You are using an outdated browser. Please upgrade your browser to improve your experience.

Suggested Results
Antes de cambiar....
Esta página no está disponible en español
¿Le gustaría continuar en la página de inicio de Brennan Center en español?
al Brennan Center en inglés
al Brennan Center en español
Informed citizens are our democracy’s best defense.
We respect your privacy .
- Research & Reports
U.S. Crime Rates and Trends — Analysis of FBI Crime Statistics
The FBI’s latest report on crime trends includes 2022 data for national, regional, and local levels.
- Accurate Crime Data
This page lists key statistics from the latest annual crime report published by the Federal Bureau of Investigation. The report, published on October 16, 2023, includes data on crime at the national, state, and local levels for 2022 along with comparisons against previous years.
Historical Trends in Crime Rates, 1990–2022
Recent changes in crime rates by geography, 2020–2022, recent changes in crime rates in selected major cities, 2020–2022.
Methodology and Limitations
Except where indicated, all data above was drawn from Crime in the United States Annual Reports , available on the FBI’s website under “Documents and Downloads.” Terms used in the tables above, such as regional groupings, are drawn from FBI reports.
FBI crime data from 2021 contained significant gaps and was based largely on estimates due to a transition in the way agencies report crime to the bureau. The tables on this page exclude 2021 data accordingly, instead making a direct comparison between 2022 and 2020, which is the most recent prior year in which a comparable number of agencies participated. This year’s report includes data accepted through the FBI’s “legacy” reporting system , significantly improving the reliability of its estimates.
Related Resources

Myths and Realities: Understanding Recent Trends in Violent Crime
The recent rise in crime is extraordinarily complex. Policymakers and the public should not jump to conclusions or expect easy answers.
Understanding the FBI’s 2021 Crime Data

Why Inclusive Criminal Justice Research Matters
Engaging with impacted community leaders can help contextualize data and drive solutions.

The Hidden Toll of New York City’s Misdemeanor System
Caseloads are shrinking but remain a burden on communities and government resources.
Myth vs. Reality: Trends in Retail Theft
Fact-checking trump’s speech on crime and immigrants, trump misleads about crime and public safety, again, criminal justice reforms aren’t driving rising crime, analyzing the fbi’s national crime data on 2022 — with an eye toward 2023 trends, informed citizens are democracy’s best defense.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.

Find crime statistics
Federal, state, and local law enforcement agencies collect data about crime. Find crime statistics around the U.S. using the FBI’s Crime Data Explorer.
Use the Crime Data Explorer to find statistics about different types of crime nationally or in your state, county, or town.
LAST UPDATED: February 1, 2024
Have a question?
Ask a real person any government-related question for free. They will get you the answer or let you know where to find it.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- SAGE - PMC COVID-19 Collection

Beyond Policing: The Problem of Crime in America
José luis morín.
1 John Jay College of Criminal Justice, CUNY, New York City, NY, USA

Photo by Francois Polito. Sculpture by Carl Fredrik Reuterswärd.
In 2020, the United States experienced the sharpest one-year rise in homicides on record. 1 In 2021, hate crimes also surged to their highest level in twelve years, with the largest increases being anti-Black crimes followed by anti-Asian crimes. 2 Pundits and politicians on the right have been quick to cite bail reform and “defunding” of police as reasons for the national rise in crime. Yet, the best available evidence points to other causes—among them, the massive social and economic dislocation resulting from the Covid-19 pandemic and the nationwide proliferation of guns along with the spread of racial and ethnic hatred and the violence it has roused.
While violent crime today [is] much lower . . . than in 1991, when [it] reached its highest point in recent history, public anxiety about crime is high.
While violent crime today registers at much lower levels than in 1991, when violent crime reached its highest point in recent history, 3 public anxiety about crime is high. Yet, more police and a redoubling of get-tough measures, however alluring, have not proven to be as effective as they appear. An examination of what is not driving the recent spike in crime as well as what probably is driving it—and revisiting the role that policing and the criminal justice system has played in U.S. society in reproducing racial, social, and economic inequalities—may move us closer to arriving at effective public safety solutions.
Starting with What Is Not: Bail Reform and Defunding the Police
The purpose of bail is to “provide reasonable assurance of court appearance or public safety,” 4 but, a 2022 briefing report by the U.S. Commission on Civil Rights suggests that the current cash bail system is also associated with producing deleterious racial disparities and economic inequities that undermine the presumption of innocence and worsen public safety. 5 The Commission report points out that low-income persons and people of color are disproportionately detained as a result of their inability to make bail, and persons of color are more often assigned higher bail amounts and considered more “dangerous” than whites. 6 To persons jailed simply because they could not afford bail, jail can result in severe trauma: loss of employment, housing, custody of a child; and economic hardship. 7 The think tank, Prison Policy Initiative, issued a report in 2016 documenting that cash bail “perpetuates an endless cycle of poverty and jail time.” 8 Nevertheless, with crime rates on the rise in 2020, bail reform became a political cudgel, and New York State’s law became a focal point of harsh condemnation from the GOP and conservative media outlets nationwide. But analyses of bail reform show no clear link between bail reform and spikes in crime. 9
To reduce unnecessary pretrial detention and ameliorate the harms associated with cash bail, New York State passed a bail reform law in 2019, ending cash bail for certain misdemeanors and most non-violent felony cases. Changes to the original law in 2020 and 2022 gave judges the ability to impose cash bail in more situations. 10 To date, research on the law shows no significant impact on crime rates. One study by the Times Union of Albany found that, of almost 100,000 cases, only a minimal number (2 percent) of individuals faced rearrest for a violent felony. As a result, as many as 80,000 people may have avoided incarceration while posing no documented threat to public safety. 11 And, looking at the national picture, the Brennan Center for Justice, a progressive law and public policy institute, points out that crime surged nationally, even in states that did not enact bail reform. 12
Another report—this one from the Office of New York City Comptroller Brad Lander—covered three calendar years and revealed that “pretrial rearrest rates remained nearly identical pre- and post-bail reform.” 13 The Comptroller’s report also warned that rollbacks to New York State’s bail reforms would “syphon money” from low-income communities. Indeed, families unable to make cash bail often turn to for-profit bail bond companies that require a non-refundable premium of 10 to 15 percent, even if no wrongdoing is found. Some form of collateral—such as a car or house—is also required. As the bail bond industry has become increasingly lucrative, growing numbers of indigent persons and their families face steep financial risks. 14 Critics of bail reform, by contrast, have produced little to no empirical evidence to support their position. Outspoken in its condemnation of bail reform, the New York Police Department has fallen short in backing up its assertions that bail reform was causing increases in gun violence. In 2021, when challenged by Albany legislators, NYPD Commissioner Dermot Shea, failed to provide any hard data to support his contention that bail reform is driving up crime. In the end, he was forced to retract his statements. 15
The term “defunding the police” has been variously understood. For the purpose of this discussion, I define the term not as a movement to eliminate police budgets, but as a call to lessen encounters with police by shifting funds away from aggressive and militarized forms of policing toward social services—such as mental health, addiction, education, and housing. In its most literal meaning, “defunding the police” is frequently cited as a reason for the surge in crime. As with bail, hard evidence to support this allegation has not materialized. Of twelve Democratic-led cities (including Austin, Louisville, Rochester, and St. Paul) cited by Republicans as examples of where crime purportedly rose due to police defunding, criminal justice scholars find no discernible link between defunding and crime. In fact, not all twelve cities defunded police; most did not substantially reduce police funding, and some actually increased their police budgets. 16
Funding quality educational programs, by comparison, has proven to be successful in diminishing crime. 17 For example, two studies—one in North Carolina and one in Michigan—showed that increased expenditures on primary schools helped to reduce adult crime by improving student academic success, which in turn provides a greater opportunity for socio-economic mobility. 18
Examining What Is: Covid-19, Guns, and the Rise in Hate
Prior to the Covid-19 pandemic, crime rates were relatively low. As the graph in Figure 1 demonstrates, the rate of violent crime offenses declined from a peak in 1991 of 758.2 per year to 398.5 per year in 2020. 19 The rate of homicide over the same period also dropped significantly, from its highest level in 1991 compared with 2020. 20 But the crime rate shows an uptick with the onset of the Covid-19 pandemic in 2020.

Rate of violent crime offenses by population in the United States: 1985-2020.
Source: Federal Bureau of Investigation, “Trend of Violent Crime from 1985 to 2020,” Crime Data Explorer, accessed September 19, 2022, https://crime-data-explorer.fr.cloud.gov/pages/explorer/crime/crime-trend .
Note. Rate per 100,000 people, by year.
The pandemic is widely understood as the cause of immense social and economic dislocation, disproportionately disadvantaging children, communities of color, immigrants, LGBTQIA+ (lesbian, gay, bisexual, transgender, queer or questioning, intersex, asexual, and more) youth, and persons with disabilities. 21 The pandemic also exposed and aggravated deeply entrenched inequities in health care, poverty, education, housing, and racial segregation. Its impact on mental health and psychosocial well-being, substance abuse, and domestic violence has become a focus of attention in relation to the rise in crime. All these factors are related to the rise in crime.
As gun violence became a major driver of crime nationwide, hate crimes also spiked. During the pandemic, reports of hate crimes reached a twelve-year high.
The proliferation of guns and gun violence nationwide appears to have contributed greatly to the spike in homicides. Sharp increases in gun purchases coincided with the start of the pandemic in 2020 and continued well into 2021. 22 The increased supply of guns as well as the types of guns—high-powered semi-automatic weapons, for instance—has been linked to the surge in gun violence. 23 Criminologists Philip J. Cook and Jens Ludwig deem gun violence and the fear of gun violence as devastating to the lives of children and families around the country, most especially in low-income neighborhoods and communities of color. In their estimation, public safety begins with addressing the needs of communities most vulnerable to gun violence, and that includes investments in social policies, such as summer jobs for teens, cleaning vacant lots, and spending more on social programs—all of which have been shown to reduce homicide rates. 24
As gun violence became a major driver of crime nationwide, hate crimes also spiked. During the pandemic, reports of hate crimes reached a twelve-year high (see Figure 2 ). 25 While anti-Black incidents topped the list of hate crimes based on race, people of Asian descent experienced a steep rise in anti-Asian violence and crime, with a 169 percent increase in reports of anti-Asian hate crimes in fifteen of America’s largest cities and counties in the first quarter of 2021 when compared with the first quarter of 2020. 26

Hate crimes in the United States: 1995-2020.
Source: Hate Crime in the United States Incident Analysis, 1995 to 2020,” Crime Data Explorer, accessed October 6, 2022, https://crime-data-explorer.fr.cloud.gov/pages/explorer/crime/hate-crime .
. . . [I]t is no surprise that the earliest form of policing in the United States was the slave patrol, established in 1704.
Even before the pandemic, former President Donald Trump’s xenophobic, racially inflammatory rhetoric and policies were understood as green-lighting racial and ethnic violence. But unfortunately, this is not unique in our history. Hate groups of different types—white nationalists, neo-Nazis, and anti-government paramilitary organizations—historically have played a major role in the spread of hatred and violence.
Policing: The Historical Context
The history of policing in the United States may help us determine the best policies and practices to advance public safety without subjecting communities to abusive police practices.
The institution of slavery—and its continuance—was integral to the founding of the nation. So, it is no surprise that the earliest form of policing in the United States was the slave patrol, established in 1704. 27 The patrols were designed to maintain the system of slave labor and to capture runaway slaves. Patrollers, often armed, used violence to terrorize slaves and deter rebellions. In 1787, the apprehension of slaves was codified in the U.S. Constitution in Article IV, Section 2, commonly referred to as the “Fugitive Slave Clause.” The intent of the clause, which passed unanimously, was “to require fugitive slaves and servants to be delivered up like criminals.” 28 The clause was nullified by passage of the Thirteenth Amendment in 1865. Slave patrols were also disbanded after the Civil War, only to be replaced by other forms of policing Black lives. These included the Ku Klux Klan and the institution of Jim Crow, which was maintained in Southern states by police who often used intimidation and terror to maintain a brutally oppressive system. 29
By the 1990s, the acquisition of military equipment by police forces across the country became ubiquitous . . .
Over time, police and other law enforcement agencies helped preserve and reproduce race and class inequality, as in the 1918 massacre of fifteen Mexican men in Porvenir, Texas and the 1921 Tulsa, Oklahoma massacre that resulted in destruction of a prosperous Black neighborhood. 30 Business and economic elites—such as Andrew Carnegie and Henry Clay Frick—also relied on police or private law enforcement agencies to employ deadly force against workers and union organizers. The massacre of strikers at the Homestead Steelworks in 1882 is one example; the 1897 massacre of coal miners in Lattimer, Pennsylvania is another. 31
The militarization of policing arose in the 1960s, amid cries for a “war on crime” and a “war on drugs.” In Los Angeles, Daryl F. Gates, then head of the Los Angeles Police Department, spearheaded an effort to outfit local police departments with military-grade armaments and equipment to handle emergencies, such as hostage situations and sniper shootings. By the 1990s, the acquisition of military equipment by police forces across the country became ubiquitous through a federal program that encouraged the militarization of law enforcement. 32 But, as a report from the American Civil Liberties Union documents, militarization, too, frequently came at the expense of individual civil liberties, particularly in Black and Latinx communities. 33
Police practices—including chokeholds, stop and frisks, and “broken windows” tactics—have come into question as the victims of police brutality have come into sharp focus. From George Floyd and Breonna Taylor to Eric Garner and Freddy Gray, their names are now familiar and—for some—synonymous with policing in the United States. Yet, despite the bright light shone on these cases, fatal police shootings continue to rise. According to the Washington Post , “2021 was the deadliest year for police shootings” since the newspaper began tracking such incidents in 2015. 34
Centering Communities to Advance Public Safety
Following incidents of excessive police force, municipalities commonly opt for police retraining. However, as some analysts observe, retraining is too often inadequate or ineffective in resolving or mitigating a recurrence of police misconduct. 35 Similarly, while there is merit to hiring police officers who resemble members of the communities they serve, a diverse police force does not necessarily decrease incidents of brutality against persons of color. Regrettably, research shows that a Black officer may be more inclined to use force in encounters with Black community members than white officers. 36 These officers often face the dilemma of how to fit into a police culture that commonly takes an “us against them” approach when patrolling communities. Aggressive behavior can be one way to prove that they belong. 37
Ensuring public safety requires attention to non-violent as well as violent situations. In the context of rising crime, expectations that police officers can resolve a wide array of concerns are high. Police are often called to aid unhoused people, assist individuals experiencing emotional difficulties, or settle domestic disputes. The police are not trained to handle such matters. Social workers or other trained professionals are much better equipped to deal with problems of this nature.
National data on homicide “clearance rates”—the rate at which homicide cases are resolved—also raise questions about the effectiveness of policing. In 2020, the clearance rate was just under 50 percent, representing a historic low and “a long, steady drop since the early 1980s, when police cleared about 70 percent of all homicides.” 38 The pandemic and the spike in violent crimes may help to explain the fall in clearance rates, but the data still beg the question of whether policing itself is sufficiently effective in meeting the public safety needs of contemporary society.
In determining the best approaches moving forward, the intractability of problems related to policing cannot be ignored. Policing remains a leading cause of death for young men in the United States. 39 People of color are most vulnerable, with Black men facing a one in one thousand risk of being killed by police. As we have seen, violent encounters with the police have profound effects on whole communities and neighborhoods, affecting the health and the life chances of individuals in those communities.
Community concerns about crime are real, especially in the most vulnerable communities of color. But the alternative of aggressive policing and mass incarceration has resulted in tremendous harm and cannot be the ultimate solution.
The high rate of recidivism—the rate at which persons released from prison are rearrested—does not point to a system that works well. The most recent Bureau of Justice Statistics covering a ten-year period (2008-2018) shows that “about 66 percent of prisoners released across 24 states in 2008 were rearrested within three years, and 82 percent were arrested within ten years.” 40 Recidivism rates this high should call into question the adequacy of the criminal justice system. It should also raise the issue of whether a system, focused on retribution rather than rehabilitation and public health, is actually serving the cause of public safety. These questions have found resonance with advocates of prison abolition. These abolitionists include scholars Angela Davis, Gina Dent, Ruth Wilson Gilmore, and Alex Vitale. In their view, the current structure of policing and incarceration is profoundly connected to systems of oppression. What is required, they believe, is a system that operates within a social-justice framework—one that substantively engages communities in maintaining their own safety. Such a system, they believe, would reaffirm the values of self-determination and community empowerment. 41 Rather than simply replicating punitive approaches that disproportionally and discriminatorily harm communities of color, abolitionists look to broader social solutions to the problem of crime—remedial measures such as restitution, reconciliation, rehabilitation, and restorative justice.
While a complete transformation of policing and the criminal justice system may not be on the immediate horizon, a variety of initiatives in recent years have sought to address the basic human needs of communities while minimizing negative interactions with police. In a 2021 experiment in Brooklyn, for example, the Brownsville Safety Alliance—a community-based organization—arranged for precinct police to disengage from their usual assignments in a two-block area for five days. In their place, trained violence interrupters and crisis management groups were charged with securing public safety. Although limited in duration, this pilot program has been praised by New York City officials as well as members of the community as “a model for the future.” 42 A range of other crime-reduction strategies that do not involve the deployment of police have also produced promising results. These include improvements in street lighting, clean-up of empty lots, provision of quality mental health and drug treatment services, and expansion of Medicaid services. 43
Community concerns about crime are real, especially in the most vulnerable communities of color. But the alternative of aggressive policing and mass incarceration has resulted in tremendous harm and cannot be the ultimate solution. The best, most promising option is to center communities and underlying social and economic inequality as the means to advance public safety.
Author Biography
José Luis Morín is a professor at John Jay College of Criminal Justice, City University of New York.
1 Jeff Asher, “Murder Rose by almost 30% in 2020: It’s Rising at a Slower Rate in 2021,” New York Times , September 22, 2021, updated November 15, 2021, available at https://www.nytimes.com/2021/09/22/upshot/murder-rise-2020.html .
2 Federal Bureau of Investigation, “FBI Releases 2020 Hate Crime Statistics,” August 30, 2021, available at https://www.fbi.gov/news/press-releases/press-releases/fbi-releases-2020-hate-crime-statistics ; See also, Christina Carrega and Priya Krishnakumar, “Hate Crime Reports in US Surge to the Highest Level in 12 Years, FBI Says,” CNN , October 26, 2021, available at https://www.cnn.com/2021/08/30/us/fbi-report-hate-crimes-rose-2020/index.html .
3 Federal Bureau of Investigation, “Trend of Violent Crime from 1985 to 2020,” Crime Data Explorer, available at https://crime-data-explorer.fr.cloud.gov/pages/explorer/crime/crime-trend .
4 Timothy Schnacke, “Fundamentals of Bail: A Resource Guide for Pretrial Practitioners and a Framework for American Pretrial Reform,” National Institute of Corrections, September 2, 2014, available at https://s3.amazonaws.com/static.nicic.gov/Library/028360.pdf .
5 U.S. Commission on Civil Rights, “Civil Rights Implications of Cash Bail,” Briefing Report, Washington, DC, available at https://www.usccr.gov/reports/2021/civil-rights-implications-cash-bail .
6 U.S. Commission on Civil Rights, 10.
7 Adureh Onyekwere, “How Cash Bail Works,” Brennan Center for Justice at NYU Law, December 10, 2019, updated February 24, 2021, available at https://www.brennancenter.org/our-work/research-reports/how-cash-bail-works#:~:text=Cash%20bail%20is%20used%20as,is%20forfeited%20to%20the%20government ; See also, U.S. Commission on Civil Rights, 6-8.
8 Bernadette Rabuy and Daniel Kopf, “Detaining the Poor: How Money Bail Perpetuates an Endless Cycle of Poverty and Jail Time,” Prison Policy Initiative , May 10, 2016, available at https://www.prisonpolicy.org/reports/DetainingThePoor.pdf .
9 Ames Grawert and Noah Kim, “The Facts on Bail Reform and Crime Rates in New York State,” Brennan Center for Justice at NYU Law, March 22, 2022, available at https://www.brennancenter.org/our-work/research-reports/facts-bail-reform-and-crime-rates-new-york-state .
10 Taryn A. Merkl, “New York’s Latest Bail Law Changes Explained,” Brennan Center for Justice at NYU Law, April 16, 2020, available at https://www.brennancenter.org/our-work/analysis-opinion/new-yorks-latest-bail-law-changes-explained ; See also, Jon Campbell, “NY Lawmakers Pass $220B Budget that Changes Bail Reform, Approves Buffalo Bills Stadium Funding,” Gothamist, April 9, 2022, available at https://gothamist.com/news/ny-lawmakers-pass-220b-budget-that-changes-bail-reform-approves-buffalo-bills-stadium-funding?utm_source=sfmc&utm_medium=nypr-email&utm_campaign=Gothamist%20Daily%20Newsletter&utm_term=https%3A%2F%2Fgothamist.com%2Fnews%2Fny-lawmakers-pass-220b-budget-that-changes-bail-reform-approves-buffalo-bills-stadium-funding&utm_id=88591&sfmc_id=2849872&utm_content=202249 .
11 Grawert and Kim, “Bail Reform and Crime.”
12 Grawert and Kim, “Bail Reform and Crime.”
13 Office of New York City Comptroller Brad Lander, “NYC Bail Trends Since 2019,” available at https://comptroller.nyc.gov/reports/nyc-bail-trends-since-2019/ .
14 Gillian B. White, “Who Really Makes Money Off of Bail Bonds?” The Atlantic , May 12, 2017, available at https://www.theatlantic.com/business/archive/2017/05/bail-bonds/526542/ ; See also, Onyekwere, “How Cash Bail Works”; Rabuy and Kopf, “Detaining the Poor.”
15 “During Questioning in Albany, NYPD Commissioner Shea Backtracks on Bail Reform Law as Big Reason for Gun Violence,” CBS New York , October 14, 2021, available at https://www.cbsnews.com/newyork/news/bail-reform-nypd-commissioner-dermot-shea-assembly-hearing/ .
16 Daniel Funke, “Fact Check: No Evidence Defunding Police to Blame for Homicide Increases, Experts Say,” USA TODAY , January 28, 2022, available at https://www.usatoday.com/story/news/factcheck/2022/01/28/fact-check-police-funding-not-linked-homicide-spikes-experts-say/9054639002/ .
17 See, for example, Brian Bell, Rui Costa, and Stephen Machin, “Why Does Education Reduce Crime?” Journal of Political Economy 130, no. 3 (2022): 732-65.
18 David J. Deming, “Better Schools, Less Crime?” Quarterly Journal of Economics 126 (2011): 2063-115; See also, E. Jason Baron, Joshua M. Hyman, and Brittany N. Vasquez, “Public School Funding, School Quality, and Adult Crime,” National Bureau of Economic Research, Working Paper 29855, available at http://www.nber.org/papers/w29855 .
19 FBI, “Trend of Violent Crime from 1985 to 2020.”
20 FBI, “Trend of Homicide from 1985-2020,” Crime Data Explorer, available at https://crime-data-explorer.fr.cloud.gov/pages/explorer/crime/crime-trend .
21 Charles Oberg, H.R. Hodges, Sarah Gander, Rita Nathawad, and Diana Cutts. “The Impact of COVID-19 on Children’s Lives in the United States: Amplified Inequities and a Just Path to Recovery,” Current Problems in Pediatric and Adolescent Health Care 52, no. 7 (2022): 1-17.
22 Sabrina Tavernise, “An Arms Race in America: Gun Buying Spiked during the Pandemic. It’s Still Up,” New York Times , May 29, 2021, updated May 30, 2021, available at https://www.nytimes.com/2021/05/29/us/gun-purchases-ownership-pandemic.html .
23 Tavernise, “An Arms Race in America.”
24 Philip J. Cook and Jens Ludwig, “Gun Violence Is THE Crime Problem,” Vital City . March 2, 2022, available at https://www.vitalcitynyc.org/articles/gun-violence-is-the-crime-problem .
25 Carrega and Krishnakumar, “Hate Crime Reports in US Surge”; FBI, “Hate Crime in the United States Incident Analysis, 1995-2020,” Crime Data Explorer,” accessed October 6, 2022, https://crime-data-explorer.fr.cloud.gov/pages/explorer/crime/hate-crime .
26 Center for the Study of Hate & Extremism at California State University, “Report to the Nation: Anti-Asian Prejudice & Hate Crime 2021,” (2021), available at https://www.csusb.edu/sites/default/files/Report%20to%20the%20Nation%20-%20Anti-Asian%20Hate%202020%20Final%20Draft%20-%20As%20of%20Apr%2028%202021%2010%20AM%20corrected.pdf .
27 Chelsea Hansen, “Slave Patrols: An Early Form of American Policing,” National Law Enforcement Museum , July 10, 2019, available at https://lawenforcementmuseum.org/2019/07/10/slave-patrols-an-early-form-of-american-policing/ ; See also, Jill Lepore, “The Invention of the Police: Why Did American Policing Get so Big, so Fast? The Answer, Mainly, Is Slavery,” The New Yorker , July 13, 2020, available at https://www.newyorker.com/magazine/2020/07/20/the-invention-of-the-police .
28 Library of Congress, “The Fugitive Slave Clause,” Constitution Annotated, available at https://constitution.congress.gov/browse/essay/artIV-S2-C3-1/ALDE_00013571/ [“clause”].
29 Hansen, “Slave Patrols.”
30 Zinn Education Project, “Massacres in U.S. History,” available at https://www.zinnedproject.org/collection/massacres-us/ .
31 Gary Potter, “The History of Policing in the United States, Part 3,” EKU Online . Eastern Kentucky University. July 9, 2013, available at https://ekuonline.eku.edu/blog/police-studies/the-history-of-policing-in-the-united-states-part-3/ ; See also, Paul A. Shackel, “How a 1897 Massacre of Pennsylvania Coal Miners Morphed from a Galvanizing Crisis to Forgotten History,” Smithsonian Magazine , March 13, 2019, available at https://www.smithsonianmag.com/history/how-1897-massacre-pennsylvania-coal-miners-morphed-galvanizing-crisis-forgotten-history-180971695/ .
32 Radley Balko, Rise of the Warrior Cop: The Militarization of America’s Police Forces , (New York: Public Affairs, 2021).
33 American Civil Liberties Union, “War Comes Home: The Excessive Militarization of American Policing” (2014), available at https://www.aclu.org/sites/default/files/assets/jus14-warcomeshome-report-web-rel1.pdf .
34 The Marshall Project, “How Policing Has—and Hasn’t—Changed since George Floyd,” August 6, 2022, available at https://www.themarshallproject.org/2022/08/06/how-policing-has-and-hasn-t-changed-since-george-floyd .
35 See, for example, Alex S. Vitale, The End of Policing (London: Verso Books, 2017), 4-11.
36 Vitale, The End of Policing , 11-13; See also, “Does Diversifying Police Forces Reduce Brutality against Minorities?” NPR , June 22, 2020, available at https://www.npr.org/2020/06/22/881559659/does-diversifying-police-forces-reduce-brutality-against-minorities .
37 Vitale, The End of Policing ; See also, José Luis Morín, Latino/a Rights and Justice in the United States: Perspectives and Approaches , 2nd edition (Durham, NC: Carolina Academic Press, 2009), 106-15; Balko, Rise of the Warrior Cop .
38 Weihua Li and Jamiles Lartey, “As Murders Spiked, Police Solved about Half in 2020,” The Marshall Project , January 12, 2022, available at https://www.themarshallproject.org/2022/01/12/as-murders-spiked-police-solved-about-half-in-2020 .
39 Frank Edwards, Hedwig Lee, and Michael Esposito, “Risk of being Killed by Police Use of Force in the United States by Age, Race–Ethnicity, and Sex,” PNAS 116, no. 34 (2019): 16793-8.
40 Leonardo Antenangeli and Matthew R. Durose, Recidivism of Prisoners Released in 24 States in 2008: A 10-Year Follow-up Period (2008–2018), Bureau of Justice Statistics NCJ Number 256094 September 2021, available at https://bjs.ojp.gov/library/publications/recidivism-prisoners-released-24-states-2008-10-year-follow-period-2008-2018 .
41 See, for example, Ruth Wilson Gilmore, Golden Gulag: Prisons Surplus, Crisis, and Oppression in Globalizing California (Berkeley: University of California Press, 2007); Vitale, The End of Policing ; Derecka Purnell, Becoming Abolitionists: Police, Protests, and the Pursuit of Freedom (New York: Astra House, 2021); Mariame Kaba, We Do This ’Til We Free Us: Abolitionist Organizing and Transforming Justice (Chicago: Haymarket Books, 2021); Angela Y. Davis, Gina Dent, Erica R. Meiners, and Beth Richie. Abolition. Feminism. Now (Chicago: Haymarket Books, 2022).
42 Yoav Gonen and Eileen Grench, “Five Days without Cops: Could Brooklyn Policing Experiment Be a ‘Model for the Future’?” The City , January 3, 2021, available at https://www.thecity.nyc/2021/1/3/22211709/nypd-cops-brooklyn-brownsville-experiment-defund-police .
43 Shaila Dewan. “‘Re-fund the Police’? Why It might Not Reduce Crime,” New York Times , November 8, 2021, updated November 11, 2021, available at https://www.nytimes.com/2021/11/08/us/police-crime.html .
The author(s) declared no potential conflicts of interest with respect to the research, authorship, and/or publication of this article.
Funding: The author(s) received no financial support for the research, authorship, and/or publication of this article.

- Society ›
- Crime & Law Enforcement
Violent crime in the U.S. - Statistics & Facts
Is violent crime actually in decline, violent crime statistics by country: how much safer is canada, who are the victims of violence, key insights.
Detailed statistics
Number of committed crimes in the U.S. 2022, by type
Reported violent crime rate in the U.S. 1990-2022
World's most dangerous cities, by murder rate 2023
Editor’s Picks Current statistics on this topic
Current statistics on this topic.
Justice System
Violent Crime
Most dangerous cities in the U.S. 2022, by violent crime rate
U.S.: number of reported violent crime 1990-2022
Related topics
Recommended.
- The impact of cybercrime on companies in the U.S.
- Property crime in the U.S.
- Crime in the United States
- U.S. consumers and cyber crime
- U.S. government and cyber crime
- Hate crime in the United States
Recommended statistics
- Basic Statistic U.S.: number of reported violent crime 1990-2022
- Basic Statistic Reported violent crime rate in the U.S. 1990-2022
- Basic Statistic Reported violent crime rate in the U.S. 2022, by state
- Basic Statistic USA - percentage of violent crimes reported to the police 2022
- Basic Statistic Most dangerous cities in the U.S. 2022, by violent crime rate
Total violent crime reported in the United States from 1990 to 2022
Reported violent crime rate in the United States from 1990 to 2022 (per 100,000 of the population)
Reported violent crime rate in the U.S. 2022, by state
Reported violent crime rate in the United States in 2022, by state (per 100,000 of the population)
USA - percentage of violent crimes reported to the police 2022
Percentage of violent crimes in the United States reported to the police in 2022
Leading cities with the largest number of violent crimes per 100,000 residents in the United States in 2022
Murder, manslaughter & homicide
- Basic Statistic U.S.: reported murder and nonnegligent manslaughter cases 1990-2022
- Basic Statistic USA - reported murder and nonnegligent manslaughter rate 1990-2022
- Basic Statistic Murder and non-negligent manslaughter rate in the U.S. 2022, by state
- Basic Statistic Murder in the U.S.: number of victims in 2022, by race
- Basic Statistic Number of murder offenders in the U.S. 2022, by gender
- Basic Statistic Homicide in the U.S. - number of victims 2022, by age
- Basic Statistic Murder in the U.S.: number of offenders 2022, by age
- Basic Statistic Murder victims by weapon used in the U.S 2022
- Basic Statistic Murder in the U.S. - relationship of victim to offender 2022
- Basic Statistic Number of justifiable homicides U.S. 2007-2022
U.S.: reported murder and nonnegligent manslaughter cases 1990-2022
Number of reported murder and nonnegligent manslaughter cases in the United States from 1990 to 2022
USA - reported murder and nonnegligent manslaughter rate 1990-2022
Reported murder and nonnegligent manslaughter rate in the United States from 1990 to 2022 (per 100,000 of the population)
Murder and non-negligent manslaughter rate in the U.S. 2022, by state
Murder and non-negligent manslaughter rate in the United States in 2022, by state (per 100,000 inhabitants)
Murder in the U.S.: number of victims in 2022, by race
Number of murder victims in the United States in 2022, by race
Number of murder offenders in the U.S. 2022, by gender
Number of murder offenders in the United States in 2022, by gender
Homicide in the U.S. - number of victims 2022, by age
Number of homicide victims in the United States in 2022, by age
Murder in the U.S.: number of offenders 2022, by age
Number of murder offenders in the United States in 2022, by age
Murder victims by weapon used in the U.S 2022
Number of murder victims in the United States in 2022, by weapon used
Murder in the U.S. - relationship of victim to offender 2022
Number of murders in the United States by relationship of victim to offender in 2022
Number of justifiable homicides U.S. 2007-2022
Number of justifiable homicides by law enforcement officers and private citizens in the United States from 2007 to 2022
Rape & sexual assault
- Basic Statistic U.S.: reported forcible rape cases 1990-2022
- Basic Statistic USA - reported forcible rape rate 1990-2022
- Basic Statistic Forcible rape rate in the U.S. by state 2022
- Premium Statistic Forcible rape and sexual assault victims in the U.S. 1993-2022, by sex
- Premium Statistic U.S. forcible rape/sexual assault victims 2022, by victim/offender relationship
- Premium Statistic U.S. forcible rape/sexual assault victims 2022, by weapon presence
U.S.: reported forcible rape cases 1990-2022
Number of reported forcible rape cases in the United States from 1990 to 2022
USA - reported forcible rape rate 1990-2022
Reported forcible rape rate in the United States from 1990 to 2022 (per 100,000 of the population)
Forcible rape rate in the U.S. by state 2022
Forcible rape rate per 100,000 inhabitants in the United States in 2022, by state
Forcible rape and sexual assault victims in the U.S. 1993-2022, by sex
Number of forcible rape and sexual assault victims in the United States from 1993 to 2022, by sex
U.S. forcible rape/sexual assault victims 2022, by victim/offender relationship
Number of forcible rape and sexual assault victims in the United States in 2022, by victim/offender relationship
U.S. forcible rape/sexual assault victims 2022, by weapon presence
Number of forcible rape and sexual assault victims in the United States in 2022, by weapon presence
- Basic Statistic U.S.: reported robbery cases 1990-2022
- Basic Statistic USA - reported robbery rate 1990-2022
- Basic Statistic Robbery rate in the U.S. 2022, by state
- Basic Statistic Robbery - number in the U.S. 2022, by location
- Basic Statistic Number of robberies in the U.S. 2022, by weapon
U.S.: reported robbery cases 1990-2022
Number of reported robbery cases in the United States from 1990 to 2022
USA - reported robbery rate 1990-2022
Reported robbery rate in the United States from 1990 to 2022 (per 100,000 of the population)
Robbery rate in the U.S. 2022, by state
Robbery rate in the United States in 2022, by state (per 100,000 inhabitants)
Robbery - number in the U.S. 2022, by location
Number of robberies in the United States in 2022, by location
Number of robberies in the U.S. 2022, by weapon
Number of robberies in the United States in 2022, by weapon used
Aggravated assault
- Basic Statistic U.S.: reported cases of aggravated assault 1990-2022
- Basic Statistic USA - reported aggravated assault rate 1990-2022
- Premium Statistic Aggravated assault rate in the U.S 2022, by state
- Basic Statistic Number of assaults U.S. 2022, by weapon used
U.S.: reported cases of aggravated assault 1990-2022
Number of reported cases of aggravated assault in the United States from 1990 to 2022
USA - reported aggravated assault rate 1990-2022
Reported aggravated assault rate in the United States from 1990 to 2022 (per 100,000 of the population)
Aggravated assault rate in the U.S 2022, by state
Aggravated assault rate in the United States in 2022, by state (per 100,000 inhabitants)
Number of assaults U.S. 2022, by weapon used
Number of assaults in the United States in 2022, by weapon used
Mass shootings
- Basic Statistic Worst mass shootings in the U.S., as of December 2023
- Basic Statistic Mass shootings in the U.S. 1982-2023, by state
- Basic Statistic Mass shootings in the U.S.: shooters by gender, as of December 2023
- Basic Statistic Mass shootings in the U.S. by shooter’s by race/ethnicity as of December 2023
- Basic Statistic Mass shootings in the U.S.: legality of shooter's weapons, as of December 2023
Worst mass shootings in the U.S., as of December 2023
Number of victims of the worst mass shootings in the United States between 1982 and December 2023
Mass shootings in the U.S. 1982-2023, by state
Number of mass shootings in the United States between 1982 and December 2023, by state
Mass shootings in the U.S.: shooters by gender, as of December 2023
Number of mass shootings in the United States between 1982 and December 2023, by shooter's gender
Mass shootings in the U.S. by shooter’s by race/ethnicity as of December 2023
Number of mass shootings in the United States between 1982 and December 2023, by shooter's race or ethnicity
Mass shootings in the U.S.: legality of shooter's weapons, as of December 2023
Number of mass shootings in the United States between 1982 and December 2023, by legality of shooter's weapons
Further reports Get the best reports to understand your industry
Get the best reports to understand your industry.
Mon - Fri, 9am - 6pm (EST)
Mon - Fri, 9am - 5pm (SGT)
Mon - Fri, 10:00am - 6:00pm (JST)
Mon - Fri, 9:30am - 5pm (GMT)
United Nations
Office on drugs and crime.
If you are not redirected automatically, follow the link
Crime and criminal justice statistics
- Fraud Alert
- Legal Notice
2024 Crime Rates in U.S. Cities Report

As a whole, Americans believe crime is getting worse , and the issue is sure to rank among the most important in the 2024 elections. Despite the widespread concern, crime is not equal across the nation.
Each year, SafeHome analysts dig into the latest FBI’s Crime in the United States reports. This year, we determined which cities have particularly high rates of property and violent crimes compared to other cities with similar populations.
Here are some key findings:
- Most violent crimes decreased in the U.S. in the most recent reporting year, but property crimes rose 7% nationwide. Motor vehicle thefts rose most significantly, increasing by 11%.
- Baltimore surpassed Detroit as the deadliest large city in the nation. Among cities with populations of 500,000 or more people, it had the highest per-capita murder and robbery rates.
- Among the largest cities, Seattle and San Francisco had high property crime rates, leading the nation in burglary and larceny, respectively.
- Salt Lake City, Utah ranked first for rape and larceny theft among small-sized cities.
- Cities such as Spokane, Tukwila, Kent, and Tacoma, Washington ranked in the top three for all types of property crimes.
National Violent and Property Crime Trends
Many Americans think crime is getting worse. When it comes to violent crime, the trends are complex. While robberies have increased, other traumatic crimes like rape, murder, and aggravated assault have decreased in the past decade and in more recent years.

Americans’ perception of crime being on an upward trend is certainly true regarding property crime in recent years. Property crime rose by seven percent between 2021 and 2022, and motor vehicle thefts increased by 11 percent in the same period. Larceny, theft without violence or a break-in, increased by eight percent in 2022. Burglary rates mainly remained constant in recent years but have declined significantly since 2012.

Despite nationwide progress toward crime reduction over the past decade, there are many cities where crime is still challenging local leaders and frightening residents. In the next section, we’ll detail the cities with the highest population-adjusted crime rates compared to other cities of like size.
>> Related reading: Best Home Security Systems of 2024
Crime in Large Cities (Populations over 500,000)
Baltimore, which has struggled with high crime rates for decades, had the highest murder rate in the country according to the latest Crime in the U.S. report from the FBI. It surpassed Memphis, which took the unwanted distinction last year. Detroit remained in second place for the second year in a row.
Top 3 large cities with highest violent crime rates (per 100,000 residents)
Despite its top ranking, Baltimore has seen its murder rate drop recently. While new public policies and educational initiatives are possible reasons, experts cite “ collective fatigue ” as a leading cause for the improvement. Residents are fed up with the violence and are making a communal effort to reduce it. Despite the drop in the murder rate, Baltimore was also the top city for robbery.
>> Also check out: The Difference Between Burglary and Robbery
For rape, Columbus entered the top three this year, while Memphis remained the top city for aggravated assault. Aggravated assault is a violent act on another person, usually resulting in physical harm.
Large cities with highest property crime rates (per 100,000 residents)
San Francisco, Portland, and Seattle, three of the largest cities on the West Coast, led the pack regarding property crime. Seattle had the dubious distinction of having the highest burglary rate two years in a row, while San Francisco passed Memphis with the highest larceny rate.
A complex variety of factors drive property crime in these Northwestern metropolises. In the case of Portland, high housing costs and understaffed police agencies contributed to its property crime issues. However, the city recently hired more officers to help reduce crime. Though Seattle led the nation in burglary rates in 2022, the city police agency reported that property crimes declined in 2023 thanks to various new tactics.
>> Related: States with Most Police
Crime in Medium Cities (250,000-499,999 Residents)
Among medium-sized cities in the U.S., with populations of more than 250,000 to less than half a million, New Orleans had the highest murder rate in 2022. More recently, the city’s homicides have dropped off dramatically overall, but murders of children rose to their highest levels in the city in 2023. St. Louis ranked second among medium-sized cities, with the murder rate increasing from 64 to 70 per 100,000 residents in 2022, a nearly 10 percent increase in just one year.
Top 3 medium-sized cities with the highest violent crime rates (per 100,000 residents)
In 2022, Anchorage became the new leading city in terms of rape rates. Its rate of 172 reported rapes per 100,000 residents is higher than last year's worst city, Cleveland, which had a rate of 117. Though Anchorage is new to the top of the list this year, Alaska has long had above-average rates of sexual violence, especially against indigenous women.
Oakland also outranked last year’s two worst cities for robbery (Cleveland and Minneapolis). Oakland was new to the data set in 2022, making it difficult to say whether this reflects a recent uptick.
Medium cities with highest property crime rates (per 100,000 residents)
Property crime has increased more dramatically than violent crime in the 2020s. Oakland and St. Louis are conspicuous among medium cities; both ranked in the top three cities for motor vehicle theft and larceny. Unfortunately, it’s challenging to bring car thieves to justice. In just three months in St. Louis, more than 2,600 cars were stolen, but only 23 people were arrested .
Crime in Small Cities (100,000-249,999 Residents)
This year, a different Alabama city took the dishonor of having the highest murder rate among its small-sized peers. Last year, it was Mobile, at a rate of 46 murders per 100,000 residents, and this year it’s Birmingham. Mobile’s rates fell dramatically after an error in the data was discovered , which also brought down its calculated rape total.
Salt Lake City became the worst small city for rape, and it seems that the issue isn’t limited to just the capital city. Across the state of Utah, rape is the only violent crime in Utah with higher rates than the national average.
Small cities with highest violent crime rates (per 100,000 residents)
Little Rock’s aggravated assault rate decreased year-over-year but it remains first among small cities in the 2022 FBI report. Other types of violent crime, like homicide, peaked in Little Rock in 2022 as well. Birmingham, Alabama was also among the worst cities for aggravated assault. A recent analysis found that Birmingham’s high violent crime rates drove up the cost of crime in the city: researchers estimated that each crime cost the city $11,392 per capita . Rockford, Illinois, the largest city in Illinois outside of Chicago, had the third-highest rate among small cities.
The small cities with the highest robbery rates were all located in the country's Western region, with Tacoma, Washington, Pueblo, Colorado, and San Bernadino, California ranking in the top three.
Small cities with highest property crime rates (per 100,000 residents)
Several of the small cities with the highest violent crime rates also ranked highly for property crime. Pueblo, Tacoma, and Salt Lake City had high property crime rates to match their troublesome violent crime statistics.
The state of Washington had two cities in the top three for larceny, topped only by Salt Lake City, Utah. Across the state, Washington is disproportionately impacted by retail theft, a type of larceny. The Forbes Retail Theft Index found that Washington gets 48 percent more reported retail thefts than it should based on its population.
Crime in Towns or Extra Small Cities (10,000-99,999 Residents)
Among very small cities with populations less than 100,000, Uvalde, Texas had the second-highest murder rate in 2022. This was driven by the tragic school shooting that year, whose victims made up almost all of the city’s murders that year.
Extra-small cities with highest violent crime rates (per 100,000 residents)
Several extra small cities in California and Arkansas appeared at the top of the lists for violent crime rates. In the case of California, violent crime rates are high across the state . Arkansas’ violent crime rates were high, too, but declined slightly in 2022 .
Extra-small cities with highest property crime rates (per 100,000 residents)
Beeville, Texas had the highest burglary rate among very small cities. According to local law enforcement, property crime increased significantly in 2022: the Beeville Police Department received two calls per resident per year. Commerce, California was the top city of its size for motor vehicle theft, and third highest for burglary. Another Washington city, Tukwila, took the top spot for larceny and ranked in the top three for vehicle theft.
This project analyzed the FBI’s Crime in the United States (CIUS) estimates from 2022, the latest year available. Particularly, we explored Table 8, Offenses Known to Law Enforcement. The data used in creating this table were from all city and town law enforcement agencies submitting 12 months of complete offense data for 2022.
To calculate the rates of crimes in each state, we divided the number of crimes reported by local law enforcement agencies by the population of the cities represented by those agencies. Then, we multiplied that number by 100,000. Please note that for 2022, limited data were available for Florida, Illinois, Maryland, and Pennsylvania.
- Skip to main content
- Skip to primary sidebar
Criminal Justice
IResearchNet
Academic Writing Services
Crime reports and statistics.
Crime reports and statistics convey an extensive assortment of information about crime to the reader and include topics such as the extent of crime and the nature or characteristics of criminal offenses, as well as how the nature and characteristics of crime change over time. Aside from these big-picture topics related to crime, crime reports and statistics communicate specific information on the characteristics of the criminal incident, the perpetrator(s), and the victim(s). (adsbygoogle = window.adsbygoogle || []).push({});
I. Introduction
Ii. what are crime reports and statistics, and why are they important, iii. who publishes crime reports and statistics, and how do they do it, iv. the federal bureau of investigation and the ucr program, a. what crimes are measured in the ucr, b. the future of the ucr program: the national incident-based reporting system, c. advantages and disadvantages of ucr data, v. the bureau of justice statistics and the ncvs, a. ncvs methodology, b. crimes measured in the ncvs, c. the future of the ncvs, d. advantages of the ncvs, e. disadvantages of the ncvs, vi. ucr data and the ncvs compared, vii. conclusion.
The purpose of this research paper is to provide an overview of crime reports and statistics. Crime reports and statistics convey an extensive assortment of information about crime to the reader and include topics such as the extent of crime and the nature or characteristics of criminal offenses, as well as how the nature and characteristics of crime change over time. Aside from these big-picture topics related to crime, crime reports and statistics communicate specific information on the characteristics of the criminal incident, the perpetrator(s), and the victim(s). For example, crime reports and statistics present information on the incident, such as weapon presence, police involvement, victim injury, and location of the crime. Details such as the age, race, gender, and gang membership of the offender are also available in many of these reports. Also, details gleaned from statistics regarding the victim, such as, but not limited to, income, race, age, relationship with the offender, education, and working status, are made available. Crime reports can convey information that affects the complete population of individuals and/or businesses, or they can convey crime-related information on a subset of victims, such as males, the elderly, businesses, or the poor. Crime reports and statistics can focus on a short period of time, such as a month, or they can cover longer periods, such as 1 year or many years. In addition, these reports can offer change in crime and its elements over time. Statistics offered in crime reports may describe crime as it pertains to a small geographical region, such one city; one region, such as the West or the Northeast; or the entire nation. Finally, on the basis of statistics, these reports can describe crime in a static, point-in-time way, and they can provide a dynamic perspective describing how crime, its characteristics, or risk change over time.
Topics covered in this research paper include a discussion on what crime reports and statistics are as well as why they are important. Information presented includes what agencies publish crime reports and statistics as well as a brief history of these bureaus. Because crime reports and statistics are social products, it is imperative to present information on the data used to generate them. Two major data sources are used to generate crime reports and statistics: (1) the Uniform Crime Reports (UCR) and (2) the National Crime Victimization Survey (NCVS). The data these reports yield, as well as the methodology and measurement they use, are described. Because no data are perfect, a description of their advantages and disadvantages are presented. Because these data are the two primary sources of crime information in the United States, the research paper explores a comparison of these data. Given that entire textbooks can be devoted to the topic of crime reports and statistics, this research paper provides readers with a relatively short overview of the major topics related to these important items. For readers who wish to delve into the topic in greater detail, a list of recommended readings is provided at the close of the research paper.
To fully appreciate the information found in crime reports and the statistics used to summarize them, one must be aware of what is meant by crime reports and statistics, why this topic is important, who is responsible for the creation of reports and statistics, and how the reports and statistics are created. To address these important issues, the research paper is structured around these significant questions. It first addresses the question “What are crime reports and statistics, and why are they important?” Next, it asks, “What agency is responsible for crime reports and statistics?” In answering this question, the research paper presents past and current information about the Federal Bureau of Investigation (FBI) and the Bureau of Justice Statistics (BJS). Next, the research paper moves to addressing the closely related question “How are crime reports and statistics generated?” This portion of the research paper is the lengthiest, because it offers information on the nuts and bolts of the UCR and the NCVS, including a look at the history of the programs as well as future directions. Included also is a discussion of the methodology, advantages, and disadvantages of each program.
Crime reports describe information about crime and cover an almost endless array of crime topics. They can focus on specific crimes, types of victims, types of offenders, and/or characteristics of the offenses. A useful tool in conveying information about crime in crime reports is by using statistics. Statistics are merely numerical measures used to summarize a large amount of information—in this case, information on crime. For example, if one noted that on average in a particular year that 50% of violent crime was reported to the police, that person has simply summarized crime data and presented a simple meaningful number (50%) about that particular phenomenon (crime reporting).
Crime reports and statistics are vital to the study of criminology. Without these tools, our understanding about what kind of crime is occurring, how often crime is being committed, who is committing crime, who is being victimized, and the characteristics of offenses would be little more than guesses. Aside from a pure information utility, crime reports and accompanying statistics serve as an important indicator of the “health” of society. A rising crime rates suggests that society is ailing. Unequal victimization risk among groups of individuals suggests a societal ill in need of attention. Conversely, a reduction in crime conveyed by these reports and statistics is one indicator of an improved quality of life. An equally important function served by crime reports and statistics is to assist researchers in the development of and testing of crime and victimization theories. Another important function of crime reports is providing policymakers valuable, empirically based information so they can design policies to further reduce crime, better assist crime victims, and effectively deal with offenders.Without reliable information on crime, policies designed to reduce all crime and victimization would not only be ineffective but would also represent misappropriated or wasted valuable resources.
In general, the federal government publishes crime reports and statistics.The department within the federal government responsible for these publications is the U.S. Department of Justice. And within the Department of Justice, publications are generated by two bureaus: (1) the FBI and (2) the BJS. Because these documents are generated using taxpayer dollars, more recent crime reports (i.e., since about 1995) are available free to the public online at the respective bureaus (http://www.foi.gov and http://www.ojp.usdoj.gov/bjs).
Most individuals are aware of the crime-fighting responsibilities of the FBI. Fewer know that the responsibilities of the FBI include those of crime data compiler, crime data analysis, and publisher of crime reports for the United States. These responsibilities are accomplished through the UCR program, which compiles crime reports submitted voluntarily either directly by local, state, federal, or tribal law enforcement agencies or through centralized state agencies across the country. Although there are some exceptions, in general, UCR data are submitted to the FBI on a monthly basis. The crime information gathered via the UCR program comprises the nation’s oldest unified national crime data. Although the crime data may be the nation’s oldest, it took approximately 50 years of calls for such data before the UCR program started collecting crime data in 1930, and even then the crime report collection did not occur in the Bureau of Investigation (the precursor to the FBI); instead, a collective of police chiefs are responsible for the commencement of one of the nation’s two major crime information sources.
Calls for unified national statistics on crime were first made first in the 19th century. Although crime data had been collected for a long time, this collection was conducted at the state and local levels by some jurisdictions only. This was problematic, because no two states defined crimes in the same way. Neither did each jurisdiction necessarily collect information on the same crimes. Because of this, there was no way to aggregate this information in any meaningful way to get a unified picture of the national crime situation, and without standard offenses, officials could not make comparisons across jurisdictions. In 1870, the Department of Justice was established. At this time, Congress mandated the reporting of annual crime statistics. A short time later, in 1871, an appeal for unified national crime information was made at the convention of the National Police Association, an organization that later became known as the International Association of Chiefs of Police (IACP). Unfortunately, neither the establishment of the Department of Justice nor the call of police chiefs resulted in the collection of national crime information.
About 50 years later, in the late 1920s, the IACP established a Committee on the Uniform Crime Records to resolve this gap in crime information. The purpose of the committee was to develop a program as well as procedures for collecting information about the extent of crime in the United States. The product of this work was the UCR. Initiated in 1927, this program was designed to provide unified, reliable, and systematic information on a set of serious crimes reported to law enforcement agencies across the country. Using these data, police chiefs could compare crime across jurisdictions and time. The IACP managed the UCR program for several years, until the responsibility moved to FBI in 1935.
The UCR program initially included crime reports from 400 law enforcement agencies from 43 states, describing crime for approximately 20% of the population. Over time, the program has grown, and it now gathers crime reports from approximately 17,000 law enforcement agencies from all states, the District of Columbia, and some U.S. territories. Furthermore, the UCR program now describes crime as it occurs in almost the entire nation. The purpose of the UCR program started as, and continues to be, serving the needs of law enforcement agencies.
The UCR program gathers information on a wide variety of criminal offenses. Since 1985, these crimes have been partitioned into Part I and Part II crimes. Part I offenses include eight crimes that are considered to be serious and occur regularly. The frequency of these offenses means that enough information can be gathered to enable comparisons regarding crime across time and across jurisdiction. The eight Part I offenses include the following: (1) murder and nonnegligent manslaughter, (2) forcible rape, (3) robbery, (4) aggravated assault, (5) burglary, (6) larceny–theft, (7) motor vehicle theft, and (8) arson.
Part II crimes are also considered serious offenses; however, they differ from Part I offenses in that they occur relatively less frequently. Because of the infrequent nature of these events, reliable comparisons between jurisdictions or over time for these offenses are not often possible. The following are Part II criminal offenses:
- Other assaults (simple)
- Forgery and counterfeiting
- Corporate fraud
- Embezzlement
- Buying, receiving, and possessing stolen property
- Possession and carrying of a weapon
- Prostitution and commercialized vice
- Drug abuse violations
- Nonviolent and unlawful offenses against family and children
- Driving under the influence
- Liquor law violations
- Drunkenness
- Disorderly conduct
- All other violations of state or local laws not specified (except traffic violations)
- Suspicion, that is, arrested and released without formal charges
- Curfew violations and loitering
The UCR program offers more than simply counts of each crime. Depending on the crime, it also offers details of the criminal incident. The crime for which there is greatest detail in the UCR is murder and nonnegligent manslaughter. Using Supplemental Homicide Reporting forms, the FBI gathers information on the homicide victim’s age, sex, and race; the offender’s age, race, and sex; weapon type (if any); victim and offender relationship; and the circumstances that led to the homicide. For other crimes, some, but not many, details are available. For instance, one can ascertain whether a rape was completed or attempted, whether a burglary involved forcible entry, the type of motor vehicle stolen, and whether a robbery included a weapon.
Since the UCR program was launched, little has changed in terms of the data collected. One exception is the addition of arson as a Part I crime. Over time, it became clear that change was needed in the UCR program. For example, the lack of incident-level detail for offense data gathered was viewed as a significant limitation. In fact, most scholars refer to the UCR program as the UCR summary program, because it collects only aggregate-level information on the eight Part I index crimes over time.Another problem is that some crime definitions had become dated. In response to these and other concerns, evaluations by the FBI, the Bureau of Justice Statistics, the IACP, and the National Security Agency in the late 1970s and early 1980s concluded that the UCR program was in need of modernization and enhancements to better serve its major constituency: law enforcement. The final report of these evaluations and recommendations are available in Blueprint for the Future of the Uniform Crime Reporting Program.
The resulting redesign, introduced in the mid-1980s, is the UCR program’s National Incident-Based Reporting System (NIBRS). As the name indicates, data submitted to the FBI include the nature and types of crimes in each incident, victim(s) and offender(s) characteristics, type and value of stolen and recovered property, and characteristics of arrested individuals. In short, the NIBRS offers much more comprehensive and detailed data than the UCR.
The NIBRS, like the traditional UCR summary program, is voluntary, reflects crimes known to the police and gathers data on the same crimes as the summary program. Although the two systems share some characteristics, major differences exist. A significant difference is that the NIBRS has the capacity to collect incident-level details for all crimes covered. Another difference in the two programs is that the nomenclature of Part I and Part II offenses was discarded in favor of Group A and Group B classes of offenses in NIBRS. Group A crimes are substantially more inclusive than Part I offenses and consist of 22 crimes covering 46 offenses, some of which are listed here:
- Homicide (murder and nonnegligent manslaughter, negligent manslaughter, justifiable homicide [which is not a crime])
- Sex offenses, forcible (forcible rape, forcible sodomy, sexual assault with an object, forcible fondling)
- Assault (aggravated, simple, intimidation)
- Burglary/breaking and entering
- Larceny–theft
- Motor vehicle theft
- Sex offense, nonforcible
- Counterfeiting/forgery
- Destruction/damage/vandalism of property
- Drug/narcotic offenses
- Pornography/obscene material
- Prostitution
- Extortion/blackmail
- Gambling offenses
- Kidnapping/abduction
- Stolen property offenses
- Weapon law violations
Group B comprises 11 offenses and covers all crime that does not fall into Group A offenses:
- Curfew/loitering/vagrancy
- Family offense/nonviolent
- Peeping tom
- Trespass of real property
- All other offenses
In the NIBRS, law enforcement agencies are categorized as full-participation agencies or limited-participation agencies. Full-participation agencies are those that can submit data without placing any new burden on the officers preparing the reports and that have sufficient data-processing and other resources to meet FBI reporting requirements. Fullparticipation agencies submit data on all Group A and B offenses. Limited-participation agencies are unable to meet the offense-reporting requirements of full-participation agencies. These agencies submit detailed incident information only on the eight Part I UCR offenses.
Yet another departure from the traditional UCR summary system is that although the NIBRS collects data on many of the same crimes, it uses some revised and new offense definitions. For example, in the traditional UCR summary program, only a female can be a victim of a forcible rape. The NIBRS redefines forcible rape as “the carnal knowledge of a person,” allowing males to be victims of these offenses. A new offense category of crime included in the NIBRS is called crimes against society; these include drug/narcotic offenses, pornography/obscene material, prostitution, and gambling offenses. An important difference between the UCR and the NIBRS is that the NIBRS enables one to distinguish between an attempted versus a complete crime. Previously, no distinction was available. A significant improvement of NIBRS data is the ability to link attributes of a crime. For instance, in the traditional system, with the exception of homicide, one could not link offender information, victim information, and incident victim information.With the NIBRS, one can link data on victims to offenders to offenses to arrestees.
In the NIBRS, the hierarchy rule was changed dramatically. In the traditional system, the hierarchy rule prevented one from counting an incident multiple times due to multiple offenses within the same incident. Using the hierarchy rule, law enforcement agencies determined the most serious offense in an incident and reported only that offense to the FBI. With the NIBRS, all offenses in a single incident are recorded and can be analyzed. Some researchers have reported that the hierarchy rule has been completely suspended in the NIBRS, but this is incorrect. Two exceptions to the hierarchy rule remain. First, if a motor vehicle is stolen (motor vehicle theft), and there were items in the car (property theft), only the motor vehicle theft is reported. Second, in the event of a justifiable homicide two offenses are reported: (1) the felonious acts by the offenders and (2) the actual nonnegligent homicide. In the NIBRS, the hotel rule was modified as well. The hotel rule states that where there is a burglary in a dwelling or facility in which multiple units were burglarized (e.g., a hotel) and the police are most likely to be reported by the manager of the dwelling, the incident is counted as a single offense. In addition, the NIBRS has extended the hotel rule to self-storage warehouses, or mini-warehouses.
The traditional UCR summary reporting system is characterized by many advantages. First, it has been ongoing for more than eight decades with remarkably stable methodology. This aspect allows meaningful trend analysis. Second, the UCR allows analyses at a variety of levels of geography. One can ascertain crime information for cities, regions, or the nation. Third, this system offers broad crime coverage, ranging from vandalism to homicide. Fourth, instead of focusing only on street crimes (i.e., homicide, robbery, and assault), the UCR offers information on other crimes, such as embezzlement, drunkenness, and vagrancy. Fifth, the UCR summary system has broad coverage from law enforcement agencies. All 50 states, the District of Columbia, and some U.S. territories report data to the FBI. Sixth and last, the UCR collects crime information regardless of the age or victim or offender. Some crime data collection systems (e.g., the National Crime Victimization Survey) gather crime data on restricted ages only. The NIBRS enjoys many of the UCR’s advantages and more. The greatest additional advantage of the NIBRS is that it offers incident-level details for every crime reported. With greater detail, one can disaggregate data by multiple victim, offender, and incident characteristics. One also can link various components of the incident.
Both the traditional summary system and the NIBRS have limitations that are important to recognize. First, both systems reflect only crimes reported to the police. Evidence is clear that many crimes are reported to the police in low percentages. For example, only about half of all violent crime comes to the attention of the police. In some cases, such as rape, fewer than 30% of the crimes are reported to the police. Second, because the data come from law enforcement agencies, they can be manipulated for political and societal purposes. Although this is not considered to be a widespread problem, it can and has happened. Third, because the UCR reporting systems are voluntary, they are subject to a lack of, or incomplete, reporting by law enforcement agencies. When information is not submitted or the submitted information does not meet the FBI’s guidelines for completeness and accuracy, the FBI uses specific protocols to impute data to account for this issue. The degree to which UCR data are imputed at the national level is sizeable and varies annually.
The NIBRS is characterized by some disadvantages not shared with the traditional UCR system. First, the NIBRS has limited coverage. It requires a lengthy certification process, and scholars have suggested that a result of this is slow conversion to the system. As of 2007, 31 states were certified and contributing data to the program. This represents reporting by 37% of law enforcement agencies and coverage of approximately 25% of the U.S. population. Furthermore, not all agencies within certified states submit any NIBRS data. In 2004, only 7 states fully reported NIBRS data. The agencies that do participate tend to represent smaller population areas. As recently as 2005, no agency covering a population of over 1 million participated in the NIBRS. Given this, it is clear that the NIBRS does not utilize data that constitute a representative sample of the population, law enforcement agencies, or states.
The second major publisher of national crime reports and statistics is the BJS, the primary statistical agency in the Department of Justice. This bureau was established under the Justice Systems Improvement Act of 1979. Prior to this, the office was recognized as the National Criminal Justice Information and Statistics Service, which was a part of the Law Enforcement Agency within the Law Enforcement Assistance Administration. Currently, the BJS is an agency in the Office of Justice Programs within the Department of Justice. The mission of the BJS is to gather and analyze crime data; publish crime reports; and make available this information to the public, policymakers, the media, government officials, and researchers.
Although the BJS collects a wide variety of data related to all aspects of the criminal justice system, its major crime victimization data collection effort is currently the National Crime Victimization Survey (NCVS). The NCVS is the nation’s primary source of information about the frequency, characteristics, and consequences of victimization of individuals age 12 and older and their households in the United States. The survey was first fielded in 1972 as the National Crime Survey (NCS). The NCS was designed with three primary purposes. First, it was to serve as a benchmark for UCR statistics on crime reported to police. Second, the NCS was to measure what was called “the dark figure of unreported crime,” that is, crime unknown by law enforcement. Third, the NCS was designed to fill a perceived need for information on the characteristics of crime not provided by the UCR.
Shortly after the fielding of the NCS, work toward improving the survey began. Beginning in 1979, plans for a thorough redesign to improve the survey’s ability to measure victimization in general, and certain difficult-to-measure crimes, such as rape, sexual assault, and domestic violence, was started. The redesign was implemented in 1992 using a split-sample design. It is at this time that the NCS changed names to the NCVS. The first full year of NCVS data based on the redesign was available in 1993. Following the redesign, the NCVS measured almost the identical set of crimes gathered in the NCS. The only exception is that, after the redesign, data on sexual assault were collected.
In general, and as anticipated, the NCS redesign resulted in an increase in the number of crimes counted. Increases measured were not uniform across crime types, however. For example, increases in crimes not reported to the police were greater than the increases in crimes reported to the police. One reason for this is that improved cues for certain questions caused respondents to recall more of the less serious crimes—those that are also less likely to be reported to law enforcement officials. As a result, the percentage of crimes reported to police based on the redesigned survey is lower than the percentage calculated based on data collected with the previous survey design. This difference is particularly significant for crimes such as simple assault, which does not involve the presence of weapons or serious injury.
NCVS crime data come from surveys administered at a sample of households in the United States. Households are selected via a stratified, multistage, cluster sample. The samples are designed to be representative of households, as well as of noninstitutionalized individuals age 12 or older in the United States. The NCVS is characterized by a very large sample size. In recent years, approximately 80,000 persons in 40,000 households were interviewed. The NCVS is also characterized by a rotating-panel design in which persons are interviewed every 6 months for a total of seven interviews. Interviews are conducted in person and over the telephone throughout the year.
NCVS surveys are administered via two survey instruments. The first is a screening instrument that is used to gather information to determine whether a respondent was a victim of a threatened, attempted, or completed crime during the preceding 6 months. If the screening instrument uncovers a possible victimization, a second incidentfocused instrument is administered to gather detailed characteristics about all victimizations revealed. These details include the victim characteristics, offender characteristics, and characteristics of the incident.
The details gathered on the incident instrument are used in two very important ways. Detailed incident information is used to determine whether the incident described by the respondent was a crime and, if the incident is deemed a crime, the type of crime that occurred. These assessments are made not by the field representative or the survey respondent but by statisticians using incident details during data processing at the U.S. Census Bureau, the agency responsible for collecting the data on behalf of the BJS.
Because one of the major purposes of the NCVS was to serve as a benchmark for UCR summary program statistics on crime reported to police, and to measure the “dark figure” of unreported crime, the offenses measured by the NCVS are analogous to Part I crimes measured by the UCR. NCVS criminal offenses measured include rape, sexual assault, robbery, aggravated assault, simple assault, pocket-picking and purse-snatching, property theft, burglary, and motor vehicle theft.
The NCVS gathers far more than merely information on the types of personal and property crimes in the United States against persons age 12 or older. For each victimization revealed, extensive detailed information is collected. This includes the outcome of the victimization (completed, attempted); time and location of the incident; the number of victims, bystanders, and offenders; victim demographics; victim–offender relationship; offender demographics; offender drug and/or alcohol use; gang membership; presence of weapon(s); injuries sustained; medical attention received; police contact; reasons for or against contacting the police; police response; victim retaliation; value of retaliation; and so on.
Currently, the future of the NCVS is unclear. During 2007 and 2008, the Committee on National Statistics, in cooperation with the Committee on Law and Justice, reviewed the NCVS to consider options for conducting it. This need for review grew on the basis of evidence that the effectiveness of the NCVS has recently been undermined via the demands of conducting an expensive survey in a continued flatline budgetary environment. Given this situation, the BJS has implemented many cost savings strategies over time, including multiple sample cuts. Unfortunately, the result of sample cuts (in conjunction with falling crime rates) is that, for the last several years, the sample size is now such that only a year-to-year change of 8% or more can been deemed statistically different from no change at all. On the basis of the review, the panel concluded that the NCVS as it currently stands is not able to achieve its legislatively mandated goal of collecting and analyzing data. The review panel provided multiple recommendations regarding a redesign of the NCVS that are currently being studied. At this time, it is unclear what a redesign would entail, or even if a redesign will happen. One possibility—not embraced by the review panel—is the termination of the NCVS. Such an outcome would be unfortunate given that the survey provides the only nationally representative data on crime and victimization with extensive details on the victim, the offender, and the incident.
A major advantage of the NCVS is that it provides data on reported and unreported crimes. As stated previously, many crimes (and in some cases, e.g., rape, most crimes) are not reported to police. A second advantage of NCVS data is that they offer a wide range of criminal victimization variables, including information about crime victims (e.g., age, gender, race, Hispanic ethnic origin, marital status, income, and educational level), criminal offenders (e.g., gender, race, approximate age, drug/alcohol use, and victim–offender relationship), and the context of the crime (e.g., time and place of occurrence, use of weapons, nature of injury, and economic consequences). A third advantage of NCVS data is the high response rates. Like all surveys, response rates in the NCVS have declined a bit in recent years; nonetheless, they continue to be relatively high. For example, between 1993 and 1998, NCVS response rates varied between 93% and 96% of eligible households and between 89% and 92% of eligible individuals. A fourth advantage of NCVS data is that the survey has been ongoing for over three decades with a stable sample and methodology. This makes trend analysis possible, and it allows one to aggregate data in an effort to study relatively rare crimes, such as rape, or relatively small populations, such as American Indians.
The NCVS performs very well for the purposes designed; however, like all surveys, it has some limitations. First, the NCVS is designed to generate national estimates of victimization. Because of this, the data cannot be used to estimate crime at most other geographic levels, such as the state, county, or local level. In 1996, a region variable was added to the NCVS data, enabling crime estimates for the Northeast, South,West, andMidwest. On rare occasions, special releases of NCVS data have provided insight into crime in major cities. Limited age coverage is a second limitation of NCVS data. Because the data do not include victimizations of persons age 11 or younger, findings are not generalizable to this group. A third limitation is limited population coverage. Because one must live in a housing unit or group quarter to be eligible for the NCVS sample, persons who are crews of vessels, in institutions (e.g., prisons and nursing homes), members of the armed forces living in military barracks, or homeless are excluded from the NCVS sample and data. The fourth and final limitation is limited crime coverage. The NCVS collects data on the few personal and property crimes listed earlier and excludes many others. NCVS data tend to focus on street crimes, excluding other offenses, such as arson, crimes against businesses, stalking, vagrancy, homicide, embezzlement, and kidnapping. A limitation of the NCVS data stems from the fact that they are derived from a sample. Like all sample surveys, the NCVS is subject to sampling and nonsampling error. Although every effort is taken to reduce error, some remains. One source of nonsampling error stems from the inability of some respondents to recall in detail the crimes that occurred during the 6-month reference period. Some victims also may not report crimes committed by certain offenders (e.g., spouses), others may simply forget about victimizations experienced, and still others may experience violence on a frequent basis and may not view such incidents as important enough to report to an NCVS field representative. A final limitation is associated with what are referred to as series victimizations. Series victimizations are defined as six or more similar but separate victimizations that the victim is unable to recall individually or to describe in detail to an interviewer. Recall that crime classification in the NCVS is based on the respondent’s answers to several incident questions. Without information on each incident, crime classification cannot occur. To address series victimization, a specific protocol is used. This protocol states that if an individual was victimized six or more times in a similar fashion during the 6-month reference period, and he or she cannot provide the details about each incident, then one report is taken for the entire series of victimizations. Details of the most recent incident are obtained, and the victimization is counted as a singular incident. It is clear that the series protocol results in an underestimate of the actual rate of victimization.
Because of the similarities between the UCR and the NCVS, it is generally expected that each data source will provide the same story about crime in the United States. Although that does often happen, many times it does not. Since 1972, yearto- year violent crime change estimates from the NCVS and UCR moved in the same direction, either up or down, about 60% of the time. Property crime rates have moved in the same direction about 75% of the time. Given that the NCVS and the UCR have different purposes and different methodologies, study different populations, examine different types of crimes, and count offenses and calculate crime rates differently, a lack of congruence on occasion should not be surprising. This section of the research paper looks at some of the reason the two series do not always track together.
Perhaps the largest difference between the UCR and NCVS is that the UCR measures only crimes reported to law enforcement agencies; that is, if the crime was not reported to the police, that crime can never be reflected in UCR data. In contrast, the NCVS interviews victims of crime and collects information on crimes that were and were not reported to the police. A second major difference in the two systems is found in the population coverage. UCR data include all reported crimes regardless of victim characteristics. This includes crimes against young children, visitors from other countries, and businesses or organizations. In contrast, the NCVS provides data on reported and unreported crimes against people age 12 or older and their households. Not included in the NCVS data are crimes against persons younger than age 12, businesses, homeless people, and institutionalized persons.A third significant difference in the two systems is crime coverage. The Part I UCR summary reporting system includes homicide and arson, neither of which is measured by the NCVS. In contrast, the NCVS collects information on simple assault—the most frequent violent crime—whereas the UCR traditional Part I crimes excludes it. In addition, the NCVS and UCR define some crimes differently and count some crimes differently. As stated earlier, the UCR defines forcible rape as “the carnal knowledge of a female forcibly and against her will” and excludes rapes of males and other forms of sexual assault. The NCVS measures rape and sexual assault of both women and men.
Yet another significant difference concerns the basic counting unit of the two data collection systems. In the NCVS, the basic counting unit is the victim. There are two types of victims in the NCVS: (1) the person and (2) the household. When considering personal or violent crimes, (i.e., rape, sexual assault, robbery, assault, purse-snatching, or pocket-picking), the number of victimizations is equal to the number of persons victimized. When considering property crimes (i.e., property theft, household burglary, and motor vehicle theft), the number of victims is equal to the number of households victimized. Therefore, crime reports using NCVS data report rates of violent crime as the number of victimizations per 1,000 people age 12 or older. Likewise, property crimes are reported as the number of property victimizations per 1,000 households. In the UCR, the basic counting unit is the offense. For some crimes, such as assault and rape, an offense is equal to the number of victims. For other crimes, such as burglary or robbery, an offense is equal to the number of incidents. All UCR crime rates, regardless of the type of victim (i.e., individual or organization), are calculated on a per capita basis: the number of offenses per 100,000 people. For some crimes, the NCVS and UCR counting rules result in similar outcomes. For instance, if in a single incident two people were assaulted by a knifewielding offender both programs would count two aggravated assaults. In contrast, other times counting rules result in different outcomes. For example, if in a single incident five people were robbed by a gun-toting offender, the NCVS would record five robbery victimizations, and the UCR would count a single robbery. If, however, a bank teller was threatened by an armed assailant during a bank robbery, the UCR would record this as a robbery with a weapon, whereas the NCVS, which measures only crimes against people and their households, would classify the same crime as an aggravated assault victimization (assuming that no personal property was stolen from the teller).
This research paper has provided an overview of crime reports and statistics, which are used to convey an extensive amount of information about crime. This includes topics such as the extent of crime and the nature or characteristics of criminal offenses, as well as how the nature and characteristics of crime change over time. Furthermore, official crime reporting systems, such as the UCR, the NIBRS, and the NCVS, allow insight into the experiences of crime and victimization for specific groups and how they may or may not differ from others or over time. Understanding what crime reports and statistics are requires an understanding of the agencies that gather the data and publish the reports. Furthermore, one must comprehend the intricacies of the data collection to fully appreciate the strengths and weaknesses of what the data (and resulting reports and statistics) offer.
Data from the UCR and the NCVS are essential to an understanding of crime. Because crime is not a directly observable phenomenon, no single measure can adequately convey or describe information about its extent and characteristics. Like other nonobservable events, such as the economy or the weather, no single measure suffices. One could not hope to understand the state of the economy by understanding only the unemployment rate. Neither could one fully realize the condition of the weather by understanding the percentage humidity only. Multiple measures are required for such phenomenon. These multiple measures are found in UCR data and the NCVS. Together, used in a complementary fashion, these data provide a more complete understanding of crime in the nation than either could alone.
References:
- Addington, L. A. (2007). Using NIBRS to study methodological sources of divergence between the UCR and NCVS. In J. P. Lynch & L. A. Addington (Eds.), Understanding crime statistics: Revisiting the divergence of the NCVS and the UCR (pp. 225–250). NewYork: Cambridge University Press.
- Barnett-Ryan, C. (2007). Introduction to the Uniform Crime Reporting Program. In J. P. Lynch & L. A. Addington (Eds.), Understanding crime statistics: Revisiting the divergence of the NCVS and the UCR (pp. 55–92). New York: Cambridge University Press.
- Biderman, A. D., & Reiss, A. J. (1967). On exploring the “dark figure” of crime. Annals of the American Academy of Political and Social Science, 374, 1–15.
- Bureau of Justice Statistics. (1989). Redesign of the National Crime Survey (NCJ Publication No. 111457). Washington, DC: U.S. Department of Justice.
- Federal Bureau of Investigation. (2004). UCR: Uniform Crime Reporting handbook. Washington, DC: U.S. Department of Justice.
- Kindermann, D., Lynch, J., & Cantor, D. (1997). Effects of the redesign on victimization estimates (NCJ Publication No. 164381). Washington, DC: U.S. Department of Justice.
- Lehnen, R. G., & Skogan, W. G. (Eds.). (1981). The National Crime Survey working papers: Vol. 1. Current and historical perspectives (NCJ Publication No. 75374). Washington, DC: U.S. Department of Justice.
- Lehnen, R. G., & Skogan,W. G. (Eds.). (1984). The National Crime Survey working papers: Vol. 2. Methodological studies (NCJ Publication No. 90307).Washington, DC: U.S. Department of Justice.
- Lynch, J. P., & Addington, L. A. (Eds.). (2007). Understanding crime statistics: Revisiting the divergence of the NCVS and the UCR. New York: Cambridge University Press.
- Maltz, M. D. (1999). Bridging gaps in police crime data (NCJ Publication No. 176365).Washington, DC: U.S. Department of Justice.
- National Research Council of the National Academies. (2008, February). Surveying victims: Options for conducting the National Crime Victimization Survey. Retrieved December 28, 2013, from http://books.nap.edu/openbook.php?record_id=12090&page=R1
- President’s Commission on Law Enforcement and the Administration of Justice. (1967a). The challenge of crime in a free society. Washington, DC: U.S. Government Printing Office.
- President’s Commission on Law Enforcement and the Administration of Justice. (1967b). Crime and its impact: An assessment. Washington, DC: U.S. Government Printing Office.
- Rennison, C. M., & Rand, M. R. (2007). Introduction to the National Crime Victimization Survey. In J. P. Lynch & L. A. Addington (Eds.), Understanding crime statistics: Revisiting the divergence of the NCVS and the UCR (pp. 17–54). NewYork: Cambridge University Press.
- U.S. Department of Justice. (1985). Blueprint for the future of the Uniform Crime Reporting Program.Washington, DC: Author.

Research/Study Research/Study
Fox News barely covered a FBI report showing crime rates declined significantly in 2023
Written by Ben Van Bloem
Research contributions from Rob Savillo
Published 04/03/24 9:00 AM EDT
Fox News largely ignored the March release of the FBI’s quarterly report showing that crime in the U.S. dropped significantly last year, undermining the right-wing narrative that crime is increasingly rampant across the country. In the two weeks after the FBI report was released Fox News gave just 2 minutes of coverage to the decline in crime rates.
The latest FBI report revealed a continuation of post-pandemic trends in which “crime in the U.S. declined significantly in 2023,” MSNBC reported , including “likely the largest one-year decline in murder that has ever been recorded,” according to crime analyst Jeff Asher, with a 13% drop nationwide. The FBI report also found that overall violent crime declined by 6% and property crime dropped 4% in the fourth quarter of 2023 compared to the same time period in 2022.
Fox News aired less than 2 minutes of coverage of the FBI’s report of lower crime rates in the two weeks following its March 18 release. Between March 18 and April 1, there were only 7 mentions of the FBI crime report or the drop in crime rates on Fox News, the longest of which included allegations from the guest, America’s Most Wanted host John Walsh, claiming that the crime data from the FBI was manipulated, calling it “bullshit” and saying, “They’re cooking the books.” Of the 6 other brief mentions, one featured Fox host Greg Gutfeld mocking “new data from the FBI [that] claims U.S. crime rate is dropping” by saying, “Let’s look at this graph while I stab you.”
Citation From the March 19, 2024, edition of Fox News' Gutfeld!
Overall, Fox’s reluctance to cover the latest FBI crime report appears to be a repeat of the network’s 2022 election year strategy to raise fears while ignoring actual crime levels. Instead of giving airtime to inconvenient truths that show crime rates have declined, Fox is pushing false narratives about a manufactured " migrant crime " crisis and insisting that people feeling like crime is up is more important than the data showing it is down. This sort of misleading coverage may explain why — despite the demonstrable decreases shown by the latest FBI report — Gallup polling finds that 77% of Americans incorrectly believe crime rates are actually worsening.
Methodology
Media Matters searched transcripts in the SnapStream video database for all original programming on Fox News Channel for any of the terms “murder,” “homicide,” “robbery,” “theft,” or “larceny” or any variation of either of the terms “crime” or “violent” within close proximity of any of the terms “FBI,” “Federal Bureau of Investigation,” dip," “drop,” “decrease,” “downward,” “decline,” “fell,” “plummet,” “trend,” or “rate” or any variation of either of the terms “reduce” or “low” from March 18, 2024, when the FBI released its Quarterly Uniform Crime Report data for the fourth quarter of 2023, through April 1, 2024.
We timed segments, which we defined as instances when the downward national trend in violent crime highlighted in the FBI Quarterly Uniform Crime Report data release was the stated topic of discussion or when we found significant discussion of the downward trend. We defined significant discussion as instances when two or more speakers in a multitopic segment discussed the downward trend with one another.
We also timed mentions, which we defined as instances when a single speaker in a segment on another topic mentioned the downward trend without another speaker in the segment engaging with the comment, and teasers, which we defined as instances when the anchor or host promoted a segment about the downward trend scheduled to air later in the broadcast.
We rounded all times to the nearest minute.
Read our research on: Gun Policy | International Conflict | Election 2024
Regions & Countries
Criminal justice, 8 facts about black lives matter.
As we mark 10 years since the #BlackLivesMatter hashtag first appeared on social media, here are eight facts about the Black Lives Matter movement.
#BlackLivesMatter Turns 10
More than 44 million #BlackLivesMatter tweets from nearly 10 million distinct users currently exist on Twitter today. Over half of all existing tweets that include the #BlackLivesMatter hashtag were posted from May to September 2020.
Support for the Black Lives Matter Movement Has Dropped Considerably From Its Peak in 2020
Today, 51% of U.S. adults say they support the Black Lives Matter movement – down from 67% in June 2020. A majority of Americans say the increased focus on race and racial inequality in the past three years hasn't led to improvement for Black Americans.
Fewer than 1% of federal criminal defendants were acquitted in 2022
In 2022, only 290 of 71,954 defendants in federal criminal cases – about 0.4% – went to trial and were acquitted.
Before release of video showing Tyre Nichols’ beating, public views of police conduct had improved modestly
Prior to the Tyre Nichols video release, views of police conduct in the U.S. had improved in three of four measures, with crime an exception.
For Black History Month, a look at what Black Americans say is needed to overcome racial inequality
Most Black adults (63%) say voting is an extremely or very effective strategy for Black progress; only 42% say the same of protesting.
Black Americans differ from other U.S. adults over whether individual or structural racism is a bigger problem
About half of Black adults (52%) say racism in U.S. laws is the bigger problem for Black people, while 43% cite racism by individuals.
Violent crime is a key midterm voting issue, but what does the data say?
With Election Day approaching, here’s a closer look at voter attitudes on violent crime and an analysis of the nation’s violent crime rate.
Black Americans Have a Clear Vision for Reducing Racism but Little Hope It Will Happen
Black Americans support significant reforms to or complete overhauls of several U.S. institutions to ensure fair treatment. Yet even as they assess inequality and ideas about progress, many are pessimistic about whether society and institutions will change in ways that would reduce racism.
How Black Americans view the use of face recognition technology by police
Black Americans are critical of key aspects of policing and criminal justice. But their views on face recognition technology are more nuanced.
Refine Your Results
About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .

Bad data from the FBI mislead about crime
T he fourth quarter 2023 crime report from the FBI, the federal government’s keeper of crime data, is unreliable at best and deceptive at worst.
The FBI’s preliminary 2023 data show murder declined by 13.2% across the country and violent crime dropped 5.7% compared to 2022 levels. Various news headlines have reported the FBI’s numbers unquestioningly, claiming murder is “plummeting” and violent crime “declined significantly” to pre-pandemic levels.
But these latest figures warrant skepticism, as we outline in a new report. In fact, violent crime is up substantially from 2019 levels, and last year’s apparent drop is less significant than it appears.
Part of the problem is how police departments report offenses to the FBI. The FBI asked, then demanded, that law enforcement agencies “transition” away from the system they used for decades to a new, more detailed but onerous one. The 2021 mandate to use NIBRS to submit crime data proved a disaster as overstretched departments, especially in large cities, failed to reach compliance and thus did not submit data.
In 2019, 89% of agencies covering 97% of the population submitted data, but by 2021, that coverage plummeted to less than 63% of departments overseeing just 65% of the population. Chicago, Los Angeles, and New York City all failed to submit crime data . To increase participation, the FBI relaxed the NIBRS requirement in 2022, allowing agencies to report via the legacy system.
But many other cities, such as St. Louis , which had transitioned to the new method, still struggle to comply and submit partial or faulty data. The FBI compensates by relying more heavily on “estimation,” or informed guesswork, to fill in the gaps and produce aggregated data.
That method of inferring offense totals is based on similar jurisdictions and past trends but is prone to error since it cannot compensate for local factors or events. For example, comparing Baltimore’s 2015 homicide total to similar cities’ trends would produce a skewed result. Baltimore, beset by riots and a police stand-down, saw murder rise 62% that year. In peer cities, murders rose in Cleveland only 15% and fell in Detroit by 1% and Memphis by 4%.
And the figures the agencies do report to the FBI do not match the agencies’ publicly reported figures. For Baltimore, the FBI reported 225 murders in 2023, but the city reported 262 — which means the FBI left out 37 murders. In Milwaukee , the police department reported a 7% increase in robberies, but the FBI showed a 13% drop. Nashville’s own data tallied more than 6,900 aggravated assaults in 2023, but the FBI counted only 5,941, leaving almost 1,000 of those offenses “missing.” This trend is consistent across the board: While 2022’s FBI city-level figures track the police’s own data, the 2023 numbers consistently undercount offense totals. Any year-to-year comparison overstates decline.
Other measures of crime levels undermine, or at least muddle, the veracity of the FBI’s data, which rely on “reported” offenses by victims and law enforcement themselves. The federal government’s own victims’ survey , which attempts to capture the gap between the number of actual offenses and the number reported to police, shows much higher offense rates than the FBI does. Moreover, a rising share of victims are failing to report their victimizations at all. In 2022, only 42% of violent crime victims and 33% of property crime victims bothered to report the crime to police.
That underreporting reduces the reliability of FBI numbers in measuring actual offense levels. For example, robbery offenses, which constitute roughly 25% of all violent crime by volume compared to 5% for murder, declined 18% between 2019 and 2022, according to the FBI, while the victim’s survey suggests a 30% rise.
Another complicating factor is underreporting by the police themselves, who might be under pressure to “downcharge” offenses or dissuade the victims from reporting the crime at all. While the prevalence of underreporting by the police is hard to quantify, an investigation found that between 2005 and 2012, the Los Angeles Police Department erased thousands of crimes, mostly violent assaults, by reclassifying them as lesser offenses or not capturing them at all. The fuzzy math artificially reduced the city’s crime rate by 7%. Any such malfeasance, when officials are under immense pressure to show progress in fighting crime, would inject bad data into the FBI’s estimation model, only compounding its errors.
Our analysis of 40 jurisdictions that both reported data to the FBI and the Major Cities Chiefs Association , which collects data from the largest police departments, shows that homicide declined 10.2% across 40 major cities in 2023 since 2022, but the FBI reported a 12.8% decline in those same jurisdictions. Similarly, the FBI reported a 6.6% decline in violent crime since 2022, but the same cities reported only a 4.5% drop, with the FBI counting 3,200 more violent crimes in 2022 than the MCCA and 2,600 fewer in 2023 — a net discrepancy of almost 5,900 offenses. That gap conveniently results in a more significant drop in crime levels year to year.
In reality, violent crime is up substantially from 2019 levels. In big cities, murder is still elevated — up 23% since 2019 across all 70 cities tracked by the MCCA and up 18% according to a 32-city analysis by the nonprofit organization Council on Criminal Justice . For aggravated assaults, CCJ's 25-city sample found those up 8%, while the MCCA larger sample of cities reported a 26% increase over the same period.
To say crime is down is like descending from a tall peak and standing on a high bluff and saying you are closer to the ground — a true but misleading statement. Worse, the FBI’s crime data serve as a poor altimeter to judge how high (or low) crime actually is.
CLICK HERE TO READ MORE FROM RESTORING AMERICA
Mark Morgan is the former assistant FBI director and acting commissioner of U.S. Customs and Border Protection and now serves as the president of the Coalition for Law Order and Safety. Sean Kennedy is the executive director of CLOS.

Portal login
ASD Cyber Threat Report 2022-2023
This rating relates to the complexity of the advice and information provided on the page.

Content written for
Attachments.
- ASD's Cyber Threat Report 2022-2023 7.67MB .pdf
- Fact Sheets - Businesses & Organisations - 2022-2023 190KB .pdf
- Fact sheets - Critical Infrastructure - 2022-2023 172KB .pdf
- Fact Sheets - Individuals - 2022-2023 173KB .pdf
I am pleased to present the Annual Cyber Threat Report 2022–23 developed by the Australian Signals Directorate (ASD).
As the Defence Strategic Review made clear, in the post-Second World War period Australia was protected by its geography and the limited ability of other nations in the region to project combat power. In the current strategic era, Australia’s geographic advantages have been eroded as more countries have enhanced their ability to project combat power across greater ranges, including through the rapid development of cyber capabilities.
Australia’s region, the Indo-Pacific, is also now seeing growing competition on multiple levels – economic, military, strategic and diplomatic – framed by competing values and narratives.
In this context, Australian governments, critical infrastructure, businesses and households continue to be the target of malicious cyber actors. This report illustrates that both state and non-state actors continue to show the intent and capability to compromise Australia’s networks. It also highlights the added complexity posed by emerging technologies such as artificial intelligence.
The report demonstrates the persistent threat that state cyber capabilities pose to Australia. This threat extends beyond cyber espionage campaigns to disruptive activities against Australia’s essential services. The report also confirms that the borderless and multi-billion dollar cybercrime industry continues to cause significant harm to Australia, with Australians remaining an attractive target for cybercriminal syndicates around the world.
Through case studies, the report demonstrates the persistence and tenacity of these cyber actors. It shows that these adversaries constantly test vulnerabilities in Australia’s cyber ecosystem and employ a range of techniques to evade Australia’s cyber defences.
The threat environment characterised in this report underscores the importance of ASD’s work in defending Australia’s security and prosperity. It also reinforces the significance of the Australian Government’s investment in ASD’s cyber and intelligence capabilities under Project REDSPICE (Resilience, Effects, Defence, Space, Intelligence, Cyber, Enablers).
It is clear we must maintain an enduring focus on cyber security in Australia. The Australian Government is committed to leading our nation’s efforts to bolster our cyber resilience.
We also know that the best cyber defences are founded on genuine partnerships between and across the public and private sectors. The development of this report, which draws on insights from across the Commonwealth Government, our international partners, Australian industry and the community, is a testament to this collaboration.
This report presents a clear picture of the cyber threat landscape we face and is a vital part of Australia’s collective efforts to enhance our cyber resilience.
The Hon Richard Marles, MP Deputy Prime Minister and Minister for Defence

About ASD’s ACSC
ASD’s Australian Cyber Security Centre (ACSC) is the Australian Government’s technical authority on cyber security. The ACSC brings together capabilities to improve Australia’s national cyber resilience and its services include:
- the Australian Cyber Security Hotline, which is contactable 24 hours a day, 7 days a week, via 1300 CYBER1 (1300 292 371)
- publishing alerts, technical advice, advisories and notifications on significant cyber security threats
- cyber threat monitoring and intelligence sharing with partners, including through the Cyber Threat Intelligence Sharing (CTIS) platform
- helping Australian entities respond to cyber security incidents
- exercises and uplift activities to enhance the cyber security resilience of Australian entities
- supporting collaboration between over 110,000 Australian organisations and individuals on cyber security issues through ASD’s Cyber Security Partnership Program.
The most effective cyber security is collaborative and partnerships are key to this work. ASD thanks all of the organisations that contributed to this report. This includes Australian local, state, territory and federal government agencies, and industry partners.
Executive summary
Malicious cyber activity continued to pose a risk to Australia’s security and prosperity in the FY 2022-23. A range of malicious cyber actors showed the intent and capability needed to compromise vital systems, and Australian networks were regularly targeted by both opportunistic and more deliberate malicious cyber activity.
ASD responded to over 1,100 cyber security incidents from Australian entities. Separately, nearly 94,000 reports were made to law enforcement through ReportCyber – around one every 6 minutes.
ASD identified a number of key cyber security trends in FY 2022–23:
State actors focused on critical infrastructure – data theft and disruption of business.
Globally, government and critical infrastructure networks were targeted by state cyber actors as part of ongoing information-gathering campaigns or disruption activities. The AUKUS partnership, with its focus on nuclear submarines and other advanced military capabilities, is likely a target for state actors looking to steal intellectual property for their own military programs. Cyber operations are increasingly the preferred vector for state actors to conduct espionage and foreign interference.
In 2022–23, ASD joined international partners to call out Russia’s Federal Security Service’s use of ‘Snake’ malware for cyber espionage, and also highlighted activity associated with a People’s Republic of China state-sponsored cyber actor that used ‘living-off-the-land’ techniques to compromise critical infrastructure organisations.
Australian critical infrastructure was targeted via increasingly interconnected systems .
Operational technology connected to the internet and into corporate networks has provided opportunities for malicious cyber actors to attack these systems. In 2022–23, ASD responded to 143 cyber security incidents related to critical infrastructure.
Cybercriminals continued to adapt tactics to extract maximum payment from victims.
Cybercriminals constantly evolved their operations against Australian organisations, fuelled by a global industry of access brokers and extortionists. ASD responded to 127 extortion-related incidents: 118 of these incidents involved ransomware or other forms of restriction to systems, files or accounts. Business email compromise remained a key vector to conduct cybercrime. Ransomware also remained a highly destructive cybercrime type, as did hacktivists’ denial-of-service attacks, impacting organisations’ business operations.
Data breaches impacted many Australians .
Significant data breaches resulted in millions of Australians having their information stolen and leaked on the dark web.
One in 5 critical vulnerabilities was exploited within 48 hours.
This was despite patching or mitigation advice being available. Malicious cyber actors used these critical flaws to cause significant incidents and compromise networks, aided by inadequate patching.
Cyber security is increasingly challenged by complex ICT supply chains and advances in fields such as artificial intelligence. To boost cyber security, Australia must consider not only technical controls such as ASD’s Essential Eight, but also growing a positive cyber-secure culture across business and the community. This includes prioritising secure-by-design and secure-by-default products during both development (vendors) and procurement (customers).
ASD’s first year of REDSPICE increased cyber threat intelligence sharing, the uplift of critical infrastructure, and an enhanced 24/7 national incident response capability.
Genuine partnerships across both the public and private sectors have remained essential to Australia’s cyber resilience; and ASD’s Cyber Security Partnership Program has grown to include over 110,000 organisations and individuals.
Year in review
What asd saw.
Average cost of cybercrime per report, up 14 per cent
- small business: $46,000
- medium business: $97,200
- large business: $71,600.
Nearly 94,000 cybercrime reports, up 23 per cent
- on average a report every 6 minutes
- an increase from 1 report every 7 minutes.
Answered over 33,000 calls to the Australian Cyber Security Hotline, up 32 per cent
- on average 90 calls per day
- an increase from 69 calls per day.
Top 3 cybercrime types for individuals
- identity fraud
- online banking fraud
- online shopping fraud.
Top 3 cybercrime types for business
- email compromise
- business email compromise (BEC) fraud
- online banking fraud.
Publicly reported common vulnerabilities and exposures (CVEs) increased 20 per cent.
What ASD did
- Responded to over 1,100 cyber security incidents , similar to last year.
- 10 per cent of all incidents responded to included ransomware , similar to last year.
- Notified 158 entities of ransomware activity on their networks, compared to 148 last year, roughly a 7 per cent increase.
- Australian Protective Domain Name System blocked over 67 million malicious domain requests, up 176 per cent.
- Domain Takedown Service blocked over 127,000 attacks against Australian servers, up 336 per cent.
- Cyber Threat Intelligence Sharing partners grew by 688 per cent to over 250 partners.
- issued 103 High-priority Operational Taskings, up 110 per cent
- distributed around 4,900 reports to approximately 1,360 organisations, up 16 per cent and 32 per cent respectively.
- 3 CI-UPs completed covering 6 CI assets
- 3 CI-UPs in progress
- 20 CI-UP Info Packs sent
- 5 CI-UP workshops held.
- Notified 7 critical infrastructure entities of suspicious cyber activity , up from 5 last year.
- Published or updated 34 PROTECT and Information Security Manual (ISM) guidance publications .
- Published 64 alerts, advisories, incident and insight reports on cyber.gov.au and the Partnership Portal.
- Individual Partners up 24 per cent
- Business Partners up 37 per cent
- Network Partners up 29 per cent.
- Led 20 cyber security exercises involving over 75 organisations to strengthen Australia’s cyber resilience.
- Briefed board members and company directors covering 33 per cent of the ASX200.
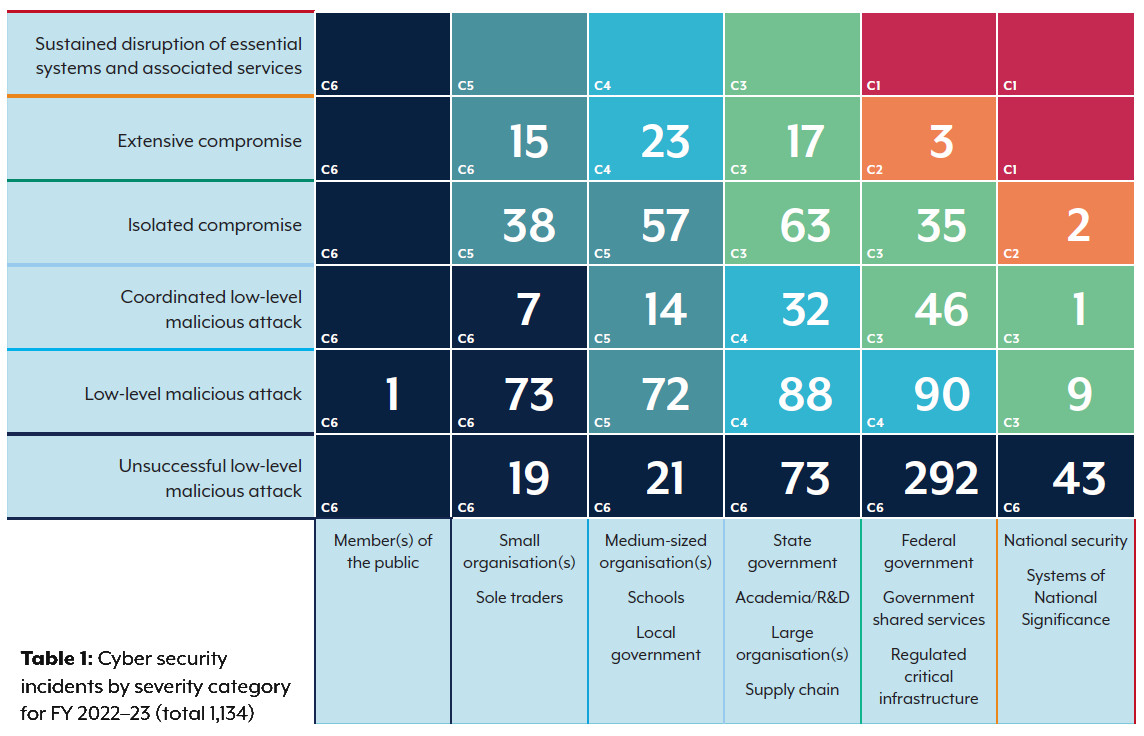
ASD is able to build a national cyber threat picture, in part due to the timely and rich reporting of cyber security incidents by members of the public and Australian business. This aggregation of cyber security incident data enables ASD to inform threat mitigation advice with the latest trends and threats posed by malicious cyber actors. Any degradation in the quantity or quality of information reported to ASD harms cyber security outcomes. Information reported to ASD is anonymised prior to it being communicated to the community.
ASD categorises each incident it responds to on a scale of Category 1 (C1), the most severe, to Category 6 (C6), the least severe. Incidents are categorised on severity of effect, extent of compromise, and significance of the organisation.
The number of C2 incidents rose from 2 in FY 2021–22 to 5 in FY 2022–23. This includes significant data breaches involving cybercriminals exfiltrating data from critical infrastructure for the purposes of financial gain.
Cyber security incidents are consistent with last financial year, with around 15 per cent of all incidents being categorised C3 or above. Of the C3 incidents, over 30 per cent related to organisations self-identifying as critical infrastructure, with transport (21 per cent), energy (17 per cent), and higher education and research (17 per cent) the most affected sectors.
The most common C3 incident type was compromised assets, network or infrastructure (23 per cent), followed by data breaches (19 per cent) and ransomware (14 per cent). Common activities leading to C3 incidents included exploitation of public–facing applications (20 per cent) and phishing (17 per cent).
Almost a quarter (24 per cent) of C3 incidents involved a tipper, where ASD notified the affected organisations of suspicious activity.
While reports of low-level malicious attacks are often categorised as unsuccessful, reports of unsuccessful activity are still indicative of continual targeting of Australian entities.
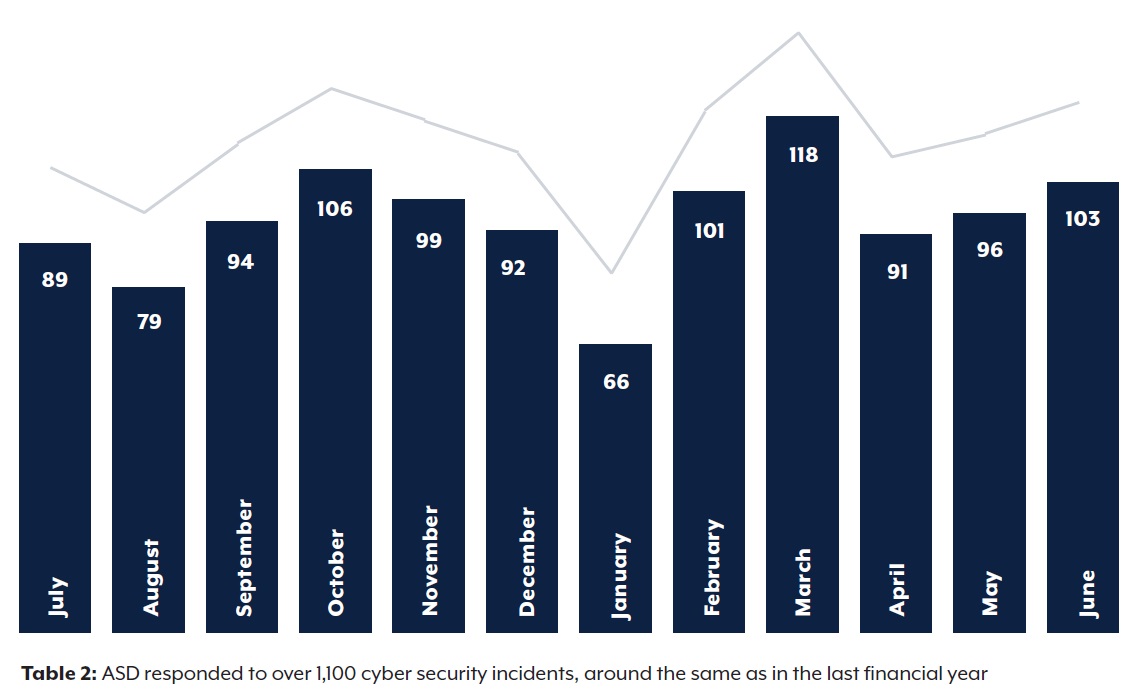
Cyber security incidents by sector
Compared to 2021–22, the information media and telecommunications sector fell out of the top 5 reporting sectors.
Government sectors and regulated critical infrastructure have reporting obligations, which may explain the relatively high reporting rate for these sectors compared with others.
ASD categorises sectors following the Australian and New Zealand Standard Industrial Classification (ANZSIC) Divisions from the Australian Bureau of Statistics. The public safety and administration division encompasses several sectors including federal, state, territory and local governments, public order and safety services, and Defence.
Table 3 : The top 10 reporting sectors
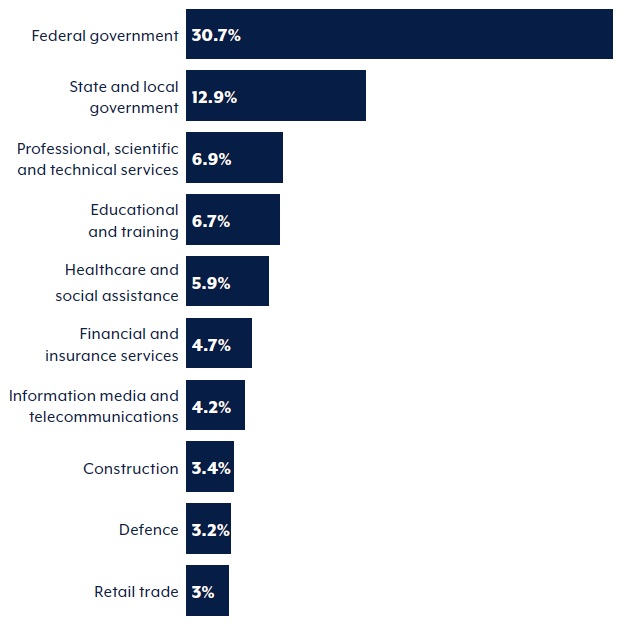
Chapter 1: Exploitation
- Half of vulnerabilities were exploited within 2 weeks of a patch, or of mitigation advice being released, highlighting the risks entities take by not promptly patching.
- Patching vulnerabilities in internet-facing services should occur within 2 weeks, or 48 hours if an exploit exists.
- Vulnerable internet-facing devices and applications are convenient targets for malicious cyber actors. In addition to patching, unnecessary internet-facing services should be disabled.
Vulnerable and exposed
As Australians integrate more technology into their lives and businesses, the number of possible weak points or vectors for malicious cyber actors to exploit – known as the attack surface – grows. The larger the attack surface, the harder it is to defend. Malicious cyber actors often exploit security weaknesses found in ICT, known as common vulnerabilities and exposures (CVEs), to break into systems, steal data, or even take complete control over a system.
The number of published CVEs has been steadily on the rise. The US National Vulnerability Database published 19,379 CVEs in FY 2020–21, 24,266 CVEs in FY 2021–22, and 29,019 CVEs in FY 2022–23.
To identify the rates at which CVEs were exploited after a patch or mitigation was made available, ASD analysed 60 CVEs covering 1 July 2020 to 28 February 2023. The analysis found around 82 per cent of vulnerabilities had an attack vector of ‘network’ under the Common Vulnerability Scoring Scheme. This indicates that malicious actors prefer vulnerabilities that are remotely exploitable and are present on internet-facing or edge devices. Exploitation of these vulnerabilities allows malicious actors to pivot into internal networks. The analysis also found:
- 1 in 5 vulnerabilities was exploited within 48 hours of a patch or mitigation advice being released
- half of the vulnerabilities were exploited within 2 weeks of a patch or mitigation advice being released
- 2 in 5 vulnerabilities were exploited more than one month after a patch or mitigation advice was released.
Despite more than 90 per cent of CVEs having a patch or mitigation advice available within 2 weeks of public disclosure, 50 per cent of the CVEs were still exploited more than 2 weeks after that patch or mitigation advice was published. This highlights the risk entities carry when not patching promptly. These risks are heightened when a proof-of-concept code is available and shared online, as malicious cyber actors can leverage this code for use in automated tools, lowering the barrier for exploitation.
ASD observed that Log4Shell (CVE-2021-44228) and ProxyLogon (CVE-2021-26855) were by far the most commonly exploited vulnerabilities throughout the analysis period, with these 2 vulnerabilities representing 29 per cent of all CVE-related incidents.
CVEs do not have an expiration date. In one instance, ASD observed that malicious cyber actors successfully exploited an unpatched 7-year-old CVE. Additionally, ASD still receives periodic reports of WannaCry malware – 6 years after its release – which is likely due to old, infected legacy machines being powered on and connected to networks. Incidents like this highlight the importance of patching as soon as possible, and also demonstrate the long tail of risks that unpatched and legacy systems can pose to entities.
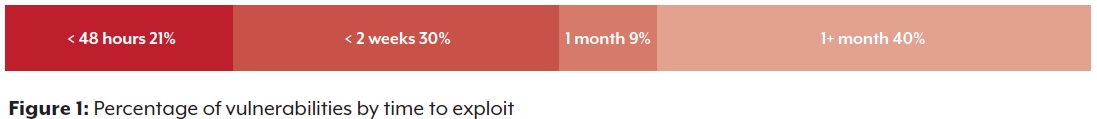
During 2022–23, ASD published many alerts warning Australians of vulnerabilities, such as the critical remote code execution vulnerability in Fortinet devices (CVE-2022-40684), and a high-severity vulnerability present in Microsoft Outlook for Windows (CVE-2023-23397). ASD also published a joint Five-Eyes advisory detailing the top 12 CVEs most frequently and routinely exploited by malicious cyber actors for the 2022 calendar year.
To help mitigate vulnerabilities, ASD recommends all entities patch, update or otherwise mitigate vulnerabilities in online services and internet-facing devices within 48 hours when vulnerabilities are assessed as critical by vendors or when working exploits exist. Otherwise, vulnerabilities should be patched, updated or otherwise mitigated within 2 weeks. Entities with limited cyber security expertise who are unable to patch rapidly should consider using a reputable cloud service provider or managed service provider that can help ensure timely patching.
ASD acknowledges not all entities may be able to immediately patch, update or apply mitigations for vulnerabilities due to high-availability business requirements or system limitations. In such cases, entities should consider compensating controls like disabling unnecessary internet-facing services, strengthening access controls, enforcing network separation, and closely monitoring systems for anomalous activity. Entities should ensure decision makers understand the level of risk they hold and the potential consequences should their systems or data be compromised as a result of a malicious actor exploiting unmitigated vulnerabilities.
Further patching advice can be found in ASD’s Assessing Vulnerabilities and Applying Patches guide.
Cyber hygiene
In addition to patching, effective cyber security hygiene is vital. At cyber.gov.au, ASD has published a range of easy-to-understand advice and guides tailored for individuals, small and medium business, enterprises, and critical infrastructure providers.
All Australians should:
- enable multi-factor authentication (MFA) for online services where available
- use long, unique passphrases for every account if MFA is not available, particularly for services like email and banking (password managers can assist with such activities)
- turn on automatic updates for all software – do not ignore installation prompts
- regularly back up important files and device configuration settings
- be alert for phishing messages and scams
- sign up for the ASD’s free Alert Service
- report cybercrime to ReportCyber.
Australian organisations should also:
- only use reputable cloud service providers and managed service providers that implement appropriate cyber security measures
- regularly test cyber security detection, incident response, business continuity and disaster recovery plans
- review the cyber security posture of remote workers, including their use of communication, collaboration and business productivity software
- train staff on cyber security matters, in particular how to recognise scams and phishing attempts
- implement relevant guidance from ASD’s Essential Eight Maturity Model, Strategies to Mitigate Cyber Security Incidents and Information Security Manual
- join ASD’s Cyber Security Partnership Program
- report cybercrime and cyber security incidents to ReportCyber.
Case study 1: Malicious cyber actors exploit devices 2 years after patch
On 24 May 2019, Fortinet, a US vendor that creates cyber security products, released a security advisory and accompanying patch for CVE-2018-13379, which was a severe vulnerability that required immediate patching.
On 2 April 2021, the US Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory on the exploitation of Fortinet FortiOS vulnerabilities, which indicated advanced persistent threat (APT) groups were scanning devices for CVE-2018-13379 and likely to gain access to multiple government, commercial, and technology services networks.
On 3 April 2021, ASD released an alert reminding organisations that APT groups had been observed exploiting CVE-2018-13379. Later, in September 2021, ASD received a report of a successful exploitation of CVE-2018-13379 against an Australian entity. Despite being vulnerable for more than 2 years, the victim’s device had not been patched.
While it is difficult to ascertain how widely Fortinet devices are used globally, researchers identified around 50,000 targets that remained vulnerable 2 years after the patch was released. This number is so significant that it was added to CISA’s Top Routinely Exploited Vulnerabilities list.
The primary mitigation against these attacks is to patch vulnerabilities as soon as possible. If patching is not immediately possible, the entity should consider removing internet access from Fortinet devices until other mitigations can be implemented.
Case study 2: A network compromise at the Shire of Serpentine Jarrahdale
The rural Shire of Serpentine Jarrahdale, 45 kilometres from the Perth CBD, may seem an unlikely place for malicious cyber activity to unfold. But, in early 2023, the Shire experienced a network compromise. Shire ICT Manager Matthew Younger said the malicious cyber actor took advantage of a public-facing system. ‘We’re quite diligent with our patching, but unfortunately we missed an update to our remote work server,’ Mr Younger said.
Before taking immediate remediation action, the Shire’s ICT team held a conference call with ASD to discuss the best way to manage the compromise, and Mr Younger said ASD’s help was first-class. ‘We put a perimeter around the compromised server, checked for lateral movement, and gathered evidence to work out what happened. Everything we found led back to the importance of the Essential Eight.’
ASD also sent an incident responder to help the Shire’s ICT team capture virtual machine snapshots and log data. ASD handles incident data with strict confidentiality, and such data helps its analysts understand how cyber security incidents occur and produces intelligence to help build the national cyber threat picture and to prevent further attacks.
Mr Younger said that after the compromise, the Shire doubled-down on its efforts to implement ASD’s Essential Eight. ‘We enforced passphrases, we improved our information security policies, and we improved our user security training. We also validated our controls through penetration testing and phishing exercises.’
Mr Younger credits much of the Shire’s success to its agile leadership who, with limited resources, foster the right security culture to both respond to cyber threats and implement mitigations.
CVE-2020-5902
BIG-IP refers to a suite of products from cyber security vendor F5, which includes firewall and application delivery solutions. On 1 July 2020, F5 released a security advisory detailing a critical vulnerability in their BIG-IP Traffic Management User Interface (TMUI). Within 48 hours of patch release, security researchers discovered malicious cyber actors scanning for and exploiting unpatched devices.
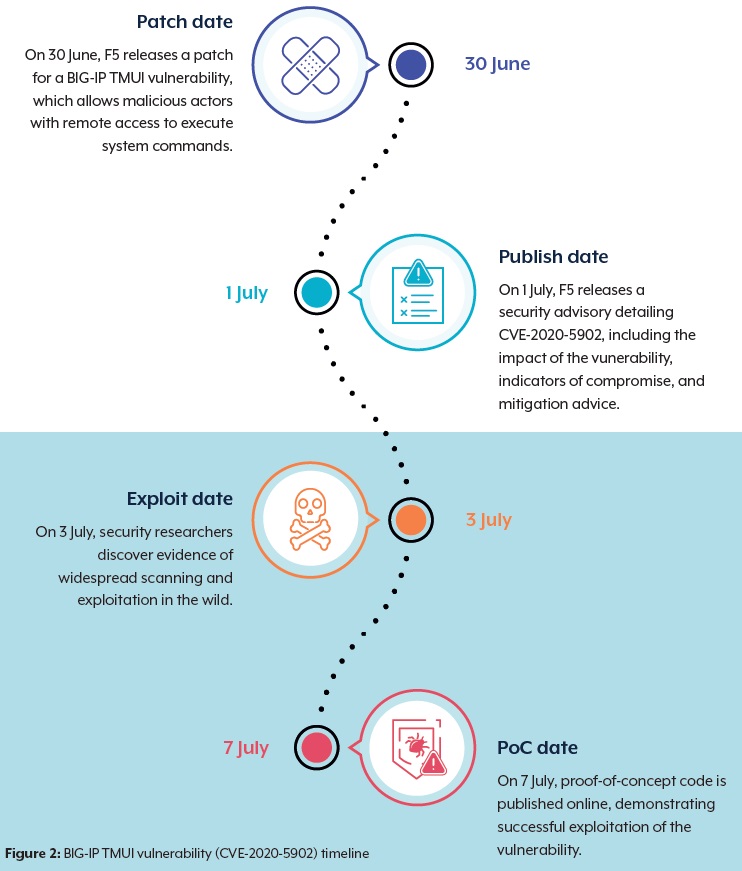
The Essential Eight
ASD’s Essential Eight are some of the most effective cyber security mitigation strategies, and includes:

ASD uses its cyber threat intelligence to ensure its cyber security advice is contemporary and actionable. ASD’s advice is not formed in a silo. Feedback from partners across government and industry, such as how cyber security mitigations are implemented within organisations, is important. Feedback helps ASD update advice like the Essential Eight.
More information on the Essential Eight, including the Essential Eight Assessment Process Guide and Essential Eight Maturity Model Frequently Asked Questions , can be found at cyber.gov.au.
Chapter 2: Critical infrastructure
- During FY 2022–23, Australian critical infrastructure networks regularly experienced both targeted and opportunistic malicious cyber activity. Activity against these networks is likely to increase as networks grow in size and complexity.
- Malicious cyber actors can steal or encrypt data, or gain insider knowledge for profit or competitive advantage. Some actors may attempt to degrade or disrupt services and these incidents can have cascading impacts.
- Designing robust cyber security measures for operational technology environments is vital to protect the safety, availability, integrity and confidentiality of essential services. Secure-by-design and secure‑by-default products should be a priority.
Actors target critical infrastructure for many reasons
Critical infrastructure assets and networks are attractive targets for malicious cyber activity as these assets need to hold sensitive information, maintain essential services, and often have high levels of connectivity with other organisations and critical infrastructure sectors.
A cyber incident can result in a range of impacts to critical services. For instance, the disruption of an electricity grid could cause a region to lose power. Without power, a hospital may lose access to patient records and struggle to function, internet services may be down and affect communications and payment systems, or water supply could be impacted.
Globally, a broad range of malicious cyber actors, including state actors, cybercriminals and issue‑motivated groups, have demonstrated the intent and the capability to target critical infrastructure. Malicious cyber actors may target critical infrastructure for a range of reasons. For example, they may:
- attempt to degrade or disrupt services, such as through denial-of-service (DoS) attacks, which can have a significant impact on service providers and their customers
- steal or encrypt data or gain insider knowledge for profit or competitive advantage
- preposition themselves on systems by installing malware, in anticipation of future disruptive or destructive cyber operations, potentially years in advance
- covertly seek sensitive information through cyber espionage to advance strategic aims.
Critical infrastructure can be targeted by the mass scanning of networks for both old and new vulnerabilities. In February 2023, an Italian energy and water provider was affected by ransomware. While there was no indication the water or energy supply was affected, it reportedly took 4 days to restore systems like information databases. Italy’s National Cybersecurity Agency publicly noted the ransomware attack targeted older and unpatched software, exploiting a 2-year-old vulnerability.
Critical infrastructure is a target globally
During 2022–23, critical infrastructure networks around the world continued to be targeted, causing impacts on network operators and those relying on critical services. In the latter half of 2022, the French health system reportedly sustained a number of cyber incidents. One hospital fell victim to a ransomware incident, resulting in the cancellation of some surgical operations and forcing patients to be transferred to other hospitals. The hospital’s computer systems had to be shut down to isolate the attack.
Russia’s war on Ukraine has continued to demonstrate that critical infrastructure is viewed as a target for disruptive and destructive cyber operations during times of conflict. Malicious cyber actors have targeted and disrupted hospitals, airports, railways, telecommunication providers, energy utilities, and financial institutions across Europe. Destructive malware was also used against critical infrastructure in Ukraine.
In September 2022 and May 2023, ASD and its international partners published advisories highlighting that state actors were targeting multiple US critical infrastructure sectors, and strongly encouraged Australian entities to review their networks for signs of malicious activity. More details about these advisories is in the state actor chapter .
Australian critical infrastructure is impacted
Australian critical infrastructure networks regularly experienced both targeted and opportunistic malicious cyber activity. During 2022–23, ASD responded to 143 incidents reported by entities who self-identified as critical infrastructure, an increase from the 95 incidents reported in 2021–22. The vast majority of these incidents were low-level malicious attacks or isolated compromises.
The main cyber security incident types affecting Australian critical infrastructure were:
- compromised account or credentials
- compromised asset, network or infrastructure
These incident types accounted for approximately 57 per cent of the incidents affecting critical infrastructure for 2022–23. Other more prominent incident types were data breaches followed by malware infection.
ASD encourages critical infrastructure entities to report anomalous activity early and not wait until malicious activity reaches the threshold for a mandatory report. Reporting helps piece together a picture of the cyber threat landscape, and informs ASD’s cyber security alerts and advisories for the benefit of all Australian entities.
Critical infrastructure networks have a broad attack surface
The interconnected nature of critical infrastructure networks, and the third parties in their ICT supply chain, increases the attack surface for many entities. This includes remote access and management solutions, which are increasingly present in critical infrastructure networks.
Operational technology (OT) and connected systems, including corporate networks, will likely be of enduring interest to malicious cyber actors. OT can be targeted to access a corporate network and vice versa, potentially allowing malicious cyber actors to move laterally through systems to reach their target. Even when OT is not directly targeted, attacks on connected corporate networks can disrupt the operation of critical infrastructure providers.
Systems where software or hardware are not up to date with the latest security mitigations are vulnerable to exploitation, particularly when these systems are exposed to the internet. ICT supply chain and managed service providers are another avenue malicious cyber actors can exploit.

Explainer 1: Operational technology
OT makes up those systems that detect or cause a direct change to the physical environment through the monitoring or control of devices, processes, and events. OT is predominantly used to describe industrial control systems (ICS), which include supervisory control and data acquisition (SCADA) systems and distributed control systems (DCS).
Australian critical infrastructure providers often operate over large geographical areas and require interconnection between dispersed OT environments. Separately, remote access to OT environments from corporate IT environments and the internet has become standard operating procedure. Remote access allows engineers and technicians to remotely manage and configure the OT environment. However, this interconnection or remote access requires an internet connection, which creates additional cyber security risks to OT environments.
In April 2023, irrigation systems in Israel were reportedly disrupted when the ICS supporting the automated water controllers were compromised. Israel’s National Cyber Organisation was able to warn many farmers to disconnect their remote control option for the irrigation systems, so the disruption was minimal. Being able to disconnect from remote control also highlights the value of a manual override mechanism in some instances.
Next-generation OT is expected to contain built-in remote access and security features, which could address some of the issues related to remote access and internet exposure. ASD continues to advise entities to prioritise secure-by-design and secure-by-default products in procurements, and take a risk-based approach to managing risks associated with new technologies or providers. Good cyber security practices will be particularly important during a transition to new technologies.
At cyber.gov.au, ASD has published a range of cyber security guides for OT and ICS, and also principles and approaches to secure-by-design and default.
In focus: food and grocery sector
The food and grocery sector covers a broad supply chain including processing, packaging, importing, and distributing food and groceries. Food and grocery manufacturing is Australia’s largest manufacturing sector, comprising over 16,000 businesses and representing around 32 per cent of all manufacturing jobs. Food and grocery organisations are an attractive target for malicious cyber actors as this sector’s provision of essential supplies has little tolerance for disruption.
The sector’s complex supply chains and growing online sales mean food and grocery organisations have a large attack surface. The sector is increasingly reliant on smart technologies, industrial control systems, and internet-based automation systems. Additionally, many entities in this sector hold sensitive data that may be of value to malicious cyber actors, such as personal information or intellectual property.
Like other manufacturing entities, food and grocery organisations have increasingly adopted just-in-time inventory and delivery chains in pursuit of greater efficiency and reduced waste. This means the food and grocery sector is also vulnerable if a supplier is affected by a cyber incident that disrupts services.
Large entities in this sector may be targeted based on the view that they can be extorted for large sums of money. Smaller entities may be perceived as having lower cyber security maturity, and may be used to access more lucrative targets in their supply chain. Malicious cyber actors may seek to remain undetected on systems to establish a secure foothold and then move to other systems within a business to exfiltrate data or maintain a presence for future malicious activity.
A cyberattack against entities in this sector could have significant impacts for both the victim organisation and its customers. For example, a ransomware attack that locks systems could halt production and delivery, rendering a business unable to fulfil its orders. The second order impacts of this could be costly – including lost revenue, or lost confidence from business partners and customers alike.
Early detection of malicious activity is vital for mitigating cyber threats. It can take time to discover a compromised network or system, so robust and regular monitoring is essential. Likewise, practised incident response plans and playbooks should form part of broader corporate and cyber plans to aid remediation and minimise the impact of a compromise. Entities in this sector should seek secure-by-design and secure‑by-default products wherever possible to boost their cyber security posture.
A comprehensive list of resources for critical infrastructure is available at cyber.gov.au, including guidance for cyber incident response and business continuity plans.
Case study 3: Global food distributor held to ransom
In February 2023, Dole – one of the world’s largest producers and distributors of fruit and vegetables – was a victim of a ransomware incident, resulting in a shut down of its systems throughout North America. Other reported impacts included some product shortages, a limited impact on operations, and theft of company data – including some employee information. While Dole acted swiftly to minimise the impacts of the incident, it still reported USD $10.5 million in direct costs, and faced reputational damage.
Explainer 2: Effective separation
Separating network segments can help to isolate critical network elements from the internet or other less sensitive parts of a network. This strategy can make it significantly more difficult for malicious cyber actors to access an organisation’s most sensitive data, and can aid cyber threat detection.
In 2022–23, ASD observed that effective separation through network segmentation and firewall policies prevented malware from impacting an Australian critical infrastructure provider. Additionally, through effective separation an Australian critical infrastructure provider prevented the deployment of malware from a contractor’s USB drive onto their OT environment.
Network separation is more than just a logical or physical design decision: it should also consider where system administration and management services are placed. Often, the corporate IT network is separated from the OT environment, because the corporate IT network is usually seen as having a higher risk of compromise due to its internet connectivity and services like email and web browsing.
However, if a malicious cyber actor compromises the corporate IT network and gains greater access privileges, then the corporate IT firewall may no longer provide the desired level of protection for the OT environment. This similarly applies if the Active Directory (AD) Domain for the OT environment is inside an AD Forest administered from the corporate IT network.
Critical infrastructure operators should regularly assess the risk of insufficient separation of system administrative and management role assignments. For example, in scenarios where the virtualisation of OT infrastructure or components is managed by privileged accounts from a corporate domain, if the corporate environment was to become compromised then the OT environment would potentially be impacted and those necessary privileged IT accounts may not be accessible.
Case study 4: Horizon Power working with ASD
Western Australian energy provider Horizon Power distributes electricity across the largest geographical catchment of any Australian energy provider – around 2.3 million square kilometres, or roughly an area 4 times bigger than France. It operates a diverse range of OT and ICT infrastructure to manage around 8,300 kilometres of transmission lines and deliver power to more than 45,000 customers.
In early 2023, Horizon Power partnered with ASD to conduct a range of activities to help examine and test its cyber security posture and controls. Horizon Power’s security team worked side-by-side with ASD’s experts to help improve threat detection, security event triage and response; practice forensic artefact collection; and enhance security communication across the enterprise. The activities have helped to improve both the speed and the quality with which Horizon Power can respond to and manage cyber incidents, including sharing cyber threat intelligence with ASD.
Horizon Power Senior Technology Manager Jeff Campbell said engaging ASD was easy, there were clear objectives, and the network assessments were excellent. ‘Long past are the days of holding cards to our chest. Sharing information is really important across multiple industries and sectors. To improve security, you need to find out what you don’t know.’
Mr Campbell said having ASD onsite helped to test many assumptions about the company’s network security, like its segmentation practices and vulnerability management. 'The engagement highlighted the importance of getting visibility over systems, and also helped to demonstrate that effective cyber security is vital to helping mitigate business risks.'
Learn more about the open, collaborative partnership between Horizon Power and the Australian Signals Directorate that enabled Horizon Power to bolster its cyber security controls.
Building cyber resilience in critical infrastructure
Malicious cyber activity against Australian critical infrastructure is likely to increase as networks grow in size and complexity. Critical infrastructure organisations can do many things to reduce the attack surface, secure systems, and protect sensitive data to help ensure Australia’s essential services remain resilient. Such as:
- Follow best practice cyber security, like ASD’s Essential Eight, or equivalent framework as required for a critical infrastructure risk-management program.
- Thoroughly understand networks, map them, and maintain an asset registry to help manage devices on all networks, including OT. Consider the security capabilities available on devices as part of routine architecture and asset review, and the most secure approach to hard-coded passwords.
- Scrutinise the organisation’s ICT supply chain vulnerabilities and risks.
- Prioritise secure-by-design or secure-by-default products. Consider the security controls of any new software, hardware, or OT before it is purchased, and understand vendor support for future patches and ongoing security costs. Build cyber security costs into budgets for the entire lifecycle of the product, including the product’s replacement.
- Understand what is necessary to keep critical services operating and protect these systems as a priority. Ensure OT and IT systems can be, or are, segmented to ensure the service is able to operate during a cyber incident.
- Treat a cyber incident as a ‘when’ not ‘if’ scenario in risk and business continuity planning, and regularly practice cyber incident response plans.
- Maintain open communication with ASD. ASD has a number of programs to support critical infrastructure, including cyber uplift activities and cyber threat intelligence sharing.
- Follow ASD’s cyber security publications tailored for critical infrastructure entities available at cyber.gov.au.
Explainer 3: The Trusted Information Sharing Network
The Department of Home Affairs’ Trusted Information Sharing Network (TISN) takes an all-hazards approach to help build security and resilience for organisations within the Australian critical infrastructure community. To rapidly and flexibly address current and future threats to Australia’s security, the TISN allows for all levels of government and industry to connect and collaborate.
Since launching the TISN platform in 2022, the network has been vital in amplifying key messages and information to members, facilitating sector group meetings and contributing to the weekly Community of Interest meetings to inform members of current data breaches, cyber threats, and technical advice available from ASD.
Explainer 4: Resilience in financial services
CPS 230 Operational Risk Management
Events of recent years have demonstrated the critical importance of financial institutions being able to manage and respond to operational risks, evident for example in the challenges of the COVID-19 pandemic, technology risks and natural disasters. Sound operational risk management is fundamental to financial safety and system stability.
To ensure that all APRA-regulated entities in Australia are well placed to manage operational risk and respond to business disruptions when they inevitably occur, on 17 July 2023, APRA released the new Prudential Standard CPS 230 Operational Risk Management (CPS 230).
CPS 230 encompasses operational risk controls and monitoring, business continuity planning and the management of third-party service providers. The aim of the standard is to:
- strengthen operational risk management with new requirements to address weaknesses that have been identified in existing practices of APRA-regulated entities. This includes requirements to maintain and test internal controls to ensure they are effective in managing key operational risks
- improve business continuity planning to ensure that APRA-regulated entities are ready to respond to severe business disruptions, and maintain critical operations such as payments, settlements, fund administration and claims processing. It is important that all APRA regulated entities are able to adapt processes and systems to continue to operate in the event of a disruption and set clear tolerances for the maximum level of disruption they are willing to accept for critical operations
- enhance third-party risk management by extending requirements to cover all material service providers that APRA-regulated entities rely upon for critical operations or that expose them to material operational risk, rather than just those that have been outsourced.
The new standard also aims to ensure that APRA-regulated entities are well positioned to meet the challenges of rapid change in the industry and in technology more generally.
CPS 234 Information Security
As part of APRA’s Cyber Security Strategy, all regulated entities are required to engage an independent auditor to perform an assessment against CPS 234, APRA’s Information Security Prudential Standard. This is the largest assessment of its kind conducted by APRA.
By the end of 2023, more than 300 banks, insurers and superannuation trustees will have completed their assessment. Early insights, from the assessments completed so far, have identified a number of common weaknesses across the industry, including:
- incomplete identification and classification for critical and sensitive information assets
- limited assessment of third-party information security capability
- inadequate definition and execution of control testing programs
- incident response plans not regularly reviewed or tested
- limited internal audit review of information security controls
- inconsistent reporting of material incidents and control weaknesses to APRA in a timely manner.
A summary of these findings, along with guidance to address gaps, have been shared in a recent APRA Insight Article – Cyber Security Stocktake Exposes Gaps. Entities are encouraged to review the common weaknesses identified and incorporate relevant strategies and plans to address shortfalls in their own cyber security controls, governance policies and practices. APRA will continue to work with entities that do not sufficiently meet CPS 234 requirements, to lift the benchmark for cyber resilience across the financial services industry.
Chapter 3: State actors
- State cyber actors will likely continue to target government and critical infrastructure, as well as connected systems and their supply chains as part of ongoing cyber espionage and information‑gathering campaigns. They do not just want state secrets; businesses also hold valuable and sensitive information.
- Some state actors are willing to use cyber capabilities to destabilise and disrupt systems and infrastructure. They may preposition on networks of strategic value for future malicious activities.
- Government and industry partnerships are vital in boosting national cyber security and resilience against cyberattacks by state actors.
Strategic context
The global and regional strategic environment continues to deteriorate, which is reflected in the observable activities of some state actors in cyberspace. In this context, these actors are increasingly using cyber operations as the preferred vector to build their geopolitical competitive edge, whether it is to support their economies or to underpin operations that challenge the sovereignty of others. In the Australian Security Intelligence Organisation’s Annual Report 2021–22, espionage and foreign interference was noted to have supplanted terrorism as Australia’s principal security concern.
Some states are willing to use cyber capabilities to destabilise or disrupt economic, political and social systems. Some also target critical infrastructure or networks of strategic value with the aim of coercion or prepositioning on a network for future disruptive activity.
State actors have an enduring interest in obtaining information to develop a detailed understanding of Australians and exploit this for their advantage. While government information is an attractive target for state actors seeking strategic insights into Australia’s national policy and decisions, many Australian businesses also hold sensitive and valuable data such as proprietary information, research, and personal information. Unlike cybercriminals who may post stolen data in public forums, state actors usually try to keep their activities covert – seeking to remain unnoticed, both when they are on an entity’s network and after a compromise.
State actors use various tools and techniques
In some cases, state actors may develop bespoke tools and techniques to fulfil their operational aims. In May 2023, ASD released a joint cyber security advisory with its international partners on the Snake implant – a cyber espionage tool designed and used by Russia’s Federal Security Service (FSB) for long-term intelligence collection on high-priority targets around the globe. Shortly after, Australia co-badged another joint cyber security advisory with international partners that outlined malicious cyber activity associated with a People’s Republic of China (PRC) state-sponsored cyber actor.
Case study 5: Advisory – People’s Republic of China state-sponsored cyber activity
[Go to advisory]
In May 2023, ASD joined international partners in highlighting a recently discovered cluster of activity associated with a PRC state-sponsored cyber actor, also known as Volt Typhoon. The campaign involved ‘living-off-the-land’ techniques – using built-in operating tools to help blend in with normal system and network activities. Private sector partners identified that this activity affected networks across US critical infrastructure sectors. However, the same techniques could be applied against critical infrastructure sectors worldwide, including in Australia.
ASD published the People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection advisory on cyber.gov.au and hosted numerous events to brief its Network Partners. For help to implement the advisory – call 1300 CYBER1 ( 1300 292 371 ).
Even when state actors have access to more advanced capabilities, they can use common tools and techniques to avoid the discovery of their best capabilities. For example, state actors continue to use relatively well-known tactics, such as exploiting unpatched or misconfigured systems and spear phishing.
The threat of state actor cyber operations is very real
State actors will likely continue to target government and critical infrastructure, as well as connected systems and their supply chains, as part of ongoing cyber espionage and information-gathering campaigns. Significant disruptive and destructive activities could occur if there were a major deterioration in Australia’s geopolitical environment. It is clear that preventative cyber security measures – such as implementing cyber security essentials, information-sharing and national cyber cooperation – are by far the best ways to help secure Australian networks.
In focus: Russia’s war on Ukraine
Cyber operations have been used alongside more conventional military activities during Russia’s war on Ukraine. Both Russia and Ukraine have faced many cyberattacks that impacted their societies, with extensive targeting of government and critical infrastructure networks.
Cyberattacks that began before the invasion of Ukraine have continued into 2023. Between January 2022 and the first week of February 2023, the Computer Emergency Response Team-Europe (CERT-EU) identified and analysed 806 cyberattacks associated with Russia’s war on Ukraine.
There has been extensive cyber targeting of Ukrainian networks across many sectors, including finance, telecommunications, energy, media, military and government. Ukraine has faced ransomware, denial‑of‑service (DoS) attacks, and mass phishing campaigns against critical infrastructure, government departments, officials and private citizens.
Russia has also been subject to cyber operations. Russian authorities have reported some of its federal agencies’ websites, including its energy ministry, were compromised by unknown attackers in a supply chain attack. Cyberattacks against Russia have tended to target entities related to the government, military, banking, logistics, transport and energy sectors.
Cyberattacks in Europe associated with Russia’s war on Ukraine
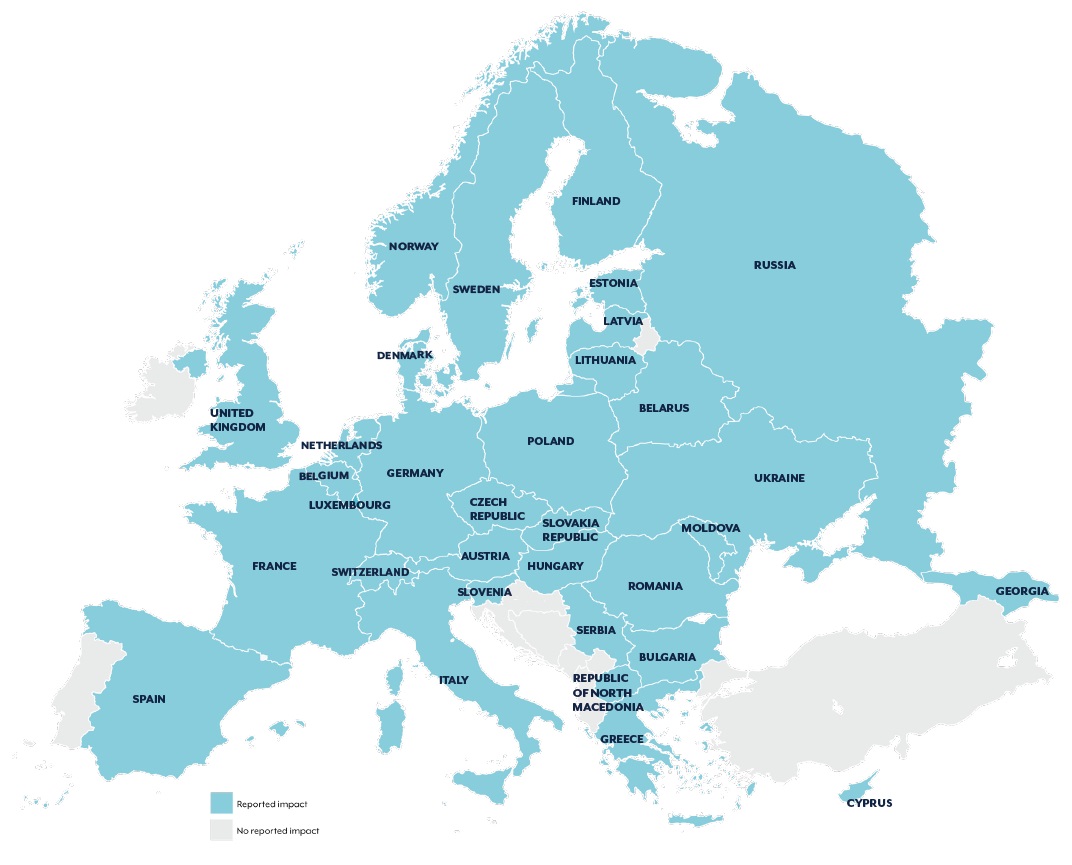
Figure 3 : Countries impacted by cyberattacks associated with Russia’s war on Ukraine
Cyber operations have enabled a borderless conflict
Cyber operations associated with Russia’s invasion have affected entities in multiple countries during the first year of the conflict, including the European Parliament, European governments, the Israeli Government, and hospitals in the Netherlands, Germany, Spain, the US, and the UK. Many of these countries have linked the attacks to pro-Russian groups. For example, pro-Russian hacktivists, KillNet, have claimed a number of attacks such as the February 2023 DoS attack on numerous German websites, including those for German airports, public administration bodies, financial sector organisations, and other private companies. Belarus also reported its railway network was disrupted by a cyberattack, allegedly as retaliation for its use in transporting Russian troops. In some cases, Australia–based operations of European organisations have been impacted.
Many cyber actors are involved in the conflict in offence and defence
The mix of state and non-state cyber actors participating in Russia’s war on Ukraine has added to an already complex cyberspace domain. While state actors were on the ‘cyber front’, particularly during the earlier stages of the conflict, there was significant activity by hacktivists from around the globe as the conflict progressed. Regardless of whether a malicious cyber actor was a state, state-sponsored, or a non-state actor acting of their own volition, the scale and frequency of malicious cyber activity during the conflict has challenged cyber defenders on all sides. For example, at least 8 variants of destructive malware were identified in the first 6 weeks of the conflict, including wiper malware designed to erase data or prevent computers from booting.
Both state and non-state cyber actors have been on the offensive and defensive. Ukraine’s networks have been resilient and have largely withstood sustained cyberattacks. Ukraine has said this resilience is due to robust defences developed following previous cyberattacks, as well as partnerships with private sector IT companies. For example, with the support of private companies, Ukrainian government data was migrated to cloud infrastructure, which assured continuity of government services. Private companies also rapidly released threat intelligence, like indicators of compromise, to assist cyber defenders to repel network attacks.
Threat intelligence that might impact Australian entities is obtained by ASD through international partners and shared through cyber.gov.au and ASD’s Cyber Security Partnership Program.
Cyber operations can cause disruption and destruction in conflict
While the conflict remains ongoing, there are many lessons Australia can learn from Russia’s war on Ukraine. The world is witnessing the destructive impact of cyber operations during conflict, or in the pursuit of a state’s national interests, and how a broad range of critical infrastructure can be disrupted as a result of malicious cyber activity. It also demonstrates the impact non-state participants can have in modern conflict. The conflict has exemplified how government and industry partnerships are critical to boosting national cyber security and resilience.
Case study 6: The CTIS community at work – KillNet
The Cyber Threat Intelligence Sharing (CTIS) platform, operated by ASD, was developed with industry, for Australian Government and industry partners to build a comprehensive national threat picture and empower entities to defend their networks. CTIS allows participating entities to share indicators of compromise (IOCs) bilaterally at machine speed. Participating entities can use these IOCs to identify and block activity on their own networks, and share IOCs observed on their own networks with other CTIS partners.
The number of partners using CTIS increased seven-fold over 2022–23:
- in July 2022 there were 32 CTIS partners (18 consuming, 14 contributing)
- in June 2023 there were 252 CTIS partners (165 consuming, 87 contributing)
- by the end of FY 2022–23, CTIS shared 50,436 pieces of cyber threat intelligence
- as of 2023, ASD is progressing a further 313 candidate organisations for on-boarding.
In March 2023, a CTIS partner shared almost 1,000 IP addresses relating to a distributed denial-of-service (DDoS) attack on an Australian organisation. The partner linked the DDoS attack to the malicious cyber actor KillNet, a well-known pro-Russian hacktivist group. Since Russia’s war on Ukraine began, KillNet’s focus had been primarily Europe; however, recent trends suggest a shift to countries abroad, including Australia and its critical infrastructure.
CTIS partner contributions help participants defend their networks, and inform ASD’s understanding of threat actors, their motives and their tactics, techniques, and procedures. This information also helps ASD to identify trends within and across sectors.
For more information on CTIS, visit cyber.gov.au and become a Network Partner. Existing Network Partners can register their interest in accessing CTIS by either clicking on the ‘Register your interest’ button via the ASD Partnership Portal, or by contacting [email protected] .
Chapter 4: Cybercrime
- Profit-driven cybercriminals continually seek new ways to maximise payment and minimise their risk, including by changing their tactics and techniques to mask their actions and extract payment from victims.
- Ransomware remains the most destructive cybercrime threat to Australians, but is not the only cybercrime. Business email compromise (BEC), data theft, and denial-of-service (DoS) continue to impose significant costs on all Australians.
- Building a national culture of cyber literacy, practicing good cyber security hygiene, and remaining vigilant to cybercriminal activity – both at work and at home – will help make it harder for cybercriminals to do business.
Cybercrime is big business and causes harm
Cybercrime is a multibillion-dollar industry that threatens the wellbeing and security of every Australian. Cybercrime covers a range of illegal activities such as data theft or manipulation, extortion, and disruption or destruction of computer-dependant services. In 2022–23, cybercrime impacted millions of Australians, including individuals, businesses and governments. These crimes have caused harm and continue to impose significant costs on all Australians.
The Australian Institute of Criminology (AIC) found, in its Cybercrime in Australia 2023 report, that individual victims and small-to-medium businesses experience a range of harms from cybercrime that extend beyond financial costs, such as impacts to personal health and legal issues. Cybercrime remains significantly underreported in Australia. The AIC’s report revealed that two-thirds of survey respondents had been victims of cybercrime in their lifetimes.
ASD needs community assistance to understand the cyber threat landscape. Australians are encouraged to report cyber security incidents and cybercrime to ReportCyber . ReportCyber is the Australian Government’s online cybercrime reporting tool coordinated by ASD and developed as a national initiative with state and territory police. ReportCyber may link Australians to other Australian Government entities for further support.
Cybercrime in 2022–23
The number of extortion-related cyber security incidents ASD responded to increased by around 8 per cent compared to last financial year.
Over 90 per cent of these incidents involved ransomware or other forms of restriction to systems, files or accounts.
ASD responded to 79 cyber security incidents involving DoS and DDoS , which is more than double the 29 incidents reported to ASD last financial year.
Cybercrime types
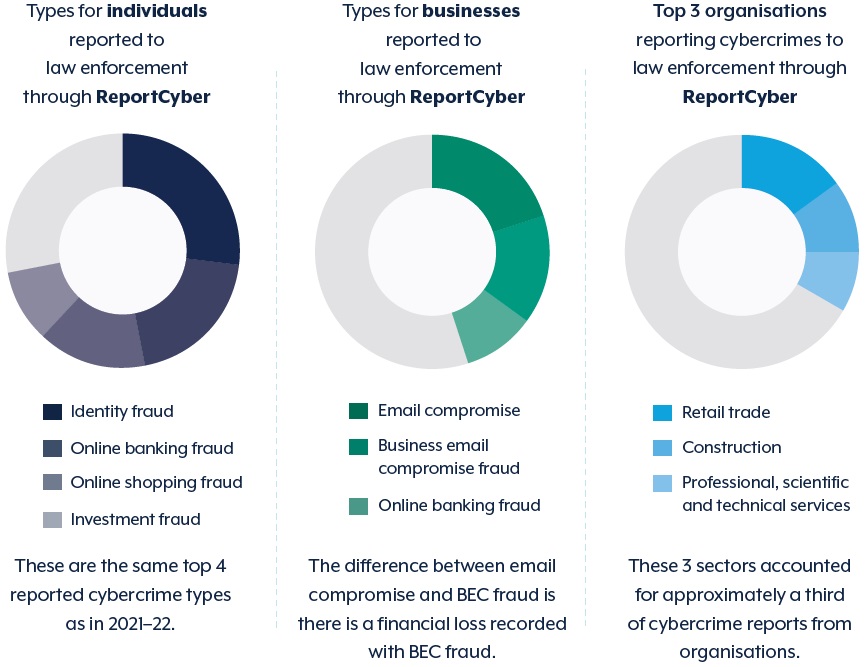
Cybercrime reports by state and territory
Australia’s more populous states continue to report more cybercrime. Queensland and Victoria report disproportionately higher rates of cybercrime relative to their populations. However, the highest average reported losses were by victims in New South Wales (around $32,000 per cybercrime report where a financial loss occurred) and the Australian Capital Territory (around $29,000).
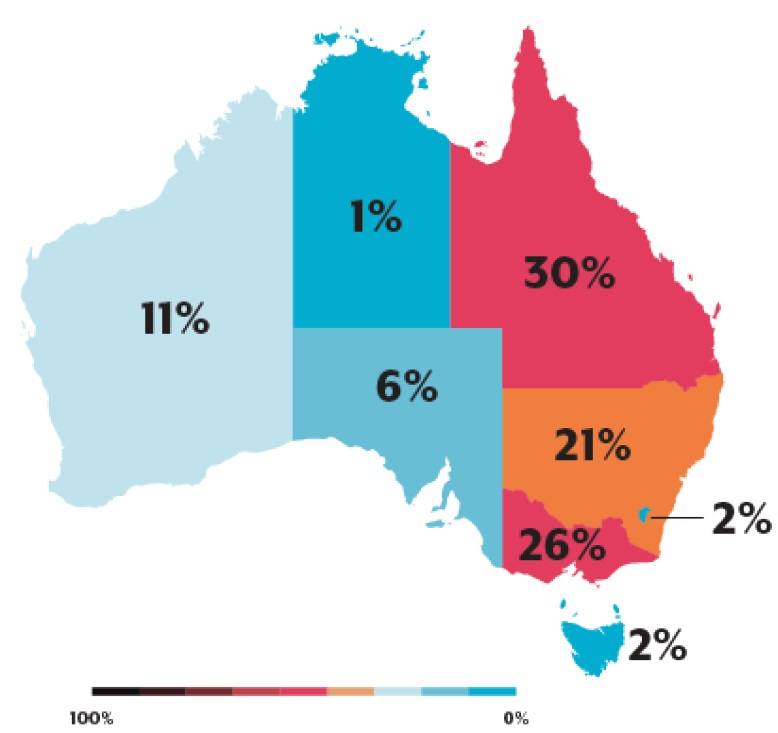
Figure 4: Breakdown of cybercrime reports by jurisdiction for FY 2022–23 Note: Approximately one per cent of reports come from anonymous reporters and other Australian territories. Data has been extracted from live datasets of cybercrime and cyber security reports reported to ASD. As such, the statistics and conclusions in this report are based on point-in-time analysis and assessment.
How criminals monetise access
Profit-driven cybercriminals continually seek new ways to maximise payment and minimise their risk, including by changing their tactics and techniques to mask their actions and extract payment from victims. Their targeting is largely opportunistic but can also be aimed at specific entities or individuals.
The professionalisation of the cybercrime industry means cybercriminals have been able to increase the scale and profitability of their activities. For example, initial access brokers sell their services and accesses to other malicious cyber actors who then use techniques, such as ransomware or data-theft extortion, to target victims. The accessibility of criminal marketplaces has also lowered the bar for entry into cybercrime, which has made cybercrime more accessible to a wide range of actors.
To gain initial access, cybercriminals may send multiple malicious links to a broad list of people (known as a phishing campaign), or scan for unpatched and misconfigured systems. Once they compromise a network, they may seek to move laterally through the network to gain access to higher-value systems, information or targets.
Cybercriminals may draw on a number of techniques to extract payment from victims, including employing multiple techniques at once – known as double or multiple extortion. While ransomware is a well-known technique, cybercriminals can monetise access to compromised data or systems in many different ways. They may scam a business out of money or goods, extort victims in return for decrypting data or non‑publication of data, on-sell compromised data or systems access for profit, or exploit compromised data or systems for future use.
Social engineering: how criminals get a foothold
Social engineering is a way in which cybercriminals can gain unauthorised access to systems or data by manipulating a person. They may do this by creating a sense of urgency or desire to help, or by impersonating a trusted source to convince a victim to click on a malicious link or file, or reveal sensitive information through other means – such as over the phone.
Phishing is one of the most common and effective techniques used by cybercriminals to gain unauthorised access to a computer system or network, and this activity may be indiscriminate or targeted. Once a victim engages with the malicious link or file, they may be prompted to provide personal details, or malware may run on their device to covertly retrieve this information. Cybercriminals may then use this information to steal money or goods, or leverage this information to access other accounts and systems of higher value.
Australians are becoming more aware of techniques dependent on social engineering, like phishing, but more can be done to build resilience:
- think twice before clicking on links from unsolicited correspondence
- verify the legitimacy of suspicious messages with the source via their official website or verified contact information, particularly if it is a request to transfer money or supply sensitive information. Visit the entity’s website directly, rather than via links in emails, SMS or other messaging services
- report unusual activity as quickly as possible to ReportCyber and Scamwatch
- educate staff on corporate-focused social engineering tactics and how to identify risk.
Explainer 5: Common cybercriminal techniques
Phishing is an attempt to trick recipients into clicking on malicious links or attachments to harvest sensitive information, like login details or bank account details, or to facilitate other malicious activity. Spear phishing is more targeted and tailored: cybercriminals may research victims using social media and the internet to craft convincing messages designed to lure specific victims.
Ransomware is a type of extortion that uses malware for data or system encryption. Cybercriminals encrypt data or a system and request payment in return for decryption keys. Ransomware-as-a-Service (RaaS) is a business model between ransomware operators and ransomware buyers known as ‘affiliates’. Affiliates pay a fee to RaaS operators to use their ransomware, which can enable affiliates with little technical knowledge to deploy ransomware attacks.
Data-theft extortion does not require data encryption, but cybercriminals will use extortion tactics such as threatening to expose sensitive data to extract payment. The added threat of reputational damage is intended to pressure a victim into complying with the malicious cyber actor’s demands.
Data theft and on-sale is when data is extracted for use by a cybercriminal for the purpose of on-selling the data (such as personal information, logins or passwords) for further criminal activity, including fraud and financial theft. Some malware known as an ‘infostealer’ can do this job for the cybercriminal.
Business email compromise (BEC) is a form of email fraud. Cybercriminals target organisations and try to scam them out of money or goods by attempting to trick employees into revealing important business information, often by impersonating trusted senders. BEC can also involve a cybercriminal gaining access to a business email address and then sending out spear phishing emails to clients and customers for information or payment.
Denial-of-service (DoS) is designed to disrupt or degrade online services, such as a website. Cybercriminals may direct a large volume of unwanted traffic to consume the victim network’s bandwidth, which limits or prevents legitimate users from accessing the website.
Ransomware is a destructive cybercrime
Ransomware remains the most destructive cybercrime threat in 2022–23 to Australian entities. ASD recorded 118 ransomware incidents – around 10 per cent of all cyber security incidents.
A quarter of the ransomware reports also involved confirmed data exfiltration, also known as ‘double extortion’, where the actor extorts the victim for both data decryption and the non-publication of data. Other ransomware actors claimed to have exfiltrated data, but it is difficult to validate these claims until data exfiltration is confirmed or the legitimacy of leaked data is confirmed.
Ransomware is deliberatively disruptive, and places pressure on victims by encrypting and denying access to files. A ransom, usually in the form of cryptocurrency, is then demanded to restore access. This can inhibit entities, particularly those that rely on computer systems to operate and undertake core business functions.
Customers may also be impacted if they rely on the goods or services from that entity, or if their data is impacted. For example, in January 2023, cybercriminals reportedly compromised the postal service in the UK, encrypting files and disrupting international shipments for weeks. In other instances, ransomware incidents have had cascading impacts, sparking panic buying, fuel shortages, and medical procedure cancellations.
ASD advises against paying ransoms. Payment following a cybercrime incident does not guarantee that the cybercriminals have not already exfiltrated data for on-sale and future extortion.
ASD’s incident management capabilities provide technical incident response advice and assistance to Australian organisations. Further information can be found in the How the ASD's ACSC Can Help During a Cyber Security Incident guide.
Case study 7: Ransomware in Australia
In late 2022, an Australian education institution was impacted by the Royal ransomware, which is likely associated with Russian-speaking cybercrime actors. Royal ransomware restricts access to corporate files and systems through encryption. Notably, it uses a technique called ‘callback phishing’, which tricks a victim into returning a phone call or opening an email attachment that persuades them to install malicious remote access software.
When the institution detected the ransomware, it shut down some of its IT systems to stop the spread, which resulted in limited service disruption. An investigation revealed that a limited amount of personal information of both students and staff was compromised. The institution notified affected individuals and reminded them to remain vigilant for suspicious emails or communication. The institution also advised all students and staff to reset their passwords and introduced an additional verification process for remote users.
An ICT manager from the institution said downtime from the incident was minimal due to an effective business continuity plan and access to regular backups, which were unaffected by encryption. After the incident, the institution began moving toward more secure data storage methods.
The ICT manager said the incident highlighted how ubiquitous data is in an enterprise environment. ‘There were no crown jewels affected, so to speak. Important data was spread across the network. This incident taught us some lessons in relation to account management, and the regular review and archival of data’.
In January 2023, ASD published to cyber.gov.au the Royal Ransomware Profile , which describes its tactics, techniques and procedures and outlines mitigations. The ransomware profile was informed by cyber threat intelligence that the education institution shared with ASD.
Sectors impacted by ransomware-related cyber security incidents
The professional, scientific and technical services sector reported ransomware-related cyber security incidents most frequently to ReportCyber in 2022–23, followed by the retail trade sector, then the manufacturing sector. These 3 sectors accounted for over 40 per cent of reported ransomware-related cyber security incidents.
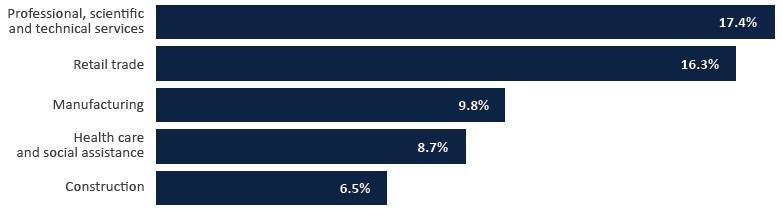
Table 5: Top 5 sectors reporting ransomware-related incidents in FY 2022–23 (ReportCyber data)
Entities should consider how a ransomware incident could impact their business and their customers. To help prevent a ransomware attack, it is important to secure devices by turning on multi-factor authentication (MFA), implementing access controls, performing and testing frequent backups, regularly updating devices, and disabling Microsoft Office macros. It is also equally important to practice incident response plans to minimise the impact in the event of a successful ransomware incident.
Business email compromise is lucrative
BEC is an effective and lucrative technique that exploits trust in business processes and relationships for financial gain. Cybercriminals can compromise the genuine email account of a trusted sender, or impersonate a trusted sender, to solicit sensitive information, money or goods from businesses partners, customers or employees.
For example, a cybercriminal may gain access to the email account of a business and send an invoice with new bank account details to a customer of that business. The customer pays the invoice using the fraudulent bank account details provided by the cybercriminal, which is often thousands of dollars. A compromised business may only detect BEC once a customer has paid cybercriminals.
In 2022–23, the total self-reported BEC losses to ReportCyber was almost $80 million. There were over 2,000 reports made to law enforcement through ReportCyber of BEC that led to a financial loss. On average, the financial loss from each BEC incident was over $39,000.
Before replying to requests seeking money or personal information, look out for changes such as a new point-of-contact, email address or bank details. Simple things like calling an existing contact or the trusted sender to verify a request for money or change of payment details can help to prevent BEC.
Explainer 6: Business email compromise advice
Organisations should implement clear policies and procedures for workers to verify and validate requests for payment and sensitive information. Additionally:
- Register additional domain names to prevent typo-squatting – cybercriminals may create misleading domain names based on common typographic errors of a website, hoping its customers do not notice. Further information on Domain Name System Security for Domain Owners is available at cyber.gov.au.
- Set up email authentication protocols business domains – this helps prevent email spoofing attacks so that cybercriminals cannot wear a ‘digital mask’ pretending to be legitimate.
ASD has published the Preventing Business Email Compromise guide to help Australian organisations understand and prevent BEC.
Case study 8: Scams in Australia
In April 2023, the Australian Competition and Consumer Commission (ACCC) released its Targeting Scams report . The report, which compiles data reported to the ACCC’s Scamwatch, ReportCyber, the Australian Financial Crimes Exchange, IDCARE and other government agencies, provides insight into the scams that impacted Australians in 2022. The report also outlines some of the activities by government, law enforcement, the private sector and community to disrupt and prevent scams.
The Targeting Scams report revealed Australians lost over $3 billion to scams in 2022. This is an 80 per cent increase on total losses recorded in 2021.
Investment scams were the highest loss category ($1.5 billion), followed by remote access scams ($229 million) and payment redirection scams ($224 million).
The most reported contact method used by scammers was text message; however, scam phone calls accounted for the highest reported losses. The second highest reported losses were from social media scams.
Older Australians lost more money to scams than other age groups with those aged 65 and over losing $120.7 million, an increase of 47.4 per cent from 2021. First Nations Australians, Australians with disability, and Australians from culturally and linguistically diverse communities each experienced increased losses to scams when compared with data from 2021.
On 1 July 2023, the Government launched the National Anti-Scam Centre. The Anti-Scam Centre will expand on the work of the ACCC’s Scamwatch service and bring together experts from government agencies, the private sector, law enforcement, and consumer groups to make Australia a harder target for scammers.
Hacktivists are using cyberattacks to further their causes
Hacktivism is used to describe a person or group who uses malicious cyber activity to further social or political causes, rather than for financial gain.
These malicious cyber actors, which include issue-motivated groups, are typically less capable, less organised, and less resourced than other types of malicious cyber actors. That said, even rudimentary disruptive activity – such as website defacement, hijacking of official social media accounts, leaking information, or DoS – can cause significant harm, reputational damage, and operational impacts to targeted entities.
Like cybercriminals, hacktivists may leverage malicious tools and services online to gain new capabilities and improve their ability to degrade or disrupt services for their cause.
Case study 9: Australian critical infrastructure targeted by issue-motivated DDoS
In March 2023, ASD became aware of reports of issue-motivated groups (hacktivists) targeting Australian organisations. Open source reporting linked the targeting of over 70 organisations to religiously motivated hacktivists.
The malicious activity commenced on 18 March with the defacement of, and/or DDoS against, the websites and other internet-facing services of small-to-medium businesses. This progressed to DDoS activity targeting the websites of Australian critical infrastructure entities, with multiple hacktivist groups announcing support for the campaign and publishing ‘target lists’ across a variety of platforms.
ASD received several incident reports from organisations experiencing hacktivist activity, including critical infrastructure providers. However, there was no impact on critical infrastructure operations, as only public-facing websites were affected. ASD provided advice and support to organisations, including by identifying IP addresses related to the attacks. ASD also shared indicators of compromise with its Network Partners.
In addition to ASD support, critical infrastructure providers worked closely with commercial incident-response providers and their in-house incident-response teams. One critical infrastructure provider identified through open source research that a second DDoS attack was being planned against their servers.
To prevent this attack, administrators enabled geo-blocking – where traffic from specific geolocations known to be used by the malicious cyber actor were blocked – to limit malicious traffic. This simple tactic helped the organisation avoid a second attack. As a result, the organisation did not suffer from any additional downtime.
ASD urges organisations to report all incidents – even those with minimal impact on operations – to enhance national situational awareness, especially of coordinated malicious activity. Your report to ASD could help prevent or defend against an attack on other Australian networks.
Denial-of-service operations are designed to disrupt
DoS attacks disrupt or degrade online services such as websites and email, and are another tactic used by cybercriminals and hacktivists. This technique causes access or service disruption to the victim, sometimes to pressure them into payment or to highlight a cause.
In these attacks, an online service is overwhelmed by so many illegitimate requests that it loses capacity to serve real users. DoS can also be achieved by hijacking an online service to redirect legitimate users to other services controlled by malicious cyber actors. In some instances, DDoS attacks can use huge numbers of ‘zombie’ computers or bots (hijacked by malware), to direct large volumes of unwanted network traffic to a web service.
ASD recorded 79 DoS and DDoS cyber security incidents in 2022–23, with service availability partly or wholly denied for the victim in 62 of those incidents. The remainder of the incidents had no impact on the victim. Entities who maintained situational awareness of DoS threats and proactively implemented mitigations were reportedly less impacted by subsequent DoS.
Although entities cannot avoid being targeted, they can implement measures to prepare for and reduce the impact of a DoS attack. This includes using DDoS protection services and exercising incident response and business continuity plans.
Defence against cybercrime
Both individuals and organisations can take simple steps to help build their cyber security. Many of these steps can often prevent initial access by cybercriminals.
- enable multi-factor authentication (MFA) for online services when available
- use long unique passphrases for every account if MFA is not available, particularly for services like email and banking (password managers can assist with such activities)
- sign up for ASD’s free Alert Service
- review the cyber security posture of remote workers including their use of communication, collaboration and business productivity software
- implement relevant guidance from ASD’s Essential Eight Maturity Model , Strategies to Mitigate Cyber Security Incidents and Information Security Manual
ASD has published a range of guides at cyber.gov.au to support Australians and Australian organisations in building their cyber resilience, including how to defend against ransomware attacks, and how to detect socially engineered messages, phishing emails and texts.
Chapter 5: Cyber enabled data breaches
- During FY 2022–23, ASD received an increase in data breach reports as millions of Australians had their information compromised through significant data breaches.
- Malicious cyber actors stole data by using valid account credentials or by exploiting internet-facing applications.
- Sensitive data should be deleted or de-identified when it is no longer needed or required. Organisational policies and processes should consider how to protect gathered and generated data.
Data ubiquity
Data is valuable to malicious cyber actors as data and data flows underpin almost every modern technology and digital service. During 2022–23, millions of Australians had their private information compromised through significant data breaches, and some Australians were exposed to multiple breaches.
A data breach occurs when information is shared with, or is accessed by, an unauthorised person or third party. Isolation and remediation of the breach could cost millions of dollars. The complete recovery cost is hard to quantify, but could include losses due to productivity, legal action and reputational damage. An entity’s customers or staff could experience harm from a data breach if their private information is used by criminals for cyber or other fraud or scams, including identity theft. Protecting data, particularly sensitive personal information, is vital for the safety of the community, the prosperity of business, and the nation’s security.
Explainer 7: Vital data
Organisations should consider what data is vital to their operations, and individuals should consider what data might affect their privacy.
Data can take many forms such as personal information. Personal information includes a broad range of information, or an opinion, that could identify an individual. It can encompass things such as an individual’s name, date of birth, drivers licence or passport details, phone number, home address, health records, credit information, mobile device location history, and voiceprint and facial recognition details.
Other forms of data could include sensitive financial information, corporate emails, intellectual property and research, or strategic business plans. Information associated with network telemetry and endpoint security information, or machine learning models, also generate potentially useful information which can be exploited by malicious cyber actors.
Data breach incidents in Australia
During 2022–23, many data breaches reported to ASD involved cybercriminals stealing customer personal information from organisations to support extortion activities. Organisations should be aware that a data breach could be a precursor to the destruction or encryption of data.
Of the cyber security incidents recorded by ASD during 2022–23, 150 were data breaches, making up around 13 per cent of all incidents. Compared to 2021–22, this is up from 81 data breaches or 7 per cent of all incidents. Data breaches were the third most common incident type in 2022–23, behind compromised infrastructure (15.2 per cent) and compromised credentials (18.8 per cent).
Phishing, a tactic whereby a user is induced to open a malicious email attachment or to visit a compromised website, was commonly used to steal credentials. Malicious cyber actors also obtained credentials from unrelated cyberattacks and breaches. ASD’s incident data showed an extensive network compromise almost always occurred when a malicious cyber actor successfully accessed privileged accounts.
In 2022–23, ASD responded to a number of data breaches that involved common characteristics and intrusion chains. Broadly, these incidents demonstrated either:
- opportunistic intrusions involving a malicious actor exploiting a single internet-facing application or service which contained data. Actors typically used a ‘smash and grab’ technique to steal data directly from this single initial access vector
- complex intrusions involving a malicious actor demonstrating a wider variety of techniques after initial access as they escalated privileges, and moved laterally seeking data to exploit. These intrusions resulted in more extensive network compromise. Generally, incidents where malicious actors successfully compromised privileged accounts also resulted in more complex intrusions and extensive incidents.
Diving deeper into data breaches
ASD conducted a detailed analysis of data breach incidents between 1 November 2021 and 30 October 2022. Analysis revealed the average amount of data reported to have been exfiltrated during a breach was around 120 gigabytes, with the highest reported amount being around 870 gigabytes. Table 6 outlines the top information types exposed during a breach.
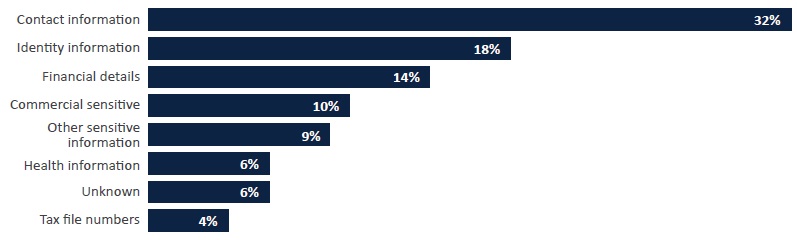
Table 6: Types of information stolen in data breaches Note: some incidents included the breach of multiple types of information.
Different types of information may carry different risks. For example, health information is likely to be more sensitive than contact information and will require greater protection. Table 6 indicates contact information was breached most frequently, likely because this type of data is widely collected and has increased exposure.
During the same analysis period, 41 per cent of data breaches involved malicious cyber actors exploiting valid accounts and credentials to access cloud services, local systems, or entire networks. Malicious cyber actors commonly used brute-force attacks to take advantage of simple and re-used passwords to access accounts, or used phishing to obtain credentials.
Around 34 per cent of data breaches involved exploitation of internet-facing applications. Common vulnerabilities and exposures (CVEs) were often exploited, and so was human misconfiguration of devices like unsecured application programming interfaces, or common bugs and flaws in software; for example, insecure direct object references.
To help Australian organisations, the ASD has published the Preventing Web Application Access Control Abuse advisory.
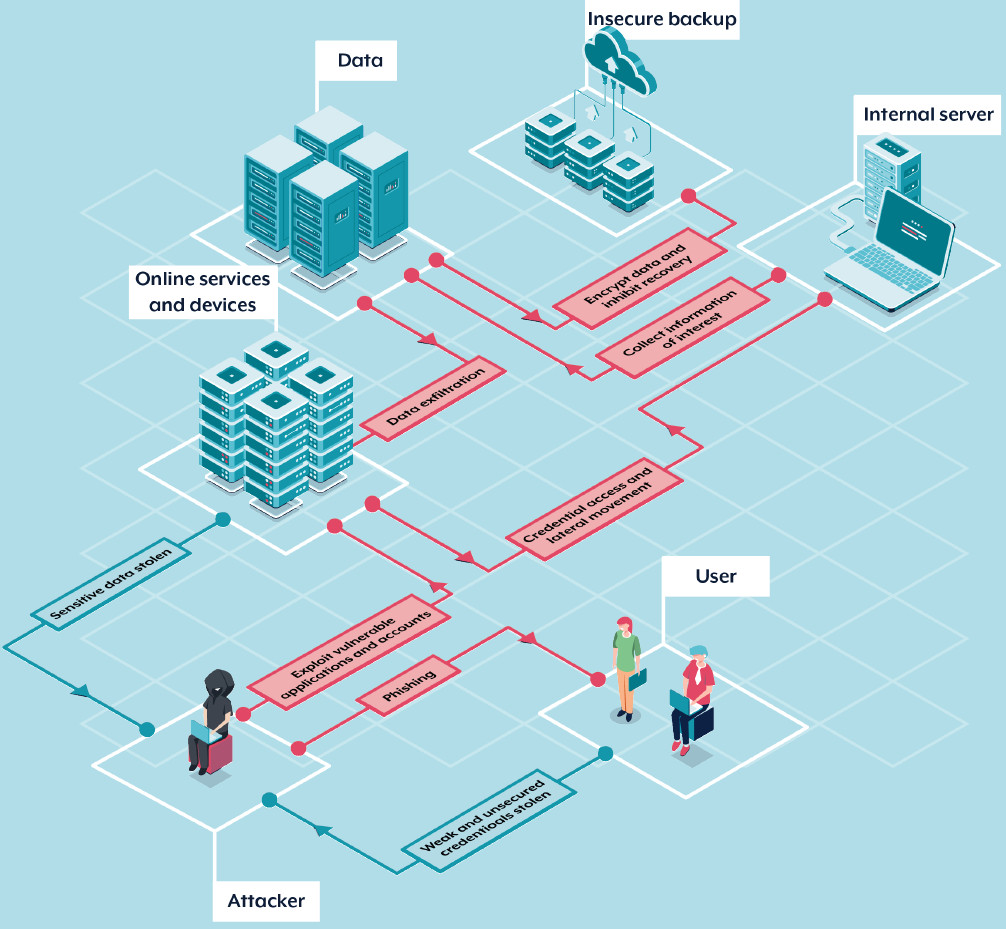
Figure 5 : Anatomy of a data breach
To steal data from an organisation, malicious cyber actors will commonly exploit online services and internet-facing devices, or penetrate a network’s perimeter using stolen or easily guessed credentials. Once inside a network, malicious actors will often attempt to escalate their privileges, move laterally across a network to find data to steal and/or other systems to exploit, and then attempt to exfiltrate data back through the network perimeter.
Stolen data for nefarious use
Different malicious cyber actors have differing motivations for stealing data. For example, cybercriminals may use stolen data, particularly personal information, as a basis for identity theft or to conduct phishing campaigns for financial gain. State actors are also interested in personal information, among other data types, although this is more likely for espionage purposes rather than financial gain. Irrespective of motivation, the impacts of data breaches on victims are actor agnostic – Australians can be exposed to harm and organisations can experience losses.
Data stolen by cybercriminals typically ends up on the dark web marketplaces where it can be shared, bought, and sold by other malicious cyber actors. For example, stolen credentials may end up with initial access brokers who specialise in dealing stolen usernames and passwords. Malicious cyber actors can also piece together seemingly innocuous information like an email address, a date of birth, or a phone number to target someone for spear phishing, fraud, or to leverage that person to gain other privileged accesses and information.
Once exposed, some data can be used in perpetuity for future crime, particularly in cases of identity theft, blackmail, or extortion. A victim’s real name and home address can be difficult to change, unlike stolen credentials which are easily updated.
ASD has also received reports of cyber security incidents in which threat actors claimed to have exfiltrated data; however, subsequent investigations have not identified evidence of exfiltration. While a threat actor’s assertion of data exfiltration may be an attempt to elevate urgency or pressure affected entities, it remains important to thoroughly investigate evidence to support or counter the claim.
Case study 10: Operation GUARDIAN
On 28 September 2022, the Australian Federal Police’s Joint Policing Cybercrime Coordination Centre (JPC3) commenced Operation GUARDIAN to coordinate efforts to protect those at higher risk of financial fraud and identity theft as a result of the Optus data breach.
Since the Optus incident, Operation GUARDIAN has expanded to include the Medibank, MyDeal, Latitude, and the Go-Anywhere data breaches. Some breaches have resulted in the exposure of personal information and sensitive data of Australians.
The purpose of Operation GUARDIAN is to monitor, disrupt and prosecute any person misusing personal information exposed as a result of data breaches. It aims to deter criminals from using data for malicious purposes and to educate the public.
Operation GUARDIAN works with the public and private sectors to search the internet and known criminal online sites to identify exposed personal information and those who are attempting to buy or sell it.
Case study 11: Awareness and impact of data breaches in the Australian community
According to the Office of the Australian Information Commissioner’s Australian Community Attitudes to Privacy Survey (ACAPS) 2023 , three-quarters (74 per cent) of Australians believe that data breaches are one of the biggest privacy risks they face today, and a quarter (27 per cent) said it is the single biggest risk to privacy in 2023.
Almost half (47 per cent) of Australians said they had been told by an organisation that their information was involved in a data breach in the prior year, and a similar proportion (51 per cent) know someone who was affected by a breach.
Three-quarters (76 per cent) of those whose data was involved in a breach said they experienced harm as a result. More than half (52 per cent) reported an increase in scams or spam texts or emails. There were 3 in 10 (29 per cent) who said they had to replace key identity documents, such as drivers licences or passports. Around 1 in 10 experienced significant issues such as emotional or psychological harm (12 per cent), financial or credit fraud (11 per cent) or identity theft (10 per cent).
Nearly half (47 per cent) of Australians said they would close their account or stop using a product or service provided by an organisation that experienced a data breach. However, most Australians are willing to remain with a breached organisation provided that organisation promptly takes action, such as quickly putting steps in place to prevent customers experiencing further harm from the breach (62 per cent) and making improvements to their security practices (61 per cent). Only 12 per cent of Australians said there is nothing an organisation could do that would influence them to stay after a data breach.
There are a range of ways organisations can protect personal information. A quarter (26 per cent) of Australians believe the most important step is for organisations to collect only the information necessary to provide the product or service. Australians view the second most important thing organisations can do is take proactive steps to protect the information they hold (24 per cent).
The OAIC commissioned Lonergan Research to undertake ACAPS 2023. The survey was conducted in March 2023 with a nationally representative sample of 1,916 unique respondents aged 18 and older. To read the full report visit oaic.gov.au/acaps .
Mitigating data breaches
Implementing ASD’s Essential Eight, and the Open Web Application Security Project (OWASP) Top Ten Proactive Controls will help protect data by minimising the risks to systems and networks, online services and internet-facing devices. At least fortnightly, organisations should use an automated method to scan for security vulnerabilities and apply timely patches or mitigations to minimise risks. Other effective controls to help mitigate data breaches include:
- deploy multi-factor authentication (MFA) to mitigate stolen credential abuse
- enforce strong passphrase policy to secure accounts
- block internet-facing services that are not authorised to be internet-facing
- immediately decommission unnecessary systems and services
- configure server applications to run as a separate account with the minimum privileges to mitigate account abuse
- mandate user training to recognise phishing or social engineering attempts.
Encryption can further protect data that is stored or in transit between systems. For example, sensitive data about former customers that must be legally retained should be encrypted and stored offline, inaccessible to the internet. Data communicated between database servers and web servers, especially over the internet, are susceptible to compromise and should be encrypted. Further guidance about how organisations can protect data is contained within ASD’s Information Security Manual .
The most cyber resilient organisations have a well-thought-out and exercised cyber incident response plan that includes a data breach response plan or playbook. A robust plan will help organisations respond to a data breach, rapidly notify relevant organisations and individuals to minimise the risk of harm, restore business operations, comply with relevant obligations, and reduce the costs and potential reputational damage that may result from a breach.
Organisations should include a strategy for communicating with customers in their cyber incident response plan, and consider how to protect customers from, and assist with, the consequences of a breach. For example, organisations can inform their customers whether or not hyperlinks will be used in their communications after a breach – or at all – to help them avoid falling prey to phishing attempts.
ASD has published guidance on cyber.gov.au, like the Guidelines for Database Systems to help organisations enhance database security.
Chapter 6: Cyber resilience
- Cyber resilience is helping to ensure an entity is resistant to cyber threats. For enterprise, this includes organisation-wide cyber risk management and consideration of third-party risks, such as vendors, service providers, and new technologies.
- Artificial intelligence (AI) has great benefits to organisations but also poses security challenges; a risk-based approach to using AI within ICT environments as per other services is recommended.
- Invest in prevention, response and recovery to reduce the impact of a compromise and build the resilience of Australian systems.
- Practice good cyber hygiene at work and at home. Enable multi-factor authentication (MFA), use unique passphrases, enable automatic updates, regularly back up important data, and report suspicious cyber activity.
- Cooperation on a national scale is one of Australia’s greatest advantages against malicious cyber activities. Keep up to date at cyber.gov.au, and engage with ASD’s Cyber Security Partnership Program to help build the nation’s collective cyber resilience.
Digital supply chains increase the attack surface
Most entities have some component of their ICT outsourced to a third party, such as hardware supply, web and data hosting, and software-as-a-service or other enterprise resource planning tools.
According to the Australian Bureau of Statistics’ Characteristics of Australian Business data, during 2021–22, around 85 per cent of Australian businesses used ICT, and 59 per cent used cloud technology. These measures have been trending up year-on-year.
During 2022–23, ASD published a number of alerts warning Australians about vulnerabilities relating to products commonly found in ICT supply chains, like Citrix Gateway and Application Delivery Controller devices. During March 2023, ASD published an alert describing a supply chain compromise affecting multiple versions of the 3CX DesktopApp – a popular voice-over-IP application.
While an entity can outsource ICT functions to access specialist skills, increase efficiency, and lower costs, it must still manage and be accountable for cyber security risk. ICT supply chain expansion can increase the attack surface, particularly as there may be varying levels of cyber security maturity among both customers and suppliers.
A malicious cyber actor can compromise numerous victims at scale by targeting a single upstream or third‑party supplier. An ICT supply chain attack comprises 2 attacks: an initial attack on a supplier, and a subsequent attack on its customers. For example, a managed service provider (MSP) might have privileged network access to hundreds of customers or hold huge amounts of sensitive data. After compromising an MSP, a malicious cyber actor could then exploit the MSP’s privileged network accesses, or steal sensitive data to extort its customers directly. This highlights that, while an entity might have leading-edge cyber defences, its security posture will only be as strong as its weakest link, which may be in its ICT supply chain.
To conduct an ICT supply chain attack, malicious cyber actors will commonly abuse misconfigurations in devices and the trust between supplier services and customer networks, conduct phishing attacks, and exploit common vulnerabilities and exposures (CVEs). Figure 6 outlines some of the common adversary goals and techniques associated with ICT supply chain attacks.
Defeating ICT supply chain threats requires effort from both customers and suppliers. The most effective measures combine both business and technical controls conducted at the earliest stage of ICT procurement or development. While a downstream customer may have no influence over their supplier’s security posture, they can improve their own cyber security to help mitigate risks. Suppliers should prioritise the secure-by-design and secure-by-default principles to improve their own product security and therefore their customers’ security.
Customers should clearly state cyber security expectations upfront as part of any contract, such as requiring that a supplier meet particular cyber security standards. Entities should appraise their suppliers of their risk tolerances, and might want to ask how the supplier will demonstrate good security practices, justify their product’s accesses and privileges, and guarantee genuine product delivery. Entities should also consider whether their supplier may be subject to foreign control or interference.
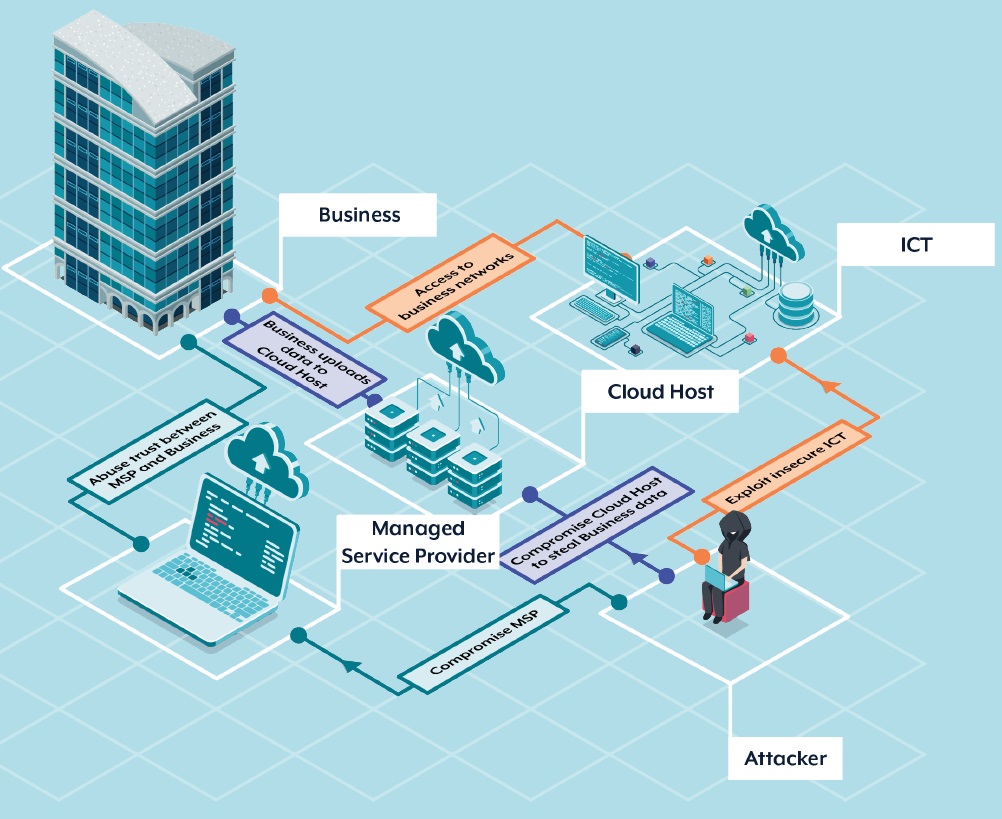
Figure 6 : ICT supply chain threats
Australian organisations face many cyber threats, including from the ICT supply chain. Malicious cyber actors who target upstream suppliers, such as by compromising a cloud host, may be able to impact downstream customers by exploiting the trust between that supplier and its customers. An attacker could then conduct data theft and extortion activities, or other attacks like denial-of-service. An organisation’s cyber security posture is only as strong as its weakest link, which could be an entity in its ICT supply chain.
Mitigating ICT supply chain threats
Organisations can boost their ICT supply chain defences in many ways, including by implementing ASD’s Essential Eight. The most effective technical controls to mitigate risks combine both mitigation and detection techniques, and are supported by a positive organisation-wide cyber secure culture. Some controls for both customers and suppliers include:
- deploy MFA to mitigate stolen credential abuse
- regularly scan for vulnerabilities and update software to minimise risks from vulnerabilities
- segment networks and enforce account management to isolate critical systems
- correctly configure software to minimise security risks
- use network and endpoint detection systems to identify malicious traffic and files
- monitor logon and network logs to detect unusual activity
To help Australian organisations, ASD has published guidance, available at cyber.gov.au such as Identifying Cyber Supply Chain Risks , Cyber Supply Chain Risk Management , Guidelines for Procurement and Outsourcing , and Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Security-by-Design and Default .
Secure-by-design and secure-by-default products
Secure-by-design products are those where the security of the customer is a core business goal, not just a technical feature, and start with that goal in mind before development. Secure-by-default products require little to no configuration changes out of the box to ensure security features are enabled.
Together, these approaches move much of the burden of staying secure to the manufacturers, which reduces the chances that customers will fall victim to security incidents resulting from misconfigurations, insufficiently fast patching, or many other common issues at the user end.
Entities are encouraged to prioritise secure-by-design and secure-by-default products in procurement processes, and collaborate with industry peers and manufacturers to help improve upcoming security initiatives in products. Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Security-by-Design and Default , offers further advice to software manufacturers and customers.
Artificial intelligence cyber security challenges
In early 2023, AI tools were among the fastest growing consumer applications globally. Broadly, AI is a collection of methods and tools that enable machines to perform tasks that would ordinarily require human intelligence. AI tools are increasingly being used to augment human activities like sorting large data sets, automating routine tasks, and assisting visual design work.
Machine learning (ML) is a sub-discipline of AI encompassing models that use feedback mechanisms to update model behaviour. ML models are typically used to make classifications and predictions, and to uncover patterns or insights in large data sets that may be impossible for a human to spot.
Over the last 3 years, the practical applications for AI have expanded, the costs have come down, and AI tools are more accessible than ever. Australians already interact frequently with AI, as AI drives internet searching, shopping recommendations, satellite navigation, and can aid complex activities like logistics management, medical diagnosis, and cyber security. AI tools can be used to provide human-like customer responses for help desks or call centres, and can help predict upcoming maintenance for industrial equipment.
While AI has benefited the economy and society, it has also created new challenges and data security risks. As AI becomes increasingly integrated into business environments and ICT infrastructures, additional and potentially unforeseen risks could be introduced. And, like any tool, AI can be misused either inadvertently or deliberately.
In 2022, a medical research collaboration for a pharmaceutical company trained an AI model using ML techniques to catalogue thousands of molecules for therapeutic use while discarding toxic molecules. While the researchers were able to catalogue many beneficial molecules, the researchers also wanted to know how AI could be misused. So they changed the AI model to find toxic rather than safe molecules. Using open source data, their AI model generated over 40,000 potentially lethal molecules in less than 6 hours.
Security researchers have also shown how data sets used for ML can be attacked and ‘poisoned’ with anomalous data to produce misleading outputs. In 2016, Microsoft abruptly ended testing of a chatbot after a subset of its users deliberately provided data containing misinformation and abusive material, resulting in offensive text being produced by the chatbot.
Malicious cyber actors could also use AI tools to augment their activities. For example, a cybercriminal may be able to produce low effort, high quality material for phishing attacks. AI could also be used to create fraudulent deepfake content like voice and video clips, or to create malware. Security researchers have demonstrated with existing technologies that malicious actors could use AI to help orchestrate cyber intrusions.
AI tools may also challenge the protection of sensitive information. For example, AI tools that produce or summarise text may not guarantee data privacy if it is fed sensitive or proprietary information. Additionally, using sensitive information for AI models and ML may contravene privacy laws, policies, or rules in some instances.
As online adversaries can use AI tools, so too can system defenders. AI can sort through large volumes of logs or telemetry data to look for malicious behaviour, identify malware, detect and block exploitation attempts, or derive intelligence insights. AI can also help triage information and automate security tasks, so humans can focus on other problems.
Entities wanting to adopt AI tools should treat them with the same care as any other ICT service, use a risk-based approach to procurement, and consider:
- if the AI tool is secure-by-design and secure-by-default, including its ICT supply chain
- if there are inaccuracies in the AI tool’s model or bias in its algorithms
- how the AI tool will be protected from misuse and interference (including foreign)
- how the AI tool will affect the entity’s privacy and data protection obligations
- how the AI tool will support, rather than outsource, human decision-making
- who is accountable for oversight or if something goes wrong with the AI tool.
Explainer 8: Ethical AI at ASD
In early 2023, ASD published the Ethical AI in ASD statement, which outlines ASD’s framework of ethical principles governing AI usage. This includes:
- lawful and appropriate use of AI consistent with the legislation, policies, processes and frameworks that govern ASD’s functions and protect the privacy of Australian citizens
- enabling human decision-making, allowing our workforce and customers to make informed decisions based on AI system outputs, and to maintain trust in AI systems
- reliable and secure AI, ensuring that technologies continue to meet their intended purpose and remain protected from external interference
- accurate and fair AI mitigating against unintended bias
- accountable, transparent and explainable AI allowing human oversight and control, with clear accountabilities enacted for all stages of the AI development lifecycle, facilitating appropriate and proportionate operations.
Ensuring remote work cyber security
Many organisations rapidly adopted new remote work solutions to support business continuity as a result of the COVID-19 pandemic. The number of Australian companies advertising remote work post-pandemic continues to grow, and it is clear that remote work will be an ongoing feature of many organisations and an expectation of many employees.
Some hastily implemented remote working solutions may not have fully considered cyber security implications. For example, bring-your-own-device policies are popular with organisations, but could introduce additional information management risks to corporate networks if not appropriately managed.
During 2022–23, ASD recorded extensive corporate network breaches that stemmed from employees conducting work from compromised personal devices. In 2022, US company LastPass suffered a data breach due to credentials being stolen via keylogger malware installed on the home computer of one of its employees.
Remote work often relies on employees using their own devices like home computers and internet routers, which usually have limited security features and less secure default settings when compared to enterprise products used in corporate environments. Internal corporate networks could be exposed to the internet directly via a remote employee’s home router, if that home router is misconfigured. Adding to the risks, employees may not regularly update their personal devices or use anti malware software, may access dubious websites or use illegal software, or may have failed to change the default credentials of their devices.
Malicious cyber actors are known to compromise common small-home-office products and internet-of-things devices to steal sensitive information, target corporate networks, or to enslave them into botnets for distributed-denial-of-service (DDoS) attacks.
Organisations should consider how cyber security mitigations for remote solutions are implemented, maintained, and audited. Organisations should also verify that policies are in place to ensure staff know how to securely use systems, and to ensure compliance with legal obligations like the protection of sensitive data.
ASD has published a number of guides at cyber.gov.au including G uidelines for Enterprise Mobility , Remote Working and Secure Mobilit y and Risk Management of Enterprise Mobility (including Bring Your Own Device) .
Explainer 9: Working from home and cybercrime
The Australian Institute of Criminology’s Cybercrime in Australia 2023 report examined whether working from home was a risk factor for cybercrime victimisation. Small-to-medium business owners who transitioned to working from home due to public health measures associated with the COVID-19 pandemic were 1.4 times as likely to be a victim of identity crime and misuse, 1.2 times as likely to be a victim of malware attacks and 1.3 times as likely to be a victim of fraud and scams.
There are various reasons that moving to remote working may have increased the likelihood of cybercrime victims. For a business working remotely, home internet connections may be less secure, devices may no longer be protected by corporate security controls or routine maintenance, and there may be a tendency to store or share sensitive work information on unsecure personal devices.
Cyber security through partnerships
The speed with which cyber threats spread and evolve means that no single entity can effectively defend against all threats in isolation. Cooperation on a national scale is one of Australia’s greatest advantages against malicious cyber activity.
It is vital cyber security incidents are reported to ASD to help build a national cyber threat intelligence picture, which better supports Australian organisations and individuals through informed guidance and mitigation advice. There are many other ways in which Australian organisations can engage with ASD.
ASD’s Cyber Security Partnership Program enables Australian entities to engage with ASD and fellow partners, drawing on collective understanding, experience, skills and capability to lift cyber resilience across the Australian economy. ASD’s Cyber Security Partnership Program is delivered through ASD’s state offices located around Australia.
An ASD Network Partnership is available to organisations with responsibility for the security of a network or networks (either their own or on behalf of customers) as well as academic, research and not-for-profit institutions with an active interest and expertise in cyber security. An ASD Business Partnership is available to those with a valid Australian Business Number. Individuals and families can sign up to the ASD Home Partner Program.
By strengthening our ties with agencies like ASD and broader cyber security partners within the transport and logistics sector, the Toll Group is proud to contribute to building resilient supply chain capability in Australia and around the world. ASD’s partnership, training, and participation in industry forums have been of tremendous value in promoting strong cyber security practices and cooperation across government and critical services, which our teams continue to benefit from. – Toll Group
The National Exercise Program (NEP) helps critical infrastructure and government organisations validate and strengthen Australia’s nationwide cyber security arrangements. The program uses exercises and other readiness activities that target strategic decision-making, operational and technical capabilities, strategic engagement and communications.
The Critical Infrastructure Uplift Program (CI-UP) assists Australian critical infrastructure organisations to improve their resilience against cyberattacks, with a focus on critical infrastructure assets and operational technology environments. As an intelligence-driven program, CI-UP focuses on improving the cyber security of critical infrastructure in a range of areas, including:
- enhancing visibility of malicious cyber activity and awareness of vulnerabilities
- enhancing the ability to contain and respond to an incident
- furthering culture and cyber maturity.
The Cyber Threat Intelligence Sharing Platform (CTIS) shares indicators-of-compromise in real‑time, within a growing community of Australian government and industry partners. CTIS also supports community partners to share their threat intelligence. Co-designed with industry, CTIS alerts security operations centre analysts to threats targeting Australian organisations.
AARNet has been engaged with the CTIS project from its inception and has seen firsthand the value of industry and government partnerships for threat intelligence sharing. By sharing information, the breadth and depth of our visibility of unwanted cyber attention is much greater. – AARnet
The Australian Protective Domain Name System (AUPDNS) is an opt-in security service available to all federal, state and territory government entities to protect infrastructure from known malicious activity. Information from AUPDNS directly assists ASD’s mission to build a national cyber threat picture, which in turn is shared with ASD partners, including individuals, businesses, academia, not-for-profits, and government entities.
The Cyber Hygiene Improvement Programs (CHIPs) track and monitor the cyber security posture of the internet-facing assets of entities at all levels of government. CHIPs also conducts High-priority Operational Tasking (HOT) CHIPs scans when potential cyber threats emerge, such as newly disclosed vulnerabilities. CHIPs builds visibility of security vulnerabilities across governments and provides notifications to system owners.
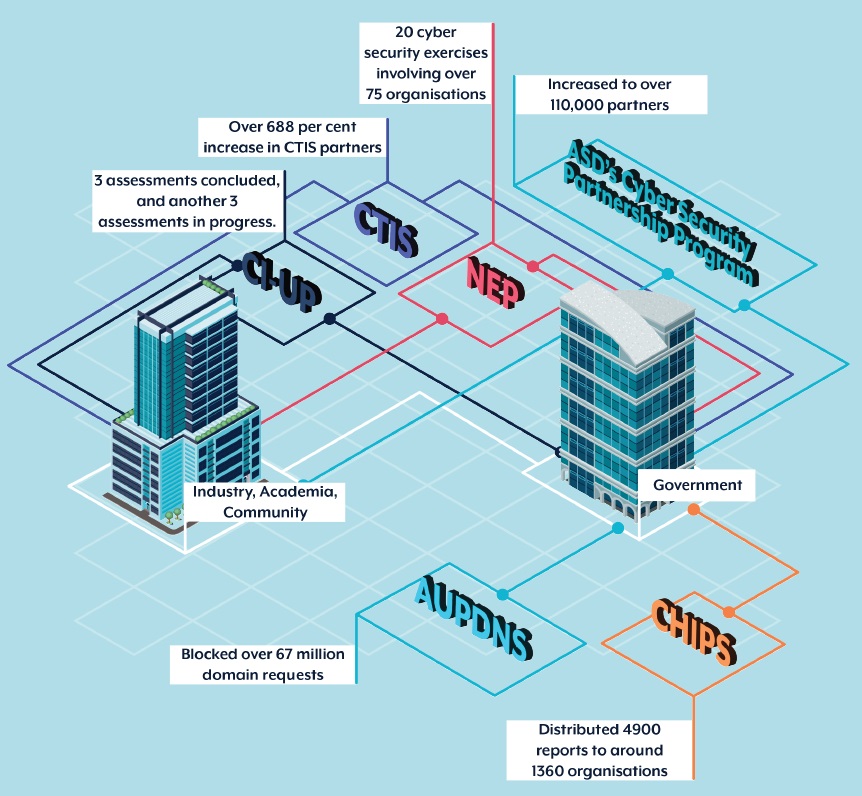
Figure 7: ASD’s program highlights
Through ASD’s Cyber Security Partnership Program, Australian organisations can draw on the collective understanding, experience and capability of the community to lift Australia’s cyber resilience. ASD Network Partners bring their insights and technical expertise to the community to collaborate on shared threats and opportunities.
Explainer 10: Incident response to stay ahead of adversaries
There is an actor behind every cyber security incident, and each actor will have different intent and capability. For example, state actors are usually focused on long-term goals in opposition to Australia’s national interests, whereas cybercriminals are generally focused on short-term financial gain. Additionally, the techniques different actors use will vary due to their risk appetites for being detected. For example, cybercriminal actions are often ‘loud and public’, as opposed to state actors whose intent is to usually remain undetected for long periods.
Customising the incident response method ensures the best outcome for impacted organisations. For example, during a cyber security incident, ASD can provide immediate incident response advice and assistance to support impacted Australian organisations. ASD can also work closely with commercial incident response partners in support of an incident.
If the incident is likely the result of a state actor, ASD may offer a more detailed approach such as a comprehensive digital forensic technical investigation to ensure comprehensive remediation.
Public communications on an incident may also differ. An immediate public statement may be required in some incidents. However, there is a need to balance public statements with remediation efforts – particularly when a state actor may be involved. If a state actor is responsible, a public statement could cause the actor to ‘lay low’, impacting a defender’s ability to detect the actor – including tradecraft or accesses that may help them to remain on an organisation’s network.
ASD’s tailored approach to incident response is consistent with industry best-practice, and highlights the importance of public–private partnerships to stay ahead of Australia’s cyber adversaries.
ASD’s ACSC Incident Response
ASD’s incident management capabilities provide tailored incident response advice and guidance to Australians impacted by a cyber security incident. ASD is not a law enforcement agency or regulator; however we work closely with these agencies if needed.
Report a cybercrime or cyber security incident
Report at cyber.gov.au/report or call the 24/7 Australian Cyber Security Hotline on 1300 CYBER1 ( 1300 292 371 ).
Cybercrime reports are automatically referred directly to the relevant state or territory law enforcement agency.
Cyber security incidents
All cyber security incidents should be reported to ReportCyber. An incident does not have to be a confirmed compromise to be reported and could include:
- denial-of-service (DoS)
- scanning and reconnaissance
- unauthorised access to network or device
- data exposure, theft or leak
- malicious code/malware
- phishing/spear phishing
- any other irregular cyber activity that causes concern.
For ASD to help you effectively, we may request:
- indicators of compromise
- memory dumps
- disk information
- network traffic captures.
How ASD can help
ASD will provide you with immediate advice and assistance such as:
- tailored information on how to contain and remediate an incident
- advisory products to assist you with your incident response
- linking you with other Australian Government entities that may further support your response such as the Australian Federal Police, or Department of Home Affairs through the National Cyber Security Coordinator and the Cyber Security Response Coordination Unit
- we may also link you to other government partners like IDCare, ScamWatch, or the e-Safety Commissioner.
How your reporting matters
ASD uses information from your report to build our understanding of the cyber threat environment. This understanding assists with the development of new and updated advice, capabilities, techniques and products to better prevent and respond to evolving cyber threats. Some of these products include:
- advisories published on ASD’s Partnership Portal
- alerts published on cyber.gov.au
- quarterly Trends and Insights reports
- the ASD's Cyber Threat Report.
Your confidentiality is paramount
ASD does not share any information provided by you without your express consent. Only information about the incident is captured when you report.
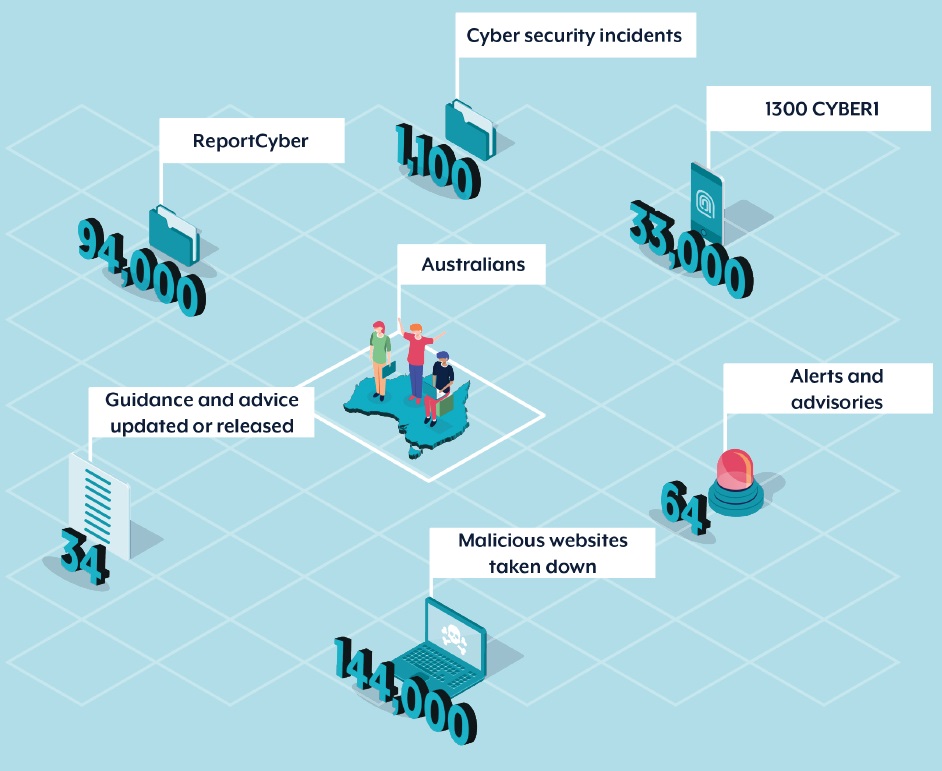
Figure 8: ASD’s support to Australians
During 2022–23, ASD monitored cyber threats across the globe 24 hours a day, 365 days a year, to alert Australians to cyber threats, provide advice, and assist with incident response. ASD’s ACSC is a hub for private and public sector collaboration and information-sharing on cyber security, to prevent and combat threats and minimise harm to Australians.
ASD’s advice and assistance is for the whole economy, including critical infrastructure and systems of national significance, federal, state and local governments, small and medium businesses, academia, not-for-profit organisations and the Australian community.
Cyber resilience for all Australians
The average Australian household has well over a dozen internet-connected devices and this number is growing. The explosion of remote and hybrid work has also seen corporate networks extend into Australian homes. While growing digitisation and virtualisation of services may have improved consumer convenience and boosted business productivity over the last 3 years, it has also increased the cyber risks for Australians.
Every Australian should practice basic cyber security hygiene to help protect themselves from online threats. The most effective cyber defences are also some of the easiest to use and fastest to setup. The top things Australians can do are:
At cyber.gov.au, ASD has published a range of simple how-to guides for all Australians, including children and seniors, that explain how individuals and families can improve their home cyber security.
Australians are encouraged to report cyber security incidents and cybercrime to ReportCyber , or by calling the Australian Cyber Security Hotline on 1300 CYBER1 ( 1300 292 371 ). The hotline is available 24 hours a day, 7 days a week.
Act Now, Stay Secure
ASD provides tailored cyber security guidance to protect Australia against evolving cyber threats. The Act Now, Stay Secure cyber security awareness-raising campaign identified key cyber threats to individuals and small-to-medium businesses, and highlighted ASD advice and tools to help improve the audience’s cyber security posture. Over 2022–23, the campaign:
- reached a potential audience of more than 490,000 Australians and achieved over 11,500 engagements, such as likes, shares, and comments through social media
- was amplified by 170 stakeholders across government, industry, non-profit sectors, and peak body associations, who shared campaign content to their channels
- attracted over 30,000 visitors to the cyber.gov.au website, resulting in nearly 73,000 page views of campaign content and cyber security guidance
- bolstered content delivered at 15 tailored events by ASD state offices.
Monthly cyber security themes were developed to promote planned or new ASD guidance, tools and products to enhance the cyber posture of Australian individuals and small-to-medium businesses. The themes for 2022–23 were:
REDSPICE is the most significant single investment in ASD’s history and will equip ASD to ensure that Australia is best prepared to respond to the strategic environment. Commencing on 1 July 2022, ASD scaled existing services and introduced new intelligence and cyber capabilities to enhance Australia’s cyber defences.
To help achieve this, in FY 2022–23, ASD opened new facilities in Brisbane and Melbourne, and received over 26,000 job applications across Canberra, Melbourne, Brisbane and Perth. ASD also:
- undertook innovative first-of-type ‘cyber hunt’ activities on the most critical government and critical infrastructure networks
- engaged over 175 new customers onto the Cyber Threat Intelligence Sharing platform to improve machine-speed cyber threat intelligence sharing across government and industry
- deployed over 25,000 new host-based sensors to customer networks to build increased visibility of emerging threats to Australia’s most critical systems
- established a secure design and architecture team to provide advice to major government information and communications technology projects
- expanded ASD’s national incident response footprint and 24/7 defence operations capability, including additional upgrades for the Australian Cyber Security Hotline (1300 CYBER 1) and ReportCyber, and a new incident response team in Melbourne
- improved the resilience of critical infrastructure through a number of uplift activities to increase cyber security maturity across Australian industry.

About the contributors
ASD manages or uses a number of unique datasets to produce tailored advice and assistance for Australian organisations and individuals. Not all cybercrimes lead to cyber security incidents, and the statistics in this report are from 2 distinct datasets: cybercrimes reported to law enforcement through ReportCyber, and cyber security incidents responded to by ASD. Data has been extracted from live datasets of cybercrime and cyber security reports reported to ASD. As such, the statistics and conclusions in this report are based on point-in-time analysis and assessment.
Cybercrime and cyber security incidents reported to ASD may not reflect all cyber threats and trends in Australia’s cyber security environment.
ASD encourages the reporting of cyber security incidents and cybercrimes to inform ASD advice and assistance to vulnerable entities, and enhance situational awareness of the national cyber threat environment.
Defining cybercrimes
In Australia, the term ‘cybercrime’ is used to describe both:
- Cyber dependent crimes, such as computer intrusions and DoS attacks, directed at computers or other ICTs.
- Cyber enabled crimes, such as online fraud, identity theft and the distribution of child exploitation material, which can increase in their scale and/or reach through the use of computers or other forms of ICTs.
The ASD glossary provides definitions for terms used in this report and other ASD publications and can be viewed at: https://www.cyber.gov.au/learn-basics/view-resources/glossary .
Thanks for your feedback!
Cookies on GOV.UK
We use some essential cookies to make this website work.
We’d like to set additional cookies to understand how you use GOV.UK, remember your settings and improve government services.
We also use cookies set by other sites to help us deliver content from their services.
You have accepted additional cookies. You can change your cookie settings at any time.
You have rejected additional cookies. You can change your cookie settings at any time.
- Crime, justice and law
Nature of crime tables: year ending March 2023
Annual data from the Crime Survey for England and Wales (CSEW). Data include when incidents happened, information about offenders, the victim's perception of the incident. Datasets include robbery, bicycle theft, burglary, criminal damage, personal and other theft, other household theft, and vehicle-related theft.
https://www.ons.gov.uk/releases/natureofcrimetablesyearendingmarch2023
Official statistics are produced impartially and free from political influence.
Is this page useful?
- Yes this page is useful
- No this page is not useful
Help us improve GOV.UK
Don’t include personal or financial information like your National Insurance number or credit card details.
To help us improve GOV.UK, we’d like to know more about your visit today. We’ll send you a link to a feedback form. It will take only 2 minutes to fill in. Don’t worry we won’t send you spam or share your email address with anyone.

IMAGES
COMMENTS
U.S. Crime Rates and Trends — Analysis of FBI Crime Statistics. The FBI's latest report on crime trends includes 2022 data for national, regional, and local levels. This page lists key statistics from the latest annual crime report published by the Federal Bureau of Investigation. The report, published on October 16, 2023, includes data on ...
Federal, state, and local law enforcement agencies collect data about crime. Find crime statistics around the U.S. using the FBI's Crime Data Explorer. Use the Crime Data Explorer to find statistics about different types of crime nationally or in your state, county, or town. LAST UPDATED: February 1, 2024.
Both the FBI and BJS data show dramatic declines in U.S. violent and property crime rates since the early 1990s, when crime spiked across much of the nation. Using the FBI data, the violent crime rate fell 49% between 1993 and 2019, with large decreases in the rates of robbery (-68%), murder/non-negligent manslaughter (-47%) and aggravated ...
The Uniform Crime Reporting (UCR) Program generates reliable statistics for use in law enforcement. It also provides information for students of criminal justice, researchers, the media, and the public. The program has been providing crime statistics since 1930. The UCR Program includes data from more than 18,000 city, university and college ...
Crime data from law enforcement agencies reflect those crimes reported to and recorded by police. The Nation's Two Crime Measures. Department of Justice agencies collect both survey and administrative data on crime. BJS's National Crime Victimization Survey (NCVS) captures incident-level data on reported and unreported crime from the victim's ...
The Bureau of Justice Statistics (BJS) is the United States' primary source for criminal justice statistics that cover a wide range of topics. ... Research and Third-party Reports; Data Corrections; Data. Data; Statistical Coverage of Crime and the Justice Process; Search Data Collections; Data Analysis Tools; National Archive of Criminal ...
State by state comparison In 2022, California reported the highest number of crimes out of all states in the U.S., followed by Texas and New York. However, as the FBI estimates national crime by ...
The U.S. murder rate in 2020 was 42% lower than the suicide rate (13.5 deaths per 100,000 people) and 71% below the mortality rate for drug overdose (27.1 deaths per 100,000 people, as of the third quarter of 2020), the CDC data shows. As was the case with murders, drug overdoses increased sharply in 2020.
Examining What Is: Covid-19, Guns, and the Rise in Hate. Prior to the Covid-19 pandemic, crime rates were relatively low. As the graph in Figure 1 demonstrates, the rate of violent crime offenses declined from a peak in 1991 of 758.2 per year to 398.5 per year in 2020. 19 The rate of homicide over the same period also dropped significantly, from its highest level in 1991 compared with 2020. 20 ...
A similar story is told by looking at the violent crime rate per 100,000 residents, which factors in the role population growth plays in increasing the overall number of crimes. Published by ...
Annual government surveys from the Bureau of Justice Statistics show no recent increase in the U.S. violent crime rate. In 2021, the most recent year with available data, there were 16.5 violent crimes for every 1,000 Americans ages 12 and older. That was statistically unchanged from the year before, below pre-pandemic levels and far below the ...
UNODC works on the development of standards for national crime and criminal justice information systems and for the conduct of victimization surveys. The office also aims to enhance the cross-national comparability of data through the development of key indicators and data reporting tools. Periodic reports on selected crime issues provide in ...
Violent Crime Rates by Race; ... Crime Prevention Research Center fellow Amanda Collins Johnson talked about being raped in college and her advocacy for "campus carry" gun laws. This event was hosted on February 29th, 2024 by the Clare Boothe Luce Center for Conservative Women in Virginia. C-SPAN...
By: SafeHome.org Research Updated: Dec 21, 2022 Compared to data from 2010, violent crime in the U.S. is trending up, while property is down by 33-percent. Small and extra-small cities have lower property crime rates than large- and medium-sized cities, but the differences are minimal. Crime is everywhere, so a home security system is a... View Article
the crime data is the natural log of the crime rate (though .01 is added to the crime rate when it is equal to zero) ao stands for the arrest rate data by type of crime. The data and its sources are described in the data appendix for my book More Guns, Less Crime (University of Chicago Press, 3rd edition, 2010).
Crime reports can convey information that affects the complete population of individuals and/or businesses, or they can convey crime-related information on a subset of victims, such as males, the elderly, businesses, or the poor. Crime reports and statistics can focus on a short period of time, such as a month, or they can cover longer periods ...
The National Crime Victimization Survey ( NCVS) is the nation's primary source of information on criminal victimization. Each year, data are obtained from a nationally representative sample of about 240,000 persons in about 150,000 households. Persons are interviewed on the frequency, characteristics, and consequences of criminal victimization ...
SpotCrime is a public facing crime map and crime alert service. With SpotCrime, it's easier than ever to check crime anywhere in the United States and many other countries worldwide. Our goal is to provide the most accurate and timely crime information to the public. As the most visited crime mapping website, SpotCrime allows you to easily ...
Between March 18 and April 1, there were only 7 mentions of the FBI crime report or the drop in crime rates on Fox News, the longest of which included allegations from the guest, America's Most ...
Support for the Black Lives Matter Movement Has Dropped Considerably From Its Peak in 2020. Today, 51% of U.S. adults say they support the Black Lives Matter movement - down from 67% in June 2020. A majority of Americans say the increased focus on race and racial inequality in the past three years hasn't led to improvement for Black Americans.
Shapiro-Davis Administration Awards $40 Million in State Violence Intervention and Pr... March 27, 2024 Harrisburg, PA - Today, the Pennsylvania Commission on Crime and Delinquency's (PCCD) School Safety and Security Committee approved a total of $40 mi...
The FBI's preliminary 2023 data show murder declined by 13.2% across the country and violent crime dropped 5.7% compared to 2022 levels. Various news headlines have reported the FBI's numbers ...
Data has been extracted from live datasets of cybercrime and cyber security reports reported to ASD. As such, the statistics and conclusions in this report are based on point-in-time analysis and assessment. ... (AIC) is Australia's national research and knowledge centre on crime and justice. The AIC informs crime and justice policy and ...
Annual data from the Crime Survey for England and Wales (CSEW). Data include when incidents happened, information about offenders, the victim's perception of the incident. Datasets include robbery ...