- Information Security

Best online PhDs in cyber security for 2024

Cyber security is a fast-growing industry – and it looks like this trend is going to continue for the foreseeable future. With more organizations operating online, it has never been more important for employers to make IT security a number one priority.
If you’ve gained either a Bachelor’s or Master’s degree in cyber security and want to advance your career further, then an online PhD in cyber security may be a promising route to take. Most senior cyber security positions won’t require a PhD (for some, a Master’s might be the minimum). However, the skills and knowledge you gain through a PhD can give you an upper hand in the job market. Moreover, a cyber security PhD opens you up to job opportunities in academia.
The main advantage of an online cyber security PhD is the flexibility and convenience it offers. You might be unsure, however, of which school or degree to choose.
In this guide, we highlight some of the best online PhDs in cyber security, as well as core aspects of these degrees you’ll want to know about, including tuition costs, PhD benefits, job prospects, and salary expectations.
Best cyber security PhD degrees online
If you study a cyber security PhD online, you’ll be able to enjoy much more flexibility than you would with an in-person course. An online degree will allow you to save on the various costs of in-person programs, such as travel and rent. Here are our top picks for online PhDs in cyber security:
1. Capitol Technology University
- Program: Doctorate (DSc) in Cybersecurity
- Tuition cost: $57,000 or $950 per credit
2. University of Fairfax
- Program: Doctorate of Information Assurance
- Tuition cost: $59,260 or $895 per credit
3. Dakota State University
- Program: Doctor of Philosophy in Cyber Operations
- Tuition cost: $69,048 or $575.40 per credit
4. Capella University
- Program: PhD in Information Technology, Information Assurance and Cybersecurity
- Tuition cost: $79,000 or $965 per credit
5. American Military University
- Program: Doctor of Global Security (DGS)
- Tuition cost: $50,054
6. Northcentral University
- Program: PhD in Technology and Innovation Management with a Specialization in Cybersecurity
- Tuition cost: $68,365 or $1,094 per credit
7. Liberty University
- Program: DBA in Information Systems
- Tuition cost: $35,700 or $595 per credit
8. University of the Cumberlands
- Program: PhD in Information Technology
- Tuition cost: $44,940 or $749 per credit
9. New Jersey City University
- Program: Civil Security – Leadership, Management and Policy (CSLMP), D.Sc.
- Tuition cost: $98,019 or $1,089 per credit
10. Purdue University Polytechnic Institute
- Program: Doctor of Technology
- Cost: $112,500 or $1,250 per credit
How to choose the right cyber security PhD
There is an abundance of cyber security PhD programs to choose from. This is a result of the fast pace at which the cyber security industry is growing and the demand for associated skills. The degrees above can give you an idea of what a PhD in cyber security degree will involve, but you still need to be aware of your priorities so you can make the right decision.
Here are the key factors you should keep in mind before opting for a particular school and degree.
1. Delivery
First, you need to decide if you want to study online or in-person. Either avenue comes with advantages and disadvantages. For instance, with an in-person degree, you get access to the school’s facilities, such as libraries and other amenities, which you would lack with an online degree. When you study in-person, you also have the opportunity to discuss topics with professors and other students face-to-face. You may feel this will help your learning in ways that are lost with online education.
You might also want to separate your studies from your home life. Some people find it easier to focus on lectures, seminars, and learning when it takes place at a location designated for them.
On the other hand, an online cyber security PhD appeals to prospective students for a variety of reasons. When studying online, there is no need to travel. You don’t have to use public transport or drive to school. You can work from the comfort of your home, which will save you a great deal of time.
Another upside of an online degree is that you may have the option to extend it. This will allow you to fit in a job and other aspects of your life around your degree. Sometimes, you can also opt for weekend or evening classes, which again will let you accommodate your other responsibilities with your education. If flexibility is a top priority for you, then an online degree will be the ideal choice.
Keep in mind that a PhD is generally a minimum of four years in duration. If you extend it (out of preference or necessity), then it could last up to seven years. You should ask yourself if you’d be happier studying for several years online or in-person.
2. School ranking
The ranking of the school is another important factor to consider. This can indicate the credibility and reputation of the institution, as well as the quality of education you will receive. After all, you want to make sure that the professors teaching you – and what they are teaching – will be of the highest standard. A school’s ranking will be determined by some or all of the following features:
- Graduation rates
- Retention rates
- Social mobility
- Faculty resources
- Financial resources per student
- Student satisfaction
- Teaching quality
- Research quality
- Staff to student ratio
- Average total debt upon graduation
- Employability
By choosing a school that scores highly in these factors, you can feel confident that you will receive a high-quality education. Higher education – particularly a PhD – is a serious investment of time, money, and effort. You want to make sure that what you invest is matched by an enjoyable experience, valuable support, and good job prospects.
You will notice from the degrees above that the cost of a cyber security PhD can vary considerably. Price may, of course, be a major factor in determining your choice of program. It’s important to have an accurate picture of your degree costs and financing options beforehand, so you can ensure that you can comfortably cover the cost of your degree up until its completion. You may be able to make savings by choosing a university in the same state as where you live. In addition to tuition fees, you’ll also need to pay for learning materials, as well as administration and admission fees.
Consider whether you can qualify for any of the school’s scholarship or bursary programs. These can significantly lower the price of your education. Loans are an option, too, if you require additional financial support.
If you’re already in employment, you may be able to get your employer to help with costs. However, if you are funding your PhD cyber security program through a job, you’ll need to create a realistic plan that will allow you to balance your studies with work.
While a PhD program may look expensive, it’s important to think of your degree as an investment. This means thinking about the career prospects for PhD graduates. A PhD in cyber security will open you up to the most senior positions in the field. According to PayScale , the average salary for those holding a PhD in cyber security is $172,000.
4. Course structure and content
No two degrees are designed alike. When researching degrees, you should have an idea of your passions, preferences, and goals. By aligning these with the structure and content of your PhD program, you can be confident that you will find the program both fulfilling and useful.
Do you want your degree to be broad or specific? This will matter, depending on the career path you have in mind. After all, some senior cyber security positions, such as chief information security officer (CISO) roles, involve broad responsibilities.
Other roles, meanwhile, are much more specialized. A diverse program will give you more options when it comes to selecting a career path. However, for a specialized role, you will want to study a more relevant degree. This will give you a competitive edge when looking for work.
You will also want to think about the kind of course structure that appeals to you most. This includes the various ways that professors will assess your work. Would you prefer to be graded based on exams, individual assignments, or team projects?
Courses will differ in how much weight is given to these forms of assessment. The degree structure should suit your personality and comfort levels. Do you thrive more when studying alone? Or do you feel more energized when collaborating with others? Do you find exams particularly stressful? These are all questions you should answer before committing to a particular PhD program.
5. Course requirements
PhD cyber security programs will have prerequisites. Make sure that you check these before moving forward so you don’t waste your time. PhD degrees will require a minimum of a Bachelor’s degree, usually with a certain grade as a prerequisite. Other cyber security PhD programs will ask that you already have a relevant Master’s degree. Again, you may need a minimum average grade in this degree to be accepted as a PhD candidate.
However, if you don’t meet every requirement, it’s always worth getting in touch with the admissions department of the school. They can sometimes give you some leeway. For example, perhaps you don’t meet the grade requirements, but you have professional experience that could act in your favor.
Benefits of an online PhD cyber security degree
Gaining a PhD qualification in cyber security will provide you with a range of benefits, including:
Improved job opportunities
A PhD in cyber security will lead to far more job opportunities than having a Bachelor’s or a Master’s. True, most cyber security positions don’t require – or even prefer – that you have a PhD qualification. This level of education isn’t necessary for success in senior positions. You can also work on your career development without it.
That said, a PhD will certainly make you stand out from the crowd. It positions you as an expert in the field. During your PhD studies, you will gain a knowledge base and skillset that goes beyond what is attainable with a Bachelor’s or Master’s program, increasing your employability.
Moreover, a PhD gives you the chance to focus on a very specific area of cyber security, as well as engage in original research and work. This kind of knowledge could make you well-suited to a senior cyber security role that requires a high level of expertise and specialization.
In addition, a PhD opens you up to work opportunities in academia. With your degree, you will be able to attain a research or teaching position. If you think an academic role would be more rewarding for you, then completing a PhD in cyber security will be the correct path to go down.
Since a PhD level qualification can give you expertise in a chosen area of cyber security, this will make you an authority on the subject. This can put you in a position to deliver sponsored talks, create articles for leading news and industry sites, and even write books on the subject.
Strong demand
Cyber security is one of the quickest growing industries in the US. According to the US Bureau of Labor Statistics (BLS) , computer and information systems manager jobs are predicted to grow 10 percent through 2029. The growth of this senior cyber security position is much faster than the national average job growth of four percent.
This trend means that you will find it relatively easy to land a senior job in this profession. By pursuing a cyber security PhD, you will increase your chances of securing a well-paid role.
High salaries
Having either a Bachelor’s degree or Master’s degree in cyber security will allow you to earn a high annual salary. With these degrees and enough career development, you can end up in a company or position that pays extremely well.
A cyber security PhD, however, is an additional qualification that can justify an even more attractive pay package. Cyber security professionals with PhDs are often the highest earners in the industry. Check out the salary section below to see what cyber security experts earn, as well as how salaries tend to progress over time for these roles.
Transferable skills
After completing your PhD in cyber security, you will have gained an impressive assortment of transferable skills. You will be able to apply the technical skills and knowledge you developed in your course to many other fields. For instance, a background in the cyber security field will prepare you for senior roles in software and web development. Transferable skills include:
- Communication
- Collaboration
- Computer forensic skills
- Technical IT knowledge
- Attention to detail
- Problem-solving
- Leadership and management skills
- Analytical and research skills
- A willingness to learn the latest developments in cyber security and IT technology
What jobs can you get with a PhD in cyber security?
Having a cyber security PhD, even with limited work experience, will make you a great candidate for academic positions. This will also allow you to apply for mid-level cyber security positions.
With a PhD in cyber security and a solid level of experience in the industry, you will be able to aim for more advanced positions. Having a PhD under your belt can benefit you in your job applications and interviews for the following high-level jobs:
- Chief information security officer
- Cyber security consultant
- Penetration tester
- Cyber security analyst
- Security auditor
- Security architect
- Network administrator
It’s crucial to keep in mind that some employers might actually prefer specific certificates over, or in addition to, a PhD. In some cases, employers are willing to fund the training for these qualifications since it will enhance what you can bring to the table. Check whether this is a possibility before signing up for any additional courses.
Cyber security PhD degree salary
So, what salary can you expect to earn after obtaining your cyber security PhD? Based on a few of the roles mentioned above, PayScale has found the following average salaries:
We should underline here, though, that these salaries are likely to vary based on company, type of organization, location, level of experience, additional qualifications, and other factors.
Other qualifications to consider
If you are unsure about committing to a PhD program, that’s completely understandable. Although highly rewarding, this undertaking can be long, stressful, and taxing. You also don’t need to have a PhD for the top cyber security positions.
So, if a cyber security PhD doesn’t personally appeal to you, you can always gain one or more certificates that will enhance your career path. These will be far less time-consuming, costly, and challenging compared to a PhD. Qualifications worth considering include:
- GIAC’s (Global Information Assurance Certification) GPEN certification
- CISSP – Certified Information Systems Security Professional
- ESCA – EC Council Certified Security Analyst
- CISM – Certified Information Security Manager
- CompTIA Security+
- SECO’s Certified Information Security Officer (S-CISO)
- EC-Council’s Certified Chief Information Security Officer
- CISA – Certified Information Security Auditor
Cyber security PhD FAQs
How much does a phd cybersecurity degree cost.
The exact cost of your cybersecurity PhD will depend on certain factors, such as the school, whether the degree is in-person or online, and how long it takes you to complete the program. Based on the length of the course, you can expect tuition fees to be higher than both Bachelor’s and Master’s degrees. The cost range for a PhD in cybersecurity is between $30,000 and $100,000.
Is a PhD in cybersecurity worth it?
A PhD in cybersecurity will give you an even better chance of obtaining a well-paid, secure position. Since a PhD can make you an attractive candidate for the highest-earning roles, your investment of time and money in your PhD studies will be well worth it. Nonetheless, if you want to enrol in a PhD program, you should be ready for several years of structured education. You will also have to study topics at a more complex level than in a Bachelor’s or Master’s program.
Is cybersecurity a good career?
The cybersecurity industry is predicted to grow rapidly over the next 10 years. We’re seeing comparatively high salaries for cyber security positions at every level, as well as ample room for career development. A cybersecurity job, especially a senior one, can involve a certain amount of stress. After all, in a top position, you will carry a lot of responsibility in terms of dealing with an organization’s IT security. You are being trusted to play a major role in preventing cyber attacks and keeping sensitive information safe. On the other hand, this level of responsibility means a senior role can make a significant, positive, and lasting impact on an organization. For this reason, such a role can feel deeply rewarding.
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
10 Best PhD in Cyber Security Online [2024 Guide]
Want to be on the frontier of research, policy formation, strategic innovation, or consulting in the exploding field of information assurance and cyber security? A PhD Cyber Security online program may help you attain this goal.

If you already have a bachelors or masters in computer science along with computer engineering and other IT-related industry certifications and work experience, you’re likely qualified to apply.
Editorial Listing ShortCode:
If you don’t meet these criteria, but love cutting edge technology research, investigation, and policy advocacy, you might want to consider mapping out a plan now in order to qualify for entering a cyber security doctoral program.
Universities Offering Online PhD in Cyber Security Degree Programs
Methodology: The following school list is in alphabetical order. To be included, a college or university must be regionally accredited and offer degree programs online or in a hybrid format.
1. Capella University
Capella University, which is an NSA / DHS designated National Center of Academic Excellence in Information Assurance / Cyber Defense, offers an information assurance and cybersecurity concentration for students in its Ph.D. in Information Technology program. The degree requires 90 total quarter credits, and there are multiple ways to save on tuition.
- PhD in Information Technology – Information Assurance and Cybersecurity
Capella University is accredited by the Higher Learning Commission.
2. Capitol Technology University
The Doctor of Science in Cybersecurity program from Capitol Technology University is designed to teach students how to conduct research in matters of cyber defense, to create innovative and creative solutions to cybersecurity problems, and to be qualified enough to make final decisions about solutions. Students can choose electives to better streamline their paths.
- Doctorate in Cybersecurity
Capitol Technology University is accredited by the Commission on Higher Education of the Middles States Association of Colleges and Schools.
3. Colorado Technical University
Students at Colorado Technical University can earn their Doctor of Computer Science in Cybersecurity and Information Assurance at an NSA / DHS designated CAE-IA/CD. The program can be completed in three years, and students work with advisors to build schedules that work best for them.
- Doctor of Computer Science – Cybersecurity and Information Assurance
Colorado Technical University is accredited by the Higher Learning Commission.
4. Dakota State University
At Dakota State University, students can earn their Ph.D. in Cyber Operations while growing their professional connections with various businesses and government agencies. The program features multiple computer science courses with a heavy emphasis on cybersecurity. In addition to rigorous online coursework, students will also undertake three, on-site research seminars.
- PhD in Cyber Operations
Dakota State University is accredited by the Higher Learning Commission.
5. Marymount University
Marymount University’s Doctor of Science in Cybersecurity program places a premium on such topics as technology, data science, policy, leadership, management, ethics, and teaching. Students are placed in real-time, real-world situations and must assess and combat threats to digital networks. Extensive research will also be conducted in the cybersecurity field.
- Doctor of Science – Cybersecurity
Marymount University is accredited by the Southern Association of Colleges and Schools Commission on Colleges.
6. National University
National University offers a PhD in Technology and Innovation Management with a Cybersecurity specialization that is designed to prepare students to become leaders in the field of cybersecurity. Graduates may pursue careers in private and government organizations.
The program requires the completion of 20 courses for a total of 60 credit hours and can typically be finished in 50 months.
- PhD in Technology and Innovation Management – Cybersecurity
National University is accredited by the WASC Senior College and University Commission.
7. New Jersey City University
Students enrolled in New Jersey City University’s Doctor Of Science in Civil Security Leadership, Management & Policy program explore three distinct areas of digital security: national security, corporate security, and information assurance and cybersecurity. The program accepts between 15 to 20 doctoral candidates each year and usually takes about three years to complete.
- Doctor of Science in Civil Security, Leadership, Management and Policy
New Jersey City University is accredited by the Middle States Commission on Higher Education.
8. Nova Southeastern University
Nova Southeastern University’s Ph.D. in Cybersecurity Management requires a total of 67 credit hours. It’s designed for working professionals who need flexible college schedules. It’s a research-based degree that aims to prepare graduates for leadership jobs in cybersecurity or university teaching positions. Equal emphasis is placed on cybersecurity skills and management training.
- PhD in Cybersecurity Management
NSU is accredited by the Southern Association of Colleges and Schools Commission on Colleges.
9. University of the Cumberlands
University of the Cumberlands offers students a Ph.D. in Information Technology program entirely online. Students are expected to tackle topics such as technology for the global economy, information governance, data science, emerging threats to IT, and enterprise risk management. These courses are designed to teach students how to improve connectivity, identify cyber threats, and more.
- PhD in Information Technology Online
The University of the Cumberlands is accredited by the Southern Association of Colleges and Schools Commission on Colleges.
10. University of Rhode Island
Students interested in cybersecurity at the University of Rhode Island can enroll in the Ph.D. in Computer Science program. Much of the degree can be completed online, but there will be occasions when visiting the campus will be required. Students can choose to focus their electives in the cybersecurity field.
- PhD in Computer Science
The University of Rhode Island is accredited by the New England Commission of Higher Education.
PhD in Cyber Security Online Programs

Getting a PhD can be very exciting. It can help put you on the cutting edge of innovation and policy research, allowing you to apply deep theoretical knowledge to emerging industry challenges, as well as ethical and legal policy debates on a national or global scale.
When you’ve completed a PhD in Information Security online, the jobs you’re ready for may not be as highly defined as they were when you got your bachelor’s or master’s degree.
This is because your area of individual specialization combined with your advanced theoretical insights should mean you actually have a unique expert profile. A PhD in Cyber Security can help open doors to exciting career paths, depending on your academic concentration:
- Teaching opportunities at colleges and universities
- Policy work
- Engineering research,
- Cyber operations leadership
The best cyber security doctorate program for you will depend in part on the kind of courses offered and the kind of expertise you want to develop.
In general, those looking into a cybersecurity PhD will want to consider if they’re more interested in technical and engineering research type applications, or prefer a career path that involves teaching, quantitative research, policy work, high-level consulting, or governance work.
Keep in mind that PhD institutions will also vary in sector orientation as well.
Some will be more focused on engineering research, others may specialize in strategic cyber operations (for corporations, government, or national security), and others might be affiliated with law or business administration programs and focusing on legal and ethical aspects of information assurance, on corporate leadership, or on regulatory or policy reform.
Finally, as a PhD candidate you’ll need to consider the kind of concentration that best fits your deepest intellectual interests, professional aptitudes, and career aspirations.
Cyber Security Careers & Salaries

Once you’ve earned a masters and PhD degree in information technology (or related field), you should see an increase in income with work opportunities in many sectors, including higher education, government, private industry, defense, and advanced software engineering research.
The Bureau of Labor Statistics provides a glimpse at the kinds of salaries that you may earn with advanced cyber security skills.
Some of the careers listed here may be accessible with a bachelor’s degree in computer science or computer engineering, but the highest paid jobs listed typically require a masters or doctorate degree like a cyber security masters degree online or a cyber security doctorate.
If you move into advanced research, teaching, consulting, or engineering roles after completing your PhD in Cybersecurity, you may, over time, develop various streams of income.
Such income sources might include consulting fees or retainers, intellectual property rights, traditional work salaries, speaking honorariums, salaries, as well as stipends related to teaching or institutional research collaborations.
Likewise, you may find yourself earning a top salary in a high-level research, consulting, policy, or operational role in industry or government, or you may find your way to a tenured position in higher education.
We expect you feel some excitement seeing what you can earn with advanced degrees in this field—keep in mind that you might also one day be shaping leading policies and innovations in cyber security for years to come!
Choosing an Online PhD in Cyber Security

We recommend doing enough research to feel confident that the school and program you select are fully accredited, have professors with solid academic and industry credentials, and, most importantly perhaps, that the courses offered are aligned with the areas of concentration that most interest you.
As you compare programs it’s also a good idea to ask yourself what kind of real-world industry experiences and expertise characterize the leading faculty at the school. Remember, PhD programs are unique in the way that students and professors collaborate closely, almost like academic colleagues!
Whether it’s a department colloquium, a research panel event, a call out to visiting scholars, or getting advice from faculty members on your dissertation prospectus…in a doctoral program, the intellectual topics, debates, and conversations you’re engaged in will be informed in large measure by the industry orientation and experiences of the department faculty.

Engineers, military operations personnel, lawyers and social policy wonks, those in business administration circles…these kinds of people can all be part of the larger cyber security universe but quite distinct in the research and applications they focus on and care about.
Finally, when looking at online options, you’ll see that some programs offer a PhD in Cybersecurity, others offer a PhD in Information Security, or even a Doctorate of Information Assurance (DIA).
You may also see online cybersecurity programs leading to a Doctor of Science (DSc) instead of a PhD, or programs offering an online Doctor of Information Technology (DIT).
Since these degree titles are somewhat interchangeable, we suggest you always look behind the degree title at course offerings, course concentrations, industry or sector affiliations, and career orientations in the programs you’re most interested in.
PhD in Cyber Security Curriculum & Courses

Your professors will be teaching some important course content no doubt, but in your online PhD cyber security program, they’ll also serve the critical role of research mentors to you and your fellow PhD candidates.
Likewise, taking courses is only one part of your academic commitment alongside engaging in original research and dissertation writing. Course offerings will differ based on programs, but here’s a broad sample of what kinds of courses you can expect:
- Technology Policy and Strategy Administration : Students get a deep dive into theoretical and practical frameworks for decision making in the area of IT policy and strategic management of IT assets.
- Advanced Reverse Engineering Methods : Students learn and apply advanced research engineering methods in real-life scenarios and demonstrate mastery of reverse engineering skills for cyber security applications.
- Cryptography and Information Assurance Protocols : Learn about the science of coding and decoding and the kinds of keys, controls, and protocols used in conjunction with cryptography and information assurance methods.
- Advanced Methods in Risk Assessment and Control : Learn about theoretical frameworks defining best practices in industry-specific cyber security risk management.
- Cyber Operations Strategy & Advanced Forensics : Learn about research methods and practical skills for operating in adversarial cyber operations or cyber threat scenarios.
- Topics in Contemporary IT Policy, Law, and Ethics : Learn about the most compelling topics, controversies, and theoretical underpinnings defining legal and ethical data privacy and protection frameworks.
- Information Assurance Consulting : Students research and study frameworks for providing senior-level consulting services in information security.
- Advanced Cybersecurity Engineering and Research : Students develop knowledge of contemporary trends at the intersection of cybersecurity software architecture development and related software engineering research.
- Databases and Information Safeguards : This course gives students insights into the methods and theories guiding contemporary practices and innovations in database uses and architectures with a focus on information security and data management ethics.
- Qualitative and Quantitative Research Methods : Students learn professional research standards and data presentation and modeling skills to apply to their dissertation research methodology.
As you can see, getting a PhD in Information Security online means building on your existing knowledge in computer science in order to engage in the highest levels of investigation, development, teaching, research, and consulting.
Admissions Requirements
Admissions to a Cybersecurity PhD program will in most if not all cases require you to have a bachelor’s or master’s degree in computer science or computer engineering or a related field. Some programs will require GRE or GMAT scores, but in some cases, waivers are available, or the university will make this requirement optional.
Most programs will expect applicants to have not only prior college degrees, but also significant work experience and, in some cases, industry certifications in prerequisite technology skills.
Accreditation

Getting a doctorate degree is a big deal. You probably want to ensure your faculty have compelling academic and industry credentials. This includes making sure you select a fully accredited program and school as well. Also, many PhD programs only recognize course credits and degrees from accredited colleges and universities, including those earned through programs like an MBA in Cybersecurity online .
The Council for Higher Education Accreditation (CHEA) is a good resource for learning more about accreditation standards and identifying accredited schools.
Due to the growing national interest in expanding the cyber security workforce, you may also find new consortiums seeking to help you navigate online cyber security degree programs , such as the government-sponsored National Centers of Academic Excellence (NCAE).
Financial Aid and Scholarships

If you have the kind of interest and motivation that makes getting a PhD sound exciting, we encourage you not to let tuition costs stop you, especially in fields like cyber security that have strong projected job growth.
Usually, financial aid options will be available to you if you’re a qualified PhD program candidate but need financial help.
And, you never know what kinds of financial assistance programs you may be eligible to tap into when you start applying for an online cyber security doctorate, especially since government, industry, and higher education leaders are presently building training pipelines to fill growing job demand in this critical field.
If you’re interested in financial aid, we suggest you stick with fully accredited programs and check with admissions counselors about school or government-sponsored scholarship.
Your employer may also offer some form of tuition assistance. If you do plan to apply for school loans or scholarships, it’s always a good idea to complete the federal financial aid application ( FAFSA ) ahead of time.
What Can You Do With a PhD in Cyber Security?

With a PhD in cyber security you should find that you’re in a great position to compete for well-paid jobs in the cyber security field.
An online cyber security doctorate degree can help you obtain the theoretical knowledge and sophisticated research skills needed to work in higher education teaching positions, prestigious consulting careers, or senior engineering research roles.
According to the Bureau of Labor Statistics, high-level information security research jobs are forecast to grow 15% on average in the coming decade, while the larger cyber security job market is forecast for a whopping 31% rate of growth.
How Much Does a PhD in Cyber Security Program Cost?

You should expect to find tuition costs ranging from as low as $500 per credit hour up to $1,200 and above, with most programs requiring between 30 and 40 credit hours of coursework.
Keep in mind time costs too, as it’s hard to predict exactly how many years you’ll need to complete your dissertation, anywhere between 15 months and 2 or 3 years, or more. As you compare programs and costs, keep in mind what’s being offered too.
Consider how important direct faculty support for your dissertation work is to you and what kind of research resources a school offers. When your goal is a doctorate degree, it’s even more important to consider these factors alongside cost.
How Long Does it Take to Get a PhD in Cyber Security Online?

Getting a PhD in Cyber Security online will usually take 3 to 5 years, depending on the program and pace at which you complete your dissertation research and writing.
Assume you’ll need 2 to 3 years to complete the course work and another year or two, at least, to finish your dissertation. Keep in mind that dissertation work may extend beyond two years, depending on your own work habits and research interests.
How long it takes to get a PhD depends largely on your schedule and program. A number of online programs have options for students who want an accelerated study timeline. Keep this in mind as you compare online cyber security PhD options.
Are There Any Affordable Online PhD in Cyber Security Programs?
Yes, there are affordable programs. With the fast-growing attention on cyber security threats and the need for qualified information security professionals across industries and roles, you’ll find a wide range of schools and programs to choose from, with a wide range of tuition costs.
You should find the more affordable programs offering per credit tuition rates between $450 and $600.
Is a PhD in Cyber Security Program Worth it?

Yes, a doctorate in cyber security online is worth it for many students. The Bureau of Labor Statistics is projecting 11% job growth in computer and information technology occupations over the next 10 years. Common careers in this field include computer and information research specialist or network engineer working in cyber security, computer engineering, and information assurance jobs.
With your cybersecurity doctorate, you may also qualify to work as a college teacher or as a high-level consultant, or policy advocate. What’s really key to remember is that whatever your individual path, you’ll be among a first wave of experts giving direction to a still very young and fast-growing profession!
Getting Your PhD in Cyber Security Degree Online

It’s true that getting an online PhD in Information Security takes time and money. But, remember, if this is the right path for you, you’ll likely be excited about pursuing an advanced degree and see it as the chance of a lifetime, not an expense.
Indeed, if your dream is to build a career in cyber security leadership applying big-picture theoretical and analytical thinking in advocacy, research, teaching, consulting, or computer engineering roles, we think it’s likely you’ll agree an investment like this is hard to quantify!

10 Best PhD Cyber Security Online Programs [2024 Guide]
Check out PhD Cyber Security Online Programs for 2024. Compare career paths, degree programs, job growth, and salary data.

Getting an online PhD in Cyber Security can help you arm yourself with the knowledge and skills required to keep everyone using the Internet safely, including all-important data.
Editorial Listing ShortCode:
Almost all business operate online these days. These businesses, as well as non-profit organizations, schools, and even government agencies, may be vulnerable to online and insider threats.
Online PhD in Cyber Security Programs

A Cyber Security doctorate can be a useful degree to have if your goal is to fully immerse yourself in the fascinating and complex world of information systems.
An online cyber security degree program encompasses classes and assignments that can help you learn how to create and evaluate IT systems and infrastructure. On top of that, being a cyber security graduate student can help you learn how to provide solutions to difficult technological problems and threats.
Critical-thinking skills, the ability to create and apply data and codes, and the foresight to understand and reduce the risk of cyber threats can help you as you study cyber security. Someone already well-versed in computer science, mathematics, and other like-minded disciplines may find it easier to apply for an online PhD in Cyber Security.
A graduate program for cybersecurity may have tough but engaging coursework in homeland security, advanced algorithms, advanced computation, artificial intelligence (AI), and information technology.
These may be hard courses and finishing a doctoral program may require an investment of several years of study, but the payoff is worth for many students.
A PhD in Cyber Security can help make you valuable to employers in both the private and public sectors. Cyber Security specialists may work in a variety of roles, from cyber security analyst to IT and software developers. Those who love the discipline may also teach it at the college level as professors.
Cyber Security Careers & Salaries
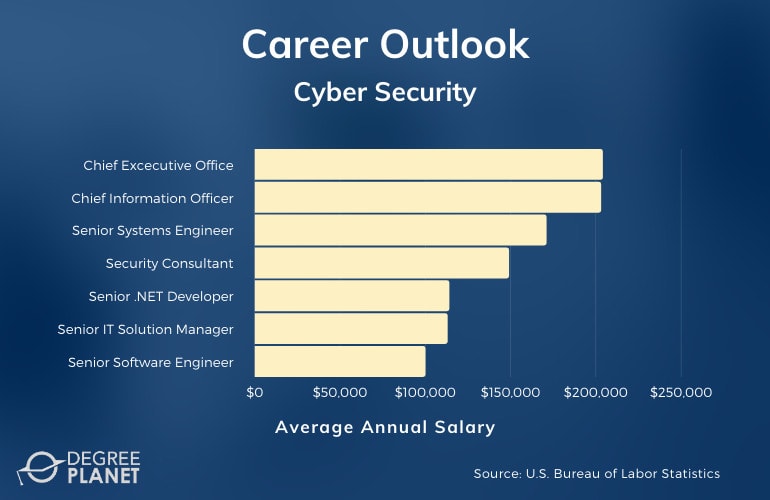
Unlike the lower level degrees such as a cyber security associate degree , a PhD in Cybersecurity can help prepare you for a fast-paced and growing career in the world of information technology (IT), business intelligence, software engineering, and so much more.
Cyber Security experts are considered top-notch, highly qualified individuals who are called upon to tackle some of the most complex digital challenges in the world.
Without the protections offered by cybersecurity experts, the basic infrastructures of the online business world (and general society at large) would be vulnerable to DDOS attacks, ransomware infiltration, identity theft scams, and other malicious activities that would put millions of dollars and lives in jeopardy.
Cybersecurity specialists are also on the cutting edge of digital forensics. When private or company data is attacked, it is often Cyber Security experts who are called in to salvage data and track and trace those guilty of the attack. Getting a graduate degree in cyber security can help you become a new kind of detective for the 21st century.
A PhD in Cyber Security can not only train you to face the challenges of today, but it can also help you equip yourself with the skills and knowledge necessary to train future generations of aspiring Cyber Security specialists. This is a high-demand job with a large number of businesses on the lookout for qualified specialists.
Average salaries for Cyber Security doctorate holders range from $84,000 a year to $185,000 a year. Few Cyber Security positions are lower than $50,000 a year.
The Bureau of Labor Statistics also shows that this is one of the fastest growing careers in the country.
Cybersecurity Curriculum & Courses

According to Cyber Degrees, the most common courses for graduate students pursuing a Ph.D. in Cyber Security are theory of computation, network security, network architecture, and many more. Here is a sample of the courses you may encounter in this program:
- Theory of Computation focuses on how to solve problems based on models of computations using advanced mathematics and algorithms. It introduces major concepts like Automata theory, Computability theory, and Computational complexity theory.
- Computer Systems, Networks and Architecture shows students how to correctly design computer networks and build data communication systems, including Intranets.
- Network Security can help equip students with knowledge about different types of malicious software attacks and how they can be countered. Network Security coursework also discusses how to properly protect online assets.
- Applied Cryptography covers information security systems, as well classic cryptographic algorithms, symmetric cryptography, asymmetric cryptography, and other management and distribution models of cybersecurity.
- Cyber Law goes into detail about the nuances and complexities of cyber law.
- Security Risk Management focuses on implementing layers of security, threats and vulnerabilities to Intranets, ways to protect data, and ways to compose security risk models.
- Homeland Security provides an up-to-date overview of homeland security issues, from online hazards, domestic and international terrorism, and technological calamities.
- Advanced Algorithms is all about the fundamentals of advanced algorithms, including how they are designed and implemented.
- Artificial Intelligence covers how to adapt human behaviors to digital networks.
- Software Engineering instructs students on how to build and maintain reliable software, which means the course also goes in-depth about the science and mechanics of computer software.
While some programs vary, almost all will at some point require students to pass one or all of these classes.
Admissions Requirements

Some of the most common admission requirements for entering an online PhD program in Cyber Security include prior course work, a master’s degree, and letters of recommendation. You may need the following requirements for your degree program:
- A master’s degree may be required, but not always
- A GPA of 3.0 or better in computer science, math, and other related courses
- Three letters of recommendation (varies depending on the school)
- Professional experience in the field, although this is not always mandatory
- A written Statement or Purpose or Personal Essay
- GRE scores, although some universities no longer require this
In general, if you are a dedicated student with good grades, solid letters of recommendation, and high marks in related coursework, then you will likely be a good candidate for this doctoral program.
Accreditation

Regional accreditation is one of the most important aspects of a doctorate degree in cyber security.
Regional accreditation comes when colleges demonstrate that their degrees, both undergraduate and graduate, meet the minimum standards and requirements per one of the seven regional accreditation agencies in the United States.
If you are unsure whether or not a school is fully accredited in its region, a good place to start would be the U.S. Department of Education website.
Financial Aid and Scholarships

Regardless of the program or the school, paying for your degree is often an issue for aspiring graduates. The good news is that the federal government and state governments offer a number of financial aid packages.
A great place to start for any student applicant is the Federal Student Aid website, which provides awesome information about how and where to apply for loans, grants, and other aid options.
All students should complete the FAFSA , or Free Application for Federal Student Aid. Filling out a FAFSA can connect you with possible aid packages that meet your personal situation.
What Can You Do With a PhD in Cyber Security Online?

The U.S. Bureau of Labor Statistics indicates that some of the most exciting and widely available jobs for cyber security graduates include IT specialist, threat analyst, information security specialist, and others.
- Information Technology Specialists
- Information Security Specialists
- Risk Managers
- Risk Compliance Specialists
Computer and information technology jobs have a projected job growth rate of 11% for the next ten years. Better yet, the U.S. Bureau of Labor Statistics says that Cyber Security professionals in this field may earn, on average, $91,250 per year.
How Long Does It Take To Get an Online PhD in Cyber Security Cost?
Like any graduate school program, an online PhD in Internet Security or Cyber Security can take a significant amount of time.
The good news is that most online programs have a proven track record of providing excellent education in a relatively short amount of time.
- A Master’s degree in Cyber Security usually takes two years.
- A PhD degree in Cyber Security online usually takes anywhere from three to seven years. But this can change depending on whether or not you’ve earned your master’s degree prior to entry.
Becoming a well-educated and well-versed specialist in any discipline takes time.
Are There Any Affordable Online Cyber Security Doctoral Programs?
Yes, there are affordable online PhD in Cyber Security programs. Because it is such an in-demand industry, online degrees are plentiful and many are affordable. Tuition for online programs range from about $50,000 per year to as low as $9,000 per year. Most programs fall somewhere in the range between $10,000 and $15,000.
Again, if you want to lower the cost of tuition, be sure to complete your Federal Application For Student Aid (FAFSA) as soon as possible so you can see what kind of loans, grants, and aid are available for you.
Is an Online PhD in Cyber Security Worth it?

Yes, a PhD in Cyber Security is worth it for many professionals. According to the Bureau of Labor Statistics, computer and information technology jobs are set to grow at 11% over the next 10 years, much faster than the average for all occupations. Common cyber security careers in this field include IT Specialist, a Cyber Lead, a Cyber Security Engineer, and others.
Almost any degree level in this field is worth it for many students. For instance, even an associates degree in cyber security is worth it to many students because it takes the shortest amount of time and can potentially lead to an entry-level position. But if you are looking for a higher-end position, then a PhD may be a better choice.
Universities Offering Online PhD in Cyber Security Degree Programs
Methodology: The following school list is in alphabetical order. To be included, a college or university must be regionally accredited and offer degree programs online or in a hybrid format.

With its Doctor of Global Security degree, American Public University offers a multidisciplinary approach to security issues face on a domestic and global level and teaches students the policies and standards that are expected in those areas.
The classes in this program have instructors that are familiar with the workings of the government agencies that utilize these skills.
- Doctor of Global Security – Cybersecurity
APUS is accredited by the Higher Learning Commission.

Capella University’s Doctor of Information Technology helps students acquire the knowledge and confidence to complete their dissertation by giving learners the support, structure, and resources needed to be successful in obtaining their degree.
Students can study data privacy, organizational requirements, and how to minimize risks that companies face every day.
- Doctor of Information Technology – Information Assurance and Cybersecurity
Capella University is accredited by the Higher Learning Commission.

Pursuing a Ph.D. in cybersecurity leadership from Capitol Technology University can give opportunities for students to conduct intensive independent research in a wide range of areas relating to computer science, cybersecurity, programming, and logistics.
Learners looking to advance their abilities, cybersecurity, and leadership to the upmost levels and secure an internship or career in the field.
- PhD in Cybersecurity Leadership
Capitol Technology University is accredited by the Commission on Higher Education of the Middles States Association of Colleges and Schools.

Colorado Technical University has a Doctor of Computer Science in cybersecurity and information assurance that is based on measurable techniques that are founded in research data to complete the dissertation process. CTU has a flexible program that can be achieved through distance learning and has multiple start dates to choose from.
- Doctor of Computer Science – Cybersecurity and Information Assurance
Colorado Technical University is accredited by the Higher Learning Commission.

A Doctor of Philosophy in Information Systems awarded from Dakota State University helps students to work in the fields of research, education, and commercial service. This is a multidisciplinary program that stresses the importance of applied research, administrative technologies, and management. DSU’s Ph.D. program typically takes about three years to complete.
- PhD in Information Systems
Dakota State University is accredited by the Higher Learning Commission.

Marymount University offers a Doctor of Science in cybersecurity that is rich in academics and mentorships to help students become a successful entrepreneur in the industry of computer science. MU’s D.Sc.’s takes into consideration new and future security threats to data and information in today’s society.
Networking, leadership, and ethical responsibility are key aspects of this program.
- Doctor of Science in Cybersecurity
Marymount University is accredited by the Southern Association of Colleges and Schools Commission on Colleges.

National University offers a Doctor of Philosophy in Technology and Innovation Management with a specialization in Cybersecurity. The program aims to help students develop the skills needed to stop cyberattacks in the information systems area. NU seeks to teach learners how to communicate effectively in various settings and discuss up-to-date theories and applications.
- PhD in Technology and Innovation Management
National University is accredited by the WASC Senior College and University Commission.

Obtaining a Doctor Of Science in civil security leadership, management, and policy from New Jersey City University may be an excellent choice for students looking to study the areas of national, corporate, and informational security. This three-year program requires students to complete a two-week residency and four weekends per year.
- Doctor of Science in Civil Security, Leadership, Management and Policy – Information Assurance/Cyber Security
New Jersey City University is accredited by the Middle States Commission on Higher Education.

Nova Southeastern University’s Ph.D. in Cybersecurity Management blends traditional learning with a dynamic online program to give students a minimum of sixty-seven credits to help prepare them to work in a career in computer science and analytic data measures.
This degree helps learners gain knowledge in multidisciplinary research to acquire a position with the government, corporate, and other related agencies.
- PhD in Cybersecurity Management
NSU is accredited by the Southern Association of Colleges and Schools Commission on Colleges.

Earning a Ph.D. in information technology from the University of the Cumberlands helps students enhance their ability to gain employment in a global community in cybercrime, data analysis, and information systems infrastructure.
This online program works to give students the boost needed to make the next step in their future professional and academic careers.
- PhD in Information Technology
The University of the Cumberlands is accredited by the Southern Association of Colleges and Schools Commission on Colleges.
Getting Your Doctorate in Cybersecurity Online

The reliance on digital technology and computers is not expected to change anytime soon. That means that businesses, schools, organizations, and others need professionals who have the expertise to keep data, networks, and infrastructure secure. That’s where cyber security professionals enter the picture.
As a cyber security professional, especially one armed with a doctorate degree, you may be the frontline defense against malicious online actions and attacks. Many find it to be a rewarding and valuable job, and it’s in high demand. It is a job with outstanding growth potential in both the private and public sectors.

Find Your School

The Best Online Doctoral Degree Programs in Cyber Security
The best online doctoral degrees in cyber security.

Methodology
Best Online Doctorates in Cyber Security Ranking Methodology
Our metrics have been honed from years of experience in higher education journalism and research, and seek to provide a balance between the traditional academic prestige of an institution with a cyber security program, and other concerns that particularly non-traditional or working students may express. Namely, that affordability and support in online learning environments is crucial for successful outcomes for non-traditional, working, and adult students.
We start the process of any academic ranking by surveying every available cyber security degree program within the purview of the ranking. All information used in our ranking process is double checked, and comes from the Integrated Postsecondary Education Data Systems (provided by the US Department of Education) or the schools themselves.
In line with our categories of excellence covered on our rankings page, our ranking methodology for our doctoral cyber security degree programs is as follow:
- Is the program an NSA / Department of Homeland Security designated program? (50%)
- The percentage of instructors who are research faculty (50%)
- Tuition per credit hour for the program (50%)
- The availability of doctoral grants, research assistant roles, and the ability to teach classes for doctoral candidates(50%)
- The percentage of graduate students taking some online courses (100%)
1.) Dakota State University

Dakota State University is a public state university with a main campus located in Madison, South Dakota. Home to some 3,000 students, the university goes by the motto “technically, we’re better” to highlight their focus on business and technology courses of study. The university offers a vigorous and wide ranging set of offerings online as well, with 54% of undergraduates and 88% of graduate students at least taking some courses online. The university has been heralded as one of the top comprehensive cyber security schools and one of only a handful of schools we know of that offer cyber security programming at the associates through doctoral levels (all available online as well). Dakota State University is also the only university to be featured in all of cyber security rankings. Of hundreds of universities, Dakota State University ranks for their top associates , bachelors , Masters, and doctoral degrees.
Dakota State University’s fully online D.Sc. in Cyber Security places first in our ranking due to excelling in all categories surveyed: affordability, academic quality, and student satisfaction. The degree is meant for students with a strong background in computer science, whether that is a bachelors with a masters in another discipline or a masters in computer science. Students without all of the prerequisite computer science knowledge may still be accepted, however, contingent upon taking up to 12 graduate credit hours of foundational computer science work to catch them up. Dakota State University’s cyber security programs are some of the most well connected in the United States, with ties to the NSA, the CIA, Navy SPAWAR, Department of Homeland Security, Johns Hopkins University’s Applied Physics Lab, Army INSCOM, Carnegie Mellon’s Software Engineering Institute and MIT’s Lincoln Labs. Unsurprisingly, the program holds the coveted NSA/CAE designation, the highest accreditation for cyber security and information assurance programs. DSU is also known for their talented cyber defense team, who often come in close to the top at national competitions.
- Tuition per credit hour: $388
- NSA/CAE Designated Program: Yes
2.) Capitol Technology University
Capitol Technology University is a private, not-for-profit, non-sectarian university located northeast of Washington, D.C. between Baltimore and Washington. The university has a long lineage of technical training, originating as a radio engineering institute for servicemembers in the early 20th century. In line with its lineage, Capitol Technology University is regularly lauded as a particularly “military friendly school.” The university is also known for its innovative online offerings. 71% of undergraduates at the university are enrolled in at least some distance education, while 95% of graduate students take only online offerings. The university has been noted by US News as a top online engineering school at the undergraduate and graduate levels.
The fully online doctor of science in Cybersecurity (DSc) offered by Capitol Technology University is geared towards fully employed students working in cyber security fields. The program, as with many doctoral programs in cyber security, aims to create future information assurance and cyber security leaders. The university’s physical location is a perfect fit for those wishing to get into policy work as well. Capitol Technology University partners with a wide range of local, state-level, regional, and national organizations, and is located within an hour of the largest concentration of cyber security jobs in the United States (Washington, D.C.). As is probably expected from one of the oldest online doctoral programs in cyber security, Capitol Technology University’s cyber security programming has been designated a Center of Academic Excellence-Cyber Defense (CAE-CD) since 2003.
- Tuition per credit hour: $867
3.) Capella University

Capella University is a private, for-profit university with a main office located in Minneapolis, Minnesota. Home to some 36,000 students, the university is known for its vast online offerings. Accordingly, 100% of learners attending Capella (at the associates through doctoral levels) are online learners. The university has been heralded as an innovative solution for non-traditional students looking to both work full time and obtain graduate degrees. The widespread use of prior learning assessment crediting allows qualified students to focus on what they already don’t know, and recieve credit for subjects they have already mastered on the job or in previous school environments.
The fully online PhD in Information Assurance Security program offered by Capella excels at flexibility and offering support to students holding down fully time jobs while seeking their doctorate. The program focuses on both advanced technical skills as well as research and has been designated a National Center of Academic Excellence in Information Assurance/Cyber Defense through the year 2021. Flexibility-enhancing components of the program include a wide range of start dates yearly (which is uncommon at the doctoral level), as well as the ability to start on your dissertation from the start of the program. This offering builds credit-bearing research seminars around the topics you would like to research for your dissertation. Tuition is capped at $5,000 per semester, with students able to pay less if they take less than a full load. Furthermore, servicemembers receieve a 10% discount on all program costs.
- Tuition per credit hour: $925
4.) Colorado Technical University

Colorado Technical University is a private, for-profit technical university with a main campus located in Colorado Springs, Colorado. The university is home to some 28,000 students at the associates through doctoral level of study. Online education is central to Colorado Technical University’s offerings, with 65% of undergraduates and 52% of graduate level students taking at least some distance courses. As one might expect, the university primarily offers programming in business and technical disciplines, for which it often ranks highly in rankings of online schools. Furthermore, Colorado Technical University is regularly ranked as one of the top schools for servicemembers and veterans due to a number of support services, flexibility, and a special tuition rate.
The fully online Doctor of Computer Science – Cybersecurity and Information Assurance degree offered by Colorado Technical University aims to prepare the next generation of senior level leadership, consulting, and teachers within cyber security disciplines. Unsurprisingly, the university’s cyber security programs hold the lauded status of being a National Center of Academic Excellence in Information Assurance/Cybersecurity through the year 2021. Unlike many doctoral programs, students may elect to choose multiple start dates a year, and may take advantage of work and life experience credits to accelerate their time until degree. The progression of CTU’s program begins with a year of foundations, followed by a year of advancing research methods and understanding in a focus area, followed by a year or more to complete 6 research based classes (for your dissertation) as well as courses on leadership.
- Tuition per credit hour: $598
5.) University of Fairfax
The University of Fairfax is a private,non-profit, fully online university with main offices located in Vienna, Virginia. The university is quite young, being founded in 2002 with the aim of providing quality instruction in information assurance and systems. Pursuant to US regulations, the school was enabled to operate for up to 10 years while in the process of seeking an initial accreditation. The University of Fairfax was granted accreditation by the Distance Education Accrediting Commission (a national accreditor) in 2012. The university’s location close to the hub of most cyber security jobs in the United State is a great boon to its students, who may also participate in bootcamps aimed at helping students to prepare for lucrative professional certifications in cyber security .
The fully online Doctorate in Information Assurance offered by the University of Fairfax pushes students to develop novel solutions to a cyber security problem of interest and to present solutions through empirical research into the topic. The objective of the program is to help provide the nation with the next generation of thought leaders, policy makers, and top consultants in cyber security. The completion time of the degree is between 3 and 5 years, and courses are taken in both synchronous and asynchronous manner (often a boon to flexibility for students). 57 credit hours of foundational pre-dissertation work are required in the program, with 5 dissertation hours (at least) required afterwards. This is actually a slightly lower number than a number of other programs, and may be seen as a way to accelerate time until degree for worthy students.
- Tuition per credit hour: $895
6.) North Central University

Northcentral University (not to be confused with North Central University, a private religious college) is a private, for-profit, virtual college with a corporate headquarters located in San Diego, CA. Home to some 10,000+ students, the university is known for its wide range of professional and practical degree offerings, primarily in counseling, education, business, and technology. The university is one of only a handful in the nation that are 100% online, and has been lauded for its online course presentation and support services by the likes of US News and other online degree ranking entities for years. Northcentral University is regionally accredited by the Western Association of Schools and Colleges.
The fully online PhD in computer in information security offers a number of high quality enhancements seldom found online. Students in the program may choose start dates on a weekly basis, only engage with faculty with doctorates in their field, and have no scheduled lecture hours. This leads to unrivaled flexibility and the ability to balance working through the several years of a PhD with work and home commitments. While the programs primary focus are is on computer and information security, the program is technically a doctorate in business administration, which frames lines of inquiry into information assurance from a business and management perspective. Though individual time-until-degree times may vary, the program requires an estimated 45 months to complete makin it one of the quicker programs on our list.
- Tuition per credit hour: $1197
- NSA/CAE Designated Program: No

- Majors & Careers
- Online Grad School
- Preparing For Grad School
- Student Life
Top 10 Best Programs for a PhD in Cyber Security

Technology is becoming more and more integrated with our daily lives — with it comes threats from hackers that make your information vulnerable. Indeed, cybersecurity threats are expected to grow even more in the next few years, making cybersecurity professionals sought-after in the hiring market. Already have an extensive computer science background? Why not take it to the next level with a PhD in cyber security?
A doctorate degree in cyber security gives you a valuable qualification and in-depth knowledge of cybersecurity challenges. Not only will you be equipped to help organizations protect their crucial information, but you’ll also be qualified to develop strategies for better data security and even teach the subject in university.
Ready to unlock unlimited career potential in the cybersecurity space? Let’s jump into our top programs for cybersecurity PhD programs, including common requirements and costs and future career potential.
Table of Contents
Best Programs for a PhD in Cyber Security
Arizona state university, ira a. fulton schools of engineering.
Ph.D. Computer Science (Cybersecurity)

Arizona State University is certified as a National Center of Academic Excellence for Information Assurance Research and Education (CAEIAE). Its doctorate of cyber security program helps students master key theories and algorithms to apply to a modern computer science realm.
- Courses: Data and information systems , information assurance and security, applied Cryptography, and advanced computer network security.
- Credits: 84
- Delivery: On-campus
- Tuition : $11,720 per year
- Financial aid: Scholarships, grants, and loans.
- Acceptance rate: 88.4%
- Location: Phoenix, Arizona
Capitol Technology University
Doctorate (DSc) in Cybersecurity

Capitol Technology University is designated as a National Center of Academic Excellence in Cyber Defense. The school’s doctorate in cybersecurity program is a low-residency online program and was the first of its kind in the USA.
- Courses : Situation awareness analysis & action plan processes, information assurance strategic management, information assurance implementation
- Credits : 54-66
- Duration : 3 years (8 semesters)
- Delivery : Online (low residency)
- Tuition : $933 per credit
- Financial aid: Loans, Grants, scholarships, work-study
- Acceptance rate: 84.4%
- Location : Laurel, MD
Northcentral University, School of Technology
Doctor of Philosophy in Cybersecurity (PhD-CY)

Northcentral University is a regionally accredited university that offers many educational programs for students all over the world with one-on-one mentorship. Its PhD cybersecurity degree has a special emphasis on global security issues and covers international laws and multicultural elements.
- Courses : Global cybersecurity demand, securing globally distributed infrastructure & support, and governance, audit, compliance & risk
- Credits : 60
- Duration : 40-44 months
- Delivery : Online
- Tuition : $1,094 per credit
- Financial aid : Grants, loans, veteran benefits, and third-party scholarships.
- Acceptance rate : 93%
- Location : San Diego, CA & Scottsdale, Arizona
University of Colorado – Colorado Springs, College of Engineering and Applied Science
Ph.D. in Security

University of Colorado, Colorado Springs has partnerships with several defense departments, semiconductor manufacturers, and other prominent institutions, thanks to its strategic location. Though students must conduct the majority of the coursework for this doctorate degree in cyber security on-campus, a provision permits some online courses.
- Courses : System administration & security, applied cryptography, and advanced system security design.
- Delivery : On-campus
- Tuition : $918.83 per credit
- Financial aid : Scholarships, student employment, and loans.
- Acceptance rate: 89.6%
- Location : Colorado Springs, Colorado
Northeastern University
Cybersecurity, Ph.D.

Northeastern University promotes a co-operative education philosophy with a blend of classroom learning and professional experience. This cybersecurity PhD program offers the opportunity to conduct research in specialized facilities and labs, including the Cybersecurity & Privacy Institute and International Secure Systems Lab.
- Courses : Software vulnerabilities & security, computer hardware security, and machine learning in cybersecurity & privacy.
- Credits : 48
- Tuition : $1,532 per credit hour
- Financial aid: Scholarships, fellowships, assistantships, and company sponsorships.
- Acceptance rate : 20.5%
- Location : Boston, Massachusetts
Dakota State University
Cybersecurity, DSc

Dakota State University is known for its specialization in computer education-related programs. Its doctorate in cyber security is delivered through a combination of various distance education methods and a handful of on-campus seminars. You can apply for the program even if you don’t have a master’s degree, but you’ll need to complete an additional 27 credits.
- Courses : Full scope security testing, cyber security research, and security software engineering.
- Credits : 61
- Duration : 3 years
- Delivery : Online (plus on-campus seminars)
- Tuition : $210.80 per credit hour
- Financial aid: Grants, work-study, and loans.
- Acceptance rate: 83%
- Location: Madison, SD
Purdue University, The Center for Education and Research in Information Assurance and Security (CERIAS)
Interdisciplinary Ph.D. Program in Information Security

Purdue University was ranked in the top 10 most innovative universities in 2022 by the US News & World Report. This interdisciplinary cybersecurity PhD program covers ethical, political, and philosophical courses, to provide insight into technology policy issues and information ethics.
- Courses include: Information security, advanced network security, and modern ethical theories.
- Credits: 60
- Delivery: On-campus
- Tuition: Refer tuition calculator
- Financial aid: Fellowships, teaching assistantships, and research assistantships.
- Acceptance rate: 67.2%
- Location: West Lafayette, IN
Nova Southeastern University, College of Computing and Engineering
Ph.D. in Cybersecurity Management

NSU is considered one of the National Centers of Academic Excellence (NCAE) in cybersecurity. To qualify for this school’s PhD program in cybersecurity, you’ll need to have either a bachelor’s or master’s degree in the field. The school also offers a direct BS to PhD pathway.
- Courses : Fundamentals of cybersecurity, information security governance, and human-computer interaction.
- Credits : 51 minimum
- Delivery : Hybrid
- Tuition : $1,282 per credit hour
- Financial aid: Fellowships, scholarships
- Acceptance rate: 76.2%
- Location : Fort Lauderdale, Florida
St Thomas University
Doctor of Business Administration in Cyber Security Management

St. Thomas University is a non-profit Catholic university that emphasizes global and cultural diversity. Its doctorate of cybersecurity program lets you choose one of three research options: traditional dissertation, action research, and article dissertation.
- Courses : Cyberlaw, policy & security, cyber security risk management, and information ethics.
- Duration : 1.5 years plus dissertation
- Delivery : On-campus, online, and hybrid options
- Tuition : $1,029 per credit hour
- Financial aid: Scholarships, grants, loans, and work-study.
- Acceptance rate: 59.6%
- Location : Miami Gardens, FL
George Mason University, Volgenau School of Engineering
Information Technology Ph.D. (Information Security and Assurance (ISA) Concentration)

George Mason University is a public research university with an emphasis on sustainability that was ranked the most diverse university in Virginia by the US News & World Report 2018. Its PhD program in Information Technology offers a concentration in Information Security Assurance (ISA) covering cybersecurity subjects.
- Courses : Secure software development, security protocol analysis, and security experimentation.
- Credits : 72 minimum
- Tuition : $663 per credit
- Financial aid : Grants, work-study, and loans.
- Acceptance rate: 89.2%
- Location : Fairfax, Virginia
What are the Prerequisites for a PhD in Cybersecurity?
Most PhD programs in cybersecurity require a master’s in computer science or a related field. Other specific requirements vary depending on the program, but you’ll typically need to submit the following in your application:
- Personal Statement and/or research proposal
- Academic resume
- Letters of recommendation
Check individual requirements for each school you’re considering well in advance of the application cut-off date. These programs can be competitive, so give yourself plenty of time to put together the strongest application you can!
Preparing for a Cybersecurity Doctorate Program
The best cybersecurity doctorate programs can be intensive and competitive. Therefore, it’s a good idea to prepare before the program even starts – this can give you the edge you need to excel in the program!
Of course, your previous studies provide the foundation for your doctorate. An internship in the field can also help you to build useful skills and knowledge, especially when it comes to the latest trends Likewise, participating in cybersecurity competitions or getting a cybersecurity certification can be highly advantageous.
However, the best thing you can do to prepare for a cybersecurity doctoral program is to build your network in the sector. Join professional organizations and mingle with industry folks to gain insights into the field. You can also use social media platforms like LinkedIn and Twitter to enhance your networks.
Related Reading: Best Master’s in Cybersecurity Programs
Why Get a Doctorate in Cybersecurity?
A doctorate in cybersecurity allows you to develop high-level skills and knowledge on preventing and analyzing security breaches, as well as formulating strategies to manage them. It is a valuable qualification that will qualify you for top jobs at some of the best organizations, with attractive remuneration.
When choosing the best cybersecurity PhD program for you, consider the school’s reputation and its accreditation. Also, look at the courses offered, as cybersecurity involves various specializations. You should also consider your budget in the context of each program’s tuition, fees, and financial aid offered.
Finally, where is the program located? Is it offered on-campus, offline, or in a hybrid program? These factors will affect your ability to balance your study with work and personal commitments.
Jobs and Salary Prospects for Doctors of Cybersecurity
Some of the common roles and median annual salaries for graduates with a PhD in cybersecurity include:
- Cybersecurity Engineer – $125,816
- Information Security Manager – $96,406
- Chief Information Security Officer (CISO) – $124,405
- Security Architect – $111,433
- Security Director – $105,907
Key Takeaways
You may not find as many options for a PhD in cyber security as other fields. After all, it’s a specialized program. However, you’ll find a few solid top cybersecurity PhD programs that give you the opportunity to learn from top research institutions and faculty.
If you’ve found this round-up of the best PhDs in cybersecurity helpful, take a look at our guides to the best online Master’s in Computer Science and online PhD Computer Science programs .
PhDs in Cybersecurity FAQs
What is the average cost of a phd in cybersecurity.
Costs vary depending on the school, program length, and delivery (on-campus or online). Usually, a PhD in cybersecurity can be anywhere between $30,000 to $100,000.
Is a PhD in Cybersecurity Worth it?
A PhD in cybersecurity is valuable because it will qualify you for some of the most in-demand and well-paid jobs available today. According to the BLS , jobs for information security professionals are estimated to grow by 33% over the next decade, significantly more than the national average.
Can You Get a PhD in Cybersecurity?
A PhD in cybersecurity is a specialized degree, but today, many universities offer it. Several programs are delivered on-campus, online, or in hybrid formats.
How Long is a PhD in Cybersecurity?
A PhD in cybersecurity can take from 3-7 years to complete. This will depend on the program, as well as individual factors such as whether you choose to study part-time or full-time.
What Can You Do with a PhD in Cybersecurity?
A PhD in cybersecurity will equip you to work for leading organizations as a CISO (Chief Information Security Officer), information security manager, or security architect. You’ll also be qualified to conduct research or work as a professor in cybersecurity or a related field.
How Many Credits are Required for a PhD in Cybersecurity?
You’ll typically need 60 credits to complete a cybersecurity PhD. However, this varies depending on the specific program or university.
What Kinds of Exams are Required During a PhD Program?
Unlike most undergraduate programs, a PhD degree relies heavily on coursework and, in particular, a main dissertation or thesis. However, you’ll still have to complete some exams.
Usually, there are three kinds of exams:
- A qualifying exam that occurs earlier in the program.
- A preliminary exam that proves the candidate’s readiness to start the dissertation/research.
- The final exam for the candidate to defend their dissertation/research work.
How Do You Choose a PhD in Cyber Security Program?
You should consider faculty experience, networking opportunities, available funding, accreditation, and alumni statistics before choosing a PhD in cyber security program.

Lisa Marlin
Lisa is a full-time writer specializing in career advice, further education, and personal development. She works from all over the world, and when not writing you'll find her hiking, practicing yoga, or enjoying a glass of Malbec.
- Lisa Marlin https://blog.thegradcafe.com/author/lisa-marlin/ 12 Best Laptops for Computer Science Students
- Lisa Marlin https://blog.thegradcafe.com/author/lisa-marlin/ ACBSP Vs AACSB: Which Business Program Accreditations is Better?
- Lisa Marlin https://blog.thegradcafe.com/author/lisa-marlin/ BA vs BS: What You Need to Know [2024 Guide]
- Lisa Marlin https://blog.thegradcafe.com/author/lisa-marlin/ The 19 Best MBA Scholarships to Apply for [2024-2025]
Best Master’s in Cybersecurity Programs in 2024
Thegradcafe and jobbio join forces to connect top talent with great companies, related posts.

- Applying to Big Tech This Year? Here’s How to Ace It.

- 73% of job seekers believe a degree is needed for a well-paying role–but is it?

Tech Talent Crunch: Cities with More Jobs Than Workers

The Most Under-Rated Career Advancement Tip for 2024

Top 5 Best Psychology PhD Programs in 2024

Good News For Early Careers: Skills-Based Hiring is Surging

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Recent Posts
- 12 Best Laptops for Computer Science Students
- Is a Master’s Degree Worth It? [2024 Guide]
- Graduate Certificate vs Degree: What’s the Difference? [2024 Guide]

© 2024 TheGradCafe.com All rights reserved
- Partner With Us
- Results Search
- Submit Your Results
- Write For Us
Online PhD in Cyber Security Degrees
Cybersecurity Degrees » Online Cybersecurity Degree Programs » Online PhD in Cyber Security Degrees
Consider a sponsored online program currently accepting applicants.
Click to see sponsored 100% online cybersecurity programs currently taking applicants for 2024 .
Doctorate-level degrees in cybersecurity provide advanced knowledge and valuable research opportunities to professionals that are looking at some of the highest positions in their industry. This type of education is also extremely valuable to professors and researchers that are looking to continue their studies even after the completion of this program. These further studies will lead to academic research papers and innovation in the field of cybersecurity.
Why consider a doctorate level cyber degree?
Obtaining a Doctor of Philosophy, or PhD, gives working professionals the skills needed to research and develop new security measures and the expertise to maintain the information technology sector of an organization.
Having the ability to do this online is convenient for those that are looking to gain an education while continuing their career path, but there are many programs that require on-campus residencies to prepare students or to present their final dissertations. Various degrees will emphasize either practical solutions to cybersecurity issues or finding new innovations through theory and historical development of protecting vital information.
What Can You Do With a PhD in Cyber Security?
Receiving the high-level graduate degree within cybersecurity opens up the entire information technology industry. There is a significant need for experts that can fend off data breaches and internet attacks to a company's network and retrieve sensitive information, such as personal client medical records or consumer transactions with exposed payment methods.
Ensuring that communication is secure has only become more important as people continue to rely on the transfer of information on various devices and apps constantly every day.
There are variations of the doctorate that students can study to receive specific education, and it revolves around the solution to industry problems within the cybersecurity. Those receiving the discipline directly will typically apply practical solutions directly to the company they represent. A Doctor of Philosophy, or PhD, may explore specific topics in network security or computer science, and education revolves around theory and how to find solutions to issues like cyber attacks through research and development.
After completion of a doctoral program, graduates should be able to solve complex issues within the company or organization they represent. They have gained the advanced and expertise knowledge in a particular sector and should be able to deal with any cybersecurity issues that arise. Ultimately, their goal is to improve cybersecurity systems and to help them protect organizations more efficiently on a national and/or global scale.
Online PhD in Cyber Security Degree Availability
Many online-based institutions that offer programs within computer science and cybersecurity also feature accredited doctorate degrees. Students can expect to find disciplines directly in cybersecurity or in a similar field, such as information assurance or security in information technology. Even though the curriculum may be fully available online, each institution has their own unique requirements when it comes to presenting final dissertations or holding on-campus residencies.
When reviewing online programs, it is important to consider institutions that have been designated as a National Center of Academic Excellence by the Department of Homeland Security and the National Security Agency. This shows that the program has been reviewed alongside a rigid criteria to ensure that students are fully prepared to enter into the field of cybersecurity. Programs hold accreditation in specific categories, such as cyber defense education, cyber defense research, and cyber operations.
What to look for in a Doctorate program
There are very few programs available online where students can fully complete a PhD within cybersecurity. Many programs require the student to complete on-campus residencies that will give them the opportunity to meet faculty members and students. During these times, they may also work on their dissertation, and they must complete a defense of their dissertation in front of faculty members to show their expertise on the particular topic.
Choose a research discipline
While there are a limited amount of programs that specifically have a discipline in data science, this can often be found as a specialization within disciplines such as Computer Science or Computer Engineering. Other similar concentrations include Information Assurance, Information Systems Security, and Digital Forensics. Information Assurance focuses on the validation and authenticity of data within an organization, and Digital Forensics focuses on the investigative process to solve digital-based crimes in a court of law.
Be prepared for some online courses but on-campus requirements
Students should prepare for online coursework that blends with on-campus requirements if they are considering a doctorate degree with an online format. An alternative to this process is finding an online Master's degree in a similar discipline that can be used to count toward the PhD. There is plenty of overlap in these programs, and this flexibility may allow for students to switch over from a Master's degree to a PhD with high academic merit.
Online Requirements and Expectations
Most PhD programs will require the student to meet on-campus at certain times of the program, such as once per year, but these are not lengthy requirements to satisfy. Residencies will typically last from a weekend to a full week and mostly consist of the student working on their dissertation. Any lab sessions or courses that require application of what is learned can generally be accomplished in a virtual setting or at the professional's place of work if applicable.
In order to complete online courses, students will need to verify that they have the proper setup to run the learning management system used by the university. This typically requires a Windows or Mac operating system that runs on a desktop or laptop computer. For some course materials, this can be accessed by a mobile device, such as a smartphone or tablet, but not all work can be completed in this format.
Additional technical requirements include having access to high-speed internet in order to download or stream on-demand lectures. A webcam and microphone may be required for courses that require students to attend lectures on a live basis. Other applications, such as Microsoft Office, web browsers such as Google Chrome or Mozilla Firefox, anti-virus software, and Adobe Acrobat Reader may be needed depending on the university.
What Are the Steps to Getting This Degree?
Doctorate degrees for cybersecurity generally require anywhere from 60 to 80 credit hours to complete, which can span from three to five years. Most of the program is dedicated to core courses and a concentration in cybersecurity if available. There may be some credit hours needed for electives that may either be part of the discipline being pursued or free electives to customize the program to fit an industry or particular career needs.
Around a third of most PhD programs will feature dissertation requirements. A dissertation is a research project with a specific focus on a topic in cybersecurity, such as a problem that is plaguing a certain industry. Once a topic is suggested and approved by a program faculty member, students are able to pursue the writing project and they will have to defend their dissertation at the end of the program.
In addition to the dissertation, multiple exams may also be needed to further expand on all the skills and concepts learned in the program. A qualifying exam will ensure that students are able to continue on with the PhD and begin their process with the dissertation. The comprehensive exam tests all the skills and concepts that the student has learned, which is usually completed at a separate time than the dissertation defense.
It is not a requirement to have a Master's degree for many computer science-based doctorate programs. Students can typically transfer over their credit from a Master's program if they choose to pursue a doctorate degree at a later date. This can cut the doctorate program nearly in half for students, decreasing the time commitment required and academic costs.
To gain the PhD degree at the end of the program, students will need to pass all examinations and successfully defend their dissertation. Many programs require that the student also maintains at least a 3.0 GPA during their studies. With many courses providing advanced topics, students must maintain a high level of academic achievement in order to successfully complete the program.
Admission Requirements
Getting into a doctorate program requires the completion of a Bachelor's degree from an accredited institution with high academic marks. Typical requirements for a Master's degree are holding a 3.0 cumulative GPA in their undergraduate studies, or this was achieved in the final 60 credit hours of their studies. For a PhD, this can jump to a GPA requirement of 3.3 or 3.5 overall.
Prospective students are not limited to this GPA requirement, but they may only receive conditional admittance into the program. This means they will need to achieve high marks in the first portion of the program in order to continue pursuing the degree. A slightly lower GPA than the requirement can be offset by higher Graduate Record Exam (GRE) scores or additional professional experience in cybersecurity.
Typical Document Requirements for Submission
Depending on the university, applicants will need to send their unofficial or official transcripts that showcase their accomplishments in higher education. If unofficial transcripts are only needed with the application, sending official transcripts are usually required once the student has been admitted into the program. This includes all academic work at various levels, including any certifications that have been earned.
Applicants should send their most updated resume to the university that showcases all of their prior work history and internship experience gained in other programs. Some programs may require a certain amount of work hours to get into the program, or students may need to complete this prior to graduating from the doctorate program. Resumes should include any accomplishments or
Multiple letters of recommendation are typically needed to verify that the student has high levels of accomplishment in this field. They may require some of the letters to be from an academic professor, but another source can be prior supervisors or managers in a professional work place. Applicants should review what specific requirements are needed with the letters of recommendation as they vary based on institution.
Personal essays are a common requirement in the application process, with potential candidates listing out why they have chosen a particular institution for their studies and what career goals they have in the cybersecurity field. These essays may also go into detail about any accomplishments within an industry that the individual has achieved.
Full-Time Versus Part-Time Enrollment for a PhD Degree
Doctorate degrees are often at least twice the length of a Master's degree program, meaning that students typically need between three to five years to complete their studies on a full-time basis. It is recommended by many schools that students pursue these graduate studies on a full-time basis due to the complexity of course content and the amount of time it takes to complete the dissertation and various assignments.
Many PhD degrees are geared for full-time study and may have some complications for those that are looking to pursue the program on a part-time basis. It may be difficult to focus on research projects without full concentration and may impact the quality of the research accomplished. Even on a part-time basis, there may be too much to balance when accomplishing high-level studies and continuing as a working professional.
Instead of completing the PhD along with a part-time job, students may consider looking at graduate assistantships or other positions within the university. This allows individuals to pursue their degree while completing various tasks for professors for a certain amount of hours per week. By accomplishing this, students will receive part or all of their tuition expenses cut and a stipend to pay for other needs.
Part-time study may be accepted at the institution, but students will have to consider the length of time it will take to complete their studies. This will increase the overall costs of the program with additional fees given out for extra years pursuing their degree. There is also a time limit at most universities, requiring students to complete the doctorate program in seven or eight years on average.
Other problems can emerge with completing the program on a part-time basis. In addition to the difficult coursework that requires plenty of focus, it may be a problem to balance struggles that exist in current employment and trying to complete advanced coursework at the same time. There are also limitations in communicating with other faculty members and students for additional help or working on group projects.
Examples of Doctorate Degrees
It is also important to determine that the program has been verified as an accredited institution and the university has been designated as a National Center of Academic Excellence (CAE) from the National Security Agency (NSA) and Department of Homeland Security (DHS). This means that the curriculum has met rigorous requirements under different security topics, such as cyber defense and cyber operations.
Regional accreditation is based on where the university is located and remains a standard when institutions are looking at students for their graduate programs. The six states based in the New England region are accredited by the New England Association of Schools and Colleges. The Southern Association of Colleges and Schools reviews a number of places in the Southeast and along the East Coast, including the states of Florida , North Carolina , Texas , and Virginia .
Online PhD Degrees for Cyber Security
Northcentral university.
This online college based in San Diego, California, has a number of doctorate programs available in technology, including the Doctor of Philosophy in Technology and Innovation Management. Within the doctorate program, there are six specializations to consider, including Cybersecurity. Students should expect to complete the program in the span of 50 months.
A total of 60 credit hours are needed to fulfill degree requirements, and with most courses being worth three credit hours, 20 courses will be taken in the program. 48 credit hours must be completed at the university, which allows for 12 total credit hours to be transferred into the program. Students must complete all courses while maintaining a 3.0 cumulative GPA.
Courses that students can explore in the main program include Computer Networks and Mobile Computing, Statistics with Technology Applications, and Technology Policy and Strategy. The latter course focuses on legal analysis in network security and gives students case study to review and policies that organizations must follow based on federal guidelines. 18 total credit hours are needed for the Cybersecurity specialization, with courses such as Cyber Forensics and Advanced Risk Management.
One of the unique student services the university offers is the Dissertation Completion Pathway, which gives those that were not able to complete their dissertation elsewhere to do so at their institution. This is a shorter program that requires at least 23 credit hours.
Capitol Technology University
Gaining a Doctorate degree in Cybersecurity through the technology institution prepares students for executive roles within the private sector and any government level. There are various electives that can customize the program and give specialty skills and knowledge within the security of health care, information assurance, cybersecurity software development, and strategic management for intrusion detection and eliminating vulnerabilities.
Up to 66 credit hours are needed to complete the curriculum at Capitol Tech, which is based in the Greater Washington DC area and is also available online. Along with dissertation preparation, some courses include Information Assurance Consulting, Advanced Mixed Methods Research, and Special Topics in Human Resource Management. There is a 16-week course that prepares students for the doctoral degree with specialized research for the career path they are pursuing.
Prospective students can apply for the doctorate degree in cybersecurity for the fall and spring semesters. An essay of at least 1,000 words that covers what the student plans to do within the cybersecurity field. Applicants must submit the essay with the application form and a fee, official transcripts, updated resume, and multiple letters of recommendation. More information may be necessary based on the college’s review.
Nova Southeastern University
The College of Computing and Engineering provide a PhD in Cybersecurity Management, which requires 67 credits to complete and is offered in a hybrid format. This means students will be mostly completing coursework and generally interacting with students and faculty members online, but they will have physical meetings once per term at the Fort Lauderdale campus. These are required meetings for students.
Examples of core courses that students will complete include Information Security Risk Management, Secure Systems Analysis and Design, and Human-Computer Interaction. 24 credits are reserved for dissertation studies, and students will also need to complete two doctoral research studies within information assurance. Some of the goals the university has for their graduates are to gain advanced knowledge within cybersecurity and to be prepared to lead and manage cybersecurity teams with strong communication skills and being fully competent of the ethics required.
Students looking for a fellowship opportunity to satisfy financial needs and gain additional experience may be eligible for one of six positions offered by the school. Applicants must submit a reference letter, hold at least a 3.0 cumulative GPA, and are going into a career that involves teaching or research. Recipients are not able to hold a job so they can commit their time to education and research, but the award provides tuition assistance for the duration of the program.
Dakota State University
The Beacom College of Computer and Cyber Sciences offers the Doctor of Philosophy in Cyber Operations, which focuses on advanced topics in cybersecurity. Graduates from the program have gone on to work at organizations such as the Central Intelligence Agency, US Army Intelligence and Security Command (INSCOM), and Carnegie Mellon’s Software Engineering Institute.
Along with the core curriculum and research-driven courses that account for 24 total credit hours, students will need to complete three credit hours of on-campus research seminars. Meeting faculty members, determining a dissertation topic, and finishing dissertation defense is accomplished in this requirement. 25 credit hours are geared toward the dissertation itself, and the remaining nine credit hours are for customizable electives.
Some courses are only available at certain times of the year. For example, dissertation work is available all year long, but Dissertation Preparation is only available in the spring on an annual basis. All students must maintain a 3.0 cumulative GPA, and no more than two C grades are allowed in the entire curriculum or the student will be put on academic probation and eventual dismissal if the grades do not improve.
In order to get into the program, students must hold a Master’s degree from an accredited institution with a 3.0 cumulative GPA or higher. GRE scores are required in the admission process, but these are waived if the student has accomplished a 3.25 cumulative GPA in their Bachelor’s degree. Entry is only available for the fall semester into this program, so applications must be received by May 1st each year.
Colorado Technical University
Students can pursue the Doctorate of Computer Science with an emphasis in Big Data Analytics or Cybersecurity and Information Assurance. This is a program with an expected time of at least three years to complete. There are multiple start times throughout the year providing flexibility for students to enter into the program.
While the curriculum is fully available, there are in-person residencies that are required – two residencies are needed for this program and they are held quarterly in the Denver area. This gives students an ability to meet with other peers in their classes and faculty members one-on-one and there are various events that will aid in dissertations required for the student to complete. Students can maintain their schedule and join discussions with the CTU Symposium mobile app.
The 100-credit hour curriculum consists of the residencies, many levels of Doctoral and Dissertation Research, and various advanced topics within cybersecurity, such as Foundations of Digital Systems Security, Enterprise Security Architecture, and Principles of Research Methods and Design. At the conclusion of the program, students will be presenting their final dissertation and must be approved by a faculty supervisor.
Capella University
An online Doctor of Information Technology (DIT) with emphasis in Information Assurance and Cybersecurity can be obtained through the Minnesota-based institution. Students can also elect to take courses at the Minneapolis campus or pursue a combination of both. The curriculum is divided up into eight core courses and four specialization courses, along with various dissertations and three residency requirements, all requiring four days of attendance.
Two different IT degrees
Capella offers two versions of information technology degrees at this education level – the DIT and the Doctor of Philosophy in Information Technology. The DIT prepares students to solve business problems and to apply what they have learned directly into their career. Having a philosophical approach in the other program explores new theories that can be used to solve these issues instead. While both programs have a difference in solution, there is overlap in the specialization of assurance and cybersecurity.
DIT specialized on cybersecurity
The Doctor of Philosophy in Information Technology features a specialization in Information Assurance and Cybersecurity, giving students the capability to learn advanced knowledge in the field. In addition to five specialization courses, students complete a comprehensive exam that reviews all of the material they have learned, a dissertation spanning a large portion of their studies, and three on-campus residencies.
Typical courses you may take
Courses in the specialization include Enterprise Security Risk Management, Network Security Advances, and System and Application Security Advances. These topics cover the advancement of security and how this has impacted their implementation into company networks. Students do not have the availability to transfer in these courses for the specialization and must be taken through the school. Some specialization courses must be completed through this campus, including System and Application Security Advances and Enterprise Security Risk Management. The latter course has students review academic research and professional reports on risk modeling that impacts managerial decisions. Security advancement courses focuses on improvements in the field and the advantages of improving these processes with new available technology.
What each program is like at Capella
All three on-campus residencies focus on dissertation research, which first begins through an overview in an online course and the student builds upon their research when they meet faculty members and other students. The goal of the dissertation is to build critical thinking skills and the ability to communicate with others to help improve the dissertation, which requires significant research after determining a topic.
GuidedPath is a unique resource available to students that helps them get through the doctorate degree in a more focused process online. They will take between one to three courses during each of the four quarter terms available, which requires 10 weeks to complete. Based on availability and schedule, students will take the courses they have time for and only pay for what they are pursuing.
University of Rhode Island
The College of Arts and Sciences offers a Doctor of Philosophy in Computer Science, which can utilize the graduate certifications available in Cyber Security and Digital Forensics. All courses are available online, with lectures streamed on demand for students to learn at any time of the day, and all lab sessions are completed through the cloud-based infrastructure.
Examples of courses that can be completed and applied to the doctorate degree include Advanced Topics in Network and Systems Security, Advanced Incident Response, and Penetration Testing. Many courses will only be available at certain times of the year, and courses must be followed along a certain path in order to meet prerequisites for the more advanced courses.
Coursework is typically distributed each Friday, meaning students will have a week to complete their assignments and submit them by each Friday, and new coursework will be available on that day. Students have the capability of studying on their own time as long as they continue to meet deadlines.
Applications are accepted for these programs throughout the first half of the year to get admission for the fall, which is required for graduate certification in Cyber Security. Students must have a Bachelor’s degree with an undergraduate cumulative GPA of 3.0 or higher. There is no requirement to submit GRE scores, but other additional needs include two letters of recommendation and a statement of purpose.
On-Campus PhD Degrees for Cyber Security
University of tennessee.
The Tickle College of Engineering offers a few options for cybersecurity studies at the Knoxville campus location. One of the advanced programs is a Doctor of Philosophy in Computer Engineering, with a concentration in Cybersecurity. The amount of credit hours needed depends on if the student has taken a Master’s degree or hold prior academic work in the same discipline or related, such as computer science.
At least 72 credit hours are needed for students that only have a Bachelor’s degree or simultaneously completing a Master’s degree in a similar field through the university. This truncates to 48 total credit hours if they already have a Master’s degree. At least 24 credit hours are earned through taking dissertation courses and completing the research and writing requirements.
The comprehensive exam features both a written and oral segment, which connects with the dissertation, but may have additional writing requirements. Students must have a strong understanding of the topic they have studied and can thoroughly explain many aspects of it while demonstrating competency in communication and critical thinking. At least six months need to separate the comprehensive exam and defense of the dissertation.
Admission requires outstanding work in a Bachelor’s degree for students to be able to jump from the undergraduate program to the PhD program. GRE scores are needed for the admission process and should have been obtained in the last three years. For students that have a Master’s degree, up to six credit hours from courses that match the 400-level and above can be transferred into the program.
Arizona State University
Through the School of Computing, Informatics, and Decision Systems Engineering, students can complete the Doctor of Philosophy in Computer Science with a concentration in Cybersecurity. Students will complete five core courses that explore different aspects of computer science, and there is no ability to transfer credit for those courses unless they have already taken the courses at Arizona State University. Students do not have the capability to duplicate credit between the concentration focus and the core curriculum.
Nine total credit hours will count toward the Cybersecurity specialization. There is an overview of Information Assurance, then students will pick two of the following three courses: Advanced Computer Network Security, Applied Cryptography, or Software Security. 24 total credit hours will go toward both the research and dissertation portion of the curriculum.
Admission requirements include submitting a personal statement that details professional goals and why they are choosing this particular program. It should also feature any research experience that the individual has accomplished personally. In addition, there should be three letters of recommendation validating these accomplishments, from prior professors or professionals in the industry the individual has worked in.
Other needs to get into the program include holding a minimum cumulative 3.5 GPA or higher in the last 60 credit hours of work from the Bachelor’s degree, and this should be similar to the Master’s degree overall if they hold one. Up to 30 credit hours within a different graduate program, such as a Master’s degree, can be used to account for some credit if approved by the program.
Sam Houston State University
A Doctor of Philosophy in Digital and Cyber Forensic Science is available exclusively on campus for students that are looking at cybersecurity careers at the executive level or academic research at an institution. Topics include understanding network and mobile device forensics, ethical and legal issues in cybersecurity, and the basic principles of this field. 85 total credit hours are needed to complete the program for students that only hold a Bachelor’s degree.
Breaking the curriculum down, 52 credit hours are part of the core academic curriculum, 15 credit hours are gained through the dissertation, and the remaining 18 credit hours are for the internship and customizable electives. Examples of elective opportunities include Cloud Computing Forensics, Cryptography and Steganography, and Social Network Forensics.
Counting for six total credit hours, the internship will require 10 weeks of full-time commitment. This is another process to apply what the student has learned to real-time situations, giving them an additional opportunity and potential to network with an organization for improving job potential.
In order to gain admittance into the program, applicants must hold at least a Bachelor’s degree in a similar field from an accredited university, and they must have obtained a 3.5 cumulative GPA or higher. Three letters of recommendation are needed for verification, with at least two of them from faculty members. Other needs include a personal statement with a maximum of 1,000 words, updated resume, GRE scores, and a potential interview may be conducted.
University of Colorado-Colorado Springs
The College of Engineering and Applied Science offers the Doctor of Philosophy in Security, which has been verified by the NSA and DHS as a CAE in Information Assurance Education. In graduating the program, individuals will become an expert in the topic they decide to develop a dissertation on, and they have been able to improve upon their communication skills when presenting findings or working with others collaboratively.
60 total credit hours are needed to complete this program, and half of that credit must be completed with courses that are at the 5000 level or higher. There is an opportunity to transfer in 24 credit hours if the student has completed the Master’s degree previously. Half of the curriculum is dedicated to dissertation development and presentation.
Applicants should have at least a Bachelor’s degree from an accredited institution with at least a 3.3 GPA, and those entering the program with the completion of the Homeland Defense graduate certificate must also have the same GPA requirement. Additional admission materials include having three letters of recommendation, latest resume, and will need GRE scores if they did not complete their education at an accredited university.
Courses that students can choose in this program include Applied Cryptography, Advanced System Security Design, and System Administration and Security. At least three months of cyber operations must be completed in the form of training, internship, or already established professional work. This can be substituted with the completion of a Certified Information Systems Security Professional (CISSP) certification.

Typical Coursework for a PhD Degree
Principles of cyber security.
Explores the basics of cybersecurity features at the executive and management level of an organization, including the latest innovations in the field and various security measures that can be added into information systems. In some cases, students that have already completed a Master’s degree in the cybersecurity field may be able to skip this course as it is also frequent at that education level.
Advanced Risk Management
Analysis of theory when defending information systems in a more complex environment, and what practices are used when implementing these solutions in an organization. Students may learn how to audit these security measures to determine their accuracy and what needs to be improved upon to avoid certain attacks. This can help in preparing recommendations and consider different strategies in established cybersecurity practices.
Security Software Development
Having security measures in place on network servers and database management systems are key to preventing intrusions, but software can also be manipulated and compromised without security. This course looks into the different ways of implementing this type of protection in the software development process. Students may also learn how to identify rogue activities within software to identify potential threats.
Critical Infrastructure
A national government-focused course that emphasizes security measures that are taken to protect the United States’ critical infrastructure. This includes the important industries of public health, transportation, telecommunication, agriculture, electricity, and more. Topics may include the strengths and weaknesses of prior security implementation and how future innovations will change these procedures.
Quantitative and Qualitative Research
Common research methods when analyzing reports and writing the dissertation includes using quantitative and qualitative information. Students will understand the differences between these analysis methods and where to best apply them in their reports. Quantitative data focuses on specific numbers and measurements, while qualitative data focuses on more subjective information that explains these figures.
Intrusion Detection
Professionals must be able to react quickly when an attack occurs on an organization’s network, mitigating disaster and sensitive information that could be compromised. Popular topics in these courses include the various tools that are used in scoping out problems and eliminating them, how to detect vulnerabilities earlier to prevent these situations, and disaster recovery processes once the damage occurs.
Penetration Testing
One of the most popular and impactful ways to determine if a strong security system has been implemented is to mimic similar attacks in a controlled environment. Penetration testing, which can be a position on its own within a cybersecurity team, oversees this event and determines the effectiveness of security that is protecting valuable information.
Cyber Operations
Institutions designated as a CAE and holding an emphasis in cyber operations will often have courses that provide a general overview of the measures taken by security-driven organizations. Topics in these courses can range from the evolution of these processes, such as how to eliminate security threats on mobile devices and cloud-based computing, and the legal and ethical policies that can be implemented.
Dissertation Research
Many doctorate degrees will have courses that prepare students for dissertations, focusing on various studying methods, sources to consider, and helping them pick topics for a proposal that they will be able to defend when presented. These courses may go into creating an outline or framework for the dissertation and look at other example proposals to gain different perspectives or to criticize. Frequently, preparation courses will serve as the platform for students to submit their proposal.
Dissertation Preparation
Many PhD programs will emphasize the dissertation, allocating around one-third or a quarter of the curriculum to the dedication of preparing students for their dissertation writing. These courses may include how to find a topic that works for the researching project and an official process to send this idea in to faculty members, They may also be able to work with professionals in the industry that can help them further their analysis in the topic selected.
Dissertation Presentation
Immediately prior to graduation, students may have the requirement to meet in front of select faculty members to present or defend their dissertation. This process tests the vulnerabilities of the writing where the student should successfully defend what they have gathered. Any preparation classes for the presentation may focus on improving presentation material and studying further information to prepare for questions.
Information Assurance
This is the specific term used when managing and securing sensitive data within the organization’s network and system. Assurance of the information means that it remains confidential and can only be accessed by authorized parties. Many degrees will have this term within the discipline, and these courses can serve as an overview of information security and to become exposed to real-world situations.
Software Assurance
Doctorate studies will focus on the development and stability of cybersecurity software, with uses of identifying potential threat and analyzing risk. Students typically assess the performance of security software, measuring their stability and how well they protect systems from attacks, and various ways that it can be implemented into networks.
Applied Research Methods
Explores various research methods and how to perform them to help students with research for their dissertation and other studies. Topics may consist of how to read complicated information, creating visualizations from raw data or cleaning it for easier organization, surveying and interviewing subjects to gain perspective, and how to use software tools for researching. Coursework typically consists of researching and report writing to demonstrate proficiency in these skills.
Network Security
Courses covering network security at the doctorate level will have an in-depth look into history and various theories involving the revolutionary technology. Topics include the advancement of network security in the industry and how this impacts various organizational networks, the benefits and disadvantages of sending sensitive information online, and encryption methods to ensure that data is kept secure when being transferred from one place to the other.
Careers and Associations
Having a doctorate in cybersecurity means that a professional has explored theories and case studies within cybersecurity, giving them expert knowledge in the field that they customized their degree toward. This makes them beneficial as information security consultants in the organization they work for. They help review the network for any vulnerabilities and they will provide information on the latest technological innovations and how to implement them for a seamless transition.
In general, IT consultants help the organization gain perspective on the strengths and limitations of the department and aids in the improvement of management and supervising team members. They may recommend technological needs based on employee and client feedback, or creating reports based off performance data and expected outcomes should the organization improve these areas.
Higher education can also give graduates with professional experience an edge in becoming a director of information technology. One of the frequent requirements when managing the entire technology infrastructure of a company is to ensure that the network security is free from vulnerabilities and that there is a protocol in place in case intrusions take place. Directors will often make the final decisions in hardware and software additions and the coordination of teams and managers.
IT directors fall under the position of computer and information systems management through the US Bureau of Labor Statistics. Average salary for this position is is approximately $142,530 , with those working within finance and computer systems design receiving above the average. The top 10 percent receives over the $200,000 mark while the lowest 10 percent sees $85,380 when salaries are reviewed across the nation.
Tuition Costs for a PhD Degree in Cyber Security
Tuition rates will range widely based on the institution that a student selects to study their cybersecurity education, and if they are a resident in the state of the university. Smaller institutions or online-based colleges will generally be cheaper than more established institutions. When adding up full tuition for a full academic year, along with various student fees, full costs can be between $20,000 up to $50,000 per year.
For example, at Capella University, tuition for the PhD in Information Technology is $965 per credit, or $5,000 total in each quarter. The comprehensive exam and dissertation sessions are $2,895 per quarter. Unlike some programs, there is no capability to transfer credits into this program, so students will have to pay for the full tuition, which is 90 quarter credit hours.
Adding up the number of years it can take to complete a PhD program, it can be very costly to pursue this type of education. Luckily, there are many ways to bring these costs down in what essentially is an investment into a job opportunity that pays more than typical positions while just holding a Bachelor’s degree.
Ways to Lower PhD Costs for Students
If pursuing the program on a full-time basis, students can consider federal student loan options if they qualify and have any remaining funds from their prior education. Part-time education is generally not acceptable for federal student loans as this requires full-time enrollment and pursuing a certain number of credit hours in a given term. Personal loans provide another option to receive funding for school, but this may have considerably higher interest rates.
In some cases, an employer may pay for the employee to receive their PhD degree in cybersecurity. This requires a commitment from the individual to stick with the company for an extended period of time, and they will likely see an upgraded role in the organization if they successfully complete the program. If the individual leaves shortly after receiving the degree, they may be responsible for paying some of this tuition.
Assistantships are frequently the best opportunity for students to receive tuition aid for their education. These are competitive positions that can pay for some or all of a student’s tuition expenses, and provide additional stipends on a monthly basis, or in each term. Assistantships will require a certain amount of hours for students to complete tasks for faculty members in addition to their studies.
Scholarship Options for a PhD Degree
For students that have excelled in their prior academics, there may be an option to apply for a scholarship to cut down on costs. While there are few scholarships that pay for full tuition, this can provide some relief for students in multiple years of their education. In addition to rewarding those with solid academics, scholarships are also available for those in difficult financial situations or are part of an underrepresented demographic.
Some graduate college-based scholarships provide automatic entry for students that are administered into the program. Select students will receive an award simply based on being admitted into a high-level program. These are typically smaller awards that lower tuition rates and there are no restrictions for these opportunities.
For the majority of scholarships that are distributed by the school or an association that is promoting cybersecurity, students will need to submit a writeup that details why they are the best candidate for the scholarship and/or list the achievements that they have accomplished so far in their career. They must also submit proof of the criteria needed to receive the scholarship award.
Examples of Cyber Security Scholarships
The National Science Foundation has a Graduate Research Fellowship Program that is geared toward students that are going after graduate-level programs within the sectors of science, technology, engineering, and management – also known as the STEM field. A total of $46,000 is awarded to an individual, which provides a $34,000 three-year stipend and $12,000 deduction in tuition that is given to the institution.
The National Defense Science and Engineering Graduate Fellowship Program also provides aid for students that are pursuing a STEM field. Students can receive up to three years of educational aid, and it covers the tuition and provides a stipend. One requirement that students must uphold is working at a laboratory session with the Department of Defense, and they need to be able to accept the full awards.
Both of these scholarships not only require students to be in the STEM field, but they must be United States citizens or nationals to be eligible. They must show proof of citizenship when applying for these awards, and they must hold strong academic standing. Eligibility for the latter program opens up in the final year of undergraduate studies.
What Can You Do With a PhD Degree in Cyber Security?
When considering the pursuit of a doctorate degree, students must determine if it is worth the time and money for their cybersecurity career opportunity. Entry-level positions only require the completion of an undergraduate degree in this discipline, or a similar discipline such as computer science or information assurance. Advanced and senior positions can be obtained with a PhD, along with more research-focused positions in academia.
PhD degrees are geared for individuals that are looking at managerial and executive positions at industries that are looking to implement or improve their cybersecurity practices. They must understand advanced processes and be able to determine what they should do for their existing systems, or what is compatible with their information systems if they are moving to cloud-based solutions in the future.
Director positions review the analysis of network and computer security practices and make significant decisions on how the company should continue forward. They must follow the latest innovations in security measures that are being improved upon in order to keep their systems secure. It is important to keep the information technology sector updated with the latest security measures and to stay ahead of the latest hacking attacks.
Academic positions will offer more researching opportunities beyond completing the dissertation at the end of the PhD degree program. Further reports can help improve the entire field of cybersecurity when published in academic journals, or these can provide a specific focus within an industry, such as health care or the finance sector. They can also use this knowledge as a professor in a technology or engineering course within cybersecurity.
Career Opportunities
Looking at specific jobs in cybersecurity while holding a PhD degree, being a security engineer is a popular position to consider with the advanced knowledge needed in developing the architecture of an information system and making sure it is secure. These are more for advanced or senior positions that require numerous years of professional experience or hold advanced certification, like the CISSP, which is geared more toward individuals looking at management positions.
Another popular position is chief information security officer , which the job title can be slightly alternative based on the organization they are working at. Bigger enterprises will have specific designations for a CISO, but some smaller companies may only have a chief technology officer that deals with the security measures that are implemented into the organization.
When disaster strikes at an organization, the CISO is usually responsible for working with federal government or legal workers in order to determine what the next steps are needed after a data breach occurs. They are also responsible for moving forward with disaster recovery measures and working with any clients or employees that are affected. In addition, they are usually responsible for making final decisions on new implementations in the information system security processes.
According to the US Bureau of Labor Statistics , information security analyst make a mean annual wage of $104,210 across the United States. This is slightly higher for those working directly in computer systems design, which is geared for those with more experience in computer engineering and architecture.
At the higher spectrum of estimated wages in this position, workers are making an average of $158,860 among the top 10 percent. Some of the top states to consider when looking at the highest wages are New York, Virginia, and California. The highest state overall is New York with over 7,000 workers represented and over $121,750 being made on an annual basis.
In addition to the state of Virginia having the most employment opportunity in any state with over 15,000 employed, the annual estimated wage across the state is at $114,760. For the District of Columbia alone, there are 2,000 workers represented and estimated $119,160 made annually. This also makes the largest metropolitan area in terms of employment when adding in the cities of Arlington and Alexandria with Washington DC.
Doctor of Philosophy in Cybersecurity
Description of program.
The Doctor of Philosophy in Cybersecurity (PhD-CY) program takes an applied approach to cybersecurity theory and research. Students will get hands on experience, explore advanced topics, learn the very latest concepts, and prepare for anticipated risks. The degree is designed to prepare researchers and technology strategies applicable to leading positions in private and public sectors. Students will explore governance, compliance, leading frameworks, models, and standards to reduce threats and vulnerabilities. Students will build portfolio of valuable capabilities, addressing internal and external issues through the intelligent manipulation of data while completing their doctoral studies.
Click here for potential career opportunities using the PhD-CY.
Learning Outcomes
- Advance theory and practical applications of cybersecurity.
- Formulate cybersecurity governance, policy, risk, and compliance.
- Devise strategic thought leadership for challenges in cybersecurity architecture and operations.
- Assess internal and external threats and vulnerabilities to reduce organizational cyber risk.
- Evaluate tools, data, and processes to enhance protection and foster resilience.
- Facilitate the protection of critical information resources from current and future loss.
Basis for Admissions
Admission to Doctor of Philosophy in Cybersecurity program requires a master’s degree from a regionally or nationally accredited academic institution.
Degree Requirements
The University may accept a maximum of 12 semester credit hours in transfer toward the doctoral degree for graduate coursework completed at an accredited college or university with a grade of “B” or better.
The PhD-CY degree programs have the following graduation requirements:
- A minimum of 48 credit hours of graduate instructions must be completed through NCU.
- GPA of 3.0 (letter grade of “B”) or higher.
- Satisfactory completion of the PhD-CY university approved Dissertation Manuscript and Oral Defense completed.
- Submission of approved final dissertation manuscript to the University Registrar, including the original unbound manuscript and an electronic copy.
- Official transcripts on file for all transfer credit hours accepted by the University.
- All financial obligations must be met before the student will be issued their complimentary diploma and/or degree posted transcript.
Fundamental Competencies
All PhD-CY students are required to demonstrate competency in these areas:
- Graduate-Level Research Methods Competency– PhD-CY students are required to complete ( TIM-7221 and TIM-7225 ), OR ( TIM-7231 and TIM-7235 ), OR ( TIM-7241 and TIM-7245 ) at NCU
- Graduate-Level Statistics Competency – PhD-CY students are required to complete TIM-7101 - Statistics with Technology Applications at NCU.
- Computer Competency - Doctoral students are required to have computer skills necessary for completing a dissertation. Students must be able to prepare documents using advanced word processing skills (e.g., creation of tables and figures, headers and footers, page breaks, tables of contents, hanging indents). Students must use computer programs for the statistical analysis of data (e.g., SAS). Students must produce a computer-based presentation (e.g., PowerPoint) for their dissertation oral examination.
Dissertation Completion Pathway
The NCU mission is dedicated to assisting students in achieving their academic aspirations and helping them become valuable contributors to their community and profession. To support our mission, NCU now offers a dissertation completion pathway for students who have successfully completed their doctoral coursework and achieved doctoral candidacy at a previous institution but were unable to complete their dissertation. NCU’s Dissertation Completion Pathway (DCP) offers a unique opportunity for students to complete their doctorate in one of the doctoral programs offered at NCU (excluding the PhD in MFT, DMFT, DNP, and DHA). Students successfully meeting the entrance and application requirements will complete a minimum of 23 credit hours to earn their doctorate.
Click below for more information on the Dissertation Completion Pathway .
Time to Completion
NCU allows 7 years to complete all doctoral programs of 60 credits or less.
The median time to completion for this program is 44 months.
Time to completion varies depending upon the pace in which a student completes courses and the number of transfer credits accepted. As most NCU students are working adults, balancing educational, professional, and personal commitments, our academic and finance advisors will work with you to develop a program schedule that works best for your needs.
Students following the preferred schedule designed by the Dean for this program, and applying no transfer credits, can expect to finish in as little as 40 months.
Dissertation Process
Faculty assists each NCU Doctoral student to reach this high goal through a systematic process leading to a high-quality completed dissertation. A PhD dissertation is a scholarly documentation of research that makes an original contribution to the field of study. This process requires care in choosing a topic, documenting its importance, planning the methodology, and conducting the research. These activities lead smoothly into the writing and oral presentation of the dissertation.
A doctoral candidate must be continuously enrolled throughout the series of dissertation courses. Dissertation courses are automatically scheduled and accepted without a break in scheduling to ensure that students remain in continuous enrollment throughout the dissertation course sequence. If additional time is required to complete any of the dissertation courses, students must re-enroll and pay the tuition for that course. Continuous enrollment will only be permitted when students demonstrate progress toward completing dissertation requirements. The Dissertation Committee determines progress.
Course Sequence
The PhD program requires a minimum of 60 credits. Additional credit hours may be allowed as needed to complete the dissertation research. If granted, additional courses will be added to the student degree program in alignment with the SAP and Academic Maximum Time to Completion policies. Students who do not complete their program in accordance with these policies may be dismissed.
The PhD in Cybersecurity requires eight foundation/core courses, five specializations, two research, a pre-candidacy prospectus, and four dissertation courses for a total of 60 credit hours.
*Students select one pair of research methods and directed research courses based on their own research proposal.
The PhD in Cybersecurity requires the following courses for every specialization:
- TIM-7010 - Computer Networks & Mobile Computing
- TIM-8301 - Principles of Cybersecurity
- TIM-8305 - Cyber Risk, Contingencies, and Incidents
- TIM-8315 - Cyber Automation, Artificial Intelligence, and Machine Learning
- TIM-8330 - Advanced Risk Management
- Specialization Course 1
- Specialization Course 2
- Specialization Course 3
- TIM-7101 - Statistics with Technology Applications
- TIM-8350 - Cyber Critical Infrastructure, Threats, Terrorism, & Warfare
- TIM-7211 - Introduction to Research Design and Methodology for Technology Leaders
- Specialization Course 4
- Specialization Course 5
- CMP-9701CY - PhD Cybersecurity Pre-Candidacy Prospectus
- DIS-9901A - Components of the Dissertation
- DIS-9902A - The Dissertation Proposal
- DIS-9903A - Institutional Review Board (IRB) and Data Collection
- DIS-9904A - The Dissertation Manuscript and Defense
Governance, Risk, and Compliance Specialization
The Doctor of Philosophy in Cybersecurity (PhD-CY), Governance, Risk, and Compliance specialization combines the four knowledge areas to complete research or synthesize cybersecurity solutions for enterprises subject to national exposures and global threats. The combined resolution of risk, compliance, audit, and privacy will enable graduates to create enhanced solutions while limiting the need for resources. The specialization investigates current and anticipated needs and solutions within all four areas, addressing key issues for larger organizations while providing improved strategic alignment. It includes important access control, and threat discovery across complex environments. The specialization includes an emphasis on preempting future losses.
Specialization Courses - 15 credit hours
- TIM-8710 - General Cyber Law, Oversight, and Regulations
- TIM-8715 - Frameworks, Models, Standards, and Controls
- TIM-8720 - Industry Laws, Regulations, and Compliance
- TIM-8725 - Cyber Policy and Leading Cyber Operations
- TIM-8390 - Strategic Management of Cybersecurity: General and Technology
- Defense Technologies
- Digital Media
- Engineering
- K-12 Programs
- Manufacturing
- Mathematics
- Occupational Safety & Health
- Supply Chain & Logistics
- Graduate Certificates
- Professional Certificates
- Savannah Campus
- Workplace Learning & Professional Development
- Corporate Education
- Train at Your Location
- Georgia Tech Summer
- Military Programs
- ESL (English as a Second Language)
- Online Courses
- Massive Open Online Courses (MOOCs)
- Global Learning Center
- Savannah Facilities
Online Master of Science in Cybersecurity
- Degree Overview
- Student Resources
- Online Learning
Spring 2025 Standard Application Deadline
Spring 2025 final application deadline, spring 2025 program start, next info session, online degree overview.
Cybersecurity isn’t just about keeping your individual computers and devices safe, it’s about safeguarding our society and our world. Whether that’s from rogue criminals and gangs who want to steal your money or identity, or nation states and terror groups who want to disrupt defense systems, elections, or cripple our energy infrastructure, the need for well-trained cybersecurity professionals who can stop these attacks has never been greater. Obtaining a degree in cybersecurity online is an important step in becoming a world-class cybersecurity professional.
Georgia Tech's Online Master of Science in Cybersecurity (OMS Cybersecurity) is the only interdisciplinary degree in cybersecurity from a U.S. News & World Report Top 10-ranked public university that you can earn online, on your own schedule, for a tuition less than $10,000. The program, offered part-time, is designed for working professionals and can be completed in two to three years.
The OMS Cybersecurity program provides the foundations so you can:
- Understand the nature of risks and pathways of threats to cyber and cyber-physical systems.
- Develop an awareness of vulnerabilities to software, networks, and computer systems.
- Comprehend methods and strategies for protecting data on networks, in software, as well as other cyber and cyber-physical systems.
- Examine the constraints and costs of cybercrime and espionage to privacy, communication, and use of technology.
- Investigate the role that government, corporate, and coalition policies can have towards slowing and stopping cybercrime and surveillance.
Cybersecurity Program-at-a-Glance
$310 per credit hour, 10 courses (32 credit hours), 2-3 years part-time program, 100% online, a credential that commands attention.
- Information Security Requirements
- Cyber-Physical Systems Track Requirements
- Policy Track Requirements
- Admission Deadlines
- How to Apply
International Applicants
Prerequisites For admission into the Information Security Track of the Online Master of Science in Cybersecurity program, all applicants are expected to have:
- A Bachelor of Science from an accredited institution in Computer Science or Computer Engineering.*
- A good understanding of computer science fundamentals such as data structures and algorithms, processor architectures, operating systems, and networking protocols.
- At least one college-level course or equivalent knowledge in discrete mathematics.
- Strong programming skills and coding experience.
- A minimum GPA of 3.0 (on a 4.0 scale).
*Qualified applicants with other degrees and relevant work experience in software development/architecture, cryptography, secure computer systems, and/or network security are also encouraged to apply. Applicants with such experience must be able to demonstrate in their application deeper understanding of these areas. If you only have familiarity with systems related to them (such as configuring a network firewall), you may not have the foundational knowledge needed for admission and successful completion of the program.
Online Application Admission is a competitive process and we carefully review all facets of your application. The information you include in your application assists our admissions committee in evaluating your potential for success in the program. Your application will not be reviewed until all of your supporting documents have been submitted.
International Students For international graduate applicants, please review the international student’s tab for requirements.
Prerequisites For admission into the Cyber-Physical Systems Track of the Online Master of Science in Cybersecurity program, all applicants are expected to have:
- A Bachelor of Science from an accredited institution in Computer Engineering, Computer Science, or Electrical Engineering.
- Basic familiarity with energy systems fundamentals and systems and controls is preferred.
- Strong programming skills.
*Qualified applicants with degrees in related fields and relevant work experience in cyber-physical, power, and/or embedded systems are also encouraged to apply.
Online Application Admission is a competitive process and we carefully review all facets of your application. The information you include in your application assists our admissions committee in evaluating your potential for success in the program. Your application will not be reviewed until all of your supporting documents have been submitted.
International Students For international graduate applicants, please review the international student’s tab for requirements.
Prerequisites For admission into the Policy Track of the Online Master of Science in Cybersecurity program, all applicants are expected to have:
Applicants with technical backgrounds are expected to have:
- A Bachelor of Science degree from an accredited institution in Engineering or Computer Science.
- Relevant experience in information system security management in a government, military, or business setting.
- Two- to-three college-level courses in political science, law, public policy, economics, or international relations.
Applicants with non-technical backgrounds are expected to have:
- A bachelor’s degree from an accredited institution in Business, Economics, International Relations, Political Science, Public Policy, Pre-law, or law degrees.
- One- to two-years of practical experience in the management or operation of information systems or networks.
- At least one college-level course in computer science or programming.
- A minimum GPA of 3.0 (on a 4.0 scale) in prior undergraduate or graduate programs.
Applicants who are accepted into the program, and lack a sufficient technical background, are encouraged to take a computer science course to ensure success in the program (we recommend Introduction to Computing in Python ). It your responsibility to start the program with this foundation knowledge.
Online Application Admission is a competitive process and we carefully review all facets of your application. The information you include in your application assists our admissions committee in evaluating your potential for success in the program. Your application will not be reviewed until all of your supporting documents have been submitted.
International Students For international graduate applicants, please review the international student’s tab for requirements.
All application materials must be submitted by the deadline — including unofficial transcripts, letters of recommendation, and TOEFL scores (if applicable).
Spring Enrollment (January) Standard Application Deadline: June 15 Final Application Deadline: Aug .1
Fall Enrollment (August) Standard Application Deadline: Feb. 1 Final Application Deadline: March 15
Ready to apply? You're in the right place. Applications are accepted year-round.
What You Need Applications are submitted electronically and include a nonrefundable application fee. You will need to upload the following items as part of your application:
- Official transcripts from each institution attended. Transcripts not in English must be accompanied by a certified translation. If you are admitted, you will be asked to send an additional official transcript. You will receive instructions at that time.
- Lawful Presence Document (U.S. Citizens Only). Applicants must verify their lawful presence in the United States prior to enrollment.
- English Proficiency (International Students Only). The language of instruction at Georgia Tech is English. With some exceptions, international applicants must take and submit scores for the Test of English as a Foreign Language (TOEFL). Minimum test scores and expectations are found on our International Students tab .
- References. You will initiate the process through the online application by entering the name and email addresses of three references. Upon submission of your application, an email will be sent to the recommender requesting a brief online recommendation. Please inform your references that they must submit the form for your application to be complete.
- Test Scores (Optional). You may choose to submit standardized test scores, most commonly GRE or GMAT. This is not required for admission into the program.
Program-Specific Questions/Materials
- Personal Statements. Describe your specific career goals and objectives, the decision to pursue an advanced degree, and other information that may be useful to the admissions committee.
- Professional Resume. A listing of your professional experience and uploaded to the online application.
Start Your Application You can submit your application to the program at any time of the year. If you have any questions during the application process, please check our Frequently Asked Questions or contact the Student Services Team .
Please set aside sufficient time — usually about two to three weeks — for Graduate Studies to receive and process your supporting documents. We cannot guarantee applications received after the deadline will be reviewed in time for the applied semester.
Application Fee A non-refundable application fee must be paid online with a credit card or electronic check if you have a U.S. bank account. The application fee is $95 for U.S. applicants and $105 for international applicants. Your application will not be received until the fee is paid.
Status Checking Once your application is completed and submitted, you may monitor its progress through CollegeNet’s online status check system (using the same CollegeNet user ID and password created when you applied).
Technical Requirements There are technical requirements for our online degree program. Please review the technology requirements in the Frequently Asked Questions area below.
Georgia Tech considers you an international applicant if you are neither a U.S. citizen nor a U.S. permanent resident, even if you currently reside in the U.S under a non-immigrant visa. Since the program is 100% online, international students admitted to the program will not be offered visas. International students do not require U.S. residency to enroll in the program. All applicants residing within the U.S. must satisfy the lawful presence requirement .
The admissions criteria applied in evaluating international applicants are the same as those for U.S. citizens and U.S. permanent residents. All application materials, including transcripts and recommendations, must be submitted in English in addition to their native language (if not originally in English). All applicants must satisfy the English Language Proficiency requirement of admission to Georgia Tech. If an international applicant is using a TOEFL or IELTS score to satisfy this requirement, please note that admission to this degree requires the minimum scores outlined below.
Georgia Tech requires that all applicants demonstrate proof of English language proficiency. Listed below are the ways that this requirement can be satisfied:
- U.S. Citizens and Permanent Residents can submit Lawful Presence documents
- provide proof of citizenship from an approved country listed here
- provide a transcript from a regionally accredited university or college located in the United States reflecting a minimum of one academic year (3 quarters or 2 semesters) of full-time enrollment
- provide a transcript from a university or college located in one of these listed countries reflecting a minimum of one academic year (3 quarters or 2 semesters) of full-time enrollment
- Applicants not meeting any of the above criteria who studied at a school where the language of instruction is English but the country in which the school is located is not listed here are required to submit acceptable standardized test scores as outlined below.
If you do not meet any of the above listed criteria, you will be required to submit a standardized test score to satisfy the English Language Proficiency requirement.
Our program-specific accepted tests and minimum score requirement for admission are listed below. Please note that meeting Georgia Tech’s minimum score does not guarantee admission since some programs (such as this one) have higher score requirements.
- IELTS ≥ 7.5 overall (with a minimum band score for Reading, Listening, and Speaking of 6.5; minimum band score for Writing is 6.0)
- TOEFL iBT ≥ 100 overall (with each section also scoring 20 or higher)
We recommend that you achieve acceptable scores prior to submitting your application. Scores must be no more than two years old on the day you are scheduled to begin your graduate studies. Failure to satisfy the English Language Proficiency requirement will impact our ability to review an application .
Transcripts
All applicants to the OMS Analytics Program must hold a U.S. bachelor's degree or international equivalent to be considered for admission. A three-year degree is not equivalent to the U.S. bachelor's degree. Neither professional designations nor work experience will count toward the fourth year of study. We're unable to make exceptions to this policy.
Georgia Tech does not accept any private evaluation of academic documents, such as those provided by companies like WES. Official transcripts and degree documents should be submitted at the time of application, but unofficial scans uploaded to your application are acceptable for the sake of admission consideration. Official copies can then be provided to us upon an offer of admission, as required.
Georgia Tech requires the following documents from international applicants:
- Official native-language transcripts from every college/university attended for credit, even if that credit wasn’t earned or was transferred to another school
- Official English translation of the native language transcript
- Official native language degree documents
- Official English translation of the native language degree document
Cost & Aid
- Tuition and Fees
- Payments and Refunds
- Financial Assistance
Program Tuition $9,920 Program Credit Hours 32 Cost/credit hour $310 Term Fees* Institutional Fee $194 Technology Fee $107 *Term fees are assessed only for the terms in which students are enrolled in courses.
All payments of tuition and fees are handled by the Bursar’s office. For deadlines and instructions on how to pay, please visit the student payment portal .
The Georgia Tech Bursar’s Office processes refunds via EFT, also known as Direct Deposit, Monday through Friday. Refunds and overpayments are electronically disbursed to the student’s checking or savings account and should be in the students account on the following day or sooner. You are not always eligible for a refund when dropping a course, so please read over the refund policy .
Education Loans U.S. citizens and permanent residents may be eligible for education loans. To learn more about graduate financial aid and loan programs, visit Georgia Tech’s Office of Scholarships and Financial Aid .
Employer Tuition Reimbursement Contact your employer’s human resources department for available tuition assistance programs and eligibility.
The Post-9/11 GI Bill Effective August 1, 2011, qualified U.S. veterans may be eligible to receive financial support for tuition, mandatory fees, books, and housing. Additional information is available through the Department of Veterans Affairs GI Bill Website .
Master's Cybersecurity Curriculum
Using multiple digital platforms and world-class instructors, you’ll have the opportunity to tailor your degree to your needs and interests by selecting a specialized degree track., program resources and related content.

FREQUENTLY ASKED QUESTIONS
Accreditation.
For information on Georgia Tech’s institutional accreditation see gatech.edu/accreditation .
NC-SARA Approval
The Institute has been approved by the state of Georgia to participate in the National Council for State Authorization Reciprocity Agreements (NC-SARA).
NC-SARA is a voluntary, regional approach to state oversight of postsecondary distance education. The State Authorization Reciprocity Agreement (SARA) is an agreement among member states, districts, and territories that establish comparable national standards for interstate offering of postsecondary distance education courses and programs. It is intended to make it easier for students to take online courses offered by postsecondary institutions based in another state. SARA is overseen by a National Council and administered by four regional education compacts.
What is the admission criteria for the OMS Cybersecurity program?
Information Security Track
- A good understanding of computer science fundamentals such as processor architectures, operating systems, and networking protocols.
*Qualified applicants with other degrees and relevant work experience in cryptography, secure computer systems, and/or network security are also encouraged to apply.
Cyber-Physical Systems Track
Policy Track
Technical backgrounds:
- Relevant experience in information system security management in a government, military or business setting.
- Two-to-three college-level courses in political science, law, public policy, economics, or international relations.
Non-technical backgrounds*:
- A bachelor’s degree from an accredited institution in Business, Economics, International Relations, Political Science, or Public Policy. Pre-law or law degrees.
- Practical experience in information management and programming.
*Applicants who are accepted into the program, and lack a sufficient technical background, will be required to take a free online computer science course to prepare for CS 6035.
If I meet the admission criteria, am I automatically admitted?
No applicant is automatically admitted into the program. All applications are reviewed by a faculty committee to ensure those admitted can succeed in the program.
Will there be a cap on admissions?
There is no hard cap on admissions.
Application Process
What are the application requirements and deadlines.
View upcoming application deadlines and more details about application requirements for each track: Information Security , Cyber-Physical Systems , and Policy .
How can I apply to the program?
Please review the information on our admissions section , which explains relevant dates, costs, and information necessary for application.
What materials must be on file before the application is considered complete and can be evaluated?
Applications are submitted electronically and include a nonrefundable application fee. You will need to upload the following items as part of your application:
- Official transcripts from each institution attended. Transcripts not in English must be accompanied by a certified translation. If you are admitted, you will be asked to send an additional official transcript. You will receive instructions at that time.
- Lawful Presence Document (U.S. Citizens Only). Applicants must verify their lawful presence in the United States prior to enrollment.
- English Proficiency (International Students Only). The language of instruction at Georgia Tech is English. With some exceptions, international applicants must take and submit scores for the Test of English as a Foreign Language (TOEFL). Minimum test scores and expectations are found on our International Applicants tab.
- References. You will initiate the process through the online application by entering the name and email addresses of three references. Upon submission of your application, an email will be sent to the recommender requesting a brief online recommendation. Please inform your references that they must submit the form for your application to be complete.
- Test Scores (Optional). You may choose to submit standardized test scores, most commonly GRE or GMAT. This is not required for admission into the program.
Program-Specific Questions/Materials
- Personal Statements. Describe your specific career goals and objectives, the decision to pursue an advanced degree, and other information that may be useful to the admissions committee.
- Professional Resume. A listing of your professional experience and uploaded to the online application.
How can I check the status of my application?
You can check the status of your admission online at the Georgia Tech Graduate Studies website .
How many courses are required to earn an Online Master of Science in Cybersecurity?
Students will take 10 courses (32 credit hours) to earn their degree.
Which tracks will be available with this program?
The Information Security track, Cyber-Physical Systems track, and Policy track are currently offered.
Are courses taught at specific times or can I learn at my own pace?
The courses are typically taught asynchronously, which means learners access and study content anytime, anywhere.
However, there may be synchronous virtual office hours with faculty and teaching assistants or for group project meetings, which students may need to attend in real time. These sessions are often recorded for later access.
Exams, in general, are open for a period of time, during which students take the exam in a shorter time period. For example, you would have two hours within a 48-hour period to take the exam.
Cost and Aid
What are the tuition and fees.
View the current tuition and fees .
Are there opportunities for financial aid or assistance?
Yes, please visit our financial aid tab to view current opportunities.
Who is considered an international applicant?
Georgia Tech considers you an international applicant if you are neither a U.S. citizen nor a U.S. permanent resident, regardless of where in the world you live.
What is the admissions process for international applicants?
International applications are evaluated in the same manner as U.S. applicants. Non-U.S. citizens/Permanent Residents may need to submit a TOEFL or IELTS test scores to satisfy Georgia Tech’s English Language Proficiency requirement . We strongly encourage all international applicants to submit application materials early to expedite the admissions process.
Who is required to take the Test of English as a Foreign Language (TOEFL) or the International English Language Testing System (IELTS)?
Please find applicable information in our International Applicants section .
What is the minimum TOEFL or IELTS score needed to be admitted?
Do i need to have my transcripts translated or converted.
You will need to provide a direct English translation of your transcript upon application. If your undergraduate institution does not grade on a 4.0 scale, you should not convert your GPA; simply enter it as it appears on your transcripts/student record.
Will I be offered a visa?
Since the program is 100% online, international students applying to the program will not be offered visas.
Do I need U.S. residency to enroll in the program?
No. International students do not require U.S. residency to enroll in the program.
General Program Information
Do i have to declare a track specialization.
Yes. Each track specialization has its own admission requirements and application process.
Is this the same program as the on-campus Master's of Science in Cybersecurity?
Yes. Online students earn the same degree and enjoy the same benefits as our on-campus Master of Science in Cybersecurity students, including the same academically challenging curriculum and outstanding faculty. View our program comparison chart to help you decide which program is best for you.
What will my transcript and diploma say?
Online students receive the same degree as our on-campus Master of Science in Cybersecurity students. The diploma and transcript will say "Master of Science in Cybersecurity."
How long does it take to complete and receive an OMS Cybersecurity degree?
OMS Cybersecurity is a part-time program, typically taking two to three years to complete. We will allow for longer enrollments—up to six years—for those students who need greater flexibility.
What are the benefits of the program?
The benefits of Georgia Tech's Online Master of Science in Cybersecurity are many, but some of the highlights include:
- Learning from the same comprehensive on-campus curriculum without interrupting your career.
- Flexibility to choose the number of courses to fit your schedule and complete your degree at your own pace.
- Earning a degree recognized worldwide, and from a U.S. News & World Report top 10-ranked university.
SIGN UP FOR UPDATES
Stay up-to-date on important deadlines, updates, and news. Also get tips for writing a stellar application!
Connect With Us
Remote learning doesn’t mean missing out. Be part of our growing social network with other students.
Want to know how a degree in cybersecurity online can help you advance your career? Want to stay current on important deadlines, updates, and news? Need more details?

Your version of Internet Explorer is either running in "Compatibility View" or is too outdated to display this site. If you believe your version of Internet Explorer is up to date, please remove this site from Compatibility View by opening Tools > Compatibility View settings (IE11) or clicking the broken page icon in your address bar (IE9, IE10)
Missouri S&T Missouri S&T
- Future Students
- Current Students
- Faculty and Staff
- distance.mst.edu
- Cybersecurity
Online Education
- 1870 Miner Circle, Rolla, MO 65409
- (573) 341-6903
- [email protected]
Distance Education Big Data & Cybersecurity
- Request Info
- Graduate Programs
Discover S&T's nationally ranked online graduate programs for those working in the defense and security industries.
With the increase in cybercrimes and the fear of private data getting hacked, companies are looking for professionals who can secure their systems. Fields like Big Data and Cybersecurity are overtaking the IT sector when it comes to hot jobs.
At Missouri S&T, we offer specialized graduate degrees and certificate programs that stand above the competition. And our rankings prove it.
- Computer information technology online graduate programs are national ranked (U.S. News and World Report Rankings 2020)
- Big Data certificates ranked No. 2 in the nation. (Value College’s Top 50 Best Value Online Big Data Graduate Programs of 2016)
Check out our extensive line-up of distance courses, which are taught by faculty experts, prominent educators and industry leaders.

Missouri S&T is accredited as a National Center of Academic Excellence in Information Assurance and Cyber Defense Research. It is the only university in Missouri with this active designation and one of 56 schools in the nation.
"The nation is constantly having to develop new resilience measures to ensure our cyber-physical security." - Dr. Bruce McMillin, professor and interim chair of the department of Computer Science
Learn Anywhere
S&T's distance programs are the same courses as those taught on campus. Attend live and interact directly with your professors and fellow classmates, or view materials at a later time to fit your schedule.
Computer Science Certificate Programs
- Big Data Management and Analytics
- Big Data Management and Security
- Computational Intelligence
- Cyber Security
- Information Systems & Cloud Computing
Computer Science MS
Information Science and Technology Certificate Programs
- AI, Machine Learning and Automation in Business
- Business Analytics and Data Science
- Business Intelligence
- Cybersecurity and Information Assurance Management
Information Science and Technology MS
Electrical and Computer Engineering Certificate Programs
- Information Assurance & Security Officer Essentials
Computer Engineering MS
Systems Engineering Certificate Programs
Systems Engineering MS/PhD
Have a Question?
We are here to answer any of your questions about Missouri S&T’s distance education programs.
Phone: 573-341-6903
Email Us Request Info
1 Distance Learning PhD Degrees in Cybersecurity 2024
- Technology Studies
- Information Technology
- Cybersecurity
Distance Learning
Technology Studies (1)
- Computer Science (6)
- Computing (1)
- Data Science (2)
- Information Systems (4)
- Cybersecurity (1)
- IT Security (1)
- Networks (2)
- Technology (1)
- Telecommunication (1)
- Back to main category
- United Kingdom (0)
- Australia (0)
- Bachelor (0)
- Certificate (0)
- Diploma (0)
- Associate of Applied Science (0)
- Associate Degree (0)
- Graduate Certificate (0)
- Associate of Arts (0)
- Summer Course (0)
- Advanced Diploma (0)
- Postgraduate Diploma (0)
- Graduate Diploma (0)
- Foundation Year (0)
- Postgraduate Certificate (0)
- A-level (0)
- Preparatory Program (0)
- Doctor of Education (0)
- Advanced Certificate (0)
- Juris Doctor (0)
- Undergraduate Pathway (0)
- Undergraduate Certificate (0)
- Graduate Pathway (0)
- 2 years (0)
- 3 years (0)
- 4+ years (0)
- Full time (0)
- Part time (0)
- English (1)
- Spanish (0)
- Portuguese (0)
- Italian (0)
- On-Campus (0)
- Distance Learning (1)
- Blended (0)
Doctorate in Cybersecurity
University of fairfax.

- Roanoke, USA
As a doctoral student, all of your courses here will explore relevant cybersecurity policy issues in enterprise management, you'll complete a cybersecurity project in each, enabling you to make immediate and lasting workplace contributions. You'll learn from leading, practitioner cybersecurity faculty whose cybersecurity colleagues can become an integral part of your professional network throughout your career.
Popular degree type
Popular education type
Popular locations
Distance Learning PhD Degrees in Cybersecurity
Governments, businesses, and private citizens all use computers on a daily basis. Cyber security exists to protect computer systems and shared data from theft or damage by any presence that plans to do harm. Security is a constant issue as technology changes and criminals circumvent existing safety measures.
Requirements for the PhD program often involve the student having already obtained a Master’s degree. Additionally, a thesis or dissertation primarily consisting of original academic research must be submitted. In some countries, this work may even need to be defended in front of a panel.
Online learning refers to use of electronic media and information and communication technologies (ICT) in education. With online learning one has the flexibility to access their studies at any time and from anywhere they can log on.

- Schools & departments

Cyber Security, Privacy and Trust PhD
Awards: PhD
Study modes: Full-time
Funding opportunities
Placements/internships
Programme website: Cyber Security, Privacy and Trust
Introduction to Postgraduate Study
Join us for this online session on 26 June to learn more about postgraduate study at Edinburgh
Find out more and register
Research profile
The increasing reliance of systems and services on information technology in the public, private and third sector has significantly raised the impact of cyber attacks in the last two decades.
This PhD programme in Cyber Security, Privacy and Trust is a response to the growing need for highly specialized research and training in these topics. Cyber security and resiliency is a complex problem that requires designing and understanding underlying technologies but also how business processes, cost, usability, trust and the law play a role for effective technology deployment.
The aim of this PhD programme is to provide students with research training in specialised topics of security, privacy and trust, helping produce the next generation of world-leading experts of the field.
Programme structure
The PhD in Cyber Security, Privacy and Trust trains you as a researcher and allows you to develop advanced techniques and in-depth knowledge in a specialist area. You will develop an all-round knowledge of your discipline, and a broad range of transferable skills.
You will carry out independent research, resulting in an original contribution to knowledge in your chosen area, working under the guidance of your supervisors.
The prescribed period of study is 36 months if studying full-time, or between 48 and 72 months if studying part-time.
Year 1 of PhD studies is probationary. Your supervisor will identify your training needs, if any, and invite you to attend lectures relevant to your research topic. These lectures may be selected from those offered to MSc students or may be specialist courses and seminars organised by the School's various research groupings.
Towards the end of Year 1, you will be expected to submit a thesis proposal which identifies a specific research topic, reviews the relevant literature, outlines a plan of research to address the topic, and describes progress made so far.
Progress during your PhD is assessed by annual reviews, which formally determine whether you can progress with your PhD. You will be required to complete and pass a PhD annual review at the end of each year of study and thesis is expected to be submitted at the end of Year 3. Following thesis submission, you will be required to attend an oral examination (or viva) which will be conducted by an external and internal examiner.
Work placements/internships
Many postgraduate research students in the School of Informatics undertake at least one optional internship during their PhD, gaining important transferable skills whilst working with companies, public or third sector organisations.
The School of Informatics maintains a range of connections to potential employers in the cyber security and other sectors. Work placements or internships are considered a valuable aspect of research training as they expose students to an applied research culture, and can provide valuable contacts for future job searches.
Training and support
As a research student in the School of Informatics, you will have access to a highly respected academic staff community, including staff who have won prizes for their research and who are Fellows of learned societies.
The University of Edinburgh has been recognised as a UK Academic Centre of Excellence in Cyber Security Research. This is based on the amount and quality of its research output, as well as its level of PhD training.
Within the School of Informatics, the Security, Privacy and Trust Group includes academic staff who lead research in a range of technical and socio-technical areas of cyber security. Staff also supervise PhD students on this programme.
- Security, Privacy and Trust Group
You will carry out your research under the guidance of a primary supervisor and at least one other secondary or co-supervisor. You will be expected to attend seminars and meetings of relevant research groups and may also attend lectures that are relevant to your research topic. Periodic reviews of your progress will be conducted to assist with research planning.
A programme of transferable skills courses will be offered, which facilitates broader professional development in a wide range of topics, from writing and presentation skills to entrepreneurship and career strategies.
The award-winning Informatics Forum is an international research facility for computing and related areas. It houses more than 400 research staff and students, providing office, meeting and social spaces.
The Forum also contains several robotics labs, an instrumented multimedia room, eye-tracking and motion capture systems, and a full recording studio amongst other research facilities. Its spectacular atrium plays host to many events, from industry showcases and student hackathons to major research conferences.
Nearby teaching facilities include computer and teaching labs with more than 250 machines, 24-hour access to IT facilities for students, and comprehensive support provided by dedicated computing staff.
There are further specific facilities to support aspects of cyber security research, including an Internet of Things Lab and a Network Security Lab. The Blockchain Technology Lab is a research lab supporting investigations into distributed ledger technology.
Among our wider entrepreneurial initiatives is Informatics Ventures, set up to support globally ambitious software companies in Scotland and nurture a technology cluster to rival Boston, Pittsburgh, Kyoto and Silicon Valley.
Career opportunities
There is high demand for security and privacy experts in industry, academia, and the public sector. Commercially, there is also a large variety of opportunities in both small and large companies.
Previous PhD graduates associated with the Security and Privacy Group have gone on to employment in industry with companies including:
- ION Geophysical
- Disney Research
- Deutsche Bank.
Students have also gone on to be employed within academia, at institutions, to name a few, including:
- University of Oxford
- University of Bristol
- University of Oldenburg
- University of Auckland
- University of Birmingham
- University of Surrey
- University of Munich
- Cambridge University
- Queen’s University Belfast
- Tsinghua University
- Lancaster University
Entry requirements
These entry requirements are for the 2024/25 academic year and requirements for future academic years may differ. Entry requirements for the 2025/26 academic year will be published on 1 Oct 2024.
A UK 2:1 honours degree, or its international equivalent, in computer science, mathematics, linguistics, or a related discipline. A Masters degree or equivalent, in information security, cyber security or a closely related discipline is recommended.
International qualifications
Check whether your international qualifications meet our general entry requirements:
- Entry requirements by country
- English language requirements
Regardless of your nationality or country of residence, you must demonstrate a level of English language competency at a level that will enable you to succeed in your studies.
English language tests
We accept the following English language qualifications at the grades specified:
- IELTS Academic: total 7.0 with at least 6.0 in each component. We do not accept IELTS One Skill Retake to meet our English language requirements.
- TOEFL-iBT (including Home Edition): total 100 with at least 20 in each component. We do not accept TOEFL MyBest Score to meet our English language requirements.
- C1 Advanced ( CAE ) / C2 Proficiency ( CPE ): total 185 with at least 169 in each component.
- Trinity ISE : ISE III with passes in all four components.
- PTE Academic: total 70 with at least 59 in each component.
Your English language qualification must be no more than three and a half years old from the start date of the programme you are applying to study, unless you are using IELTS , TOEFL, Trinity ISE or PTE , in which case it must be no more than two years old.
Degrees taught and assessed in English
We also accept an undergraduate or postgraduate degree that has been taught and assessed in English in a majority English speaking country, as defined by UK Visas and Immigration:
- UKVI list of majority English speaking countries
We also accept a degree that has been taught and assessed in English from a university on our list of approved universities in non-majority English speaking countries (non-MESC).
- Approved universities in non-MESC
If you are not a national of a majority English speaking country, then your degree must be no more than five years old* at the beginning of your programme of study. (*Revised 05 March 2024 to extend degree validity to five years.)
Find out more about our language requirements:
- Academic Technology Approval Scheme
If you are not an EU , EEA or Swiss national, you may need an Academic Technology Approval Scheme clearance certificate in order to study this programme.
Fees and costs
Scholarships and funding, featured funding.
- Security, Privacy and Trust Group PhD topics (some with scholarships)
- School of Informatics scholarships for research students
- Research scholarships for international students
Please note that some University and School scholarships require separate applications via the Scholarships portal.
UK government postgraduate loans
If you live in the UK, you may be able to apply for a postgraduate loan from one of the UK’s governments.
The type and amount of financial support you are eligible for will depend on:
- your programme
- the duration of your studies
- your tuition fee status
Programmes studied on a part-time intermittent basis are not eligible.
- UK government and other external funding
Search for scholarships and funding opportunities:
- Search for funding
Further information
- IGS Admissions Administrator
- Phone: +44 (0)131 650 3091
- Contact: [email protected]
- School of Informatics Graduate School
- Office 3.42
- Informatics Forum
- Central Campus
- Programme: Cyber Security, Privacy and Trust
- School: Informatics
- College: Science & Engineering
Select your programme and preferred start date to begin your application.
PhD Cyber Security, Privacy and Trust - 3 Years (Full-time)
Application deadlines.
Applications for 2024/25 entry are now open and can be submitted all year round.
Please submit your completed application at least three months prior to desired entry date.
If you want to be considered for School funded PhD scholarships you must apply by one of two rounds:
(Revised 25 October 2023 to update application deadlines)
(Revised 15 February 2024 to extend the round 2 application deadline)
- How to apply
You must submit two references with your application.
You must submit an application via the EUCLID application portal and provide the required information and documentation. This will include submission of:
- a Curriculum Vitae (CV)
- research proposal (2-5 pages long)
- degree certificates and official transcripts of all completed and in-progress degrees (plus certified translations if academic documents are not issued in English)
- two academic references
Only complete applications will progress forward to the academic selection stage.
Read through detailed guidance on how to apply for a PGR programme in the School of Informatics:
- School of Informatics PGR Application Guidance
Find out more about the general application process for postgraduate programmes:

Studying Here
- Find your course
- Fees and funding
- International students
- Undergraduate prospectus
- Postgraduate prospectus
- Studying abroad
- Foundation Year
- Placement Year
- Your future career
- Central London campus
- Distance learning courses
- Prospectuses and brochures
- For parents and supporters
- Schools and colleges
Sign up for more information
Student life, accommodation.
- Being a student
Chat with our students
Support and wellbeing.
- Visit Royal Holloway
- The local area
- Virtual experience
Research & Teaching
Departments and schools.
- COP28 Forum
Working with us
- The library
Our history
- Art Collections
Royal Holloway today
- Equality, Diversity and Inclusion
- Recruiting our students
- Past events
- Environmental Sustainability
- Facts and figures
- Collaborate with us
- Governance and strategy
- Online shops
- How to find us
- Financial information
- Local community
- Legal Advice Centre
In this section

Find the right course

Online undergraduate prospectus

- Student life

What our students say
Explore our virtual experience
- Research and teaching

Research institutes and centres

Our education priorities
Our phd programmes, site search, phd in information security.
The Information Security Group runs a popular full-time and part-time PhD research programme on a wide variety of information security-related topics. The ISG has supervised hundreds of PhD students in its history, many now holding influential positions within the cyber security industry. We are looking for enthusiastic, inquisitive, and dedicated individuals who have the potential to contribute to the growing and diverse field of information security as applied inside and outside of academia. Our research actively contributes to industry, policy, and the development of secure products.
Enquiries: Dr Andrew Dwyer, [email protected], Information Security Group PGR Lead
How does a PhD in Information Security work?
All PhD students are assigned at least one named supervisor and an advisor. The supervisor directs the work and acts as the first line of research, administrative, and welfare support. The role of the advisor varies, but in all cases the advisor provides a second line of support.
The PhD programme is research-based with substantial research and study, both independently and in close coordination with the supervisor. All PhD students are expected to regularly meet with the supervisor and take part in training as part of researcher development. PhD students in the Information Security Group regularly attend relevant seminar series, workshops, and study groups. This involves discussing and presenting work to other students and staff. Where appropriate, students will be expected to attend or present work at seminars, workshops or research meetings off the campus based just outside London in scenic Egham, including at international research conferences.
How long does the PhD take to complete?
Full-time Study: Three- to four-year course equivalent in commitment to a full-time job. This is the most common mode of pursuing a PhD. Full-time students in their first three years of study are guaranteed desk space and computer facilities in the department and are expected to contribute fully to the departmental research community.
Part-time Study: Four- to seven-year course for committed students who wish to study their PhD alongside a full-time job, caring responsibilities, or similar commitments. Part-time study is the default mode for students working for more than fifteen hours per week or with caring responsibilities which preclude full-time study. Part-time students are expected to attend Royal Holloway’s campus at some points and to have regular meetings with their supervisor (either in person or online).
How are PhD degrees examined?
Once the research has been successfully completed the student must write and submit a final report in the form of a PhD research thesis. This will be evaluated by at least two experts (one internal to Royal Holloway, and one external) and the student will be invited to attend an oral examination where they must defend their thesis.
Entry Requirements
The minimum entry requirement for an MPhil or an MPhil leading to a PhD degree is the equivalent of a UK Second Class Honours degree in an appropriate subject, although in many cases a Master's level qualification will also be expected. Candidates must also be demonstrably proficient in English to write and communicate about their research adequately and confidently.
Funding Requirements
It is extremely important to ensure that there are sufficient funds (both to cover fees and living costs) to complete a PhD programme. Click here for current fees for our PhD programme. It may be that some overseas students seek funding from organisations outside of the UK.
Obtaining funding can be extremely difficult and so potential candidates are advised to actively explore all available opportunities to secure funds. Click here to see current funding opportunities. Please note that any departmentally administered scholarships for admission to the PhD in Information Security will be advertised in the ‘Scholarships’ section.
Scholarships
As part of a consortium of six universities – the South East Doctoral Training Arc (SEDarc)- we are accepting applications for PhD scholarships that focus on the social science of cyber security . For information on deadlines for application to this scholarship opportunity, please click on the above link.
How do I apply?
To apply to our PhD programme, there are a series of steps which you must follow that are outlined below. Please be aware that if you are applying from overseas, certain countries may be subject to extra checks in addition to any visa applications, so please apply as soon as possible (and ideally 6 months before your start date).
Write down an initial research idea. At a minimum, this should include 1) a research title , 2) a short research abstract (of no more than 300 words) describing your research idea, and 3) a short proposed methodology. You are also welcome to propose more developed research projects (as expected in Step 3).
Take a look at the research profiles of staff members in the Information Security Group, click here to find their profiles. All PhD positions (whether self-funded or not) may be applied for only after consultation with a proposed supervisor. Before you start working on an application you will need to identify a supervisor by contacting a member of academic staff in the Information Security Group (with research interests similar to yours) to discuss your proposal. If you find a member of academic staff who is prepared to supervise you, then they will be able to answer any questions that you have and help you with your application. If you need help finding a member of staff to work with, you can contact the ISG’s PGR lead, Dr Andrew Dwyer .
If a supervisor supports your application, you should make a formal application ( click here for more information ). In your application, please name the proposed supervisor. As part of the application, you are expected to provide:
- Research Proposal: No longer than 2500 words, including the title, abstract, research background (including relevant literature and research questions), a methods section stating how you will investigate the topic, and a timeline for the planned research to be completed within three years (or six years if part-time).
- Personal Statement: No longer than 500 words, stating your reasons for applying to the PhD, how your skills and knowledge will help you succeed.
This is in addition to an up-to-date CV, degree transcripts, English language qualifications, and contact details for two references.
This application will be reviewed by both the proposed supervisor and the PGR Lead to ensure that you meet our minimum entry requirements. If you meet our minimum requirements, you will be invited to an interview. The interview panel will consist of the supervisor and at least one independent member of academic staff in the Information Security Group.
If you are successful, the PGR Lead will inform Royal Holloway of our decision and you will be contacted by central administration for any further information required. If you are unsuccessful, we can offer brief comments on the reason for not progressing your application.

Explore Royal Holloway

Get help paying for your studies at Royal Holloway through a range of scholarships and bursaries.

Clubs and societies
There are lots of exciting ways to get involved at Royal Holloway. Discover new interests and enjoy existing ones.

Heading to university is exciting. Finding the right place to live will get you off to a good start.

Whether you need support with your health or practical advice on budgeting or finding part-time work, we can help.

Discover more about our 21 departments and schools.

Research Excellence Framework
Find out why Royal Holloway is in the top 25% of UK universities for research rated ‘world-leading’ or ‘internationally excellent’.

Challenge-led research themes
Royal Holloway is a research intensive university and our academics collaborate across disciplines to achieve excellence.

Discover world-class research at Royal Holloway.

Discover more about who we are today, and our vision for the future.

Royal Holloway began as two pioneering colleges for the education of women in the 19th century, and their spirit lives on today.

We’ve played a role in thousands of careers, some of them particularly remarkable.

Find about our decision-making processes and the people who lead and manage Royal Holloway today.

- Staff intranet
- Staff directory

MSc Cyber Security

Computer security is one of the key challenges in contemporary computing. You will gain critical knowledge within the cyber security and digital forensic domains, combining academic principles and industrial practice.
The course is informed by current research in security and digital forensics, and is underpinned by our experience with external partners in law enforcement, the cyber security industry financial institutions, and other knowledge transfer activities.
Course specialisms include network security, penetration testing, incident response, malware analysis, cryptography, audit and compliance, and host and mobile digital forensics. The specialisation you gain in the taught modules is further developed through an extensive research-based MSc dissertation project, leading towards a mastery of a subject area and enhancing your particular specialism.
The course is a fully online version of the MSc Cyber Security on-campus programme. All teaching and learning resources are online, with all assessments also carried out remotely. There is also the option to spread the course modules out over a number of years, making the course ideal for students who cannot attend on-campus classes or those in employment.
Typical entry points to this course are in January and September. Please enquire for more information.

Mode of Study:
Distance learning (available as Full-time | Part-time )
Start date:
“Edinburgh Napier is without doubt the premier institution in the fields of computer security and digital forensics."
This MSc is one of a very small number of courses certified by NCSC, recognising UK universities which are excellent in Cyber Security and accredited by the British Computing Society, the Chartered Institute for IT.
Course Overview from Richard MacFarlane
Our student stories, course details.
You will gain foundation knowledge in all the key areas of cyber security, both defensive and offensive, as well as post-incident response and malware analysis. The digital forensic aspects of the course include network and computer forensics, allowing you to develop the knowledge required to conduct computer-related investigations across networks, systems, and other digital devices.
The School of Computing has developed close ties with industry, law enforcement, and the public sector, through partnerships with organisations such as Cisco Systems, Guidance Software, Symantec, NCC Group, NCA, Police Scotland, and many others.
This helps inform the course, and provides guest lecturers by industry experts. Extensive innovative research is also carried out in key domains by academics and PhD students in our dedicated cyber security and forensic research group.
Lead academics
Programme Leader
Rich Macfarlane
Module Leaders
Rich Macfarlane Prof Bill Buchanan OBE Dr Thomas Tan Robert Ludwiniak Peter Cruickshank Dr Gordon Russell

How you’ll be taught
Our industry-informed course combines thorough coverage of academic theory aligned with extensive hands-on practical activities, supported by fully online web-based materials with virtualised lab environments that provide an equivalent experience to our on-campus specialist facilities.
This is a distance-learning course which you can start in September or January with flexibility in the number of taught modules taken in each trimester. The distance learning course runs in parallel with our on-campus course and is aligned to the same three 15-week academic trimesters, including the assessments, which are taken in the same weeks as on-campus students. Students normally take 2.5 years to complete this course but you can take up to 4 years depending on your commitments and availability.
As the teaching runs to the same weekly schedule, distance students who wish to attend some of the taught classes here in Edinburgh are more than welcome, but there is no requirement to attend. The course content and assessments are fully online and are supported by the same staff as the on-campus teaching, leading to an academically equivalent MSc degree.

Assessments
Assessments are all fully online including virtualised practical environments for hands on assessments.

Modules that you will study* as part of this course
Applied Cryptography and Trust ( CSN11131 )
The focus of this module is to provide a core understanding of the fundamental areas of cryptography, identity, and trust. A key feature is to cover both the theoretical areas, while often demonstrating practical applications including key protocols. The module key areas are: • Privacy, and Cryptography Fundamentals (Confidentiality, Sec Models, Cipher types) • Asymmetric Key Encryption. Including RSA and Elliptic Curve Cryptography (ECC). • Symmetric Key Encryption. Including AES and associated modes. • Hashing and MAC Methods. Including MD5, SHA-1, SHA-256, SHA-3 and PBKDF2. • Security Protocols: HTTPS, SSL/TLS, DNSSec, IPSec, WPA • Key Exchange. Diffie-Hellman Method, ECDH. • Trust Infrastructures. Digital Certificates, Signatures, Key Distribution Centres (Kerberos), OAuth • Identity and Authentication (Passwords, Authentication tokens, Key pair identity, Multi-factor, Biometric Authentication). • Distributed Systems: Blockchain, Distributed Ledgers and Cryptocurrency. Smart Contracts, Data Tokenization, and Transactions. • Future Cryptography: Zero Knowledge Proof, Homomorphic Encryption, Light-weight cryptography, and Quantum robust methods. • Host and Domains: Trust systems. Authentication with Active Directory Authorisation: Log integration and rights.
Further information
Computer Penetration Testing ( CSN11127 )
This module will cover a range of elements concerned with digital penetration testing and security testing. Initial lectures consider important soft skills such as documentation techniques, reporting, the law, and risk assessment and management. The practical skills and their related theoretical knowledge include operating system weaknesses, information gathering (both passive and active), and various ethical hacking techniques and processes. Considerable practical focus is made on available tools to assist in auditing and penetration testing. Aspects targeted include operating systems, common network services, and network-based applications.
Host-Based Forensics (DL) ( CSN11126 )
This module will cover elements of operating system disk-level architectures, such as Windows and Linux. This will allow students to study how operating systems store system and user data, and thus students will gain an understanding as to what information could technically be held on such systems. This data could include user files, as well as user activities such as login session data, browsing histories, operating system manipulation, and general user interactions with a variety of operating system tools. This understanding will be expanded through theoretical knowledge and practical exercises in extracting information from systems, using a variety of open source and commercial forensic analysis tools, and documenting the results of such a process using consistent and thorough evidential procedures. This includes the production of event timelines, as well as the analysis of system logs, operating system state, file systems, and application data. The module will also consider the ethical and professional issues related to digital forensics.
Incident Response and Malware Analysis ( CSN11129 )
The aim of the module is to develop a deep understanding of advanced areas related to security and live/network forensics, with a strong focus on virtualised and Cloud-based environments that will allow graduates to act professionally within incident response and in malware/threat analysis. An outline of the main areas includes: • Threat Analysis. This involves an in-depth analysis of a range of current threats, such as DDoS, Botnets, trojans, and so on. • System Architectures, Services and Devices. Networked infrastructures (Servers/Firewall/IDS/ Syslog). • Network Forensics. Advanced Network Protocol Analysis, Advanced Trace Analysis, IDS Signature Detection, and Security Threat Network Traces. • Live Forensics. Code Analysis, Host/Network Analysis, Reverse Engineering. Mobile/x86 architecture, Machine Code Analysis, Vulnerability Analysis, Sandboxed Analysis. • Log Capture/Analysis, and Time-lining. Creating large-scale data infrastructure and analysis methods such as Big Data, SIEM and cross-log analysis (such as Splunk). • Malware Analysis. Static/Dynamic Analysis. Disassembly. Obfuscation. Behaviour Analysis. Encoding methods. • Data Hiding and Data Loss Detection/Prevention. Data hiding methods, detection methods, tunnelling, and disk encryption. • Host Investigation Evidence Gathering: Windows, Linux, Android and Mac OS. • Current Related Research.
Masters Dissertation ( SOC11101 )
The work for this module comprises the completion of an individual research project. Each student is assigned a personal Supervisor, and an Internal Examiner who monitors progress and feedback, inputs advice, examines the dissertation and takes the lead at the viva. There are two preliminary deliverables prior to the submission of the final dissertation: (1) Project proposal (2) Initial Report including time plan and dissertation outline
Network Security (D/L) ( CSN11118 )
The aim of the module is to develop a deep understanding of advanced areas related to security and digital forensics that will allow graduates to act professionally in the design, analysis, implementation, and reporting of network security strategies. An outline of the main areas includes: • Introduction. Networking Concepts; Network Security Concepts; Network Threats and Attacks; Network Defence - Perimeter, Defence in Depth • Firewalls. Concepts; Types - Host, Network; Technologies - Static packet filtering; Stateful packet filtering; Multilayer firewall; Architectures; Polices; Implementation and Deployment. • Intrusion Detection and Prevention Systems (IDPS). Concepts; Types; Alert Monitoring and Sensor Tuning; behavioural analysis, in-line/out-of-line. • Access Control and Authentication. Concepts: Trust and Identity; Attacks; Models - Access Control Models; Network Device Access Control; AAA, Layer 2; Device Hardening. • Remote Access and VPNs. Concepts; Cryptography; Types - L2, L3 and L4/5; Technologies; IPSec and SSL. • Wireless Security. Wireless Overview; Attacks; Encryption; Authentication. • CCNA Certification - Concepts. CIA; Attacks on CIA; Data Classification; Law and Ethics; Network policies; Risk Management and Secure Network Design; Security in the SDLC; Cisco self-defending network; Secure Administration. • CCNA Certification - Secure Infrastructure and Extending Security. Cisco Layer 2 Security; Cisco IOS Firewalls. Cisco IOS IPS; Cisco VPN and Cryptographic Solutions; Digital Signatures and PKI.
Security Audit & Compliance ( INF11109 )
The aim of the module is to let you develop a deep understanding of the context that information security operates in, and to give you an opportunity to carry out your own research and the present findings professionally. Topics covered include: • The role of laws and regulations: national and international, covering Data Protection, computer misuse and other legal issues. • The relation between governance models and frameworks including: ISACA’s COBIT and ISO Standards (ISO27000 in particular) • The role of the professionals, security culture and ethical environments • Management of risks and controls • Availability and continuity planning
* These are indicative only and reflect the course structure in the current academic year. Some changes may occur between now and the time that you study.
ACCREDITED BY

Study modules mentioned above are indicative only. Some changes may occur between now and the time that you study.
Full information is available in our disclaimer .
Entry requirements
English language, international students, admissions policies.
The entry requirement for this course is a Bachelor (Honours) Degree at a 2:2 or above in a Computing discipline e.g. Computing, Computer Science, Computer Networking, Software Engineering, or Cyber Security.
Other IT disciplines may be considered provided a minimum of 50% of the modules undertaken in the last two years of study were Computing related.
We may also consider lesser qualifications if you have sufficient relevant work experience.
Edinburgh Napier University welcomes applications from current and former Armed Forces personnel and offers entry based on training and education already received while in service. To assess your eligibility please contact our UK Student Recruitment team providing digital copies of your qualifications and indicating which course you would like to apply for.
Edinburgh Napier University is a member of the MOD’s Enhanced learning Credit scheme (ELC)
Can I get admission into Cyber Security based on my working experience in this sector?
This course has academic entry requirements which are assessed alongside relevant work experience. Full details of any relevant work experience, including references should be submitted with your application and may be considered for entry where the minimum academic entry requirements are below those required. Usually, unrelated work experience is not considered sufficient for entry without meeting the minimum academic entry requirements. Please contact us with your specific circumstances by submitting an enquiry form above and we will be happy to discuss your options.
Can I make an appointment with an advisor to discuss further about the admission process?
If you want to get more information on the admission process, please get in touch with the postgraduate admissions team by submitting an enquiry form above.
If your first language isn't English, you'll normally need to undertake an approved English language test and our minimum English language requirements will apply.
This may not apply if you have completed all your school qualifications in English, or your undergraduate degree was taught and examined in English (within two years of starting your postgraduate course). Check our country pages to find out if this applies to you.
- BM Midwifery/MM Midwifery
- All Graduate Apprenticeship courses.
See who can apply for more information on Graduate Apprenticeship courses.
We’re committed to admitting students who have the potential to succeed and benefit from our programmes of study.
Our admissions policies will help you understand our admissions procedures, and how we use the information you provide us in your application to inform the decisions we make.
Undergraduate admissions policies Postgraduate admissions policies
Fees & funding
The course fees you'll pay and the funding available to you will depend on a number of factors including your nationality, location, personal circumstances and the course you are studying. We also have a number of bursaries and scholarships available to our students.
- Undergraduate student fees and funding information
- Postgraduate student fees and funding information
- International student fees and funding information
The continued growth in the current requirement for cyber security professionals means there are a wide range of careers which can be followed after graduating from the course, such as:
- Security Consultant/Analyst
- Penetration Tester
- Network Security Analyst
- Forensic Investigator
- Audit/Compliance Consultant
- Security Certification Engineer
- Incident Response Analyst
- System Admin
- Network Engineer
The programme develops a range of key skills currently needed in industry, covering areas such as network security, penetration testing, security monitoring, incident response, malware analysis, operating systems, network and computer forensics, virtualisation and malware analysis. Materials from many professional courses are integrated into the curriculum, towards helping students prepare for sought after professional certification such as:
- Cisco Security Certifications
- Certified Information Systems Security Professional (CISSP)
- Offensive Security Certified Professional (OSCP)
- Centre for Research and Evidence on Security Threats (CREST)


COMMENTS
All figures below are based on out-of-state tuition rates. $32,940 is the most affordable online PhD program and its available at the University of Cumberlands. $56,004 is the average cost of the 14 online cybersecurity PhD programs. $85,248 is the highest tuition and is at the University of North Texas.
This means thinking about the career prospects for PhD graduates. A PhD in cyber security will open you up to the most senior positions in the field. According to PayScale, the average salary for those holding a PhD in cyber security is $172,000. 4. Course structure and content.
The University of Fairfax strives to extend learner-centered education through distance means to working professionals on various subjects, including cybersecurity. You can choose to pursue this online PhD in cyber security program in a hybrid format, where part of the program is delivered face to face through an on-campus residency.
PhD in Cyber Operations. Dakota State University is accredited by the Higher Learning Commission. 5. Marymount University. Marymount University's Doctor of Science in Cybersecurity program places a premium on such topics as technology, data science, policy, leadership, management, ethics, and teaching.
Yes, there are affordable online PhD in Cyber Security programs. Because it is such an in-demand industry, online degrees are plentiful and many are affordable. Tuition for online programs range from about $50,000 per year to as low as $9,000 per year. Most programs fall somewhere in the range between $10,000 and $15,000.
Learn cybersecurity skills from Stanford faculty and professionals with online courses and programs. Choose from graduate-level courses for academic credit or self-paced courses for certificates.
PhD's in Cyber Security often take between 3 and 7 years to complete. This process is often broken down into two years of graduate level classes, followed by three to five years in which students are preparing a substantial original piece of research. ... The University of Fairfax was granted accreditation by the Distance Education ...
PhD in Cybersecurity Program Outcomes. Formulate solutions to cybersecurity problems. Evaluate the scope and impact of emerging technologies in cybersecurity on a local and global scale. Manage legal, ethical, and security risks in technology-based systems. Explain concepts and arguments associated with cybersecurity.
Best Online PhD Cybersecurity Programs in 2024. Pursuing an online PhD in cybersecurity is a convenient way to advance your career. Learn more about enrolling in an accredited program that works for you.
The Doctor of Computer Science with a concentration in Cybersecurity and Information Assurance (DCS-CIA) is a 100-credit-hour terminal degree in computer science. The program includes 40 credit hours of core management courses, 20 credit hours of cybersecurity and information assurance concentration courses, 4 credit hours of symposium-related ...
Jobs and Salary Prospects for Doctors of Cybersecurity. Some of the common roles and median annual salaries for graduates with a PhD in cybersecurity include: Cybersecurity Engineer - $125,816. Information Security Manager - $96,406. Chief Information Security Officer (CISO) - $124,405. Security Architect - $111,433.
A Ph.D. in cybersecurity prepares graduates for advanced, high-level job opportunities, including roles in research, education and management. Cybersecurity Ph.D. programs allow students and ...
The degree requires completion of eight graduate-level courses (listed below) and a minimum of 24 credit hours of Praxis Research (SEAS 8188). ... SEAS 8416 Python Tools for Cybersecurity: Learning Python & and its role in cybersecurity. Perform secure coding, network analysis, cryptography, malware analysis, and automation of cybersecurity ...
Online PhD in Cyber Security Degree Availability. Many online-based institutions that offer programs within computer science and cybersecurity also feature accredited doctorate degrees. Students can expect to find disciplines directly in cybersecurity or in a similar field, such as information assurance or security in information technology.
The Cybersecurity Graduate Program provides a professional, technical and policy view of the challenges created by rapid advancements in information technology. You'll examine principles of computer systems security, including attack protection and prevention. By combining computer science and application, this program's interdisciplinary approach will give you the vital skills needed for ...
The PhD in Cybersecurity requires the following courses for every specialization: TIM-7010 - Computer Networks & Mobile Computing; TIM-8301 - Principles of Cybersecurity; TIM-8305 - Cyber Risk, Contingencies, and Incidents; TIM-8315 - Cyber Automation, Artificial Intelligence, and Machine Learning; TIM-8330 - Advanced Risk Management ...
The benefits of Georgia Tech's Online Master of Science in Cybersecurity are many, but some of the highlights include: Learning from the same comprehensive on-campus curriculum without interrupting your career. Flexibility to choose the number of courses to fit your schedule and complete your degree at your own pace.
Fields like Big Data and Cybersecurity are overtaking the IT sector when it comes to hot jobs. At Missouri S&T, we offer specialized graduate degrees and certificate programs that stand above the competition. And our rankings prove it. Computer information technology online graduate programs are national ranked (U.S. News and World Report ...
Distance Learning PhD Degrees in Cybersecurity Governments, businesses, and private citizens all use computers on a daily basis. Cyber security exists to protect computer systems and shared data from theft or damage by any presence that plans to do harm.
A UK 2:1 honours degree, or its international equivalent, in computer science, mathematics, linguistics, or a related discipline. A Masters degree or equivalent, in information security, cyber security or a closely related discipline is recommended. International qualifications
The Information Security Group runs a popular full-time and part-time PhD research programme on a wide variety of information security-related topics. The ISG has supervised hundreds of PhD students in its history, many now holding influential positions within the cyber security industry. We are looking for enthusiastic, inquisitive, and ...
Extensive innovative research is also carried out in key domains by academics and PhD students in our dedicated cyber security and forensic research group. Lead academics. Programme Leader. Rich Macfarlane. Module Leaders. Rich Macfarlane ... The distance learning course runs in parallel with our on-campus course and is aligned to the same ...