
- Cyber Crimes
- Popular Categories
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Powerpoint Templates and Google slides for Cyber Crimes
Save your time and attract your audience with our fully editable ppt templates and slides..
Item 1 to 60 of 83 total items
- You're currently reading page 1

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of thirty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Introduce your topic and host expert discussion sessions with this Cyber Crime Powerpoint Ppt Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
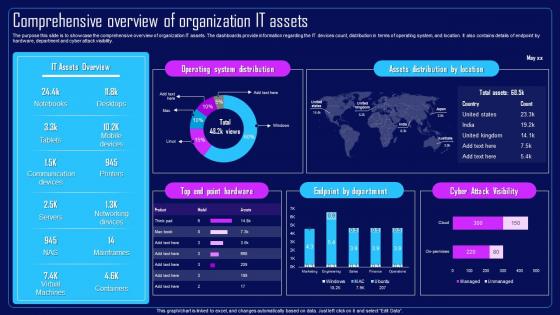
The purpose this slide is to showcase the comprehensive overview of organization IT assets. The dashboards provide information regarding the IT devices count, distribution in terms of operating system, and location. It also contains details of endpoint by hardware, department and cyber attack visibility. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Comprehensive Overview Of Organization IT Assets. Use it as a tool for discussion and navigation on Comprehensive Overview, Organization IT Assets, Dashboards, IT Devices Count, Operating System And Location. This template is free to edit as deemed fit for your organization. Therefore download it now.
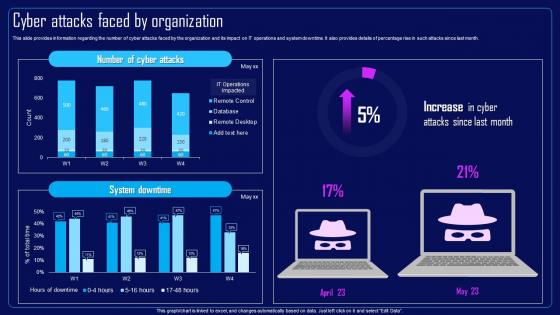
This slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks Faced By Organization, IT Operations And System Downtime, Remote Desktop using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
The slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Dashboard For Tracking, Cyber Attack Risk Levels, Risk Score And Infected Systems, Preventive Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
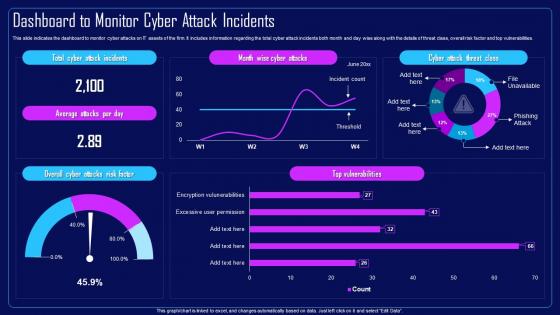
This slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
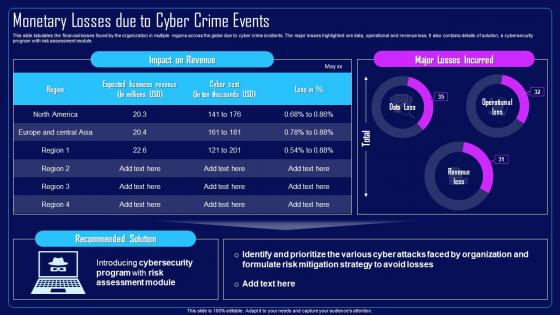
This slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Monetary Losses Due To Cyber Crime Events. Dispense information and present a thorough explanation of Tabulates The Financial Losses, Cyber Crime Incidents, Operational And Revenue Loss, Cybersecurity Program, Risk Assessment Module using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
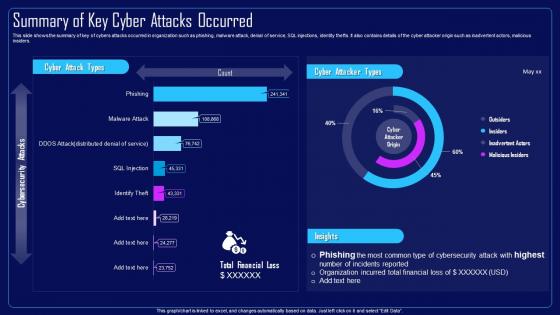
This slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred In Organization, Malware Attack, Denial Of Service, SQL Injections, Inadvertent Actors, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Present the topic in a bit more detail with this Compressive Planning Guide Monetary Losses Due To Cyber Crime Events. Use it as a tool for discussion and navigation on Introducing Cybersecurity Program, Risk Assessment Module, Tabulates The Financial Losses, Operational And Revenue Loss. This template is free to edit as deemed fit for your organization. Therefore download it now.
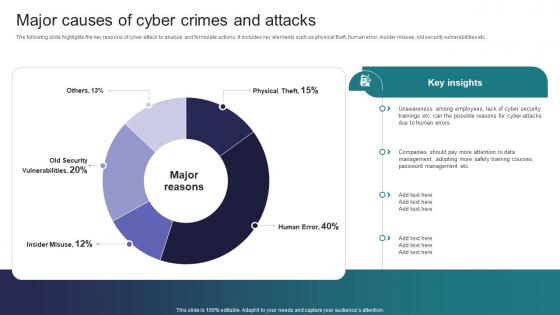
The following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
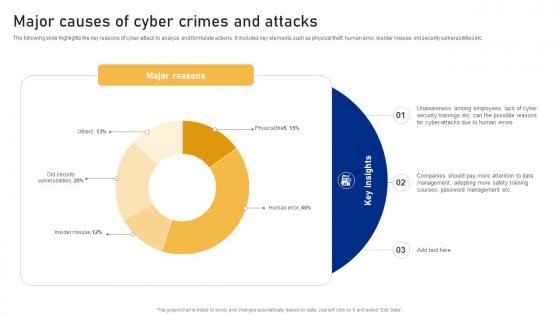
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment Use it as a tool for discussion and navigation on Major Reasons, Major Causes, Cyber Crimes And Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
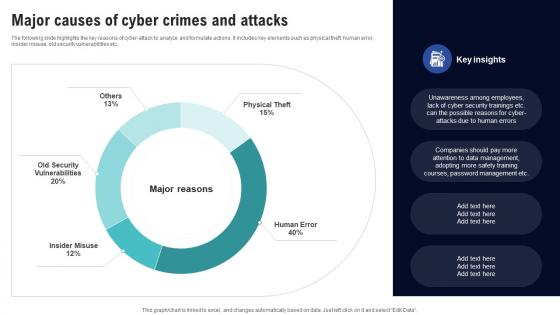
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
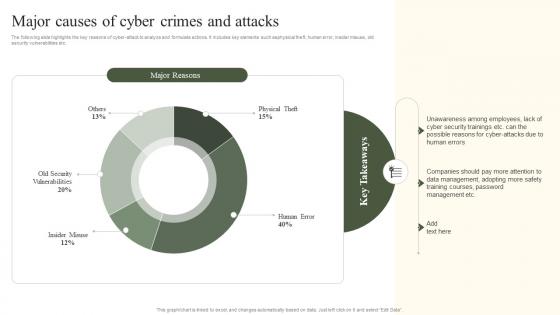
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such asphysical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Major Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.

Presenting Preventive Measures to Avoid Cyber crimes at Hotel. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizablealter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
Presenting Example Cyber Crimes In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Example Cyber Crimes. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Cyber Crime Money Laundering In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Crime Money Laundering. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
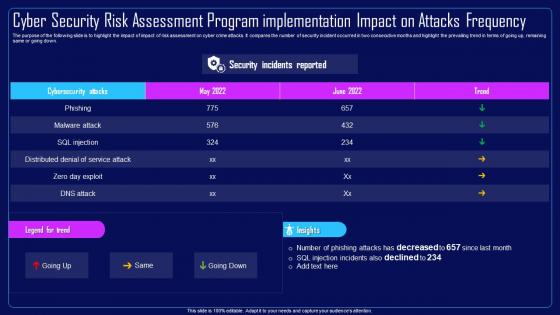
The purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes For Table Of Content Ppt Icon Format Ideas. Dispense information and present a thorough explanation of Action Plan To Combat, Comprehensive Overview, Organization IT Assets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
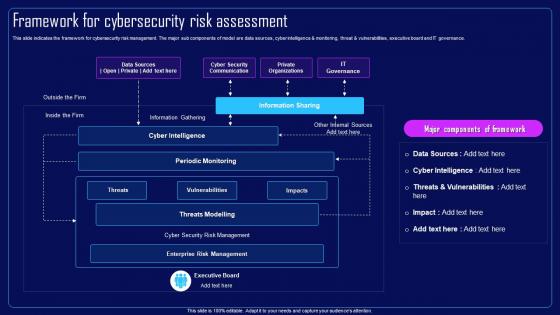
This slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Framework For Cybersecurity Risk Assessment. Use it as a tool for discussion and navigation on Cyber Intelligence, Periodic Monitoring, Threats Modelling, Cyber Security Risk Management, Enterprise Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
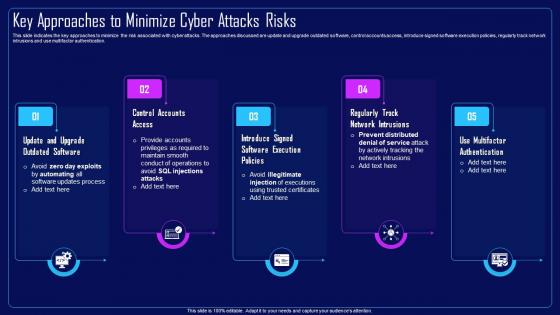
This slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Introducing Action Plan To Combat Cyber Crimes Key Approaches To Minimize Cyber Attacks Risks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Track Network Intrusions, Use Multifactor Authentication, Control Accounts Access, Update And Upgrade Outdated Software, using this template. Grab it now to reap its full benefits.
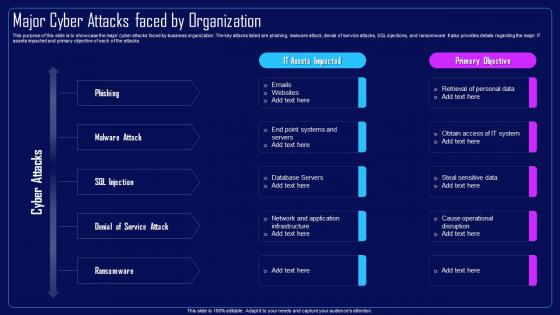
This purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Major Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Major Cyber Attacks, Malware Attack, Denial Of Service Attacks, SQL Injections, IT Assets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
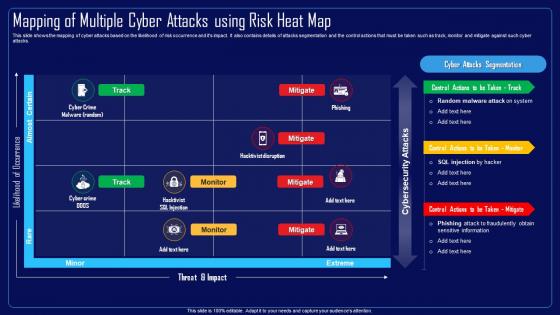
This slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Use it as a tool for discussion and navigation on Mapping Of Multiple Cyber Attacks, Risk Heat Map, Risk Occurrence, Attacks Segmentation And The Control Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Increase audience engagement and knowledge by dispensing information using Action Plan To Combat Cyber Crimes Multistep Approach To Conduct Cybersecurity Risk Assessment. This template helps you present information on four stages. You can also present information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
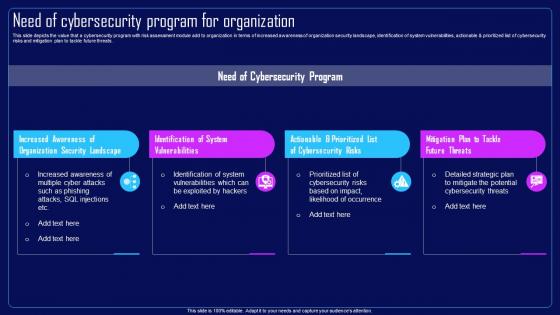
This slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Introducing Action Plan To Combat Cyber Crimes Need Of Cybersecurity Program For Organization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization Security Landscape, System Vulnerabilities, Actionable And Prioritized, Cybersecurity Risks, Mitigation Plan, using this template. Grab it now to reap its full benefits.
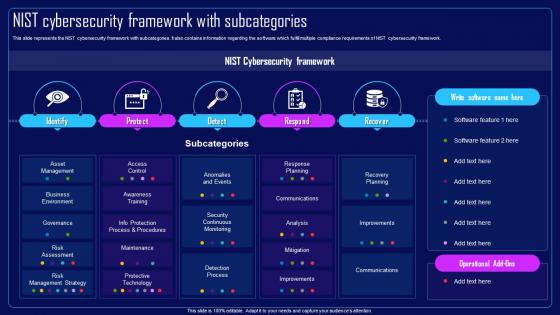
This slide represents the NIST cybersecurity framework with subcategories. It also contains information regarding the software which fulfill multiple compliance requirements of NIST cybersecurity framework. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes NIST Cybersecurity Framework With Subcategories. Dispense information and present a thorough explanation of Response Planning, Communications, Mitigation, Detection Process, Security Continuous Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
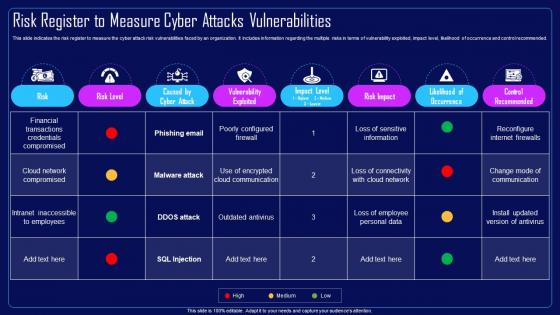
This slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cloud Network Compromised, Financial Transactions, Credentials Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.

The slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Risk Mitigation Plan, Multiple Cyber Attacks, Mitigation Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
Increase audience engagement and knowledge by dispensing information using Agenda For Action Plan To Combat Cyber Crimes Ppt Icon Example Introduction. This template helps you present information on five stages. You can also present information on Cybersecurity Risk Assessment, Program For Organization, Cyber Attacks, Program On Attacks Frequency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
Introducing our well researched set of slides titled Icons Slide For Action Plan To Combat Cyber Crimes Ppt Icon Example Topics. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
Introducing Table Of Contents For Action Plan To Combat Cyber Crimes Ppt Icon File Formats to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks Faced By Organization, Cyber Attacks Risk Assessment, Cyber Attacks Identification, Cyber Attacks Risk Mitigation, using this template. Grab it now to reap its full benefits.

This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Present the topic in a bit more detail with this Chatbot Using Gpt 3 How Chatgpt Can Help In Preventing Cyber Crimes Use it as a tool for discussion and navigation on Threat Intelligence, Anomaly Detection This template is free to edit as deemed fit for your organization. Therefore download it now.
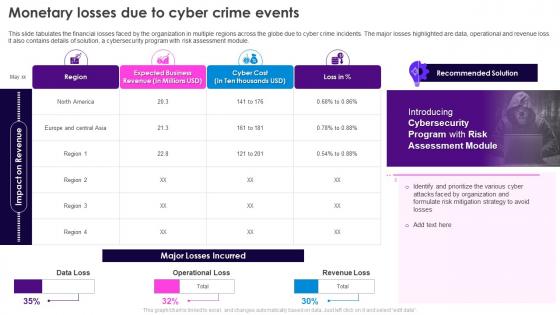
This slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Monetary Losses Due To Cyber Crime Events. Use it as a tool for discussion and navigation on Financial Losses, Multiple Regions Across, Cyber Crime Incidents, Operational And Revenue Loss, Cybersecurity Program, Risk Assessment Module. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Deliver an outstanding presentation on the topic using this How ChatGPT V2 Can Help In Preventing Cyber Crimes. Dispense information and present a thorough explanation of Threat Intelligence, Predictive Analytics, Anomaly Detection, Malware Detection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
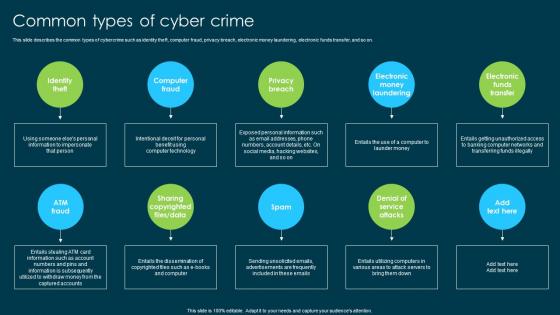
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Introducing Ethical Hacking And Network Security Common Types Of Cyber Crime to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Electronic Money Laundering, Electronic Funds Transfer, Denial Of Service Attacks, Sharing Copyrighted Files Or Data, using this template. Grab it now to reap its full benefits.

Presenting pptx cyber terrorism cyber crime ppt background. This is a cyber terrorism cyber crime ppt background. This is a five stage process. The stages in this process are security threats, cyber terrorism, cyber espionage, cyber war, cyber line.
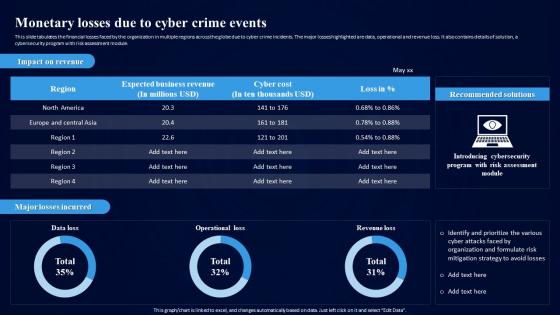
This slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Monetary Losses Due To Cyber Crime Events. Use it as a tool for discussion and navigation on Monetary Losses Due, Cyber Crime Events, Mitigation Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
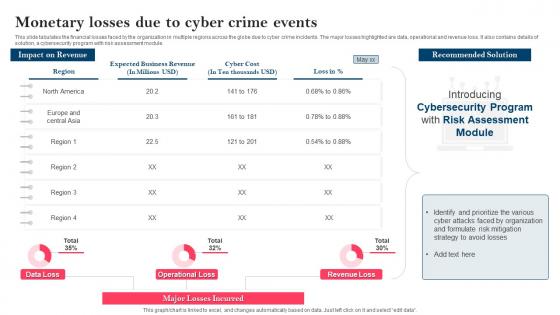
This slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Monetary Losses Due To Cyber Crime Events. Dispense information and present a thorough explanation of Monetary Losses, Recommended Solution, Cybersecurity Program, Risk Assessment Module using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
Give your next presentation a sophisticated, yet modern look with this 100 percent editable Spoofing and cyber crime colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
Make your presentation profoundly eye-catching leveraging our easily customizable Spoofing and cyber crime monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
Give your next presentation a sophisticated, yet modern look with this 100 percent editable Sybil attack and cyber crime colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
Make your presentation profoundly eye-catching leveraging our easily customizable Sybil attack and cyber crime monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
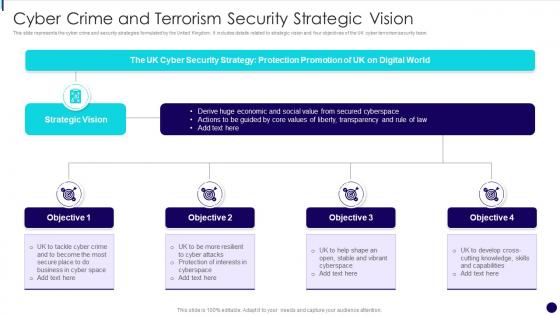
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team. Introducing our premium set of slides with name Cyber Crime And Terrorism Security Strategic Vision. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategic Vision, Protection Promotion, Protection Of Interests In Cyberspace. So download instantly and tailor it with your information.
Presenting our set of slides with name Cyber Crime And Terrorism Strategies Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Crime And Terrorism Strategies Icon.
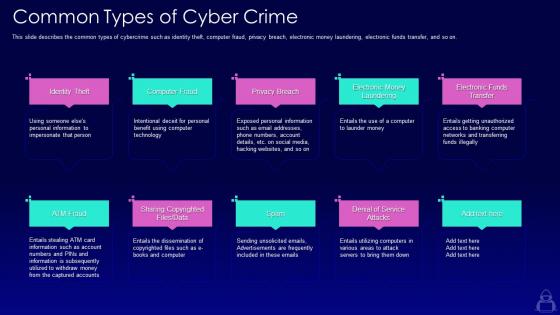
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Increase audience engagement and knowledge by dispensing information using Common Types Of Cyber Crime Ppt Powerpoint Presentation Professional Example File. This template helps you present information on ten stages. You can also present information on Identity Theft, Computer Fraud, Privacy Breach, ATM Fraud, Spam using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

Presenting Cyber Crime Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Crime Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
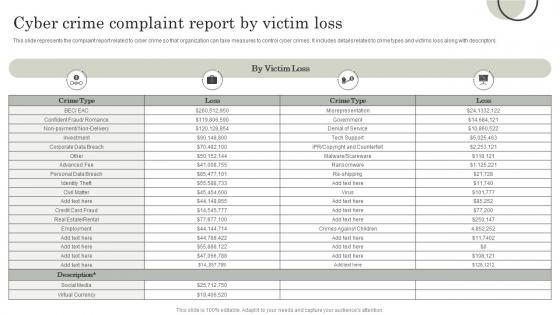
This slide represents the complaint report related to cyber crime so that organization can take measures to control cyber crimes. It includes details related to crime types and victims loss along with descriptors. Presenting our well structured Cyber Crime Complaint Report By Victim Loss. The topics discussed in this slide are Cyber Crime, Complaint Report, Victim Loss. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.

This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Present the topic in a bit more detail with this How Chatgpt Can Help In Preventing Cyber Crimes. Use it as a tool for discussion and navigation on Threat Intelligence, Predictive Analytics, Chatbot Based Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
Presenting Cyber Crime Banking Sector In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Crime Banking Sector. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Introducing our Icon Showcasing Digital Safety From Cyber Crime set of slides. The topics discussed in these slides are Digital Safety, Cyber Crime. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
Presenting Cyber Crime Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Crime Examples. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
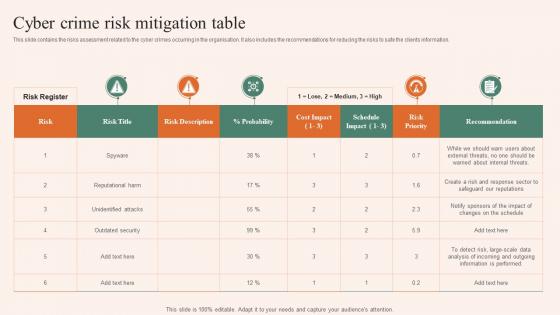
This slide contains the risks assessment related to the cyber crimes occurring in the organisation. It also includes the recommendations for reducing the risks to safe the clients information. Introducing our Cyber Crime Risk Mitigation Table set of slides. The topics discussed in these slides are Cyber Crime, Risk Mitigation, Table. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.

This slide demonstrates the various uses of ChatGPT in medical industry. The purpose of this slide is to explain how ChatGPT can help in the growth of medical field. These are medical diagnosis, virtual assistance, medical research and education, etc. Present the topic in a bit more detail with this How ChatGPT Can Help Preventing Cyber Crimes Applications Of ChatGPT In Different Sectors. Use it as a tool for discussion and navigation on Medical Diagnosis, Virtual Assistance, Medical Research. This template is free to edit as deemed fit for your organization. Therefore download it now.

Presenting History Cyber Crime Timeline In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like History Cyber Crime Timeline. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting our Cyber Crime Impact Business In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Crime Impact Business This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
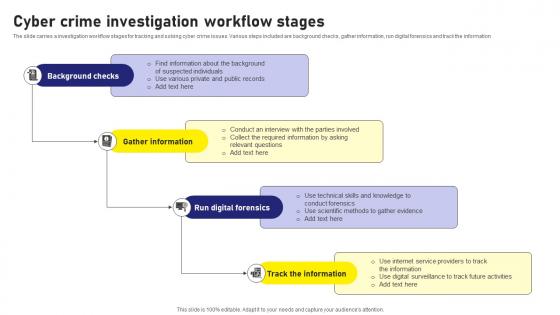
The slide carries a investigation workflow stages for tracking and solving cyber crime issues. Various steps included are background checks, gather information, run digital forensics and track the information Introducing our premium set of slides with Cyber Crime Investigation Workflow Stages. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Investigation, Crime, Workflow. So download instantly and tailor it with your information.
Presenting Cyber Crimes Against Individuals In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Crimes Against Individuals. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Types Cyber Crime Example In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Cyber Crime Example. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.

This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Deliver an outstanding presentation on the topic using this How Chatgpt Can Help In Preventing Cyber Crimes Open Ai Language Model It. Dispense information and present a thorough explanation of Threat Intelligence, Anomaly Detection, Predictive Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc.Present the topic in a bit more detail with this How ChatGPT Can Help In Preventing Cyber Crimes Regenerative Ai. Use it as a tool for discussion and navigation on Predictive Analytics, Threat Intelligence, Anomaly Detection. This template is free to edit as deemed fit for your organization. Therefore download it now.
Presenting our Cyber Enabled Crime In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Enabled Crime This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.

Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

presentation on cyber crimes-slides

Related Papers
Faruk Ahmmed
Nadia Khadam
Ramandeep Kaur
IRJET Journal
Amnah Rashid
Prasad Pednekar
Bhartiya Shodh
Crime, in whatever forms it is, directly or indirectly, always affects the society. In today’s world, there is immense increase in the use of Internet in every field of the society and due to this increase in usage of Internet, a number of new crimes have evolved. Such crimes where use of computers coupled with the use of Internet is involved are broadly termed as Cyber Crimes.
Pauline Reich
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Mustafa Ally
Omar Diagne
ABRAHAM BLANQUET
Journal of Materials Processing Technology
Tatsuhiko Aizawa
Steven Duplij
Ivanir Maciel
Revista Brasileira de Geriatria e Gerontologia
Antonia Oliveira Silva
KHAIRIL NIZAM MOHAMAD DARUS
Antonio Maia Goncalves
International Journal of Simulation: Systems, Science & Technology
Zikri Baharudin
Information Technologies and Learning Tools
Alfie Arcelo
Bioscience Biotechnology Research Communications
Priyanka Kashyap
Pfl�gers Archiv European Journal of Physiology
Journal of The Royal Society Interface
Bayerisches Jahrbuch für Volkskunde
Elisabeth Luggauer
Sustainability
Abdelaziz El Shinawi
Empiria. Revista de metodología de ciencias sociales
Javier Serra Callejo
Asian Journal of Oncology
Kaustav Chatterjee
Gopiya Naik S.
International Journal for Research in Applied Science and Engineering Technology
Nisy Prasad
Physical Review B
Kyung Kiu Kim
JOURNAL OF REHABILITATION- …
Heather Becker
International Journal of Systematic Bacteriology
george poinar
Fabrizio Frezza
Acta Horticulturae
Elina Coneva
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

49 templates

18 templates

32 templates

42 templates

40 templates

16 templates
Cybercrime Minitheme
Cybercrime minitheme presentation, free google slides theme and powerpoint template.
We spend many hours in front of the computer screen, browsing the net, so we have to be careful with our eyes, to avoid straining them too much... but we also have to be careful with cybercrime! Educate your audience on the various types of phishing and hacking! To do so, customize this template and fill it with your own informative content. We've used backgrounds with gradients, some linear icons and some photos of masked hackers (they're just models, not actual hackers!).
Features of this template
- 100% editable and easy to modify
- 21 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the free resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access

Register for free and start editing online

Cyber Crime & Investigation
Jul 26, 2014
1.1k likes | 2.25k Views
Cyber Crime & Investigation. Presented by: Arnel C. Reyes IT Security Consultant. Fast Growth of Cyber Crime. Converged Telecom and Information Technologies Frequent Transnational Communication Highly Organized and Globalized Management of Crime Rings
Share Presentation
- locate network route hard
- related targets
- cross check
- large volume
- new converged ict technologies

Presentation Transcript
Cyber Crime & Investigation Presented by: Arnel C. Reyes IT Security Consultant
Fast Growth of Cyber Crime Converged Telecom and Information Technologies Frequent Transnational Communication Highly Organized and Globalized Management of Crime Rings Ineffective Investigation with Joint Effort of Multi-countries
Globalized Cyber Crime Where is the swindler? Cloud Computing = Network Computing Through Internet, computers can cooperate with each other, or services are available more far-reaching...
Globalized Cyber Crime Source: http://www.darkgovernment.com/news/fbi-warning-cyber-threat-bigger-than-ever
Common Cyber Crime Features Internet as primary criminal tools, places, or targets New Converged ICT Technologies High technical skill at all online and network services Predict and profile the characteristics of unknown criminal subjects or offenders
Investigation on Criminals e-Positioning Tracking Monitoring Lawful Intercept Victim & Witness Interview Interrogation Database Lookup Warrant & Confiscation Traditional investigation on criminals is commonly applied in cyber crime events quite often.
Difficulties of Investigation How to Identify Criminal Hard to Conduct Analysis of Large Volume of Data Hard to Track Transnational Communication Hard to Maintain Integrity of Data Hard to Locate Network Route Hard to Identify Anonymity or Dummy Account
Different Investigation Processes
Process Flow for Cyber Investigation Follow-up investigation on related targets & evidence and hunting for clues from other members to combat all gangsters Clues, informer, case claim, daily crime information collection and integration, sourcing Study primary data, cross check databases in Police Department, Google on Internet and confirm crime type in order to prepare investigation Arrest all suspects, confiscate all evidences, check all computers, telephone record, booking record etc... Phone record, lawful intercept, tracking, location positioning, knowledge of crime organization and members
e-Detective Tactical Server Best Tactical Solution for: Network Protocol Decoding and Content Reconstruction Auditing and Record Keeping with ISO 27001, SOX, HIPPA etc… Internet Surveillance/Monitoring & Network Behavior Recording Forensics Analysis and Cyber Investigation Internet Surveillance and Forensics Analysis System
Lawful Interception Solution
Corporate Interception Solution
INTERNET HTTPS/SSL Interception Solution Web/Mail Server HTTPS/SSL 2 Gateway Router HTTPS MITM (ED2S) L3 Core Switch (Re-routing Function) Targeted Users HTTPS traffic needs to be routed or redirected to this MITM system. 1 Target Users
e-Detective is Easy to Operate Just use IE Browser login system from local or remote Uses https protocol for security protection Multi password, user’s name and User’s Group for system login control
e-Detective: Homepage
e-Detective: Email – POP3/SMTP/IMAP
e-Detective: Web Mail (Read)
e-Detective: Web Mail (Sent)
e-Detective: IM/Chat - Yahoo
e-Detective: File Transfer - FTP
e-Detective: File Transfer – P2P
e-Detective: HTTP – Link/Content
e-Detective: HTTP Upload/Download
e-Detective: HTTP Video Stream
e-Detective: Search – Condition/Parameter
e-Detective: Search – Association/Relation
e-Detective: Backup Storage External Storage (SAN/NAS/CD/DVD) for preserving digital assets & for future recovery of DATA (Backup CD Reader SW is provided)
Who Needs e-Detective? Types Of Companies Need E-Detective Aside from Government Companies that install E-Detective as a Deterrent, will inform their staffs that Internet activities are being fully monitored. Financial, Banking and Investment Companies such as derivatives, futures, etc. All transactions to be monitored. Companies like marketing, design house, high technologies, which critically need to prevent leakage of data. Staffs communicate with customers or vendors through web-based system need E-Detective to archive data.
Crackdown on Fraud Rings Europe US China Taiwan Vietnam Philippines Thailand Malaysia Indonesia Africa
Network Forensics and Lawful Interception E-Detective Wireless-Detective E-Detective Decoding Centre Enterprise Data Guard System E-Detective LEMF Centralized Management System Data Retention Management System HTTPS/SSL Interceptor VoIP Detective FIT (Forensics Investigation Toolkit) NIT (Network Investigation Toolkit) Network Packet Forensic Analysis Training National Security Surveillance Training Cyber Crime Investigation Training DECISION GROUP INC.
Thank you!!! I hope you find it informative… Email Me @ [email protected] Visit our website @ www.tasaheelglobal.com
- More by User
Cyber Crime
Cyber Crime. Chapter 7. BUSINESS LAW TODAY Essentials 9 th Ed. Roger LeRoy Miller - Institute for University Studies, Arlington, Texas Gaylord A. Jentz - University of Texas at Austin, Emeritus. Learning Objectives . What distinguishes cyber crime from “traditional” crime?
119 views • 11 slides

Cyber Crime. By: Benjamin Lewis, Alex Lesko , Patricia Di Pietro , & Gabbrielle Cadieux. Types of Cyber Crime. Targets Computers: Malware Viruses Code Hacking Spam Vandalism. Uses Computers ID Theft Internet Scams Cyber Stalking/Harassment/Child Pornography Fraud Drug Trafficking
357 views • 5 slides

Cyber Crime I
2. Roles of Computers. Crimes directed against a computerCrimes where the computer contains evidenceCrimes where the computer is used to commit the crime. 3. Searching and Seizing by the Organization that Owns the Computer. May be governed by the Electronic Communications Privacy Act and other pri
375 views • 19 slides

2. What You Can Expect in this Course. We will cover the following topicsCyber crime and information warfareTechnical aspects of cyber crimeInvestigation techniquesLegal issuesHost and server investigationsComputer forensicsWireless networksYou will be graded onResearch project 20%Class
553 views • 34 slides

2. Internet Terms. BackboneA high-speed line or series of connections that forms a major pathway within a network BandwidthHow much stuff you can send through a connection. Usually measured in bits-per-second. A full page of English text is about 16,000 bits. ByteA set of Bits that represent a
452 views • 30 slides

Cyber-crime
Cyber-crime Science. 2. Crime. Behaviour commonly considered harmful to individuals and/or society, against:persons (e.g. rape, assault, murder, suicide)property (e.g. fraud, arson, theft, vandalism)the state (e.g. riot, treason, sabotage, terrorism)morality (e.g. gambling, drugs, obscenity)Dis
460 views • 26 slides

Cyber Crime. MSIT 458: Information Security & Assurance By Curtis Pethley. Selection. Selecting a Firewall. There are 6 General Steps Identify your topology, applications, and protocol needs. Analyze trust relationships within your organization.
480 views • 21 slides

Cyber Crime. What is Cyber Crime?. Cyber crime has become a serious threat to anyone who especially use Internet. Steal personal data Hack into computer Identify fraud Pornography Terrorism embezzlement Theft stalking. Privacy OR Security ?.
456 views • 7 slides

Crime Scene Investigation
Crime Scene Investigation. Forensic Science Mr. Glatt 2013-14. Crime Scene Team. Police Officers (First Responders) Usually first at scene Secure Scene District Attorney (possibly) Sometimes present to determine if a search warrant is needed for crime-scene investigators
1.16k views • 16 slides

Cyber Crime & Cyber Terrorism
Cyber Crime & Cyber Terrorism. Dr Richard Overill Department of Informatics King’s College London [email protected] www.inf.kcl.ac.uk/staff/richard/. Terminology. Cyber prefix – involving the Internet or other wide area digital networks and networked systems.
459 views • 15 slides

Cyber-crime Science
Cyber-crime Science. Pieter Hartel Elmer Lastdrager. The Course. Goals Study cybercrime from a social perspective Organisation Teams of 2-3 Do an experiment Write a paper Review each other’s papers Present your paper at a conference http://www.ewi.utwente.nl/~pieter/CCS/. Team.
329 views • 20 slides

Cyber Crime: Cyber-Bullying
Kaitlyn Deutsch Jordan Wright Becky Thompson Joe Yosten. Cyber Crime: Cyber-Bullying. Definitions. Wikipedia “Involves the use of information and communication technology to support deliberate, repeated, and hostile behavior by an individual or group that is intended to harm others.”.
967 views • 27 slides

Crime Scene Investigation. Crime Scene Investigators: Alex Linton, Dhruv Mathur, Alex Abraham. Problem.
351 views • 12 slides

CYBER CRIME
CYBER CRIME. Cyber crime. is a CRIMINAL activity done using COMPUTERS and INTERNET. Cyber crime basically are committed against individuals or groups of individuals with a CRIMINAL MOTIVE
611 views • 21 slides

CYBER CRIME. e-rule e-safety e-care. PREPARED BY: CA 11132 KANGESWARY A/P KUPPUSAMY KE 11058 SHOBANA A/P SINNIAH. E-RULE. E-SAFETY. Internet threats can come in various forms or attacks. The Internet can create the illusion that strangers are actually “friends”.
397 views • 7 slides

Cyber Crime. Statistics. The 2000 Computer Security Institute/FBI Computer Crime and Security Survey Ninety percent of the study's 585 respondents reported computer security breaches within the last twelve months
203 views • 6 slides
STAY SAFE ONLINE. Cyber Crime. What is Cyber Crime?. Cyber Crime is an online or Internet-based illegal act. Bahayanya Cyber Crime…. Types of Cyber Crime. Types of Cyber Crime. Nak buat macamana ni..?. How To Prevent Cyber Crime. Protect Your Personal Information.
816 views • 9 slides

CYBER CRIME. What is computer crime?. Computer crime refers to any crime that involves a computer and a network . The computer may have been used in the commission of a crime.
396 views • 16 slides
STAY SAFE ONLINE. Cyber Crime. What is Cyber Crime?. Cyber Crime is an online or Internet-based illegal act. Why Are System Vulnerable?. Contemporary Security Challenges and Vulnerabilities. Cyber Crime Trends. Criminal Gangs. Criminal Organizations. Friends. Lone Ranger.
690 views • 16 slides

Crime Scene Investigation. You are about to apply skills of prediction, questioning and inference to a series of clues that can be found within a crime story. You will need to put your detective hats on to solve the mystery of a murder. . Firstly, consider the difference between
536 views • 10 slides

CYBER CRIME. WHAT IS CYBER CRIME???. Also known a computer crime, digital crime , e-crime, and electronic crime.
674 views • 13 slides


Crime and Cyber-crime
Crime and Cyber-crime. Pieter Hartel. Crime. Acts or missions forbidden by law that can be punished […] , against: persons (e.g. rape, assault, murder, suicide) property (e.g. fraud, arson, theft, vandalism) the state (e.g. riot, treason, sabotage, terrorism)
511 views • 18 slides
Home PowerPoint Templates Shapes Cyber Crime PowerPoint Template
Cyber Crime PowerPoint Template

The Cyber Crime PowerPoint Template is a collection of multiple slide designs to present various cybercrime concepts. The SlideModel premium catalog contains several more cyber security and online hacking PowerPoint templates. For example, Cyber Security Shapes PowerPoint and Cyber Technology Template . This template of cybercrime includes PowerPoint diagrams and shapes that are ideal of reporting presentations. There are 6 slides of modern shapes and clipart to complement concept diagrams and reports. Such as hackers on desktop screens with currency and biometric prints to illustrate identity theft. Similarly, the template presents a danger symbol of skull and bones using to visualize cyber threats.
The cyber security has become an international issue in last decay. Because it is costing businesses and individuals billion dollars globally. Apart from financial losses, online crimes have social effects such as hate speech, bullying, inflicting emotional harm, etc. The slides of cybercrime concepts could help present complex topics about internet world that affect people worldwide.
The Cyber Crime PowerPoint Template provides a visual illustration of data breach, unauthorized access, and other online crimes. Therefore, this PowerPoint template is a good start of technology and cyber security. All the slides of cybercrime template are fully editable shapes and clipart in blue and gray color theme. The users can apply various colors or change its theme completely with simple PowerPoint features.
You must be logged in to download this file.
Favorite Add to Collection
Details (6 slides)

Supported Versions:
Subscribe today and get immediate access to download our PowerPoint templates.
Related PowerPoint Templates
Value Chain Analysis PowerPoint Template
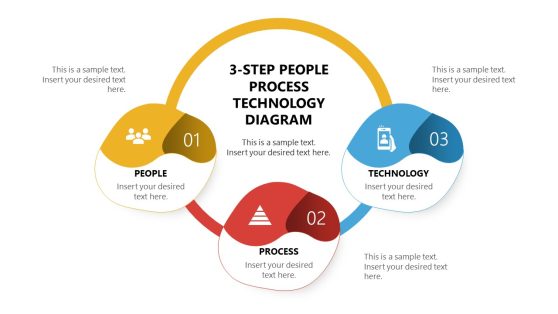
3-Step People Process Technology Diagram Template for PowerPoint
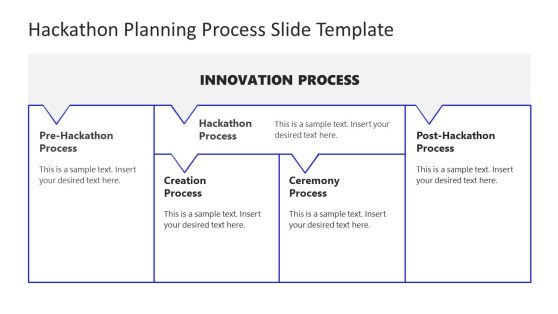
Hackathon Planning Process PowerPoint Template
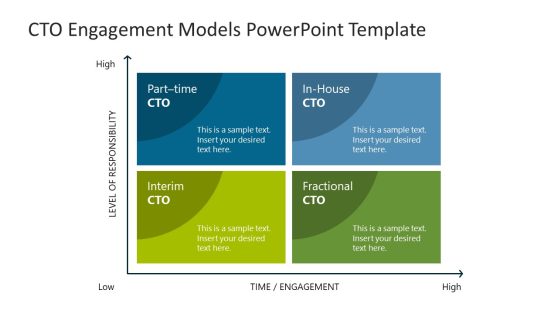
CTO Engagement Models PowerPoint Template
Home Collections Technology Cyber Security Cyber Crime PPT Presentation
Cyber Crime PPT Presentation Template and Google Slides
Amazing Animated Modern Cyber Crime PPT presentation Slide
About the template:, features of this template:.
- 100 % customizable slides and easy to download.
- Slides available in different nodes & colors.
- The slide contained in 16:9 and 4:3 format.
- Easy to change the slide colors quickly.
- Well-crafted template with instant download facility.
- The clear layout of this template will help you to design a professional-looking presentation.
- The multi-color visuals of this slide will make your presentation eye-catching.
- cyber security
- Cyber Security
- Cyber Security Threats
- Cyber Security Risks
- Cyber Security Infographics
- Cyber Security Agency
- Cyber Security Strategy
- Google Slides
325+ Templates

1590+ Templates
Artificial Intelligence
212+ Templates
134+ Templates

48+ Templates
Cloud computing
186+ Templates
Cyber security
258+ Templates
Mobile Phones
221+ Templates
26+ Templates
66+ Templates
You May Also Like These PowerPoint Templates

- Preferences

Cyber Crime - PowerPoint PPT Presentation

Cyber Crime
Cyber crime is the crime that which have a computer or internet. – powerpoint ppt presentation.
- Cyber Crime is the crime
- that have a computer, a
- network or network
- devices. These types of
- crimes include viruses and
- DOS (denial-of-service)
- Crimes thats use computer
- network to progression criminal activities.
- It can be classified into four major categories as
- Cyber crime against individual
- Cyber crime against property
- Cyber crime against organization
- Cyber crime against society
- Email spoofing It is one in which email header is forget so that pass to originate one source but actually sent another source.
- Spamming it means send multiple copies of unsolicited mails.
- Cyber Defamation it occur when defamation take place with the help of computers or internet.
- Harassment and Cyber stalking it means following moves of an individuals activity over the internet.
- Credit card fraud
- Intellectual property
- crimes These include
- Software piracy
- Copyright infringement
- Trademarks violations
- Theft of computer source Code
- III. Internet time theft it usage internet hours by unauthorized person which is actually paid by another person.
- Unauthorized Accessing of computer
- Denial of service
- Virus Attack
- Trojan Horse
- Email Bombing
- Salami Attack
- Data diddling
- Forgery currency notes, marks-sheets and stamps etc can be forged by computers and high quality Scanner and printer.
- Cyber Terrorism Use of computer resources to intimidate pr coerce others.
- Web Jacking Hackers gain access or control over the websites of another,
- Cyber bullying
- Cyber stalking
- Virus dissemination
- Cyber Security is the
- potential activity by
- which information and
- other communications
- systems are protected
- from against unauthorized
- use or modifications or even theft.
- Keep your operating system and all system software updated regularly.
- Do proper password management
- keep antivirus software updated regularly
- Use firewall and other security software
- Avoid untrusted Wi-Fi connections
- Have data backup , update it regularly
- Avoid surfing untrusted websites.
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.


An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Fact Sheets
Fact Sheet: How DHS is Combating Child Exploitation and Abuse
Every day, the Department of Homeland Security (DHS) leads the fight against child exploitation and abuse. As part of the Department’s mission to combat crimes of exploitation and protect victims, we investigate these abhorrent crimes, spread awareness, collaborate with interagency and international partners, and expand our reach to ensure children are safe and protected.
DHS battles child exploitation and abuse using all available tools and resources department-wide, emphasizing its commitment in April 2023 by adding “Combat Crimes of Exploitation and Protect Victims” as its sixth core mission.
As part of the Department’s ongoing work on this mission, today DHS is announcing Know2Protect, the U.S. government’s first prevention and awareness campaign to combat online child sexual exploitation and abuse. In recognition of April’s Child Abuse Prevention Month, DHS is committed to raising awareness, preventing child exploitation and abuse, and bringing perpetrators to justice.
Between October 2022 and April 2024, DHS:
- Expanded and unified the Department’s focus on combating cybercrimes by redesignating the HSI Cyber Crimes Center as the DHS Cyber Crimes Center to enhance coordination across all DHS agencies and offices to combat cyber-related crimes and further the Department’s mission to combat online child sexual exploitation and abuse (CSEA).
- The Blue Campaign, now part of the DHS Center for Countering Human Trafficking, increased national partnerships from 43 in FY22 to 64 in FY23. The campaign hosted 194 national trainings on the indicators of human trafficking and how to report these crimes with over 19,000 participants from the federal government, non-governmental organizations, law enforcement, and the general public. In April 2024, Blue Campaign announced a partnership with rideshare company Lyft to train their drivers, who interact with millions of riders per year, on how to recognize and report human trafficking. Read more accomplishments in the DHS Center for Countering Human Trafficking’s FY 2023 Annual Report .
- Identified and/or assisted 2,621 child victims of exploitation through the work of Homeland Security Investigations and made more than 6,100 arrests for crimes involving the sexual exploitation of children. Learn more in Immigration and Customs Enforcement (ICE) ’s FY2023 Annual Report .
- Joined the Biden-Harris Administration and interagency partners to collaborate on actions to keep children and teens safe as part of the Kids Online Health and Safety Task Force and the White House Online Harassment and Abuse Task Force.
- Tasked the Department’s external advisory bodies, including the Homeland Security Advisory Council , the Homeland Security Academic Partnership Council , and the Faith-Based Security Advisory Council , to each form a subcommittee to review DHS efforts to combat online child sexual exploitation and abuse. In the coming months, they will share their findings, which will help inform the Department’s future efforts to tackle these issues.
- Began implementing a trauma-informed and victim and survivor-centered multidisciplinary workplan through the Joint Council on Combating Child Sexual Exploitation, established by President Biden and Australian Prime Minister Albanese. The Council, co-chaired by Secretary Alejandro N. Mayorkas, is focused on building the capacity of countries in the Indo-Pacific region to combat this crime; jointly developing policy recommendations to tackle the issue; conducting joint investigations and operations; sharing research and development efforts; preventing victimization through education and awareness campaigns; and safety-by-design.
To accomplish this work, DHS coordinates with law enforcement at home and abroad to enforce and uphold our laws, protects victims with a victim-centered approach that prioritizes respect and understanding, and works to stop this heinous crime through public education and outreach.
Enforcing Our Laws
DHS works with domestic and international partners to enforce and uphold the laws that protect children from abuse. The Department works collaboratively with the Department of Justice, the FBI, U.S Marshals, Interpol, Europol, and international law enforcement partners to arrest and prosecute perpetrators.
- Increased U.S. government and law enforcement efforts to combat financial sextortion – a crime targeting children and teens by coercing them into sending explicit images online and extorting them for money. In the past two years HSI received 4500 sextortion tips from Cote d’Ivoire and 665 children have been identified and supported by HSI. Learn more about the crime of sextortion .
- Helped deny more than 1,400 convicted, registered U.S. child sex offenders entry to foreign countries through travel notifications sent by the HSI Angel Watch Center. These efforts build international cooperation to ensure all countries are safe from predators.
- Partnered with 61 regional Internet Crimes Against Children Task Forces to investigate people involved in the online victimization of children, including those who produce, receive, distribute and/or possess child sexual abuse material, or who engage in online sexual enticement of children.
- Researched and developed modern tools and technologies that equip domestic and international law enforcement partners with advanced forensic capabilities to accomplish their mission to identify victims and apprehend child sexual abusers. For example, DHS’s Science and Technology Directorate developed the StreamView application to help law enforcement more efficiently address child exploitation cases by helping investigators aggregate, organize, and analyze investigative leads to identify the location of a crime, the victim, and bring the perpetrator to justice. Since May 2023, StreamView has led to the rescue of 68 victims, 47 arrests, eight life sentences, and dismantled eight trafficking networks having up to one million registered users.
- The U.S. Secret Service provides forensic and technical assistance to the National Center for Missing and Exploited Children (NCMEC) and state/local law enforcement in cases involving missing and exploited children.
- U.S. Customs and Border Protection screens all unaccompanied children and other arriving minors for indicators of abuse or exploitation, human trafficking, and other crimes, and all suspected criminal cases are referred to HSI.
Protecting and Supporting Victims
DHS incorporates a victim-centered approach into all Department programs, policies, and operations that involve victims of crime. This effort seeks to minimize additional trauma, mitigate undue penalization, and provide needed stability and support to victims.
HSI’s “ Operation Renewed Hope ” mission in July 2023 resulted in the generation of 311 probable identifications of previously unknown victims, including 94 positive contacts and several confirmed victim rescues from active abuse due to their locations being discovered through materials uncovered during the investigations. The investigation also led to the identification of perpetrators of child sexual abuse material. HSI completed “ Operation Renewed Hope II ” in Spring 2024, which resulted in the generation of 414 probable identifications of previously unknown victims, and positive identification of 30 previously unknown child sexual abuse victims, which included 8 victims rescued from active abuse.
- Once victims of child exploitation are identified and/or rescued, the HSI Victim Assistance Program (VAP) supports them and their non-offending caretaker(s) by using highly trained forensic interview specialists to conduct victim-centered and trauma-informed forensic interviews. In addition, VAP’s victim assistance specialists provide other resources to victims such as crisis intervention, referrals for short and long term medical and/or mental health care, and contact information for local social service programs for young victims, and agencies to assist in the healing process.
- The Center for Countering Human Trafficking hosted its second annual virtual DHS Human Trafficking Seminar for DHS employees who are part of the Department’s mission to end human trafficking or are interested in this work. Over 900 employees from across the Department attended to learn more about DHS’s work and victim-centered approach to combating this crime.
- HSI provides short-term immigration protections to human trafficking victims , including victims of child sex trafficking. U.S. Citizen and Immigration Services (USCIS) provides victim-based or humanitarian-related immigration benefits to child victims of human trafficking, abuse, and neglect, including Special Immigration Juvenile (SIJ) classification, T visa, U visa, and VAWA immigrant classification.
Educating and Increasing Public Awareness
An integral part of this work is educating and expanding public awareness to help prevent this crime and hold perpetrators accountable. DHS does this important work every day.
- Trained more than 2,000 law enforcement officials and child advocacy personnel throughout the country to enhance their counter-child exploitation tactics.
- Educated over 186,000 kids, teens, parents, and teachers about internet safety and how to stay safe from sexual predators through the iGuardian program. DHS recently revamped Project iGuardian materials and using those materials, HSI has trained 419 special agents and completed presentations across 32 states and 8 countries. Presentations target kids aged 10 and up and their trusted guardians and focus on sharing information about the dangers of online environments, how to stay safe online, and how to report abuse and suspicious activity.
- USSS Childhood Smart Program Ambassadors educated more than 112,000 children, parents, and teachers across 31 states and the District of Columbia about how to prevent online sexual exploitation and child abduction. The Childhood Smart Program provides age-appropriate presentations to children as young as five as well as to adults. Presentations focus on internet and personal safety as well as other topics such as social media etiquette and cyber bullying.
- The HSI Human Rights Violations and War Crimes Center trained over 955 individuals across the interagency on female genital mutilation or cutting, a severe form of child abuse under federal law when done to individuals under the age of 18.
- The DHS Blue Campaign Blue Lighting Initiative, part of the Center for Countering Human Trafficking, trained over 260,000 aviation personnel to identify potential traffickers and human trafficking victims and report their suspicions to law enforcement in FY 2023. The Initiative added 31 new partners this past year, raising its total partners to 136 aviation industry organizations, including its first two official international partners.
- The Cybersecurity and Infrastructure Security Agency administers SchoolSafety.gov, an interagency website that includes information, guidance and resources on a range of school safety topics. SchoolSafety.gov houses a child exploitation section and corresponding resources to help school communities identify, prevent and respond to child exploitation. Since its launch in January 2023, the SchoolSafety.gov child exploitation section has been viewed more than 17,380 times.
What You Can Do and Resources Available
- Project iGuardians™: Combating Child Predators
- Childhood Smart Program
- Visit SchoolSafety.gov for resources to help educators, school leaders, parents, and school personnel identify, prevent, and respond to child exploitation.
- Learn more about sextortion : it is more common than you think.
- Learn more from the National Center for Missing and Exploited Children .
How to report suspected online child sexual exploitation and abuse in the United States:
- Contact your local, state, campus, or tribal law enforcement officials directly. Call 911 in an emergency.
- If you suspect a child has been abducted or faces imminent danger, contact your local police and the NCMEC tip line at 1-800-THE-LOST (1-800-843-5678) .
- If you suspect a child might be a victim of online sexual exploitation, call the HSI Tip Line at 1-866-347-2423 and report it to NCMEC’s CyberTipline .
- Law Enforcement
- Child Exploitation
How Ukraine’s cyber police fights back against Russia’s hackers
Ukraine's cyber police talks crypto, ransomware and documenting war crimes after russia's invasion.

On February 24, 2022 , Russian forces invaded Ukraine. Since then, life in the country has changed for everyone.
For the Ukrainian forces who had to defend their country, for the regular citizens who had to withstand invading forces and constant shelling, and for the Cyberpolice of Ukraine, which had to shift its focus and priorities.
“Our responsibility changed after the full scale war started,” said Yevhenii Panchenko, the chief of division of the Cyberpolice Department of the National Police of Ukraine, during a talk on Tuesday in New York City. “New directives were put under our responsibility.”
During the talk at the Chainalysis LINKS conference, Panchenko said that the Cyberpolice is comprised of around a thousand employees, of which about forty track crypto-related crimes. The Cyberpolice’s responsibility is to combat “all manifestations of cyber crime in cyberspace,” said Panchenko. And after the war started, he said, “we were also responsible for the active struggle against the aggression in cyberspace.”
Panchenko sat down for a wide-ranging interview with TechCrunch on Wednesday, where he spoke about the Cyberpolice’s new responsibilities in wartime Ukraine. That includes tracking what war crimes Russian soldiers are committing in the country, which they sometimes post on social media; monitoring the flow of cryptocurrency funding the war; exposing disinformation campaigns; investigating ransomware attacks; and training citizens on good cybersecurity practices.
The following transcript has been edited for brevity and clarity.
TechCrunch: How did your job and that of the police change after the invasion?
It almost totally changed. Because we still have some regular tasks that we always do, we’re responsible for all the spheres of cyber investigation.
We needed to relocate some of our units in different places, of course, to some difficult organizations because now we need to work separately. And also we added some new tasks and new areas for us of responsibilities when the war started.
From the list of the new tasks that we have, we crave information about Russian soldiers. We never did that. We don’t have any experience before February 2022. And now we try to collect all the evidence that we have because they also adapted and started to hide, like their social media pages that we used for recognizing people who were taking part in the larger invading forces that Russians used to get our cities and kill our people.
Also, we are responsible for identifying and investigating the cases where Russian hackers do attacks against Ukraine. They attack our infrastructure, sometimes DDoS [distributed denial-of-service attacks], sometimes they make defacements, and also try to disrupt our information in general. So, it’s quite a different sphere.
Because we don’t have any cooperation with Russian law enforcement, that’s why it’s not easy to sometimes identify or search information about IP addresses or other things. We need to find new ways to cooperate on how to exchange data with our intelligence services.
Some units are also responsible for defending the critical infrastructure in the cyber sphere. It’s also an important task. And today, many attacks also target critical infrastructure. Not only missiles, but hackers also try to get the data and destroy some resources like electricity, and other things.
When we think about soldiers, we think about real world actions. But are there any crimes that Russian soldiers are committing online?
[Russia] uses social media to sometimes take pictures and publish them on the internet, as it was usual in the first stage of the war. When the war first started, probably for three or four months [Russian soldiers] published everything: videos and photos from the cities that were occupied temporarily. That was evidence that we collected.
And sometimes they also make videos when they shoot in a city, or use tanks or other vehicles with really big guns. There’s some evidence that they don’t choose the target, they just randomly shoot around. It’s the video that we also collected and included in investigations that our office is doing against the Russians.
In other words, looking for evidence of war crimes?
How has the ransomware landscape in Ukraine changed after the invasion?
It’s changed because Russia is now not only focused on the money side; their main target is to show citizens and probably some public sector that [Russia] is really effective and strong. If they have any access on a first level, they don’t deep dive, they just destroy the resources and try to deface just to show that they are really strong. They have really effective hackers and groups who are responsible for that. Now, we don’t have so many cases related to ransom, we have many cases related to disruption attacks. It has changed in that way.
Has it been more difficult to distinguish between pro-Russian criminals and Russian government hackers?
Really difficult, because they don’t like to look like a government structure or some units in the military. They always find a really fancy name like, I don’t know, ‘Fancy Bear’ again. They try to hide their real nature.
But we see that after the war started, their militaries and intelligence services started to organize groups — maybe they’re not so effective and not so professional as some groups that worked before the war started. But they organize the groups in a massive [scale]. They start from growing new partners, they give them some small tasks, then see if they are effective and truly succeed in a small portion of IT knowledge. Then they move forward and do some new tasks. Now we can see many of the applications they also publish on the internet about the results. Some are not related to what governments or intelligence groups did, but they publish that intelligence. They also use their own media resources to raise the impact of the attack.
What are pro-Russian hacking groups doing these days? What activities are they focused on? You mentioned critical infrastructure defacements; is there anything else that you’re tracking?
It starts from basic attacks like DDoS to destroy communications and try to destroy the channels that we use to communicate. Then, of course, defacements. Also, they collect data. Sometimes they publish that in open sources. And sometimes they probably collect but not use it in disruption, or in a way to show that they already have the access.
Sometimes we know about the situation when we prevent a crime, but also attacks. We have some signs of compromise that were probably used on one government, and then we share with others.
[Russia] also creates many psyops channels. Sometimes the attack did not succeed. And even if they don’t have any evidence, they’ll say “we have access to the system of military structures of Ukraine.”
How are you going after these hackers? Some are not inside the country, and some are inside the country.
That’s the worst thing that we have now, but it’s a situation that could change. We just need to collect all the evidence and also provide investigation as we can. And also, we inform other law enforcement agencies in countries who cooperate with us about the actors who we identify as part of the groups that committed attacks on Ukrainian territory or to our critical infrastructure.
Why is it important? Because if you talk about some regular soldier from the Russian army, he will probably never come to the European Union and other countries. But if we talk about some smart guys who already have a lot of knowledge in offensive hacking, he prefers to move to warmer places and not work from Russia. Because he could be recruited to the army, other things could happen. That’s why it’s so important to collect all evidence and all information about the person, then also prove that he was involved in some attacks and share that with our partners.
Also because you have a long memory, you can wait and maybe identify this hacker, where they are in Russia. You have all the information, and then when they are in Thailand or somewhere, then you can move in on them. You’re not in a rush necessarily?
They attack a lot of our civil infrastructure. That war crime has no time expiration. That’s why it’s so important. We can wait 10 years and then arrest him in Spain or other countries.
Who are the cyber volunteers doing and what is their role?
We don’t have many people today who are volunteers. But they are really smart people from around the world — the United States and the European Union. They also have some knowledge in IT, sometimes in blockchain analysis. They help us to provide analysis against the Russians, collect data about the wallets that they use for fundraising campaigns, and sometimes they also inform us about the new form or new group that the Russians create to coordinate their activities.
It’s important because we can’t cover all the things that are happening. Russia is a really big country, they have many groups, they have many people involved in the war. That type of cooperation with volunteers is really important now, especially because they also have a better knowledge of local languages.
Sometimes we have volunteers who are really close to Russian-speaking countries. That helps us understand what exactly they are doing. There is also a community of IT guys that’s also communicating with our volunteers directly. It’s important and we really like to invite other people to that activity. It’s not illegal or something like that. They just provide the information and they can tell us what they can do.
What about pro-Ukrainian hackers like the Ukraine IT Army . Do you just let them do what they want or are they also potential targets for investigation?
No, we don’t cooperate directly with them.
We have another project that also involves many subscribers. I also talked about it during my presentation: it’s called BRAMA . It’s a gateway and we coordinate and gather people. One thing that we propose is to block and destroy Russian propaganda and psyops on the internet. We have really been effective and have had really big results. We blocked more than 27,000 resources that belong to Russia. They publish their narratives, they publish many of psyops materials. And today, we also added some new functions in our community. We not only fight against propaganda, we also fight against fraud, because a lot of fraud today represented in the territory of Ukraine is also created by the Russians.
They also have a lot of impact with that, because if they launder and take money from our citizens, we could help. And that’s why we include those activities, so we proactively react to stories that we received from our citizens, from our partners about new types of fraud that could be happening on the internet.
And also we provide some training for our citizens about cyber hygiene and cybersecurity. It’s also important today because the Russians hackers not only target the critical infrastructure or government structures, they also try to get some data of our people.
For example, Telegram. Now it’s not a big problem but it’s a new challenge for us, because they first send interesting material, and ask people to communicate or interact with bots. On Telegram, you can create bots. And if you just type twice, they get access to your account, and change the number, change two-factor authentication, and you will lose your account.
Is fraud done to raise funds for the war?
Can you tell me more about Russian fundraising? Where are they doing it, and who is giving them money? Are they using the blockchain?
There are some benefits and also disadvantages that crypto could give them. First of all, [Russians] use crypto a lot. They create almost all kinds of wallets. It starts from Bitcoin to Monero. Now they understand that some types of crypto are really dangerous for them because many of the exchanges cooperate and also confiscate the funds that they collect to help their military.
How are you going after this type of fundraising?
If they use crypto, we label the addresses, we make some attribution. It’s our main goal. That’s also the type of activities that our volunteers help us to do. We are really effective at that. But if they use some banks, we only could collect the data and understand who exactly is responsible for that campaign. Sanctions are the only good way to do that.
What is cyber resistance?
Cyber resistance is the big challenge for us. We wanted to play that cyber resistance in cyberspace for our users, for our resources. First of all, if we talk about users, we start from training and also sharing some advice and knowledge with our citizens. The idea is how you could react to the attacks that are expected in the future.
How is the Russian government using crypto after the invasion?
Russia didn’t change everything in crypto. But they adapted because they saw that there were many sanctions. They create new ways to launder money to prevent attribution of the addresses that they used for their infrastructures, and to pay or receive funds. It’s really easy in crypto to create many addresses. Previously they didn’t do that as much, but now they use it often.

IMAGES
VIDEO
COMMENTS
This presentation covers the history, categories, types, threats, and security of cyber crime. It also explains the cyber law of India and some safety tips to prevent cyber crime.
Module 13 examines the types of crimes that are considered as cyber organized crime and the types of organized criminal groups that engage in cybercrime. This Module further explores the measures used to counter cyber organized crime. Module 14 examines topics, such as hacktivism, terrorism, espionage, disinformation
A presentation on cyber crime and security by Lipsita Behera, a B.Sc IST student at Ravenshaw University. It covers the definition, history, categories, types, prevention and safety tips of cyber crime.
Introduce your topic and host expert discussion sessions with this Cyber Crime Powerpoint Ppt Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template.
11. • This has become a major problem with people using the Internet for cash transactions and banking services. • In this cyber crime, a criminal accesses data about a person's bank account, credit cards, Social Security, debit card and other sensitive information to siphon money or to buy things online in the victim's name.
2. CYBER CRIME: THE INTRODUCTION In a digital age, where online communication has become the norm, internet users and governments face increased risks of becoming the targets of cyber attacks. As cyber criminals continue to develop and advance their techniques, they are also shifting their targets — focusing less on theft of financial information and more on business espionage and accessing ...
Different types of cyber crime. Cyber-dependent crimes - committed through communications, where the devices are both the tool for committing the crime, and the target of the crime. (National Cyber Security Strategy 2016-2021, 2016).Examples - Denial of Service (DDOS) attacks, Cyber-terrorists, Hacking and Disruption of Computer Functionality.
Prevent Cyber Crime Workshop Presentation . Technology . Premium Google Slides theme and PowerPoint template . Every day we do more and more things online: shopping, booking vacations, bank transactions, etc. Without a doubt, it makes things much easier for us and gives us convenience and flexibility, but the Internet is full of cybercriminals ...
Fascinate your viewers with our innovative Cyber Crime presentation template, designed for PowerPoint and Google Slides, and make an impact like never before! Utilize it to explain criminal misconduct, such as phishing and data theft, done on a company's network using the internet. You can further discuss the economic, reputational, and other ...
Types of Cyber crime. Cybercrime encompasses a range of illicit activities conducted in the digital realm. Some prevalent types include phishing, where deceptive emails or messages trick users into revealing sensitive information; ransomware attacks, during which malicious software encrypts data until a ransom is paid; identity theft, where ...
In today's world, there is immense increase in the use of Internet in every field of the society and due to this increase in usage of Internet, a number of new crimes have evolved. Such crimes where use of computers coupled with the use of Internet is involved are broadly termed as Cyber Crimes. Download Free PDF. View PDF. Cybercrime & Security.
Cyber Crime Awareness. Aug 09, 2014. 290 likes | 587 Views. Criminal Investigation and Detection Group. Cyber Crime Awareness. EFREN LAGAC FERNANDEZ II, GCTCP Police Chief Inspector Chief, Administrative Branch Chief, MIS/Forensic Sec, Investigation Branch Anti-Transnational Crime Division. Why learn about CYBER CRIME ?.
Free Google Slides theme and PowerPoint template. We spend many hours in front of the computer screen, browsing the net, so we have to be careful with our eyes, to avoid straining them too much... but we also have to be careful with cybercrime! Educate your audience on the various types of phishing and hacking! To do so, customize this template ...
Presentation Transcript. Cyber Crime & Investigation Presented by: Arnel C. Reyes IT Security Consultant. Fast Growth of Cyber Crime Converged Telecom and Information Technologies Frequent Transnational Communication Highly Organized and Globalized Management of Crime Rings Ineffective Investigation with Joint Effort of Multi-countries.
The Cyber Crime PowerPoint Template is a collection of multiple slide designs to present various cybercrime concepts. The SlideModel premium catalog contains several more cyber security and online hacking PowerPoint templates. For example, Cyber Security Shapes PowerPoint and Cyber Technology Template.This template of cybercrime includes PowerPoint diagrams and shapes that are ideal of ...
Learn about cybercrime, the use of a computer as an instrument to further illegal ends, such as fraud, child pornography, identity theft, or cyberterrorism. Explore the types, causes, and challenges of cybercrime, as well as the international treaties and laws to combat it.
The presentation includes sections on cyberbullying, cyber stalking, financial cyber crimes, cyber terrorism, selling illegal articles online, and software piracy. It is presented by 5 students and addresses topics like how these crimes are committed, examples of related crimes, prevention methods, and potential penalties.
With our templates you can create a high-quality presentation that will leave a lasting impression on your audience about Cyber Crime. The slide contained 16:9 and 4:3 format. It is easy to change the slide colors quickly. It is a well-crafted template with an instant download facility.
This cyber crime Ppt presentation has a huge space to add texts. This template's four corners are covered with text space and the center is covered with animated images of network related things and apps and a boy with a laptop. This animated image looks nice and it helps you in presenting an interesting presentation. Download Now!! Features of ...
Cyber Crime. Description: Cyber crime is the crime that which have a computer or internet. - PowerPoint PPT presentation. Number of Views: 52098. Slides: 13. Provided by: Parveen-Bala. Category: Medicine, Science & Technology.
Short Presentation On Cyber Crime And Security which includes Cyber crime introduction and types , Hacking and its types, different Threats , and in last Prevention for Hacks and Threats. Read more. Technology. 1 of 17. Download Now. Download to read offline. Cyber Crime And Security - Download as a PDF or view online for free.
Presentations focus on internet and personal safety as well as other topics such as social media etiquette and cyber bullying. The HSI Human Rights Violations and War Crimes Center trained over 955 individuals across the interagency on female genital mutilation or cutting, a severe form of child abuse under federal law when done to individuals ...
Apr 16, 2024 - 02:01 PM. Testifying April 16 before a House Energy and Commerce Subcommittee on Health hearing on addressing health care cybersecurity vulnerabilities in the wake of the Change Healthcare attack, AHA shared proposals and concerns for Congress and the Administration to consider. "To make meaningful progress in the war on ...
GroupSense is a cyber security firm that focuses on ransomware — a type of digital crime where businesses and other organizations have their digital information and systems held hostage.
Ukraine's cyber police talks crypto, ransomware and documenting war crimes after Russia's invasion Lorenzo Franceschi-Bicchierai 3 days On February 24, 2022 , Russian forces invaded Ukraine.
Learn about cybercrime, its definition, categories, methods, and importance of cyberlaws in this presentation by Anshuman Tripathi. Find out how to protect yourself and your system from cybercriminals and their activities.
And a Case Presentation on Transnational Repression. Tuesday, April 30, 2024 6:00 P.M. - 8:00 P.M. FBI Federal Building 600 Arch St., 2nd Fl, Conf. Rm. 2A Philadelphia, PA 19106. Please forward all RSVPs to [email protected]