest Islamic seminary in the world, hosted an anti-terrorist conference in 2008. This was attended by 6000 Imams declaring that ‘Islam is a religion of mercy for all humanity. Islam sternly condemns all kinds of oppression, violence and terrorism. It has regarded oppression, mischief, rioting and murder among sins and crimes’ (Press Trust of India, 2008 ). However, it is yet to be ascertained how many religious schools in Pakistan adopted this school of thought. With the revolution in the world of information technology, experts agree that the internet played an important role in the radicalisation and self-recruitment process into terrorist groups. Messages and videos on jihadi websites target the ‘soft spots’ of potential recruits and inflame their imagination (Kruglanski & Fishman, 2009 ).
The link between terrorism and mental disorder
With both mental disorder and terrorism in Pakistan being highly prevalent, it would be a fair assumption that the two may have a causal relationship. Walter Laqueur wrote that ‘all terrorists believe in conspiracies by the powerful, hostile forces and suffer from some form of delusion and persecution mania… The element of… madness plays an important role in terrorism’ (Silke, 2003 ).
However, apart from certain pathological cases, a causal connection between an individual's mental disorder and engagement in terrorist activity could not be established (Daraz et al , 2012 ). However, there can be a connection between an individual engaging in terrorist activity and developing a mental disorder as mental disorders worsen in stress, anxiety and depression.
The adverse impacts of terrorism lead the masses towards anomie and create the tendency towards suicide and mental illnesses (Daraz et al , 2012 ). Poor health, depressive symptoms, risky behaviours in young adults, personality variables, social inequalities, criminality, social networks and international foreign policy have all been proposed to be influential drivers for grievances that lead to radicalisation and terrorism (La Free & Ackerman, 2009 ).
It may well be that individuals with mild depression would be a better target for gradual psychological moulding. Female suicide bombers who are predominantly motivated by revenge as opposed to their male counterparts may have some degree of clinical depression (Jacques & Taylor, 2008 ). Personality traits are useless as predictors for understanding why people become terrorists. However, personality traits and environmental conditions are the contributing factors for terrorism (Horgan, 2008 ). There are protective and modifiable risk factors early on the path towards radicalisation. The benefits of early intervention have far reaching implications for preventing significant depressive symptoms, promoting wellbeing and perhaps social capital (Bhui et al , 2014 ).
By understanding, appreciating and addressing the psychosocial factors contributing to terrorism in Pakistan, one may find long-lasting solutions to the fall out on Pakistan's war against terror. This war has led to a loss of innocent human lives, compounded by the deep psychological scars for survivors which will undoubtedly persist for generations to come. An ongoing, concerted effort to gain peace and security in the region is essential and is the only way to counteract the revenge attacks and further brainwashing of young impressionable youths. These psychological determinants, however, are markedly different than terrorist activities in Western countries, where it seems that a different set of psychological rules apply.
- Atran S. (2003) Genesis of suicide terrorism . Science , 299 , 1534–1539. [ PubMed ] [ Google Scholar ]
- Bano M. (2007) Beyond politics: the reality of a deobandi madrasa in Pakistan . Islamic studies , 18 , 43–68. [ Google Scholar ]
- Bergen P. & Pandey S. (2006) The madrassa scapegoat . Washington Quarterly , 29 , 115–125. [ Google Scholar ]
- Bhui K., Everitt B. & Jones E. (2014) Might depression, psychosocial adversity, and limited social assets explain vulnerability to and resistance against violent radicalization ? PLoS ONE , 9 ( 9 ), e105918 (doi: 10.1371/journal.pone.0105918 ). [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Bloom M. (2005) Dying to Kill. The Allure of Suicide Terror . Columbia University Press. [ Google Scholar ]
- Cockcroft A., Andersson N., Milne D., et al. (2009) Challenging the myths about madaris in Pakistan: a national household survey of enrolment and reasons for choosing religious schools . International Journal of Educational Development , 29 , 342–349. [ Google Scholar ]
- Daraz U., Naz A. & Khan W. (2012) Sociological analysis of terrorism in Pakistan . Academic Research International , 3 ( 1 ). [ Google Scholar ]
- Horgan J. (2008) From profiles to pathways and roots to routes: perspectives from psychology on radicalization into terrorism . The Annals of the American Academy of Political and Social Science , 618 ( 1 ), 80–94. [ Google Scholar ]
- Jacques K. & Taylor P. J. (2008) Male and female suicide bombers: different sexes, different reasons? Terrorism , 31 , 304–326. [ Google Scholar ]
- Kruglanski A. W. & Fishman S. (2006) The psychology of terrorism: “syndrome” versus “tool” perspectives . Terrorism and Political Violence , 18 , 193–215. [ Google Scholar ]
- Kruglanski A. W. & Fishman S. (2009) Psychological factors in terrorism and counterterrorism: individual, group, and organizational levels of analysis . Social Issues and Policy Review , 3 , 1–44. [ Google Scholar ]
- La Free G. & Ackerman G. (2009) The empirical study of terrorism: social and legal research . Annual Review of Law and Social Science , 5 , 347–374. [ Google Scholar ]
- Lankford A. (2013) The Myth of Martyrdom: What Really Drives Suicide Bomber, Rampage Shooters, and Other Self-Destructive Killers (1st edn). Palgrave Macmillan. [ PubMed ] [ Google Scholar ]
- Nizami A. T., Rana M. H., Hassan T. M., et al. (2014) Terrorism in Pakistan: a behavioral sciences perspective . Behavioral Sciences & The Law , 32 , 335–46. [ PubMed ] [ Google Scholar ]
- Press Trust of India (2008) Muslim clerics declare terror “un-Islamic.” The Times of India , 25 Feb. Available at http://timesofindia.indiatimes.com/india/Muslim-clerics-declare-terror-un-Islamic/articleshow/2813375.cms (accessed 6 July 2015).
- Sageman M. (2004) Understanding terrorist networks . University of Pennsylvania Press. [ Google Scholar ]
- Silke A. (2003) Becoming a terrorist In Terrorists, Victims and Society: Psychological Perspectives on Terrorism and its Consequences (ed. Silke A.), John Wiley & Sons. [ Google Scholar ]
- Wadhwani R. (2011) Essay On Terrorism In Pakistan: Its Causes, Impacts And Remedies. Civil Service Pakistan Forum 28 September 2011. Available at: http://www.cssforum.com.pk/css-compulsory-subjects/essay/essays/54746-essay-terrorism-pakistan-its-causes-impacts-remedies.html .
Home / Essay Samples / Social Issues / Terrorism
Terrorism Essay Examples
Terrorism is a topic that encompasses a wide range of issues, including its causes, effects, and strategies to combat it. Essays on this subject can be informative, persuasive, argumentative or a combination of these types.
These essays demand thorough research and critical thinking, as they explore complex and often controversial issues. The goal is not only to present facts but also to make a compelling argument, drawing on evidence and logical reasoning
The structure of an essay on terrorism generally follows the traditional essay format, which includes an introduction, body paragraphs, and a conclusion. However, the specific content within these sections may vary depending on the type of essay (e.g., informative, argumentative, persuasive, etc.).
The Importance of Essays About Terrorism
Essays about terrorism play a crucial role in understanding one of the most pressing global challenges of our time. The purpose of such essays is to analyze the motivations, methods, impacts, and countermeasures related to acts of terrorism. By examining the complexities of terrorism, these essays contribute to informed discussions, policy decisions, and efforts to prevent and counteract terrorism.
One of the primary goals of essays about terrorism is to understand the motivations that drive individuals and groups to engage in acts of terrorism. These essays explore factors such as political, religious, ideological, and social grievances that may contribute to radicalization.
The Events at Amritsar as the Catalysator the Movement for Freedom of India
Gandhi advocated protest without the use of violent acts because he believed in the religious concept of ‘Ahimsa’, meaning ‘doing no harm’. Gandhi believed that protesting peacefully would assist the Indians in their fight for freedom and independence from the British simply by showing colonizers...
Amritsar Massacre: Response to the Gandhi and Indian Nationalist Movement
However, the situation in India is still not convincing enough to justify Dyer’s actions. The prevailing ideas of paternalism and racial attitudes in British India shaped Dyer’s actions should be self-evident, which could be said about the policies and practices within the empire and therefore...
The Taliban and Its Impact on the War
Parachinar is the capital of Kurram agency which boarders with three different Afghan provinces, namely ningrahar to its north, paktia to its west and khost to south west.it is the nearest city of Pakistan to Kabul. It also borders with north Waziristan, Orakzai and Khyber...
Genocide, Holocaust, Or Dehumanization: Causes and Consequences
Genocide, Holocaust, or Dehumanization are all methods that are deliberately aimed to erase a mass number of people on the basis of their caste, color, race, or Religion, usually carried out by a superior and stronger group of people. The method of genocide was popular...
Taliban and Evolution of Terrorist Groups in Afghanistan
To analysis the eradication of regional terrorism in Afghanistan, we must look at The evolution of terrorist groups in Afghanistan. When the Soviet Union invaded at the request of Central government of Afghanistan which was called by Mujahidin Soviet designated government, in that war which...
Operation Anaconda: Mission to Destroy the Taliban
Operation Anaconda was an operation that took place in the Shahi-Kot Valley and Arma Mountains of Afghanistan from 2 March 2002 through 18 March 2002. It was a joint mission between U.S. military branches, six other nations, and Afghans led by Major General Franklin L....
Tajfel’s Social Identity Theory Explaining the Discrimination Malala Yousafzai Faced by the Taliban
The legendary story of Malala of Pakistan is one of the most famous and well-known stories in history. The attempted murder of Malala Yousafzai by the Taliban for speaking out for girls' education and peace can be viewed as an isolated act by religious extremists....
Suicide Bombing as an Aspects of Terrorism
Until the 1990s, terrorism tended to be relegated to a secondary position in the international politics due to the relative irrelevance to the world affairs. However, as the global tension escalated to a significant extent with the September 11 terrorist attacks, the significance of terrorism...
The End of Torure: Why the Guantanamo Bay Should Be Closed
There is always somebody with more information, money, and power. Usually it is the government, for various reasons, that will not give out information regarding torture. Therefore, whatever we see on TV, read in books, hear from other and sometimes experience ourselves will be the...
Change of the Concept of Sovereignty: 9/11 Attack, War on Terror, and Guantanamo Bay
Throughout history, there have been episodes with such an impactful magnitude that they have been able to change the course of history forever. For example, the assasination of Archduke Ferdinand II in 1914 was the incident which led to the outbreak of the First World...
Trying to find an excellent essay sample but no results?
Don’t waste your time and get a professional writer to help!
- War on Terror
- Twin Towers
- Suicide Bombing
- Osama Bin Laden
- Animal Rights
- Immigration
- Overpopulation
- Women's Rights
samplius.com uses cookies to offer you the best service possible.By continuing we’ll assume you board with our cookie policy .--> -->