- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic


Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

High-Impact Research Collection
Explore a collection of freely available high-impact research from 2020 and 2021 published in the Journal of Cybersecurity .
Browse the collection here

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.

Cyber and Digital Forensic Investigations
A Law Enforcement Practitioner’s Perspective
- © 2020
- Nhien-An Le-Khac 0 ,
- Kim-Kwang Raymond Choo ORCID: https://orcid.org/0000-0001-9208-5336 1
School of Computer Science, University College Dublin, Dublin, Ireland
You can also search for this editor in PubMed Google Scholar
The University of Texas at San Antonio, San Antonio, USA
- Presents an experiential learning approach to digital forensic education
- Featuring contributions by law enforcement forensic practitioners, it discusses the state of the art in incident response and digital forensic
- Includes recent research on cyber and digital forensic investigations
Part of the book series: Studies in Big Data (SBD, volume 74)
10k Accesses
24 Citations
5 Altmetric
This is a preview of subscription content, log in via an institution to check access.
Access this book
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
- Durable hardcover edition
Tax calculation will be finalised at checkout
Other ways to access
Licence this eBook for your library
Institutional subscriptions
Table of contents (12 chapters)
Front matter, the increasing importance of digital forensics and investigations in law enforcement, government and commercial sectors.
- Nhien-An Le-Khac, Kim-Kwang Raymond Choo
Defending IoT Devices from Malware
- William O’Sullivan, Kim-Kwang Raymond Choo, Nhien-An Le-Khac
Digital Forensic Investigation of Internet of Thing Devices: A Proposed Model and Case Studies
- Alexander Hilgenberg, Trung Q. Duong, Nhien-An Le-Khac, Kim-Kwang Raymond Choo
Forensic Investigation of Ransomware Activities—Part 1
- Cian Young, Robert McArdle, Nhien-An Le-Khac, Kim-Kwang Raymond Choo
Forensic Investigation of Ransomware Activities—Part 2
- Christopher Boyton, Nhien-An Le-Khac, Kim-Kwang Raymond Choo, Anca Jurcut
CCTV Forensics in the Big Data Era: Challenges and Approaches
- Richard Gomm, Ryan Brooks, Kim-Kwang Raymond Choo, Nhien-An Le-Khac, Kien Wooi Hew
Forensic Investigation of PayPal Accounts
- Lars Standare, Darren Hayes, Nhien-An Le-Khac, Kim-Kwang Raymond Choo
Digital Forensic Approaches for Cloud Service Models: A Survey
- Sebastian Schlepphorst, Kim-Kwang Raymond Choo, Nhien-An Le-Khac
Long Term Evolution Network Security and Real-Time Data Extraction
- Neil Redmond, Le-Nam Tran, Kim-Kwang Raymond Choo, Nhien-An Le-Khac
Towards an Automated Process to Categorise Tor’s Hidden Services
- Andrew Kinder, Kim-Kwang Raymond Choo, Nhien-An Le-Khac
The Bitcoin-Network Protocol from a Forensic Perspective
- Cornelis Leendert (Eelco) van Veldhuizen, Madhusanka Liyanage, Kim-Kwang Raymond Choo, Nhien-An Le-Khac
So, What’s Next?
- Cyber Crime
- Cyber Forensics
- Cyber Security
- Cyber Security Education
- Digital Forensic Education
- Digital Forensics
- Incident Response
- IoT Forensics
- Mobile Forensics
- National Security
- Smart Home Forensics
About this book
Editors and affiliations.
Nhien-An Le-Khac
Kim-Kwang Raymond Choo

About the editors
Bibliographic information.
Book Title : Cyber and Digital Forensic Investigations
Book Subtitle : A Law Enforcement Practitioner’s Perspective
Editors : Nhien-An Le-Khac, Kim-Kwang Raymond Choo
Series Title : Studies in Big Data
DOI : https://doi.org/10.1007/978-3-030-47131-6
Publisher : Springer Cham
eBook Packages : Intelligent Technologies and Robotics , Intelligent Technologies and Robotics (R0)
Copyright Information : The Editor(s) (if applicable) and The Author(s), under exclusive license to Springer Nature Switzerland AG 2020
Hardcover ISBN : 978-3-030-47130-9 Published: 26 July 2020
Softcover ISBN : 978-3-030-47133-0 Published: 27 July 2021
eBook ISBN : 978-3-030-47131-6 Published: 25 July 2020
Series ISSN : 2197-6503
Series E-ISSN : 2197-6511
Edition Number : 1
Number of Pages : XV, 278
Number of Illustrations : 14 b/w illustrations, 124 illustrations in colour
Topics : Data Engineering , Cyber-physical systems, IoT , Computational Intelligence , Big Data
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Stanford University

A program of the Cyber Policy Center , a joint initiative of the Freeman Spogli Institute for International Studies and Stanford Law School .
APRIL 30 DEADLINE | CALL FOR PROPOSALS: 2024 TRUST & SAFETY RESEARCH CONFERENCE
How to fix the online child exploitation reporting system.
- Stanford Internet Observatory
- The CyberTipline is enormously valuable, and leads to the rescue of children and prosecution of offenders.
- Many online platforms submit low-quality reports.
- NCMEC has faced challenges in rapidly implementing technological improvements that would aid law enforcement in triage.
- Legal constraints on NCMEC and U.S. law enforcement have implications for efficiency.
- These issues would be best addressed by a concerted effort to massively uplift NCMEC's technical and analytical capabilities, which will require the cooperation of platforms, NCMEC, law enforcement and, importantly, the U.S. Congress.
- DOWNLOAD REPORT
The CyberTipline is the main line of defense for children who are exploited on the internet. It leads to the rescue of children and the arrest of abusers. Yet after 26 years many believe the entire system is not living up to its potential. A new Stanford Internet Observatory report examines issues in the reporting system and what the technology industry, the nonprofit that runs the tipline, and the U.S. Congress must do to fix it.
If online platforms in the U.S. become aware of child sexual abuse material (CSAM), federal law requires that they report it to the CyberTipline. This centralized system for reporting online child exploitation is operated by the National Center for Missing and Exploited Children (NCMEC), a nonprofit organization. NCMEC attempts to identify the location of the users who sent and received the abuse content, and may attempt to locate the victim. These reports are then sent to local or national law enforcement agencies in the U.S. and abroad.
The report is based on interviews with 66 respondents across industry, law enforcement, and civil society. Researchers also visited NCMEC’s headquarters for three days of extensive interviews.
While our research focuses on CyberTipline challenges, we want to note that many respondents highlighted that the entire CyberTipline process is enormously valuable and the fact that U.S. platforms are required to report CSAM is a strength of the system. “The system is worth nurturing, preserving, and securing,” one respondent said.
Law enforcement officers are overwhelmed by the high volume of CyberTipline reports they receive. However, we find that the core issue extends beyond volume: officers struggle to triage and prioritize these reports to identify offenders and reach children who are in harm. An officer might examine two CyberTipline reports – each documenting an individual uploading a single piece of CSAM – yet, upon investigation, one report might lead nowhere, while the other could uncover ongoing child abuse by the uploader. Nothing in the reports would have indicated which should be prioritized.
We identify three key challenges for law enforcement to prioritize reports for investigation.
First, while some tech companies are known for providing careful and detailed CyberTipline reports, many reports are low quality. Executives may be unwilling to dedicate engineering resources to ensure the accurate completion of fields within the reporting API. Trust and safety staff turnover and a lack of documentation on reporting best practices cause knowledge gaps in consistency and effective reporting. This is especially true for platforms that make fewer reports. That said, submitting a high volume of reports is not necessarily correlated with submitting high quality reports.
Second, NCMEC has faced challenges in rapidly implementing technological improvements that would aid law enforcement in triage. NCMEC faces resource constraints and lower salaries, leading to difficulties in retaining personnel who are often poached by industry trust and safety teams. While there has been progress in report deconfliction—identifying connections between reports, such as identical offenders—the pace of improvement has been considered slow. Additionally, varied case management interfaces used by law enforcement to process CyberTipline reports make it difficult to ensure linked reports are displayed. Integration difficulties with external data sources, which could enrich reports and facilitate triage, are partly attributed to the sensitive nature of CyberTipline data and potentially staffing constraints for technical infrastructure upgrades. Legal restrictions on NCMEC’s use of cloud services hampers their ability to leverage advanced machine learning tools, although opinions vary on the appropriateness of cloud storage for their sensitive data.
Third, there are legal constraints on NCMEC’s and law enforcement’s roles. A federal appeals court held in 2016 that NCMEC is a governmental entity or agent, meaning its actions are subject to Fourth Amendment rules. As a result, NCMEC may not tell platforms what to look for or report, as that risks turning them into government agents too , converting what once were voluntary private searches into warrantless government searches (which generally requires suppression of evidence in court). Consequently, NCMEC is hesitant to put best practices in writing. Instead, many trust and safety staff who are new to the CyberTipline process must learn from more established platforms or industry coalitions.
Another federal appeals court held in 2021 that the government must get a warrant before opening a reported file unless the platform viewed that file before submitting the report. Platforms often do not indicate whether content has been viewed; if they have not so indicated, then NCMEC, like law enforcement, cannot open those files. Platforms may automate reports to the CyberTipline on the basis of a hash match hit to known CSAM instead of having staff view each file, whether due to limited review capacity or not wanting to expose staff to harmful content. Where reported files weren’t viewed by the platform, law enforcement may need a warrant to investigate those reports, and NCMEC currently cannot help with an initial review.
This review process makes it difficult to process the high volume of reported viral and meme content. Such content commonly gets shared widely, for example out of outrage or a misguided attempt at humor; nevertheless, if it meets the definition of CSAM, it is still illegal and must be reported. Platform staff don’t always review meme content (to avoid repeated unnecessary exposure to known material), but if these reports with unviewed files are submitted without checking the CyberTipline report form’s box for memes, it creates an enormous amount of work for law enforcement to close out these unactionable reports. Meanwhile, since platforms are required to preserve reported material for only 90 days, the time it takes to process a report means preserved content has often been deleted by the time law enforcement follows up with the platform in actionable cases.
Recommendations
- Online platforms should prioritize child safety staffing with expertise for in-depth investigations that proactively identify and address child sexual abuse and exploitation to stay ahead of measures taken by bad actors to avoid detection.
- Platforms should invest dedicated engineering resources in implementing the NCMEC reporting API . Ensure there is an accurate and (where possible) automated process for completing all relevant fields Our interviews suggest reports are more actionable when they provide offender information (including location information, particularly an upload IP address), victim information (including location information), the associated file (a hash alone is insufficient) or chat, and the time of the incident (including a description of how the platform defines the incident time).
- To avoid state actor concerns, an NGO that is not NCMEC should publish the key CyberTipline form fields that platforms should complete to increase the likelihood that law enforcement will be able to investigate their reports.
- Congress should increase NCMEC’s budget to enable it to hire more competitively in the technical division, and to dedicate more resources to CyberTipline technical infrastructure development. This funding should not be taken out of the budget for Internet Crimes Against Children Task Forces.
- NCMEC should prioritize investment in technical staff and the technical infrastructure of the CyberTipline to speed up implementation of their technical roadmap.
- NCMEC and Internet Crimes Against Children Task Forces should partner with researchers to bring insights into the CyberTipline reporting flow along with the relationship between CyberTipline reports, arrests, and victim identification.
- Congress should pass legislation that extends the required preservation period to at least 180 days, but preferably one year.
- The U.S. Supreme Court should resolve the split in authority over whether the private search doctrine requires human review by platform personnel in order for law enforcement to open a file without a warrant, or whether the doctrine is satisfied where a reported file is a hash match for a previously-viewed file.
Investigation Finds AI Image Generation Models Trained on Child Abuse
Addressing child exploitation on federated social media, an update on the sg-csam ecosystem.

AI + Machine Learning , Announcements , Azure AI , Azure AI Studio
Introducing Phi-3: Redefining what’s possible with SLMs
By Misha Bilenko Corporate Vice President, Microsoft GenAI
Posted on April 23, 2024 4 min read
- Tag: Copilot
- Tag: Generative AI
We are excited to introduce Phi-3, a family of open AI models developed by Microsoft. Phi-3 models are the most capable and cost-effective small language models (SLMs) available, outperforming models of the same size and next size up across a variety of language, reasoning, coding, and math benchmarks. This release expands the selection of high-quality models for customers, offering more practical choices as they compose and build generative AI applications.
Starting today, Phi-3-mini , a 3.8B language model is available on Microsoft Azure AI Studio , Hugging Face , and Ollama .
- Phi-3-mini is available in two context-length variants—4K and 128K tokens. It is the first model in its class to support a context window of up to 128K tokens, with little impact on quality.
- It is instruction-tuned, meaning that it’s trained to follow different types of instructions reflecting how people normally communicate. This ensures the model is ready to use out-of-the-box.
- It is available on Azure AI to take advantage of the deploy-eval-finetune toolchain, and is available on Ollama for developers to run locally on their laptops.
- It has been optimized for ONNX Runtime with support for Windows DirectML along with cross-platform support across graphics processing unit (GPU), CPU, and even mobile hardware.
- It is also available as an NVIDIA NIM microservice with a standard API interface that can be deployed anywhere. And has been optimized for NVIDIA GPUs .
In the coming weeks, additional models will be added to Phi-3 family to offer customers even more flexibility across the quality-cost curve. Phi-3-small (7B) and Phi-3-medium (14B) will be available in the Azure AI model catalog and other model gardens shortly.
Microsoft continues to offer the best models across the quality-cost curve and today’s Phi-3 release expands the selection of models with state-of-the-art small models.
Azure AI Studio
Phi-3-mini is now available
Groundbreaking performance at a small size
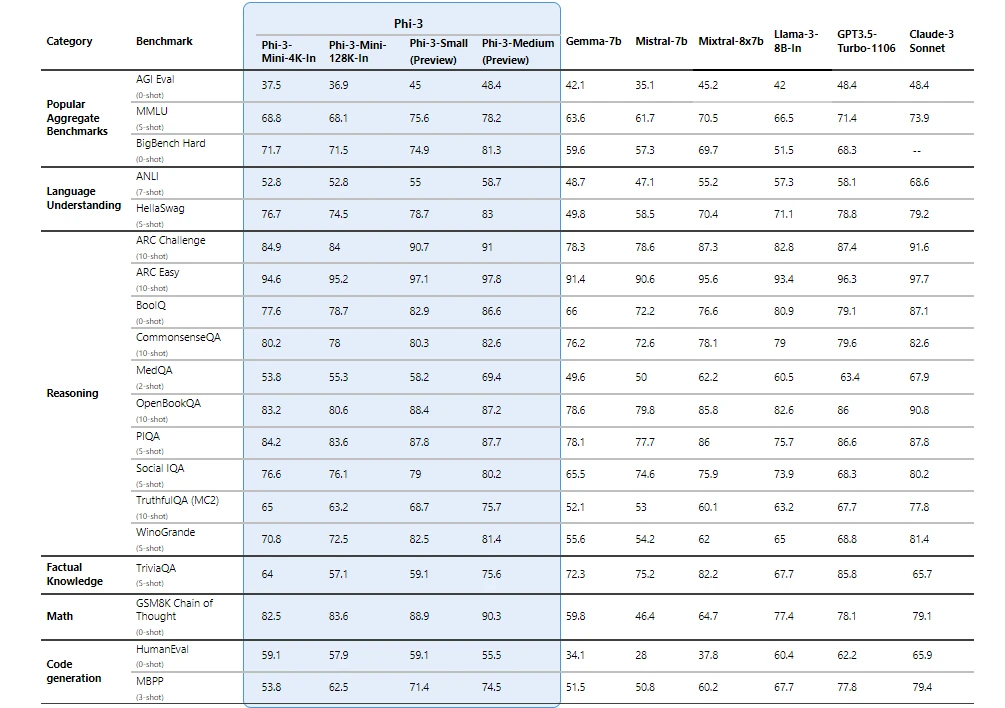
Phi-3 models significantly outperform language models of the same and larger sizes on key benchmarks (see benchmark numbers below, higher is better). Phi-3-mini does better than models twice its size, and Phi-3-small and Phi-3-medium outperform much larger models, including GPT-3.5T.
All reported numbers are produced with the same pipeline to ensure that the numbers are comparable. As a result, these numbers may differ from other published numbers due to slight differences in the evaluation methodology. More details on benchmarks are provided in our technical paper .
Note: Phi-3 models do not perform as well on factual knowledge benchmarks (such as TriviaQA) as the smaller model size results in less capacity to retain facts.
Safety-first model design
Responsible ai principles
Phi-3 models were developed in accordance with the Microsoft Responsible AI Standard , which is a company-wide set of requirements based on the following six principles: accountability, transparency, fairness, reliability and safety, privacy and security, and inclusiveness. Phi-3 models underwent rigorous safety measurement and evaluation, red-teaming, sensitive use review, and adherence to security guidance to help ensure that these models are responsibly developed, tested, and deployed in alignment with Microsoft’s standards and best practices.
Building on our prior work with Phi models (“ Textbooks Are All You Need ”), Phi-3 models are also trained using high-quality data. They were further improved with extensive safety post-training, including reinforcement learning from human feedback (RLHF), automated testing and evaluations across dozens of harm categories, and manual red-teaming. Our approach to safety training and evaluations are detailed in our technical paper , and we outline recommended uses and limitations in the model cards. See the model card collection .
Unlocking new capabilities
Microsoft’s experience shipping copilots and enabling customers to transform their businesses with generative AI using Azure AI has highlighted the growing need for different-size models across the quality-cost curve for different tasks. Small language models, like Phi-3, are especially great for:
- Resource constrained environments including on-device and offline inference scenarios.
- Latency bound scenarios where fast response times are critical.
- Cost constrained use cases, particularly those with simpler tasks.
For more on small language models, see our Microsoft Source Blog .
Thanks to their smaller size, Phi-3 models can be used in compute-limited inference environments. Phi-3-mini, in particular, can be used on-device, especially when further optimized with ONNX Runtime for cross-platform availability. The smaller size of Phi-3 models also makes fine-tuning or customization easier and more affordable. In addition, their lower computational needs make them a lower cost option with much better latency. The longer context window enables taking in and reasoning over large text content—documents, web pages, code, and more. Phi-3-mini demonstrates strong reasoning and logic capabilities, making it a good candidate for analytical tasks.
Customers are already building solutions with Phi-3. One example where Phi-3 is already demonstrating value is in agriculture, where internet might not be readily accessible. Powerful small models like Phi-3 along with Microsoft copilot templates are available to farmers at the point of need and provide the additional benefit of running at reduced cost, making AI technologies even more accessible.
ITC, a leading business conglomerate based in India, is leveraging Phi-3 as part of their continued collaboration with Microsoft on the copilot for Krishi Mitra, a farmer-facing app that reaches over a million farmers.
“ Our goal with the Krishi Mitra copilot is to improve efficiency while maintaining the accuracy of a large language model. We are excited to partner with Microsoft on using fine-tuned versions of Phi-3 to meet both our goals—efficiency and accuracy! ” Saif Naik, Head of Technology, ITCMAARS
Originating in Microsoft Research, Phi models have been broadly used, with Phi-2 downloaded over 2 million times. The Phi series of models have achieved remarkable performance with strategic data curation and innovative scaling. Starting with Phi-1, a model used for Python coding, to Phi-1.5, enhancing reasoning and understanding, and then to Phi-2, a 2.7 billion-parameter model outperforming those up to 25 times its size in language comprehension. 1 Each iteration has leveraged high-quality training data and knowledge transfer techniques to challenge conventional scaling laws.
Get started today
To experience Phi-3 for yourself, start with playing with the model on Azure AI Playground . You can also find the model on the Hugging Chat playground . Start building with and customizing Phi-3 for your scenarios using the Azure AI Studio . Join us to learn more about Phi-3 during a special live stream of the AI Show.
1 Microsoft Research Blog, Phi-2: The surprising power of small language models, December 12, 2023 .
Let us know what you think of Azure and what you would like to see in the future.
Provide feedback
Build your cloud computing and Azure skills with free courses by Microsoft Learn.
Explore Azure learning
Related posts
AI + Machine Learning , Azure AI , Azure AI Content Safety , Azure Cognitive Search , Azure Kubernetes Service (AKS) , Azure OpenAI Service , Customer stories
AI-powered dialogues: Global telecommunications with Azure OpenAI Service chevron_right
AI + Machine Learning , Azure AI , Azure AI Content Safety , Azure OpenAI Service , Customer stories
Generative AI and the path to personalized medicine with Microsoft Azure chevron_right
AI + Machine Learning , Azure AI , Azure AI Services , Azure AI Studio , Azure OpenAI Service , Best practices
AI study guide: The no-cost tools from Microsoft to jump start your generative AI journey chevron_right
AI + Machine Learning , Azure AI , Azure VMware Solution , Events , Microsoft Copilot for Azure , Microsoft Defender for Cloud
Get ready for AI at the Migrate to Innovate digital event chevron_right
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
What the data says about crime in the U.S.
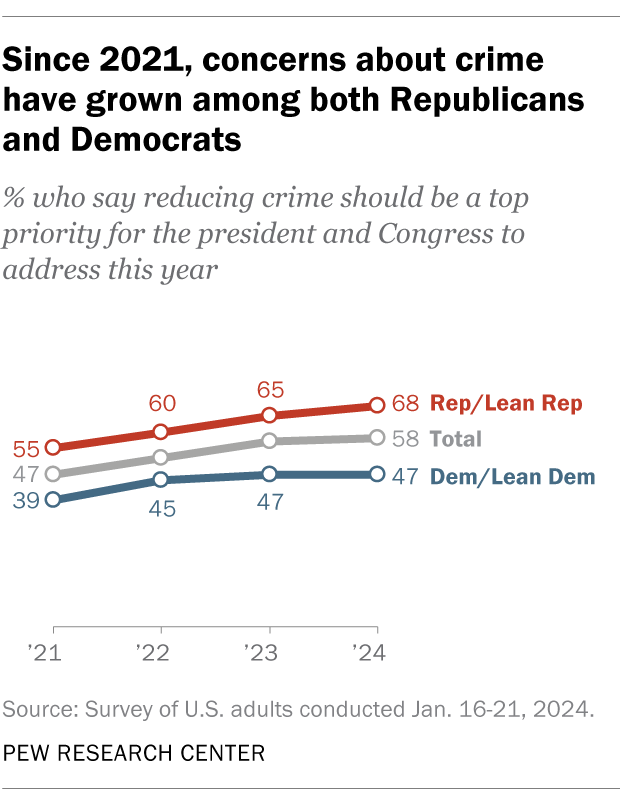
A growing share of Americans say reducing crime should be a top priority for the president and Congress to address this year. Around six-in-ten U.S. adults (58%) hold that view today, up from 47% at the beginning of Joe Biden’s presidency in 2021.
We conducted this analysis to learn more about U.S. crime patterns and how those patterns have changed over time.
The analysis relies on statistics published by the FBI, which we accessed through the Crime Data Explorer , and the Bureau of Justice Statistics (BJS), which we accessed through the National Crime Victimization Survey data analysis tool .
To measure public attitudes about crime in the U.S., we relied on survey data from Pew Research Center and Gallup.
Additional details about each data source, including survey methodologies, are available by following the links in the text of this analysis.
With the issue likely to come up in this year’s presidential election, here’s what we know about crime in the United States, based on the latest available data from the federal government and other sources.
How much crime is there in the U.S.?
It’s difficult to say for certain. The two primary sources of government crime statistics – the Federal Bureau of Investigation (FBI) and the Bureau of Justice Statistics (BJS) – paint an incomplete picture.
The FBI publishes annual data on crimes that have been reported to law enforcement, but not crimes that haven’t been reported. Historically, the FBI has also only published statistics about a handful of specific violent and property crimes, but not many other types of crime, such as drug crime. And while the FBI’s data is based on information from thousands of federal, state, county, city and other police departments, not all law enforcement agencies participate every year. In 2022, the most recent full year with available statistics, the FBI received data from 83% of participating agencies .
BJS, for its part, tracks crime by fielding a large annual survey of Americans ages 12 and older and asking them whether they were the victim of certain types of crime in the past six months. One advantage of this approach is that it captures both reported and unreported crimes. But the BJS survey has limitations of its own. Like the FBI, it focuses mainly on a handful of violent and property crimes. And since the BJS data is based on after-the-fact interviews with crime victims, it cannot provide information about one especially high-profile type of offense: murder.
All those caveats aside, looking at the FBI and BJS statistics side-by-side does give researchers a good picture of U.S. violent and property crime rates and how they have changed over time. In addition, the FBI is transitioning to a new data collection system – known as the National Incident-Based Reporting System – that eventually will provide national information on a much larger set of crimes , as well as details such as the time and place they occur and the types of weapons involved, if applicable.
Which kinds of crime are most and least common?
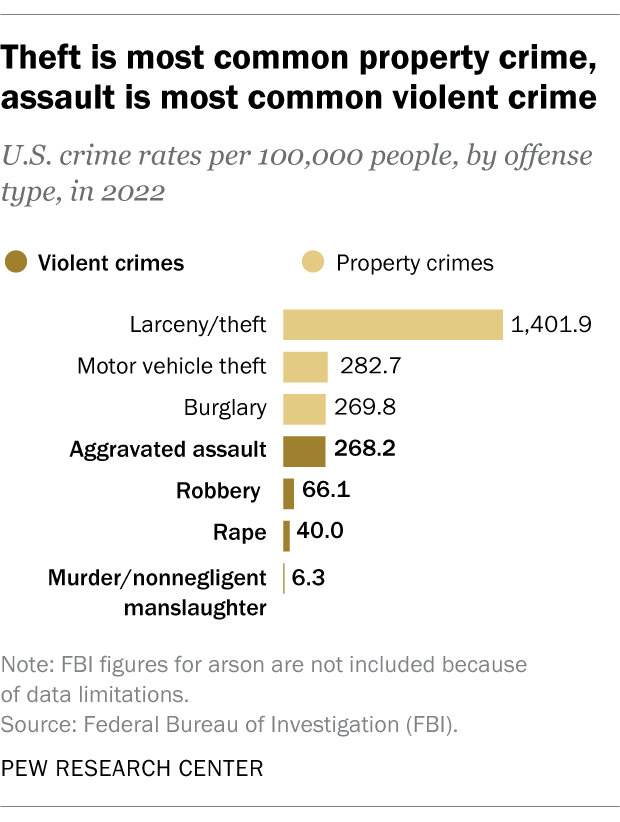
Property crime in the U.S. is much more common than violent crime. In 2022, the FBI reported a total of 1,954.4 property crimes per 100,000 people, compared with 380.7 violent crimes per 100,000 people.
By far the most common form of property crime in 2022 was larceny/theft, followed by motor vehicle theft and burglary. Among violent crimes, aggravated assault was the most common offense, followed by robbery, rape, and murder/nonnegligent manslaughter.
BJS tracks a slightly different set of offenses from the FBI, but it finds the same overall patterns, with theft the most common form of property crime in 2022 and assault the most common form of violent crime.
How have crime rates in the U.S. changed over time?
Both the FBI and BJS data show dramatic declines in U.S. violent and property crime rates since the early 1990s, when crime spiked across much of the nation.
Using the FBI data, the violent crime rate fell 49% between 1993 and 2022, with large decreases in the rates of robbery (-74%), aggravated assault (-39%) and murder/nonnegligent manslaughter (-34%). It’s not possible to calculate the change in the rape rate during this period because the FBI revised its definition of the offense in 2013 .
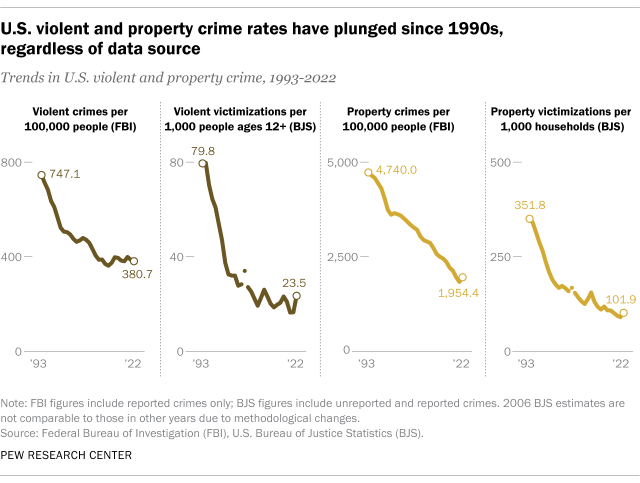
The FBI data also shows a 59% reduction in the U.S. property crime rate between 1993 and 2022, with big declines in the rates of burglary (-75%), larceny/theft (-54%) and motor vehicle theft (-53%).
Using the BJS statistics, the declines in the violent and property crime rates are even steeper than those captured in the FBI data. Per BJS, the U.S. violent and property crime rates each fell 71% between 1993 and 2022.
While crime rates have fallen sharply over the long term, the decline hasn’t always been steady. There have been notable increases in certain kinds of crime in some years, including recently.
In 2020, for example, the U.S. murder rate saw its largest single-year increase on record – and by 2022, it remained considerably higher than before the coronavirus pandemic. Preliminary data for 2023, however, suggests that the murder rate fell substantially last year .
How do Americans perceive crime in their country?
Americans tend to believe crime is up, even when official data shows it is down.
In 23 of 27 Gallup surveys conducted since 1993 , at least 60% of U.S. adults have said there is more crime nationally than there was the year before, despite the downward trend in crime rates during most of that period.
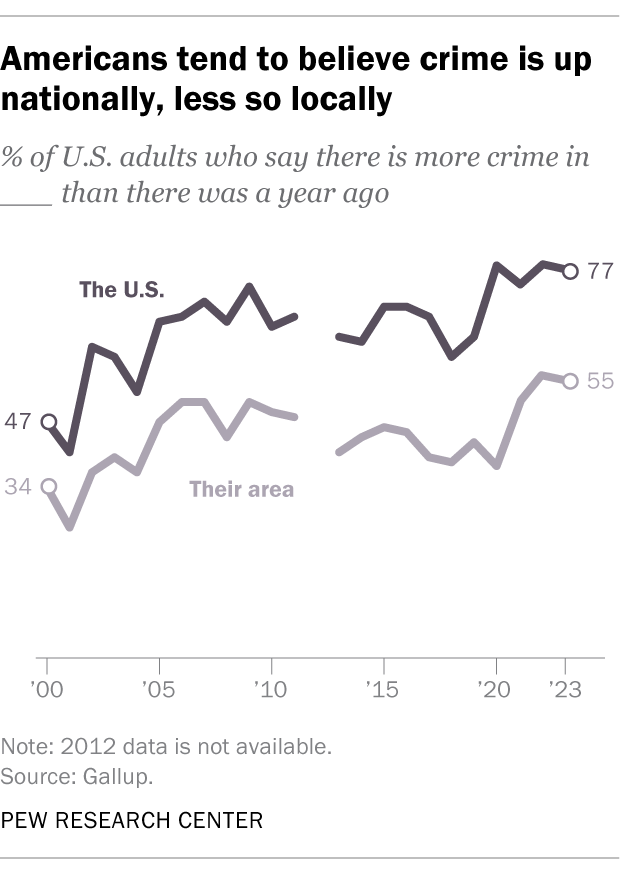
While perceptions of rising crime at the national level are common, fewer Americans believe crime is up in their own communities. In every Gallup crime survey since the 1990s, Americans have been much less likely to say crime is up in their area than to say the same about crime nationally.
Public attitudes about crime differ widely by Americans’ party affiliation, race and ethnicity, and other factors . For example, Republicans and Republican-leaning independents are much more likely than Democrats and Democratic leaners to say reducing crime should be a top priority for the president and Congress this year (68% vs. 47%), according to a recent Pew Research Center survey.
How does crime in the U.S. differ by demographic characteristics?
Some groups of Americans are more likely than others to be victims of crime. In the 2022 BJS survey , for example, younger people and those with lower incomes were far more likely to report being the victim of a violent crime than older and higher-income people.
There were no major differences in violent crime victimization rates between male and female respondents or between those who identified as White, Black or Hispanic. But the victimization rate among Asian Americans (a category that includes Native Hawaiians and other Pacific Islanders) was substantially lower than among other racial and ethnic groups.
The same BJS survey asks victims about the demographic characteristics of the offenders in the incidents they experienced.
In 2022, those who are male, younger people and those who are Black accounted for considerably larger shares of perceived offenders in violent incidents than their respective shares of the U.S. population. Men, for instance, accounted for 79% of perceived offenders in violent incidents, compared with 49% of the nation’s 12-and-older population that year. Black Americans accounted for 25% of perceived offenders in violent incidents, about twice their share of the 12-and-older population (12%).
As with all surveys, however, there are several potential sources of error, including the possibility that crime victims’ perceptions about offenders are incorrect.
How does crime in the U.S. differ geographically?
There are big geographic differences in violent and property crime rates.
For example, in 2022, there were more than 700 violent crimes per 100,000 residents in New Mexico and Alaska. That compares with fewer than 200 per 100,000 people in Rhode Island, Connecticut, New Hampshire and Maine, according to the FBI.
The FBI notes that various factors might influence an area’s crime rate, including its population density and economic conditions.
What percentage of crimes are reported to police? What percentage are solved?
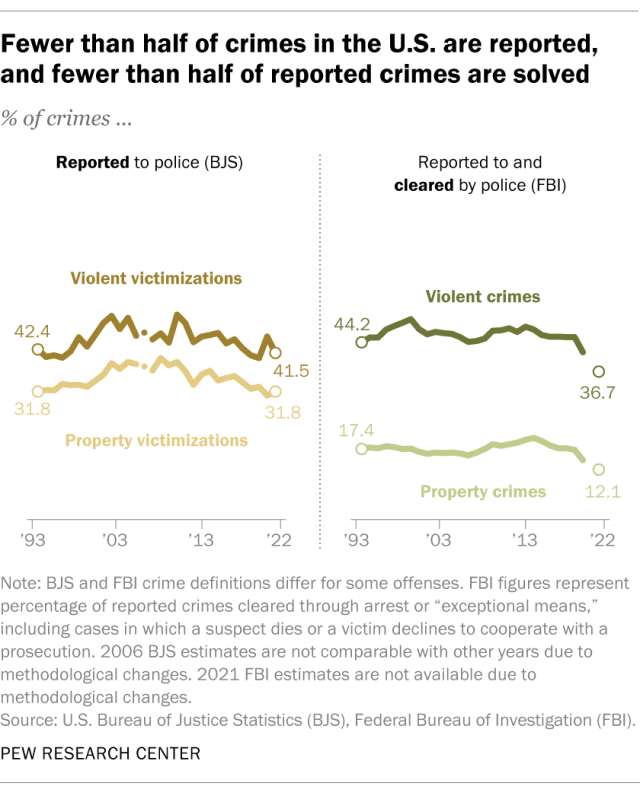
Most violent and property crimes in the U.S. are not reported to police, and most of the crimes that are reported are not solved.
In its annual survey, BJS asks crime victims whether they reported their crime to police. It found that in 2022, only 41.5% of violent crimes and 31.8% of household property crimes were reported to authorities. BJS notes that there are many reasons why crime might not be reported, including fear of reprisal or of “getting the offender in trouble,” a feeling that police “would not or could not do anything to help,” or a belief that the crime is “a personal issue or too trivial to report.”
Most of the crimes that are reported to police, meanwhile, are not solved , at least based on an FBI measure known as the clearance rate . That’s the share of cases each year that are closed, or “cleared,” through the arrest, charging and referral of a suspect for prosecution, or due to “exceptional” circumstances such as the death of a suspect or a victim’s refusal to cooperate with a prosecution. In 2022, police nationwide cleared 36.7% of violent crimes that were reported to them and 12.1% of the property crimes that came to their attention.
Which crimes are most likely to be reported to police? Which are most likely to be solved?
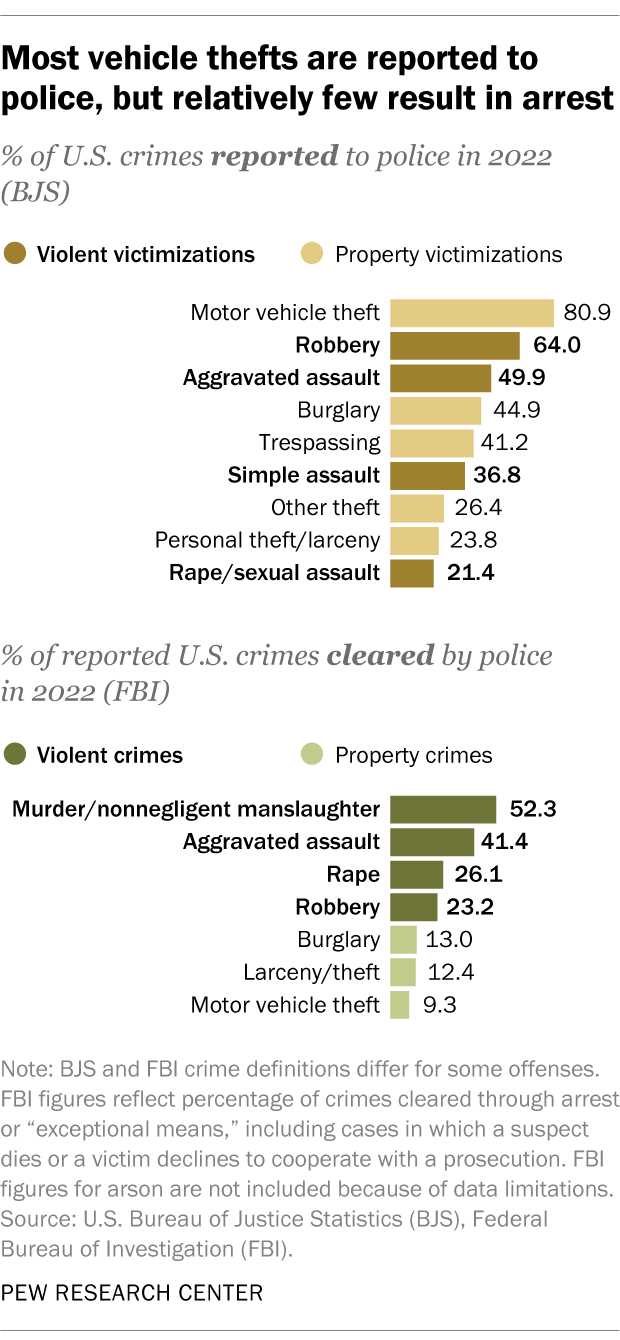
Around eight-in-ten motor vehicle thefts (80.9%) were reported to police in 2022, making them by far the most commonly reported property crime tracked by BJS. Household burglaries and trespassing offenses were reported to police at much lower rates (44.9% and 41.2%, respectively), while personal theft/larceny and other types of theft were only reported around a quarter of the time.
Among violent crimes – excluding homicide, which BJS doesn’t track – robbery was the most likely to be reported to law enforcement in 2022 (64.0%). It was followed by aggravated assault (49.9%), simple assault (36.8%) and rape/sexual assault (21.4%).
The list of crimes cleared by police in 2022 looks different from the list of crimes reported. Law enforcement officers were generally much more likely to solve violent crimes than property crimes, according to the FBI.
The most frequently solved violent crime tends to be homicide. Police cleared around half of murders and nonnegligent manslaughters (52.3%) in 2022. The clearance rates were lower for aggravated assault (41.4%), rape (26.1%) and robbery (23.2%).
When it comes to property crime, law enforcement agencies cleared 13.0% of burglaries, 12.4% of larcenies/thefts and 9.3% of motor vehicle thefts in 2022.
Are police solving more or fewer crimes than they used to?
Nationwide clearance rates for both violent and property crime are at their lowest levels since at least 1993, the FBI data shows.
Police cleared a little over a third (36.7%) of the violent crimes that came to their attention in 2022, down from nearly half (48.1%) as recently as 2013. During the same period, there were decreases for each of the four types of violent crime the FBI tracks:
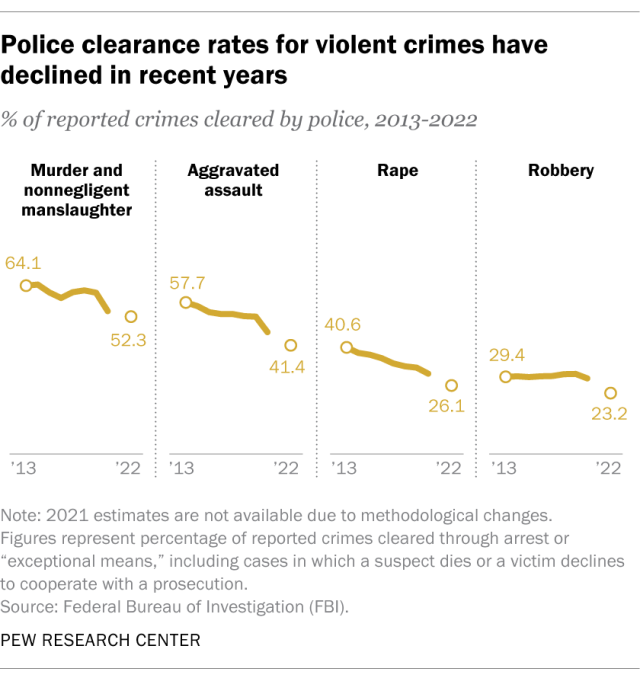
- Police cleared 52.3% of reported murders and nonnegligent homicides in 2022, down from 64.1% in 2013.
- They cleared 41.4% of aggravated assaults, down from 57.7%.
- They cleared 26.1% of rapes, down from 40.6%.
- They cleared 23.2% of robberies, down from 29.4%.
The pattern is less pronounced for property crime. Overall, law enforcement agencies cleared 12.1% of reported property crimes in 2022, down from 19.7% in 2013. The clearance rate for burglary didn’t change much, but it fell for larceny/theft (to 12.4% in 2022 from 22.4% in 2013) and motor vehicle theft (to 9.3% from 14.2%).
Note: This is an update of a post originally published on Nov. 20, 2020.
- Criminal Justice

John Gramlich is an associate director at Pew Research Center
8 facts about Black Lives Matter
#blacklivesmatter turns 10, support for the black lives matter movement has dropped considerably from its peak in 2020, fewer than 1% of federal criminal defendants were acquitted in 2022, before release of video showing tyre nichols’ beating, public views of police conduct had improved modestly, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Terms & Conditions
Privacy Policy
Cookie Settings
Reprints, Permissions & Use Policy

IMAGES
VIDEO
COMMENTS
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on CYBER LAW. Find methods information, sources, references or conduct a literature review on CYBER LAW
Cybercrime and the Law: Computer Fraud and Abuse Act and the 116th Congress Congressional Research Service 1 Introduction Today, with computers more prevalent than ever before,1 illicit computer-based activities such as hacking—intrusions or trespasses "into computer systems or data"2—are commonplace.3 For example, on July 15, 2020, a malicious actor temporarily coopted the social ...
Abstract. This is the full text of my interdisciplinary "eCasebook" designed from the ground up to reflect the intertwined nature of the legal and policy questions associated with cyber-security.
Cybercrime and the Law: Primer on the Computer Fraud and Abuse Act Congressional Research Service 1 Introduction Computers are more prevalent than ever before.1 Their ubiquity has made them a favored tool for, and target of, criminals.2 In 2022—the most recent year for which data is available—the FBI's Internet Crime Complaint Center received 800,944 reported complaints of cybercrime with
Dr. Tamar Berenblum is the research director of the The Federmann Cyber Security Center - Cyber Law Program, Faculty of Law, the Hebrew University of Jerusalem, Israel, and the co-chair of the European Society of Criminology (ESC) Working Group on Cybercrime. Tamar is also a Post-Doc Research Fellow at the Netherlands Institute for the Study of Crime and Law Enforcement (NSCR), Netherlands ...
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the ...
This paper reviews current research, providing a comprehensive account of cybercrime and addressing issues in policing such offences. We achieve this by describing the technological, individual, social and situational landscapes conducive to cybercrime, and how this knowledge may inform strategies to overcome current issues in investigations.
Keywords: Cyber Laws, Cyberspace, information and communication technology, Cyberspace, electronic Suggested Citation: Suggested Citation Chauhan, Abha, Evolution and Development of Cyber Law - A Study with Special Reference to India (January 2, 2013).
Cybercrime is estimated to have cost the global economy just under USD 1 trillion in 2020, indicating an increase of more than 50% since 2018. With the average cyber insurance claim rising from USD 145,000 in 2019 to USD 359,000 in 2020, there is a growing necessity for better cyber information sources, standardised databases, mandatory reporting and public awareness. This research analyses ...
As further specified in the U.K. Home Office's Online Harms White Paper, ... rather than crime and law enforcement. As such, cyber terrorism is not the core interest of these UN "negotiations", but it is one of the few diplomatic fora where the concept is discussed. ... artistic or research purposes or for awareness-raising purposes ...
Finally the conclusion of the paper is presented. 2. ... The cyber action is carried out by a computer system and is merely in violation of criminal law. Cyber-attack and cyber-warfare: ... Manz D.O. (Eds.), Research Methods for Cyber Security, Syngress (2017), pp. 33-62 (Chapter 2) View PDF View article Google Scholar. Furnell and Shah, 2020.
The rise of cybercrime, often known as e-crimes (electronic crimes), is a major challenge confronting today's society. As a result, cybercrime poses a threat to nations, companies, and individuals all across the world. It has expanded to many parts of the globe, and millions of individuals have become victims of cybercrime.
In the post-COVID-19 era, international consensus is in agreement of the threat of cybercrime being a top-level concern [].The pandemic led society and institutions to a global accelerated digitalisation, and in doing so reshaped the landscape in which cybercrime and cybersecurity operate [].With domestic statistics suggesting an 89% increase in computer misuse offences and a 25% increase in ...
The conclusions established that close ties at the level of international law enforcement systems aimed at addressing cybercrime issues could be effective in overcoming these difficulties. Combating cybercrime is one of the most relevant areas of the legal community development since the widespread integration of digital technologies into all spheres of human activity demonstrates the need to ...
He has published more than 150 scientific papers in peer-reviewed journal and conferences in related research fields and his recent edited book has been listed the Best New Digital Forensics Book according to BookAuthority. Kim-Kwang Raymond Choo received the Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia.
The International Journal of Multi-Disciplinary Research ISSN: 3471-7102, ISBN: 978-9982-70-318-5 1 Paper-ID: CFP/731/2018 www.ijmdr.net Analysis of Cybercrime and Cyber Law Effectiveness in Zambian (Conference ID: CFP/731/2018 1 Nizah Lawrence Mutambo, 2 Dr. Phiri
Abstract. With the rapid development of computer technology and internet over the years, the problem of cyber crime has assumed gigantic proportions and emerged as a global issue. It has created an entirely new set of problems for law enforcement agencies all over the world. It has equally become cause of serious concern for the legal ...
IJCRT2201567 International Journal of Creative Research Thoughts (IJCRT) www.ijcrt.org f6 THE ROLE OF CYBER LAW IN CYBER SECURITY IN INDIA: AN ANALYSIS Advocate Sanchi Gupta This paper would be discussing about the various form of cyber-crimes and the problem faced in the society because of the crimes in digital form.
Legal constraints on NCMEC and U.S. law enforcement have implications for efficiency. These issues would be best addressed by a concerted effort to massively uplift NCMEC's technical and analytical capabilities, which will require the cooperation of platforms, NCMEC, law enforcement and, importantly, the U.S. Congress.
Starting with Phi-1, a model used for Python coding, to Phi-1.5, enhancing reasoning and understanding, and then to Phi-2, a 2.7 billion-parameter model outperforming those up to 25 times its size in language comprehension. 1 Each iteration has leveraged high-quality training data and knowledge transfer techniques to challenge conventional ...
Abstract. This paper mainly deals with the laws relating to the cyber crimes in India. The objectives of this research paper are four-fold: firstly, to analyze the concept of jurisdiction and the various theories to determine jurisdiction in cases where such offences are committed relating to cyber crimes; secondly, to analyze the jurisdiction theories applicable under Cybercrime Convention ...
To measure public attitudes about crime in the U.S., we relied on survey data from Pew Research Center and Gallup. ... Overall, law enforcement agencies cleared 12.1% of reported property crimes in 2022, down from 19.7% in 2013. The clearance rate for burglary didn't change much, but it fell for larceny/theft (to 12.4% in 2022 from 22.4% in ...