BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings

Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
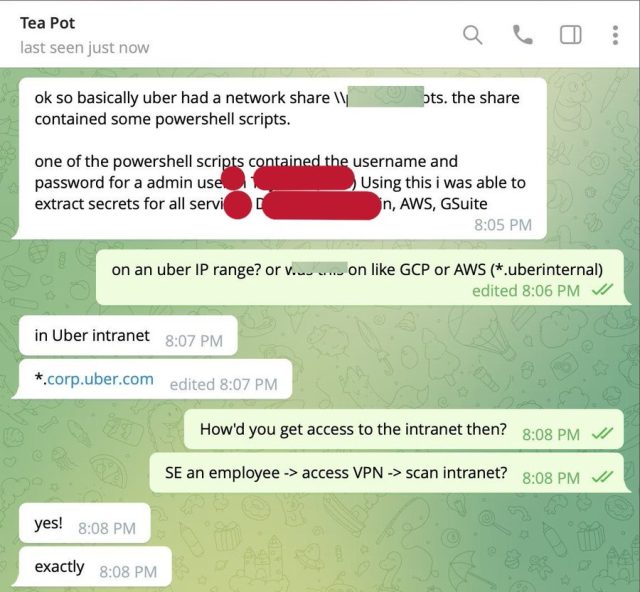
What caused the uber data breach in 2022.

Edward Kost
The Uber data breach began with a hacker purchasing stolen credentials belonging to an Uber employee from a dark web marketplace. An initial attempt to connect to Uber’s network with these credentials failed because the account was protected with MFA. To overcome this security obstacle, the hacker contacted the Uber employee via What’s App and, while pretending to be a member of Uber’s security, asked the employee to approve the MFA notifications being sent to their phone. The hacker then sent a flood of MFA notifications to the employee’s phone to pressure them into succumbing to this request. To finally put an end to this notification storm, the Uber employee approved an MFA request, granting the hacker network access, which ultimately led to the data breach.
After completing the attack, the hacker compromised an Uber employee’s Slack account and announced the successful breach to the entire company.

This isn’t the first time Uber has been hacked. In 2016, two hackers breached Uber’s systems , accessing names, email addresses, and phone numbers of 57 million users of the Uber app.
What Data Did the Hacker Access?
After successfully connecting to Uber’s intranet, the hacker gained access to the company’s VPN and discovered Microsoft Powershell scripts containing the login credentials of an admin user in Thycotic - the company’s Privileged Access Management (PAM) solution . This discovery significantly increased the severity of the breach by facilitating full admin access to all of Uber’s sensitive services, including DA, DUO, Onelogin, Amazon Web Services (AWS), and GSuite.
The hacker also allegedly accessed Uber’s bug bounty reports which usually contain details of security vulnerabilities yet to be remediated.
The 18-year-old hacker, believed to be associated with the cybercriminal group, Lapsus$, revealed the details of the attack in a conversation with cybersecurity researcher Corben Leo .

Was any Sensitive User Data Stolen During the Uber Breach?
Despite the deep level of compromise the hacker achieved, no evidence of customer data theft has been announced. This is likely because the hacker wasn’t intent on causing harm but was, rather, chasing the thrill of a successful cyberattack and the hacker community respect that comes with it.
Had the hacker been motivated by financial gain, he would have likely sold Uber’s bug bounty reports on a dark web marketplace. Given the devastating data breach impact that’s possible with the findings of a bug bounty program, it would have sold for a very high price.
To say that Uber is lucky this hacker wasn’t an actual cybercriminal is a significant understatement. The company came so close to a complete system shutdown. From a cybersecurity perspective, it seems almost unbelievable that after taking complete control of Uber’s systems, the hacker just dropped everything and walked away. Without any security obstacles left to overcome, it would have been so easy to tie off the breach with a quick installation of ransomware.
Given Uber’s poor reputation for handling extorsion attempts, thankfully, this didn’t happen. When Uber was breached in 2016, the company paid the cybercriminals their $100,000 ransom in exchange for deleting their copy of the stolen data. Then, in an attempt to conceal the event, the company forced the hackers to sign a non-disclosure agreement and made it appear like the ransom payment was an innocuous reward within the company’s bug bounty program.

4 Key Lesson From the Uber Data Breach
Several critical cybersecurity lessons can be learned from the Uber data breach. By applying them to your cybersecurity efforts, you could potentially avoid suffering a similar fate.
1. Implement Cyber Awareness Training
The fact that the Uber employee eventually gave into the flood of MFA requests in the initial stage of the attack is evidence of poor awareness of a common MFA exploitation tactic known as MFA Fatigue. Had the Uber employee been aware of this tactic, they would have likely reported the threat rather than falling victim to it, which would have prevented the breach from happening. The hacker also utilized social engineering techniques to fool the Uber employee into thinking they were a member of Uber’s security team, which is another common cyberattack tactic.
Implementing cyber awareness training will equip your staff to recognize the common cyberattack methods that made this breach possible - MFA fatigue and social engineering.
The following free resources can be used to educate your employees about common cyber threats and the importance of cybersecurity:
- What is Phishing?
- What is Ransomware-as-a-Service?
- What is Malware?
- What is a Cyber Threat?
- Why is Cybersecurity Important?
- What is a Data Breach?
2. Be Aware of Common MFA Exploitation Methods
Not all Multi-Factor Authentication protocols are equal. Some are more vulnerable to compromise than others. Your cybersecurity teams should compare your current MFA processes against common exploit tactics and, if required, upgrade the complexity of authentication protocols to mitigate exploitation.
Learn about common MFA bypass methods >
3. Never Hardcode Admin Login Credentials Anywhere (Ever)
Probably the most embarrassing cybersecurity blunder in this incident is the hardcoding of admin credentials inside a Powershell script. This meant that the potential of an unauthorized user accessing uber’s sensitive systems was always there - all that was required was for someone to read the Powershell script and discover admin credentials contained therein.
This security flaw would have been avoided if secure coding practices had been followed. Admin credentials should always be stored securely in a password vault and certainly never hardcoded anywhere.
4. Implement a Data Leak Detection Service
If the Uber hacker had more malicious intentions, customer data woud have been stolen, published on the dark web, and accessed multiple times by cybercriminals before Uber even realized it was breached. It’s crucial for organizations to have a safety net in place for detecting dark web data leaks from undetected data breaches, from both first-hand and third-party attacks.
A data leak detection service notifies impacted businesses when sensitive data leaks are detected on the dark web so that cybersecurity teams can secure compromised accounts before they’re targeted in follow up attacks.
Learn how data leak detection can reduce the impact of ransomware attacks.

See how your organization's security posture compares to Uber's.
View Uber's security report .
Learn about other Famous Data Breaches:
- What Caused the Optus Data Breach?
- What Caused the Medicare Data Breach?
- How did LAUSD Get Hacked?
- How did Plex Get Hacked?
- How did Cash App Get Hacked?
Reviewed by

Kaushik Sen
Ready to see upguard in action, join 27,000+ cybersecurity newsletter subscribers, a complete guide to data breaches.

Related posts
How to prevent data breaches in 2024 (highly effective strategy), the 72 biggest data breaches of all time [updated 2024].

9 Ways to Prevent Third-Party Data Breaches in 2024
What are cloud leaks, what is a supply chain attack examples & prevention strategies, zero trust as a defence against supply chain attacks.
- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
- Mobile Site
- Staff Directory
- Advertise with Ars
Filter by topic
- Biz & IT
- Gaming & Culture
Front page layout
UBER HACKED —
Uber was breached to its core, purportedly by an 18-year-old. here’s what’s known, “i announce i am a hacker and uber has suffered a data breach,” intruder says on slack..
Dan Goodin - Sep 16, 2022 5:29 pm UTC

Uber employees on Thursday discovered that huge swaths of their internal network had been accessed by someone who announced the feat on the company Slack channel. The intruder, who sent screenshots documenting the breach to The New York Times and security researchers, claimed to be 18 years old and was unusually forthcoming about how it occurred and just how far it reached, according to the news outlet, which broke the story .
It didn’t take long for independent researchers, including Bill Demirkapi , to confirm The New York Times coverage and conclude that the intruder likely gained initial access by contacting an Uber employee over WhatsApp.
The Uber hack is quite severe and wide ranging. Wishing their blue teams the best of luck and love during this understandably difficult period. Some thoughts & observations based on what we've seen so far 👉 1/N — Bill Demirkapi (@BillDemirkapi) September 16, 2022
After successfully obtaining the employee’s account password, the hacker tricked the employee into approving a push notification for multifactor authentication. The intruder then uncovered administrative credentials that gave access to some of Uber’s crown-jewel network resources. Uber responded by shutting down parts of its internal network while it investigates the extent of the breach.
It’s not yet clear precisely what data the hacker had access to or what other actions the hacker took. Uber stores a dizzying array of data on its users, so it’s possible private addresses and the hourly comings and goings of hundreds of millions of people were accessible or accessed.
Here’s what’s known so far.
How did the hacker get in?
According to the NYT, the above-linked tweet thread from Demirkapi, and other researchers, the hacker socially engineered an Uber employee after somehow discovering the employee’s WhatsApp number. In direct messages, the intruder instructed the employee to log in to a fake Uber site, which quickly grabbed the entered credentials in real time and used them to log in to the genuine Uber site.
Uber had MFA, short for multifactor authentication, in place in the form of an app that prompts the employee to push a button on a smartphone when logging in. To bypass this protection, the hacker repeatedly entered the credentials into the real site. The employee, apparently confused or fatigued, eventually pushed the button. With that the attacker was in.
After rifling around, the attacker discovered powershell scripts that an admin had stored that automated the process of logging in to various sensitive network enclaves. The scripts included the credentials needed.
What happened next?
The attacker reportedly sent company-wide texts on Uber Slack channels, announcing the feat.
“I announce I am a hacker and Uber has suffered a data breach,” one message read, according to the NYT. Screenshots provided evidence that the individual had access to assets, including Uber’s Amazon Web Services and G Suite accounts and code repositories.
It remains unclear what other data the hacker had access to and whether the hacker copied or shared any of it with the world at large. Uber on Friday updated its disclosure page to say: "We have no evidence that the incident involved access to sensitive user data (like trip history)."
What do we know about the hacker?
Not much. The person claims to be 18 years old and took to Uber Slack channels to complain that Uber drivers are underpaid. This, and the fact that the intruder took no steps to conceal the breach, suggest that the breach is likely not motivated by financial gain from ransomware, extortion, or espionage. The identity of the individual remains unknown so far.
What is Uber doing now?
The company acknowledged the breach and is investigating.
We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available. — Uber Comms (@Uber_Comms) September 16, 2022
Did an 18-year-old really access the crown jewels of one of the world’s most sensitive companies? How can this be?
It’s too soon to say for sure, but the scenario seems plausible, even likely. Phishing attacks remain one of the most effective forms of network intrusion. Why bother with expensive and complex zero-day exploits when there are much easier ways to trespass?
Further Reading
Does this mean mfa using one-time passwords or pushes are useless.
This sort of MFA will protect users if their password is compromised through a database breach. But as has been demonstrated repeatedly, they are woefully inadequate at stopping phishing attacks. So far, the only forms of MFA that are phishing-resistant are those that comply with an industry standard known as FIDO2. It remains the MFA gold standard.
Many organizations and cultures continue to believe that their members are too smart to fall for phishing attacks. They like the convenience of authenticator apps as compared to FIDO2 forms of MFA, which require the possession of a phone or physical key. These types of breaches will remain a fact of life until this mindset changes.
What is the reaction to the breach so far?
Uber’s stock price was down about 4 percent on Friday, amid a broad sell off that sent share prices of many companies even lower. The Dow Jones Industrial Average dropped 1 percent. The S&P 500 and Nasdaq Composite fell 1.2 percent and 1.6 percent, respectively. It’s not clear what’s driving Uber shares lower and what effect, if any, the breach has in the drop.
Promoted Comments
Reader comments, channel ars technica.
Uber Users: What You Need to Know about Last Month’s Data Breach
MET cybercrime expert on how hacker likely gained access to company data and systems

Educating employees is crucial to prevent hacks, BU cybersecurity expert says. File photo by Jeff Chiu/AP Photo
Lindsay Shachnow (COM’25)
Last month, the internal databases of American multinational ride-share company Uber were hacked . The unnamed 18-year-old who claimed responsibility for the hack said Uber’s ineffective security measures made the breach possible. The hacker, who was eventually arrested and is in police custody, is said to have gained access to Uber’s secure data through “social engineering,” which means manipulating or deceiving someone, often with email or phone calls, to gain access to personal or financial information. These manipulation methods are becoming commonplace in the world of cybercrime. By posing as a corporate information technology worker, the hacker claimed to have convinced an Uber contractor to reveal the password to Uber’s systems. Uber says it is also possible the hacker bought the corporate password on the dark web.
According to Uber, having obtained the contractor’s password, the hacker sent repeated log-in requests to the contractor’s account and was then able to bypass Uber’s two-factor log-in authentication—a system where a user is granted access after electronically confirming their identity twice—when the contractor finally accepted the authentication. The hacker was also admitted to the Uber Slack account and posted a message that read: “I announce I am a hacker and Uber has suffered a data breach.”
A security update from Uber says they believe the cybercrime group Lapsus$ is responsible for the attack. “We’re working with several leading digital forensics firms as part of the investigation,” Uber writes. “We will also take this opportunity to continue to strengthen our policies, practices, and technology to further protect Uber against future attacks.”
BU Today spoke with Kyung-shick Choi (MET’02), a Metropolitan College professor of the practice and director of its Cybercrime Investigation & Cybersecurity programs , about the implications of the hack and how companies and users can protect themselves.
This interview has been edited for length and clarity.
with Kyung-shick Choi
Bu today: can you briefly describe the scope of uber’s security breach.
Choi: Uber’s security breach is quite an interesting case, because unlike other major breaches, I wonder if the hacker attained what they really wanted to attain. I was expecting some sort of ransomware attack so they could seek financial gain. But this time, it looks like they didn’t really get much. Of course, maybe Uber’s cybersecurity quickly responded to the incident, but they clearly stated they hacked right on the Slack. And so to me, that’s much more what the motivation could be. They already identified the potential suspect, Lapsus$. It’s a Brazilian hacker group—I presume a group of teenagers. We call them “cyber punks.” They have been really active recently and are gaining fame. I think maybe that’s why they were aiming at such a huge company.
BU Today: Can you talk about their methods, how they possibly gained access?
Choi: According to Uber, the hacker group purchased the log-in password from the dark web. It’s very common that hackers are trading, selling, and buying older password and log-in names. So consider, if they are cyber punks and not extremely skillful, just getting the credential through the dark web is the easiest way to commit crime, rather than a complicated hacking process. So maybe that’s what’s happening in this case. Now, Uber has a two-factor authentication system, and so that’s double protection. With two-factor authentication, you get that notification and you have to press the buttons. So maybe [an Uber worker] thought, okay, I did it, and so they approve. So that’s one way, and that’s pure luck to be honest, if [the hackers] did it that way. Another way, if they’re really dedicated hackers, [is to] get deeper into the system. And then they [would] escalate the privilege and change the information to switch the contact to their own. It has to be a burner phone so that you can get your own authentication using the burner. That’s what pretty skillful hackers do, but it looks like the [Uber hackers were] not at that level. That’s my assumption. But normally cyber punks try and try and try, and can kind of luckily get in.
BU Today: What are the potential ramifications for users and their data as a result of the hack?
Choi: Personal data is so important. Every single person’s data can be weaponized and used against them. Your data can be used for criminal purposes, for account takeover, or financial gain. And then, of course, [hackers] can sell the information. And that’s why privacy is so important, in that we really have to protect ourselves. I can expand it to sexual crime. And so if hackers find out the date of birth, location, and all of that, they can stalk people and then even commit sextortion. I’ve seen those cases a lot. People think, oh, this is just one hack. But it’s not just one hack. The damage could be substantial to individuals, families, and the community at large. That’s why we have to be really cautious.
BU Today: What data is believed to be compromised by the attack?
Hackers downloaded the financial information from Slack. The financial information could be anything. It could be invoices or employment information. So, I think [Uber and the authorities] are currently investigating that and what types of information were compromised. According to them, nonsensitive data was exposed, but we don’t know until we really see what happened. Credit card information is encrypted and so that information is safe, and other travel information is secure. I think right after the incident [Uber] reported it to law enforcement and now the FBI is involved. I think [Uber] did the right thing, so once the FBI gets involved and they do a very extensive investigation, we will receive much more accurate information.
BU Today: Do you think Uber handled the situation well?
I didn’t see the evidence. If I investigated it, then maybe I could see the log file and when they really got hacked. In most hacking incidents, especially on a big scale, the corporations don’t report the victimization right away. I hope Uber reported it right away. At least the suspect and the hacking group left a message, but we don’t know when they really started. And so maybe they spent extensive time, maybe a month of time, until they got to that stage. Commonly, major cases are similar in that way because [hacked companies] don’t want to ruin their reputation from the corporate side. They don’t want to give bad images to the public. Who’s going to use Uber if they constantly get hacked? In this case, [Uber] saw the sign of the hack and they reported it to law enforcement. I think that’s the right way to do it. And that’s why maybe the damages, according to Uber, are minimal. Although, we don’t know yet.
BU Today: Are other rideshare apps vulnerable to similar attacks?
Of course. Because of the tendency of hackers, if they are professional hackers, they will never attack headquarters, because headquarters have a lot of security built right there. All the major hacks, if you really examine them, are not really happening by directly hacking into the main server. [Hackers] are always finding the small vendors. The size of the company could be very small. That’s a vulnerability right there. That’s also how you handle digital information, and that’s very important. But definitely Lyft and all the others should be careful. So that means they need to educate their employees.
BU Today: What steps should Uber and other rideshare apps take to prevent similar attacks in the future?
I have my own theory and my theory has become dominant in computer crime victimization. It’s called “cyber-routine activities theory.” Very simple. There are two factors that contribute to computer crime victimization. So either online behavior, that means a human error, and/or there’s a security issue. Business emails getting compromised is always the number one computer crime victimization throughout the history of the internet or email. Then another factor is cybersecurity. What if you don’t have basic protection? What if you don’t have the internal security management? Meaning, do you have a strong policy in place in your company? If something happens, incident response is so important. If you don’t have an incident response policy…they have everything. You just have to wait for law enforcement and watch the hackers stealing every single thing. You cannot do anything because you don’t know what to do. Also important is educating employees. It’s critical. Many [hacking] cases, I would say close to 50 percent, come from an insider. So that’s why you have to maintain all the security credentials, especially when [employees] leave the company. Revenge is a huge factor. [If] they’re not just leaving nicely…[if] they’re doing something with it, maybe selling the information, or sharing all the credentials, or selling it to the dark web.
BU Today: It’s believed the hacker potentially gained access to Uber’s internal systems through a psychological manipulation tactic referred to as social engineering. How can Uber and other companies better prepare and train their employees to identify these persuasive techniques?
The effective training has to be hands-on training. So statistically speaking, hands-on training really boosts your long-term memory. This type of training is essential so that you feel it when you click it and see what happens. Our programs at MET are designed to train our future law enforcement in cybercrime investigation and cybersecurity. We’re creating a scenario. So we have a suspect and a victim. Students really feel it. They are investigating the case and see how [the hacker] sends a phishing email and they really observe. Also, technology quickly evolves, almost everyday. And then our online behavior quickly adapts. The companies should think about that and the changing technology. Companies should really know their employee populations and the characteristics for using social media, for example.
BU Today: How can users protect themselves and their personal data when using rideshare apps?
Anytime you hear an incident has happened, the first thing you have to do is change your passwords. If you see anything happen, like a hacking incident from the company side, I highly recommend changing passwords so [hackers] cannot do anything further. And so of course, never use the password you have used before. If I were an Uber customer, I would have a very strong password. And be careful when you download apps, by making sure you are downloading genuine apps, because there are lots of replicated ones.
Explore Related Topics:
- Cybersecurity
- Digital Learning
- Public Safety
- Share this story
- 4 Comments Add
Lindsay Shachnow (COM’25) Profile
Comments & Discussion
Boston University moderates comments to facilitate an informed, substantive, civil conversation. Abusive, profane, self-promotional, misleading, incoherent or off-topic comments will be rejected. Moderators are staffed during regular business hours (EST) and can only accept comments written in English. Statistics or facts must include a citation or a link to the citation.
There are 4 comments on Uber Users: What You Need to Know about Last Month’s Data Breach
Excellent interview with Dr. Choi. Very important points to consider regarding doing what we can to take responsibility to be more cyber-safe.
Dr. Choi states, “Hackers downloaded the financial information from Slack. The financial information could be anything. It could be invoices or employment information.”
I have never seen invoices or financial information stored in Slack. Can someone elaborate?
Other patterns to look for:
Get an email from or about old bank accounts or companies you’ve had dealings with. This could be an indicator of a compromise. One should think “Did I initiate this?” If you didn’t be suspect of that information.
As a active defender in cybersecurity, I can say we the fronts are being fought with very complex hacking methods and defenses. One that often get skipped is the human element.
We can secure information in a variety of ways, and almost all of them can be undone with the human factor. People may very well still be our best line of defense against cyber threats.
Protection against the threat actors is not just the responsibility of cybersecurity professionals, we work with you, to help protect you. The better informed our human firewalls are the more armed they to stop these threats, even the lazy ones.
@emily “I have never seen invoices or financial information stored in Slack. Can someone elaborate?”
I’m going to assume a lot here: Slack does have inherent security protocols, that companies often deem “internal”. So with an internal slack channel companies and employees feel these pathways are safe to divulge sensitive information. This is understandable for the following: Teams are separated with remote work and pandemics Teams maybe separated by buildings or someone is out of the office etc..
All viable reasons, but while the measure are there to protect the information systems, it doesn’t take into account “what if someone else sees it” from over the shoulder to screen capture.
So good security best practice is even in slack (secure channels) the assumption should be ” is this information valuable to someone other than the intended recipient?” If your answer is YES?
ENCRYPT or DO NOT POST IT in slack. Logs exists for many reasons, but historical data that is not redacted, backed up, or secured is always a risk.
Back to the human element. Its easier for the team to work remotely if we can post invoices in slack for quick viewing. That same ease of workflow, also provides ease of access to information that should be guarded,
Even if the intent is to improve, the risk of that improvement should be mitigated.
I am an uber driver and I feel as if my phone has been hacked ever since the end of August 2022. My phone company, us cellular can’t seem to figure out what is going on with my service not working. Even a new phone didn’t fix the problem.
Post a comment. Cancel reply
Your email address will not be published. Required fields are marked *
Latest from BU Today
Pov: baseball needs to shake up the game—or risk a slow death, meet bu’s diy bicycle repair shop, women’s golf going for fourth patriot league title this weekend, the weekender: april 18 to 21, louis chude-sokei brings bu, spoken word, and dub reggae sounds to venice biennale, can i fall in love with ai, a visit to auschwitz exhibition in boston recalls one of history’s darkest periods, bu’s macklin celebrini wins 2024 hobey baker memorial award, learn more about bu spark bu’s innovation and experiential learning lab, bu student aviator soars to new heights, pov: policymakers are entitled to their own opinions. but should they be entitled to their own science, bu falls 2-1 in overtime in 2024 ncaa semifinal, bu ras authorize four-day strike over contract negotiations, ai task force report recommends critical embrace of technology and cautious use of ai-detector apps, a wrinkle in time closes out wheelock family theatre’s 2023–2024 season, bu softball hosts holy cross in 2024 patriot league home opener, six bu runners share their boston marathon charity stories, join the citywide festivities for one boston day: discover events across town, seven things to know as bu begins the 2024 frozen four, the weekender: april 11 to 15.
The Uber Breach Case Study: Cybersecurity Lessons Learned

Industry: Personal transportation industry
Uber, a global transportation technology company that has revolutionized the way people travel, work, and connect in the modern world. Founded in 2009, Uber has rapidly grown to become one of the most recognizable and disruptive brands in the transportation and technology industry.
How Did the Data Breach Occur?
Uber, a globally recognized ride-sharing and technology company experienced a data breach, as a result of a sophisticated cyberattack. The attack was orchestrated by a hacker affiliated with the hacking group known as Lapsus$ . The breach was identified on September 19, 2022, at 10:45 am PT, as reported by the Uber Team via their official newsroom.
The breach unfolded as follows:
- Compromised Contractor Account : An external contractor working with Uber had their account compromised by the attacker. The attacker likely gained access to the contractor’s Uber corporate password through illicit means, potentially purchasing it on the dark web.
- Malware Infection : The contractor’s personal device became infected with malware, which exposed their login credentials. This breach provided the attacker with a significant foothold.
- Repetitive Login Attempts : The attacker repeatedly attempted to log in to the contractor’s Uber account. Initially, these attempts were blocked by two-factor authentication (2FA), as the contractor received approval requests. Eventually, the user accepted one of those requests, allowing the attacker to successfully access the account. A classic example of Social Engineering where human error was caused as a result of MFA fatigue.
- Elevation of Privileges : Once in, the attacker leveraged this compromised account to access other employee accounts. This enabled them to gain elevated permissions, including access to vital tools such as G-Suite and Slack.
- Message Post and Configuration Change : The attacker posted a message on a company-wide Slack channel, informing employees about their successful intrusion. They also reconfigured Uber’s OpenDNS to display a graphic image on some internal sites, affecting employees’ access.
What Was Compromised?
The Uber data breach, which saw the compromise of their Privileged Access Management (PAM) platform, has had far-reaching consequences, critically impacting the company’s security posture. The breach revealed the severity of the incident, as it potentially granted the attacker access to multiple internal systems and services that Uber relies on.
The list of systems that were compromised:
- Thycotic (PAM)
- Google Workspace Admin
- AWS Instance
- SentinelOne (XDR)
- VMware vSphere
- Slack Workspace
- UberInternal Financial Data
What was the Impact of the Data Breach as a Whole?
The impact of the Uber data breach was massive. Here’s an impact analysis of the breach:
- Data Exposure : The attacker gaining admin access to the Thycotic PAM system was a severe blow to Uber’s security. Privileged Access Management or PAM tools are designed to secure, control, and monitor access to critical information and resources. With access to Thycotic, the attacker unlocked a treasure of sensitive credentials and passwords, compromising the security of various Uber systems.
- Data Exposure : The hacker having administrative access to Uber’s Google Workspace raised concerns about the potential exposure of sensitive corporate documents, emails, and communication records.

- Security Vulnerabilities : Unauthorized access to Uber’s AWS services posed a significant security risk, potentially allowing the hacker to manipulate or exfiltrate data.

- Network Vulnerability : Access to Uber’s firewall could have enabled the hacker to manipulate network traffic, compromise communication channels, and potentially gain deeper access to the company’s systems.

- On-Premise Server Risk : The attacker could potentially infiltrate on-premise servers, jeopardizing data security, executing unauthorized commands, and moving laterally through Uber’s infrastructure.
- Cloud Resource Manipulation : Administrative access enabled the attacker to manipulate cloud resources, potentially disrupting services, misusing computing power, and impacting critical system availability.

- Communication Exposure : Gaining access to Uber’s Slack workspace jeopardized the privacy of internal communications. Messages exchanged on Slack, including sensitive discussions and file sharing, might have been compromised.

- Detailed Vulnerability Information: HackerOne is a platform used by organisations to compensate and collaborate with security researchers who identify vulnerabilities in systems, offering rewards for their contributions. The severity of this breach is underscored by the amount of detailed information often provided by security researchers. Access to the HackerOne account could have exposed these detailed “how-to” guides on exploiting vulnerabilities within Uber’s IT systems.

- Financial Risk : Access to Uber’s financial data posed significant financial risks. The breach may have exposed sensitive financial information, making it susceptible to misuse or extortion.

How organisations can protect against incidents like the Uber data breach?
Social engineering was the root cause of the Uber breach, and in this instance, MFA Fatigue allowed the hacker to gain access. With the continuous advancement of AI, hackers and their tactics are growing more sophisticated every day. Traditional security awareness and training methods are no longer sufficient. Organizations must shift their focus towards bringing behavioural change by influencing users’ psychology. Smart, gamified learning holds the key.
- Network Isolation : Organizations can minimize the impact of a breach by segregating their networks into separate segments. This strategy will help contain potential intrusions, limiting the lateral movement of attackers within the network.
- Access Control : Apply the principle of least privilege. Implementing network segmentation ensures that employees and systems only have access to the resources and data required for their roles, reducing the attack surface for potential breaches.
- Granular Control : Robust PIM/PAM solutions grant organizations the ability to control, monitor, and secure privileged identity and access to critical systems. This includes the enforcement of strong access policies, multi-factor authentication, and continuous monitoring of privileged accounts.
- Audit Trails : Keeping detailed audit trails helps organizations track privileged access and detect unusual activity, enabling swift responses to potential breaches.
- Smart Adaptive Training and Awareness : Humans are the most attacked vectors and, organizations must invest in gamified employee training and awareness programs. This not only involves running advanced phishing simulations but also, educating staff about phishing threats, best practices, and making them suspicious by nature.
- Continuous Monitoring : What you can measure, you can manage! Implement tools that continuously assess and monitor employees’ behaviour to detect unusual patterns and potential insider threats.
- Build the culture of reporting : Establish a company-wide culture that prioritizes security and encourages employees to be vigilant. Encourage and enable them to report suspicious activities with 1 click, fostering a collaborative approach to cybersecurity.
- Clear Policies and Reporting Mechanisms : Ensure that employees understand company security policies, know how to easily and seamlessly report incidents, and feel supported in doing so.
- Automate and Gamify the Learning Experience : There are over 20,000+ types of attack scenarios. You cannot train your employees for all. Instead, you can make them suspicious by nature by altering their psychology. It’s crucial to both automate and gamify the learning experience in order to alter the psychology. Automation ensures that employees receive timely and relevant training, staying up-to-date with the ever-evolving threat landscape. By introducing gamification elements, learning becomes engaging and competitive, motivating participants to enhance their security awareness.
- Seeing is believing : Conducting live hack show demonstrations is essential for organizations to provide a hacker’s perspective and help users understand just how vulnerable they can be to cyberattacks. It can help them to stay motivated not only to protect the organisation but also, to ensure vigilance for their personal safety.
The crucial lesson from this Uber breach is that in today’s evolving cybersecurity landscape, continuous training and putting people at the centre of security are paramount. Human error, often unintentional, can lead to dire consequences, making it crucial for organizations to invest in robust security awareness training. It’s not just about technology; it’s about bringing the culture of security and ensuring that employees are well-prepared and enabled to recognize & respond to threats efficiently. This human-centric approach is key to preventing cyberattacks and safeguarding sensitive data.
- Skip to main content
- Keyboard shortcuts for audio player
After a serious breach, Uber says its services are operational again
The Associated Press

An Uber sign is displayed at the company's headquarters in San Francisco on Monday. Jeff Chiu/AP hide caption
An Uber sign is displayed at the company's headquarters in San Francisco on Monday.
The ride-hailing service Uber said Friday that all its services are operational following what security professionals were calling a major data breach. It said there was no evidence the hacker got access to sensitive user data.
What appeared to be a lone hacker announced the breach on Thursday after apparently tricking an Uber employee into providing credentials.
Screenshots the hacker shared with security researchers indicate this person obtained full access to the cloud-based systems where Uber stores sensitive customer and financial data.
It is not known how much data the hacker stole or how long they were inside Uber's network. Two researchers who communicated directly with the person — who self-identified as an 18-year-old to one of them— said they appeared interested in publicity. There was no indication they destroyed data.
But files shared with the researchers and posted widely on Twitter and other social media indicated the hacker was able to access Uber's most crucial internal systems.
"It was really bad the access he had. It's awful," said Corbin Leo, one of the researchers who chatted with the hacker online.
He said screenshots the person shared showed the intruder got access to systems stored on Amazon and Google cloud-based servers where Uber keeps source code, financial data and customer data such as driver's licenses.
"If he had keys to the kingdom he could start stopping services. He could delete stuff. He could download customer data, change people's passwords," said Leo, a researcher and head of business development at the security company Zellic.
Screenshots the hacker shared — many of which found their way online — showed they had accessed sensitive financial data and internal databases. Among them was one in which the hacker announced the breach on Uber's internal Slack collaboration ssytem.
Sam Curry, an engineer with Yuga Labs who also communicated with the hacker, said there was no indication that the hacker had done any damage or was interested in anything more than publicity. "My gut feeling is that it seems like they are out to get as much attention as possible."
Curry said he spoke to several Uber employees Thursday who said they were "working to lock down everything internally" to restrict the hacker's access. That included the San Francisco company's Slack network, he said.
In a statement posted online Friday, Uber said "internal software tools that we took down as a precaution yesterday are coming back online."
It said all its services — including Uber Eats and Uber Freight — were operational.
The company did not respond to questions from The Associated Press including about whether the hacker gained access to customer data and if that data was stored encrypted. The company said there was no evidence that the intruder accessed "sensitive user data" such as trip history.
Curry and Leo said the hacker did not indicate how much data was copied. Uber did not recommend any specific actions for its users, such as changing passwords.
The hacker alerted the researchers to the intrusion Thursday by using an internal Uber account on the company's network used to post vulnerabilities identified through its bug-bounty program, which pays ethical hackers to ferret out network weaknesses.
After commenting on those posts, the hacker provided a Telegram account address. Curry and other researchers then engaged them in a separate conversation, where the intruder provided screenshots of various pages from Uber's cloud providers to prove they broke in.
The AP attempted to contact the hacker at the Telegram account, but received no response.
Screenshots posted on Twitter appeared to confirm what the researchers said the hacker claimed: That they obtained privileged access to Uber's most critical systems through social engineering. Effectively, the hacker discovered the password of an Uber employee. Then, posing as a fellow worker, the hacker bombarded the employee with text messages asking them to confirm that they had logged into their account. Ultimately, the employee caved and provided a two-factor authentication code the hacker used to log in.
Social engineering is a popular hacking strategy, as humans tend to be the weakest link in any network. Teenagers used it in 2020 to hack Twitter and it has more recently been used in hacks of the tech companies Twilio and Cloudflare.
Uber has been hacked before.
Its former chief security officer, Joseph Sullivan, is currently on trial for allegedly arranging to pay hackers $100,000 to cover up a 2016 high-tech heist in which the personal information of about 57 million customers and drivers was stolen.
- Share full article
Advertisement
Supported by
Guest Essay
The Uber Hack Exposes More Than Failed Data Security

By Bruce Schneier
Mr. Schneier is a security technologist and the author of 14 books, including the forthcoming “A Hacker’s Mind: How the Powerful Bend Society’s Rules, and How to Bend them Back.”
Uber was hacked this month. The company said that the attacker — a teenager possibly linked to the incident was just arrested i n London — most likely obtained the corporate password of an Uber contractor. Using that person’s access, the hacker gained access to some of Uber’s internal systems: internal Slack messages, a finance tool for invoices and the dashboard where the company’s security researchers report bugs and vulnerabilities. It’s a big deal, and an embarrassment to the company.
Uber has said that it believes that the attacker is affiliated with a hacking group called Lapsus$, whose members are mostly teenagers and which has recently targeted several technology companies. Uber also said it had not seen any evidence that user data was compromised during the incident. In the lawsuits that will invariably result, we will learn more about what happened.
But any litigation against the company, whether it be by government agencies like the Federal Trade Commission, or class-action lawsuits by shareholders or perhaps even customers, will focus on the proximate causes of the hack. More fundamental are the underlying causes of security breaches: Current economic and political forces incentivize companies to skimp on security at the expense of both personal and national security. If we are ever to have a hope of doing better, we need to change the market incentives.
When you’re a high-tech start-up company, you are likely to cut corners in a lot of areas. It makes business sense — your primary focus is to earn customers and grow quickly enough to remain in business when your venture capital funding runs out. Anything that isn’t absolutely essential to making the business work is left for later, and that includes security culture and practices. It’s a gamble: Spending money on speed and features rather than security is a more likely path to success than being secure yet underfunded, underfeatured, or — worst of all — a year later to market.
Security can be improved later, but only if necessary. If you’ve survived the start-up world and become a runaway success, you’ve had to scale to accommodate your customers or users. You’ve been forced to improve performance and reliability, because your new higher-profile customers demand more. You’ve had to make your internal systems work for your hundreds and maybe thousands of employees. You’re now an established company, and you had better look and act that way.
But in all of that, you’ve never had incentive to upgrade your security. The quick-and-dirty systems you built in the beginning still work, and your customers or users don’t know what’s going on behind the curtain. Your employees are expected not to tell anyone, like chefs being told to stay in the kitchen. And truth be told, it’s expensive and time-consuming to rebuild everything from the ground up with security in mind.
This is something I see again and again in companies, and not only in start-ups. It’s even the same thing that the former Twitter security chief Peiter Zatko (better known as Mudge) is accusing that company of doing. Companies large and small skimp on security when the market doesn’t reward doing any better. The result is that hackers have an easier time breaking into networks, and once they break in there are few controls that prevent them from accessing everything.
Some companies do manage to make the change. We saw it with Microsoft, when Bill Gates changed the company’s direction in 2002 with a now-famous memo . Google’s shift to a more robust security culture happened in 2010, after being hacked by attackers in China .
The lack of incentives obviously has profound implications for the security of all of our personal data, stored by a seemingly unknowable number of different companies who are all collecting dossiers on our movements and habits. It also has national security implications. We know that countries are stealing as much data as possible for their own purposes. China, in particular, is apparently using its resources collecting data on Americans in general. State-sponsored Chinese hackers are believed to be behind the theft of personal data on U.S. government employees, especially those with security clearances, from the U.S. Office of Personnel Management in 2015. Hackers suspected of working on behalf of the country’s civilian spy agency were also apparently behind the theft of data on 500 million guests from the Marriott hotel chain in 2018 and about 80 million former and current patients and employees from the health insurer Anthem in 2015.
In all of these cases, the victimized organizations could have very likely protected our data better, but the reality is that the market does not reward healthy security. Often customers aren’t even able to abandon companies with poor security practices, as many of them build “ digital moats ” to lock their users in. Customers don’t abandon companies with poor security practices. Hits to the stock prices quickly recover . It’s a classic market failure of a powerful few taking advantage of the many, and that failure is one that only representation through regulation can fix.
We need strong regulations that force organizations to maintain good security practices. The focus must be on resilient security for the user data entrusted to the company. Government regulation should not be involved (for example) if Uber loses the source code to its phone apps or its employee Slack channel. Government regulation should be involved if Uber loses data about the rides taken by its 100 million-plus users. (One risk of this data for Uber: It can be used to find one-night stands , for either fun or blackmail opportunities.)
Worries that any regulation will somehow quell innovation are overblown. Good security isn’t incompatible with features, agility or time to market. But even so, a smart internet-security regulatory regime will take a page from successful industry regulations such as banking, and tailor requirements to the size of the organization. Just as a small local bank doesn’t have to follow the same level of regulation that a large national bank does, or a jumbo jet has a more extensive preflight checklist than a single-engine two-seater, there’s no reason a small start-up with only a few customers has to follow the same rules as a Twitter or an Uber. And as a company becomes larger and more successful, its security requirements should increase because the impact of insecurity increases.
In 2020, Russian hackers breached the internet infrastructure company SolarWinds. SolarWinds followed the trajectory from start-up to established company. This particular hack was a national security disaster. The hackers were able to use their access to penetrate the computer networks of some 18,000 SolarWinds customers, including U.S. government agencies such as the Homeland Security Department and State Department, government contractors, nuclear research labs, I.T. companies, and nongovernmental agencies around the world. Here again, the market rewarded poor security practices in the name of short-term profits. If the government mandated better ones, things might have turned out differently.
Last week’s Senate Judiciary Committee hearing, “ Protecting Americans’ Private Information From Hostile Foreign Powers ,” further highlighted that personal data privacy is now a matter of national security. And while regulation isn’t a panacea — nothing is in the world of security — it will serve to align corporate incentives with our broader societal goals. It will keep us all safer against both hackers and foreign governments.
Bruce Schneier is a security technologist and the author of 14 books, including the forthcoming “A Hacker’s Mind: How the Powerful Bend Society’s Rules, and How to Bend them Back.” He is a fellow at the Belfer Center at the Harvard Kennedy School and at the Berkman Klein Center for Internet and Society at Harvard.
The Times is committed to publishing a diversity of letters to the editor. We’d like to hear what you think about this or any of our articles. Here are some tips . And here’s our email: [email protected] .
Follow The New York Times Opinion section on Facebook , Twitter (@NYTopinion) and Instagram .
- International edition
- Australia edition
- Europe edition

Uber’s ex-security chief faces landmark trial over data breach that hit 57m users
Joe Sullivan’s trial is believed to be the first case of an executive facing criminal charges over such a breach
Uber’s former security officer, Joe Sullivan, is standing trial this week in what is believed to be the first case of an executive facing criminal charges in relation to a data breach.
The US district court in San Francisco will start hearing arguments on whether Sullivan, the former head of security at the ride-share giant, failed to properly disclose a 2016 data breach affecting 57 million Uber riders and drivers around the world.
At a time when reports of ransomware attacks have surged and cybersecurity insurance premiums have risen, the case could set an important precedent regarding the culpability of US security staffers and executives for the way the companies they work for handle cybersecurity incidents.
The breach first came to light in November 2017, when Uber’s chief executive, Dara Khosrowshahi, revealed that hackers had gained access to the driver’s license numbers of 600,000 US Uber drivers as well as the names, email addresses and phone numbers of as many as 57 million Uber riders and drivers.
Public disclosures like Khosrowshahi’s are required by law in many US states, with most regulations mandating that the notification be made “in the most expedient time possible and without unreasonable delay”.
But Khosrowshahi’s announcement came with an admission: a whole year had passed since the information had been breached.
“You may be asking why we are just talking about this now, a year later,” Khosrowshahi said at the time, adding that the company had investigated the delay and had fired two executives who had led the response to the breach, one of whom was Sullivan.
Uber’s disclosure sparked several federal and statewide inquiries. In 2018, Uber paid $148m over its failure to disclose the data breach in a nationwide settlement with 50 state attorneys general. In 2019, the two hackers pleaded guilty to hacking Uber and then extorting Uber’s “bug bounty” security research program. In 2020, the Department of Justice filed criminal charges against Sullivan.
In court filings , federal prosecutors alleged that in an attempt to cover up the security violation, Sullivan had “instructed his team to keep knowledge of the 2016 Breach tightly controlled” and to treat the incident as part of the bug bounty program.
That program was intended to incentivize hackers and security researchers to report vulnerabilities in exchange for cash rewards, but it did not allow for “rewarding a hacker who had accessed and obtained personally identifiable information of users and drivers from Uber-controlled systems”, the complaint says.
The hackers in the 2016 breach were rewarded $100,000, the complaint says, more than any bounty the company had paid as part of the program until that point.
Sullivan also allegedly had the hackers sign a supplemental non-disclosure agreement (NDA) which “falsely represented that the hackers had not obtained or stored any data during their intrusion”, federal prosecutors wrote.

In 2018, months after he was fired, Sullivan contested any claims of a cover-up and said he was “surprised and disappointed when those who wanted to portray Uber in a negative light quickly suggested this was a cover-up”.
Neither Sullivan nor Uber immediately responded to a request for comment.
The justice department complaint alleged that only Sullivan and the former Uber chief executive Travis Kalanick had knowledge of the full extent of the hack as well as a role in the decision to treat it as an authorized disclosure through the bug bounty program. However, as the New York Times first reported , the security industry is divided over whether Sullivan deserves to be held solely responsible for the breach. Some have questioned whether the role of other company executives and its board should be investigated as well, while others say Sullivan’s role in it was clear.
“I don’t know if Uber management knew about the concealment … or if Sullivan was directed to make the $100,000 payment to hide the breach. The trial will ferret all that out,” Jamil Farshchi, the chief information security officer at Equifax, wrote in a Linkedin post . “What I do know is that nobody is disputing that a breach of 57 million people occurred, Uber concealed it, and that Joe Sullivan … was involved in the concealment.”
The trial will play out as reports of ransomware attacks continue to rise. In 2021, the US saw a more than 95% increase in ransomware attacks, according to the threat intelligence firm SonicWall . Many of those attackers have targeted healthcare facilities and schools. Hackers targeted the Los Angeles unified school district, the second-largest school district in the US, with a cyber-attack over Labor Day weekend.
- San Francisco
- Silicon Valley
Most viewed
Jury finds former Uber security chief guilty of concealing data breach
- Medium Text

- Company Uber Technologies Inc Follow
- Company Uber, Inc. Follow
Jumpstart your morning with the latest legal news delivered straight to your inbox from The Daily Docket newsletter. Sign up here.
Reporting by Yuvraj Malik in Bengaluru; Editing by Krishna Chandra Eluri
Our Standards: The Thomson Reuters Trust Principles. New Tab , opens new tab
Read Next / Editor's Picks

Industry Insight Chevron

Mike Scarcella, David Thomas

Karen Sloan

Henry Engler

Diana Novak Jones
Uber investigating cybersecurity incident after hacker breaches its internal network

Uber confirmed on Thursday that it’s responding to a cybersecurity incident after reports claimed a hacker had breached its internal network.
The ride-hailing giant discovered the breach on Thursday and has taken several of its internal communications and engineering systems offline while it investigates the incident, according to a report by The New York Times , which broke news of the breach.
Uber said in a statement given to TechCrunch that it’s investigating a cybersecurity incident and is in contact with law enforcement officials, but declined to answer additional questions.
The sole hacker behind the beach, who claims to be 18 years old, told the Times that he compromised Uber because the company had weak security. The attacker reportedly used social engineering to compromise an employee’s Slack account, persuading them to hand over a password that allowed them access to Uber’s systems. This has become a popular tactic in recent attacks against well-known companies, including Twilio , Mailchimp and Okta .
Shortly before the Slack system was taken offline on Thursday afternoon, Uber employees received a message that read, “I announce I am a hacker and Uber has suffered a data breach,” the Times reports. The hacker also reportedly said that Uber drivers should receive higher pay.
We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available. — Uber Comms (@Uber_Comms) September 16, 2022
According to Kevin Reed, CISO at cybersecurity company Acronis, the attacker found high-privileged credentials on a network file share and used them to access everything, including production systems, Uber’s Slack management interface and the company’s endpoint detection and response (EDR) portal.
“If you had your data in Uber, there’s a high chance so many people have access to it,” Reed said in a LinkedIn post, noting that it’s not yet clear how the attacker bypassed two-factor authentication ( 2FA ) after obtaining the employee’s password.
The attacker is also believed to have gained administrative access to Uber’s cloud services, including on Amazon Web Services (AWS) and Google Cloud (GCP), where Uber stores its source code and customer data, as well as the company’s HackerOne bug bounty program.
Sam Curry, a security engineer at Yuga Labs who described the breach as a “complete compromise,” said that the threat actor likely had access to all of the company’s vulnerability reports, which means they may have had access to vulnerabilities that have not been fixed. HackerOne has since disabled the Uber bug bounty program.
In a statement given to TechCrunch, Chris Evans, HackerOne CISO and chief hacking officer, said the company “is in close contact with Uber’s security team, have locked their data down, and will continue to assist with their investigation.”
This is not the first time that Uber has been compromised. In 2016, hackers stole information from 57 million driver and rider accounts and then approached Uber and demanded $100,000 to delete the data. Uber made the payment to the hackers but kept the news of the breach quiet for more than a year.
If you know more about the Uber breach, you can contact this author via Signal at +44 1536 853968.

- Penetration Testing|The Ultimate Tool for Cyber Security Assessment
- Internal Network Penetration Testing| Are You Protected Against Internal Security Threats?
- Incident Response|Comprehensive Expert Help After a Security Incident
- Computer Forensics|Arm Your Legal Team with Digital Evidence
- Expert Witness Services|Build Your Case with Kevin's Expertise
- Security Awareness Training|Your Comprehensive Security Training Library
- Vulnerability Assessment|See Your System Through the Eyes of a Hacker
- Product Claims Testing|Get Unbiased Proof From the Best in the Business
- Red Team Operations|Evaluate Your Response to An Active Data Breach
- Social Engineering Strength Testing|Safeguarding Your Security From Human Manipulation
- The Art of Invisibility|The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data
- Ghost in the Wires|My Adventures as the World's Most Wanted Hacker: A New York Times Bestseller
- The Art of Intrusion|The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers
- The Art of Deception|Controlling the Human Element of Security
- About Kevin|Whether you call him famous or infamous, Kevin Mitnick is one of a kind.
- Global Ghost Team|The Best of the Best In Cyber Security and Pentesting, Handpicked for Your Team
- Our Clients|Our Legacy of Extraordinary Services for Extraordinary Clients
- Testimonials & Reviews|Approved Quotes about Kevin's Live Hacking Appearances
- Press Archives|The Latest Cybersecurity Articles & News About Kevin Mitnick & Mitnick Security
- Media Kit|Bureau-Friendly Material For Your Website, E-mail and Print Needs
- FAQs|Explore answers to commonly-asked questions from fans, clients, colleagues and everyone in between.
- Blog|The latest news from Kevin Mitnick and the Global Ghost Team
- Virtual Events|Unsurpassed Experience in Successful Online Events and Trainings
- Lockpick Business Card|Learn More About the Card That Opens Doors Around the World
- Submit a Proposal|Contact Kevin’s Team With Your Proposal or Business Opportunity
- Join the Team|Do You Want to Work With Us?
Uber Data Breach: What To Know About the 2022 Cybersecurity Attack
No matter how robust network security is, even the biggest companies fall victim to cyber attacks. These malicious attacks can be costly — to the tune of 4.3 million on average — but they also disrupt operations and hurt a company’s reputation.
In fact, it is anticipated that cybercrime will cost the world $10.5 trillion annually by 2025. A recent breach at Uber reminds us of how social engineering attacks are on the rise and urges us to protect and train our employees to prevent such detrimental attacks. Below, we’ll dissect the Uber data breach and what you can do to avoid facing a similar devastating situation.
So, What Happened at Uber?
On September 15, 2022, Uber employees were surprised to find an unauthorized user posting in their company’s slack channel. They had hacked their way into the account and left a message that read, “I announce I am a hacker and Uber has suffered a data breach.” Uber employees, who did not reveal their identities, admitted that it appeared as if the hacker breached multiple internal applications and accessed sensitive data.
Although the suspected hacker, who is allegedly only 18 years old, has been arrested , the damage was done. The hacker had left an explicit image within Uber’s internal systems and exposed how they had hacked the company using social engineering . Uber is now having to launch their own internal investigation into the incident, and will more than likely have to enact a costly remediation plan.
How Did the Hacker Gain Access to Uber’s Internal Systems?
The Uber cybersecurity protocols would have probably been enough to prevent the data breach — if it weren’t for the use of social engineering. The hacker admitted on Twitter that they gained access to the company’s internal VPN by tricking an employee into handing it over. The hacker claimed they were a corporate information technology expert and needed the password. The threat actor also had access to credentials that allowed them to breach Uber’s AWS and G Suite accounts.
Social engineering — or the practice of using human emotion to get the victim to perform an action or give the threat actor needed information — is not uncommon in the cybersecurity world. In fact, many experts agree that untrained employees are your biggest area of vulnerability. The threat actor responsible for the Uber data breach has also claimed to have used social engineering when launching an attack against Rockstar Games .
Protect Your Company Against Incidents Like the Uber Data Breach
Stay up to date with the latest social engineering techniques.
Although direct messaging and calling are popular social engineering techniques, it’s expected that the cybercrime trend of impersonating well-known companies through email phishing scams will continue to grow this year. To protect your organization, be aware of these trends and speak with a cybersecurity consultant if you feel your organization is vulnerable.
Test Your Network Vulnerabilities Regularly
Unfortunately, social engineering isn’t going away — which means you need to know if there are vulnerabilities within your network that can make a social engineering attack even more disastrous. For example, a threat actor who has gained access to your internal network with stolen login credentials may be able to move laterally within your organization’s internal framework and escalate their privileges with help from unpatched applications or outdated technologies.
Routine vulnerability assessments performed quarterly can help your organization’s private data stay private. An expert assessment can help identify false positives from vulnerability scans and provide a report with more information. An assessment report may include discovered vulnerabilities, a walkthrough of what was done, and research and solutions to better protect your organization.
Continuously Train Your Employees To Recognize Attacks
Uber was hacked in 2022 because an employee did not recognize that they were a victim of social engineering. Cybersecurity awareness training can arm employees with valuable information so that they know what to do when suspicious activity occurs at work. Engaging learning tools such as training videos and live hack demonstrations can not only get your team up to speed, but can help motivate them to stay vigilant.
Kevin Mitnick Security Awareness Training
Aside from learning the details about cyberattacks like the Uber data breach, security awareness training for your employees can help keep you one step ahead of social engineers.
Train your team when and where it’s convenient, with the world's largest security awareness training content library. Begin strengthening your organization’s security posture by exploring the Security Awareness Training Library by Mitnick Security.
Topics: Social Engineering

Latest Posts
Kevin offers three excellent presentations, two are based on his best-selling books. His presentations are akin to technology magic shows that educate and inform while keeping people on the edge of their seats. He offers expert commentary on issues related to information security and increases “security awareness.”
Redefining Your Enterprise’s Cyber Security Posture During Mergers & Acquisitions
With 3,205 data compromises occurring in 2023 alone, fortifying your enterprise’s cybersecurity posture is more important than ever.
Choosing a Penetration Testing Company for Mac-based Environments
Powering your business with Apple devices because of their reputable security and privacy features? You may be surprised to learn that while Apple dev..
AI in Cyber Security: Impacts, Benefits, and More To Be Aware Of
Artificial intelligence in cybersecurity has been a hot topic lately, especially with the rise of OpenAI’s ChatGPT. But does that mean it would make a..

© Copyright 2004 - 2024 Mitnick Security Consulting LLC. All rights Reserved. | Privacy Policy
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World
Uber data breach – an insurance case study for directors and officers
When we evaluate the merits of what actually took place, we will see an interesting scenario develop that could directly impact uber’s board of directors..

On November 21, 2017, Uber announced that the personal data of 57 million users were stolen in a breach, including 600,000 drivers in the United States. Reuters just reported that “ Uber received an email last year from an anonymous person demanding money in exchange for user data and the message was forwarded to the company’s bug bounty team in what was described as Uber’s routine practice for such solicitations, according to three sources familiar with the matter. ”
When we evaluate the merits of what actually took place, we will see an interesting scenario develop that could directly impact Uber’s board of directors. So, let us first examine how this breach compares with others. In Figure 1. We see that the raw number of records disseminated is low when we compare against other major breaches. However, how many of the other breaches exposed both client and employee data?
According to Uber, the demand for money came in and they forwarded the demand to the team that handles bug bounties (a type of contest many large firms employ to help ensure their cyber risk mitigation strategies are up to par by challenging the hacker community to try and identify a weakness that would garner a cash award – in this case up to $10,000).
The first problem with this theory the underwriters need to consider is that this is not how a bug bounty program “should” work. The intent is to identify a material weakness, proven with a proof of concept, and then get paid. If you take your activities to the next level – and actually “steal” information – not only does that violate the law, it generally null and voids the terms and conditions set forth by the bug bounty program itself. But Uber’s program has no such language. Here’s what language is present:
Exposure of User Data: the ability to access user or employee data without having an authorized relationship from the Victim. In-scope vulnerability class examples: AWS Identity & Access Management credential exposure resulting in access to driver documents in an S3 bucket. Adding a user to a Partner’s account, without them accepting the invite, resulting in exposure of name, phone number, and trip history. Password reset token exposure, allowing attacker the ability to reset password of victim and login to view sensitive user data. IDOR/authorization vulnerabilities resulting in exposure of personal data. Out-of-scope vulnerability class examples: The ability to determine if a phone number or email has an Uber account, also known as an account oracle. Potential domains to look at: auth.uber.com, partners.uber.com, riders.uber.com, eats.uber.com
There does not appear to me a scenario either in or out of scope that would be consistent with what Uber alleges took place. The ability to access is not the same thing as “exfiltration.” Even if this is the case, the dollar threshold is exceeded by 10x. So, something is not right here. Was this simply a tactic to downplay the event?
Was this a simple oversight by Uber’s staff when they received the demand? Was there a corporate policy in place to define what to do in the face of a ransom? Perhaps a subsection of their Incident Response Plan?
If we do some quick math using the infamous IBM and Ponemon statistics, the cost per record is $141.00 each. If we use that metric, we look at over $8 Billion in potential loss. Do I believe that it will cost them this amount, not likely.
Reading “ Executive Liability for Data Breach Notification Delay? “ by Kevin LaCroix made me think of the potential financial implications to underwriting this cyber event and its linkage with Directors and Officers lines of coverage.
Uber has a fairly new CEO who was not present at the time of the breach as well as a new general counsel, Tony Scott, who was recently quoted as saying:
“I’m not the first to recognize that the company over-indexed on growth without putting in the appropriate guardrails,” he said in an interview Friday. “Fostering a culture of compliance is going to be one of my top priorities.”
Any company with excessive growth can find it hard to scale in areas that generally go unchecked by most businesses. Such as at what point do I hire a CISO, at what point do I hire additional staff with the following skill sets based on gaps that exist today. Does this constitute willful or intentional wrongdoing, a negating factor for D&O coverage? In my opinion, no.
However, what was known by Uber and when? Also failing to abide by 48 State Regulatory Agencies (47 at the time of the breach), becomes the discerning factor (or should be) by the insurance carrier(s).
If Uber submits a claim for damages incurred by the theft of data, are they entitled to do so under a cyber policy? Depends on the following:
- Was the policy written in a manner that imposes limits of liability when state laws applicable to data breach notification are not met?
- Is a future claim of damages negated if you fail to use the carrier’s post-breach service providers?
- Was the insurance application constructed in a manner that took into account the use of a third party, in this case GitHub, and what was Uber’s inherent obligations to protect sensitive software development?
- Did the underwriters, brokers, or agents even assess the bug bounty program for assertion of potential exclusionary provisions?
Now comes the interesting part. Since we are a litigious society and there is always an attorney to champion a good cyber breach case, there exists a chance that Board Members could be subject to being swept into this debacle. Are there factors under a D&O policy that could convert over to negating the cyber policy?
According to Mackoul and Associates there are 10 scenarios that void a D&O claim. I draw your attention to the first line item “Breach of Contract”. The reason for this is that a contractual duty is not a liability imposed by law but rather a voluntarily undertaken obligation. Failure to comply with a signed contract would fall under willful or intentional wrongdoing and would not be covered.
There may exist a claim of breaching the contract by the 600,000 employees. If you go to Uber’s privacy site , you will see how they define their own policy.
For a number of years, the Federal Trade Commission has levied sanctions against companies for either misrepresenting or not adhering to stated privacy policies on corporate websites as an unfair and deceptive business practice.
While this case is still under investigation and more information is sure to surface, can the mere fact that Uber willfully did not advise each State Attorney General as basis for breaching a contract between employer and employee if the employer had a lawful duty to disclose? If the answer is “yes” then this factor alone could negate any top cover a D&O policy may provide
Furthermore, as described by Mackoul, under the header of “Willful or Intentional Wrongdoing”
“A board may still be able to recover a fine resulting from intentional conduct if it can prove that it was only vicariously liable for misconduct but willful or intentional wrongdoing is normally not covered by D&O policies.”
Was this incident made aware to the board prior to public disclosure? If yes, what actions did they take to ensure State laws were met? If they did nothing and failed to meet the standard of care, does that constitute willful or intentional wrongdoing? Did they even know about these requirements and if not, is ignorance of the law an excuse to vacate a guilty decision from being rendered? Short answer after over 1,000 hours in a courtroom, “no.”
Related content
Insuring uncle sam’s cyber risk, underwriting cyber exposure – the business case for certifying, training insurance agents and brokers in cyber risk, cyber insurance in the 2018 regulatory landscape, from our editors straight to your inbox.
Carter Schoenberg is the President and Chief Executive Officer of HEMISPHERE Cyber Risk Management, Inc. Mr. Schoenberg is a certified information system security professional with over 23 years of combined experience in criminal investigations, cyber threat intelligence, cyber security, risk management and cyber law. He is a cybersecurity subject matter expert supporting government and commercial markets to better define how to evaluate a risk profile and defining criteria for brokers and carriers to utilize in their determination on coverage and premium analysis.
HEMISPHERE is working with insurance stakeholders to define appropriate standards and training of brokers and agents in determining coverage requirements, scheduled for release later in 2017. HEMISPHERE is also working with the National Association of Insurance Commissioner’s Cyber Task Force.
Mr. Schoenberg’s expertise has been featured at many events and his background and knowledge in the Latin American markets, specifically in Panama’, has provided him with a unique and detailed view of this market segment.
Mr. Schoenberg is responsible for designing practical solutions to address cyber risk management using his proprietary cost-benefit analysis enabling system owners to make mission and cost justified decisions on cyber risk. Starting his career in law enforcement as a homicide detective, his work products have been actively used by DHS, the ISAC communities, and the Georgia Bar Association for Continuing Learning Educational (CLE) credits on the topic of cybersecurity risk and liability. His expertise is profiled at conferences including ISC2, SecureWorld Expo, ISSA and InfosecWorld.
The opinions expressed in this blog are those of Carter Schoenberg and do not necessarily represent those of IDG Communications, Inc., its parent, subsidiary or affiliated companies.
Most popular authors

Show me more
Cisco fixes vulnerabilities in integrated management controller.

UK law enforcement busts online phishing marketplace

Consolidation blamed for Change Healthcare ransomware attack

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

CSO Executive Sessions: Former convicted hacker Hieu Minh Ngo on blindspots in data protection

LockBit feud with law enforcement feels like a TV drama

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
Uber Breach 2022 – Everything You Need to Know
On Thursday, September 15th, Uber confirmed reports of an organization-wide cybersecurity breach. This is an evolving situation, but we will bring you here the latest information and commentary as we get it.

Mackenzie Jackson
Mackenzie is a developer advocate at GitGuardian, he is passionate about technology and building a community of engaged developers to shape future tools and systems.
More posts by Mackenzie Jackson.

“What makes this breach appear so significant is that this does not appear to be a breach of a single system. The attackers seem to have moved laterally between systems for a complete organization takeover” Mackenzie Jackson – Security Advocate at GitGuardian
Update 9/20/22: Uber confirmed in a security update that the named attacker "Tea Pot" was affiliated with the Lapsus$ hacking group, famous for breaching NVIDIA, Samsung , and Microsoft earlier this year. According to their early investigations, it is likely that the attacker targeted an external contractor whose credentials were bought on the dark web.
What happened
Here’s what we know so far, pending investigation and confirmation from Uber’s security teams.
- The attack started with a social engineering campaign on Uber employees, which yielded access to a VPN, in turn granting access to Uber's internal network *.corp.uber.com.
- Once on the network, the attacker found some PowerShell scripts, one of which contained hardcoded credentials for a domain admin account for Thycotic, Uber’s Privileged Access Management (PAM) solution.
- Using admin access, the attacker was able to log in and take over multiple services and internal tools used at Uber: AWS, GCP, Google Drive, Slack workspace, SentinelOne, HackerOne admin console, Uber’s internal employee dashboards, and a few code repositories.
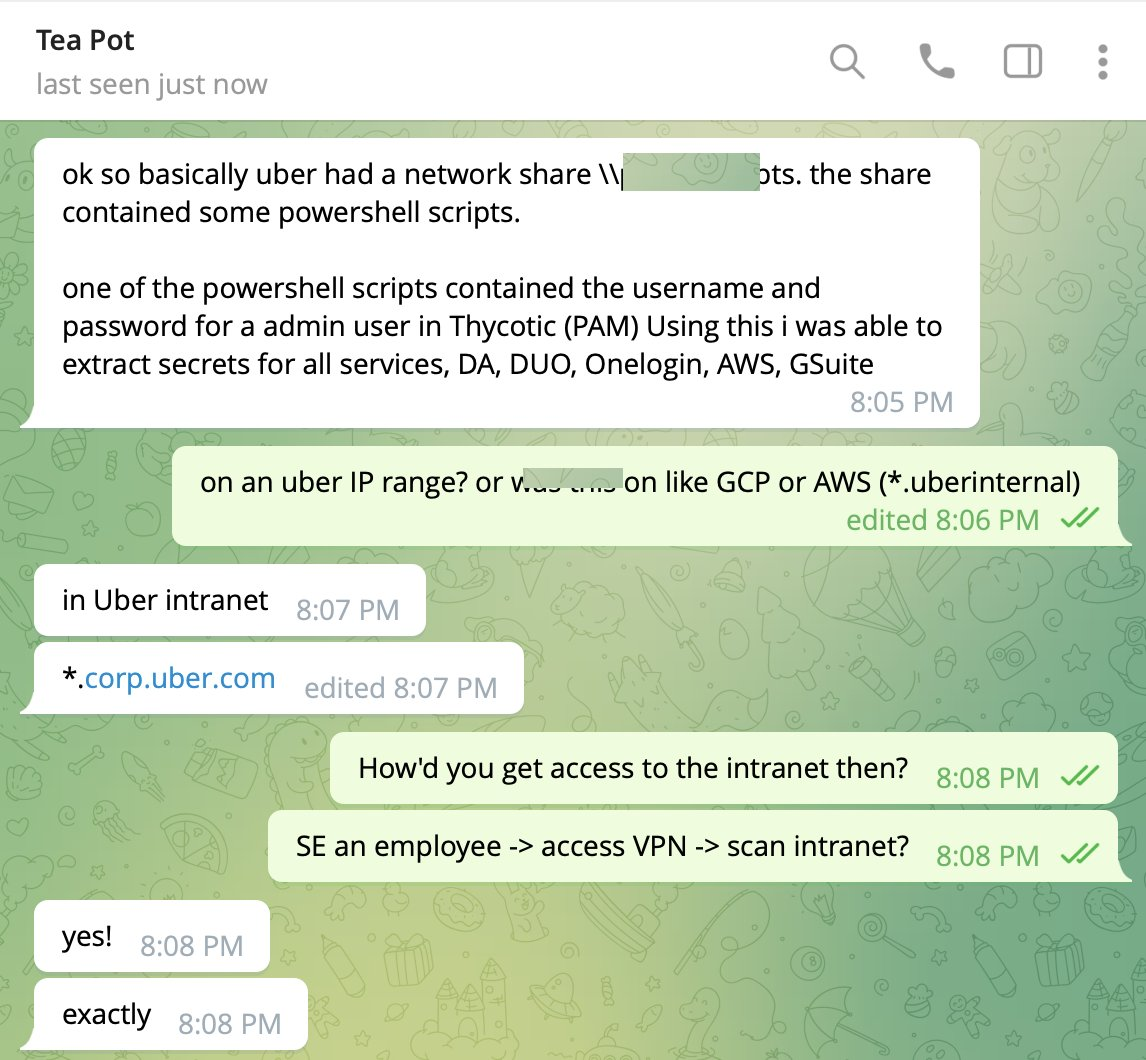
The critical vulnerability that granted the attacker such high levels of access was hardcoded credentials in a PowerShell script . These credentials gave admin access to a Privileged Access Management (PAM) system: Thycotic . This tool carries huge amounts of privilege, making it a single point of failure; it stores both end-user credentials for employee access to internal services and third-party apps as well as DevOps secrets used in the context of software development. This is a worst-case scenario . The PAM system controls access to multiple systems, and having admin access means you can give yourself or extract secrets to all connected systems. This has appeared to give the attacker complete access to all of Uber's internal systems.
This isn't the first time we've seen an Uber data breach: in 2014 hackers gained access to an AWS S3 bucket after developers leaked secrets to a public git repository. Two years later, a similar incident happened when attackers exploited poor password hygiene by some developers to gain access to private repositories which contained multiple access credentials. Now we appear to have the final episode in the trilogy, and it appears to be the most serious situation yet.
“There have been three reported breaches involving Uber in 2014, 2016, and now 2022. It appears that all three incidents critically involve hardcoded credentials (secrets) inside code and scripts” Mackenzie Jackson – Security Advocate at GitGuardian
How bad is it?
Critically, Uber’s Privileged Access Management (PAM) platform was compromised through the exposure of its admin credentials. Privileged access management (PAM) is the combination of tools and technology used to secure, control, and monitor employee access to an organization's critical information and resources. With that in mind, the attacker may have gained access to nearly all the internal systems of Uber. Let’s go through the ones we know of based on preliminary information and evidence to understand the severity of this incident.
“We very often find credentials and secrets for specific systems that have leaked, but finding admin credentials to an access management system is like finding a master key to every room and alarm system, in every building, in every country that an organization owns.” Mackenzie Jackson – Security Advocate at GitGuardian
Thycotic – Severity = Critical
The attacker gained admin access to the Thycotic PAM system. PAM systems can be a single full-featured software console or a collection of multiple tools; in the case of Thycotic, it is a single tool with many features. It can control access to different services and also has a secrets manager where credentials and passwords are stored. It appears the hacker was able to access secrets inside the secure storage, granting the worst possible scenario for Uber.
AWS instance – Severity = Critical
The AWS instance controls the cloud infrastructure of Uber's applications. Depending on configuration, privileges, and architecture, the attacker can potentially shut down services, abuse computing resources, access sensitive user data, delete or ransom data, change user access, and many more things.
VMware vSphere – Severity = Critical
VMware vSphere is a cloud computing virtualization platform. This is a critical platform as it interfaces with both cloud computing and on-premise servers which can give attack access to controlled on-premise servers as well as many administrative functions that would help an attacker move deeper into systems.
SentinelOne – Severity = High
SentinelOne is an XDR (eXtended Detection and Response) platform. Simply put, this platform connects to your mission-critical systems and lets you know if there are security issues. Any attacker that can obtain privileged access to this system can obfuscate their activity and prolong their attacks. XDRs can bake in "backdoors" for Incident Response (IR) teams, such as allowing IR teams to "shell into" employee machines and potentially widening the attacker's access.
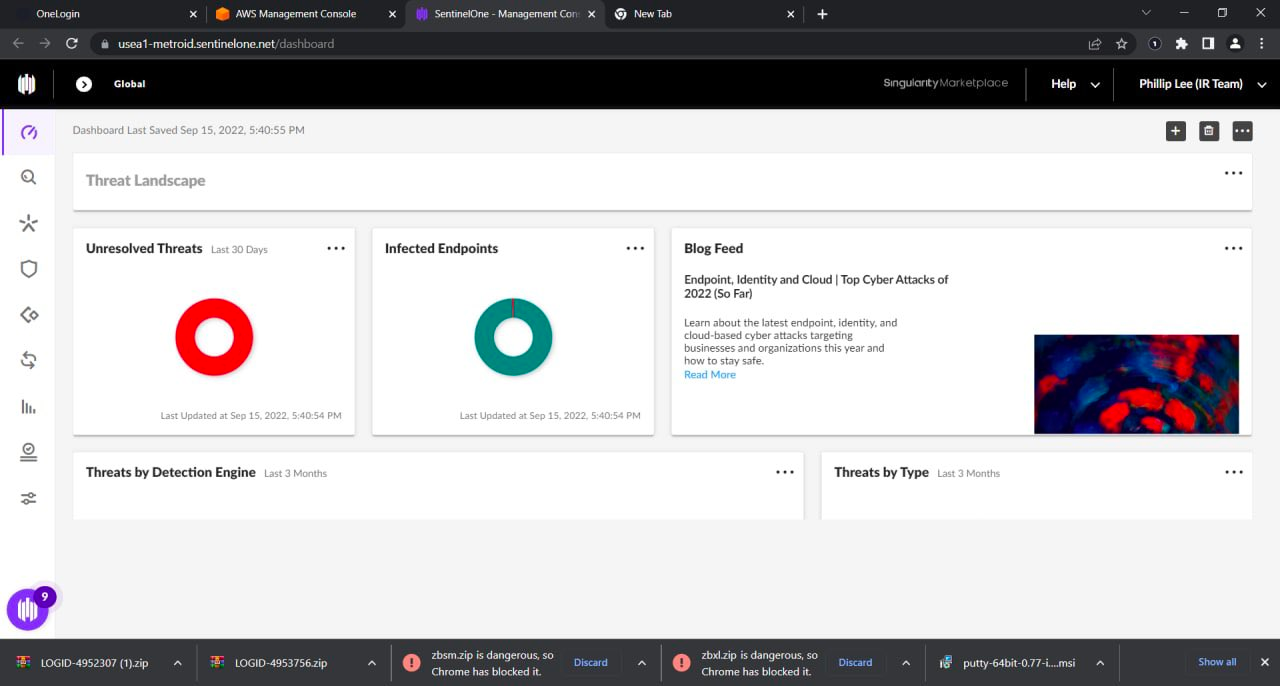
Slack workspace – Severity = Medium
The internal messaging system of Slack can be used to great effect as an attacker to launch phishing campaigns. As the attacker has the instant trust of other users, they can send malicious links, try and get admins to elevate their privilege, and access sensitive information. As the attacker has made themselves known, this is likely a smaller threat.
GSuite Admin – Severity = Medium
GSuite is a tool used by many companies to manage their users, store data, and many other administrative tasks. With admin access, the attacker can create and delete accounts, but would also likely have access to employee data and other sensitive company data.
HackerOne – Severity = Medium
HackerOne is the platform used to pay and communicate with security researchers that find vulnerabilities within systems for rewards. Given the level of detail bounty hunters usually provide, anyone with access to the HackerOne tenant has detailed how-tos on how to exploit (likely unpatched) vulnerabilities in other areas of their IT systems. This means persistence is highly likely.
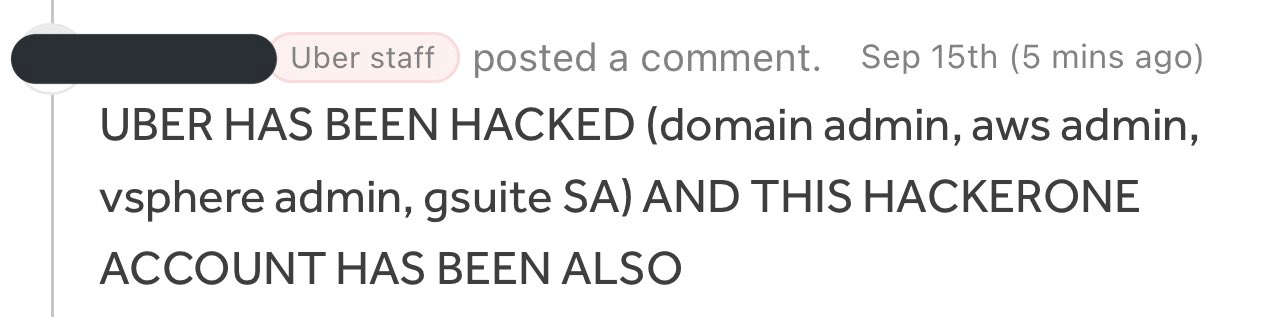
What’s next for Uber?
Although we can't be sure at this point, the immediate disclosure of the breach by the attacker himself both to security researchers on the HackerOne platform and Uber personnel on their Slack workspace tend to indicate that he might not be financially motivated.
From what we have seen, the attacker likely has access to many more systems and services belonging to Uber, but these are the ones we know about. Given the blast radius of this breach, we believe it will be extremely difficult and costly for Uber to sift through all their systems and access logs to ensure the attacker has not achieved persistence.
Before you go
Want to learn more about the problem of hardcoded credentials? Read our State of Secrets Sprawl 2023 report or request a complimentary audit of your secrets exposure .
If you are interested in other 2022 data breaches and attacks, you can find a detailed analysis of the Cloudflare breach and the Toyota data breach .
Related Articles
Early lessons from the sisense breach.
Business intelligence company Sisense has seen secrets compromised in its GitLab repositories, leading to a siphoning of its customers' sensitive data.
Thomas Segura
15 Apr 2024 – 3 min read
The Open-Source Backdoor That Almost Compromised SSH
The open-source world narrowly escaped a sophisticated supply-chain attack that could have compromised countless systems. A stark reminder of the necessity of vigilant monitoring and rigorous vetting within the open-source ecosystem to maintain trust and security.
2 Apr 2024 – 3 min read
Misconfigurations in Google Firebase lead to over 19.8 million leaked secrets
Read our summary of research that found millions of records that exposed user passwords due to misconfigured or missing security settings.
Dwayne McDaniel
20 Mar 2024 – 3 min read
Nation-state hackers access Microsoft source code and steal secrets
Microsoft has been experienced a sustained attack by Russian-backed nation-state attacker Midnight Blizzard (also known as NOBELIUM). This blog examines all we know so far
11 Mar 2024 – 3 min read
Start your journey to secrets-free source code
And keep your secrets out of sight
GitGuardian is the code security platform for the DevOps generation. With automated secrets detection and remediation, our platform enables Dev, Sec, and Ops to advance together towards the Secure Software Development Lifecycle.
Subscribe to our newsletter to receive the latest content and updates from GitGuardian.
By submitting this form, I agree to GitGuardian's Privacy Policy
- PLATFORM Secrets Detection Honeytoken Infra as Code Security Public Monitoring GITGUARDIAN VS GitHub Advanced Security GitLab Secret Detection truffleHog v3 Gitleaks More alternatives
- DEVELOPERS GitGuardian CLI Documentation API Documentation Good Samaritan Labs GitHub Roadmap API Status
- RESOURCES Blog Learning Center Dev & Sec resources State of Secrets Sprawl Events Free GitHub Secrets Audit PRICING Plans Value Calculator
- COMPANY About Us Wall of fame Careers Contact us FAQ Partners Newsroom
© 2024 GitGuardian. All Rights Reserved.

- Dynamic Application Security Testing
- API Security Testing
- Penetration Testing - PT
- Banking, Financial Services, and Insurance
- Internet Companies
- Governments & Ministries
- The Fortune Global - 500 & 2000
- Cybersecurity Jargons
- Infographics
- Whitepapers
- Case Studies

Uber Data Breach 2022: What You Need to Know
The world of digital security has been under the spotlight for various reasons in the last year. Several high-profile incidents have directly impacted the general public, from cyber attacks to privacy scandals.
Uber is the latest company to be caught up in this whirlwind after hackers managed to breach their security and steal sensitive user data from the ride-hailing service.
This article provides an overview of what happened, what went wrong, and what you can do to keep your accounts safe.
What Caused Uber Data Breach in Security?
On September 15, Uber announced the news of its system breach. Through social engineering, the hacker compromised an employee’s Slack account.
During the uber cyber attack , the hacker persuaded the employee to hand over a critical password that allowed them access to Uber’s systems.
The screenshots the hacker shared with security researchers suggest that this person gained complete access to the cloud-based systems where Uber stores sensitive customer and financial information.
One of the company employees (who wished to stay anonymous) resource page is said to have had an unsafe work image posted by the hacker.
Some noteworthy points include the following:
- First, they failed to monitor login attempts properly. Uber doesn’t receive notifications if third-party tries to log into a business account but fails to enter the network. These failed entry attempts don’t trigger Uber’s security system networks, which shows an apparent lag in the system.
- Second, Uber failed to restrict the available data to third-party apps. Such easy availability allows hackers to access sensitive information from other linked third-party apps.
- Thirdly, there is a possibility this attack was a result of phishing. In phishing, hackers pose as a trustworthy person or entity to gain access to sensitive information. This breach is notable as there have been multiple breaches in Uber’s history. Such multiple violations are unusual, as most breaches only happen once or twice.
How Was Uber’s Security Breached?
An attempt was made by the hacker to socially engineer Uber workers, which resulted in access to a VPN and the company’s internal network.
Allegedly, an 18-year-old hacker is responsible for stealing data from Uber . However, last week, Uber shared more details about the attack, which notably pinned the threat actor’s affiliation to the notorious LAPSUS$ hacking group.
Uber’s system vulnerability came to the fore when its native Privileged Access Management (PAM) platform admin credentials were compromised.
Privileged Access Management is a collection of tools and technologies that protects, restricts, and monitors employee access to a company’s vital data and resources.
Once a hacker enters the network, they get access to PowerShell scripts, which include the domain admin’s account login information in a hard-coded form.
During the recent breach, the hijacker gained full administrative access to the company’s AWS, vSphere domain, Duo, G Suite, OneLogin, VMware, and other accounts. They even obtained Uber’s source code; screenshots were provided as evidence.
Since there were no ransom or extortion notes, researchers believe that the hacker performed the engineering attack only for cheap thrills.
Predefined parameters in a PowerShell script are a significant weakness that gives the attacker such extensive access. These login credentials granted administrator access to Thycotic, a PAM system.
This tool carries a lot of privileges for the company’s users. It holds both end-user keys for personnel access to internal resources and third-party programs.
Additionally, it includes DevOps insights used commonly during software development, making it a single failure point.
The PAM system manages access to several systems. As a result, the attacker had full access to all of Uber’s core systems.
Who Was Affected by Uber Cybersecurity Attack?
Although the hackers only gained access to some information from Uber’s users, they still managed to breach their security. The breach means the hackers found a way to infiltrate their system and enter other accounts.
It’s possible the hackers also gained access to sensitive information from other apps tracking users. Therefore, hackers likely gained access to information such as addresses, email addresses, and license numbers ( although no evidence proves it yet ).
Such information might include unwarranted access to users’ bank accounts while receiving Social Security benefits in someone else’s name and even driving cars without being detected.
Some people have questioned Uber’s response to the data breach in light of how they had previously failed to disclose the 2016 breach that cost them $148 million in legal penalties.
Additionally, it’s also been reported that the company didn’t immediately notify everyone affected by the breach, which is unusual. Some people may have been left unaware that their information has been breached.
Unlike Uber's Cyber attack and data breach , if you wish to not happen to your company then, keep yourself updated in the world of cybersecurity with Appknox's cyber security jargon and take some knowledge.
Uber data breach

Keep the momentum going!
Continue reading by signing up with your email.
DISCOVER MORE
April 8, 2024
How Appknox stood out at Gartner® Security & Risk Management Summit 2024
March 28, 2024
Choosing the Best Mobile Application Security Testing Tool in 2024
March 21, 2024
A Complete Guide to NIST Compliance 2024
Gartner and g2 recommends appknox | see how we can help you with a free demo, similar blogs.

Hackers Demanding Money - Uber Is Not The Only One Paying Them
The big news in the security space in the last couple of days is Uber revealing that they got hacked last year. ...

Biggest Data Breaches and Cyber Attacks of Q2 2018
We had reported earlier how the first quarter of 2018 was quite significant in terms of data breaches and cyber ...

Top 10 Data Breaches of 2022 (So Far...)
As we are in the midst of the October Cybersecurity Awareness Month of 2022, all of us need to be more cautious than ...

Using Other Product?

2 Weeks Free Trial!

Appknox is the worlds most powerful plug and play security platform which helps Developers, Security Researchers and Enterprises to build a safe and secure mobile ecosystem using a system plus human approach to outsmart smartest hackers.
Subscribe to our newsletter
- Start Free Trial
- Book a Demo
- Switch to Appknox
- Partner with Appknox
- Privacy Policy
- Static application security
- Dynamic application security
- Case studies

Copyright © 2024 Appknox, Xysec Labs

- CCI Magazine
- Writing for CCI
- Career Connection
- NEW: CCI Press – Book Publishing
- Advertise With Us
- See All Articles
- Internal Audit
- HR Compliance
- Cybersecurity
- Data Privacy
- Financial Services
- Well-Being at Work
- Leadership and Career
- Vendor News
- Submit an Event
- Download Whitepapers & Reports
- Download eBooks
- New: Living Your Best Compliance Life by Mary Shirley
- New: Ethics and Compliance for Humans by Adam Balfour
- 2021: Raise Your Game, Not Your Voice by Lentini-Walker & Tschida
- CCI Press & Compliance Bookshelf
- On-Demand Webinars: Earn CEUs
- Leadership & Career
- Getting Governance Right
- Adam Balfour
- Jim DeLoach
- Mary Shirley

Executive Responsibilities and Consequences: A Case Study of Uber’s Data Breaches
Individuals potentially face criminal charges for failing to disclose a data breach.

Organizations at risk of a data breach (that’s every organization, by the way) can learn something from Uber’s data privacy missteps. Squire Patton Boggs attorneys Colin Jennings, Ericka Johnson and Dylan Yépez offer key takeaways from the company’s high-profile data breaches.
On August 19, 2020, the former Chief Security Officer (CSO) for Uber Technologies Inc. (Uber) was charged with obstruction of justice and misprision of felony for allegedly trying to conceal from federal investigators a cyberattack that occurred in 2016, exposing the data of 57 million riders and drivers. Although an extreme case, it is a good reminder for companies and executives to take data breach disclosure obligations seriously.
The criminal complaint, filed in the U.S. District Court for the Northern District of California (“the Complaint”), appears to claim that Uber, through its former CSO, Joseph Sullivan, should have reported the 2016 data breach to federal investigators. But a business’s duty to disclose a data breach is not always clear, and there are often a myriad of laws, regulatory practices and consumer expectations when navigating a breach. Using Uber’s 2016 breach as a case study, company executives must be aware of and recognize the business and personal consequences associated with breach response, and specifically with intentionally concealing a breach.
The Obligation to Report a Data Breach is Often Not Straightforward
Across the world, countries have widely varying laws related to the protection of personal information and even greater variance on the requirements to disclose a breach of such information. Even within the United States, the definitions of “personal information” and “data breach” differ greatly from state to state, with no two state laws being identical, so businesses, particularly those operating on a national or global scale, must conduct multijurisdictional analyses to determine whether an obligation to disclose a given breach exists and, if so, the scope of the obligation. Often there are inconsistent laws and obligations, and regulatory and consumer expectations can vary greatly based on the nature, scope and context of the breach.
Many laws require disclosure of a data breach only if there is a “reasonable risk of harm” to the individual(s) whose personal information was unlawfully accessed and/or exfiltrated. This requires businesses to determine whether, based on the totality of circumstances, it is reasonably likely that a breach of personal information will harm affected individuals. On the other hand, some laws do not require any risk of harm. Further, given that the forensic review of a data breach evolves over time, it is not uncommon for the initial findings to change dramatically over the course of a breach response. What often appears to be a limited attack can become a wholesale loss of sensitive consumer or business data – and oftentimes both simultaneously.
The legal analysis is then complex, fact-specific and ever changing. Perhaps, for example, only a portion of the sensitive data was exposed (e.g., only the last four digits of a social security number or only an individual’s last name). Maybe, due to insufficient logs, forensic investigators cannot rule out the possibility that an unauthorized third party accessed the sensitive data or moved laterally into human resources data or databases containing consumer financial information. Or perhaps evidence suggests that the cybercriminals appear to be staging sensitive data for exfiltration, but have destroyed any evidence that data was actually taken. These are but a few examples of factors that can make the obligation to report far from straightforward.
As Uber’s 2016 breach response indicates, the difficulty of ascertaining a business’s breach notification obligations is not a defense to those company executives who intentionally conceal a breach. As discussed below, company executives who ultimately have to decide whether to disclose a breach should take notice of the potential consequences of making the wrong decision.
A Case Study in Intentionally Failing to Report a Breach
The Complaint alleges that, in response to Uber’s 2016 breach, former CSO Joseph Sullivan “engaged in a scheme to withhold and conceal from the [Federal Trade Commission] both the hack itself and the fact that that data breach had resulted in the hackers obtaining millions of records associated with Uber’s users and drivers.”
At the time of the breach, Sullivan was helping oversee Uber’s response to a Federal Trade Commission (FTC) investigation into Uber’s data security practices, which had been triggered, in part, by another Uber data breach that occurred in or around 2014. Sullivan was “intimately familiar with the nature and scope of the FTC’s investigation.”
About 10 days after providing sworn testimony to the FTC, however, Sullivan received an email from “[email protected],” claiming to have found a “major vulnerability in uber [ sic ],” and threatening that the hacker “was able to dump uber [ sic ] database and many other things.” Within days, Sullivan’s security team realized that an unauthorized person or persons had accessed Uber’s data and obtained, among other things, a copy of a database containing approximately 600,000 driver’s license numbers for Uber drivers.
Based on available information, this massive data breach likely triggered Uber’s duty to notify under numerous jurisdictions’ data breach laws. By contrast, the 2016 breach appeared significantly more expansive than the 2014 breach, in which a cybercriminal accessed over 100,000 individuals’ personal information on a cloud-based data warehouse.
Based on the Complaint, Sullivan allegedly took affirmative measures to conceal the data breach and the resulting exposure of data. Among other things, he allegedly:
- negotiated with the cybercriminals to pay $100,000 in exchange for the hackers to sign a nondisclosure agreement (NDA), “falsely represent[ing] that the hackers had not obtained or stored any data during their intrusion,” even though “[b]oth the hackers and Sullivan knew at the time that this representation in the NDA was false;”
- “instructed his team to keep knowledge of the 2016 breach tightly controlled;”
- “never informed the FTC of the 2016 data breach, even though he was aware that the FTC’s investigation focused on data security, data breaches and protection of [Personally Identifiable Information];” and
- “removed certain details … that would have illustrated the true scope of the [2016] breach” from a prepared summary for the new Uber CEO – changes which “resulted in both affirmative misrepresentations and misleading omissions of fact.”
Sullivan’s alleged motives to cover up the 2016 hack and data breach are the concerns that all companies must assess in connection with their breach notification responsibilities.
First , the Complaint appears to allege that one motive to conceal the breach was to prevent further reputational harm to the company. Like Uber’s customers, individuals entrust their data to companies on a daily basis, from making purchases to requesting services. Companies know, therefore, that they risk losing revenue if their customers lose confidence in the protection of their data.
Understanding this dynamic, he “became aware the attackers had accessed [the cloud] in almost the identical manner the 2014 attacker had used,” according to the Complaint. “That is, the attackers were able to access Uber’s source code on GitHub (this time by using stolen credentials), locate [a cloud] credential and use that credential to download Uber’s data.” As such, the Complaint appears to allege that both the embarrassment of falling victim to the same attack vector and the associated reputational consequences may have motivated Sullivan to conceal the breach.
Second , the Complaint appears to allege that another motive for concealing the breach was to prevent additional regulatory scrutiny. In the United States, companies like Uber are subject to many state- and industry-specific regulators (e.g., state Attorneys General, the Securities and Exchange Commission, FTC) — often simultaneously. Additionally, outside of the United States there are numerous laws and data protection or other authorities that govern data breaches.
At the time of the breach, Sullivan was actively responding to the FTC’s inquiries to assist in reaching a settlement related to the 2014 breach. For example, he approved language to the FTC representing that “‘all new database backup files’ had been encrypted since August 2014,” when in fact, they had not. Sullivan’s fears may not have been misplaced. In light of the new information regarding the 2016 breach, the FTC effectively withdrew its previous settlement terms and added requirements to the resolution with Uber.
Ultimately, it appears that such attempts to rationalize and avoid Uber’s breach notification responsibilities may have led Sullivan to engage in the actions he did.
Lesson Learned
In a public statement, the FBI advised that, “[w]hile this case is an extreme example of a prolonged attempt to subvert law enforcement, we hope companies stand up and take notice.” In effect, the consequences of failing to disclose a data breach are the most extreme in cases where a notification obligation clearly exists and the company and its officers consciously decide to circumvent that obligation during the course of an ongoing investigation. While companies have incentives to rationalize and avoid their disclosure obligations (e.g., reputational harm, regulatory oversight, expense), this incident highlights the potential consequences executives should be aware of when weighing the business decision to disclose a breach. Disclosure and direct individual notification of a data breach is now the expectation, and the decision to not disclose must be very carefully weighed – taking into account law, regulatory practice and consumer/customer expectations. One size does not fit all, and the nature, scope and circumstance of the specific breach must be carefully assessed in real time.
Ultimately, the legal analysis to determine whether an obligation exists and the business decision to disclose the same are nuanced and complex. If you experience a data breach, it is best to retain counsel who is highly experienced in the nuances of data breaches and the complexities of data breach notification laws for help determining whether and how to disclose a given breach.
How COVID-19 is Shifting Tax Reporting Regulations
Cci media group launches book publishing division targeting global audience in compliance, ethics, risk, internal audit.
Colin Jennings, Ericka Johnson and Dylan Yépez

Related Posts

Navigating Personal Liability: Post–Data Breach Recommendations for Officers
Executives may be on the hook if info is compromised

Primary Markets Abuse: High Stakes and High Consequences for Investment Banks
Agencies signal that random monitoring is not enough

From Departments of War to the Basement Next Door: The AI-Disinformation Threat to Companies
The evolving threat of AI-based disinformation requires risk mitigation planning to avoid catastrophic reputational damage. As disinformation threats can materialize...

Corporate Litigation Trends 2024
Patchwork data privacy laws deepen corporate legal exposure 19th Annual Survey of In-House Corporate Counsel Litigation Trends for 2024 What’s...

Privacy Policy
Founded in 2010, CCI is the web’s premier global independent news source for compliance, ethics, risk and information security.
Got a news tip? Get in touch . Want a weekly round-up in your inbox? Sign up for free. No subscription fees, no paywalls.
Browse Topics:
- Compliance Podcasts
- eBooks Published by CCI
- GRC Vendor News
- On Demand Webinars
- Resource Library
- Uncategorized
- Whitepapers
© 2024 Corporate Compliance Insights
Privacy Overview

IMAGES
COMMENTS
Free trial. The Uber data breach began with a hacker purchasing stolen credentials belonging to an Uber employee from a dark web marketplace. An initial attempt to connect to Uber's network with these credentials failed because the account was protected with MFA. To overcome this security obstacle, the hacker contacted the Uber employee via ...
By Kate Conger and Kevin Roose. Sept. 15, 2022. Uber discovered its computer network had been breached on Thursday, leading the company to take several of its internal communications and ...
First published on Thu 15 Sep 2022 22.26 EDT. Uber has been hacked in an attack that appears to have breached the ride-hailing company's internal systems. The California-based company confirmed ...
Phase 1: Initial Access. The attacker got inside Uber's IT environment by gaining access to credentials to Uber's VPN infrastructure. Phase 2: Discovery. Most likely, this contractor did not have special or elevated privileges to sensitive resources but did have access to a network share, as did other Uber workers.
The attacker reportedly sent company-wide texts on Uber Slack channels, announcing the feat. "I announce I am a hacker and Uber has suffered a data breach," one message read, according to the NYT.
Last month, the internal databases of American multinational ride-share company Uber were hacked. The unnamed 18-year-old who claimed responsibility for the hack said Uber's ineffective security measures made the breach possible. The hacker, who was eventually arrested and is in police custody, is said to have gained access to Uber's secure ...
Extracted from Law360. Uber Technologies Inc.'s former chief information security officer, or CISO, Joe Sullivan, was found guilty Oct. 5 by a jury in federal court on charges of obstruction of justice under Title 8 of the U.S. Code, Section 1505, and misprision of a felony, under Title 18 of the U.S. Code, Section 4, based on what the U.S. Department of Justice called his "attempted cover-up ...
This website uses cookies. Analytical cookies help us improve our website by providing insight on how visitors interact with our site, and necessary cookies which the website needs to function properly.
Uber, a globally recognized ride-sharing and technology company experienced a data breach, as a result of a sophisticated cyberattack. The attack was orchestrated by a hacker affiliated with the hacking group known as Lapsus$. The breach was identified on September 19, 2022, at 10:45 am PT, as reported by the Uber Team via their official newsroom.
Jeff Chiu/AP. The ride-hailing service Uber said Friday that all its services are operational following what security professionals were calling a major data breach. It said there was no evidence ...
Government regulation should be involved if Uber loses data about the rides taken by its 100 million-plus users. (One risk of this data for Uber: It can be used to find one-night stands , for ...
The September 2022 Uber data breach included a hot new cyberattack tactic - the Multi-Factor Authentication (MFA) fatigue attack. Cybersecurity experts Sher...
Uber's former security officer, Joe Sullivan, is standing trial this week in what is believed to be the first case of an executive facing criminal charges in relation to a data breach.
The case pertains to a breach at Uber's systems that affected data of 57 million passengers and drivers. The company did not disclose the incident for a year.
Uber confirms incident and says no evidence of sensitive user data exposure. Uber/Twitter. This confirms that the investigation and response efforts continue and states that Uber has "no evidence ...
On January 27, 2023, a cybersecurity incident at Genova Burns LLC, a law firm representing Uber, brought to light the critical importance of robust third-party cyber risk management. After discovering that their systems had been compromised, an investigation revealed that hackers had infiltrated the firm's systems on December 14, 2022 ...
The recent third-party breach of Uber data where an attack on its vendor Teqtivity exposed sensitive employee and customer data to the BreachForums hacking forum, was the latest in a string of ...
Uber made the payment to the hackers but kept the news of the breach quiet for more than a year. If you know more about the Uber breach, you can contact this author via Signal at +44 1536 853968.
On September 15, 2022, Uber employees were surprised to find an unauthorized user posting in their company's slack channel. They had hacked their way into the account and left a message that read, "I announce I am a hacker and Uber has suffered a data breach.". Uber employees, who did not reveal their identities, admitted that it appeared ...
On November 21, 2017, Uber announced that the personal data of 57 million users were stolen in a breach, including 600,000 drivers in the United States. Reuters just reported that " Uber ...
Breach explained Uber Breach 2022 - Everything You Need to Know. On Thursday, September 15th, Uber confirmed reports of an organization-wide cybersecurity breach. ... This is a worst-case scenario. The PAM system controls access to multiple systems, and having admin access means you can give yourself or extract secrets to all connected ...
According to the 2022 Ponemon Institute's report, insider attacks increased by 47%, resulting in compromised user credentials. An attempt was made by the hacker to socially engineer Uber workers, which resulted in access to a VPN and the company's internal network. Allegedly, an 18-year-old hacker is responsible for stealing data from Uber.
Using Uber's 2016 breach as a case study, company executives must be aware of and recognize the business and personal consequences associated with breach response, and specifically with intentionally concealing a breach. ... (FTC) investigation into Uber's data security practices, which had been triggered, in part, by another Uber data ...