TheLeanSuite

Got a question? Call us at +1-616-433-6688

People and Morale
Suggestions, suggestion platform.
Collect and implement million dollar ideas
Compentency Planning
Track and upscale workforce skills with ease
Learning Management System
Build and deploy on-demand training with ease
Job Cover Matrix
Loss and cost management.
Collect data and compile production loss trees
Quality Management
Prioritize internal and external quality defects
Issue Tracker
Identify, assign and close shop-floor anomalies quickly
Continuous Improvement
Document and manage quick to complex kaizens
Gemba Walker
Make the most out of the shop floor walks
CILR Management
Schedule & plan maintenance activities
Suggestion Management
Issue tracker for quality, issue tracker for operations, issue tracker for safety, suggestions, suggestion system for hr, suggestion system for operations.
- Why TheLeanSuite
FEATURED BLOG POST

- What is a Continuous Improvement Culture (CIC)?
PDCA Cycle: What is the Plan-Do-Check-Act Cycle?
- Five Benefits of Continuous Improvement in Manufacturing
The 8 Wastes of Lean: DOWNTIME
- Continuous Improvement vs Process Improvement: the Differences
- The Most Popular Lean Six Sigma Tools and Techniques
- SCHEDULE FREE DEMO
Depending on the complexity of the problem, some tools are more appropriate than others. That is to say, as the complexity of the problem increases, use the relevant tools (described above in the graph) accordingly.
What are the Four Lean Tools for Simple Problem Solving?
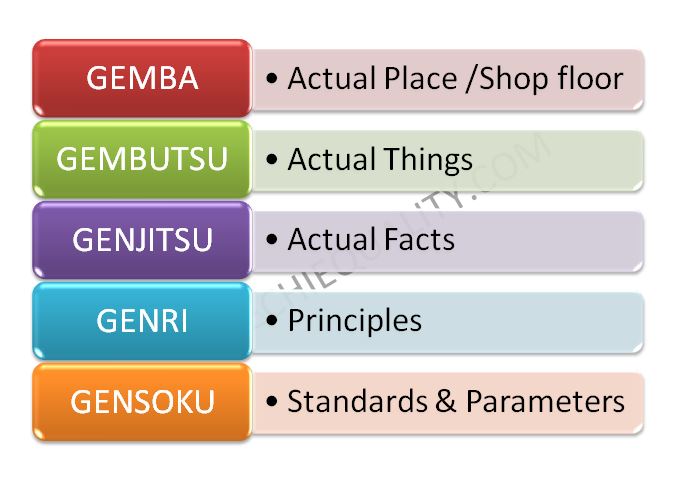
The most basic and first of four lean tools for simple problem solving is 5G. Also known as the 5 Gen Methodology or the 5 Gen principle, 5G is a popular Japanese problem-solving method used for improving various manufacturing activities. That is to say, it is a tool that describes a loss phenomenon that can be related to safety, quality, parts shortage, etc. 5G is made up of five Japanese words that all start with the letter “G”: Gemba, Gembutsu, Genjitsu, Genri, and Gensoku.
The 5G Procedure

5W1H is the second of four lean tools for simple problem solving. Essentially, it helps contribute to the resolution of a problem by answering existing questions and triggering ideas.

The 5W1H questions are:
- 1. Who — this refers to a specific person or group of people who are relevant to the problem or situation. For example, this can include who identified the problem, who can potentially solve the problem, and who will be responsible for implementing the solution.
- 2. What — when answering what, you should describe the situation and problem in detail. If possible, you should also identify the overall goal for implementing the determined solution.
- 3. Where — for the where , state the exact location, area, or position of the identified problem. For example, this can be at a specific pillar or machine.
- 4. When — the when should include anything related to the problem that has to do with dates. For example, the timeline, deadline, duration, or any other date-related details that can help solve the identified problem.
- 5. Why — this is the most important element of the 5W1H method. The why details the reason and objectives for why action needs to be taken or why there’s a need to use the 5W1H method. Additionally, this last W is usually asked five times to discover the root cause of the problem and to prevent it from happening again — this approach is better known as the 5 Whys analysis.
- 6. How — for the how , specify the steps necessary to implement the solution to solve the problem. This includes all the tools, resources, methods, and even expenses needed to carry out the plan.
4M1D, or also known as the 4M1D fishbone diagram, is the third of four lean tools for simple problem solving. In short, this is a fairly universal tool used to identify as many potential causes for a problem as possible. Moreover, it can be used to structure a brainstorming session and immediately sorts significant contributors into useful categories. The major categories of the 4M1D fishbone diagram are material, method, machine, man, and design. However, other “M’s” that may have an impact include management, money, and maintenance. In essence, the 4M1D fishbone diagram can be adjusted based on the needs of the identified problem. 4M1D is similar to the 5 Ms of Lean Manufacturing .

The 4M1D Procedure
The procedure for conducting the 4M1D fishbone diagram is usually done with pen and paper, or on a whiteboard, and are as follows:
- 1. Identify a specific problem (in as little as 3-5 words) then write it at the centre right of your paper or whiteboard. Draw a box around it and then starting from the left side of the box, draw a horizontal line running across to the centre left of the page.
- 2. Brainstorm and determine the major categories that may have an impact on the identified problem. Then write each category as branches from the main horizontal line running across the paper or whiteboard.
- 3. Brainstorm and identify all the possible causes for the specified problem and ask, “why does this happen?” As each idea is given, the leader of this analysis writes it as a branch from the relevant category. It is important to note that possible causes can be placed in more than one category.
- 4. Again, ask “why does this happen?” for each cause that is written down and write down sub-causes that branch off from the main cause. Continue doing this to create a deeper understanding of the causes — the layers of branches represent causal relationships.
The primary goal of the 5 Whys analysis is to find the root cause of a given problem by asking a series of “why” questions five times. However, in some cases, it may take more or fewer whys, depending on the complexity of the root cause.
The 5 Whys analysis is the final of four lean tools for simple problem solving and it is one of the most powerful assessment tool of all non-statistical analyses. In short, by using this analysis, you’ll be able to identify the root cause of the problem and understand the underlying cause and effect of the identified problem.
The 5 Whys Procedure
Listed below are the steps you should follow to complete the 5 Whys analysis:
- 1. Start by identifying a specific problem — what is it that you are having difficulties with? Jot this down somewhere. For example, on a piece of paper.
- 2. Ask why this problem has occurred and write the answer below the identified problem.
- 3. Continuously ask “why” to each of the successive answers you write down until you arrive at and determine the root cause of the problem.
To reiterate, again, the 5 Whys analysis may take more or fewer than 5 whys to determine the root cause. Additionally, it is important to ensure that all team members collaborating on the 5 Whys analysis agree with each of the questions being answers, as well as the root cause of the problem.
Share this:
Related blogs.

The Plan-Do-Check-Act (PDCA) cycle is a timeless and iterative management

In the search for operational excellence, businesses are continually refining

DMAIC Process: A Quick Guide for Beginners
The DMAIC process stands out as a powerful tool for
360 Degree view of Lean Program

Ready to Digitze your Lean Manufacturing Journey?
Fill out the form and an advisor will reach out to you at the earliest..
Invalid value
Discover more from TheLeanSuite
Subscribe now to keep reading and get access to the full archive.
Type your email…
Continue reading

- New Zealand
- Czech Republic
- Netherlands
- United Kingdom
- South Africa
- Training
- Certification
- Tours
- Learning Material
- Glossary
- Use KAIZEN™
Kaizen Institute Blog

12. Jun 2018
Kobetsu KAIZEN™ and 5G methodology
by Narasimhan Gopalkrishnan-Senior Consultant at Kaizen Institute IndAf
$post['sub_header']?>
Kobetsu Kaizen™ is the first pillar of TPM. It is loosely translated as Self-Improvement or Focussed improvement. It is difficult to find the right meaning for the word Kobetsu. Japanese is written in two scripts – Kanji and Kana 個別. If written in Kana, the meaning would be house-to-house, door-to-door, each house. If written in Kanji, it would represent particular case; discrete; individual; separate etc., Since this pillar focuses on solving a particular type of loss, it is preferred to be termed as Focused improvement. Unlike the Autonomous Maintenance (Jishu Hozen) where equipment per se is addressed, Focused improvement (Kobetsu Kaizen™) is intended to prevent the accelerated deterioration of equipment parts.
The Kobetsu Kaizen™ (or FI teams) often face recurring problems in the performance of the Equipment. We all are aware that the objective of TPM is Zero stoppages (unplanned stoppages). The losses can be classified into two categories – Sporadic and Chronic. Sporadic losses indicate sudden large deviations from the standard. They are immediately addressed and arrested. Chronic problems indicate smaller but frequent deviations from the standards. They are not immediately addressed and gradually we all accept them as a part of the process and start living with those problems. While the sporadic losses are attacked, the chronic problems that results in loss of performance, quality and productivity does not seem to go away. It is a well-established fact that Chronic losses attribute to 5~10% of the total losses. Under such circumstances, achieving Zero Breakdowns becomes next to impossible.
Kunio Shirose defined TPM as not only a set of activities for restoring equipment to optimal conditions but also to create an environment to sustain those conditions. Focused Improvement is the process of applying systematic problem solving methods to manufacturing. It is all about the focused improvement of not only the equipment but also the processes as to reduce the losses in manufacturing. This is achieved by the collaborative effort of production workers and the maintenance team. The process relies on aligning the correct method to the correct scenario. When a known solution exists to a problem clearly demonstrated, the rigour and analysis to find this solution becomes unnecessary as the learning from the history can be used to resolve the problem and it is inexpensive to implement. If such a solution is expensive or difficult to implement, the rigour and analysis of the problem must be improved.
The methodical approach of resolving the problems in Kobetsu KaizenÔ has some similarities with the 5G approach. The five Gs are Gemba – the real place, Gembutsu – the real tools pertaining to the Gemba, Genjitsu – the real facts which can be obtained only from the Gemba, Genri – that explains the principle of operation and Gensuko – Standardization or Institutionalization.
Gemba: The first “G” is called the Gemba. Gemba is a combination of two Japanese words Gem and Ba. Roughly translated Gemba means a “raised podium or raised platform”. Just as a raised platform draws attention of one and all, the Gemba should draw attention of one and all. Or in other words, Gemba means the real place where the value is added, where the problems are resolved, where the work is happening. The Gemba is the location where the incident actually occurred…..at the SOURCE of the problem, which may not be where the majority of the losses occurred. Whenever there is a problem or an abnormality, the first thing we need to do is to “go-to-the-Gemba”! It is especially important for the members of the team that is assigned to resolve the problem. Everyone needs to have the same perspective and knowledge of the current equipment areas that are being investigated. During the visit to the Gemba the remaining 4 “G” should be considered by the team.
Genbutsu: The second “G” is known as Genbutsu. This is also termed as Genchi Gembutsu loosely translated means “go & see”. The use of M or N in Gemba, Gembutsu does not matter considering the phonetic issues. While at the Gemba, the team should examine the equipment parts and materials that were associated with the problem or the failed equipment. At times, there could be instances, where the problematic parts would have been removed (as to keep the line running) even before the team arrives on the Gemba. However, the team should insist on all the parts pertaining to the place for a detailed study which could explain how the failure had happened.

Genjitsu: The third “G” is Genjitsu. Genjitsu refers to Data and Facts around the area of concern. In this step, the team must gather all the data available about the 4Ms precisely say, process, equipment and materials before and after the condition of the problem. These data will assist the team in linking the facts behind the evidence that the team sees and what had happened. While collecting the data, ensure the team includes the variable control data from the line, collect the real-facts after having informal chat with the Gemba-owners at the time of the failure or problem occurred
Genri: The fourth “G” represents Genri. Genri refers to Principles. Prior to attending to resolve an abnormality or a problem, one should be aware of the principle of operation. This would help the problem-solvers to do the root cause analysis in the right perspective. This is because, knowing the operational principle would help the team discriminate the current condition from the ideal condition. The gaps will be clearly seen without which, at times, the problem-solvers will be groping in dark and could be misled too.
Gensoku: The fifth “G” is Gensoku. Gensoku refers to Standards and parameters. There could be a possibility that the equipment failed because of deviations from the standards – more importantly the method-standard. The Gemba-owner might be unaware of the Standard Operating Procedures. The One Point Lessons were not made or not providing clarity. The standard parameter chart was missing and the operator had set wrong parameters. In short, the actions or wrong-actions of the operator might lead to the problem. Verifying the Standards, SoPs, OPLs, JI (Job Instructions), EIS (Element Instruction sheets), enables the team identify the origin of the problem. Once the problem is resolved, the team should also ensure that the standards are revised accordingly as to prevent the recurrence.

Utilizing the “5G Principles” will enable the leader to conduct the root cause analysis (RCA) in the right perspective. To be precise, this 5G methodology is well adapted in QRQC (Quick Response Quality Control) popularized by Valeo Engineering that harps on Rapid problem solving by Gemba-owners. As a result, the process will be more stable and working on the line will be less problematic.
As and when we face problems or abnormalities, all 5G’s should be used however, the 1st G – Go-to-Gemba must always be studied to ensure all our assumptions are correct. The use of Gembutsu, Genjitsu, Genri & Gensoku to resolve problems is purely based on experience. The study of Gembutsu and Genjitsu has to be systematic. This has dual benefits, the first one that provides a common methodology across the organisation on how the data and facts are collected, recorded and used in root-cause-problem-solving. The second benefit is such systematic approach of collecting data & facts brings in a common understanding of the problem across the organization. This is followed by the 5W1H approach.
The other 2G’s, Genri & Gensoku can be studied if experience does not reveal the causes of the problem even after the 5W+1H problem statement is made. The root cause of the problem will be found only when we find the immediate cause. Once the root cause is found, the solution should be implemented as to eliminate the cause without which we will not experience the benefits of Kobetsu Kaizen. The practice of Kobetsu KAIZEN™ has always yielded results. The added advantage is the 5G approach quashes the division in organizations created by opinions as it is focussed on Data & Facts. Problem solving becomes more structured with revision of standards happening as the team learns from the problem-solving exercise. Let us adapt this 5G approach in our problem solving too. Happy problem solving!
If you wish to read & learn more from our blog, click here to follow our blog by subscribing the same.
Recent Posts
11. Sep 2020
by N Gopalkrishnan, Director & Senior Consultant – East Africa & Farms at Kaizen Institute
04. Sep 2020
by Diwakar Jayaswal , Senior Consultant at Kaizen Institute
07. Aug 2020
by Vineet Rajak, Consultant & Member R&KD at Kaizen Institute
30. Jul 2020
by Mr. Arvind Kulkarni, Director HR at Kaizen Institute.
24. Jul 2020
by Venkatesh Pandarinathan, Senior Consultant at Kaizen Institute
13. Jul 2020
by Naresh Chawla, Sr Consultant at Kaizen Institute
02. Jul 2020
by Ajit Bhist and Paresh Chaudhary of Kaizen Institute
24. Jun 2020
22. Jun 2020
19. Jun 2020
by Atul Ghai, Senior Consultant at Kaizen Institute
11. Jun 2020
by N. Gopalkrishnan, Director – East Africa at Kaizen Institute
10. Jun 2020
by Vineet Rajak and Satish Bahale of Kaizen Institute
02. Jun 2020
by Naresh Chawla, Senior Consultant at Kaizen Institute
25. May 2020
by Murali Venkitanarayana & Harsh Choudhary of Kaizen Institute
21. May 2020
by Vishwanathan Ramamurthy, Senior Consultant at Kaizen Institute
20. May 2020
by Sourabh Satbhai, Senior Consultant at Kaizen Institute
18. May 2020
by Satish Bahale & Murali Venkitanarayana of Kaizen Institute
15. May 2020
by Murali Venkitanarayana, Senior Consultant at Kaizen Institute
13. May 2020
by N. Gopalkrishnan, Director at Kaizen Institute-East Africa
26. Mar 2020
by Kaizen Institute India
27. Jun 2019
04. Dec 2018
by NARASIMHAN GOPALKRISHNAN-SENIOR CONSULTANT AT Kaizen Institute India and Africa
30. Oct 2018
by Narasimhan Gopalkrishnan, Senior Consultant, Kaizen Institute India
11. Sep 2018
by NARASIMHAN GOPALKRISHNAN-SENIOR CONSULTANT AT Kaizen Institute INDAF
05. Sep 2018
25. Jul 2018
27. Jun 2018
19. Jun 2018
29. May 2018
by SUNIL MALAGI-SENIOR CONSULTANT AT Kaizen Institute INDAF
22. May 2018
15. May 2018
by Sunil Malagi-Senior Consultant at Kaizen Institute Indaf
08. May 2018
01. May 2018
10. Apr 2018
by NARASIMHAN GOPALKRISHNAN
03. Apr 2018
28. Mar 2018
17. Jan 2018
by Divyakumar Soneji
02. Jan 2018
by Masaaki Imai
26. Dec 2017
13. Dec 2017
by Fons Trompenaars and Charles Hampden
05. Dec 2017
by CHRISTENSEN CALAYTON M
29. Nov 2017
by Christensen calayton M
14. Nov 2017
by Harish Jose
07. Nov 2017
01. Nov 2017
24. Oct 2017
11. Oct 2017
by Alan Culler
26. Sep 2017
19. Sep 2017
by Jayanth Murthy
05. Sep 2017
29. Aug 2017
by Dr. Richard W. Taylor and Alan Cay Culler
22. Aug 2017
by PETER F DRUCKER
16. Aug 2017
by Peter F Drucker
08. Aug 2017
01. Aug 2017
26. Jul 2017
18. Jul 2017
11. Jul 2017
07. Mar 2017
by Keki R Bhote
28. Feb 2017
07. Feb 2017
by MASAAKI IMAI
31. Jan 2017
25. Jan 2017
18. Jan 2017
by Benjamin Franklin
10. Jan 2017
by Euclides A. Coimbra
27. Dec 2016
20. Dec 2016
13. Dec 2016
06. Dec 2016
30. Nov 2016
22. Nov 2016
15. Nov 2016
08. Nov 2016
25. Oct 2016
18. Oct 2016
by Amy Chavez
12. Oct 2016
04. Oct 2016
27. Sep 2016
by Micah Solomon
21. Sep 2016
13. Sep 2016
by Alan G. Robinson,Dean M. Schroeder
06. Sep 2016
30. Aug 2016
23. Aug 2016
by James P.Womack, Daniel T.Jones, Daniel Roos
16. Aug 2016
09. Aug 2016
02. Aug 2016
by Joseph T. Dager
26. Jul 2016
22. Jul 2016
19. Jul 2016
by A Japanese technique for overcoming laziness
13. Jul 2016
by RUSSELL EISENSTAT,BERT SPECTOR,MICHAEL BEER
05. Jul 2016
by Russell Eisenstat,Bert Spector,Michael Beer
28. Jun 2016
by HARISH JOSE
21. Jun 2016
14. Jun 2016
07. Jun 2016
31. May 2016
24. May 2016
by Vinod Grover, Founding Partner & Director,Kaizen Institute India
17. May 2016
10. May 2016
by JAMES WOMACK & JIM WOMACK
03. May 2016
by James Womack & Jim Womack
26. Apr 2016
19. Apr 2016
12. Apr 2016
05. Apr 2016
29. Mar 2016
22. Mar 2016
15. Mar 2016
by Lisa Quast
08. Mar 2016
by David Mann
01. Mar 2016
26. Feb 2016
by Vinod Grover
23. Feb 2016
19. Feb 2016
by Jim Rohn
12. Feb 2016
by Creating A Lean Culture book by David Mann
09. Feb 2016
by Jon Miller,Ex-CEO, Kaizen Institute Consulting Group
05. Feb 2016
02. Feb 2016
29. Jan 2016
25. Jan 2016
19. Jan 2016
15. Jan 2016
12. Jan 2016
08. Jan 2016
05. Jan 2016
02. Jan 2016
22. Dec 2015
18. Dec 2015
15. Dec 2015
by Brian Maskell & Bruce Bagalley
09. Dec 2015
01. Dec 2015
24. Nov 2015
17. Nov 2015
10. Nov 2015
29. Oct 2015
23. Oct 2015
16. Oct 2015
13. Oct 2015
09. Oct 2015
06. Oct 2015
29. Sep 2015
26. Sep 2015
22. Sep 2015
18. Sep 2015
16. Sep 2015
11. Sep 2015
08. Sep 2015
04. Sep 2015
01. Sep 2015
28. Aug 2015
18. Aug 2015
14. Aug 2015
11. Aug 2015
07. Aug 2015
04. Aug 2015
31. Jul 2015
28. Jul 2015
24. Jul 2015
22. Jul 2015
17. Jul 2015
14. Jul 2015
07. Jul 2015
03. Jul 2015
30. Jun 2015
23. Jun 2015
19. Jun 2015
09. Jun 2015
05. Jun 2015
02. Jun 2015
26. May 2015
22. May 2015
19. May 2015
15. May 2015
08. May 2015
05. May 2015
02. May 2015
21. Apr 2015
17. Apr 2015
14. Apr 2015
10. Apr 2015
07. Apr 2015
31. Mar 2015
27. Mar 2015
24. Mar 2015
17. Mar 2015
14. Mar 2015
10. Mar 2015
05. Mar 2015
03. Mar 2015
27. Feb 2015
25. Feb 2015
20. Feb 2015
18. Feb 2015
13. Feb 2015
by Nidhi Shah
10. Feb 2015
06. Feb 2015
03. Feb 2015
30. Jan 2015
23. Jan 2015
20. Jan 2015
13. Jan 2015
09. Jan 2015
06. Jan 2015
02. Jan 2015
23. Dec 2014
19. Dec 2014
16. Dec 2014
09. Dec 2014
02. Dec 2014
28. Nov 2014
21. Nov 2014
17. Nov 2014
13. Nov 2014
10. Nov 2014
06. Nov 2014
03. Nov 2014
30. Oct 2014
28. Oct 2014
21. Oct 2014
20. Oct 2014
14. Oct 2014
10. Oct 2014
07. Oct 2014
02. Oct 2014
01. Oct 2014
29. Sep 2014
25. Sep 2014
22. Sep 2014
15. Sep 2014
11. Sep 2014
08. Sep 2014
04. Sep 2014
02. Sep 2014
01. Sep 2014
28. Aug 2014
25. Aug 2014
21. Aug 2014
19. Aug 2014
14. Aug 2014
12. Aug 2014
11. Aug 2014
07. Aug 2014
04. Aug 2014
01. Aug 2014
31. Jul 2014
28. Jul 2014
22. Jul 2014
21. Jul 2014
17. Jul 2014
14. Jul 2014
12. Jul 2014
08. Jul 2014
03. Jul 2014
01. Jul 2014
30. Jun 2014
19. Jun 2014
16. Jun 2014
09. Jun 2014
05. Jun 2014
02. Jun 2014
29. May 2014
26. May 2014
22. May 2014
19. May 2014
16. May 2014
15. May 2014
12. May 2014
08. May 2014
05. May 2014
28. Apr 2014
24. Apr 2014
21. Apr 2014
17. Apr 2014
15. Apr 2014
14. Apr 2014
10. Apr 2014
07. Apr 2014
04. Apr 2014
03. Apr 2014
31. Mar 2014
25. Mar 2014
18. Mar 2014
13. Mar 2014
10. Mar 2014
06. Mar 2014
03. Mar 2014
24. Feb 2014
19. Feb 2014
18. Feb 2014
10. Feb 2014
03. Feb 2014
30. Jan 2014
27. Jan 2014
23. Jan 2014
20. Jan 2014
17. Jan 2014
16. Jan 2014
13. Jan 2014
09. Jan 2014
06. Jan 2014
02. Jan 2014
24. Dec 2013
12. Dec 2013
09. Dec 2013
05. Dec 2013
02. Dec 2013
01. Dec 2013
29. Nov 2013
26. Nov 2013
19. Nov 2013
15. Nov 2013
14. Nov 2013
13. Nov 2013
12. Nov 2013
09. Nov 2013
04. Nov 2013
31. Oct 2013
29. Oct 2013
24. Oct 2013
21. Oct 2013
19. Oct 2013
17. Oct 2013
15. Oct 2013
14. Oct 2013
11. Oct 2013
08. Oct 2013
03. Oct 2013
02. Oct 2013
26. Sep 2013
24. Sep 2013
23. Sep 2013
20. Sep 2013
18. Sep 2013
03. Sep 2013
02. Sep 2013
31. Aug 2013
29. Aug 2013
22. Aug 2013
19. Aug 2013
by KAIZEN™
13. Aug 2013
12. Aug 2013
09. Aug 2013
06. Aug 2013
03. Aug 2013
31. Jul 2013
27. Jul 2013
25. Jul 2013
24. Jul 2013
22. Jul 2013
19. Jul 2013
16. Jul 2013
12. Jul 2013
11. Jul 2013
06. Jul 2013
04. Jul 2013
03. Jul 2013
01. Jul 2013
27. Jun 2013
26. Jun 2013
21. Jun 2013
18. Jun 2013
17. Jun 2013
13. Jun 2013
04. Jun 2013
31. May 2013
28. May 2013
24. May 2013
22. May 2013
21. May 2013
18. May 2013
17. May 2013
16. May 2013
10. May 2013
03. May 2013
02. May 2013
30. Apr 2013
26. Apr 2013
24. Apr 2013
23. Apr 2013
16. Apr 2013
11. Apr 2013
10. Apr 2013
04. Apr 2013
30. Mar 2013
26. Mar 2013
25. Mar 2013
23. Mar 2013
21. Mar 2013
19. Mar 2013
15. Mar 2013
12. Mar 2013
09. Mar 2013
07. Mar 2013
05. Mar 2013
04. Mar 2013
28. Feb 2013
27. Feb 2013
25. Feb 2013
23. Feb 2013
22. Feb 2013
19. Feb 2013
16. Feb 2013
13. Feb 2013
12. Feb 2013
09. Feb 2013
06. Feb 2013
28. Jan 2013
24. Jan 2013
22. Jan 2013
21. Jan 2013
16. Jan 2013
12. Jan 2013
11. Jan 2013
07. Jan 2013
05. Jan 2013
02. Jan 2013
31. Dec 2012
26. Dec 2012
25. Dec 2012
24. Dec 2012
22. Dec 2012
21. Dec 2012
20. Dec 2012
17. Dec 2012
14. Dec 2012
23. Aug 2012
22. Aug 2012
01. Feb 2010
03. Nov 2009
26. May 2009
03. May 2009
09. Apr 2009
Get all the latest news about Kaizen Institute India. Subscribe now.
By signing up, you agree to our Privacy Policy
- Brand Promise
- Why KAIZEN™
- What is KAIZEN™
- Masaaki Imai
- Origami Symbols
- Learn KAIZEN™
- Certification
- Learning Material
- KI Training: Brochure Download
- What we offer
- Consulting Models
- Lean Transformation
- Find the right Consultant
- Senior Consultant
- Support Consultant
Terms of Use
Privacy Policy
Cookie Policy

Thank you for your interest in Kaizen Institute’s services. Please provide the following information about your business needs to help us serve you better.
* required fields

TECHIEQUALITY
5g problem solving technique | manufacturing example |free template.
5G Problem solving technique is the most popular Japanese technique, this will help and guide you on how to solve problems. Many problems is being occurred day to day in manufacturing industries like machine breakdowns, customer complaints, in-process rejection problems, material problems, etc. So to tackle the everyday problem in an unsystematic way is a big challenging work. To overcome this issue, you can follow the 5S Japanese concept to resolve actual/real place problems. It’s namely called 5G because every Japanese word starts with the letter “G” i.e. [1] GEMBA, [2] GEMBUTSU, [3] GENJITSU, [4] GENRI, [5] GENSOKU; these are the 5G where you have to find out the causes. In some cases, you can propose and predict the right cause without visiting the real place and analyzing the actual facts. So this method helps you to resolve the problem.
DOWNLOAD Template- 5W1H , CAPA , 5W2H , 4M check sheet , 8D Format .
5G Problem solving Technique with Manufacturing Example:
Here I’m sharing my own experience that once upon a time I had made a great mistake during an analysis of a customer complaint, one of our customers informed us 5% of the last batch of consignment products had been rejected due to a pinhole issue. Immediately after receiving the customer complaint, we called a meeting with all my team members. And we all started discussing in the conference room to find out the cause of the problem and finally, we proposed an action plan and implemented the same but later on we faced the same problem again.
Our hypothesis / predicted root cause of the failure was invalid. From this experience, I learned that we can’t find an effective action plan by hypothesis or prediction. We must investigate the actual things and verify the principles. And finally, we applied the Japanese technique 5G for problem-solving i.e. [1] GEMBA, [2] GEMBUTSU, [3] GENJITSU, [4] GENRI, [5] GENSOKU.
Before continuing with the above example I would like to elaborate on the 5G Technique /Method.
GEMBA: Go to the Real /Actual Place.
It’s the place/location where the problem actually occurred e.g. Shop floor. First of all, we have to visit the shop floor or the actual location where we need to start the investigation.
GEMBUTSU: Examine the objects /machine/tools etc.
Your problem-solving team members should examine the machine, parts, objects, and tools that were involved in the failure. During the examination, you can find any clues of failure.
GENJITSU: Check the real Facts
Your team must collect the before and after data and test report, and the team should link the data to the actual facts that what really happened.
GENRI: Refer to the theory /verify the principle.
The team should verify the principle and condition of the machine/equipment/tools etc.
GENSOKU: Check the process parameters /SOP/Standards.
In this technique the team member should check and verify the process parameters, SOP, Work procedure, Visual instruction, and one-point lesson are followed by operators and that there is no any deviation.
How to apply 5G technique in the manufacturing industry?
We will elaborate on this section continuing with the above example that our action plan against the customer complaint (Pin-hole problem) was not valid. When we applied the 5G technique, the action plan was very effective. First of all, all the team members visited to the shop floor to know the exact problem when we examined the problem we came to know that the actual problem was a blow-hole but not a pin-hole. This was visualized when we went through the G-2 (Gembutsu).
Next, we continued the rest of three-G, some clues we found at the stage of Genjutsu from the Core curing time and some from Gensoku. That curing procedure was not being maintained as per the standard operating procedure. And finally, we concluded after completing the 5G technique on a fact basis that the core curing process was not maintained as per SOP. This is my own experience that how I could able to find out the problem causes using the 5G technique. Given below are the 5-steps, details meanings, concepts, and illustrations of 5G.
Step-by-Step Guide to 5G Problem Solving Technique Application
Free Templates / Formats of QM : we have published some free templates or formats related to Quality Management with manufacturing / industrial practical examples for better understanding and learning. if you have not yet read these free template articles/posts then, you could visit our “ Template/Format ” section. Thanks for reading…keep visiting techiequality.com
More on TECHIEQUALITY
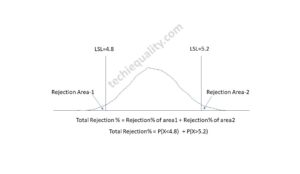
Normal Distribution Probability Formula, Calculation & Manufacturing Examples
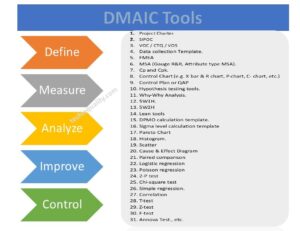
DMAIC Tools | DMAIC Template | Six Sigma Methodologies | 30+ Free Tools

Six Sigma Project Examples | 15+ Project Examples
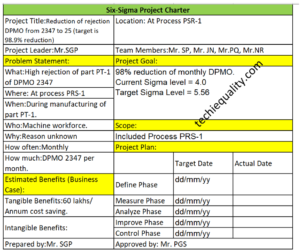
Six Sigma Project Charter Template
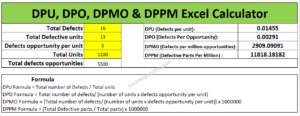
DPMO Calculation, Formula, Template & Manufacturing Example
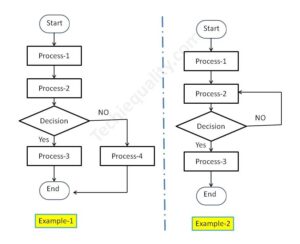
Process Flow Diagram Template | Examples |Symbols |PFD
What is Visual Management? | Visual Management Board Examples
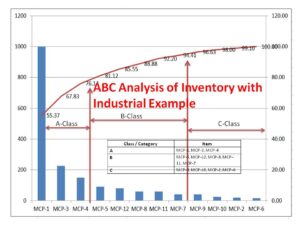
ABC Analysis of Inventory with Industrial Example
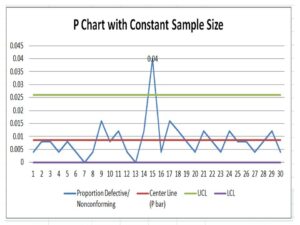
P Chart Excel Template | Formula |Example | Control Chart | Calculation
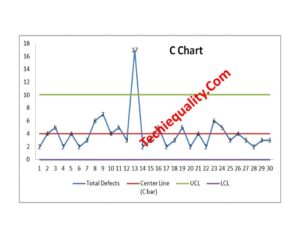
C Chart Excel Template | Formula | Example | Calculation

4M Change Management | How to implement in Manufacturing unit | Template | Format
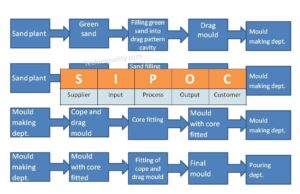
SIPOC Template | SIPOC Diagram Example of Manufacturing & Service Industry
Popular Post
Related Posts
The Author is an Expert in Quality Management System, Operation Management, Business Excellence, Process Excellence, IATF 16949, ISO 9001, ISO 14001, ISO 45001, ISO 17025, TQM, TPM & QA. He is Certified as an IA for ISO 9001, IATF 16949, ISO 14001, ISO 17025 & ISO 45001 Standard.
Your email address will not be published. Required fields are marked *
Email Address: *
Save my name, email, and website in this browser for the next time I comment.
Researchers work to solve 5G network problems when it matters: right now
- Kelly Izlar
14 Dec 2022
- Share on Facebook
- Share on Twitter
- Copy address link to clipboard

5G can enable smart cities, virtual realities, and self-driving cars — but will these applications be convenient and safe to use if network connection is delayed? Commonwealth Cyber Initiative researchers from Virginia Tech developed a methodology that provides optimal solutions to network problems on the fly and in real time.
The fifth generation of mobile network (5G) is bringing more applications, devices, and users into network operations. But spiking demand can stress local networks, creating bottlenecks that are narrowed by safety-critical or other high-priority tasks that need to happen as soon as possible.
Computer engineers such as Virginia Tech’s Tom Hou have dedicated their careers to fine-tuning network parameters and components to get ever closer to peak performance — an endeavor further complicated by real-time demands.
“The holy grail of my research has always been timing,” said Hou, the Bradley Distinguished Professor of Electrical and Computer Engineering in the College of Engineering.
Timing constraints have forced computer engineers to modify their algorithms to stay within suboptimal network thresholds, which limits functionality and throttles performance.
This changed in 2018, when Hou’s research group hit upon a methodology that pulled real-time into range.
“This was a major breakthrough,” said Hou. “With support from the Commonwealth Cyber Initiative in Southwest Virginia , we elevated network optimization to a whole different level: solving problems in the field in real time.”
Ultra-high precision for ultra-low latency
In the context of 5G, timing is tied up with the concept of latency. Latency refers to time duration, or how long it takes to complete a certain task or step in a process. Minimizing latency is an attempt to reduce delay. When it comes to 5G, a delay of even a few milliseconds can make a difference to an industrial automation system or a power grid , for instance.
As a delay stretches, not only will user experience degrade, but risk to device, information, or safety increases.
“Think about industrial automation or autonomous driving , which require information to be transported over different systems very quickly to ensure tight synchronization,” said Hou. “Reaction time on the road or in a warehouse is critical to preventing accidents, making latency of utmost importance.”
To deliver that kind of end-to-end latency on the order of millisecond, scheduling from the 5G base station has to be on the same order or even lower.
How it started
In 2018, Hou and his team were designing a system to meet the stringent timing requirements of new radio access technology for the 5G mobile network. To support applications with ultra-low latency, the minimum timing resolution for optimal 5G New Radio performance was capped at 125 microseconds — almost 10 times faster than what was possible with 4G LTE.
Up until then, no one had been able to deliver optimal scheduling in that interval.
The Virginia Tech team proposed a scheduling algorithm that incorporated a graphics processing unit (GPU) — a specialized circuit that uses parallel computing to accelerate workloads in high performance computing.
Parallel computing isn’t a new technology. A supercomputer processes computations in parallel with thousands of central processing units, but it’s expensive, cumbersome, and can’t be accomplished locally — by the time a base station outsources a task to the cloud and receives the results, it’s far too late to meet real time scheduling needs.
Originally designed for graphics rendering, a GPU isn’t in the same league as a supercomputer in terms of processing capability. It wasn’t designed for scientific computation or solving complex optimization problems, but when coupled with Hou’s new scheme, it doesn’t have to be.
Hou and his team developed a multistep methodology that breaks down a big problem into a smaller set of sub problems and then zeros in on the sub problems that are likely to yield the most promising results. For this manageable set of small problems, custom solutions can be developed by a GPU processing in parallel.
“With this technique, even a low-end GPU can find near-optimal solutions within the sub-millisecond time window,” said Hou.
Hou’s team’s innovation rocked the field of wireless network optimization.
“Probably the most important feature of 5G is the ability to communicate with low latency, and Professor Hou’s work makes this feasible,” said Jeff Reed, the Commonwealth Cyber Initiative's chief technology officer and the Willis G. Worcester Professor of electrical and computer engineering at Virginia Tech.
GPU manufacturer Nvidia showcased Hou's work, which was carried out in collaboration with fellow Commonwealth Cyber Initiative researcher Wenjing Lou in computer science. The invention was awarded a U.S. patent as it was applied to 5G schedulers. But this was just the beginning.
“We thought — wait a minute, there’s more than just scheduling for 5G problem,” said Hou. “We identified the key steps, theorized the technique, and implemented it to solve other wireless networking and communications problems with similar mathematical structure.”
Scaling up to secure autonomous vehicles
Armed with a process that brings real-time solutions into reach, Hou’s research group was ready to apply it to complex problems in different domains. With continued support from the Commonwealth Cyber Initiative in Southwest Virginia, the team is tackling radar interference in autonomous vehicles.
In addition to camera and lidar, autonomous vehicles monitor road conditions with radar because it’s not finicky about weather or lighting conditions. Day, night, rain, or snow — radar is robust.
It is, however, susceptible to interference. A radar bounces a signal off nearby objects and then measures the reflected signal to determine what’s on the road and around the vehicle. When there are too many radars on the road, signals bounce around willy-nilly, compromising a radar’s normal capability.
“Such radar-to-radar interference offers a relatively easy way to unleash a cyberattack on an autonomous vehicle and compromise safety,” said Hou.
Hou is applying the methodology to sort through which signals should matter to an autonomous vehicle, mitigating high levels of interference in real time, in-vehicle, and with an affordable GPU.
The application of the scheduling algorithm as applied to radar mitigation will be published through IEEE Radar Conference proceedings in early spring, and a patent has been filed with Virginia Tech Intellectual Properties. The Commonwealth Cyber Initiative provides funds for the translation of research into practice through programs such as “ Innovation: Ideation to Commercialization ” and patent support costs.
Edge computing and elsewhere
Hou and his team also are applying their technique to task-offloading for edge computing, which involves determining which tasks should be processed on a local device and which should be offloaded to the 5G base station.
“Our new real-time optimization methodology has many, many applications. It’s opened up a new life, certainly for me, but also for other researchers doing network optimizations,” said Hou. “We keep seeing new places where this methodology can be applied, and in many cases, finding groundbreaking solutions along the way.”
Lindsey Haugh
- Autonomous Vehicles
- College of Engineering
- Commonwealth Cyber Initiative
- Commonwealth Cyber Initiative, Southwest Virginia Node
- Computer Science
- Cybersecurity
- Electrical and Computer Engineering
- LINK+LICENSE+LAUNCH
- Research Areas
- Research Frontiers
- Security Frontier
Related Content

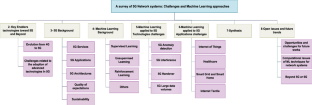
A survey of 5G network systems: challenges and machine learning approaches
- Original Article
- Published: 19 August 2020
- Volume 12 , pages 385–431, ( 2021 )
Cite this article

- Hasna Fourati 1 ,
- Rihab Maaloul 1 &
- Lamia Chaari 1
4789 Accesses
81 Citations
Explore all metrics
5G cellular networks are expected to be the key infrastructure to deliver the emerging services. These services bring new requirements and challenges that obstruct the desired goal of forthcoming networks. Mobile operators are rethinking their network design to provide more flexible, dynamic, cost-effective and intelligent solutions. This paper starts with describing the background of the 5G wireless networks then we give a deep insight into a set of 5G challenges and research opportunities for machine learning (ML) techniques to manage these challenges. The first part of the paper is devoted to overview the fifth-generation of cellular networks, explaining its requirements as well as its key technologies, their challenges and its forthcoming architecture. The second part is devoted to present a basic overview of ML techniques that are nowadays applied to cellular networks. The last part discusses the most important related works which propose ML solutions in order to overcome 5G challenges.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Machine Learning: Algorithms, Real-World Applications and Research Directions
Iqbal H. Sarker

Towards 6G wireless communication networks: vision, enabling technologies, and new paradigm shifts
Xiaohu You, Cheng-Xiang Wang, … Ying-Chang Liang
A Review of Indoor Localization Techniques and Wireless Technologies
Huthaifa Obeidat, Wafa Shuaieb, … Raed Abd-Alhameed
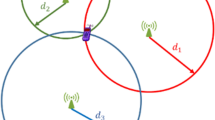
A backhaul network is an intermediary that enables the data transmission and reception between core networks, or macro base station and small base stations. It can be a wired or wireless link.
Monserrat JF, Mange G, Braun V, Tullberg H, Zimmermann G, Bulakci Ö (2015) Metis research advances towards the 5G mobile and wireless system definition. EURASIP J Wirel Commun Netw 2015(1):53
Google Scholar
Al-Falahy N, Alani OY (2017) Technologies for 5G networks: challenges and opportunities. IT Prof 19(1):12–20
Onoe S (2016) 1.3 evolution of 5G mobile technology toward 1 2020 and beyond. In: 2016 IEEE international solid-state circuits conference (ISSCC). IEEE, pp 23–28
Valente KP, Imran MA, Onireti O, Souza RD (2017) A survey of machine learning techniques applied to self organizing cellular networks. IEEE Commun Surv Tutor 19:2392–2431
Intelligence G (2014) Understanding 5G: perspectives on future technological advancements in mobile. White paper, pp 1–26
Agiwal M, Roy A, Saxena N (2016) Next generation 5G wireless networks: a comprehensive survey. IEEE Commun Surv Tutor 18(3):1617–1655
Talwar S, Choudhury D, Dimou K, Aryafar E, Bangerter B, Stewart K (2014) Enabling technologies and architectures for 5G wireless. In: 2014 IEEE MTT-S international microwave symposium (IMS2014). IEEE, pp 1–4
Andrews JG, Buzzi S, Choi W, Hanly SV, Lozano A, Soong AC, Zhang JC (2014) What will 5G be? IEEE J Sel Areas Commun 32(6):1065–1082
Osseiran A, Boccardi F, Braun V, Kusume K, Marsch P, Maternia M, Queseth O, Schellmann M, Schotten H, Taoka H et al (2014) Scenarios for 5G mobile and wireless communications: the vision of the metis project. IEEE Commun Mag 52(5):26–35
Li QC, Niu H, Papathanassiou AT, Wu G (2014) 5G network capacity: key elements and technologies. IEEE Veh Technol Mag 9(1):71–78
Hossain E, Hasan M (2015) 5G cellular: key enabling technologies and research challenges. IEEE Instrum Meas Mag 18(3):11–21
Papadopoulos H, Wang C, Bursalioglu O, Hou X, Kishiyama Y (2016) Massive mimo technologies and challenges towards 5G. IEICE Trans Commun 99(3):602–621
Larsson EG, Edfors O, Tufvesson F, Marzetta TL (2014) Massive mimo for next generation wireless systems. IEEE Commun Mag 52(2):186–195
Zhang Y, Yu R, Nekovee M, Liu Y, Xie S, Gjessing S (2012) Cognitive machine-to-machine communications: visions and potentials for the smart grid. IEEE Netw 26(3):6–13
Goudar SI, Hassan S, Habbal A (2017) 5G: The next wave of digital society challenges and current trends, Journal of Telecommunication. Electron Comput Eng (JTEC) 9(1–2):63–66
Alnoman A, Anpalagan A (2017) Towards the fulfillment of 5G network requirements: technologies and challenges. Telecommun Syst 65(1):101–116
Wu G, Yang C, Li S, Li GY (2015) Recent advances in energy-efficient networks and their application in 5G systems. IEEE Wirel Commun 22(2):145–151
Mell P, Grance T et al (2011) The nist definition of cloud computing
Zhang Q, Cheng L, Boutaba R (2010) Cloud computing: state-of-the-art and research challenges. J Internet Serv Appl 1(1):7–18
Nguyen V-G, Brunstrom A, Grinnemo K-J, Taheri J (2017) Sdn/nfv-based mobile packet core network architectures: a survey. IEEE Commun Surv Tutor 19(3):1567–1602
Abdelwahab S, Hamdaoui B, Guizani M, Znati T (2016) Network function virtualization in 5G. IEEE Commun Mag 54(4):84–91
Rangan S, Rappaport TS, Erkip E (2014) Millimeter wave cellular wireless networks: potentials and challenges. arXiv preprint arXiv:1401.2560
Ma Z, Zhang Z, Ding Z, Fan P, Li H (2015) Key techniques for 5G wireless communications: network architecture, physical layer, and mac layer perspectives. Sci China Inf Sci 58(4):1–20
Zheng G (2015) Joint beamforming optimization and power control for full-duplex mimo two-way relay channel. IEEE Trans Signal Process 63(3):555–566
MathSciNet MATH Google Scholar
Mao Y, You C, Zhang J, Huang K, Letaief KB (2017) A survey on mobile edge computing: the communication perspective. IEEE Commun Surv Tutor 19(4):2322–2358
Wang S, Zhang X, Zhang Y, Wang L, Yang J, Wang W (2017) A survey on mobile edge networks: convergence of computing, caching and communications. IEEE Access 5:6757–6779
Letaief KB, Chen W, Shi Y, Zhang J, Zhang Y-JA (2019) The roadmap to 6g-AI empowered wireless networks. arXiv preprint arXiv:1904.11686
Arfaoui G, Vilchez JMS, Wary J-P (2017) Security and resilience in 5G: current challenges and future directions. In: 2017 IEEE Trustcom/BigDataSE/ICESS. IEEE, pp 1010–1015
Klautau A, Batista P, Prelcic N, Wang Y, Heath R (2016) 5G mimo data for machine learning: application to beam-selection using deep learning. In: 2018 proceedings of information theory and applications workshop (ITA), pp 1–9
Kafle VP, Fukushima Y, Martinez-Julia P, Miyazawa T (2018) Consideration on automation of 5G network slicing with machine learning. In: 2018 ITU Kaleidoscope: machine learning for a 5G future (ITU K). IEEE, pp 1–8
International Telecommunication Union (ITU) (2017) Focus Group on Machine Learning for Future Networks including 5G (FG-ML5G). https://www.itu.int/en/ITU-T/focusgroups/ml5g/Pages/default.aspx . Accessed Nov 2017
5G Public Private Partnership (5G-PPP) (2015) CogNet-building an intelligent system of insights and action for 5G network management. http://www.cognet.5g-ppp.eu/ . Accessed 1 July 2015
Wang X, Li X, Leung VC (2015) Artificial intelligence-based techniques for emerging heterogeneous network: State of the arts, opportunities, and challenges. IEEE Access 3:1379–1391
Kibria MG, Nguyen K, Villardi GP, Zhao O, Ishizu K, Kojima F (2018) Big data analytics, machine learning, and artificial intelligence in next-generation wireless networks. IEEE Access 6:32328–32338
Long F, Li N, Wang Y (2017) Autonomic mobile networks: the use of artificial intelligence in wireless communications. In: 2017 2nd international conference on advanced robotics and mechatronics (ICARM). IEEE, pp 582–586
Moysen J, Giupponi L (2018) From 4G to 5G: self-organized network management meets machine learning. Comput Commun 129:248–268
Pérez-Romero J, Sánchez-González J, Sallent O, Agustí R (2016) On learning and exploiting time domain traffic patterns in cellular radio access networks. In: International conference on machine learning and data mining in pattern recognition. Springer, pp 501–515
Alsharif MH, Nordin R (2017) Evolution towards fifth generation (5G) wireless networks: current trends and challenges in the deployment of millimetre wave, massive mimo, and small cells. Telecommun Syst 64(4):617–637
Li S, Da Xu L, Zhao S (2018) 5G internet of things: a survey. J Ind Inf Integr 10:1–9
Kazi BU, Wainer GA (2019) Next generation wireless cellular networks: ultra-dense multi-tier and multi-cell cooperation perspective. Wirel Netw 25(4):2041–2064
Gupta A, Jha RK (2015) A survey of 5G network: architecture and emerging technologies. IEEE Access 3:1206–1232
Marsch P, Da Silva I, Bulakci O, Tesanovic M, El Ayoubi SE, Rosowski T, Kaloxylos A, Boldi M (2016) 5G radio access network architecture: design guidelines and key considerations. IEEE Commun Mag 54(11):24–32
Elijah O, Leow CY, Rahman TA, Nunoo S, Iliya SZ (2016) A comprehensive survey of pilot contamination in massive mimo-5G system. IEEE Commun Surv Tutor 18(2):905–923
Ahmed I, Khammari H, Shahid A, Musa A, Kim KS, De Poorter E, Moerman I (2018) A survey on hybrid beamforming techniques in 5G: architecture and system model perspectives. IEEE Commun Surv Tutor 20(3060):3097
Chin WH, Fan Z, Haines R (2014) Emerging technologies and research challenges for 5G wireless networks. IEEE Wirel Commun 21(2):106–112
Zhang C, Patras P, Haddadi H (2019) Deep learning in mobile and wireless networking: a survey. IEEE Commun Surv Tutor 21:2224–2287
Zhu G, Zan J, Yang Y, Qi X (2019) A supervised learning based qos assurance architecture for 5G networks. IEEE Access 7:43598–43606
Jiang C, Zhang H, Ren Y, Han Z, Chen K-C, Hanzo L (2017) Machine learning paradigms for next-generation wireless networks. IEEE Wirel Commun 24(2):98–105
Javaid N, Sher A, Nasir H, Guizani N (2018) Intelligence in iot-based 5G networks: opportunities and challenges. IEEE Commun Mag 56(10):94–100
Li R, Zhao Z, Zhou X, Ding G, Chen Y, Wang Z, Zhang H (2017) Intelligent 5G: when cellular networks meet artificial intelligence. IEEE Wirel Commun 24(5):175–183
Zhang J (2016) The interdisciplinary research of big data and wireless channel: a cluster-nuclei based channel model. China Commun 13(Supplement 2):14–26
Bogale TE, Wang X, Le LB (2018) Machine intelligence techniques for next-generation context-aware wireless networks. arXiv preprint arXiv:1801.04223
Latif S, Qadir J, Farooq S, Imran MA (2017) How 5G wireless (and concomitant technologies) will revolutionize healthcare? Future Internet 9(4):93
Qadir J, Yau K-LA, Imran MA, Ni Q, Vasilakos AV (2015) Ieee access special section editorial: Artificial intelligence enabled networking. IEEE Access 3:3079–3082
Chen M, Challita U, Saad W, Yin C, Debbah M (2017) Machine learning for wireless networks with artificial intelligence: a tutorial on neural networks. arXiv preprint arXiv:1710.02913
Salahuddin MA, Al-Fuqaha A, Guizani M (2016) Reinforcement learning for resource provisioning in the vehicular cloud. IEEE Wirel Commun 23(4):128–135
Latif S, Pervez F, Usama M, Qadir J (2017) Artificial intelligence as an enabler for cognitive self-organizing future networks. arXiv preprint arXiv:1702.02823
Tien JM (2017) Internet of things, real-time decision making, and artificial intelligence. Ann Data Sci 4(2):149–178
Fadlullah Z, Tang F, Mao B, Kato N, Akashi O, Inoue T, Mizutani K (2017) State-of-the-art deep learning: evolving machine intelligence toward tomorrow’s intelligent network traffic control systems. IEEE Commun Surv Tutor 19(4):2432–2455
Bui N, Cesana M, Hosseini SA, Liao Q, Malanchini I, Widmer J (2017) A survey of anticipatory mobile networking: context-based classification, prediction methodologies, and optimization techniques. IEEE Commun Surv Tutor 19(3):1790–1821
Le NT, Hossain MA, Islam A, Kim D-Y, Choi Y-J, Jang YM (2016) Survey of promising technologies for 5G networks. Mob Inf Syst 2016:2676589
Boutaba R, Salahuddin MA, Limam N, Ayoubi S, Shahriar N, Estrada-Solano F, Caicedo OM (2018) A comprehensive survey on machine learning for networking: evolution, applications and research opportunities. J Internet Serv Appl 9(1):16
Sultan K, Ali H, Zhang Z (2018) Big data perspective and challenges in next generation networks. Future Internet 10(7):56
Xie J, Song Z, Li Y, Zhang Y, Yu H, Zhan J, Ma Z, Qiao Y, Zhang J, Guo J (2018) A survey on machine learning-based mobile big data analysis: challenges and applications. Wirel Commun Mob Comput 2018:8738613
Xie J, Song Z, Li Y, Ma Z (2018) Mobile big data analysis with machine learning. arXiv preprint arXiv:1808.00803
Buda TS, Assem H, Xu L, Raz D, Margolin U, Rosensweig E, Lopez DR, Corici M-I, Smirnov M, Mullins R et al (2016) Can machine learning aid in delivering new use cases and scenarios in 5G? In: NOMS 2016–2016 IEEE/IFIP network operations and management symposium. IEEE, pp 1279–1284
Wang Y, Xu J, Jiang L (2014) Challenges of system-level simulations and performance evaluation for 5G wireless networks. IEEE Access 2:1553–1561
Yao M, Sohul M, Marojevic V, Reed JH (2019) Artificial intelligence defined 5G radio access networks. IEEE Commun Mag 57(3):14–20
Boccardi F, Heath RW, Lozano A, Marzetta TL, Popovski P (2014) Five disruptive technology directions for 5G. IEEE Commun Mag 52(2):74–80
Razavizadeh SM, Ahn M, Lee I (2014) Three-dimensional beamforming: a new enabling technology for 5G wireless networks. IEEE Signal Process Mag 31(6):94–101
Farhang-Boroujeny B, Moradi H (2016) Ofdm inspired waveforms for 5G. IEEE Commun Surv Tutor 18(4):2474–2492
Mitra RN, Agrawal DP (2015) 5G mobile technology: a survey. ICT Express 1(3):132–137
Wunder G, Jung P, Kasparick M, Wild T, Schaich F, Chen Y, Ten Brink S, Gaspar I, Michailow N, Festag A et al (2014) 5Gnow: non-orthogonal, asynchronous waveforms for future mobile applications. IEEE Commun Mag 52(2):97–105
Schaich F, Wild T (2014) Waveform contenders for 5G–OFDM vs. FBMC vs. UFMC. In: 2014 6th international symposium on communications, control and signal processing (ISCCSP). IEEE, pp 457–460
van der Neut N, Maharaj B, de Lange FH, Gonzalez G, Gregorio F, Cousseau J (2014) PAPR reduction in FBMC systems using a smart gradient-project active constellation extension method. In: 2014 21st international conference on telecommunications (ICT). IEEE, pp 134–139
Danneberg M, Datta R, Festag A, Fettweis G (2014) Experimental testbed for 5G cognitive radio access in 4G LTE cellular systems. In: 2014 IEEE 8th sensor array and multichannel signal processing workshop (SAM). IEEE, pp 321–324
Fettweis GP, Krondorf M, Bittner S (2009) GFDM-generalized frequency division multiplexing. In: VTC. Spring, pp 1–4
Mukherjee M, Shu L, Kumar V, Kumar P, Matam R (2015) Reduced out-of-band radiation-based filter optimization for UFMC systems in 5G. In: 2015 international wireless communications and mobile computing conference (IWCMC). IEEE, pp 1150–1155
Song L, Niyato D, Han Z, Hossain E (2015) Wireless device-to-device communications and networks. Cambridge University Press, Cambridge
Mumtaz S, Huq KMS, Rodriguez J (2014) Direct mobile-to-mobile communication: paradigm for 5G. IEEE Wirel Commun 21(5):14–23
Fortuna C, Mohorcic M (2009) Trends in the development of communication networks: cognitive networks. Comput Netw 53(9):1354–1376
Aliu OG, Imran A, Imran MA, Evans B (2013) A survey of self organisation in future cellular networks. IEEE Commun Surv Tutor 15(1):336–361
Zhang N, Cheng N, Gamage AT, Zhang K, Mark JW, Shen X (2015) Cloud assisted hetnets toward 5G wireless networks. IEEE Commun Mag 53(6):59–65
Liu Y, She X, Chen P, Zhu J, Yang F (2015) Easy network: the way to go for 5G. China Commun 12(Supplement):113–120
Feng Z, Qiu C, Feng Z, Wei Z, Li W, Zhang P (2015) An effective approach to 5G: wireless network virtualization. IEEE Commun Mag 53(12):53–59
Chowdhury NMK, Boutaba R (2009) Network virtualization: state of the art and research challenges. IEEE Commun Mag 47(7):20–26
Han B, Gopalakrishnan V, Ji L, Lee S (2015) Network function virtualization: challenges and opportunities for innovations. IEEE Commun Mag 53(2):90–97
Hawilo H, Shami A, Mirahmadi M, Asal R (2014) Nfv: state of the art, challenges and implementation in next generation mobile networks (vepc). arXiv preprint arXiv:1409.4149
Open Networking Foundation (ONF) (2014) OpenFlow-enabled SDN and Network Functions Virtualization. https://www.opennetworking.org/wp-content/uploads/2013/05/sb-sdn-nvf-solution.pdf . Accessed 17 Feb 2014
Yousaf FZ, Bredel M, Schaller S, Schneider F (2017) Nfv and sdn-key technology enablers for 5G networks. IEEE J Sel Areas Commun 35(11):2468–2478
Rangisetti AK, Tamma BR (2017) Software defined wireless networks: a survey of issues and solutions. Wirel Pers Commun 97(4):6019–6053
Goyal S, Liu P, Panwar SS, Difazio RA, Yang R, Bala E et al (2015) Full duplex cellular systems: will doubling interference prevent doubling capacity? IEEE Commun Mag 53(5):121–127
Hong S, Brand J, Choi JI, Jain M, Mehlman J, Katti S, Levis P (2014) Applications of self-interference cancellation in 5G and beyond. IEEE Commun Mag 52(2):114–121
Hu YC, Patel M, Sabella D, Sprecher N, Young V (2015) Mobile edge computing—a key technology towards 5G. ETSI White Pap 11(11):1–16
Xiao L, Wan X, Dai C, Du X, Chen X, Guizani M (2018) Security in mobile edge caching with reinforcement learning. arXiv preprint arXiv:1801.05915
Ordonez-Lucena J, Ameigeiras P, Lopez D, Ramos-Munoz JJ, Lorca J, Folgueira J (2017) Network slicing for 5G with sdn/nfv: concepts, architectures, and challenges. IEEE Commun Mag 55(5):80–87
Soleymani B, Zamani A, Rastegar SH, Shah-Mansouri V (2017) RAT selection based on association probability in 5G heterogeneous networks. In: IEEE symposium on communications and vehicular technology (SCVT), pp 1–6
Pérez JS, Jayaweera SK, Lane S (2017) Machine learning aided cognitive RAT selection for 5G heterogeneous networks. In: IEEE international black sea conference on communications and networking (BlackSeaCom), Istanbul, Turkey. IEEE, pp 1–5
Nadeem Q-U-A, Kammoun A, Alouini M-S (2018) Elevation beamforming with full dimension mimo architectures in 5G systems: a tutorial. arXiv preprint arXiv:1805.00225
Wei L, Hu RQ, Qian Y, Wu G (2014) Enable device-to-device communications underlaying cellular networks: challenges and research aspects. IEEE Commun Mag 52(6):90–96
Li Y, Wu T, Hui P, Jin D, Chen S (2014) Social-aware d2d communications: Qualitative insights and quantitative analysis. IEEE Commun Mag 52(6):150–158
Maimó LF, Clemente FJG, Pérez MG, Pérez GM (2017) On the performance of a deep learning-based anomaly detection system for 5G networks. In: 2017 IEEE SmartWorld, ubiquitous intelligence & computing, advanced & trusted computed, scalable computing & communications, cloud & big data computing, internet of people and smart city innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). IEEE, pp 1–8
Bouras C, Kollia A, Papazois A (2017) SDN & NFV in 5G: advancements and challenges. In: 2017 20th conference on innovations in clouds, internet and networks (ICIN). IEEE, pp 107–111
Sun S, Gong L, Rong B, Lu K (2015) An intelligent sdn framework for 5G heterogeneous networks. IEEE Commun Mag 53(11):142–147
Chih-Lin I, Han S, Xu Z, Sun Q, Pan Z (2016) 5G: rethink mobile communications for 2020+. Philos Trans R Soc A Math Phys Eng Sci 374(2062):20140432
MacCartney GR, Zhang J, Nie S, Rappaport TS (2013) Path loss models for 5G millimeter wave propagation channels in urban microcells. In: 2013 IEEE global communications conference (GLOBECOM), pp 3948–3953
Shafi M, Molisch AF, Smith PJ, Haustein T, Zhu P, De Silva P, Tufvesson F, Benjebbour A, Wunder G (2017) 5G: a tutorial overview of standards, trials, challenges, deployment, and practice. IEEE J Sel Areas Commun 35(6):1201–1221
You X, Zhang C, Tan X, Jin S, Wu H (2019) Ai for 5G: research directions and paradigms. Sci China Inf Sci 62(2):21301
Shariatmadari H, Ratasuk R, Iraji S, Laya A, Taleb T, Jäntti R, Ghosh A (2015) Machine-type communications: current status and future perspectives toward 5G systems. IEEE Commun Mag 53(9):10–17
Tullberg H, Popovski P, Li Z, Uusitalo MA, Hoglund A, Bulakci O, Fallgren M, Monserrat JF (2016) The metis 5G system concept: meeting the 5G requirements. IEEE Commun Mag 54(12):132–139
Queseth O, Bulakci Ö, Spapis P, Bisson P, Marsch P, Arnold P, Rost P, Wang Q, Blom R, Salsano S, et al (2017) 5G ppp architecture working group: view on 5G architecture (version 2.0, December 2017)
Nawaz SJ, Sharma SK, Wyne S, Patwary MN, Asaduzzaman M (2019) Quantum machine learning for 6g communication networks: state-of-the-art and vision for the future. IEEE Access 7:46317–46350
Gubbi J, Buyya R, Marusic S, Palaniswami M (2013) Internet of things (iot): a vision, architectural elements, and future directions. Future Gener Comput Syst 29(7):1645–1660
Alliance N (2015) 5G white paper, Next generation mobile networks, white paper, pp 1–125
Perera C, Zaslavsky A, Christen P, Georgakopoulos D (2014) Context aware computing for the internet of things: a survey. IEEE Commun Surv Tutor 16(1):414–454
Fortino G, Guerrieri A, Russo W, Savaglio C (2014) Integration of agent-based and cloud computing for the smart objects-oriented IoT. In: Proceedings of the 2014 IEEE 18th international conference on computer supported cooperative work in design (CSCWD). IEEE, pp 493–498
Wang D, Chen D, Song B, Guizani N, Yu X, Du X (2018) From iot to 5G i-iot: the next generation iot-based intelligent algorithms and 5G technologies. IEEE Commun Mag 56(10):114–120
Ratasuk R, Prasad A, Li Z, Ghosh A, Uusitalo MA (2015) Recent advancements in M2M communications in 4G networks and evolution towards 5G. In: 2015 18th international conference on intelligence in next generation networks. IEEE, pp 52–57
Kumar N, Misra S, Rodrigues JJ, Obaidat MS (2015) Coalition games for spatio-temporal big data in internet of vehicles environment: a comparative analysis. IEEE Internet Things J 2(4):310–320
Lee JD, Caven B, Haake S, Brown TL (2001) Speech-based interaction with in-vehicle computers: the effect of speech-based e-mail on drivers’ attention to the roadway. Hum Factors 43(4):631–640
Oleshchuk V, Fensli R (2011) Remote patient monitoring within a future 5G infrastructure. Wirel Pers Commun 57(3):431–439
West DM (2016) How 5G technology enables the health internet of things. Brook Cent Technol Innov 3:1–20
Gungor VC, Sahin D, Kocak T, Ergut S, Buccella C, Cecati C, Hancke GP (2011) Smart grid technologies: communication technologies and standards. IEEE Trans Ind Inform 7(4):529–539
Jeong S, Jeong Y, Lee K, Lee S, Yoon B (2016) Technology-based new service idea generation for smart spaces: application of 5G mobile communication technology. Sustainability 8(11):1211
Rappaport TS, Sun S, Mayzus R, Zhao H, Azar Y, Wang K, Wong GN, Schulz JK, Samimi M, Gutierrez F (2013) Millimeter wave mobile communications for 5G cellular: it will work!. IEEE access 1:335–349
Simsek M, Aijaz A, Dohler M, Sachs J, Fettweis G (2016) 5G-enabled tactile internet. IEEE J Sel Areas Commun 34(3):460–473
Aijaz A, Dohler M, Aghvami AH, Friderikos V, Frodigh M (2016) Realizing the tactile internet: haptic communications over next generation 5G cellular networks. IEEE Wirel Commun 24(2):82–89
Popovski P (2014) Ultra-reliable communication in 5G wireless systems. In: 1st international conference on 5G for ubiquitous connectivity. IEEE, pp 146–151
Hossain E, Rasti M, Tabassum H, Abdelnasser A (2014) Evolution towards 5G multi-tier cellular wireless networks: an interference management perspective. arXiv preprint arXiv:1401.5530
Wang C-X, Haider F, Gao X, You X-H, Yang Y, Yuan D, Aggoune HM, Haas H, Fletcher S, Hepsaydir E (2014) Cellular architecture and key technologies for 5G wireless communication networks. IEEE Commun Mag 52(2):122–130
Zhang H, Jiang C, Beaulieu NC, Chu X, Wen X, Tao M (2014) Resource allocation in spectrum-sharing of dma femtocells with heterogeneous services. IEEE Trans Commun 62(7):2366–2377
Hao P, Yan X, Yu-Ngok R, Yuan Y (2016) Ultra dense network: challenges enabling technologies and new trends. China Commun 13(2):30–40
Ge X, Tu S, Mao G, Wang C-X, Han T (2015) 5G ultra-dense cellular networks. arXiv preprint arXiv:1512.03143
Grover J, Garimella RM (2019) Optimization in edge computing and small-cell networks. In: Edge computing. Springer, pp 17–31
Hong X, Wang J, Wang C-X, Shi J (2014) Cognitive radio in 5G: a perspective on energy-spectral efficiency trade-off. IEEE Commun Mag 52(7):46–53
ETSIV (2011) Machine-to-machine communications (m2m): functional architecture. Int Telecommun 102:690 ( Union, Geneva, Switzerland, Tech. Rep. TS )
Mehmood Y, Haider N, Imran M, Timm-Giel A, Guizani M (2017) M2m communications in 5G: state-of-the-art architecture, recent advances, and research challenges. IEEE Commun Mag 55(9):194–201
Mehmood Y, Görg C, Muehleisen M, Timm-Giel A (2015) Mobile m2m communication architectures, upcoming challenges, applications, and future directions. EURASIP J Wirel Commun Netw 2015(1):250
Roh W, Seol J-Y, Park J, Lee B, Lee J, Kim Y, Cho J, Cheun K, Aryanfar F (2014) Millimeter-wave beamforming as an enabling technology for 5G cellular communications: theoretical feasibility and prototype results. IEEE Commun Mag 52(2):106–113
Zhang J, Ge X, Li Q, Guizani M, Zhang Y (2017) 5G millimeter-wave antenna array: design and challenges. IEEE Wirel Commun 24(2):106–112
Checko A, Christiansen HL, Yan Y, Scolari L, Kardaras G, Berger MS, Dittmann L (2014) Cloud ran for mobile networks—a technology overview. IEEE Commun Surv Tutor 17(1):405–426
Checko A, Christiansen HL, Yan Y, Scolari L, Kardaras G, Berger MS, Dittmann L (2015) Cloud ran for mobile networks—a technology overview. IEEE Commun Surv Tutor 17(1):405–426
Zhang H, Jiang C, Cheng J, Leung VC (2015) Cooperative interference mitigation and handover management for heterogeneous cloud small cell networks. IEEE Wirel Commun 22(3):92–99
Rost P, Bernardos CJ, De Domenico A, Di Girolamo M, Lalam M, Maeder A, Sabella D, Wübben D (2014) Cloud technologies for flexible 5G radio access networks. IEEE Commun Mag 52(5):68–76
Pan C, Elkashlan M, Wang J, Yuan J, Hanzo L (2018) User-centric c-ran architecture for ultra-dense 5G networks: challenges and methodologies. IEEE Commun Mag 56(6):14–20
ETSI-European Telecommunications Standards Institute (2019) 5G; system architecture for the 5G System (5GS)(3GPP TS 23.501 version 15.5.0 Release 15). https://www.etsi.org/deliver/etsi_ts/123500_123599/123501/15.05.00_60/ts_123501v150500p.pdf . Accessed Apr 2019
The 5G Infraestructure Public Private Partnership (2019) 5G Americas White Paper The Status of Open Source for 5G. http://www.5gamericas.org/files 6915/5070/2509/5G_Americas_White_Paper_The_Status_of_Open_Source_for_5G_Feb_2018.pdf . Accessed Feb 2019
ETSI-European Telecommunications Standards Institute (2018) 5G; system architecture for the 5G system (3GPP TS 23.501 version 15.2.0 Release 15). https://www.etsi.org/deliver/etsi_ts/123500_123599/123501/15.02.00_60/ts_123501v150200p.pdf . Accessed June 2018
Wu D, Wang J, Cai Y, Guizani M (2015) Millimeter-wave multimedia communications: challenges, methodology, and applications. IEEE Commun Mag 53(1):232–238
Comsa I-S, De-Domenico A, Ktenas D (2017) Qos-driven scheduling in 5G radio access networks-a reinforcement learning approach. In: GLOBECOM 2017-2017 IEEE global communications conference. IEEE, pp 1–7
Comşa I-S, Zhang S, Aydin M, Kuonen P, Lu Y, Trestian R, Ghinea G (2018) Towards 5G: a reinforcement learning-based scheduling solution for data traffic management. IEEE Trans Netw Serv Manag 15:1661–1675
Kamel A, Al-Fuqaha A, Guizani M (2014) Exploiting client-side collected measurements to perform QoS assessment of IaaS. IEEE Trans Mobile Comput 14(9):1876–1887
International Telecommunication Union (2017) Vocabulary for performance, quality of service and quality of experience . https://www.itu.int/rec/T-REC-P.10-201711-I . Accessed 13 Nov 2017
European Cooperation in Science and Technology, QoE definition, http://www.cost.eu
International Telecommunication Union, Reference guide to quality of experience assessment methodologies. https://www.itu.int/rec/T-REC-G.1011-201607-I/en
Chen Y, Wu K, Zhang Q (2014) From qos to qoe: a tutorial on video quality assessment. IEEE Commun Surv Tutori 17(2):1126–1165
Qiao J, Shen XS, Mark JW, Shen Q, He Y, Lei L (2015) Enabling device-to-device communications in millimeter-wave 5G cellular networks. IEEE Commun Mag 53(1):209–215
Pierucci L (2015) The quality of experience perspective toward 5G technology. IEEE Wirel Commun 22(4):10–16
Petrangeli S, Wu T, Wauters T, Huysegems R, Bostoen T, De Turck F (2017) A machine learning-based framework for preventing video freezes in http adaptive streaming. J Netw Comput Appl 94:78–92
Imran A, Zoha A, Abu-Dayya A (2014) Challenges in 5G: how to empower son with big data for enabling 5G. IEEE Netw 28(6):27–33
Wu J, Zhang Y, Zukerman M, Yung EK-N (2015) Energy-efficient base-stations sleep-mode techniques in green cellular networks: A survey. IEEE Commun Surv Tutor 17(2):803–826
Jaber M, Imran MA, Tafazolli R, Tukmanov A (2017) Energy-efficient SON-based user-centric backhaul scheme. In: 2017 IEEE wireless communications and networking conference workshops (WCNCW). IEEE, pp 1–6
Jaber M, Imran MA, Tafazolli R, Tukmanov A (2016) A distributed son-based user-centric backhaul provisioning scheme. IEEE Access 4:2314–2330
Jaber M, Imran MA, Tafazolli R, Tukmanov A (2016) A multiple attribute user-centric backhaul provisioning scheme using distributed SON. In: 2016 IEEE global communications conference (GLOBECOM). IEEE, pp 1–6
Morocho-Cayamcela ME, Lee H, Lim W (2019) Machine learning for 5G/b5G mobile and wireless communications: potential, limitations, and future directions. IEEE Access 7:137184–137206
Wold S, Esbensen K, Geladi P (1987) Principal component analysis. Chemom Intell Lab Syst 2(1–3):37–52
Comon P (1994) Independent component analysis, a new concept? Signal Process 36(3):287–314
MATH Google Scholar
Yuan Y, Wan J, Wang Q (2016) Congested scene classification via efficient unsupervised feature learning and density estimation. Pattern Recognit 56:159–169
Amiri R, Mehrpouyan H, Fridman L, Mallik RK, Nallanathan A, Matolak D (2018) A machine learning approach for power allocation in hetnets considering qos. arXiv preprint arXiv:1803.06760
Van Hasselt H, Guez A, Silver D (2016) Deep reinforcement learning with double q-learning. In: AAAI, vol 2. Phoenix, AZ
Wang S, Chaovalitwongse W, Babuska R (2012) Machine learning algorithms in bipedal robot control. IEEE Tran Syst Man Cybern Part C (Appl Revs) 42(5):728–743
Baştuğ E, Bennis M, Debbah M (2015) A transfer learning approach for cache-enabled wireless networks. In: 2015 13th international symposium on modeling and optimization in mobile, ad hoc, and wireless networks (WiOpt). IEEE, pp 161–166
LeCun Y, Bengio Y, Hinton G (2015) Deep learning. Nature 521(7553):436
Muthuramalingam S, Thangavel M, Sridhar S (2016) A review on digital sphere threats and vulnerabilities. In: Combating security breaches and criminal activity in the digital sphere. IGI Global, pp 1–21
Mohr W (2015) The 5G infrastructure public-private partnership. In: Presentation in ITU GSC-19 meeting
Li J, Zhao Z, Li R (2017) Machine learning-based ids for software-defined 5G network. IET Netw 7(2):53–60
Fiore U, Palmieri F, Castiglione A, De Santis A (2013) Network anomaly detection with the restricted Boltzmann machine. Neurocomputing 122:13–23
Maimó LF, Gómez ÁLP, Clemente FJG, Pérez MG, Pérez GM (2018) A self-adaptive deep learning-based system for anomaly detection in 5G networks. IEEE Access 6:7700–7712
Garcia S, Grill M, Stiborek J, Zunino A (2014) An empirical comparison of botnet detection methods. Comput Secur 45:100–123
Zago M, Sánchez VMR, Pérez MG, Pérez GM (2016) Tackling cyber threats with automatic decisions and reactions based on machine-learning techniques. In: Proceedings of the 2nd conference on network management, quality of service and security for 5G networks, Oulu, Finland, pp 1–4
Chang Z, Lei L, Zhou Z, Mao S, Ristaniemi T (2018) Learn to cache: machine learning for network edge caching in the big data era. IEEE Wirel Commun 25(3):28–35
Baldo N, Giupponi L, Mangues-Bafalluy J (2014) Big data empowered self organized networks. In: European wireless 2014; 20th European wireless conference. VDE, pp 1–8
Srinivasa S, Bhatnagar V (2012) Big data analytics: first international conference, BDA 2012, New Delhi, India, December 24-26, 2012, Proceedings, vol 7678. Springer Science & Business Media
Parwez MS, Rawat DB, Garuba M (2017) Big data analytics for user-activity analysis and user-anomaly detection in mobile wireless network. IEEE Trans Ind Inform 13(4):2058–2065
Aref MA, Jayaweera SK, Machuzak S (2017) Multi-agent reinforcement learning based cognitive anti-jamming. In: 2017 IEEE wireless communications and networking conference (WCNC). IEEE, pp 1–6
Mulvey D, Foh CH, Imran MA, Tafazolli R (2019) Cell fault management using machine learning techniques. IEEE Access 7:124514–124539
Kumar Y, Farooq H, Imran A (2017) Fault prediction and reliability analysis in a real cellular network. In: 2017 13th international wireless communications and mobile computing conference (IWCMC). IEEE, pp 1090–1095
Mfula H, Nurminen JK (2017) Adaptive root cause analysis for self-healing in 5G networks. In: 2017 international conference on high performance computing & simulation (HPCS). IEEE, pp 136–143
Mismar FB, Evans BL (2018) Deep Q-learning for self-organizing networks fault management and radio performance improvement. In: 2018 52nd asilomar conference on signals, systems, and computers. IEEE, pp 1457–1461
Alias M, Saxena N, Roy A (2016) Efficient cell outage detection in 5G hetnets using hidden markov model. IEEE Commun Lett 20(3):562–565
Yu P, Zhou F, Zhang T, Li W, Feng L, Qiu X (2018) Self-organized cell outage detection architecture and approach for 5G H-CRAN. Wirel Commun Mob Comput 2018:6201386
Farooq H, Parwez MS, Imran A (2015) Continuous time Markov chain based reliability analysis for future cellular networks. In: 2015 IEEE global communications conference (GLOBECOM). IEEE, pp 1–6
Asheralieva A, Miyanaga Y (2016) Qos-oriented mode, spectrum, and power allocation for d2d communication underlaying lte-a network. IEEE Trans Veh Techno 65(12):9787–9800
Zhang L, Xiao M, Wu G, Alam M, Liang Y-C, Li S (2017) A survey of advanced techniques for spectrum sharing in 5G networks. IEEE Wirel Commun 24(5):44–51
Fan Z, Gu X, Nie S, Chen M (2017) D2D power control based on supervised and unsupervised learning. In: 2017 3rd IEEE international conference on computer and communications (ICCC). IEEE, pp 558–563
Rohwer JA, Abdallah CT, El-Osery A (2002) Power control algorithms in wireless communications. In: Digital wireless communications IV, vol 4740. International Society for Optics and Photonics, pp 151–159
Xu J, Gu X, Fan Z (2018) D2D power control based on hierarchical extreme learning machine. In: 2018 IEEE 29th annual international symposium on personal, indoor and mobile radio communications (PIMRC). IEEE, pp 1–7
Wang L-C, Cheng SH (2018) Data-driven resource management for ultra-dense small cells: an affinity propagation clustering approach. IEEE Trans Netw Sci Eng 6:267–279
Balevi E, Gitlin RD (2018) A clustering algorithm that maximizes throughput in 5G heterogeneous F-RAN networks. In: 2018 IEEE international conference on communications (ICC). IEEE, pp 1–6
Alqerm I, Shihada B (2018) Sophisticated online learning scheme for green resource allocation in 5G heterogeneous cloud radio access networks. IEEE Trans Mob Comput 17:2423–2437
AlQerm I, Shihada B (2017) Enhanced machine learning scheme for energy efficient resource allocation in 5G heterogeneous cloud radio access networks. In: IEEE symposium on personal, indoor and mobile radio communications (PIMRC), pp 1–7
Lin P-C, Casanova LFG, Fatty BK (2016) Data-driven handover optimization in next generation mobile communication networks. Mob Inf Syst 2016:2368427
Khunteta S, Chavva AKR (2017) Deep learning based link failure mitigation. In: 2017 16th IEEE international conference on machine learning and applications (ICMLA). IEEE, pp 806–811
Kanwal K (2017) Increased energy efficiency in lte networks through reduced early handover
Hou T, Feng G, Qin S, Jiang W (2018) Proactive content caching by exploiting transfer learning for mobile edge computing. Int J Commun Syst 31(11):e3706
Shen G, Pei L, Zhiwen P, Nan L, Xiaohu Y (2017) Machine learning based small cell cache strategy for ultra dense networks. In: 2017 9th international conference on wireless communications and signal processing (WCSP). IEEE, pp 1–6
Sadeghi A, Sheikholeslami F, Giannakis GB (2018) Optimal and scalable caching for 5G using reinforcement learning of space-time popularities. IEEE J Sel Top Signal Process 12(1):180–190
Zeydan E, Bastug E, Bennis M, Kader MA, Karatepe IA, Er AS, Debbah M (2016) Big data caching for networking: moving from cloud to edge. IEEE Commun Mag 54(9):36–42
LeCun Y (1998) The MNIST database of handwritten digits. http://yann.lecun.com/exdb/mnist/
Tang F, Fadlullah ZM, Mao B, Kato N (2018) An intelligent traffic load prediction-based adaptive channel assignment algorithm in sdn-iot: a deep learning approach. IEEE Internet Things J 5(6):5141–5154
Mohammadi M, Al-Fuqaha A, Sorour S, Guizani M (2018) Deep learning for iot big data and streaming analytics: a survey. IEEE Commun Surv Tutor 20(4):2923–2960
Chen M, Yang J, Zhou J, Hao Y, Zhang J, Youn C-H (2018) 5G-smart diabetes: toward personalized diabetes diagnosis with healthcare big data clouds. IEEE Commun Mag 56(4):16–23
Chen M, Yang J, Hao Y, Mao S, Hwang K (2017) A 5G cognitive system for healthcare. Big Data Cogn Comput 1(1):2
Kumar PM, Gandhi UD (2018) A novel three-tier internet of things architecture with machine learning algorithm for early detection of heart diseases. Comput Electr Eng 65:222–235
Saghezchi FB, Mantas G, Ribeiro J, Al-Rawi M, Mumtaz S, Rodriguez J (2017) Towards a secure network architecture for smart grids in 5G era. In: 13th international wireless communications and mobile computing conference (IWCMC). IEEE, pp 121–126
Miao Y, Jiang Y, Peng L, Hossain MS, Muhammad G (2018) Telesurgery robot based on 5G tactile internet. Mob Netw Appl 23(6):1645–1654
Paolini M, Fili S (2019) Ai and machine learning: Why now?
Benzaid C, Taleb T (2020) Ai-driven zero touch network and service management in 5G and beyond: challenges and research directions. IEEE Netw 34(2):186–194
Sun Y, Peng M, Zhou Y, Huang Y, Mao S (2019) Application of machine learning in wireless networks: key techniques and open issues. IEEE Commun Surv Tutor 21(4):3072–3108
Wang X, Gao L, Mao S (2016) Csi phase fingerprinting for indoor localization with a deep learning approach. IEEE Internet Things J 3(6):1113–1123
Wang J-B, Wang J, Wu Y, Wang J-Y, Zhu H, Lin M, Wang J (2018) A machine learning framework for resource allocation assisted by cloud computing. IEEE Netw 32(2):144–151
Le L-V, Sinh D, Lin B-SP, Tung L-P (2018) Applying big data, machine learning, and SDN/NFV to 5G traffic clustering, forecasting, and management. In: 2018 4th IEEE conference on network softwarization and workshops (NetSoft). IEEE, pp 168–176
de Vrieze C, Simic L, Mahonen P (2018) The importance of being earnest: performance of modulation classification for real RF signals. In: IEEE international symposium on dynamic spectrum access networks (DySPAN). IEEE, pp 1–5
Koumaras H, Tsolkas D, Gardikis G, Gomez PM, Frascolla V, Triantafyllopoulou D, Emmelmann M, Koumaras V, Osma MLG, Munaretto D et al (2018) 5GENESIS: the genesis of a flexible 5G facility. In: IEEE 23rd international workshop on computer aided modeling and design of communication links and networks (CAMAD). IEEE, pp 1–6
Kotz D, Henderson T (2005) Crawdad: a community resource for archiving wireless data at dartmouth. IEEE Pervasive Comput 4(4):12–14
Lee W, Kim M, Cho D-H (2018) Deep power control: transmit power control scheme based on convolutional neural network. IEEE Commun Lett 22(6):1276–1279
Ahmed KI, Tabassum H, Hossain E (2019) Deep learning for radio resource allocation in multi-cell networks. IEEE Net 33(6):188–195
Tariq F, Khandaker M, Wong K-K, Imran M, Bennis M, Debbah M (2019) A speculative study on 6g. arXiv preprint arXiv:1902.06700
Routray SK, Mohanty S (2019) Why 6G? Motivation and expectations of next-generation cellular networks. arXiv preprint arXiv:1903.04837
Strinati EC, Barbarossa S, Gonzalez-Jimenez JL, Kténas D, Cassiau N, Dehos C (2019) 6g: The next frontier. arXiv preprint arXiv:1901.03239
Saad W, Bennis M, Chen M (2019) A vision of 6g wireless systems: applications, trends, technologies, and open research problems. arXiv preprint arXiv:1902.10265
David K, Berndt H (2018) 6g vision and requirements: is there any need for beyond 5G? IEEE Veh Technol Mag 13(3):72–80
Li R (2018) Towards a new internet for the year 2030 and beyond
Zhang H, Ren Y, Chen K-C, Hanzo L et al (2019) Thirty years of machine learning: the road to pareto-optimal next-generation wireless networks. arXiv preprint arXiv:1902.01946
Luong NC, Hoang DT, Gong S, Niyato D, Wang P, Liang Y-C, Kim DI (2019) Applications of deep reinforcement learning in communications and networking: a survey. IEEE Commun Surv Tutor 21:3133–3174
Download references
Author information
Authors and affiliations.
Laboratory of Technology and Smart Systems (LT2S), Digital Research Center of SFAX (CRNS), University of Sfax, Sfax, Tunisia
Hasna Fourati, Rihab Maaloul & Lamia Chaari
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Hasna Fourati .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Fourati, H., Maaloul, R. & Chaari, L. A survey of 5G network systems: challenges and machine learning approaches. Int. J. Mach. Learn. & Cyber. 12 , 385–431 (2021). https://doi.org/10.1007/s13042-020-01178-4
Download citation
Received : 11 December 2019
Accepted : 01 August 2020
Published : 19 August 2020
Issue Date : February 2021
DOI : https://doi.org/10.1007/s13042-020-01178-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- 5G cellular network
- 5G services
- 5G key technologies
- 5G architectures
- 5G challenges
- ML solutions
- Intelligence
- Find a journal
- Publish with us
- Track your research
Trending People
trending technology, trending entities.

- Systems & Design
- Low Power - High Performance
- Manufacturing, Packaging & Materials
- Test, Measurement & Analytics
- Auto, Security & Pervasive Computing
- Startup Corner
- Industry Research
- Special Reports
- Business & Startups
- Knowledge Center
- Architectures
- Automotive/ Aerospace
- Communication/Data Movement
- Design & Verification
- Lithography
- Manufacturing
- Optoelectronics / Photonics
- Power & Performance
- Test, Measurement & Analytics
- Transistors
- Z-End Applications
- Newsletters
- Low Power-High Performance
- Technical Papers
Solving 5G’s Thorniest Issues
Incomplete roadmaps and continued uncertainty about millimeter-wave technology make this technology’s future hazy, but solutions are in the works.

5G rollouts are beginning to hit the market, accompanied by a long list of unsolved technical and business issues surrounding this next-generation wireless technology. But progress is being made on some of the key challenges facing this technology, even though not all of those solutions will be in place at launch.
The real challenges are with millimeter-wave implementations of 5G , which operate at significantly higher RF frequencies than existing wireless communication. The first phase of rollouts will be sub-6GHz implementations, which behave much like 4G. Those signals still travel long distances with little disruption.
Millimeter wave is where things get much more interesting and difficult. The technology is capable of transmitting large quantities of data, such as streaming high-resolution video, extremely quickly. But there are some fundamental issues that need to be resolved before that can happen.
Among the top challenges:
- With mmWave technology, arrays of antennas will be required because of the limited reach of mmWave signals. Those antennas likely will be embedded into a package with no exposed leads to test. So far, there is no proven approach for high-volume production testing.
- The effectiveness of those antennas will depend on signal coverage, and so far it isn’t clear how many base stations and small cells will be required to supply adequate coverage in different environments. Numbers may vary greatly, depending on where the cells are located, how many people they need to serve, and how much interference there is between base stations, small cells and people. With mmWave technology, trees and weather can disrupt signals.
- There is no single mmWave spectrum or standard waveform. There are many of them, and they are not the same from one region to the next. That makes it difficult to build devices that will leverage 5G in multiple regions, and there is confusion about what happens with digital and analog technology.
Despite all of that, millimeter-wave technology itself is well understood. It has been used for military applications such as radar for decades. But applying it to billions of consumer devices, many of which are in motion at varying speeds, and maintaining connections is a nightmarish problem.
“It is a realistic technology, but it’s definitely a challenge,” said Neill Mullinger, product manager in the vertical market solutions group at Mentor, a Siemens Business . “The reason that it is worth taking the challenge up is that we have nowhere else to go. We’ve used up all the spectrum, and demand is still skyrocketing. If you look at any city in the world, you test out the performance of your cellular phone at 3 a.m. and it’s pretty good. You try it out at 6 p.m. and it’s lousy because of the sheer volume of users. It’s like being on a congested highway. You can drive freely at night, but you can’t at 6 p.m. It’s the exact same problems, so we have to go there. We have to go into the millimeter wave. But it comes with these really problematic attenuation problems—200 meters and the signal has faded away.”
And this is where things begin to get really complicated. Some of the solutions involve developments in other technology areas, including the edge , which is still a vague concept, and the addition of artificial intelligence, which is in a state of almost constant flux. All of the pieces need to work together seamlessly.
“There is quite a change in the architecture required for 5G,” said Ian Dennison, senior group director for Cadence’s customized IC and PCB Group. “We’ve got all these small cells distributed on lamp poles and in buildings. But we now have to centralize the baseband. And this is where edge compute comes in. You can share baseband processing across a large number of small cells and have a greater efficiency as a result, but the timing needs to be just right for us to be bringing in AI processing to the edge computer, as well, so that AI can assist with the baseband processing. So if I’ve got small cells in different places with different contexts, then AI can learn about how the small cell can best bounce the beams off of local buildings. It sends multiple beams by multiple pathways to the same user to improve the connectivity. If you’re in a strong signal area, it can provide multiple concurrent pathways to the same user via multiple beams. There are a variety of different ways that beamforming is going to have to be intelligent, and AI is arriving at just the right time. That will help a lot with some of the difficulty with 5G.”
Solving many of these issues involves a massive global effort, and it involves a lot of moving pieces— including many that are well beyond the scope of the people working on various pieces of the solution.
“When you have all those mini cells doing this, the 5G solution is not just wireless,” said Peter Zhang, R&D manager in Synopsys ‘ Solutions Group. “The wireless portion of the 5G’s impact on the communication network is only one aspect of that. There is also the gigantic backbone land line networking systems that we’re constructing and working on. We all have to be working together congruently, each with our own 5G wireless portion, so you can access a data network everywhere with a high-performance type of experience.”
A key component of that will be the edge, but so far the edge remains more of a concept than reality.
“There is still a lot of uncertainty about the edge, but some characteristics are starting to come into focus,” said Mike Fitton, senior director of strategic planning at Achronix . “There is a wide variety of devices, there is an increase in the number of devices that are coming, and there is a variety of devices that produce very little data to sensors that produce significant amounts of data, with different characteristics, as well. Classically, we saw all of that data moving from edge devices to the cloud and back, but because of requirements from a latency point of view, we’re starting to push this closer to the edge or edge compute.”
Test and reliability Millimeter wave will play a key role in that paradigm, but one of the big problems today with mmWave is the reliability of data communication. Beamforming, which directs signals from multiple cells around objects, is a proven approach to maintaining a connection. But how well an end device receives and processes that signal depends to a large extent on the antenna array, and testing of an array is a slow process using over-the-air testing.
“We’re starting to see millimeter wave base stations and early testing of the topology, and you’ll see more of those in a year or two,” said Adrian Kwan, senior business development manager at Advantest . “That will be followed by cell phones in 2021. It’s the same base station technology as today, but you need five to six times more pico cells. The wireless has to be in place first before you see customers developing devices to support millimeter wave.”
Kwan said that packaging and testing both have evolved to be able to support testing of the antennas over the air, but so far nothing has been done in high volume. But that’s not the only issue.
“What we’re seeing with multiple carriers is that the waveforms are different,” said Kwan. “There are new standards being defined to deal with this. That all has to be in place before 5G is ready.”

Others report similar challenges.
“To support these bands we have to significantly change the design and testing we do in these environments,” said Ben Thomas, director of technical marketing at Qorvo, in speech at the recent NIWeek. “Combine that with more carrier aggregation combinations, dual uplink, and more complex waveforms and modulation schemes, and quite frankly you’re looking at an exponential impact on the RF section.”
There are other issues on the test side, as well. “The challenge with 5G is that some of this stuff has to get pushed up to the system level,” said Doug Elder, vice president and general manager of the semiconductor business at OptimalPlus . “So you may need to do some of this stuff with system-level test, as opposed to functional test or earlier in the process. If you collect the data that comes out of that test process, you can look at that data and draw some conclusions that you can drive back into your process.”
In addition, just testing a 5G device in the fab or packaging house isn’t sufficient. Because this technology is so new, quality of service is expected to be spotty at first. The early generations of cell phones dropped calls regularly with far lower data rates.
“The current frequencies clearly aren’t going away, so we have to continue to test those in this way that we have done in the past,” said Mentor’s Mullinger. “But then you augment that with new solutions to deal with the expanded frequencies of 5G. The current family of testers allows you to do a lot of that virtually, which means we can set up a test environment for the lab or the field and run the exact same environment.”
That will be critical for improving coverage and quality of service.
“Part of this an expectation-management problem, and we should expect that our 5G systems start to improve over time as the AI systems start to kick in, start to develop better quality of service,” said Cadence’s Dennison. “But straight out the box, it may not be perfect. So testing as it were is going to be a continuous thing, and something that the network operators are going to be relying on to improve the quality of their service. So there is yet another sort of difficulty that is new to us as we move from 4G to 5G.”
Thinking differently So far, there is no consistency in how companies propose to solve the signal attenuation problem for millimeter wave. Still, the solution may not just be blanketing the walls of buildings with small cells. At least part of the answer may be in thinking differently about how a 5G mmWave device behaves, or even what it looks like.
On the behavior side, one possible solution is to use different technology for the uplink and downlink.
“If a mobile device moves relative to the base station, the real problem is the uplink,” said David Hall, principal product marketing manager at National Instruments . “To use beamforming is difficult, so you can use LTE for the uplink and millimeter wave for the downlink. The big questions are about the infrastructure. Most of the end devices have full radio capability, but for the base stations, the choice is whether to use digital versus analog for beamforming. Analog circuits are less efficient, which creates more heat in the base station.”
The 5G standard allows for both and analog and digital, but the beams look different.
“If you using a digital beam, it involves a change of the waveform itself,” said Hall. “You need to adjust the phase to wave carriers.”
Another change involves the end device. The introduction of mmWave technology has much broader ramifications than being able to download more video.
“We shouldn’t get overly focused on 5G just being the next increment over 3G and 4G for the end user with the mobile phone,” said Cadence’s Dennison. “5G is laying claim to a lot of things, and one of them is a very low latency to enable robots, in particular. Robots today are in factories and they’re in cages in factories. If we can get the latency down in communicating with them—imagine you’ve got that massive AI on the edge and it’s talking to robots through 5G and that has a very low latency of communication over milliseconds of order—then you’ve got a chance that those robots can be responsive in real time and not harm human beings that are around them. So 5G opens up a whole new set of opportunities like that. Maybe robots will break out of the factories and the cages, and it could be 5G low latency might be the enabler for that. While these chipsets already are being developed for handsets, that is only one possible device that can take advantage of 5G.”
Along similar lines, there is a lot of concern about relying on 5G for linking cars to the cloud because connectivity is unreliable. But communication to other vehicles is a different story.
“With wireless network, the cars can talk to each other,” said Synopsys’ Zhang. “We can create a link so that they can they can communicate with that, with short latencies, with the highest possible car reliability because they don’t want cars to crash. Those are the things that make 5G more interesting.”
Conclusion Investments in 5G are rising, and so is the industry reliance on this technology for a variety of applications, including fixed structures such as smart buildings and cell phone towers that serve rural areas as well as densely populated areas. There is simply more data being produced and a growing demand for information everywhere.
The global communications business is betting heavily on 5G, even it remains to be seen exactly how that technology will be used and what an 5G end device actually looks like and how it will be served. Nevertheless, progress is being made on some of the most difficult problems in 5G, even if there is a long way to go before all the kinks are worked out and it is fully functioning like 4G LTE.
—Kevin Fogarty contributed to this report.

Ed Sperling
Leave a reply cancel reply.
Name * (Note: This name will be displayed publicly)
Email * (This will not be displayed publicly)
- Merging Power and Arithmetic Optimization Via Datapath Rewriting (Intel, Imperial College London) April 19, 2024 by Technical Paper Link
- RF General-Purpose Photonic Processor April 17, 2024 by Technical Paper Link
- Memristor Crossbar Architecture for Encryption, Decryption and More April 16, 2024 by Technical Paper Link
- Single-Molecule Transistor Using Quantum Interference April 16, 2024 by Technical Paper Link
- Feasibility and Potential of Quantum Computing For a Typical EDA Optimization Problem April 16, 2024 by Technical Paper Link
Knowledge Centers Entities, people and technologies explored
Related articles, money pours into new fabs and facilities, the rising price of power in chips, chiplet ip standards are just the beginning, the future of memory, backside power delivery gears up for 2nm devices, silicon photonics manufacturing ramps up, visa shakeup on tap to help solve worker shortage, x-ray inspection in the semiconductor industry, newsletter signup, popular tags, recent comments.
- Anne Meixner on Too Much Fab And Test Data, Low Utilization
- Mark Hahn on CXL: The Future Of Memory Interconnect?
- Dr. Richard Roy on Future-Proofing Automotive V2X
- Frank-Peter Ludwig on Enabling Advanced Devices With Atomic Layer Processes
- Piyush Kumar Mishra on Using AI/ML To Minimize IR Drop
- Rakesh on Timing Library LVF Validation For Production Design Flows
- Mike Cawthorn on What Will That Chip Cost?
- Liz Allan on Early STEM Education Key To Growing Future Chip Workforce
- Rob Pearson - RIT on Early STEM Education Key To Growing Future Chip Workforce
- Maury Wood on Examining The Impact Of Chip Power Reduction On Data Center Economics
- Erik Jan Marinissen on Chiplet IP Standards Are Just The Beginning
- Peter Bennet on Design Tool Think Tank Required
- Dr. Dev Gupta on Chiplet IP Standards Are Just The Beginning
- Jesse on Hunting For Open Defects In Advanced Packages
- Matt on Chip Ecosystem Apprenticeships Help Close The Talent Gap
- Leonard Schaper IEEE-LF on 2.5D Integration: Big Chip Or Small PCB?
- Apex on Nanoimprint Finally Finds Its Footing
- AKC on Gearing Up For Hybrid Bonding
- Allen Rasafar on Backside Power Delivery Gears Up For 2nm Devices
- Nathaniel on Intel, And Others, Inside
- Chris G on Intel, And Others, Inside
- Richard Collins on Too Much Fab And Test Data, Low Utilization
- Jerry Magera on Why Chiplets Are So Critical In Automotive
- Jenn Mullen on Shattered Silos: 2024’s Top Technology Trends
- Valerio Del Vecchio on Security Becoming Core Part Of Chip Design — Finally
- Lucas on Hybrid Bonding Basics: What Is Hybrid Bonding?
- Robin Grindley on Expand Your Semiconductor’s Market With Programmable Data Planes
- V.P.Sampath on RISC-V Micro-Architectural Verification
- Thermal Guy on Is UCIe Really Universal?
- Colt Wright on Shattered Silos: 2024’s Top Technology Trends
- Nicolas Dujarrier on The Future Of Memory
- Tony on Challenges Of Logic BiST In Automotive ICs
- Raymond Meixner's child on Visa Shakeup On Tap To Help Solve Worker Shortage
- Michael Alan Bruzzone on How Is The Chip Industry Really Doing?
- Art Scott on How Is The Chip Industry Really Doing?
- Liz Allan on Rethinking Engineering Education In The U.S.
- Telkom University on Rethinking Engineering Education In The U.S.
- Ramesh Babu Varadharajan on SRAM’s Role In Emerging Memories
- jake_leone on Visa Shakeup On Tap To Help Solve Worker Shortage
- d0x on How Secure Are FPGAs?
- Mike Bradley on RISC-V Micro-Architectural Verification
- Charles E. Bauer ,Ph.D. on Visa Shakeup On Tap To Help Solve Worker Shortage
- AMAN SINGH on Power Aware Intent And Structural Verification Of Low-Power Designs
- Ed Trevis on Visa Shakeup On Tap To Help Solve Worker Shortage
- AMAN SINGH on Get To Know The Gate-Level Power Aware Simulation
- Pitchumani Guruswamy on RISC-V Micro-Architectural Verification
- Manil Vasantha on AI Accelerator Architectures Poised For Big Changes
- Ramachandra on Packaging Demands For RF And Microwave Devices
- garry on New Insights Into IC Process Defectivity
- Brian Bailey on The Good Old Days Of EDA
- Ann Mutschler on AI Accelerator Architectures Poised For Big Changes
- John Derrick on AI Accelerator Architectures Poised For Big Changes
- allan cox on AI Accelerator Architectures Poised For Big Changes
- Madhusudhanan RAVISHANKAR on Curbing Automotive Cybersecurity Attacks
- Eric Cigan on The Good Old Days Of EDA
- Peter Flake on The Good Old Days Of EDA
- Mike Cummings on MEMS: New Materials, Markets And Packaging
- Bill Martin on The Good Old Days Of EDA
- Gretchen Patti on 3D-ICs May Be The Least-Cost Option
- Carlos on An Entangled Heterarchy
- Ann Mutschler on Flipping Processor Design On Its Head
- Gil Russell on Flipping Processor Design On Its Head
- Ed Sperling on China Unveils Memory Plans
- David on The Limits Of AI-Generated Models
- Bill on The Limits Of AI-Generated Models
- Dr. Dev Gupta on Gearing Up For Hybrid Bonding
- Faizan on China Unveils Memory Plans
- Jan Hoppe on Streamlining Failure Analysis Of Chips
- Riko R on Why Curvy Design Now? Manufacturing Is Possible And Scaling Needs It
- Derrick Meyer on Higher Automotive MCU Performance With Interface IP
- Kevin Cameron on Why Silent Data Errors Are So Hard To Find
- Rale on How Secure Are RISC-V Chips?
- Ed Sperling on Patterns And Issues In AI Chip Design
- Chip Greely on Building Better Bridges In Advanced Packaging
- Art Scott on Setting Standards For The Chip Industry
- Muhammet on Higher Creepage And Clearance Make For More Reliable Systems
- Andy Deng on Quantum Plus AI Widens Cyberattack Threat Concerns
- Dr. Rahul Razdan on The Threat Of Supply Chain Insecurity
- Roger on Patterns And Issues In AI Chip Design
- David Leary on Improving Reliability In Chips
- Ann Mutschler on The Threat Of Supply Chain Insecurity
- Cliff Greenberg on Setting Standards For The Chip Industry
- Kevin Parmenter on The Threat Of Supply Chain Insecurity
- Esther soria on Automotive Complexity, Supply Chain Strength Demands Tech Collaboration
- Kumar Venkatramani on Predicting The Future For Semiconductors
- Spike on Is UCIe Really Universal?
- David Sempek on Power Semis Usher In The Silicon Carbide Era
- Dp on Specialization Vs. Generalization In Processors
- Eric on Addressing The ABF Substrate Shortage With In-Line Monitoring
- Karl Stevens Logic Designer on Software-Hardware Co-Design Becomes Real
- Jim Handy on MRAM Getting More Attention At Smallest Nodes
- Nicolas Dujarrier on MRAM Getting More Attention At Smallest Nodes
- Lou Covey on Are In-Person Conferences Sustainable?
- Cas Wonsowicz on AI Transformer Models Enable Machine Vision Object Detection
- Nancy Zavada on Are In-Person Conferences Sustainable?
- Fred Chen on High-NA Lithography Starting To Take Shape
- Dave Taht on Wi-Fi 7 Moves Forward, Adding Yet Another Protocol
- Robert Boissy on Rethinking Engineering Education In The U.S.
- Allen Rasafar on High-NA Lithography Starting To Take Shape
- Mathias Tomandl on Multi-Beam Writers Are Driving EUV Mask Development
- K on High-NA Lithography Starting To Take Shape
- Adibhatla krishna Rao on How Do Robots Navigate?
- Doug L. on Getting Rid Of Heat In Chips
- Ken Rygler on DAC/Semicon West Wednesday
- Mark Camenzind on Why IC Industry Is Great Place To Work
- Peter Bennet on The True Cost Of Software Changes
- ALLEN RASAFAR on Balancing AI And Engineering Expertise In The Fab
- Ron Lavallee on The True Cost Of Software Changes
- Alex Peterson on Welcome To EDA 4.0 And The AI-Driven Revolution
- Allen Rasafar on Managing Yield With EUV Lithography And Stochastics
- Art Scott on Rethinking Engineering Education In The U.S.
- Paul Clifton on Week In Review: Semiconductor Manufacturing, Test
- Mark L Schattenburg on A Highly Wasteful Industry
- Gordon Harling on Rethinking Engineering Education In The U.S.
- Santosh Kurinec on Rethinking Engineering Education In The U.S.
- Brian Bailey on Rethinking Engineering Education In The U.S.
- CdrFrancis Leo on Will There Be Enough Silicon Wafers?
- Advertising on SemiEng
- Newsletter SignUp
- Low Power-High Perf
- Knowledge Centers
Connect With Us
- Twitter @semiEngineering
Privacy Overview
5G Coverage Problem Analysis and Optimization Scheme Exploration
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

How to solve 5G’s biggest challenges

In a recent posting, the folks at Wind River have detailed what they believe to be are the solutions that communications service providers need to enact in order to solve 5G’s biggest challenges.
Among the hurdles facing today’s communication providers:
- Mitigating the complexity of 5G distributed networks – This includes addressing the very modern need for increased density
- Keeping OpEx cost under control in the 4G to 5G transition
- Meeting ultra-low, deterministic latency requirements
- Capably serving up new capabilities – This includes entering new markets
- Addressing ever evolving security Issues
SPONSORED: EnerCera – a new Li-ion battery solution to eliminate bottlenecks in IoT power supply
From the paper’s abstract:
5G promises exciting advances for Communications Service Providers (CSPs), but the 5G rollout is going to be challenging. CSPs must rapidly build out dense, low-latency edge networks in ways that are affordable, secure, and easily maintainable. CSPs are looking toward open-source, containerbased network infrastructures that meet the 5G latency, reliability, and flexibility requirements while being inexpensive to deploy and maintain. This eBook explores the technologies that will power this next wave of telecommunications.
Download the paper in full: Solving 5G’s biggest challenges for communications service providers

Recommended for you

Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

After VMware Acquisition Broadcom Shows Telco Muscle at MWC

Revolutionizing Industry Through the Metaverse

Key Players in Taiwan’s IC Industry Showcase Hard Power in Ecosystem

Wearables and the IIoT

What IoT Tools Help Streamline Hospital Resource Management?

Smartwatches Go Beyond Step Counting and Heartbeats
How DECT NR+ Revolutionizes Smart Building Connectivity

IoT-Enabled Smart City Data Analytics Framework

IoT-powered Smart Shoes for Assisting Visually Impaired Individuals

10 ways IoT is Revolutionizing Industrial Sustainability in 2024 and Beyond
Subscribe to Our Newsletter
Subscribe to our newsletter to stay up-to-date on all that is happening in and around the Internet of Things!
- Name First Last
- Country Afghanistan Åland Islands Albania Algeria American Samoa Andorra Angola Anguilla Antarctica Antigua and Barbuda Argentina Armenia Aruba Australia Austria Azerbaijan Bahamas Bahrain Bangladesh Barbados Belarus Belgium Belize Benin Bermuda Bhutan Bolivia Bonaire, Sint Eustatius and Saba Bosnia and Herzegovina Botswana Bouvet Island Brazil British Indian Ocean Territory Brunei Darrussalam Bulgaria Burkina Faso Burundi Cambodia Cameroon Canada Cape Verde Cayman Islands Central African Republic Chad Chile China Christmas Island Cocos Islands Colombia Comoros Congo, Democratic Republic of the Congo, Republic of the Cook Islands Costa Rica Côte d'Ivoire Croatia Cuba Curaçao Cyprus Czech Republic Denmark Djibouti Dominica Dominican Republic Ecuador Egypt El Salvador Equatorial Guinea Eritrea Estonia Eswatini (Swaziland) Ethiopia Falkland Islands Faroe Islands Fiji Finland France French Guiana French Polynesia French Southern Territories Gabon Gambia Georgia Germany Ghana Gibraltar Greece Greenland Grenada Guadeloupe Guam Guatemala Guernsey Guinea Guinea-Bissau Guyana Haiti Heard and McDonald Islands Holy See Honduras Hong Kong Hungary Iceland India Indonesia Iran Iraq Ireland Isle of Man Israel Italy Jamaica Japan Jersey Jordan Kazakhstan Kenya Kiribati Kuwait Kyrgyzstan Lao People's Democratic Republic Latvia Lebanon Lesotho Liberia Libya Liechtenstein Lithuania Luxembourg Macau Macedonia Madagascar Malawi Malaysia Maldives Mali Malta Marshall Islands Martinique Mauritania Mauritius Mayotte Mexico Micronesia Moldova Monaco Mongolia Montenegro Montserrat Morocco Mozambique Myanmar Namibia Nauru Nepal Netherlands New Caledonia New Zealand Nicaragua Niger Nigeria Niue Norfolk Island North Korea Northern Mariana Islands Norway Oman Pakistan Palau Palestine, State of Panama Papua New Guinea Paraguay Peru Philippines Pitcairn Poland Portugal Puerto Rico Qatar Réunion Romania Russia Rwanda Saint Barthélemy Saint Helena Saint Kitts and Nevis Saint Lucia Saint Martin Saint Pierre and Miquelon Saint Vincent and the Grenadines Samoa San Marino Sao Tome and Principe Saudi Arabia Senegal Serbia Seychelles Sierra Leone Singapore Sint Maarten Slovakia Slovenia Solomon Islands Somalia South Africa South Georgia South Korea South Sudan Spain Sri Lanka Sudan Suriname Svalbard and Jan Mayen Islands Sweden Switzerland Syria Taiwan Tajikistan Tanzania Thailand Timor-Leste Togo Tokelau Tonga Trinidad and Tobago Tunisia Turkey Turkmenistan Turks and Caicos Islands Tuvalu Uganda Ukraine United Arab Emirates United Kingdom United States Uruguay US Minor Outlying Islands Uzbekistan Vanuatu Venezuela Vietnam Virgin Islands, British Virgin Islands, U.S. Wallis and Futuna Western Sahara Yemen Zambia Zimbabwe
- Consent I would like to receive free eNewsletters and emails from IoT Times (I understand I can opt-out at any time) Yes
- Privacy and Terms * I agree to the use of my personal information in accordance with the AspenCore Terms of Use and Privacy Policy Yes *
- > A Structured Approach to Problem-Solving | Webinar Recap
A Structured Approach to Problem-Solving | Webinar Recap
Posted by Noah Paratore
Jun 9, 2021 12:08:46 PM
We had the pleasure of presenting a webinar hosted by Chad Westbrook, a manufacturing engineering manager and AGCO production system manager at AGCO Corporation . AGCO is a full-line manufacturer of agricultural equipment. The company makes everything, including tractors, tillers, sprayers, bailers, and other equipment. Chad joined our own Mark Graban to discuss a different way of thinking about problem-solving. This post is a recap of the presentation - watch the full thing for all the details!
A Structured Approach to Problem-Solving
Presented by Chad Westbrook, AGCO

In this webinar, you'll learn a structured approach to problem-solving using the following tools:
- 5G – A tool used to describe a loss phenomenon
- 5W1H – An approach to the revised phenomenon
- 4M1D – Defining the contributing factors to the revised phenomenon
- 4M1D Confirmation – Validating the contributing factors
- 5 Why’s – Root cause and effective countermeasures
The Structured Problem-Solving Process
Chad explained that the Heston, KS plant where he is based produces a complex array of multiple product types and brands. Like many other companies, the standard way of addressing issues in the past at AGCO was to react and contain the issue when something came up. The Leadership team realized that this band-aid type approach was not really solving problems. It just covered up issues. Good product went out the door, but it wasn’t uncommon for the same problem to creep up time and time again.
The team decided to change old habits by developing a structured problem-solving process for the Heston facility. The approach leverages several tools including 5G, 5W1H, 4M1D & Confirmation, the 5 Whys , and levels of countermeasures. AGCO also implemented KaiNexus to support every aspect of the new problem-solving paradigm.
At AGCO, the process begins with a close look at the “initial phenomenon,” also know as anything that is creating an issue for anyone at the Heston site on a given day. The purpose of the structured problem-solving process is to identify the root cause and apply an effective corrective action. Starting with the initial phenomenon establishes the finish line for the team. Once the countermeasures are implemented, they can verify that the initial phenomenon has been resolved.
5G (Gemba, Gembutsu, Genjitsu, Genri, Gensoku)
5G is a tool used to describe a loss phenomenon. It can be related to safety, quality, a minor stoppage on the line, a major breakdown, lengthy set-up, a parts shortage, etc. The purpose of a 5G is to describe a situation in a complete and detailed way, to keep a proper relationship between theory and practice, and to follow a logical flow during the process.
AGCO uses the 5G tool during the first phase of the problem investigation. They typically walk through it with the 5G1H form so they can fill it out as they understand the problem.
Gemba means the real place. It involves going to the place where the original phenomena occurred. Then the team starts walking that back through the processes to see who needs to be involved in the solution. Visiting the workplace where the problem happened helps the team avoid making assumptions about the issue. There may be things that would otherwise be missed. Before structured problem-solving, sometimes countermeasures were applied based on incorrect assumptions.
Gembutsu means the real things. The next step is to examine the materials, process, machinery, people, and objects that are actually involved in the event. Most of AGCO’s work involves creating their own parts, so because of that complexity, they must often include several different value streams and departments to fully understand the evolution of that part through assembly.
Genjitsu calls for the actual facts. Problem-solving requires getting the real facts and actual data, what you can observe with your own eyes. The goal again is to separate facts from assumptions. Here the team takes into account things like how the part was designed and the tools used to make it, along with the assembly process that is used.
These first three “Gs” are the main focus of the team. They get leaders to the shop floor, instead of trying to solve the issue behind the desk.
Genri and gensoku are necessary when the previous steps do not reveal the causes of the problem. Generi involves principles and theories that come into play when there is not a standard for a particular process. The operator shares what they believe the theory is supposed to be. That leads to gensoku, or standards & parameters. At times, planning may be to blame for problems with the part or production. Operators may be compensating for incorrect standards or lack of information.
5W1H – Phenomenon Description (What, When, Where, Who, Which, How)
The 5W1H is the tool that is used to determine what the revised phenomena will be. In manufacturing an initial phenomenon is a deviation between the current condition (what is) and the desired condition (what should be) with an unknown cause for the gap.
When AGCO walks through the 5W1H, the first step is to get a full statement from the person experiencing the problem and define the problem condition, so they know what the desired state is. The object is to describe the revised phenomenon or to make visible what currently cannot be seen.
For example, AGCO uses a micrometer to check the sizes of shafts to determine if a part meets specs or not. In one experiment, the team asked three different people to measure the same shaft, and they got three different measurements. That identified a gap that may have contributed to the initial phenomenon. When the analysis is superficial, or assumptions are made, the scope of the problem to be fixed is broadened, leaving the team a lack of direction in terms of solving the initial problem and many possible causes to consider. 5W1H and 5G help narrow the scope, getting to the root cause faster.
The 5G1H form starts with necessary information including dates and team participants and a clear statement of the problem. The first step is to initiate the containment process. The team determines if any containment measures are necessary, whether damaged or failed parts are accounted for, and how to prevent delivery to any other customers. Immediate actions must be documented and known to all parties involved. This usually involves a cross-functional team.
Once containment is defined, the first “W” in the 5W1H is addressed – What ? The team determines what happened, what is the phenomenon, and whether it can be reproduced. Using the 5 G, they define what machine, product, or material is involved.
The next in line is the when . When did it start? Was it associated with moving from shift to shift or introducing a new model? When in the process does it occur? Do we see a pattern?
That leads to where . Where did we see the phenomenon? Where did it occur? Depending on the issue, they may ask where on the equipment or material. This helps in understanding containment and narrowing the scope of the possible causes.
After that comes who . Who is doing the process? Who does the problem affect? Who can generate the phenomenon? Could the problem be skills related?
The final W is which . Which trend or pattern does the phenomenon have? Which direction are things trending? Which factors influence the occurrence? Is the problem related to any process variable? This helps find the revised phenomenon.
The 1H stands for how and how many . How is it being done? What is the extent of the phenomenon? Is the process in control? How is the state of the equipment changed from the optimal? How many times does the phenomenon occur?
Once all of this is identified, the team can get to a revised phenomenon.
The result of the duly executed 5W1H is a narrow focus on the problem to identify the revised phenomenon.
4M1D – Fishbone Diagram (Martial, Method, Machine, Man, Design)
The next step in AGCO’s approach is using the 4M1D fishbone diagram, an industry standard, and fairly universal tool. This is how the team starts understanding the contributors to the revised phenomenon. The revised phenomenon is inserted into the fishbone diagram, and the major categories of the 4M1D are considered. They include material, method, machine, man, and design. Other “Ms” that may have an influence are mission, mother nature, management, money, and maintenance. The fishbone diagram can be adjusted to meet the needs of a specific issue.
As the team starts walking through the different issues, they fill out the significant contributors using brainstorming to document all of the factors. Once the list is complete, they begin the analysis process and remove any trivial items. Typically, four or five contributing elements are selected.
Next, the team transfers the important causes to the Confirmation form that includes the 4M category, the contributing factors, and a check to determine whether the 5 Whys should be applied to each factor.
The 5 Whys is another standard tool from the Lean methodology . It is a simple problem-solving tool that helps users identify a countermeasure. AGCO starts by asking Why the problem is happening. Asking is simple, but answering requires thought and intelligent application, so the path from the revised phenomenon becomes clear. AGCO uses KaiNexus to see if they’ve addressed the same type of opportunity in the past.
The number “5” is not important. The goal is to continue asking “why?” until the team has reached an effective countermeasure and can go no further.
Chad shared an example. Coolant was discovered on the factory floor. The team asked why and determined that coolant was leaking from the machine. They asked why again and found that a seal was damaged. In the past, the solution would have been to simply replace the seal and stop the leak, but asking why one more time revealed metal shavings in the coolant. Why? The coolant pump guard allowed the shavings to pass behind the coolant screen. Now the team understood the root cause of the coolant leak. This led to an effective countermeasure, which was to design and install a new guard over the screen.
Levels of Countermeasures and Controls
At the Heston location, AGCO uses four different types of countermeasures. Which is used depends on cost and risk. They include:
Defect Elimination – Error proof the product or process completely to eliminate the opportunity of making a defect.
Defect Prevention – Mistake-proof the product or process to minimize the chances of making a defect.
Defect Detection – Test, validate or inspect the product to catch defects before they are passed on.
Defect Awareness – Use visual controls, training, documentation, and communication to give operators information that may help prevent defects.
Structured Problem Solving at AGCO in Action
Chad shared another example that covers the typical problem-solving approach at the Heston facility.
The problem involved air leaks in the air ride suspension of a new model of wind rower. Using the 5G process, the team went to the factory floor and examined the object. They then went through the design to understand the intent of the design and each component.
Next, they completed the 5W1H form. They discovered precisely where the air leaks were occurring. From there, they looked at the contributing factors using the 4M1D document to identify the contributing factors and eliminated potential causes. The confirmation sheet was used to analyze the contributing factors further. The first “not-ok” factor turned out to be the incorrect hose being used with the fittings. Additionally, the correct tools weren’t being used to install the hose to the fitting.
Next, the 5 Whys were used to find out why the incorrect hoses were being used. The ultimate cause turned out to be that the hoses were not approved with the fittings; therefore design didn’t consider compatibility, therefore the incorrect hose was being used. The countermeasure was to change the hose to meet the fitting specks.
At AGCO, KaiNexus is used to model the PDSA methodology. The details of the problem, the root cause, and the countermeasures are all entered into the system. Tasks are assigned to correct the problem. The costs of the project are analyzed to make sure that the countermeasure is indicated.
We are very grateful to Chad for sharing the details of how AGCO approaches problem-solving. They are an excellent example of how thoughtful processes can help organizations get to the root cause of issues and address them effectively using these techniques along with the KaiNexus solution. You can watch this webinar and check out other informative presentations here .
Topics: Lean , Spread Continuous Improvement
Add a Comment
Subscribe via email, recent posts.

- Our Customers
Why KaiNexus
- Collaboration
- Standardization
- Customer Success Manager
- Lean Strategy
- Solutions Engineering
- Customer Marketing
- Configuration
- Continuous Enhancements
- Employee Driven
- Leader Driven
- Strategy Development
- Process Driven
- Daily Huddles
- Idea Generation
- Standard Work
- Visual Management
- Advanced ROI
- Notifications
- Universal Badges
- Case Studies
- Education Videos
Copyright © 2024 Privacy Policy
Facing Today's 5G Issues and Challenges
In recent years, 5G adoption has been viewed as a race, with the earliest adopters seen as the "winners" — of the biggest business opportunities and the first chances to sell the new technology to customers. But an array of 5G issues and challenges have caused deployment to play out a bit differently than anticipated.
Rather than a marathon progressing deterministically toward a finish line, it's been more like a puzzle to be put together piece by piece. Even though the puzzle isn't yet complete, you can begin to imagine what the final 5G picture will look like as the pieces come together.
5G technology has no doubt matured in the past two years. Cellular service providers began releasing the first 5G-enabled smartphones in mid-2020, with more on the way. Good progress has been made to develop and deploy wireless infrastructure technologies like massive multiple input-multiple output (mMIMO) and millimeter wave (mmWave), both of which contribute to 5G's improved speeds. Innovative hyperscalers, like Google and Amazon Web Services, have even started hosting their own 5G virtual network capabilities.
In addition to technological progress, the business and commercial landscape has expanded. New entrants are emerging. Existing players — from cellular service providers (CSPs), cloud network developers and infrastructure vendors to manufacturers of antennas, chipsets and modules — are all interacting in new and interesting ways. The relationships between customer, supplier and collaborator are ever evolving.
The promise of 5G is still there: higher data rates, mission critical connectivity and support for Massive Internet of Things (IoT). Businesses are thinking about the value proposition of 5G — the role it plays in Industry 4.0 and the benefits of connected devices, data, automation and artificial intelligence .
However, actual adoption is still in the early stages. While deployments are well underway globally, 5G has not yet made the impact on our daily lives that 4G made. In a survey of 193 telecommunications stakeholders fielded by Jabil and SIS International Research in the fall of 2021 about the challenges and opportunities associated with 5G deployment, only 14% of respondents said they believe 5G usage is already mainstream. Nearly two-thirds, 64%, believe it will take another one to three years, while 19% believe it will be three to five years before 5G is widely adopted.
There's been plenty of investment in 5G technology development, in spectrum to deploy 5G and in networks to support 5G. Nevertheless, we have not yet seen the enthusiasm and economic boom that accompanied 4G. Why is that?
Let's explore how the technology and the ecosystem have evolved over the past several years and how we can overcome the new challenges we face in building the age of 5G.
Download the full 5G Technology Trends Survey Report.
The 5G "Triangle" Has Grown in Diversity & Complexity
As the technology underpinning 5G has become more developed, a realization of the complexity of 5G has come along with it. Early capability charts showed the famous triangle that highlighted 5G's three main benefits — faster speeds, lower latency and the ability to host many more IoT connections at once.
Image Source: Qualcomm
As the 5G standards have evolved, more features have been defined and added, to the point where an 11-axis spider diagram is now required to summarize the capabilities visually. The areas where 5G provides substantial improvements over 4G are:
- Extreme data rates (multi-Gbps peak rates; 100+ Mbps user-experienced rates)
- Extreme capacity (10 Tbps per km 2 ) to handle more devices in a small area
- Deep awareness (discovery and optimization for machine learning)
- Ultra-low latency (as low as 1 millisecond of lag time)
- Ultra-high reliability (10 -5 per 1 millisecond)
- Strong security (especially important for healthcare, government and financial institutions)
- Extreme user mobility (connection is maintained for devices/vehicles moving up to 500 km/h or 310 mph)
- Ultra-low energy connections that help give IoT devices 10+ years of battery life
- Ultra-high density (1 million nodes per km 2 ) so more devices can be connected simultaneously
- Ultra-low complexity (10s of bits per second)
- Deep coverage
Clearly the 5G specifications have grown in richness and capabilities. Having such a diverse "toolbox" of capabilities is a great benefit to service providers; it enables them to customize and optimize their networks tailored to customers' needs and to add new and innovative services.
However, this richness of capabilities could also present some difficulties. The companies developing 5G products and services now have a much broader spectrum of features they need to develop. This will require a significantly larger investment than in prior generations. Also, these companies are typically resource-constrained, so they will need to prioritize which feature sets they develop and decide which features they will defer.
Challenges do not exist only on the supply side. The customers for these products and features, the service providers, generally have different strategies on how to deploy 5G. As such, they would tend to focus on a subset of 5G features that they would purchase. Since not all service providers are interested in all features, there will likely be an overall dilution in the willingness to pay across the broad 5G feature set.
The breadth of features and the investment required could lead to a slower rollout of 5G features. Dilution on the demand side could present challenges to the overall economics of 5G. Almost a third of respondents in Jabil's 5G survey (31%) indicated that these business model challenges were the most difficult category of 5G issues for their organization to solve, compared with 19% who were most challenged by operational hurdles, 18% technology challenges and 16% by supply chain or customer issues. It seems that telecommunications companies have yet to determine how to best package 5G, as creating subscription models was the biggest business challenge faced by survey respondents (31%). It will be interesting to observe the balance between these challenges and the substantial benefits of the broad capabilities in the 5G "toolbox."
5G Spectrum Allocation, Investment and Deployment Are Happening — But Slowly
As noted previously, there has been lots of progress in technology rollout and investment in product development for 5G. So why don't we see ubiquitous high-speed 5G service affecting our daily lives?
To provide that pervasive high-speed coverage over a broad geographic area requires the wireless equivalent of real estate — namely spectrum. This spectrum needs to be allocated, typically by national regulatory bodies, and then equipment needs to be deployed to utilize the spectrum. This takes time.
It is quite well known that there has been substantial activity in allocating spectrum on a global basis . There has also been a high degree of enthusiasm to invest in this spectrum, as evidenced by the recent $81 billion auction of mid-band spectrum in the U.S.
The question of how much time is required to deploy it depends on which area of the 5G spectrum we're talking about. There are a variety of speeds and services available within the 5G spectrum bands .
For mid-band 5G spectrum (in the range from around 1 GHz to 6 GHz) the time factor is driven by the fact that the spectrum is not immediately available for use. After an auction happens, it can take many months to clear the spectrum and deploy the equipment that will eventually operate in that band. For example, the spectrum awarded in the United States' February 2021 auction is expected to be available in December 2021 for service providers to begin testing. At that point, the challenge shifts from a spectrum availability problem to an equipment investment and deployment problem.
5G spectrum bands cover different geographies
The dynamic for high-band spectrum (from 24 GHz to 40 GHz) is different. In this case, the spectrum is generally clear, and there's plenty of "real estate." However, to get good high-band coverage, many millimeter-wave base stations must be deployed. This is due to the fact wireless signals do not propagate, or travel, very far distances in this band. Typical coverage for a base station in this band is several hundred meters, requiring many base stations to provide service across a broad geographical area.
Similar to traditional small-cell deployments, it can take substantial time to obtain leases, site approvals, power and connectivity for the site. Compounding this across the many sites required presents a difficult and time-consuming logistical process; nearly one-third of Jabil's 5G survey respondents (32%) said identifying the physical locations to install 5G equipment was a hurdle to their organization's 5G deployment, the most common challenge amongst respondents.
In either case, the combination of spectrum licensing costs and equipment deployment will add up to a substantial investment for network operators and service providers. The critical question then becomes, "What will generate the revenue to offset that investment?"
The answer could lie in the elusive killer app.
Where Is the Killer App?
At this point in time, the question "What is 5G?" is generally answered in terms of capabilities: extreme capacity, ultra-low latency and ultra-high reliability. None of these describe the actual user experience with 5G, and indeed, some of these capabilities are so esoteric that typical users may not be able to relate to them.
When the user experience is considered, you might respond with answers such as, "It's fast er , security is strong er and reliability is bett er ." These are attributes that users can relate to somewhat better. However, these are adjectives that describe an incremental experience.
As discussed earlier, the investments in technology development and spectrum are by no means incremental. They lean more toward astronomical. In order to balance these investments, the user experience in 5G cannot be incremental. It needs to be disruptive .
There is always talk of the "killer app," almost to the point that the term has become glib. However, in the case of 5G, the notion of a killer app that delivers a disruptive experience is essential. This is because, while there's certainly a lot of buzz around 5G, many consumers aren't sure what it's all about or whether they should invest in it when the time comes.
A recent study by Ericsson found mobile device consumers are willing to pay 20% to 30% more for 5G plans bundled with new apps and services. But that finding came with a big caveat. About 70% of current 5G users are dissatisfied with the lack of new and innovative apps. In other words, they want the killer app.
Admittedly, the question of the killer app is an easy one to ask but a difficult one to answer. Indeed, if I knew the answer, I might be in another line of business. However, we will soon look at some potential areas where the elusive killer app might emerge.
Solutions to the Biggest 5G Challenges
The complexity and diversity of the 5G specifications, the challenges of spectrum clearance and deployment, and the absence of a killer app are all headwinds facing 5G rollout. However, these are by no means intractable problems. The question is, what can be done about them?
A number of the current challenges — like spectrum clearing and auctioning, along with equipment deployment — will just take time and traditional effort to overcome. Cellular service providers in the U.S. have said they expect consumers to begin accessing the C-band awarded in spring 2021 by the same time next year. Extrapolate that out, and the C-band spectrum auctioned off in the fall of 2021 could be rolled out by the end of 2022. Considering only 12% of U.S. smartphone users have a 5G-enabled phone, this also gives consumers time to plan and make their device upgrades.
This also gives providers, operators and other players within the diversifying 5G ecosystem the opportunity to dig deeper into possible solutions for the hurdles the industry still faces — while also exploring new opportunities the technology presents.
Leveraging the Evolving 5G Ecosystem
While 5G has primarily depended on new, innovative technology for its solutions, in one case, new research is finding that existing, commercially available technology might be the best way to bring down the cost of in-demand millimeter wave coverage. Mobile Experts determined that operators could save up to 52% of the cost to deploy mmWave base stations by using a mix of wired and solar-powered smart repeaters to spread coverage between base stations — reducing the number of base stations needed in a given area.
The issue of 5G's complexity and diversity, and the solution to driving faster development of 5G's comprehensive feature set, will likely require a deeper engagement of the broader ecosystem. To that end, more companies outside of the traditional telecommunications industry and equipment providers are developing network and user equipment — like handsets, radios, small cells and customer premise equipment (a " 5G box " you can put right in your home or building). Such efforts can address the broader needs caused by 5G's complexity. There is so much demand for 5G technology and equipment that the opportunity is ripe for disruptive companies, startups and new entrants.
Open Radio Access Network, or Open RAN , is a great example of this. Open RAN has three key elements : cloudification of the RAN applications, intelligence and automation, and open internal RAN interfaces. With an open network, a set of standard specifications across the industry would allow cellular service providers to deploy components from various OEMs for their 5G technologies — radios, digital units, and so on — to get highly competitive pricing and potentially more features. Additionally, a majority of Jabil's 5G survey respondents believe Open RAN adoption will help reduce their overall costs; 81% said it would help an organization cut their capital expenditures, while 85% believe it will help bring down their operational expenditures.
Three elements of Open RAN
Open RAN enables a broader and diversified supply of radio equipment from even non-traditional players to help meet the demands of all of 5G's many capabilities. With more equipment options, CSPs can customize their offerings and give customers an optimized 5G experience.
5G is creating an ecosystem that is welcoming smaller companies, startups and other businesses outside of the typical equipment manufacturers and cellular service providers. Hyperscalers and other non-traditional tier 2 companies are using Open RAN to host their own wireless network functions and develop the associated software, pushing the boundaries of what 5G can do and who can use it. However, some telecommunications stakeholders are still unsure how hyperscalers will fit into the 5G picture. More than half of Jabil's survey respondents (56%) said hyperscalers like Amazon, Microsoft and Google don't fit into their organization's Open RAN strategy.
Who Will Develop the Killer App?
Discussions about potential applications of 5G often include ideas such as private networks, fixed wireless internet and healthcare. Our survey respondents suggested financial services (22%), transportation (17%) and healthcare (16%) could be the industries that are most impacted by 5G. While these may seem incremental in comparison to 4G capabilities, let's examine two areas that may unleash unprecedented opportunities. The single most important element to fuel investment in the 5G ecosystem will be the emergence of applications that provide enough differentiation in capabilities to entice a power user or a family to pull an additional $10 or $20 per month out of their pocket. For a true killer app, we need to look deeper.
The 5G ecosystem is creating an environment for non-traditional technology companies to explore out-of-the-box connectivity or technology options. I would expect to see one of these disruptive players, companies similar to Facebook and Uber that came before them, hit on the killer app that truly ushers in the age of 5G. Overwhelmingly, survey respondents indicated they believe the killer app will benefit the business world most (58%), rather than personal (20%), enterprise (18%) or healthcare use cases (4%). Still, there are a few different areas we should keep an eye on for this eventual game-changer.
It is important to consider users who are on-the-go most often, generally in a business capacity. In previous generations, we may have called them "road warriors." Today, we might call them "digital nomads," or individuals who aren't tied to one location for work. Whenever the world opens up post-pandemic, what will these frequent fliers, long-distance drivers and serious streamers need to keep their GPS running and their video calls crystal-clear, wherever they are in the world? The key is understanding how to leverage key capabilities of 5G, which can power their lifestyle and make them more effective in ways that mark a drastic improvement over 4G.
A fundamental benefit 5G provides is the ability to securely provide reliable high-speed data in a mobile environment. Think about taking cutting-edge connectivity applications outdoors and on the road, which Wi-Fi cannot support effectively. There has been intriguing speculation on the future of AR/VR-enabled games and apps , exciting for a closet gamer like me. Further, imagine bringing true AR/VR experience and the "metaverse" (such as Facebook's Horizon Workrooms virtual office) to any environment. Ubiquitous human connectivity is a capability for which people have been paying a premium since the introduction of long-distance telephone service. Apps that provide a new level of connectivity, ones that consumers are willing to pay extra for, are exactly the driver that can fuel the economic engine of 5G.
Augmented and virtual reality go mobile with 5G
There is hardly a technology article written these days that does not reference artificial intelligence or machine learning (this one included). Slowly but surely these technologies are making their way into our everyday lives, from smart home voice assistants to their use in fields like healthcare (to discover new drugs) or renewable energy , optimizing systems based on sensors and weather data. The algorithms and techniques have progressed greatly in the past decade. The enormous amounts of data required to fuel the algorithms have been collected, are available and are growing.
However, imagine challenges for AI in a mobile environment; having enough processing power in the hands of the mobile user and having immediate access to vast amounts of data are the biggest hurdles. 5G technologies provide true differentiation in this space. Advanced network architectures supporting edge computing can place substantial processing close to the mobile user without burdening the mobile handset with the power, heat and cost required to support these algorithms. The ultra-low latency and ultra-high reliability connectivity inherent in 5G effectively reduces the 3x10 8 (speed of light) delay in system design. This will enable the massive amounts of data required to power AI and ML algorithms to be centrally located in a cloud repository while being logically or architecturally "close" to the edge processor executing the algorithm.
It is clear that such a tandem of capabilities, powered by 5G, can enable a new generation of mobile AI/ML features not possible with other communication technologies.
Edge computing brings artificial intelligence to mobile users
It is not a big leap to imagine a disruptive company, perhaps currently germinating in the 5G ecosystem, applying technologies like these to an application that has "killer" potential.
5G Is the Future. The Future Is Probably Coming Soon.
The headwinds facing 5G (specification complexity, spectrum availability, and the absence of a killer app) are not insignificant. At least for now, 5G has not yet led to substantial economic growth the way 4G did in the last decade. It's estimated that between 2011 and 2019, 10% of U.S. GDP growth was due to the wireless industry (powered by 4G). This obviously has yet to happen with 5G.
Despite the complexity of mission, complexity of technology, complexity of economics, and complexity associated with uncertainty, 5G is clearly progressing. This progress is not only in technology and investment, but perhaps more importantly, the ecosystem of players is maturing greatly. The traditional linear business model historically prevalent in wireless is transforming. The 5G world will continue to see an influx of new players, and companies might find themselves customers, suppliers and partners all at the same time.
Given this, the successful players in the 5G space will be exceptional at collaboration and will play active roles in a broader ecosystem. This is a great advantage that 5G has over previous generations, and I believe it will power 5G strongly through the current headwinds. Teamwork, flexibility and a whole lot of creativity will be key to putting together the 5G puzzle.
The future of 5G is bright, and it is probably soon.
Download the 5G Technology Trends Survey Report
Insights from 193 telecommunications decision-makers on 5G adoption, predictions, opportunities and challenges.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- 5G Simulation Tools EXPLAINED
Fifth-generation mobile communication is one of the fastest-growing wireless communication technologies. Get to Know about Top 12+ 5G simulation tools . Let’s start with a question, i.e., what are the expected demands out of 5G?
- Enhancement of reliability
- Increased throughput
- Efficiently working in the mix of high traffic
For these purposes, proper hardware and software have to be deployed, and at the same time, some parameters have to be optimally managed inevitably. The following are the important parameters in 5G simulation that have to be considered by researchers
- Positioning of the network (based on the density of deployment – dense, ultra-dense, and very dense)
- The increased power of transmission
- Reduce the cost of acquisition
- Higher throughput
- A minimal amount of energy radiation
- Handover zone optimization
There is still a lot to know about the optimum dimensioning about which our experts have gained great knowledge. It is important to be noted that the condition for optimum functioning of the communication network depends primarily on the environment and situation in which it is being implemented. Now let us see in detail.
- Minimal cost for acquisition of the site
- The maximum value of throughput
- Deployment density at transmission and reception
- The bandwidth of the system
- Ultra-dense
- Requirements of coverage
- Capacities both hardware and software that are required
Thus, we can choose the best 5G Network revolutionary option that can be implemented in real-time. Our developers gained big experience in working with different 5G simulation tools . You can readily approach us without any hesitation to get your doubts about simulation software solved. This article will give you a complete idea of different simulation tools for 5G networks. Let us first start by understanding it’s working.
5G network project has to be simulated to test its performance under various real-time situations. So it can be used to test the network and its requirements even before implementation. The following are the steps based on which a 5G simulation tool works.
HOW DOES THE 5G SIMULATION WORK?
We have listed below important points regarding simulation working model, based on this we can select best 5g simulation tools for your research work.
- 5G network simulation for various base stations and nodes have to be determined
- The 5G network architecture is to be defined for cross layers
- 6 GHz is the minimum range of frequency of the spectrum
- Transmission has to happen securely
- Security in multiple layer connection should be ensured
- LTE device performance should be achieved at a high degree
- Cellular networks for multiple sectors supported
- Modeling and management of network carrier
- Managing the frequency of the spectrum
- LTE connectivity at multiple levels
Our experts are here to support you in all aspects regarding the working of any 5G simulator . You can interact with us and have an idea of choosing the best 5G simulation tools for your project . The following are the major steps involved in 5G simulation using any standard simulator.
- The proper scenarios are to be selected
- Assignment of MS location and path loss determination is the next step
- Coefficients of the channel are generated
- Service for each MS is requested
- Allocation of the channel and modulation are performed
- Assignment of precoding matrix is the next step
- Signal to noise ratio is effectively calculated
The deployment of 5G towers, virtual nodes, servers, base stations, and controllers requires different libraries and several tools and predicting network behavior . Our technical team is well known for its experience in advanced 5G simulation architecture . From our technical knowledge, we will guide you through the process of making the best 5G simulation software. Now let us understand the different simulators that are present today.
5G NETWORK SIMULATORS
Before getting into the different simulators available for simulation of 5G network projects , we should have a quick look at its broad classification.
- System-level simulations – these are affected by the exchanged messages and packet flows (examples include extend sim and SIM grid)
- Full-stack simulations (packet-level simulations) – these kinds of simulators include ns2, ns3, OPNET, OMNET ++, and QUALNET
You should be very cautious while using these simulators because the simulation you choose should align with your project objective. Such circumstances where the simulators are to be deployed can use more than one simulation tool to complement each other.
Now let us see in detail different packet-level simulation tools.
- The ns2 simulator is an open-source platform that is also user friendly to be a part of 5G network simulation
- LTE – A model (IEEE 802.15c standard) is used for simulation
- It supports OPNET 18.0 standard
- It can be better used for analyzing the performance of many different network types
- Generally, MATLAB is used for the simulation of many projects, including 5G networks
- The 5G toolbox present in Matlab are specifically attributed to doing the following
- Generating signals
- Modeling of channels
- Simulations at the link level
- Toolbox for antenna, LTE system, a system of communication, SimRF, a system of the phased array is present in MATLAB Simulink
- Novel algorithms and infrastructure of 5G network are deployed using this simulator
- FPGA hardware prototyping using the platform of SDR is supported in the unified environment (dynamic)
- MIXIM framework – IEEE 802.11.3ad + SimuLTE and INET framework – IEEE 802.15.3c + SimuLTE are the two protocols for 5G implementation using OMNET ++ framework
- It is an open-source simulation tool that has a good graphical user interface supporting simuLTE and mmwave module in the 5G network environment of INET
Do you want to have a sample procedure in the OMNET ++ network simulator ? We are here to give you customized solutions to all your 5G network simulation queries. Now we will give you a sample simulation steps using OMNET ++.
- mmwave tarball and simuLTE are to be downloaded and installed
- INET to 5G directory conversion is the next step
- Generation of ‘makefiles’ have to be carried out
- Type “make” for building implementable simuLTE
- ./run is finally used to run the simulation
Our experts have guided many projects related to 5G simulation using the OMNET framework . For more details on OMNeT ++, contact our experts. Now let us see about the other important 5G simulators.
- The library software of ns3, called the 5G mmwave module is written using python and c++
- Mac layers and physical layers are designed well using this simulation
- It supports uplink, downlink scheduling of Mac protocols, OFDM, and TDD
As an example here, we have provided the procedure for NS3 interfacing with mmwave module
- LTE folder is copied into mmwave
- It is then put into NS3 Src
- Terminal is opened
- Then go to NS – all-in-one – 3.2x/ ns – 3.2x
- “sudo ./waf configure” is typed
- “sudo ./waf build” is used to build the module
We are here to solve all the technical doubts regarding different simulation tools for the 5G network in a more precise and logical manner. As we have also guided in the implementation of a lot of projects in real-time, we are capable enough to give you the practical solutions to many of the research problems that you might face now. Let us have some idea on different 5G network simulation tools other than those mentioned above.
OTHER RELATED 5G SIMULATION TOOLS
In order to choose the best simulation tool for your 5G communication network project , you should first understand the working of different simulators so as to choose from among the simulators with different characteristics.
- The cloud services based on 5G network systems are simulated using this tool
- EURECOM partners sponsor this simulation tool
- 5G cellular networks development is based on this simulation (commercial off – the shelf hardware)
- It is used in the generation of temporal and spatial wideband thus; as a result response of the channel impulse is studied
- User-friendly interface
- Carrier frequency range from 2 and 73 gigahertz
- It is the best simulation tool using NS3, where education and research are the major domains in which it is used
- S – 5G channel is the next generation simulation tool
- It is one of the innovations carried out by recent researchers
- It is an open-source simulator
- Py layers can be used to simulate particular radio channels that are specific to different areas of applications which include the following
- Mobile communication propagation
- Heterogeneous networks
- Wearable communication devices
- Large-scale 5G communication network simulation is possible using the Vienna LTE simulator
- It is oriented under multiple tiers
- The software coats are free to use which can be used to support parallelization of many nodes
- It is a system-level 5G simulator
- WISE is a multi-tiered orientation tool
- Validating and simulation of 5G is possible using the available source code present in.
- RANPLAN stands for Radio Network Planning
- AR and VR like novel 5G services can be simulated using this tool
- It is helpful in the following
- Deployment of heterogeneous networks
- Deploying small cells in an ultra-dense model
- 5G link-level simulation
- Implementation of transceiver
You can get any kind of research support on all the above 5G simulation tools from our dedicated team of experts providing research support for 5G simulation projects . Other simulation tools have the following characteristics.
- Simulators with interfaces for open functioning
- Simultaneous transmission across different technologies that are accessible
- Supportive to heterogeneous networks
- The capability of transmission at mm wave frequencies
- Users scheduling techniques and AMC
Connect with us to know in detail about the working efficiency of different simulators, and then choose the best tool for your project. Let us now talk about the important requirements of a good 5G simulator.
MAJOR REQUIREMENTS OF 5G SIMULATORS
The conditions of the channel and the network traffic define the configuration of any network. The 5G nodes are included dynamically based on the above two aspects and the bit rate. So the first major requirement of the 5G simulator is its capability to act according to the dynamic nature of the network. The other essentials of a 5G simulation tool are listed below
- BS-MS channel link modeling
- Relay at the intermediate level (at D2D link)
- QoS supportive
- Enhanced gain of the channels acting as relay nodes at the intermediate level for MSs
- Simulator embedded channel links are possible
- Maximizing the rate of data (using the MU – Massive MIMO techniques) – The complex post-processing methods that are highly efficient in computation using proper techniques for beamforming (accepted QoS provisions and separation of users are supported)
- 4G and 5G networks co-existing in the same area form the better infrastructure, which is heterogeneous. Quality of service parameters has to be preserved even when the network switches from one form to another.
- The features that are created and developed using the simulation codes for 5G should be verified universally. The flexibility and reusability of the simulation tool, which is also supportive to different real-time situations, are also needed
- The dynamic configuration of the 5G networks should involve the techniques of adaptive RRM. Optimization of various variables associated with the network functioning is complex to be determined. Based on the characteristics of the present link, the different link’s fronthaul ability decides the function split.
You can talk to our world-class certified developers and engineers regarding any technical doubts about different 5G simulation tools. We will solve your problems by giving practical examples and solutions to your questions instantly. Now let us have a quick look into different security threats that can take place in a 5G network simulation project .
SECURITY ATTACKS IN 5G NETWORK SIMULATIONS
Until now, we have seen that the channel has to be modeled by incorporating BS-MS link, relay nodes at the intermediate levels, v2x communication, and D2D link. In such a design, some threats can become potential while simulation. Before getting into detail about such security threats, we need to ponder upon the following aspects of the 5G network simulation
- Network performance
- 5G and advanced Behaviour of the network
- Networks behavior, along with its formation, can be easily determined
- There is a possibility of different attacks as a result of the ns3 simulation tool used over mm-wave
In the case of networks with multiple nodes, the following are the major security threats that can arise. You can get the help of our research experts who gained enough experience in solving such issues
- The nodes are replicated or are imitated so as to confuse the servers.Mm-wave ns3 simulation can be used to avoid such types of Sybil Threats in the future
- The environment of the network is damaged by injection at the front end level
- Conventionally the packets are let into the network channels, and critical information is damaged
- Again mm-wave ns3 simulator libraries and code can be used to solve this problem by simulation
- The package is distributed from sources which in turn will stall the 5G network functioning
- In that situation, mmwave ns3 simulator can be used to deploy a preventive algorithm that prevents such kind of attacks when a particular number of users are achieved in a network
From the points mentioned above, you should have now understood the infrastructure for the 5G simulation , which would need the following aspects to be fulfilled.
- Physical layer transmission aspects like protocols for accessing, massive MIMO, mm wave transmission
- Adaptive RRM algorithms for access control
- Services that demand new bandwidth
- Configuring the networks for a variety of elements
- a unified framework in the midst of inbuilt complexity
- The best simulation tool to handle all the above aspects of 5G network projects must be thus made as your choice.
We are updating ourselves regularly on all the latest breakthroughs that are recorded in the 5G infrastructure. We have also proposed better options for solutions in order to handle problems with different essentials in the 5G simulation. You should keep an eye on the network traffic and the metrics associated with analyzing the 5G networks’ performance to do the best research work. Reduction in execution time can be established only when parallelization norms are taken into consideration due to the complexity of the network itself.
The complications that arise in simulations due to the network complexity can be easily solved by our technical team of engineers, who will share with you their huge user experience in guiding 5G simulation projects . The application of 5G network simulation is a huge list which includes the following.
- Applications that show zero latency
- Autonomous vehicles
- Unmanned automatic vehicles configured for dynamic situations
High accuracy in representing the channels, better network design and orientations, and the apt simulation tool can be the only solution to solve research problems in 5G. You, as a researcher, need to understand the importance of it and make your project contribute an immensely important application to the above list. Our engineers are here to support you in all aspects of your research work using 5G Simulation Tools . So get in touch with us to get your entire project guided by world-class research experts.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.

MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
5 WHY Analysis, a TPM Tool for Root Cause Analysis (RCA)
5 why process.
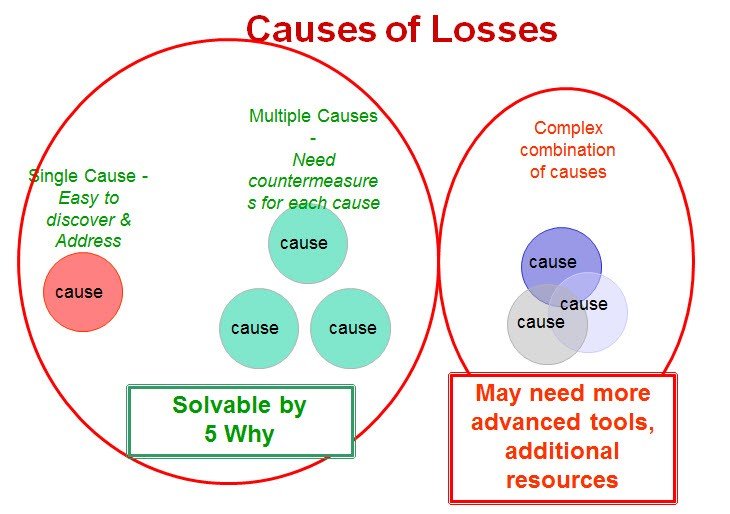
Causes of Losses are Often Complicated:
Common failure scenario:.
1. Management system breakdown 2. Failure to implement countermeasures 3. Premature equipment failure 4. Employees fail to follow the procedure 5. Failure to ID & Respond 6. Large Loss Results
5 Why Analysis is Proactive Addresses the Underlying Causes of Losses:
- 5 Why identifies the Root Causes of Losses
- Supports Implementation of Countermeasures
- Promotes Transfer of Learning
Where Does 5 WHY Fit in the Focused Improvement Process?
Focused Improvement Process
- Collect Data
- Identify, Prioritize & Select Projects.
- Ensure Equipment Is Restored
- Establish the Team
- Use the CAP-Do Process (5 Why is used here) …….. to manage the improvement cycle
- Monitor and Hold the Gains
- Document the Project (Kaizen Summary Sheet, Kaizen database)
- Celebrate Success
- Replicate Where Applicable.
- Share Learnings (Kaizen database, CI and Pillar CoP)
How is 5 WHY used in CAP-Do?
a. Identify the problem
b. Understand the Ideal Situation
- Machine: equipment sketches and the operational principle
- Material: samples of material involved in the problem
- Method: Flow charts of the process
- Man: Forms, procedures
c. Identify the Phenomenon 5W1H Analysis
Root Cause Analysis tools: 5 WHY
a. Action Plans (Immediate, Intermediate, Long Term)
- Safety Comes First!
- OPL’s
- Implement Actions
- Observe Results & Hold the Gains
Before Starting a 5 WHY ANALYSIS …
- The CHECK phase of CAP-Do must be completed . . .
– The problem identified
– The Ideal Situation understood
– The Phenomenon identified through the 5W 1H Analysis
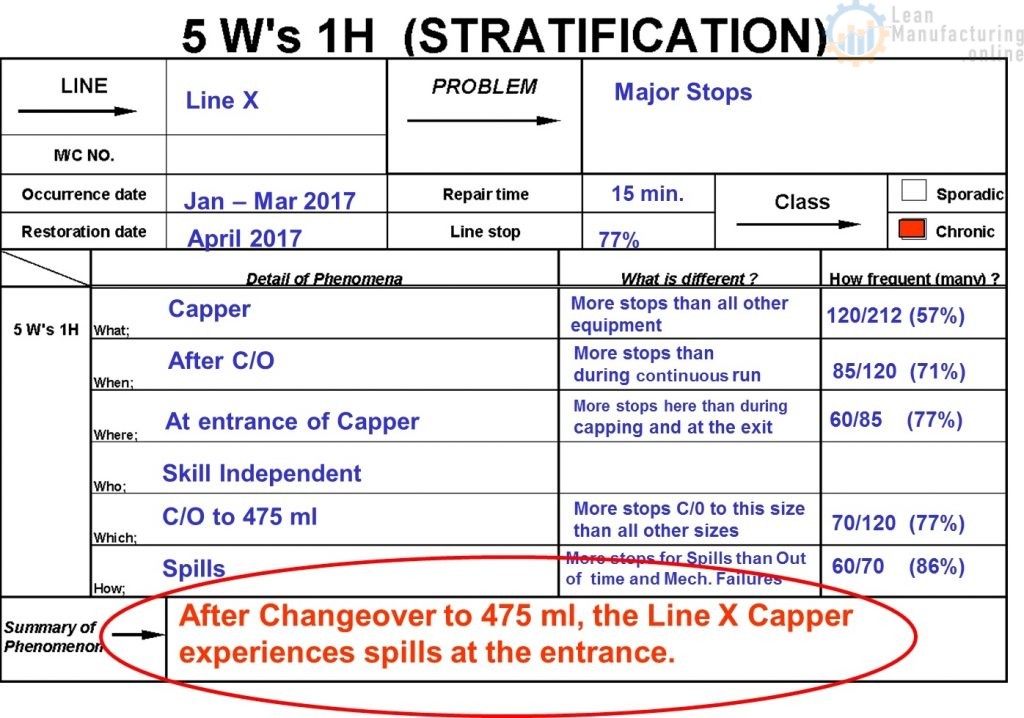
How Do You Start the 5 WHY Analysis once you identify the Phenomenon (5W 1H Analysis)?
- The 5 WHY Analysis involves asking the question “WHY ?” multiple times (typically 5) until you arrive at the root cause.
- The Phenomenon Statement from the 5W1H is the starting point for the first WHY.
EXAMPLE (see picture above) – Transition from 5W1H (CHECK Phase) to 5 WHY (ANALYZE Phase)
- Why does Line X Capper experience spill at the entrance after the changeover to 475 ml?
Ask Why…? Ask Successive Whys…?
(follow phenomenon – (be) cause relationship).
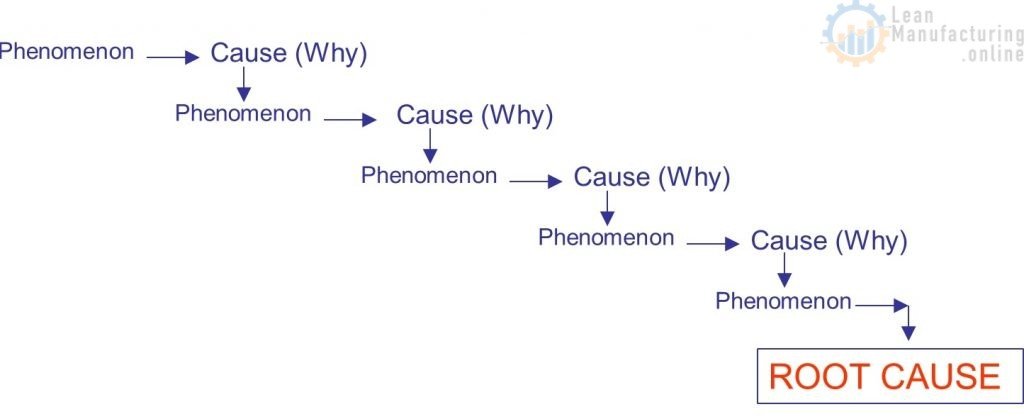
Develop a Cause Tree to Order your Thinking
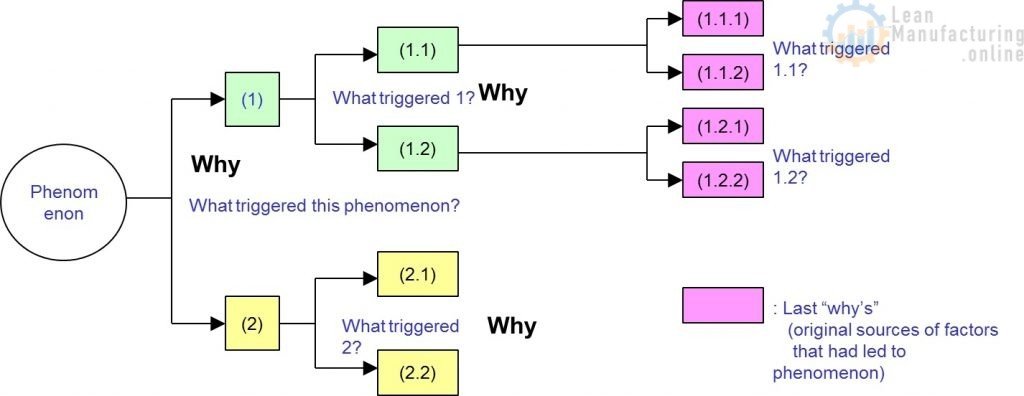
5 WHY Analysis Using the 4 M’s
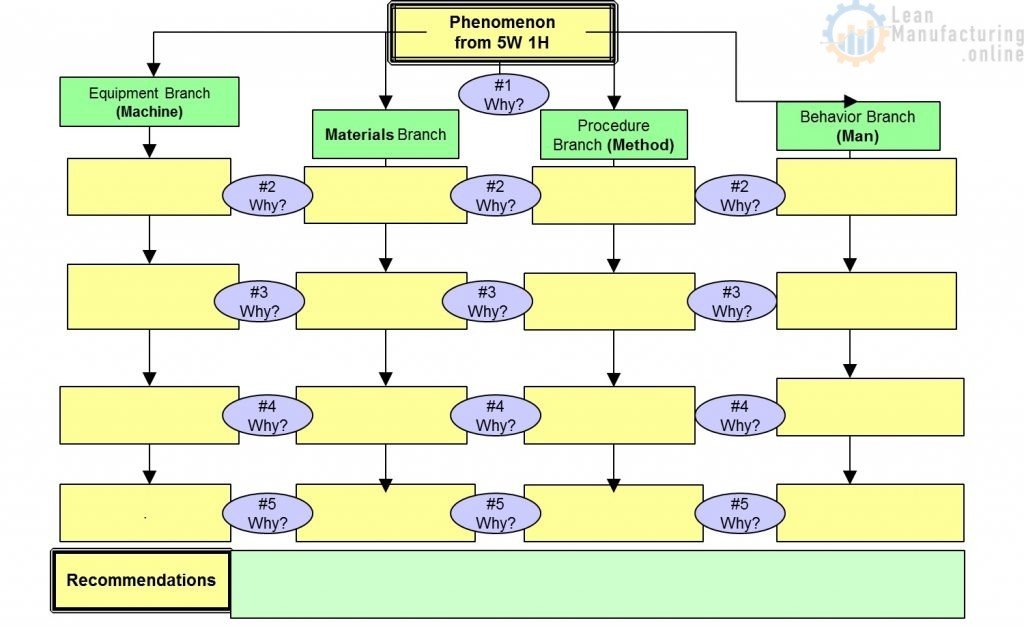
Causes to Consider:
Equipment Branch (Machine)
- Improper Equipment Ordered
- Poorly Designed Equipment
- Inadequate Maintenance
- Wear & Tear
- Abuse or Misuse
Materials Branch (Material)
- Materials out of spec:
- Ingredients
- Materials damaged:
- from storage
- from supplier
Procedural (Method)
- Lack of Procedures
- Inadequate Procedures
- Misunderstood Procedures
- Failure to Warn or Respond Note: Large losses often occur because of failure to take timely action
Behavioural Branch (Man)
- Lack of Knowledge
- Lack of Skill
- Physically Incapable
- Lack of Motivation
5 Why Analysis Pitfalls to Avoid
- Failure to step SLOWLY and METHODICALLY through the process
- Tendency to jump several “Why” s at once
- Tendency to assign pre-conceived causes
- Failure to consider ALL of the causes
- Use the 4-M approach to help avoid this pitfall
5 Why Analysis – Recommendations
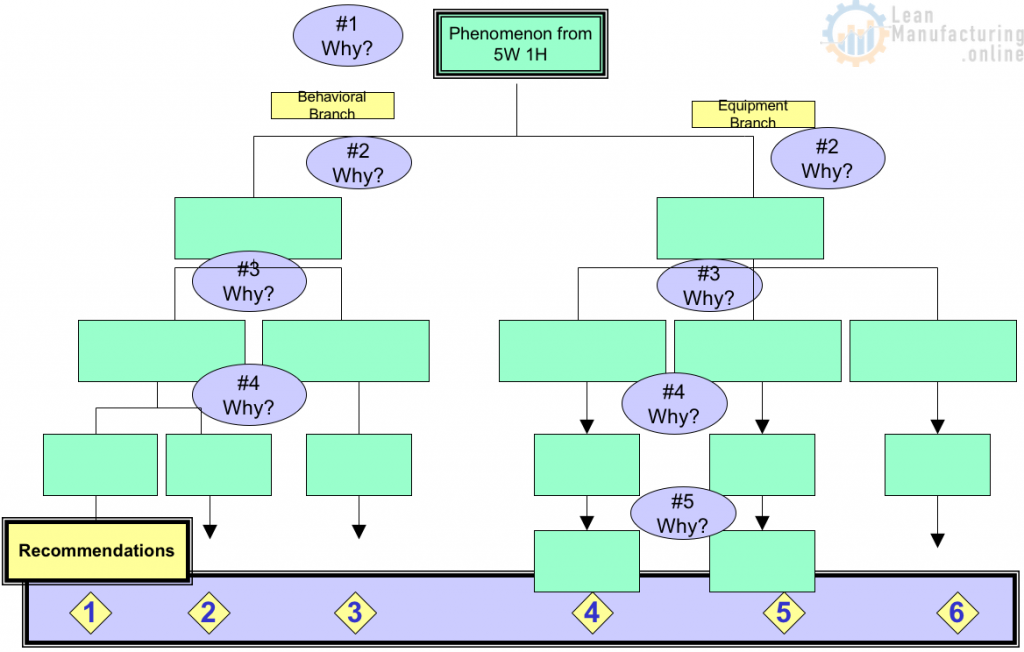
What to do with the Recommendations? . . .Follow CAP-Do . . .

How to go from 5 Why to the PLAN Phase of CAP-Do?
- For each of the last Why answers, identify recommendation(s) (countermeasures):
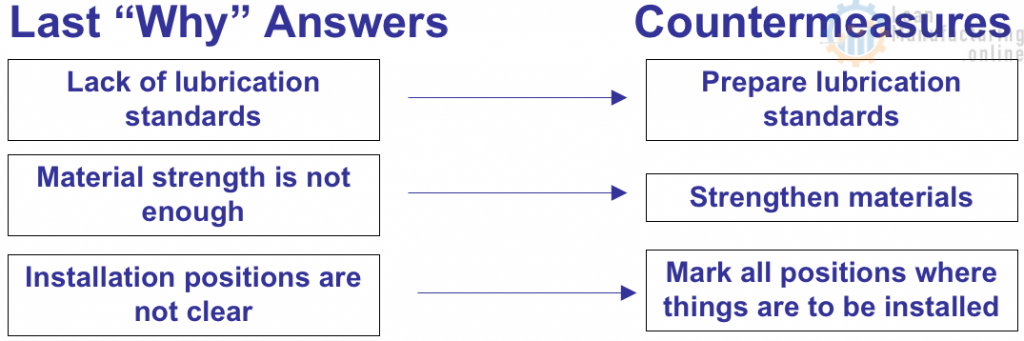
- Develop an Action Plan for each of the countermeasures:
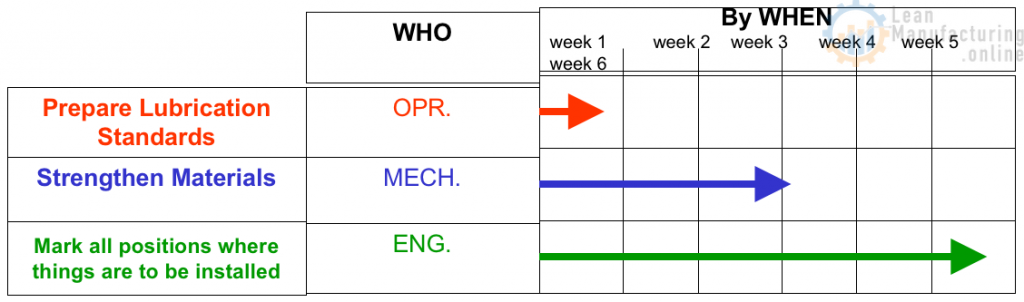
Carry Out “Do” Phase of CAP-Do
Implement the Action Plan
Hold the Gains by Developing Standards:
- Cleaning, Inspection & Lubrication Standards
- Processing Standards
- Maintenance Standards
- Training Standards (i.e. One Point Lessons )
- Engineering Standards
One Point Lesson
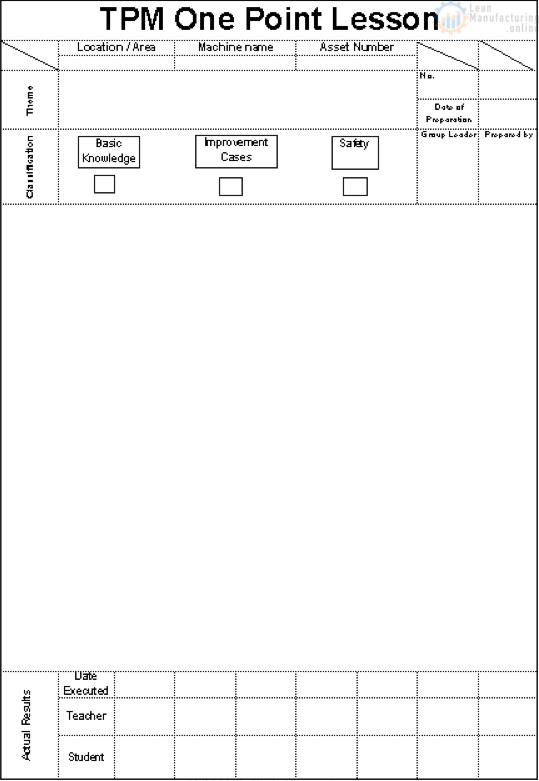
Section 2. Application of the 5 WHY Process
The Loss Pyramid
Application of 5 Why Enables Identification of Problems BEFORE They Escalate Up the Pyramid
- Identifying Sources of Contamination, Stoppages (AM Pillar)
- Tool for Analyzing Cause / Losses in Focused Improvement (FI Pillar)
- ID Reasons for Breakdowns (EM Pillar)
- ID Causes of Minor Defects, Out of Spec (QM Pillar)
- ID Causes of Near Misses, First Aids (SHE Pillar)
Section 3 Field Case Studies
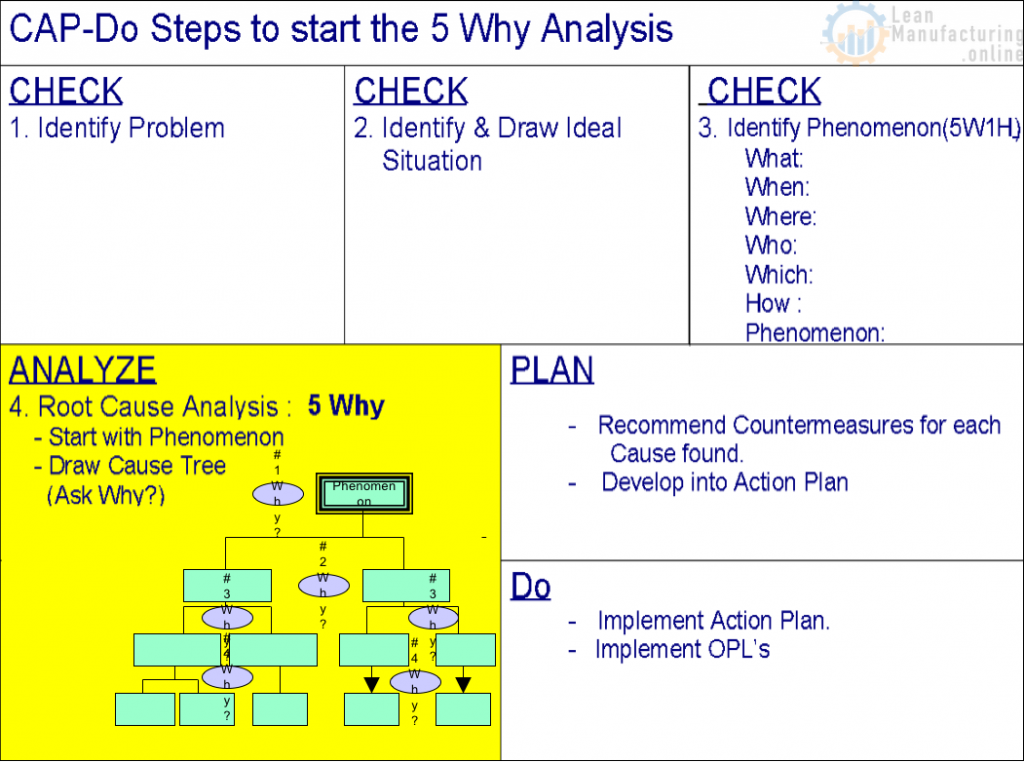
Root cause analysis
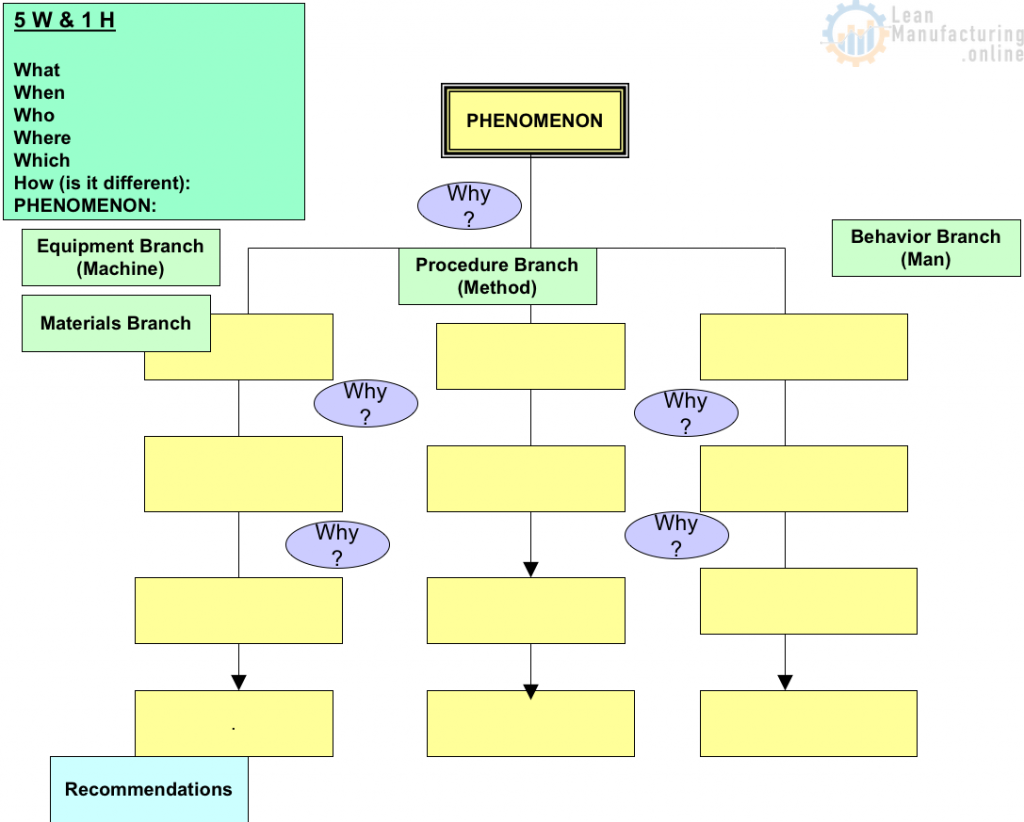
- More By sensei
- More In 5 Why Analysis
Unlock the Power of Continuous Learning with Udemy’s Frequent Sales

How to Ace Your Next Job Interview: Expert Insights and Strategies

Mastering the Trio: Project, Program & Portfolio Management

The Evolution of Performance Reviews: From Annual Appraisals to Continuous Feedback

Behaviors that kill employee motivation

Free Udemy Courses 100% Coupon
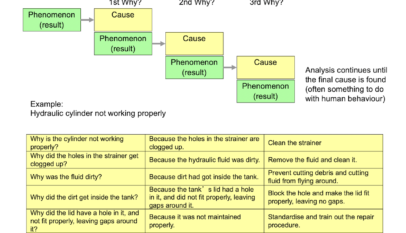
Why-Why Analysis

Safety, Health and Environment Investigation Report and Analysis
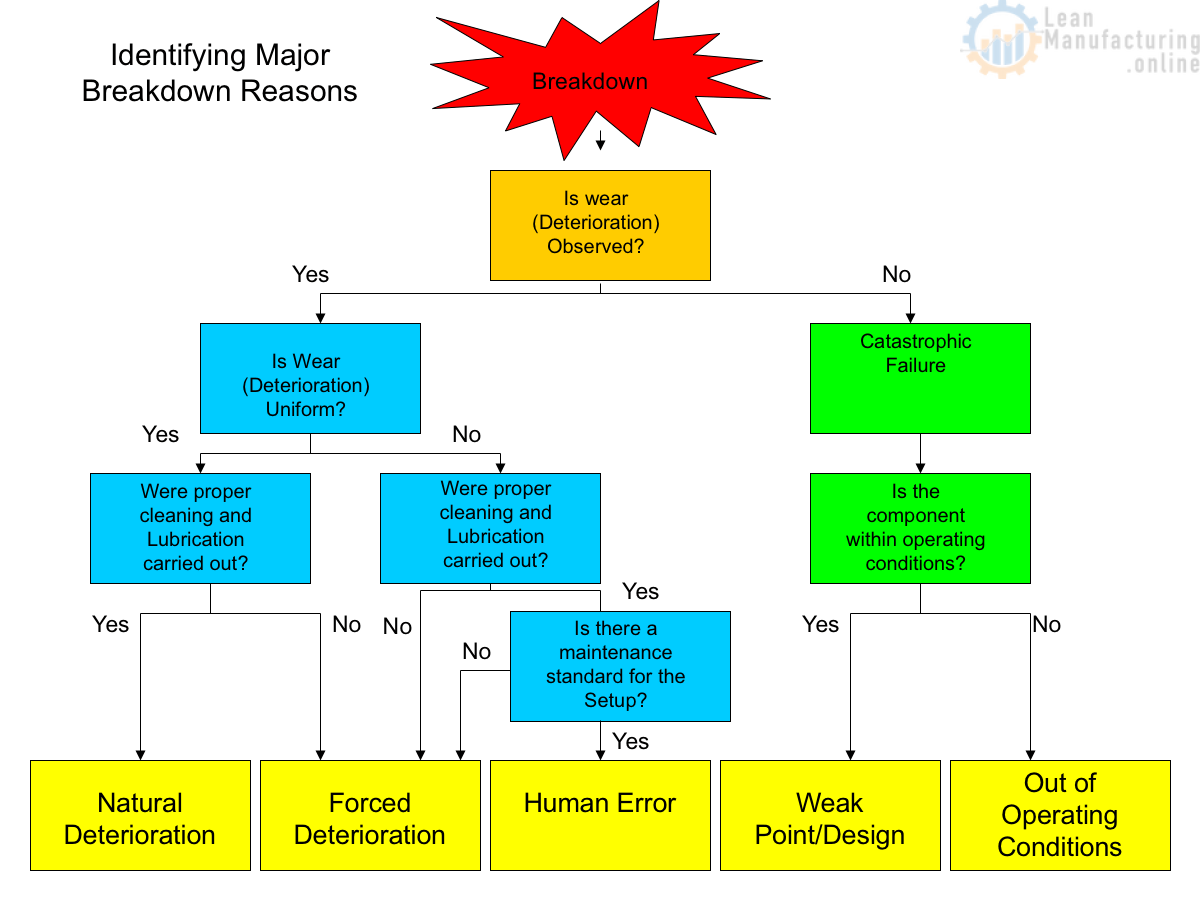
Breakdown analysis. Case Study
Lessons Learnt as a communication tool
Broken Parts Museum – Analyzing and Preventing Breakdowns due to Forced Deterioration
Leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Most Popular
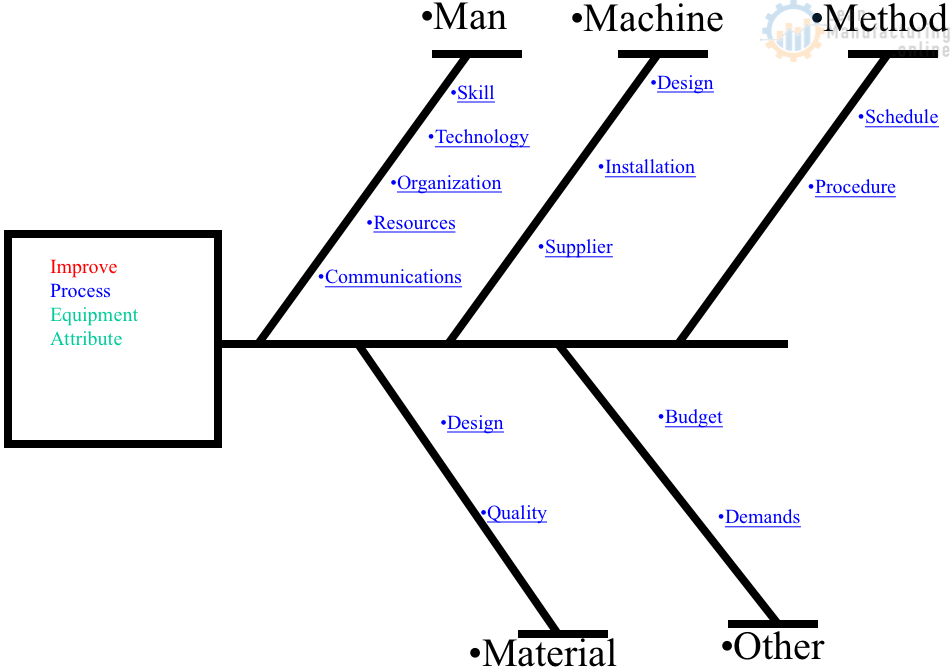
4M Analysis Process
The purpose of this procedure is to define the steps to do a 4M …

PDCA – A Process Approach
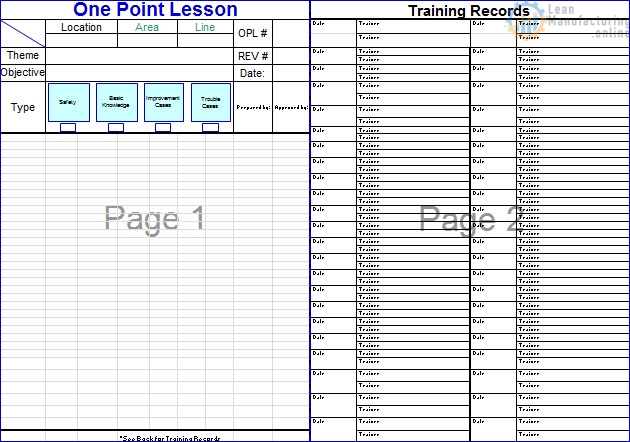
OPL – One Point Lesson Template – Free Download

5S Audit Checklist and Report

Blog Search

- Terms of Use
- Privacy Policy
- About Our Ads
- Skip to main content
- Skip to primary sidebar
- Skip to footer
Additional menu

Nine essential problem solving tools: The ultimate guide to finding a solution
October 26, 2023 by MindManager Blog
Problem solving may unfold differently depending on the industry, or even the department you work in. However, most agree that before you can fix any issue, you need to be clear on what it is, why it’s happening, and what your ideal long-term solution will achieve.
Understanding both the nature and the cause of a problem is the only way to figure out which actions will help you resolve it.
Given that most problem-solving processes are part inspiration and part perspiration, you’ll be more successful if you can reach for a problem solving tool that facilitates collaboration, encourages creative thinking, and makes it easier to implement the fix you devise.
The problem solving tools include three unique categories: problem solving diagrams, problem solving mind maps, and problem solving software solutions.
They include:
- Fishbone diagrams
- Strategy maps
- Mental maps
- Concept maps
- Layered process audit software
- Charting software
- MindManager
In this article, we’ve put together a roundup of versatile problem solving tools and software to help you and your team map out and repair workplace issues as efficiently as possible.
Let’s get started!
Problem solving diagrams
Mapping your way out of a problem is the simplest way to see where you are, and where you need to end up.
Not only do visual problem maps let you plot the most efficient route from Point A (dysfunctional situation) to Point B (flawless process), problem mapping diagrams make it easier to see:
- The root cause of a dilemma.
- The steps, resources, and personnel associated with each possible solution.
- The least time-consuming, most cost-effective options.
A visual problem solving process help to solidify understanding. Furthermore, it’s a great way for you and your team to transform abstract ideas into a practical, reconstructive plan.
Here are three examples of common problem mapping diagrams you can try with your team:
1. Fishbone diagrams
Fishbone diagrams are a common problem solving tool so-named because, once complete, they resemble the skeleton of a fish.
With the possible root causes of an issue (the ribs) branching off from either side of a spine line attached to the head (the problem), dynamic fishbone diagrams let you:
- Lay out a related set of possible reasons for an existing problem
- Investigate each possibility by breaking it out into sub-causes
- See how contributing factors relate to one another
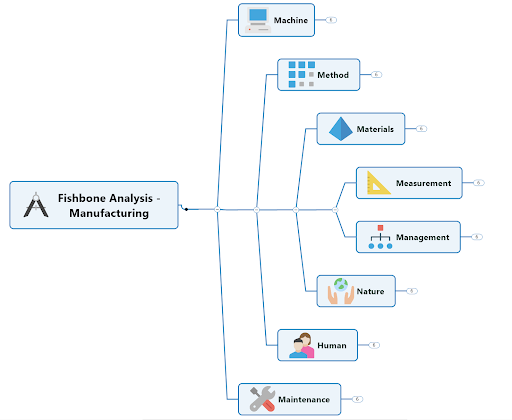
Fishbone diagrams are also known as cause and effect or Ishikawa diagrams.
2. Flowcharts
A flowchart is an easy-to-understand diagram with a variety of applications. But you can use it to outline and examine how the steps of a flawed process connect.
Made up of a few simple symbols linked with arrows indicating workflow direction, flowcharts clearly illustrate what happens at each stage of a process – and how each event impacts other events and decisions.
3. Strategy maps
Frequently used as a strategic planning tool, strategy maps also work well as problem mapping diagrams. Based on a hierarchal system, thoughts and ideas can be arranged on a single page to flesh out a potential resolution.
Once you’ve got a few tactics you feel are worth exploring as possible ways to overcome a challenge, a strategy map will help you establish the best route to your problem-solving goal.
Problem solving mind maps
Problem solving mind maps are especially valuable in visualization. Because they facilitate the brainstorming process that plays a key role in both root cause analysis and the identification of potential solutions, they help make problems more solvable.
Mind maps are diagrams that represent your thinking. Since many people struggle taking or working with hand-written or typed notes, mind maps were designed to let you lay out and structure your thoughts visually so you can play with ideas, concepts, and solutions the same way your brain does.
By starting with a single notion that branches out into greater detail, problem solving mind maps make it easy to:
- Explain unfamiliar problems or processes in less time
- Share and elaborate on novel ideas
- Achieve better group comprehension that can lead to more effective solutions
Mind maps are a valuable problem solving tool because they’re geared toward bringing out the flexible thinking that creative solutions require. Here are three types of problem solving mind maps you can use to facilitate the brainstorming process.
4. Mental maps
A mental map helps you get your thoughts about what might be causing a workplace issue out of your head and onto a shared digital space.
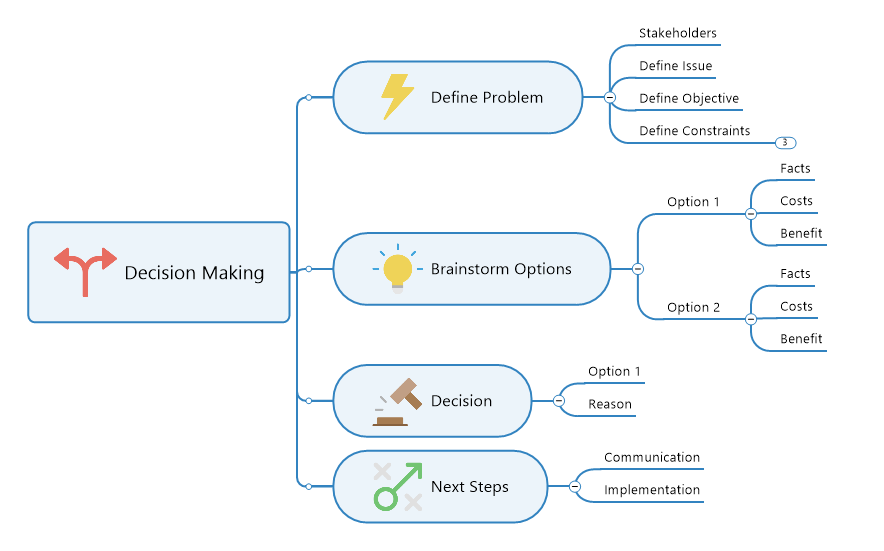
Because mental maps mirror the way our brains take in and analyze new information, using them to describe your theories visually will help you and your team work through and test those thought models.
5. Idea maps
Idea maps let you take advantage of a wide assortment of colors and images to lay down and organize your scattered thought process. Idea maps are ideal brainstorming tools because they allow you to present and explore ideas about the best way to solve a problem collaboratively, and with a shared sense of enthusiasm for outside-the-box thinking.
6. Concept maps
Concept maps are one of the best ways to shape your thoughts around a potential solution because they let you create interlinked, visual representations of intricate concepts.
By laying out your suggested problem-solving process digitally – and using lines to form and define relationship connections – your group will be able to see how each piece of the solution puzzle connects with another.
Problem solving software solutions
Problem solving software is the best way to take advantage of multiple problem solving tools in one platform. While some software programs are geared toward specific industries or processes – like manufacturing or customer relationship management, for example – others, like MindManager , are purpose-built to work across multiple trades, departments, and teams.
Here are three problem-solving software examples.
7. Layered process audit software
Layered process audits (LPAs) help companies oversee production processes and keep an eye on the cost and quality of the goods they create. Dedicated LPA software makes problem solving easier for manufacturers because it helps them see where costly leaks are occurring and allows all levels of management to get involved in repairing those leaks.
8. Charting software
Charting software comes in all shapes and sizes to fit a variety of business sectors. Pareto charts, for example, combine bar charts with line graphs so companies can compare different problems or contributing factors to determine their frequency, cost, and significance. Charting software is often used in marketing, where a variety of bar charts and X-Y axis diagrams make it possible to display and examine competitor profiles, customer segmentation, and sales trends.
9. MindManager
No matter where you work, or what your problem-solving role looks like, MindManager is a problem solving software that will make your team more productive in figuring out why a process, plan, or project isn’t working the way it should.
Once you know why an obstruction, shortfall, or difficulty exists, you can use MindManager’s wide range of brainstorming and problem mapping diagrams to:
- Find the most promising way to correct the situation
- Activate your chosen solution, and
- Conduct regular checks to make sure your repair work is sustainable
MindManager is the ultimate problem solving software.
Not only is it versatile enough to use as your go-to system for puzzling out all types of workplace problems, MindManager’s built-in forecasting tools, timeline charts, and warning indicators let you plan, implement, and monitor your solutions.
By allowing your group to work together more effectively to break down problems, uncover solutions, and rebuild processes and workflows, MindManager’s versatile collection of problem solving tools will help make everyone on your team a more efficient problem solver.
Download a free trial today to get started!
Ready to take the next step?
MindManager helps boost collaboration and productivity among remote and hybrid teams to achieve better results, faster.
Why choose MindManager?
MindManager® helps individuals, teams, and enterprises bring greater clarity and structure to plans, projects, and processes. It provides visual productivity tools and mind mapping software to help take you and your organization to where you want to be.
Explore MindManager
For IEEE Members
Ieee spectrum, follow ieee spectrum, support ieee spectrum, enjoy more free content and benefits by creating an account, saving articles to read later requires an ieee spectrum account, the institute content is only available for members, downloading full pdf issues is exclusive for ieee members, downloading this e-book is exclusive for ieee members, access to spectrum 's digital edition is exclusive for ieee members, following topics is a feature exclusive for ieee members, adding your response to an article requires an ieee spectrum account, create an account to access more content and features on ieee spectrum , including the ability to save articles to read later, download spectrum collections, and participate in conversations with readers and editors. for more exclusive content and features, consider joining ieee ., join the world’s largest professional organization devoted to engineering and applied sciences and get access to all of spectrum’s articles, archives, pdf downloads, and other benefits. learn more →, join the world’s largest professional organization devoted to engineering and applied sciences and get access to this e-book plus all of ieee spectrum’s articles, archives, pdf downloads, and other benefits. learn more →, access thousands of articles — completely free, create an account and get exclusive content and features: save articles, download collections, and talk to tech insiders — all free for full access and benefits, join ieee as a paying member., 5g networks are worryingly hackable, a shift to the cloud is opening the industry up to new attacks.

Prominent tech firms like Microsoft and NEC have recently expressed concerns over the security and perhaps too-rapid adoption, respectively, of critical 5G technologies. Now German security researchers have given some substance to the industry’s fears and unease.
At a hacker conference held in the Netherlands last month, Karsten Nohl , founder of Berlin-based Security Research Labs , outlined how his team had breached live 5G networks in a series of “red teaming” exercises—where hackers are hired by a company to test their defenses. In most cases they were able to take control of the network, he says, potentially allowing them to steal customer data or disrupt operations.
The hacks, revealed at the May Contain Hackers 2022 event (a.k.a. MCH2022 ), were made possible thanks to poorly configured cloud technology, which is playing an increasingly important role in 5G networks. Nohl says many telcos are inexperienced in how to protect such systems, and his team found that operators had failed to apply basic cloud security techniques that could help mitigate hacks.
The push toward Open RAN, virtualization, and “cloudifcation” unlocks more choice and functionality for 5G operators. It has also thrust them into the unfamiliar role of system integrator, suddenly responsible for securing the entire supply chain.
“5G has swept over telcos with all its implications, and nobody seems well prepared,” says Nohl. “We are introducing new technology into mobile networks, and those technologies can greatly enhance the security of our mobile networks. Or they can basically destroy any hacking resistance we’ve built up over the years. People are not aware of those choices.”
Mobile operators have traditionally relied on proprietary hardware from vendors like Ericsson, Nokia, and Huawei to build their networks. But in recent years, there has been a major push to “virtualize” network functions, which involves replicating key components in software so they can run on generic hardware, or even in the cloud. And the advent of 5G has only heightened the demand for virtualization, in particular when it comes to radio access networks (RANs) —the part of the network involved in connecting end-user devices like cellphones to the network core.
Virtualization has a host of benefits, including the ability to deploy networks faster and more cheaply, to quickly upgrade networks, and even to dynamically reconfigure them in response to changing situations on the ground. The decoupling of hardware and software also prevents vendor lock-in and allows network operators to mix and match components from different companies, something advocated for by the Open RAN movement .
But these new capabilities are also making 5G networks more complex, says Nohl, which in turn necessitates the increasing use of automation to manage networks. And the ability to mix and match software and services from different companies means far more people are involved in the development pipeline. “The more stuff you have and the more moving parts, the more opportunities for mistakes, little misconfigurations,” says Nohl.
This makes it much easier to break into such virtualized networks than was previously possible. Among the entry points the team discovered included a backdoor-revealing API that had been posted publicly to the Internet as well as an old development site that had accidentally been left online. But the increased ease with which attackers can penetrate the networks is not in and of itself the main problem. “The really critical question is how difficult it is to break through from your initial foothold to something actually valuable within the network,” says Nohl.
His team found it was worryingly easy to move deeper into the networks they tested, thanks primarily to poorly configured “containers.” These are self-contained packages of software that bundle up an application and everything needed to run it—code, software libraries, and configuration files—so that it can be run on any hardware. Containers are a critical part of the cloud, because they allow different applications from different companies or departments to run alongside one another on the same servers. Containers are supposed to be isolated from one another, but if they are poorly configured it’s possible to break out and gain access to other containers or even to take control of the host system. In multiple instances Nohl and his team found misconfigured containers that allowed them to do just this.
“I saw it many times when security teams were invited to the party when all is done and almost finished. The security guys have a very short time slot in order to fine-tune it—if they are actually allowed to touch it.” —Dmitry Kurbatov, SecurityGen
Some of the above difficulties could be attributed to the fact that telcos are inexperienced when it comes to cloud security, says Nohl. But they also may be taking shortcuts. Often operators are “lifting and shifting” preexisting software components into containers, Nohl said, but many of the settings designed to isolate containers from one another prevent the software from working as it should. Rather than rewriting code, developers often simply remove these protections, says Nohl. “Those shortcuts we see everywhere now,” he says.
“Network operators are having to move into a new operating model that’s significantly different than what they’ve done in the past,” says Eric Hanselman , chief analyst at 451 Research. “The reality is that telcos have never had to deal with these levels of software development or low-level infrastructure management before. They always rely on their suppliers for this.”
While the shift toward Open RAN and the growing virtualization and “cloudifcation” of networks is unlocking more choice and functionality for operators, says Hanselman, it has also thrust them into the unfamiliar role of system integrator, responsible for securing the entire supply chain.
Xavier Costa Pérez , head of 5G networks R&D at NEC Laboratories Europe , disputes that operators are behind the curve when it comes to 5G security. While he admits that the transition to more virtualized networks entails inevitable risks, he says major players are investing heavily in security and partnering with cloud providers to tap into their security expertise. “I think the telco industry is very much aware that this can be a big issue,” he says. “It’s critical for survival, so I don’t think it’s taken lightly at all.”
It’s also important to remember that these kinds of highly virtualized networks still represent only a small portion of the 5G infrastructure today, probably less than 10 percent, says Costa Pérez. And all operators have backup 4G networks that they can switch to in the event of any problems.
Network operators aren’t complacent, says Ian Smith, security operations director at the industry body GSMA . “We know that maintaining security, especially for new network technologies, is an ongoing and evolving effort, and one to which the mobile industry is wholeheartedly committed.”
However, that hasn’t been the experience of Dmitry Kurbatov , cofounder of telecom security startup SecurityGen. He has found that security often appears to be an afterthought, rather than being part of the development process from the start. “I saw it many times when security teams were invited to the party when all is done and almost finished.” he says. “The security guys have a very short time slot in order to fine-tune it—if they are actually allowed to touch it.”
Nonetheless, he’s optimistic about the shift to 5G. Previously, operators had little option but to trust vendors when it came to security, but now they will be able to take matters into their own hands. “You actually can have full visibility and control over [5G] systems and functions, which means now you have the chance as the network owner to be much more secure,” he says.
And even more important, the industry isn’t alone in going through the transition to the cloud, says John Carse, chief information security officer at the Japanese operator Rakuten Mobile , which has been a champion of Open RAN principles. “This is a good thing because it means telecom doesn’t have a special problem to solve,” he says. “Telecom can benefit from adoption of techniques happening in all the industries surrounding it versus trying to overcome proprietary challenges.”
- The “Softwarization” of Telecommunications Systems - IEEE Spectrum ›
- Why the World's Militaries Are Embracing 5G - IEEE Spectrum ›
- Why Are Large AI Models Being Red Teamed? - IEEE Spectrum ›
- Virtualized 5G RAN : why, when and how? - Ericsson ›
- 5G network virtualization: will you take the lead? - Kearney ›
Edd Gent is a freelance science and technology writer based in Bengaluru, India. His writing focuses on emerging technologies across computing, engineering, energy and bioscience. He's on Twitter at @EddytheGent and email at edd dot gent at outlook dot com. His PGP fingerprint is ABB8 6BB3 3E69 C4A7 EC91 611B 5C12 193D 5DFC C01B. His public key is here. DM for Signal info.
Really marvelous write. That 5G issue with virtualization and slicing is really big problem in our networks and services because everybody talk only about possibilities but they don't talk about cyber security challenges at all. And attacker and cyberattackers use those 5G vulnerabiltiers and different attack possibilities from almost everywhere from our networks and services around the world to attack against our systems. I have talk about this in my dissertation "Cyber Security and Energy Efficiency in the Infrastructures of Smart Societies", JYU Dissertation, 173, 2019. A lot of thanks to Edd Gent.
Smart Roads Get Better Eyesight
Get to know the ieee board of directors, curving terahertz signals around obstacles for 6g, related stories, ieee spectrum’s top telecom stories of 2023, electronic warfare, hackable 5g networks, and cell towers on the moon, space 5g is on the launchpad.

- Remember me Not recommended on shared computers
Forgot your password?
Or sign in with one of these services
- We ask and you answer! The best answer wins!
- problem solving

Asked by Vishwadeep Khatri , March 8, 2022

5G is a Japanese rapid problem solving tool that enables teams to perform the root cause analysis with a holistic perspective. It stands for Gemba – the real place, Gembutsu – the real tools pertaining to the Gemba, Genjitsu – the real facts which can be obtained only from the Gemba, Genri – that explains the principle of operation and Gensuko – Standardization or Institutionalization.
An application-oriented question on the topic along with responses can be seen below. The best answer was provided by Johanan Collins and Shiva Kumar V.
Applause for all the respondents - Johanan Collins, Shiva Kumar V.
Vishwadeep Khatri
Q 452. Explain the 5G technique for problem solving with a suitable example.
Note for website visitors - Two questions are asked every week on this platform. One on Tuesday and the other on Friday.
- All questions so far can be seen here - https://www.benchmarksixsigma.com/forum/lean-six-sigma-business-excellence-questions/
- Please visit the forum home page at https://www.benchmarksixsigma.com/forum/ to respond to the latest question open till the next Tuesday/ Friday evening 5 PM as per Indian Standard Time. Questions launched on Tuesdays are open till Friday and questions launched on Friday are open till Tuesday.
- When you respond to this question, your answer will not be visible till it is reviewed. Only non-plagiarised (plagiarism below 5-10%) responses will be approved. If you have doubts about plagiarism, please check your answer with a plagiarism checker tool like https://smallseotools.com/plagiarism-checker/ before submitting.
- The best answer is always shown at the top among responses and the author finds honorable mention in our Business Excellence dictionary at https://www.benchmarksixsigma.com/forum/business-excellence-dictionary-glossary/ along with the related term
Link to comment
Share on other sites, 3 answers to this question.
- Sort by votes
- Sort by date
Recommended Posts

Shiva Kumar V
The first “G” is called the Gemba. “Go to the real place” The Gemba is the place where the event took place /at the s ource of the problem. It is critical that your team start by jointly going to the Gemba to start your investigation.
The second “G” is known as Genbutsu. “Examine the Object/tool”. While at the Gemba, your team observe the equipment parts and materials that were involved in the equipment failure. In most cases, the part may have been removed or replaced before the team has assembled. Hence, your team must keep the failed part handy to perform analysis to see if you can find any evidences to see how the part failed.
The third “G” is Genjitsu. “Check the real facts”, for this step, your team must gather all the available data about the process, equipment, and materials before and after the equipment failure. This data will play a key role in link the facts behind the evidence that the team sees and understand what really happened.
The fourth “G” represents Genri. “Vefiy the Principles” Having the principles of operation available while your team is gathering data about the equipment is key in being able to position the correct movement of the equipment. This will help your team clearly see how the equipment is different from standard.
The fifth “G” is Gensoku. “Check the Process SOPs/Standard practices” There is a chance that the equipment didn’t just fail because it was poorly manufactured. The team must also have knowledge of the operating procedures that administer the actions of the machine operator and verify that human intervention did not lead to the equipment failure. You should reference your process SOPs, instruction manual during your investigation
Car accident
Johanan Collins
Gen-ba or Gemba means Real Place . It means going to the actual place where the problem has occurred. An interesting article about the difference between Gemba and MBWA (Management by Walking Around) is on the Benchmark Six Sigma Forum. (Link in Reference 1)
Gen-butsu means Real Part . Go to the real place and observe the real part and the real process.
Gen-jitsu means Real Facts . It means collecting the real facts by going to the real place and observing the real part and the real process. This can be compared to the standard or ideal condition. The 4M data, i.e., Man, Machine, Material and Method may be collected.
3G Principles . Genba, Gebbutsu, and Genjitsu form the 3G Principles.
5G Principles . Genri and Gensoku are added to the 3G Principles
Genri means Principles . It means verifying the related theory and/or principles. This helps in Root Cause Analysis
Gensoku means Fundamental Rules . It means checking the Standards, Standard Operating Procedures, parameters, the level of training, motivation, etc.
Example. Optimizing Crew Transportation of an Airline at a Metro City.
ABC Airlines operates International and Domestic flights for their Pilots and Cabin crew from XYZ city. A transport delay generally leads to a flight delay causing both tangible and intangible loss for the airline. The transportation operations are contracted out to a vendor to carry out the operations.
Problem . Increase in Flights being delayed on account of transport. Vendor asking for an increase in the number of cars for the operation.
Application of 5G Principle
Genba . This involved a visit to the airport and observing the operations both secretively, from a distance, and from within the parking lot.
Genbutsu . Here it was observing the real process both for travel from home to airport and vice versa.
Genjitsu . The real facts were collected some of these were, the geolocation of the addresses of all crew to calculate time and distance, flight schedule throughout the day, no of cars actually deployed with their registration numbers, odometer reading of all cars, number of crew in each car per trip, the spatial distance between crew being clubbed together in each trip, flight time – airport droptime on pickup , waiting time on drop, GPS feed, number of vendor supervisors deployed, non-productive trips (one way empty), breakdowns, preventive maintenance, the interaction between vendor supervisor, airline supervisor and crew, etc.
Genri . The next step was to verify the related theory/principles.
Timeline . A timeline of the entire operations was drawn out in Excel and peak loads and lean periods were calculated. The operations were balanced by combining the domestic and international operations into one contract. Further peak loads were handled through the hiring of Meru/Ola/Uber Cabs available at the airport.
Geolocation . Geolocations of all crew members were plotted on the map and theoretical distances were calculated. These were compared with the actual odometer readings for corroboration of the facts. Infor Optimization Software, which is designed on various transportation and supply chain optimization theories such as traveling salesman etc., was deployed for optimizing the operations.
Actual Odometer Readings . Actual daily odometer readings for each day of operations obtained from the cars, compared with the GPS readings. Average readings and standard deviations were calculated and the area under the normal curve was used to calculate probabilities of delay.
Non-Productive Trips . Details of non-productive trips were studied and fed into the software which reduced the number of trips.
Stakeholder Analysis . The stakeholders were the management (reduction in cost), crew (improved quality of service), vendor (increase in profit), Unions (political reasons), etc.
Gensoku . The last step was to establish the Fundamental Rules. The number of cars for the operations was theoretically calculated and corroborated with the actual cars on the ground. Service Level Agreements, taking into consideration inputs from all stakeholders, were included as part of the contract. Airline Supervisors were given authority to hire Meru/Ola/Uber cabs on an as-required basis. The SLAs included the number of cars to be deployed during various time periods (peak and lean time periods) of the operations, waiting times (waiting times were increased in lean periods), number of crew to be clubbed in each cab (this was increased during peak operations), clear accountability and distribution of responsibilities between vendor and airline supervisor.
Final Outcome . The above operations led to a reduction in the number of cars being deployed, nil transport delay on account of transport, increased satisfaction by the crew, clear accountability between vendor and airlines supervisor. The same model with a few modifications was applied in other Metros.
The above example has been written after a detailed discussion with the person in charge of optimizing the transport optimization.
https://www.benchmarksixsigma.com/forum/topic/35238-gemba/#comment-46468
https://www.nikunjbhoraniya.com/2022/01/5-gen-methodology.html
http://www.sixsigmatrainingfree.com/six-sigma-blog/gemba-gembutsu-genjitsu
Mayank Gupta
Both the answers are excellent and very well structured. Hence, both have been declared as winners. Well done!!
Create an account or sign in to comment
You need to be a member in order to leave a comment
Create an account
Sign up for a new account in our community. It's easy!
Already have an account? Sign in here.
Who's Online (See full list)
- There are no registered users currently online
Forum Statistics
- Total Topics 3.3k
- Total Posts 16.8k
Member Statistics
- Total Members 55,131
- Most Online 990 January 13, 2023

- Existing user? Sign In
- Think Pieces
- Guest Posts
Discussions on Topics
- Hypothesis Testing
- Business Analytics
- Customer Satisfaction
- Metrics and Measurement Systems
- DFSS - Design for Six Sigma
- Lean Management
- Root Cause Analysis
- Problem Solving Methodologies
- Efficiency and Productivity
- Online Green Belt
- Online Black Belt
- Create New...
- Memberships
5G model explained

5G Model: This article explains the 5G model in a practical way. Next to what it is, this article also higlights why it is important to analyze our own behavior, the five G’s explained and a pratical example. After reading it, you will understand the basics of this self-development and behavior change method. Enjoy reading!
What is the 5G model?
The 5G model is a Cognitive Behavioral Therapy (CBT) tool for organizing thoughts and behavior. It was developed to get a deeper understanding of the effects certain events have on human behavior.
It helps to accurately explain thoughts and emotions and to discover patterns, schemas and non-functional behavior in them. This makes it easier to adjust our behavior and function better.

The meaning of events especially becomes clear from the way we deal with and react to these events. Its interpretation and associated feelings therefore play an important role.
Where one person quickly becomes upset in a certain situation, another can easily park things or ignore them. What goes for everyone is that events can be used to learn something about our own response. That response is also the only thing we can control as humans. The events themselves are outside our influence.
The 5Gs are derived from Dutch and translate as follows:
- Event (Gebeurtenis)
- Thoughts (Gedachten)
- Feelings (Gevoelens)
- Behavior (Gedrag)
- Result (Gevolg)
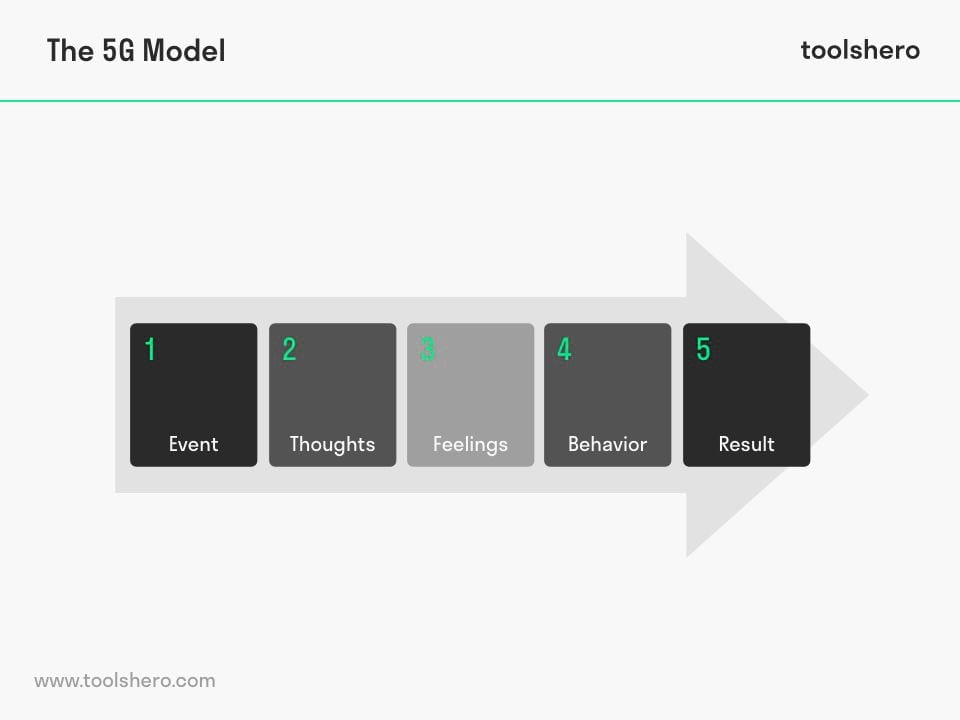
Figure 1 – the five G’s to analyse behavior
5G model: why is it important to analyze our own behavior?
In difficult times and in difficult situations, people often behave in the same way. Some people, with the power of positive thinking, will do everything they can to approach the situation in a positive way.
Other people, however, are quick to think negatively and repeat doomsday scenarios in their heads so that the outcome is almost always negative. The focus is on the negative, on what can go wrong.
This focus on the negative keeps people from doing new things. They withdraw from new situations and hardly gain any new experiences. The consequence of this is that in the long term people get stuck in a negative thinking pattern.
This situation will not improve as long as behavior and response remain the same. We call this a non-functional response. This mindset makes people passive and negative.
5G model: the 5Gs explained
The five Gs are briefly explained below:
A person is confronted with events throughout the day. These events are either fun or less fun.
These events lead to having thoughts. These thoughts are not created manually, but automatically enter one’s mind and are actually a concrete interpretation of the events. The kinds of thoughts a person gets when experiencing an event are often based on previous experiences of a similar event.
Getting certain thoughts comes with a feeling. The primary, most important categories of feelings are fear, anger, sadness, happiness, etc. These feelings are always personal and based on emotions.
Feeling is expressed in behavior. When someone is afraid of something, this person often chooses the easy way out. This also happens when someone knows that choosing the easy way out does not lead to the desired result. Behavior stems from feelings and emotions and is therefore not always rational.
The behavior that one shows has consequences. There are fun and less fun results associated with different types of behavior.
How can the 5G model help?
The 5G model can help to map these behaviors and the patterns in these behaviours. Write down what thoughts and feelings come up as you experience an event. Afterwards, determine whether these feelings and thoughts were realistic or not.
Then determine whether the thoughts and feelings you have are helping you get to the desired result. Or are these based on fear of the unknown or simply an irrational fear of something that need not be feared? What would happen when negative thoughts are replaced by positive thoughts? How would this affect your feelings and behavior? Would the desired outcome be achieved?
Practical example
In the example below you can read how one event could turn out in two different ways.
Situation 1
- Event : Ricky has vowed to abstain from alcohol for a month. When having lunch with his 5 friends, a bottle of wine is ordered. His friends ask him to join in the fun.
- Thoughts : If I say no, everyone thinks I’m unsociable and boring.
- Feeling : Fear of the opinion of his friends. Possibly a need for approval and prone to peer pressure.
- Behavior : Even though Ricky had resolved not to drink alcohol, he still says yes to the glass of wine that is offered to him.
- Result : Ricky does not keep his own agreement and therefore does not achieve the desired outcome.
Situation 2
- Thoughts : I’d like to have a glass of wine, but I can safely explain to my friends why I don’t want to drink right now and ask for support to help me with this.
- Feeling : Proud of keeping himself to his own agreement.
- Behavior : Ricky shares his intentions with his friend and does not drink wine.
- Result : Ricky sticks to his own agreements and achieves his goal.
Behavioral Therapy
As mentioned, the 5G model is based on Cogntive Behavioral Therapy, or CBT and on the Aaron Beck model. This Cognitive Behavioral Therapy focuses in particular on changing and eliminating useless and harmful thoughts. By changing harmful thinking patterns, you can find relief from intense emotions such as anxiety that can lead to depression.
CBT methods ensure that the brain is re-learned how to deal with certain thoughts. This often changes the client’s mood in the short and long term. This form of therapy has been shown to be effective in:
- Anxiety disorders
- Preventing and fighting depression
- Treatment of post-traumatic stress disorder (PTSD)
- Chronic forms of pain
- Hormonal problems
- Self-image problems
- Panic attacks
5G model: why negative thoughts?
Even if one doesn’t need cognitive behavioral therapy, it can still be a good idea to use it every now and then. Many people experience stress on a daily basis. With this method, this stress can be coped with.
Many people see negative thoughts that arise during stress as an inner bully. These thoughts come from a certain part of the brain. This part of the brain is widely associated with a mechanism that wants to help us. Thoughts often miss the purpose and so more often make us feel worse than better. This dysfunction can be solved with CBT.
In summary, you can take the following steps to get started:
- Identify a negative thought that often crosses your mind.
- Ask yourself what the purpose is of these thoughts.
- Gather evidence to disprove these thoughts.
- Ask yourself what the wisest and most calm version of yourself would say about these thoughts.
- Make sure you can focus this criticism on something else. Extract meaning from the thoughts.
- Think of another thought for yourself that can help you get out of a negative situation.
- Remind yourself of the new thought until you believe it.

Now it’s your turn
What do you think? Do you recognize the explanation about the 5G model? Can you use this model to organize your thoughts and actions? What other methods for mapping behavior do you know? Do you have any tips or comments?
Share your experience and knowledge in the comments box below.
More information
- van den Berg, B. (unknown). Gedachtentraining… maar dan anders .
- Rothbaum, B. O., Meadows, E. A., Resick, P., & Foy, D. W. (2000). Cognitive-behavioral therapy .
- Beck, A. T., Ward, C., Mendelson, M., Mock, J., & Erbaugh, J. J. A. G. P. (1961). Beck depression inventory (BDI) . Arch Gen Psychiatry, 4(6), 561-571.
- Hollon, S. D., & Beck, A. T. (2013). Cognitive and cognitive-behavioral therapies . Bergin and Garfield’s handbook of psychotherapy and behavior change, 6, 393-442.
How to cite this article: Janse, B. (2022). 5G model . Retrieved [insert date] from Toolshero: https://www.toolshero.com/psychology/5g-model/
Published on: 08/10/2022 | Last update: 04/17/2023
Add a link to this page on your website: <a href=”https://www.toolshero.com/psychology/5g-model/”>Toolshero: 5G model</a>
Did you find this article interesting?
Your rating is more than welcome or share this article via Social media!
Average rating 4 / 5. Vote count: 4
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?

Vincent van Vliet
Vincent van Vliet is co-founder and responsible for the content and release management. Together with the team Vincent sets the strategy and manages the content planning, go-to-market, customer experience and corporate development aspects of the company.
Related ARTICLES

Mandela effect: the meaning, basics and some examples

Albert Bandura biography, theory and quotes

David McClelland biography, books and theory

McGurk Effect in Psychology explained

5 Stages of Grief by Elisabeth Kübler-Ross

Prospect Theory by Amos Tversky and Daniel Kahneman
Also interesting.

Psychological Safety by Amy Edmondson

Barrett Model, a great motivation theory

McClelland Theory of Motivation
Leave a reply cancel reply.
You must be logged in to post a comment.
BOOST YOUR SKILLS
Toolshero supports people worldwide ( 10+ million visitors from 100+ countries ) to empower themselves through an easily accessible and high-quality learning platform for personal and professional development.
By making access to scientific knowledge simple and affordable, self-development becomes attainable for everyone, including you! Join our learning platform and boost your skills with Toolshero.

POPULAR TOPICS
- Change Management
- Marketing Theories
- Problem Solving Theories
- Psychology Theories
ABOUT TOOLSHERO
- Free Toolshero e-book
- Memberships & Pricing

IMAGES
VIDEO
COMMENTS
The most basic and first of four lean tools for simple problem solving is 5G. Also known as the 5 Gen Methodology or the 5 Gen principle, 5G is a popular Japanese problem-solving method used for improving various manufacturing activities. That is to say, it is a tool that describes a loss phenomenon that can be related to safety, quality, parts ...
The methodical approach of resolving the problems in Kobetsu KaizenÔ has some similarities with the 5G approach. The five Gs are Gemba - the real place, Gembutsu - the real tools pertaining to the Gemba, Genjitsu - the real facts which can be obtained only from the Gemba, Genri - that explains the principle of operation and Gensuko ...
Step-by-Step Guide to 5G Problem Solving Technique Application. Step-1. GEMBA. Go to the real place. Create a team and visit to the shop floor or a place where the problem occurred. Step-2. GEMBUTSU. Examine the objects. Examine the machine /tools /equipment/non-conforming pats to know the clues.
The added advantage is the 5G approach quashes the division in organizations created by opinions as it is focussed on Data & Facts. Problem solving becomes more structured with revision of ...
Utilizing the "5G Principles" truly took my ability to lead a team during an RCA to another level. The use of 5G in combination with access to a robust root cause analysis tool allowed me to ...
Cyber researchers from Virginia Tech developed a technique to solve 5G network problems in the field and in real time. With support from the Commonwealth Cyber Initiative, they are applying their invention to safeguard autonomous vehicles and provide efficient network solutions in other domains.
discuss problem structuring and modelling techniques and their application to our problem. Further, we apply stakeholder mapping and Hierarchical Process Modeling (HPM). In section IV we discuss the implications of our problem structuring. In section V we perform a second iteration of our methodology incorporating our findings so far.
1.3 Scope and paper organization. The objective of this survey is to give a definite guide for 5G network and ML methods researchers and understand how the existing works addressed 5G problems and developed solutions in order to tackle the 5G challenges, what are ML methods that must be applied and how it can solve the problems.
Solving 5G's Thorniest Issues. Incomplete roadmaps and continued uncertainty about millimeter-wave technology make this technology's future hazy, but solutions are in the works. August 1st, 2019 - By: Ed Sperling. 5G rollouts are beginning to hit the market, accompanied by a long list of unsolved technical and business issues surrounding ...
Quality of coverage is the key to affect the quality and index of mobile communication, so it is very important to solve the problem of coverage. From the perspective of improving the quality of 5G wireless network, this paper studies the common weak coverage and over coverage problems in 5G wireless network, analyzes the causes, the processing ideas and analysis methods in daily centralized ...
Mitigating the complexity of 5G distributed networks. - This includes addressing the very modern need for increased density. Keeping OpEx cost under control in the 4G to 5G transition. Meeting ultra-low, deterministic latency requirements. Capably serving up new capabilities. - This includes entering new markets.
This is a much smaller number than it sounds like. Apple is going to sell something like 150-175 million 5G phones in fiscal 2021. That's 1.2-1.4 billion front-end modules. The much bigger ...
The team decided to change old habits by developing a structured problem-solving process for the Heston facility. The approach leverages several tools including 5G, 5W1H, 4M1D & Confirmation, the 5 Whys, and levels of countermeasures. AGCO also implemented KaiNexus to support every aspect of the new problem-solving paradigm.
Almost a third of respondents in Jabil's 5G survey (31%) indicated that these business model challenges were the most difficult category of 5G issues for their organization to solve, compared with 19% who were most challenged by operational hurdles, 18% technology challenges and 16% by supply chain or customer issues.
Mastering GEMBA, GENBUTSU, GENJITSU, GENRI, GENSOKU Problem Solving" 🌐 #5GProblemSolvingMasteryDescription:🚀 Ready to propel your career to new heights in ...
High accuracy in representing the channels, better network design and orientations, and the apt simulation tool can be the only solution to solve research problems in 5G. You, as a researcher, need to understand the importance of it and make your project contribute an immensely important application to the above list.
ITU AI/ML in 5G Challenge 2021 Problem statements Published Version #3, 30 June 2021 Contents ... Resources NOTE 6- e.g. simulators, APIs, lab setups, tools, algorithms, add a link in clause 2. Any controls or restrictions NOTE 7- e.g. this problem statement is open only to students or
Root Cause Analysis tools: 5 WHY. 3. PLAN. a. Action Plans (Immediate, Intermediate, Long Term) 4. DO. Safety Comes First! OPL's; Implement Actions; Observe Results & Hold the Gains; Before Starting a 5 WHY ANALYSIS … The CHECK phase of CAP-Do must be completed . . . - The problem identified - The Ideal Situation understood
Problem solving software is the best way to take advantage of multiple problem solving tools in one platform. While some software programs are geared toward specific industries or processes - like manufacturing or customer relationship management, for example - others, like MindManager , are purpose-built to work across multiple trades ...
At a hacker conference held in the Netherlands last month, Karsten Nohl, founder of Berlin-based Security Research Labs, outlined how his team had breached live 5G networks in a series of "red ...
5G is a Japanese rapid problem solving tool that enables teams to perform the root cause analysis with a holistic perspective.It stands for Gemba - the real place, Gembutsu - the real tools pertaining to the Gemba, Genjitsu - the real facts which can be obtained only from the Gemba, Genri - that explains the principle of operation and Gensuko - Standardization or Institutionalization.
The 5G model is a Cognitive Behavioral Therapy (CBT) tool for organizing thoughts and behavior. It was developed to get a deeper understanding of the effects certain events have on human behavior. It helps to accurately explain thoughts and emotions and to discover patterns, schemas and non-functional behavior in them.