

Data Communication Past Papers Exam Questions
Guess paper 1: data communication fall – 2020 past papers.
Time Allowed: 3 hours
Total Marks: 70, Passing Marks (35)
Q1. Define the following terms:
a) Physical path and channel b) Network topology c) Protocol suit d) Composite signal e) Transmission mode
Q2. Give brief introduction of layer architecture and discuss first 3 layers of OSI model in detail.
Q3. What is the importance of multiplexing in data communication? Discuss its different application in detail.
Q4. Give a brief introduction to local area network. Differentiate between FDDI and Token ring network in detail with suitable examples.
Q5. Explain the concept of switching in data communication along its different categories.
Q6. Write a detail discussion on “Encoding and Modulation” mechanism.
Q7. Write short notes on any two of the following. a. Error detection and correction b. Transmission media c. Data link protocols
Guess Paper 2: Data Communication Spring – 2020 Past Papers
Q.1 Multiple Choice Questions i)____________ Layer responsible for movements of individual bits from one hop (node) to the next. (a) Physical Layer (b) Data link layer (c) Transport layer ii) Communication between a computer and a keyboard involves ______________ transmission. (a)Simplex (b) Half Duplex (c)Full Duplex iii) Line coding is the process of converting digital data to a ____________ signal. (a) Digital (b) Analog (c) Hybrid iv) Frequency-division multiplexing (FDM) is a _____________ technique (a) Digital (b) Analog (c) Hybrid v) The process-to-process delivery of the entire message is the responsibility of the _______ layer. (a) Transport (b) Application (c) Physical vi) A digital signal is a composite analog signal with a/an __________ bandwidth. (a)Infinite (b) Finite (c)Unlimited vii)The physical, data link, and ____________ layers are the network support layers. (a) Network (b) Transport (c) Presentation
Q2. (a) What are the differences between parallel and serial transmission? (b) Differentiate between TCP/IP Protocol suits and OSI Model?
Q3 (a) A complex low-pass signal has a bandwidth of 200 kHz. What is the minimum sampling rate for this signal? b) We want to digitize the human voice. What is the bit rate, assuming 8 bits per sample? (Hint: The human voice normally contains frequencies from 0 to 4000 Hz)
Q4 (a)What are the two approaches to packet-switching? (b) Distinguish between a link and a channel in multiplexing?
Q5 (a) List three techniques of digital-to-digital conversion? (b) What are the advantages of dividing an Ethernet LAN with a bridge?
Q6 (a) An analog signal carries 4 bits per signal element. If 1000 signal elements are sent per second, find the bit rate? (b) Define each term PSK, FSK and ASK.
Q7 (a) How does a single-bit error differ from a burst error? (b) How do guided media differ from unguided media?
Q.8 Write short notes on any two of the following: a). Checksum b). Attenuation c). Time Division Multiplexing (TDM)
Guess Paper 3: Data Communication Spring – 2019 Past Papers
i. Full Duplex ii. Serial and parallel transmissions iii. Periodic signal iv. Burst error v. Composite signal
Q2. Write a comprehensive note on OSI reference model.
Q3. Explain the importance and functionality of guided media in detail.
Q4. Discuss the in detail the encoding and modulation techniques.
Q5. Discuss the need of error detection and correction method. Also explain the working of VRC with a comprehensive example.
Q6. Write a detailed note on local area networks.
Q7. Write short notes on the following. i. Analog and Digital signals ii. Multiplexing
Guess Paper 4: Data Communication Fall – 2019 Past Papers
Guess paper 5: data communication spring – 2018 past papers.
Q.1 Attempt all parts of this question. (30 marks)
A. Write down True or False for the following (10 marks) a. Twisted Pair cable is the most widely used transmission media in Local Area Network (LAN). b. Port number is assigned at application layer which identifies the specific process or service in the end system. c. In Virtual Circuit (VC) switching data is transmitted over a packet switched network where the paths are identified by the VC numbers. d. FECN and BECN bits are used in the Frame Relay networks for congestion avoidance. e. In the Internet Protocol (IP) hostname to IP address mapping is done by the ARP (Address Resolution Protocol).
B. Choose the correct option. (10 marks) a. On a busy router port the incoming packets are stored in a) Firewall c) Queue/Buffer of the router b) Email Server d) Queue/Buffer of the receiver node b. DLCI (Data link connection identifier) is used in ….. networks to assign frames to PVC or SVC. a) ATM c) Ethernet networks b) Frame Relay d) both (a) and (b) c. Repeaters and Hubs are …. devices. a) Network Layer c) Data Link Layer b) Application Layer d) Physical Layer d. In a “class B” IPv4 address scheme the number of bits reserved for Network ID are a) 8 bits c) 16 bits b) 24 bits d) 32 bits e. ATM Cell size is …. Bytes. a) 52 c) 65535 b) 128 d) 512
C. Fill in the blanks (10 marks) a. IPv6 consists total of ……. bits. b. TFTP stands for …. . c. ICMP stands for … . d. UDP is used at …. layer for real time multimedia transmission. e. IP addresses are assigned at … layer of OSI model.
Q.2 What is Multiplexing? Explain Frequency and Time division multiplexing (FDM and TDM) in detail with examples/diagrams? (10 marks)
Q.3 Explain Circuit Switching and Packet Switching in detail with example for each specific type? Provide diagrams for the two types of Packet Switching that is (a) datagram and (b) virtual circuit switching. (10 marks)
Q.4 What is a Frame Relay? Explain Packet format, DLCI assignment and Congestion avoidance scheme in Frame Relay networks? (10 marks)
Q.5 What is Transmission Media? Write different types of Transmission Media used in Computer Networks. Explain briefly Cable Media. (10 marks)
Q.6 What is Domain Name System (DNS)? Briefly explain flat name space and hierarchical name space with diagrams. Explain the need of DNS in the IP networks? (3+4+3=10 marks)
Q.7 Write short note on any two of the following: (10 marks) a) ISDN, its services and layers b) Simple Network Management Protocol (SMNP) c) ATM and its connection types (PVC and SVc) d) Flow control schemes of the Data Link Layer
500+ Past Papers – Computer Science
Related posts:.
- Electronic Communication Past Papers Exam Questions
- Effective Communication Past Papers Exam Questions
- Functional Communication Past Papers Exam Questions
- Data Structures Past Papers Exam Questions
- Data Warehousing Past Papers Exam Questions
- Communication Systems Important Questions – Past Papers
Contents Copyrights reserved by T4Tutorials
New York University
Computer Science Department
Courant Institute of Mathematical Sciences
Course Title: Data Communication & Networks Course Number: g22.2662-001
Instructor: Jean-Claude Franchitti Session: 4
Assignment #2
I. Due Thurday March 6, 2008, at the beginning of class.
II. Objectives
- See protocols in action.
III. References
- Slides and handouts posted on the course Web site
- Textbook chapters as applicable
IV. Software Required
- Wireshark Packet Sniffer and Packet Capture Library (see section V below).
- Microsoft Word.
- Win Zip as necessary.
V. Assignment
Preamble and Disclaimer:
As noted on the corresponding SourceForge site, the Ethereal development team switched names from Ethereal to Wireshark in May 2006 due to trademark issues (see http://www.wireshark.org/faq.html#q1.2 for more details on this). Incidentally, some people pronounce the name Ethereal as “ether-real,” while others pronounce it “e-thir-E-al,” as in the English word ethereal, which means ghostly or insubstantial. The Ethereal name’s origin comes from the Ethernet protocol, a link-level protocol that is studied extensively in Chapter 5 of the textbook, and in the class labs.
1. Wireshark Lab - Getting Started
One’s understanding of network protocols can often be greatly deepened by “seeing protocols in action” and by “playing around with protocols” – observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. This can be done in simulated scenarios or in a “real” network environment such as the Internet. The Java applets that accompany the textbook take the first approach. In the Wireshark labs, we’ll take the latter approach. You’ll be running various network applications in different scenarios using a computer on your desk, at home, or in a lab. You’ll observe the network protocols in your computer “in action,” interacting and exchanging messages with protocol entities executing elsewhere in the Internet. Thus, you and your computer will be an integral part of “live” labs in this class. You’ll observe, and you’ll learn, by doing.
The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer . As the name suggests, a packet sniffer captures (“sniffs”) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine.
Figure 1 shows the structure of a packet sniffer. At the right of Figure 1 are the protocols (in this case, Internet protocols) and applications (such as a web browser or ftp client) that normally run on your computer. The packet sniffer, shown within the dashed rectangle in Figure 1 is an addition to the usual software in your computer, and consists of two parts. The packet capture library receives a copy of every link-layer frame that is sent from or received by your computer. Recall from the discussion from section 1.5.2 in the text (Figure 1.20 in the 4 th Edition of the textbook used for the class) that messages exchanged by higher layer protocols such as HTTP, FTP, TCP, UDP, DNS, or IP all are eventually encapsulated in link-layer frames that are transmitted over physical media such as an Ethernet cable. In Figure 1, the assumed physical media is an Ethernet, and so all upper layer protocols are eventually encapsulated within an Ethernet frame. Capturing all link-layer frames thus gives you all messages sent/received from/by all protocols and applications executing in your computer.
The second component of a packet sniffer is the packet analyzer , which displays the contents of all fields within a protocol message. In order to do so, the packet analyzer must “understand” the structure of all messages exchanged by protocols. For example, suppose we are interested in displaying the various fields in messages exchanged by the HTTP protocol in Figure 1. The packet analyzer understands the format of Ethernet frames, and so can identify the IP datagram within an Ethernet frame. It also understands the IP datagram format, so that it can extract the TCP segment within the IP datagram. Finally, it understands the TCP segment structure, so it can extract the HTTP message contained in the TCP segment. Finally, it understands the HTTP protocol and so, for example, knows that the first bytes of an HTTP message will contain the string “GET,” “POST,” or “HEAD,” as shown in Figure 2.8 in the text.
We will be using the Wireshark packet sniffer (i.e., www.wireshark.org) for these labs, allowing us to display the contents of messages being sent/received from/by protocols at different levels of the protocol stack. (Technically speaking, Wireshark is a packet analyzer that uses a packet capture library in your computer). Wireshark is a free network protocol analyzer that runs on Windows, Linux/Unix, and Mac computers. It’s an ideal packet analyzer for our labs – it is stable, has a large user base and well-documented support that includes:
(a) A user-guide (i.e., http://www.wireshark.org/docs/ )
(b) Man pages (i.e., http://www.wireshark.org/docs/man-pages/ )
(c) A detailed FAQ (i.e., http://www.wireshark.org/faq.html )
(d) Rich functionality that includes the capability to analyze more than 500 protocols
(e) A well-designed user interface
The Wireshark packet sniffer operates in computers using Ethernet to connect to the Internet, as well as so-called point-to-point protocols such as PPP.
2. Wireshark Lab – Getting Wireshark
In order to run Wireshark, you will need to have access to a computer that supports both Wireshark and the libpcap packet capture library. If the libpcap software is not installed within your operating system, you will need to install libpcap or have it installed for you in order to use Wireshark. See http://www.wireshark.org/download.html for a list of supported operating systems and download sites.
Download and install the Wireshark and (if needed) the libpcap software:
· If needed, download and install the libpcap software. Pointers to the libpcap software are provided from the Wireshark download pages. For Windows machines, the libpcap software is known as WinPCap , and can be found at http://winpcap.mirror.ethereal.com/ .
· Go to www.wiresharkl.org and download and install the Wireshark binary for your computer. It is recommended to download from http://sourceforge.net/project/showfiles.php?group_id=255 which includes a WinPCap bundle option.
· Download the Wireshark user guide. You will most likely only need Chapters 1 and 3.
The Wireshark FAQ has a number of helpful hints and interesting tidbits of information, particularly if you have trouble installing or running Wireshark.
3. Wireshark Lab – Running Wireshark
When you run the Wireshark program, the Wireshark graphical user interface shown in Figure 2a will be displayed. Initially, no data will be displayed in the various windows.
Figure 2a: Wireshark Capture Options Window
Figure 2 below shows the original Ethereal graphical user interface along with an explanation of the various areas which applies to both Ethereal and Wireshark.
The Wireshark interface has five major components:
· The command menus are standard pulldown menus located at the top of the window. Of interest to us now are the File and Capture menus. The File menu allows you to save captured packet data or open a file containing previously captured packet data, and exit the Wireshark application. The Capture menu allows you to begin packet capture.
· The packet-listing window displays a one-line summary for each packet captured, including the packet number (assigned by Wireshark; this is not a packet number contained in any protocol’s header), the time at which the packet was captured, the packet’s source and destination addresses, the protocol type, and protocol-specific information contained in the packet. The packet listing can be sorted according to any of these categories by clicking on a column name. The protocol type field lists the highest level protocol that sent or received this packet, i.e., the protocol that is the source or ultimate sink for this packet.
· The packet-header details window provides details about the packet selected (highlighted) in the packet listing window. (To select a packet in the packet listing window, place the cursor over the packet’s one-line summary in the packet listing window and click with the left mouse button.). These details include information about the Ethernet frame and IP datagram that contains this packet. The amount of Ethernet and IP-layer detail displayed can be expanded or minimized by clicking on the right-pointing or down-pointing arrowhead to the left of the Ethernet frame or IP datagram line in the packet details window. If the packet has been carried over TCP or UDP, TCP or UDP details will also be displayed, which can similarly be expanded or minimized. Finally, details about the highest level protocol that sent or received this packet are also provided.
· The packet-contents window displays the entire contents of the captured frame, in both ASCII and hexadecimal format.
· Towards the top of the Wireshark graphical user interface, is the packet display filter field, into which a protocol name or other information can be entered in order to filter the information displayed in the packet-listing window (and hence the packet-header and packet-contents windows). In the example below, we’ll use the packet-display filter field to have Wireshark hide (not display) packets except those that correspond to HTTP messages.
4. Wireshark Lab – Taking Wireshark for a Test Run
The best way to learn about any new piece of software is to try it out! Do the following
1. Start up your favorite web browser, which will display your selected homepage.
2. Start up the Wireshark software. You will initially see a window similar to that shown in Figure 2, except that no packet data will be displayed in the packet-listing, packet-header, or packet-contents window, since Wireshark has not yet begun capturing packets.
3. To begin packet capture, select the Capture pull down menu and select Options . This will cause the “Wireshark: Capture Options” window to be displayed, as shown in Figure 3.
Figure 3: Wireshark Capture Options Window
4. You can use all of the default values in this window. The network interfaces (i.e., the physical connections) that your computer has to the network will be shown in the Interface pull down menu at the top of the Capture Options window. In case your computer has more than one active network interface (e.g., if you have both a wireless and a wired Ethernet connection), you will need to select an interface that is being used to send and receive packets (mostly likely the wired interface). After selecting the network interface (or using the default interface chosen by Wireshark), click Start . Packet capture will now begin - all packets being sent/received from/by your computer are now being captured by Wireshark!
5. After you begin packet capture, you can select Statistics > Protocol Hierarchy from the command menus to obtain a summary of the number of packets of various types that are being captured as shown in Figure 4.
Figure 4: Wireshark Protocol Hierarchy Statistics
6. While Wireshark is running, enter the URL: http://gaia.cs.umass.edu/ethereal-labs/INTRO-ethereal-file1.html and have that page displayed in your browser. In order to display this page, your browser will contact the HTTP server at gaia.cs.umass.edu and exchange HTTP messages with the server in order to download this page, as discussed in section 2.2 of the text. The Ethernet frames containing these HTTP messages will be captured by Wireshark.
7. After your browser has displayed the INTRO-ethereal-file1.html page, stop Wireshark packet capture by selecting Capture > Stop in the Wireshark in the command menus. The Wireshark window will display all packets captured since you began packet capture. The Wireshark window should now look similar to Figure 2. You now have live packet data that contains all protocol messages exchanged between your computer and other network entities! The HTTP message exchanges with the gaia.cs.umass.edu web server should appear somewhere in the listing of packets captured. But there will be many other types of packets displayed as well (see, e.g., the many different protocol types shown in the Protocol column in Figure 2). Even though the only action you took was to download a web page, there were evidently many other protocols running on your computer that are unseen by the user. We’ll learn much more about these protocols as we progress through the text! For now, you should just be aware that there is often much more going on than “meet’s the eye”!
8. Type in “http” (without the quotes, and in lower case – all protocol names are in lower case in Wireshark) into the display filter specification window at the top of the main Wireshark window. Then select Apply (to the right of where you entered “http”). This will cause only HTTP message to be displayed in the packet-listing window.
9. The HTTP GET message that was sent from your computer to the gaia.cs.umass.edu HTTP server should be shown among the first few http message shown in the packet-listing window. When you select the HTTP GET message, the Ethernet frame, IP datagram, TCP segment, and HTTP message header information will be displayed in the packet-header window. Recall that the HTTP GET message that is sent to the gaia.cs.umass.edu web server is contained within a TCP segment, which is contained (encapsulated) in an IP datagram, which is encapsulated in an Ethernet frame. If this process of encapsulation isn’t quite clear yet, review section 1.5 in the text. By clicking on the expansion buttons (+ or -) to the left side of the packet details window, you can minimize or maximize the amount of Frame, Ethernet, Internet Protocol, and Transmission Control Protocol information displayed. Maximize the amount information displayed about the HTTP protocol. Your Wireshark display should now look roughly as shown in Figure 5 (Note, in particular, the minimized amount of protocol information for all protocols except HTTP, and the maximized amount of protocol information for HTTP in the packet-header window).
10. Exit Wireshark
Figure 5: Wireshark Display After Step 9
Congratulations! You’ve now completed the first lab.
5. Wireshark Lab – What to hand in
The goal of this first lab was primarily to introduce you to Wireshark. The following questions will demonstrate that you’ve been able to get Wireshark up and running, and have explored some of its capabilities. Answer the following questions, based on your Wireshark experimentation.
1. What is the MAC address of your Host? You can find this in the frame level information.
2. List the different protocols that appear in the protocol column in the unfiltered packet-listing window in step 4.7 above.
3. How long did it take from when the HTTP GET message was sent until the HTTP OK reply was received? (By default, the value of the Time column in the packet-listing window is the amount of time, in seconds, since Wireshark tracing began. To display the Time field in time-of-day format, select the Wireshark View pull down menu, then select Time Display Format , then select Time-of-day .)
4. What is the Internet address of the gaia.cs.umass.edu (also known as www-net.cs.umass.edu)? What is the Internet address of your computer?
5. Print the two HTTP messages displayed in step 4.9 above. To do so, select Print from the Wireshark File command menu, and select “ Selected Packet Only” under Packet Range and “As displayed” under Packet Format and then click OK.
Save your capture in a capture file named Nxxx.cap where Nxxx is your student ID.
Submit this capture file and the answers to the questions above.
Email your assignment (archive) file to your TA.
VI. Deliverables
- Electronic: Your assignment (archive) file must be emailed to the TA. The file must be created and sent by the beginning of class. After the class period, the homework is late. The email clock is the official clock.
- Written: Printout of the file(s) included in your assignment (archive) file. The cover page supplied on the next page must be the first page of your assignment file
Fill in the blank area for each field.
The sequence of the hardcopy submission is:
1. Cover sheet
1. Assignment Answer Sheet(s)
VII. Sample Cover Sheet
Name ________________________ Username: ______________ Date: ____________ (last name, first name) Section: ___________
Assignment 2
Assignment Layout (25%)
o Assignment is neatly assembled on 8 1/2 by 11 paper.
o Cover page with your name (last name first followed by a comma then first name), username and section number with a signed statement of independent effort is included.
o Answers to all assignment questions are correct. o File name is correct.
Total in points ___________________ Professor’s Comments:
Affirmation of my Independent Effort: _____________________________
(Sign here)
For Solo Learner Computer science
Data communication and networking mcqs set-1.
Home » Computer Science MCQs Sets » Data Communication & Networking MCQs » Data Communication and Networking MCQs Set-1
Data Communication and Networking MCQs offer a valuable resource to test and enhance your understanding of the intricate world of data transmission, network protocols, and communication technologies. Whether you’re a student preparing for exams or a professional aiming to strengthen your knowledge, these multiple-choice questions with Answers cover a wide spectrum of topics, including network architecture, protocols, and security. Dive into the realm of data communication and networking with these thought-provoking MCQs to bolster your expertise in this ever-evolving field.
PRACTICE IT NOW TO SHARPEN YOUR CONCEPT AND KNOWLEDGE
1. A computer network permits sharing of
- Information
- None of these
Resources and information among multiple devices such as computers, printers, and servers. Some of the resources that can be shared in a computer network include:
- Files and documents: Network users can share files and documents with each other. This makes it easy to collaborate on projects and to access files from different devices.
- Printers: Multiple users can share a single printer, making it easier to print documents without the need for each user to have their own printer.
- Internet connection: A network can share a single internet connection among multiple devices. This can be useful in situations where internet access is limited or expensive.
- Applications and software: In a networked environment, software and applications can be installed on a central server and accessed by multiple users.
- Storage devices: Network storage devices such as network-attached storage (NAS) devices allow users to store and share large amounts of data across a network.
- Peripherals: Other peripheral devices such as scanners, cameras, and projectors can be shared in a networked environment.
By allowing users to share these resources, a computer network can improve productivity, enhance communication, and reduce costs.
2. The first operational computer network in the world was the _________ for the United States Department of Defense
The first operational computer network in the world was the ARPANET (Advanced Research Projects Agency Network), which was created in the late 1960s by the United States Department of Defense. The ARPANET was designed to connect computers at different locations so that researchers could share resources and collaborate on projects. It was the predecessor to the modern Internet and was a key development in the history of computer networking.
3. ATM stands for
- Automatic taller machine
- Automated teller machine
- Automatic transfer machine
- Automated transfer machine
ATM stands for "Automated Teller Machine." It is a specialized computer terminal that allows users to perform banking transactions without the need for a human teller. ATMs are typically used to withdraw cash, check account balances, and transfer funds between accounts. They can be found in banks, retail locations, and other public places such as airports and shopping malls. ATMs are available 24/7 and provide users with convenient access to their bank accounts.
4. _______ is the technology that connects the machines and people within a site in a small area
The technology that connects machines and people within a site in a small area is called a Local Area Network (LAN). A LAN is a computer network that is confined to a relatively small area, such as a single building or campus. It typically consists of a group of interconnected devices such as computers, printers, and servers, along with the necessary networking hardware such as switches and routers. A LAN can be used to share resources and information among devices within a site, allowing users to communicate and collaborate more effectively. Some examples of LANs include office networks, school networks, and home networks.
5. ______ is a network that covers geographic areas that are larger, such as districts or cities
MAN stands for "Metropolitan Area Network". A Metropolitan Area Network is a type of computer network that covers a larger geographic area than a Local Area Network (LAN) but smaller than a Wide Area Network (WAN). It typically covers a metropolitan area, such as a city or a town. A MAN can be used to connect multiple LANs together, providing users with access to shared resources and information over a wider area. MANs are often used by businesses, universities, and other organizations that need to connect geographically dispersed locations within a city or a town.
6. ______ is a network that this technology connects sites that are in diverse locations
A network that covers geographic areas larger than a LAN, such as districts or cities, is called a Wide Area Network (WAN). A WAN is a network that spans a large geographic area and typically connects multiple LANs or other networks together. WANs can be used to connect devices in different buildings, cities, or even countries, allowing users to communicate and share resources over long distances. Examples of WAN technologies include the internet, leased lines, and satellite links. WANs are often used by businesses, government agencies, and other organizations that need to connect geographically dispersed locations.
7. ______ is a collection of point-to-point links that may form a circle
- Ring topology
A Ring Network is a collection of point-to-point links that may form a circle. In a ring network, each device is connected to two other devices, forming a continuous loop or ring. Data is transmitted around the ring in one direction, with each device passing the data to the next device until it reaches its destination. Ring networks can be used to connect devices in a local area network (LAN) or a wide area network (WAN), depending on the network topology and the type of devices being used. Ring networks have the advantage of being resilient to individual link failures, as data can still be transmitted around the ring in the opposite direction. However, they can be slower than other types of networks due to the need for data to travel around the entire ring.
8. The ISDN Internetworking Equipment devices are
- Terminal Adapters(TAs)
- ISDN Bridges
- ISDN Routers
- All of these
ISDN (Integrated Services Digital Network) Internetworking Equipment devices are devices used to connect ISDN networks with other types of networks. They are typically used in telecommunications to provide a bridge between different types of networks, allowing users to communicate and exchange information across different types of networks. Some common ISDN internetworking equipment devices include:
- ISDN routers: These devices are used to connect ISDN networks with other types of networks, such as local area networks (LANs) or wide area networks (WANs). They provide routing functions to enable data to be transmitted between the networks.
- ISDN switches: These devices are used to connect multiple ISDN devices to a single ISDN line, allowing users to share a single connection.
- ISDN terminal adapters: These devices are used to connect non-ISDN devices, such as analog telephones or fax machines, to an ISDN network.
ISDN internetworking equipment devices are an important component of telecommunications infrastructure and are used by businesses, government agencies, and other organizations to connect and communicate with others across different types of networks.
9. ATM networks are
- connectionless
- Interconnected
- connection oriented
- ATM (Asynchronous Transfer Mode) networks are a type of high-speed networking technology used to transmit large amounts of data over a network. ATM networks use a fixed-size cell-based transmission protocol, which provides a highly efficient and reliable means of transmitting data.
- In an ATM network, data is divided into fixed-size cells, each of which contains a header and a payload. The header contains information about the cell's destination and the priority level of the data, while the payload contains the actual data being transmitted. These cells are then transmitted over the network using virtual circuits, which are established between two devices to provide a dedicated communication path for the transmission of data.
- ATM networks are used in a variety of applications, including voice and video transmission, high-speed data transfer, and internet access. They are commonly used by service providers to provide high-speed network connectivity to businesses and other organizations, as well as for backbone networks that connect different types of networks together. While ATM technology has been largely superseded by newer networking technologies such as Ethernet and IP, it is still used in some specialized applications where high-speed, reliable data transmission is critical.
10. DHCP stands for
- Dynamic Host Configuration Protocol
- Digital Host Communication Provider
- Digital Host Communication Protocol
- Dynamic Host Configuration Provider
- DHCP stands for "Dynamic Host Configuration Protocol". DHCP is a network protocol used to automatically assign IP addresses and other network configuration information to devices on a network.
- When a device connects to a network using DHCP, it sends a request to a DHCP server for an IP address and other network configuration information, such as the subnet mask, default gateway, and DNS server addresses. The DHCP server then assigns an available IP address to the device, along with the other configuration information. This allows the device to communicate with other devices on the network and access the internet.
- DHCP is widely used in local area networks (LANs) and is a key component of most home and small business networks. It simplifies network administration by automating the assignment of IP addresses and other network configuration information, which can be time-consuming and error-prone if done manually. DHCP also allows network administrators to manage IP addresses and other network resources more efficiently, as it can help prevent IP address conflicts and ensure that devices are configured correctly.
1. Transmission media are usually categorized as __________
- fixed or unfixed
- determinate or indeterminate.
- guided or unguided.
- metallic or nonmetallic.
2. ___________ cable consists of an inner copper core and a second conducting outer sheath.
- Twisted pair
- Fiber-optic
- Shielded twisted pair.
3. Which of the following is not a guided medium?
- Twisted – pair.
- Coaxial cable
4. Which of the following primarily uses guided media?
- Cellular telephone system
- Local telephone system
- Satellite Communications
- Radio broadcasting
5. The amount of uncertainty in a system of symbol is called ______
6. coaxial cable has conductors with ________.
- equal resistance
- the same diameter
- a common axis
- above the common axis
7. A device that converts digital signals into analog signals is __________
8. all of the parts in a computer talk to each other by sending _________.
- digital signals
- smoothly varying signal waves
- analog signals
9. If user get both local and remote echoes, every character type will appear on the screen _______
- three times
10. What protects the coaxial cable from noise?
- Inner conductor
- Outer conductor
- Diameter of cable
- Insulating material
Looking for more? Check out the below resources.
Copyright © 2024 | ExamRadar. | Contact Us | Copyright || Terms of Use || Privacy Policy
CS 53600: Data Communication and Computer Networks (Spring 2024)
Course information.
LE1 TR 1:30-2:45pm LWSN 1142
Instructor: Kihong Park [email protected] +1-765-494-7821 office hours: TR 3-4pm (HAAS 220) or by appointment
PSO: (HAAS G050) W 2:30-3:20pm (Chen) W 3:30-4:20pm (Guo) F 9:30-10:20am (Chen)
Textbook: Computer Networks: A Systems Approach by Peterson and Davie (latest edition)
Announcements
- The fifth lab assignment has been graded. To check your score (lab5.rpt), please follow the same procedure as before.
- The final exam is scheduled on 4/30/2024, 1-2:30pm; HAMP 1252, closed note/book. The scope is comprehensive but focus will be on material covered after the midterm. Sample exam and solution: fall 21 exam ( sol ) | fall 16 exam ( sol )
- The sixth assignment, lab6, has been released. As noted in the lab description, lab6 is an optional bonus assignment whose points contribute to the exam (midterm, final) component of the course. lab6 has a shortened due date.
- Correction to lab5, 1.4, second-to-last paragraph: The sentence "If Q(t) < targetbuf ..." should state that 10 - (q * 10) is sent back as feedback, not q * 10. I have updated the handout which includes an example.
- The fourth lab assignment has been graded. To check your score (lab4.rpt), please follow the same procedure as before. You have one week to follow up.
- The midterm has been graded. Please follow the same procedure as the lab assignments to check your score (mid.rpt). The text file, mid-stats.txt, in the course directory contains relevant stats. You may pick up your exam during my office hours. Compare your answers against the posted solution key. If you have any questions, please come to my office hours. You have two weeks to follow up. Copy of midterm and solution: exam | solution .
- The fifth assignment, lab5, has been released.
- The midterm is scheduled on March 19, 2024; in-class, closed note/book. Scope: material covered in class and lab assignments until/inclusive transport layer protocols (lec1 and lec2). Sample exam and solution: fall 21 exam ( sol ) | fall 19 exam ( sol ).
- The third lab assignment has been graded. To check your score (lab3.rpt), please follow the same procedure as before. You have until March 22 to follow up if you have any questions.
- My office hour on 3/5, 3-4pm, will be held on 3/8, 11am-noon. I will also hold an additional office hour on 3/18, 1-2pm.
- The fourth assignment, lab4, has been released.
- The second lab assignment has been graded. To check your score (lab2.rpt), please follow the same procedure as lab1.
- lab3 has been updated with the Bonus Problem specification.
- The third assignment, lab3, has been released.
- Due to family emergency I will be away 2/13 and 2/15. Prof. Sonia Fahmy will guest lecture on 2/13, Prof. Muhammad Shahbaz will guest lecture on 2/15. PSOs and TA office hours will follow regular schedule.
- The first lab assignment has been graded. To check your score, please follow the instructions in scores.txt in the course directory accessible from the lab machines. You have one week to follow up if there are questions.
- The second assignment, lab2, has been released.
- The first assignment, lab1, has been released.
- There are no PSOs and TA office hours during the first two weeks of class.
Lab Assignments
Lecture notes.
- Introduction. ( lec1 | lec2 )
- Fundamentals of data transmission. ( lec1 | lec2 | lec3 )
- Link layer: basic techniques. ( lec1 | lec2 )
- Link layer technologies. ( lec1 | lec2 | lec3 )
- Internetworking. ( lec1 | lec2 )
- Transport layer protocols. ( lec1 | lec2 )
- Congestion control and multimedia streaming. ( lec1 | lec2 )
- TCP congestion control for file transport. ( lec1 )
- Intra- and inter-domain routing. ( lec1 | lec2 ) [ SecurityTrails | CIDR Report ]
- Internet traffic and quality of service. ( lec1 )
- Wireless communication: basic features and idiosyncrasies. ( lec1 | lec2 )
- Application layer protocols. ( lec1 ) [Slides from P&D textbook.] Performance driven evolution of HTTP from 1.0 to 3, including end system design. Configuration of DNS, performance support for CDN and cloud.
Prerequisites
Undergraduate-level exposure to operating systems; solid background in C and Linux/UNIX (experience with projects and system programming); basic CS undergraduate-level mathematics preparation (calculus, discrete math, linear algebra).

Grading Policy
The grade will be determined by a midterm, a final, and 6 lab assignments. Their relative weights are:
Lab assignments may have opportunities to earn bonus points. These points serve to more easily reach the maximum achievable points in the lab assignment component. The points do not carry over and are capped at 45%. The same goes for the midterm and final exams which are capped at 25% and 30%, respectively. The course grade is not curved. Approximately, a total weighted score in the 90s maps to an A-range grade (includes +/- grades), mid-70s to 80s for B-range, mid-60s to low-70s C and C+.
Lab Assignment Policies
We will use Linux PCs in HAAS G050 as our development and testing environment. The lab machines are accessible via ssh remotely.
Getting your CS account.
Students registered in the course should have an account automatically set up. Please check by going to HAAS G050 and logging into one of the machines. If you have registered but don't have an account, please contact [email protected] .
Late Policy
To help manage unexpected scheduling demands, you are given 4 late days in total that may be used for late submissions of lab assignments. For example, you may submit 1 day late on four lab assignments, or 4 days late on one lab assignment. Any combination is valid as long as the total days delayed does not exceed 4. There will be a total of 6 lab assignments. Late days not utilized at the end of the semester will be converted to 15 bonus points each (maximum of 60).
Academic Integrity
We aim to foster an open and collegial class environment. At the same time, we are vigorously opposed to academic dishonesty because it seriously detracts from the education of honest students. Because of this, we have the following standard policy on academic integrity, consistent with Purdue University's official policy.
All CS536 assignments, by default, are individual efforts and collaboration of any form is not allowed. This includes discussing solution ideas and sharing of code. Utilizing others' code found on the Internet is not allowed. Utilizing code generated by AI tools such as ChatGPT is not allowed. If you have a question or are unsure, please contact me.
Students who share their work with others are as responsible for academic dishonesty as the student benefiting from the material. Students are not to show work to other students, and are responsible for the security of their work. File/directory permissions must be set to be unreadable to others (e.g. use "chmod -R 700 *" from your home directory). The same goes if you utilize depositories such as GitHub. If you need assistance protecting your work, please contact the TAs or the instructor.
Students who encourage others to cheat or plagiarize, or students who are aware of plagiarism or cheating and do not report it are also participating in academically dishonest behavior.
We will use a software tool, MOSS , to check for copying among submitted assignments. Additionally, we will inspect all submitted material to detect academic integrity violation.
If you have any assignment related questions, please utilize the PSOs and office hours which are scheduled Monday-Friday. The main difference between getting help on coding related questions from the instructor/TAs versus a fellow student is that the instructor/TAs will provide assistance that help you tackle a problem on your own without revealing the solution.
Any case of academic dishonesty will be dealt with by a severe grade penalty in the overall class grade and referral to the office of the Dean of Students.
Emergencies
In the event of an emergency, course requirements, deadlines, and grading percentages are subject to changes that may be necessitated by a revised semester calendar. If such unusual circumstances arise, students may determine any such changes by contacting their instructors via email or phone, and checking the course web page for updates. In the event of a family emergency, please contact the instructor to set accommodations following university rules.
Campus emergencies and closings will be announced on local media and on the main Purdue University WWW site http://www.purdue.edu . Please consult the Purdue emergency preparedness resources web site for detailed information and relevant resources. Consult PUSH for COVID-19 related information.
In the event of health issues, please contact the Protect Purdue Health Center (PPHC) or your health care provider to receive support and medical attention. Reach out to your Academic Case Manager [email protected] to receive additional assistance. In case of hospitalization and other urgency care, please contact the Office of the Dean of Students (ODOS) who will document and notify the instructor. Please check the Excused Absence Policies site for additional details.
Purdue University is committed to advancing the mental health and well-being of its students. If you or someone you know is feeling overwhelmed, depressed, and/or in need of mental health support, services are available. For help, contact Counseling and Psychological Services (CAPS) at 765-494-6995 during and after hours, on weekends and holidays, or by going to the CAPS office on the second floor of the Purdue University Student Health Center (PUSH) during business hours.
Nondiscrimination
Purdue University is committed to maintaining a community which recognizes and values the inherent worth and dignity of every person; fosters tolerance, sensitivity, understanding, and mutual respect among its members; and encourages each individual to strive to reach his or her potential. In pursuit of its goal of academic excellence, the University seeks to develop and nurture diversity. The University believes that diversity among its many members strengthens the institution, stimulates creativity, promotes the exchange of ideas, and enriches campus life. A hyperlink to Purdue's full Nondiscrimination Policy Statement is included in Brightspace under University Policies.
Accessibility
Purdue University is committed to making learning experiences accessible. If you anticipate or experience physical or academic barriers based on disability, you are welcome to let me know so that we can discuss options. You are also encouraged to contact the Disability Resource Center at: [email protected] or by phone: 765-494-1247.
Course Content
This is a graduate-level introductory course to computer networks and data communication. Our goal is to understand fundamental networking concepts, their implementation and application in today's interconnected information technology world. Computer networks is a rapidly evolving field, with new technologies and standards in the works as we speak. This makes the field relevant and exciting. Without a firm grounding in its fundamentals, however, it can also be a confusing and overwhelming subject matter. This course aims to provide this grounding.
This course is a modern introduction to computer networks, spanning the logical organization of four pertinent features: architecture, algorithms, implementation, and performance. The course will cover background and current issues facing modern communication networks, network architecture (hardware, software), fundamentals of data transmission (wired, wireless), LAN technology and data link protocols (switched Ethernet, wireless LAN CSMA/CA, OFDM, OFDMA, personal area networks, cellular network OFDMA, TDMA, FDMA, CDMA, MIMO, GPS, mobility), packet/circuit switching in wide-area networks, internetworking using TCP/UDP/IP (socket programming in Linux), routing (intra- and inter-domain), congestion control (TCP and multimedia UDP streaming), real-time video/audio/voice and quality of service, network security, and high-level network services (DNS, HTTP, SNMP, e-mail). One of the topics we will emphasize is wireless networks, a key driver of today's ubiquitous mobile environment.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Data Communication And Network Assignment 01

Related Papers
Boyyosaa Korme
bishal bhusal
joy stevenson
The ultimate goal of the transport layer is to provide efficient, reliable, and cost-effective data transmission service to its users, normally processes in the application layer. To achieve this, the transport layer makes use of the services provided by the network layer. The software and/or hardware within the transport layer that does the work is called the transport entity. The transport entity can be located in the operating system kernel, in a library package bound into network applications, in a separate user process, or even on the network interface card. The first two options are most common on the Internet. Transport layer services are conveyed to an application via a programming interface to the transport layer protocols. The services may include the following features: • Connection-oriented communication: It is normally easier for an application to interpret a connection as a data stream rather than having to deal with the underlying connection-less models, such as the datagram model of the User Datagram Protocol (UDP) and of the Internet Protocol (IP). • Same order delivery: The network layer doesn't generally guarantee that packets of data will arrive in the same order that they were sent, but often this is a desirable feature. This is usually done through the use of segment numbering, with the receiver passing them to the application in order. This can cause head-of-line blocking. • Reliability: Packets may be lost during transport due to network congestion and errors. By means of an error detection code, such as a checksum, the transport protocol may check that the data is not corrupted, and verify correct receipt by sending an ACK or NACK message to the sender. Automatic repeat request schemes may be used to retransmit lost or corrupted data. • Flow control: The rate of data transmission between two nodes must sometimes be managed to prevent a fast sender from transmitting more data than can be supported by the receiving data buffer, causing a buffer overrun. This can also be used to improve efficiency by reducing buffer underrun. • Congestion avoidance: Congestion control can control traffic entry into a telecommunications network, so as to avoid congestive collapse by attempting to avoid oversubscription of any of the processing or link capabilities of the intermediate nodes and networks and taking resource reducing steps, such as reducing the rate of sending packets. For example, automatic repeat requests may keep the network in a congested state; this situation can be avoided by adding congestion avoidance to the flow control, including slow-start. This keeps the bandwidth consumption at a low level in the beginning of the transmission, or after packet retransmission. • Multiplexing: Ports can provide multiple endpoints on a single node. For example, the name on a postal address is a kind of multiplexing, and distinguishes between different recipients of the same location. Computer applications will each listen for information on their own ports, which enables the use of more than one network service at the same time. It is part of the transport layer in the TCP/IP model, but of the session layer in the OSI model. Transport Service Primitives To allow users to access the transport service, the transport layer must provide some operations to application programs, that is, a transport service interface. Each transport service has its own
Edward Nangaku
Venkatesh Konada
IJAR Indexing
A majority of the internet uses a protocol suite called the Internet Protocol Suite also known as the TCP/IP protocol suite. This suite is a combination of protocols which encompasses a number of different protocols for different purpose and need. Because the two major protocols in this suites are TCP (Transmission Control Protocol) and IP (Internet Protocol), this is commonly termed as TCP/IP Protocol suite. This protocol suite has its own reference model which it follows over the internet. In contrast with the OSI model, this model of protocols contains less layers. An application layer is an abstraction layer that specifies the shared protocols and interface methods used by hosts in a communications network. The application layer abstraction is used in both of the standard models of computer networking; the Internet Protocol Suite (TCP/IP) and the Open Systems Interconnection model (OSI model). There are several protocols which work for users in Application Layer. Application layer protocols can be broadly divided into two categories.
Mymemes Mugala
Computer networking has become the core centre of computing across many platforms of devices; mobile phones, game consoles, tablets and computers in general. The need to communicate using audio and video has been widely used and is growing. This is often referred to as multimedia networking. For communication to be complete, multimedia applications or any applications require the services that are provided by the transport layer. The transport layer cannot be by passed. This layer is an interface between the Application layer and the Network layer of the TCP/IP protocol stack. The transport layer has protocols that play a huge role in offering the necessary services for process to process delivery to be successful. The protocols are responsible for the delivery of packets from the source to destination application.
Amenu Nageksi Fekadu
RELATED PAPERS
revistamotricidade.com
Luiza Augusta Tereza Gil Breitenfeld Granadeiro
Social Cognition
Journal of Social Cognition
Analytical Chemistry
The Photogrammetric Record
Andreas Klik
Roshdi Khalil
NeuroRehabilitation
George Wittenberg
Van Mensen en Dingen: tijdschrift voor volkscultuur in Vlaanderen
Els Veraverbeke
aulia syahdita
Crustaceana
Ernesto Chavez Ortiz
Jan-Erik Nylund
JETP Letters
Mikhail Katsnelson
Journal of Failure Analysis and Prevention
[1990] Proceedings of the 23rd Annual Workshop and Symposium@m_MICRO 23: Microprogramming and Microarchitecture
Tuyển tập công trình HNKH toàn quốc lần thứ 3 về điều khiển & Tự động hoá VCCA - 2015
Czechoslovak Journal of Physics
Peter Kopčanský
Zenodo (CERN European Organization for Nuclear Research)
Diana Constantino
Computer Physics Communications
Cédric Boulbe
Human Ecology
Mikael Jansson
Journal of Neurosciences in Rural Practice
Bharati Sahu
Archives of Current Research International
Sanjeeva Witharana
Internal Medicine
Mariana Jinga
Journal of Clinical Medicine
Emre Gazyakan
Marlène Lavrieux
Anne E . BARGES
Shegaw Getachew
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- School Guide
- Class 12 Syllabus
- Class 12 Revision Notes
- Maths Notes Class 12
- Physics Notes Class 12
- Chemistry Notes Class 12
- Biology Notes Class 12
- NCERT Solutions Class 12 Maths
- RD Sharma Solutions Class 12
- Data Communication Tutorial
Basics of Data Communication
- Data Communication - Definition, Components, Types, Channels
- Types of Computer Networks
- Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex)
- Difference between Serial and Parallel Transmission
- How Data Encapsulation & De-encapsulation Works?
- Network Layer Services- Packetizing, Routing and Forwarding
- Transport Layer responsibilities
- TCP/IP Model
Data and Signals
- Frequency Domain Filters and its Types
- Difference between Bit Rate and Baud Rate
Transmission of Signals
- Transmission Impairment in Data Communication
- What is Bandwidth? Definition, Working, Importance, Uses
- Digital To Digital Conversion in Computer Network
- Line Coding
- Analog to Digital Conversion
- Digital to Analog Conversion
- Quadrature Amplitude Modulation
- Analog to Analog Conversion (Modulation)
- What is Modulation?
Multiplexing
- Multiplexing (Channel Sharing) in Computer Network
- Types of Multiplexing in Data Communications
- Frequency Division and Time division multiplexing
Transmission Media
- Types of Transmission Media
- Twisted-pair Cable
- What is Coaxial Cable ?
- Fiber Optics and Types
- Difference between Twisted pair cable, Co-axial cable and Optical fiber cable
- Radio Waves
- Infrared light for Transmission
- Difference between Guided and Unguided Media
Error Detection and Correction
- Error Detection in Computer Networks
- Forward Error Correction in Computer Networks
- Vertical Redundancy Check (VRC) or Parity Check
- Longitudinal Redundancy Check (LRC)/2-D Parity Check
- Hamming Code in Computer Network
- Concepts of hamming distance
- Error Detection Code - Checksum
Channelization
- Frequency Division Multiple Access (FDMA) Techniques
- CDMA Full Form
- What is Ethernet?
- Bridges (local Internetworking device)
- Introduction of Gigabit Ethernet
- Network Address Translation (NAT)
Network Security
- Cryptography Introduction
- Substitution Cipher
- Columnar Transposition Cipher
- Symmetric Cipher Model
- Data encryption standard (DES) | Set 1
- Advanced Encryption Standard (AES)
- Block Cipher modes of Operation
- RSA Algorithm in Cryptography
- What is Digital Signature in Blockchain?
- Message Digest in Information security
- Birthday attack in Cryptography
- IP security (IPSec)
- What is VPN and How It Works?
- Wireless Security | Set 1
- Implementation of Diffie-Hellman Algorithm
- What is Email Security?
- PGP - Authentication and Confidentiality
Data Communication – Definition, Components, Types, Channels
Communication is defined as a process in which more than one computer transfers information, instructions to each other and for sharing resources. Or in other words, communication is a process or act in which we can send or receive data. A network of computers is defined as an interconnected collection of autonomous computers. Autonomous means no computer can start, stop or control another computer.
Components of Data Communication
A communication system is made up of the following components:
- Message: A message is a piece of information that is to be transmitted from one person to another. It could be a text file, an audio file, a video file, etc.
- Sender: It is simply a device that sends data messages. It can be a computer, mobile, telephone, laptop, video camera, or workstation, etc.
- Receiver: It is a device that receives messages. It can be a computer, telephone mobile, workstation, etc.
- Transmission Medium / Communication Channels: Communication channels are the medium that connect two or more workstations. Workstations can be connected by either wired media or wireless media.
- Set of rules (Protocol): When someone sends the data (The sender), it should be understandable to the receiver also otherwise it is meaningless. For example, Sonali sends a message to Chetan. If Sonali writes in Hindi and Chetan cannot understand Hindi, it is a meaningless conversation.
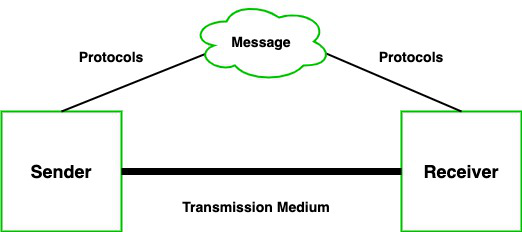
Therefore, there are some set of rules (protocols) that is followed by every computer connected to the internet and they are:
- TCP(Transmission Control Protocol) : It is responsible for dividing messages into packets on the source computer and reassembling the received packet at the destination or recipient computer. It also makes sure that the packets have the information about the source of the message data, the destination of the message data, the sequence in which the message data should be re-assembled, and checks if the message has been sent correctly to the specific destination.
- IP(Internet Protocol) : Do You ever wonder how computer determines which packet belongs to which device. What happens if the message you sent to your friend is received by your father? Scary Right. Well! IP is responsible for handling the address of the destination computer so that each packet is sent to its proper destination.
Type of data communication
As we know that data communication is communication in which we can send or receive data from one device to another. The data communication is divided into three types:
- Simplex Communication: It is one-way communication or we can say that unidirectional communication in which one device only receives and another device only sends data and devices uses their entire capacity in transmission. For example, IoT, entering data using a keyboard, listing music using a speaker, etc.
- Half Duplex communication: It is a two-way communication, or we can say that it is a bidirectional communication in which both the devices can send and receive data but not at the same time. When one device is sending data then another device is only receiving and vice-versa. For example, walkie-talkie.
- Full-duplex communication: It is a two-way communication or we can say that it is a bidirectional communication in which both the devices can send and receive data at the same time. For example, mobile phones, landlines, etc.
Communication Channels
Communication channels are the medium that connects two or more workstations. Workstations can be connected by either wired media or wireless media. It is also known as a transmission medium. The transmission medium or channel is a link that carries messages between two or more devices. We can group the communication media into two categories:
- Guided media transmission
- Unguided media transmission
1. Guided Media: In this transmission medium, the physical link is created using wires or cables between two or more computers or devices, and then the data is transmitted using these cables in terms of signals. Guided media transmission of the following types:
1. Twisted pair cable: It is the most common form of wire used in communication. In a twisted-pair cable, two identical wires are wrapped together in a double helix. The twisting of the wire reduces the crosstalk. It is known as the leaking of a signal from one wire to another due to which signal can corrupt and can cause network errors. The twisting protects the wire from internal crosstalk as well as external forms of signal interference. Types of Twisted Pair Cable :
- Unshielded Twisted Pair (UTP): It is used in computers and telephones widely. As the name suggests, there is no external shielding so it does not protects from external interference. It is cheaper than STP.
- Shielded Twisted Pair (STP): It offers greater protection from crosstalk due to shield. Due to shielding, it protects from external interference. It is heavier and costlier as compare to UTP.
2. Coaxial Cable: It consists of a solid wire core that is surrounded by one or more foil or wire shields. The inner core of the coaxial cable carries the signal and the outer shield provides the ground. It is widely used for television signals and also used by large corporations in building security systems. Data transmission of this cable is better but expensive as compared to twisted pair.
3. Optical fibers: Optical fiber is an important technology. It transmits large amounts of data at very high speeds due to which it is widely used in internet cables. It carries data as a light that travels inside a thin glass fiber. The fiber optic cable is made up of three pieces:
- Core: Core is the piece through which light travels. It is generally created using glass or plastic.
- Cladding: It is the covering of the core and reflects the light back to the core.
- Sheath: It is the protective covering that protects fiber cable from the environment.
2. Unguided Media : The unguided transmission media is a transmission mode in which the signals are propagated from one device to another device wirelessly. Signals can wave through the air, water, or vacuum. It is generally used to transmit signals in all directions. Unguided Media is further divided into various parts :
1. Microwave: Microwave offers communication without the use of cables. Microwave signals are just like radio and television signals. It is used in long-distance communication. Microwave transmission consists of a transmitter, receiver, and atmosphere. In microwave communication, there are parabolic antennas that are mounted on the towers to send a beam to another antenna. The higher the tower, the greater the range.
2. Radio wave: When communication is carried out by radio frequencies, then it is termed radio waves transmission. It offers mobility. It is consists of the transmitter and the receiver. Both use antennas to radiate and capture the radio signal.
3. Infrared: It is short-distance communication and can pass through any object. It is generally used in TV remotes, wireless mouse, etc.
Please Login to comment...
Similar reads.
- TrueGeek-2021
- Computer Networks
- School Learning
- School Programming
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- IGNOU CBCS BAG SOLVED ASSIGNMENT 2023-2024
- IGNOU CBCS BCOM(G) SOLVED ASSIGNMENT 2023-2024
- IGNOU CBCS BSC(G) SOLVED ASSIGNMENT 2022-2023
- IGNOU BA Hindi (BAHDH) SOLVED ASSIGNMENT
- IGNOU B.A English SOLVED ASSIGNMENT
- IGNOU B.A Sociology SOLVED ASSIGNMENT
- IGNOU B.A History SOLVED ASSIGNMENT
- IGNOU B.A Psychology SOLVED ASSIGNMENT
- IGNOU B.A Public Administration SOLVED ASSIGNMENT
- IGNOU B.A Political Science SOLVED ASSIGNMENT
- IGNOU BAECH (Economics) SOLVED ASSIGNMENT
- IGNOU B.A Philosophy SOLVED ASSIGNMENT
- IGNOU M.A Hindi SOLVED ASSIGNMENT
- IGNOU M.A English SOLVED ASSIGNMENT
- IGNOU M.A History SOLVED ASSIGNMENT
- IGNOU M.A Sociology SOLVED ASSIGNMENT
- IGNOU M.A Public Administration SOLVED ASSIGNMENT
- IGNOU M.A Political Science SOLVED ASSIGNMENT
- IGNOU M.A Psychology SOLVED ASSIGNMENT
- IGNOU M.A Economics SOLVED ASSIGNMENT
- IGNOU M.A RURAL DEVELOPMENT SOLVED ASSIGNMENT
- BCA 1st Semester
- BCA 2nd Semester
- BCA 3rd Semester
- BCA 4th Semester
- BCA 5th Semester
- BCA Question Papers
- Study Material
- Whatsapp Group
- RESULT TERM-END
- +919811854308

MCS-218 Data Communication and Computer Networks Previous Year Question Papers
Ignou all previous year question papers in one pdf.
एक PDF में पिछले वर्ष के सभी प्रश्न पत्र
The Advantages of studying IGNOU Solved Assignments are given below:
- Easy Accessibility: IGNOU solved assignments are easily accessible online, which means students can access them anytime and anywhere.
- Comprehensive Solutions: The solved assignments provide comprehensive answers to the questions asked in the assignments, which makes it easier for students to understand and study the topics.
- Cost-Effective: The solved assignments are available at a very economical rate, which makes them a great option for those who are on a budget.
- Reference Material: The solved assignments can be used as reference material for further study, as they provide detailed answers to the questions asked.
- Time-Saving: The solved assignments save a lot of time for students as they do not need to spend time researching and writing the answers themselves.
Can I score good marks by getting solved assignments?
Yes, you can get good marks by getting the Solved Assignment as it contains the answers to the questions asked in the assignment and will help you to understand the concepts better and score better.
Read more: How to Make IGNOU Solved Assignment?
RELATED ARTICLES MORE FROM AUTHOR
Bsw-131 समाज कल्याण प्रशासन और सामाजिक कार्य in hindi previous year question papers, bsw-131 social welfare administration and social action in english previous year question papers, bsw-130 मादक द्रव्यों के सेवन की रोकथाम in hindi previous year question papers, leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
- Terms & Condition
- Privacy Policy
- Refund & Cancellation
- Paid Solved Assignment

IMAGES
VIDEO
COMMENTS
Find step-by-step solutions and answers to Data Communications and Networking - 9780077445393, as well as thousands of textbooks so you can move forward with confidence. ... Questions. Page 153: Problems. Exercise 1. Exercise 2. Exercise 3. Exercise 4. Exercise 5. Exercise 6. Exercise 7. ... Programming Assignments. Exercise 1. Exercise 2 ...
Total Marks: 70, Passing Marks (35) Q.1 Multiple Choice Questions i)_____ Layer responsible for movements of individual bits from one hop (node) to the next. (a) Physical Layer (b) Data link layer (c) Transport layer ii) Communication between a computer and a keyboard involves _____ transmission. (a)Simplex (b) Half Duplex (c)Full Duplex iii) Line coding is the process of converting digital ...
Assignment 2 . Assignment Layout (25%) o Assignment is neatly assembled on 8 1/2 by 11 paper. o Cover page with your name (last name first followed by a comma then first name), username and section number with a signed statement of independent effort is included. o Answers to all assignment questions are correct. o File name is correct.
Assignment is neatly assembled on 8 1/2 by 11 paper. Cover page with your name (last name first followed by a comma then first name), username and section number with a signed statement of independent effort is included. Program and documentation submitted for Assignment #8 are satisfactory. File name is correct.
illustrate how you should formulate your answers. This midterm exam covers the following data communications and networks topics. covered in class: introduction and overview, the application laye r, data encoding and. transmission, and data link control. As the exam is ra ther long, it is EXTREMELY IMPORTANT to use GOOD TEST.
1800. in this year, engineers and scientists pioneer electrical communication method. 1836. the year where electrical telegraph system was invented. Study with Quizlet and memorize flashcards containing terms like Data, Communication, 1. Transmitter (source) 2. Transmission line (transmission medium) 3. Receiver (destination) and more.
COMSATS University Islamabad. Answer 1: Functions of Application layer: File transfer, access, and management (FTAM): An application layer allows a user to access the files in a remote computer, to retrieve the files from a computer and to manage the files in a remote computer. Mail services: An application layer provides the facility for email ...
Data Communication and Networking MCQs offer a valuable resource to test and enhance your understanding of the intricate world of data transmission, network protocols, and communication technologies. Whether you're a student preparing for exams or a professional aiming to strengthen your knowledge, these multiple-choice questions with Answers cover a wide spectrum of topics, including network ...
Data Communications and Networking Questions and Answers. Introduction. What is meant by Data Communication and explain its characteristics? What are the components of Data communication? Explain different Data flow directions. What is Network and explain characteristics of Networks? Write about different types of connections.
You have one week to follow up if there are questions. The second assignment, lab2, has been released. The first assignment, lab1, has been released. ... This is a graduate-level introductory course to computer networks and data communication. Our goal is to understand fundamental networking concepts, their implementation and application in ...
Download Data Communication Questions and problems and more Assignments Data Communication Systems and Computer Networks in PDF only on Docsity! Electronics II - Assignment (6) Lara Mamdouh Abdel-latif | 202124003 1 Review Questions: 1. Describe the goals of multiplexing.
Find notes, summaries, exercises for studying Data Communication Systems and Computer Networks! Prepare for your exams. Get points ... question bank for data communication and networking. DATA COMMUNICATION NETWORKS UNIT-1 PART-1 NOTES. Business Data Communication & Security - Assignment 2 UNICAF. Business Data Communication & Security ...
Download Data communication Exercises (Assignment) and more Data Communication Systems and Computer Networks Assignments in PDF only on Docsity! Electronics II - Assignment (4) Lara Mamdouh Abdel-latif | 202124003 1 Review Questions: 1. List three techniques of digital-to-digital conversion.
The need to communicate using audio and video has been widely used and is growing. This is often referred to as multimedia networking. For communication to be complete, multimedia applications or any applications require the services that are provided by the transport layer. The transport layer cannot be by passed.
Data communication refers to the transmission of digital data between two or more computers. A computer network allows computers to exchange data and consists of two or more linked computers that share resources. Personal area networks (PANs) interconnect personal devices to communicate within 10 meters, typically using wireless technology.
Data Communication Assignment 2. Introduction to Data Communication and Networking 95% (38) 6. Homework #4 - Jader Ricarte. ... P2-2: Answer the following questions about Figure 2 when the communication is from Maria to Ann: a. What is the service provided by layer 2 to layer 3 at Maria's site? Answer: Layer 2 takes the plaintext from layer 3 ...
Communication is defined as a process in which more than one computer transfers information, instructions to each other and for sharing resources. Or in other words, communication is a process or act in which we can send or receive data. A network of computers is defined as an interconnected collection of autonomous computers.
9. What are the issues in data link layer? The data link layer has a number of specific functions it can carry out. These functions include, a) Providing a well-defined service interface to the network layer. b) Dealing with transmission errors. c) Regulating the flow of data so that slow receivers are not swamped by fast senders. 10.
Distinguish among various types of Computer Networks. c. Distinguish between de-facto and de-jure standards in brief. Explain any two forums of standards. Unit II a. Differentiate OSI reference model with TCP/ IP model. b. Draw and explain the layout of ARPANet and NSFnet c.
3 CIT 852 DATA COMMUNICATION AND NETWORK Course Adapter Afolorunso, A. A. National Open University of Nigeria Course Coordinator Afolorunso, A. A.
Course: CICS-202 - Data Communication and Networks II Individual Assignment Design Assignment Question 1: Network Systems Design Implementation Setups Using VMware Environment Windows AD Server doud pfsense RT (LI OS) -- Vit Switch LAN Segment LAN W 2 (Win) Setup the above system layout in a VM Workstation Environment and make sure all connectivity configurations are working seamlessly.
Data Communications and Networking Question and Answers. Introduction. 1. What is meant by Data Communication and explain its characteristics? 2. What are the components of Data communication? 3. Explain different Data flow directions.
Comprehensive Solutions: The solved assignments provide comprehensive answers to the questions asked in the assignments, which makes it easier for students to understand and study the topics. Cost-Effective: The solved assignments are available at a very economical rate, which makes them a great option for those who are on a budget.